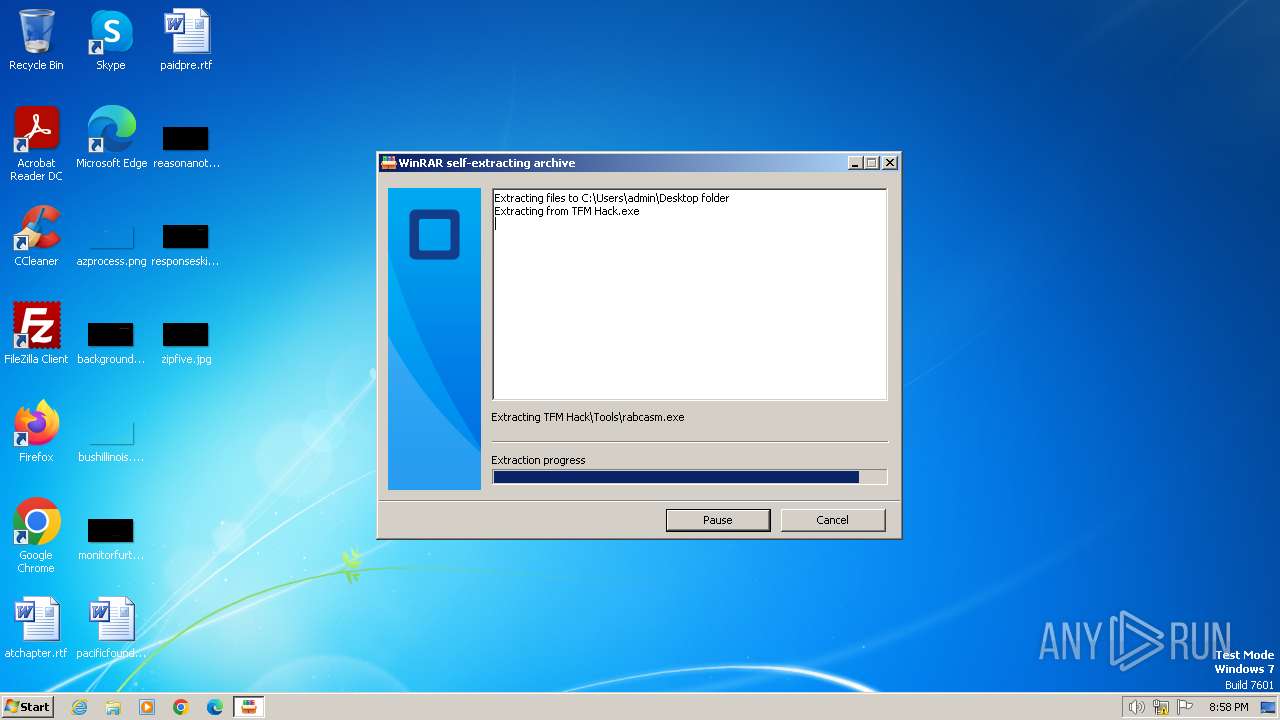
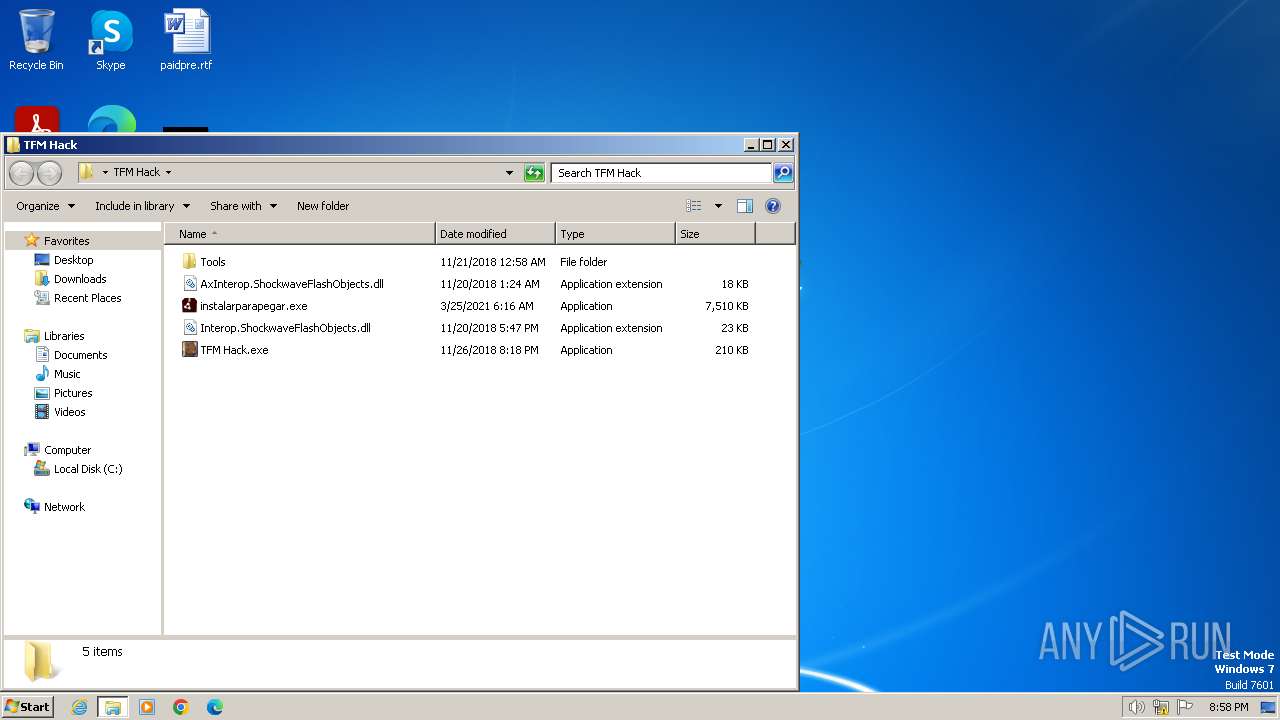
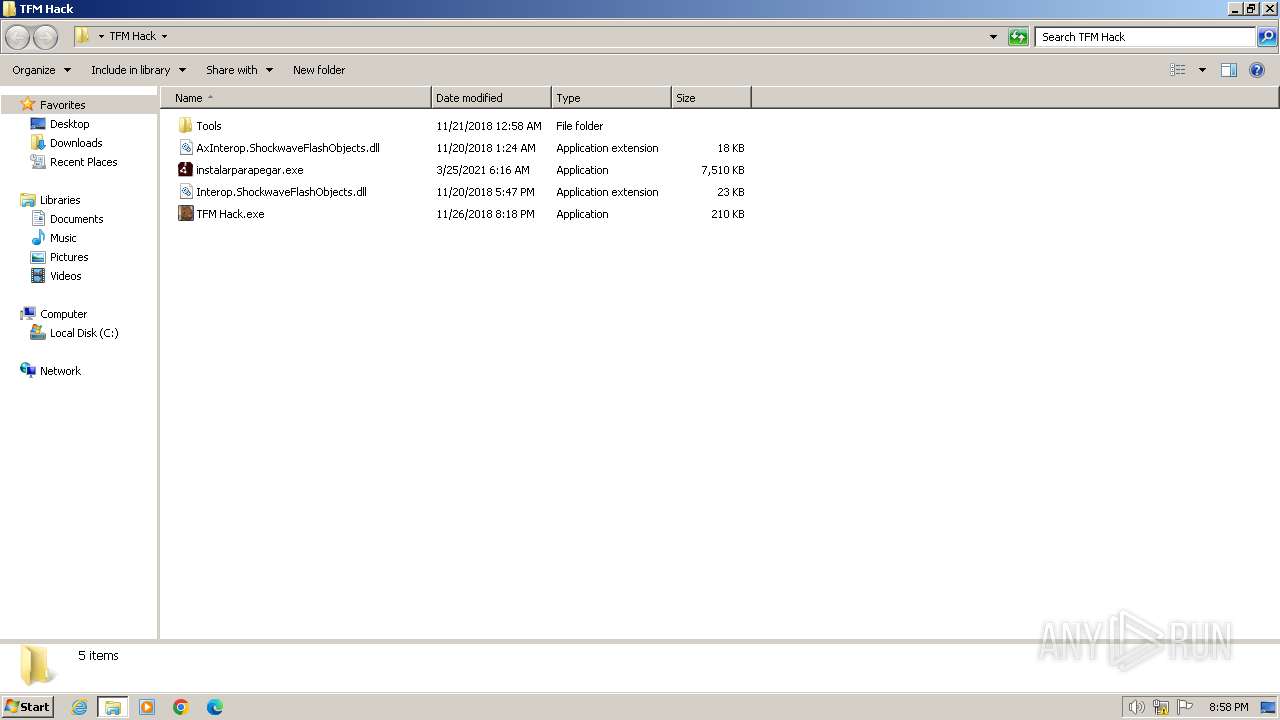
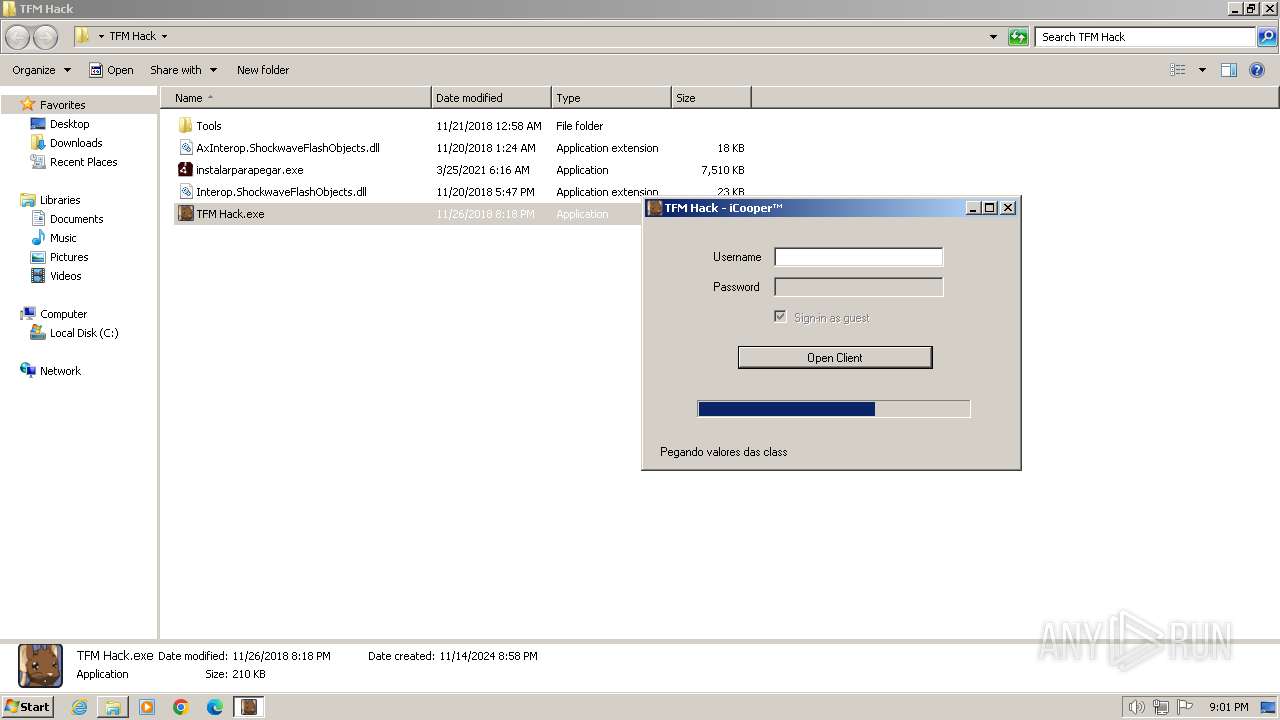
| File name: | TFM Hack.exe |
| Full analysis: | https://app.any.run/tasks/68c46728-bff5-487d-88bb-1a9c615c67d9 |
| Verdict: | Malicious activity |
| Analysis date: | November 14, 2024, 20:57:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | C4809C0D73A68D2B1866D65BB7E3A1E1 |
| SHA1: | 3102B24D5BB8FE0F44A20312AEAADF570B251791 |
| SHA256: | 65D152527E39C98C9E7D3B61F82925714871CBA960940AE3535C6224ABB87F6F |
| SSDEEP: | 98304:k1zY2fboBYg1TLYgBrExkxmMDJaIJfK0dU/4vfoe6vAqDEdzXYm4e2Lk4EB15IQ0:YqK/uh5l55hyh |
MALICIOUS
Executing a file with an untrusted certificate
- rabcdasm.exe (PID: 1468)
- abcexport.exe (PID: 3132)
- rabcdasm.exe (PID: 3360)
- rabcdasm.exe (PID: 3496)
- rabcdasm.exe (PID: 3328)
SUSPICIOUS
Reads security settings of Internet Explorer
- TFM Hack.exe (PID: 2640)
Reads Microsoft Outlook installation path
- TFM Hack.exe (PID: 2640)
Reads Internet Explorer settings
- TFM Hack.exe (PID: 2640)
Executable content was dropped or overwritten
- TFM Hack.exe (PID: 2640)
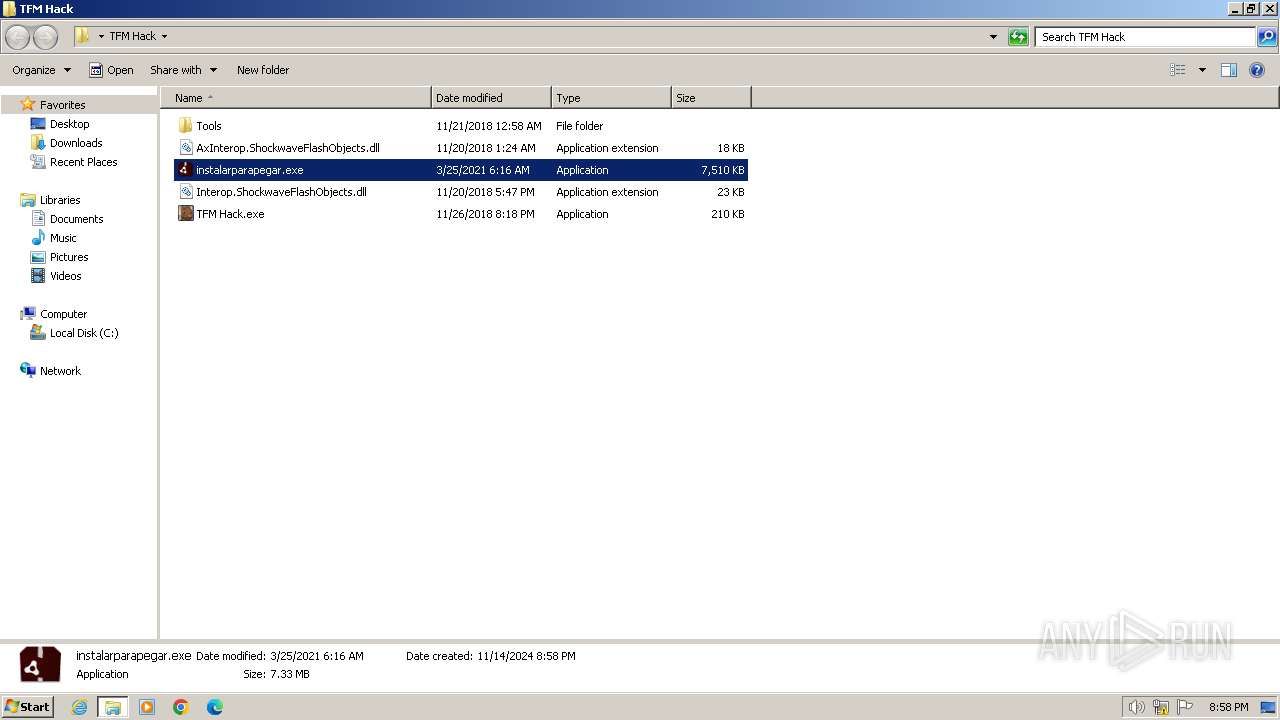
- instalarparapegar.exe (PID: 924)
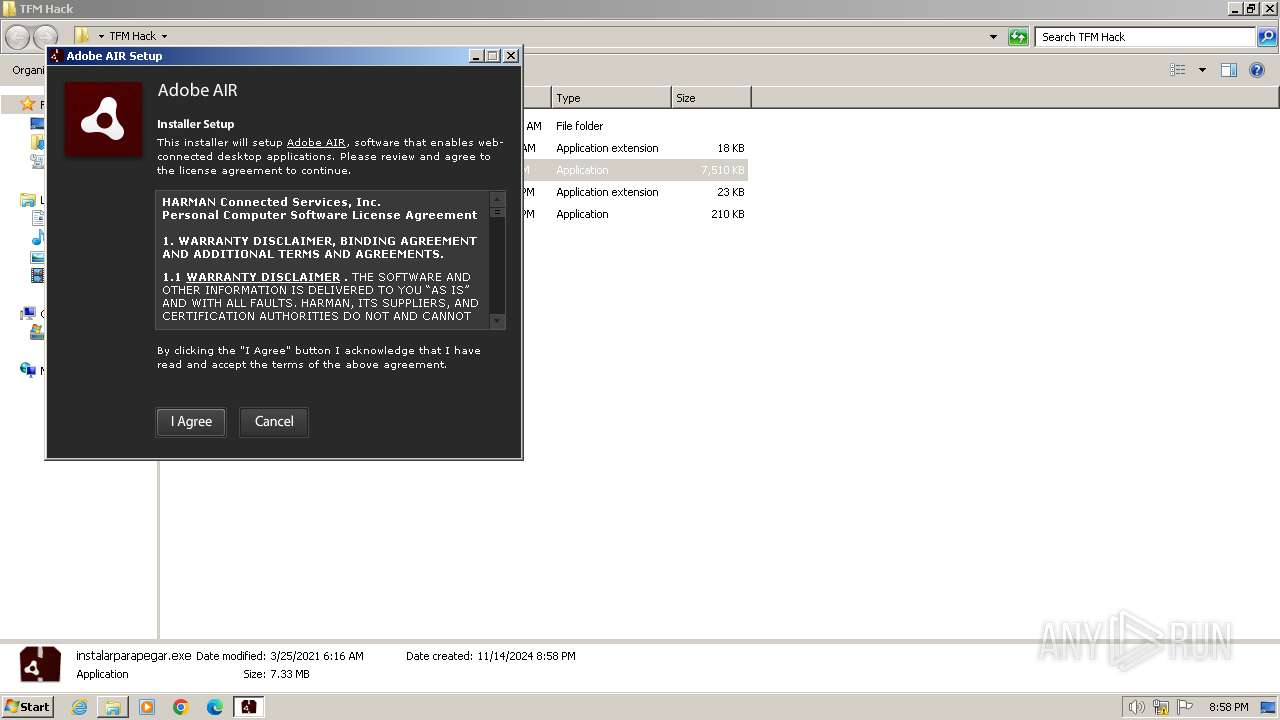
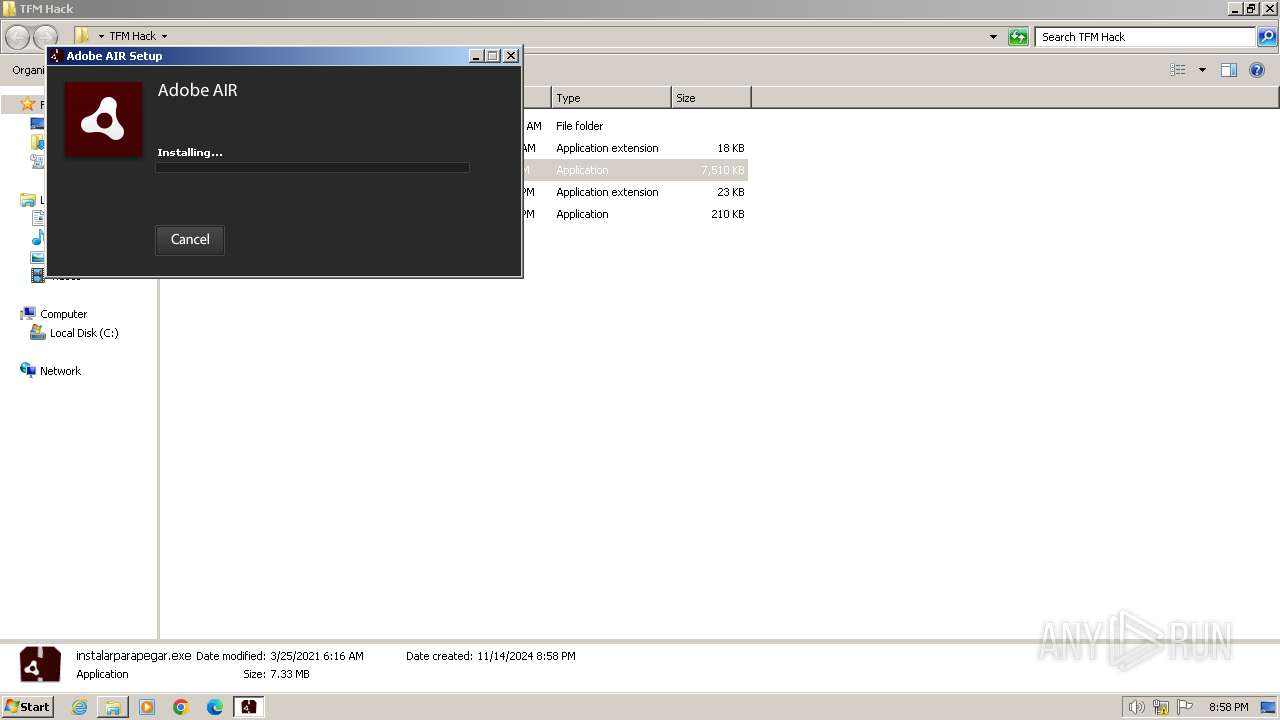
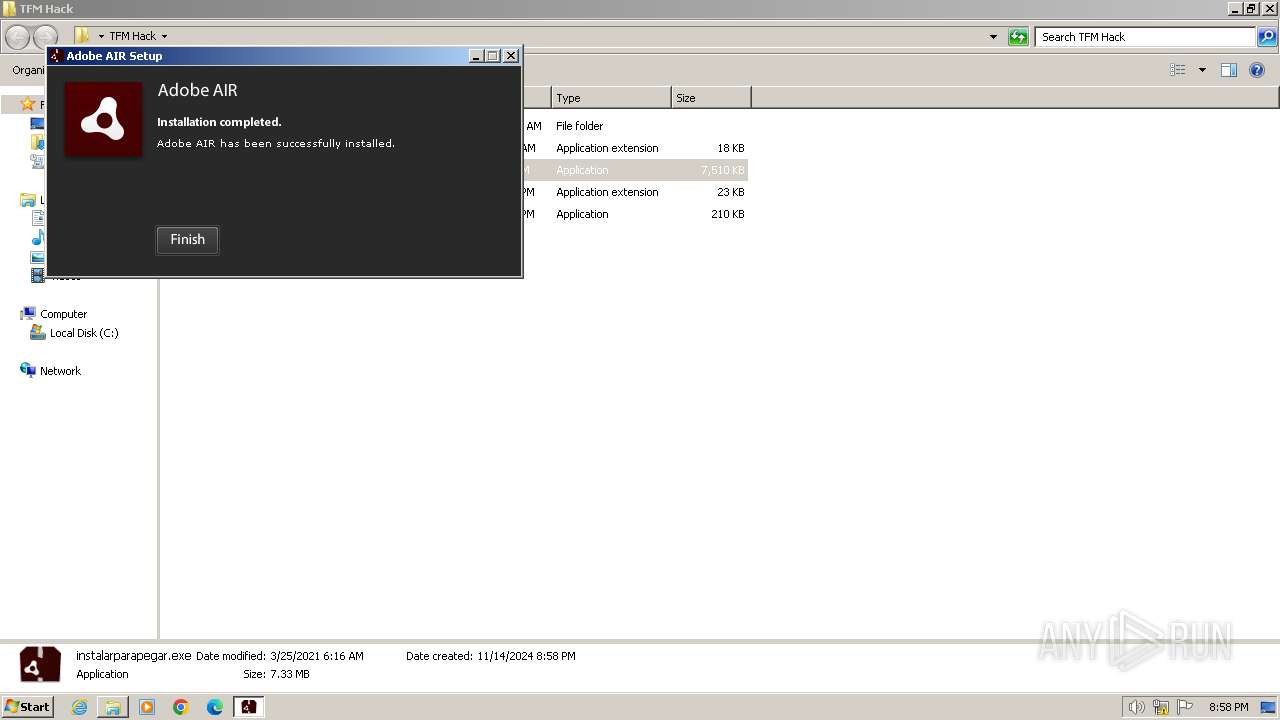
- AIRInstaller.exe (PID: 1808)
- Adobe AIR Installer.exe (PID: 3524)
- Adobe AIR Installer.exe (PID: 4056)
Starts itself from another location
- instalarparapegar.exe (PID: 924)
Application launched itself
- Adobe AIR Installer.exe (PID: 4056)
Reads the Internet Settings
- TFM Hack.exe (PID: 2640)
INFO
Checks supported languages
- TFM Hack.exe (PID: 2640)
Reads the computer name
- TFM Hack.exe (PID: 2640)
Reads the machine GUID from the registry
- TFM Hack.exe (PID: 2640)
Manual execution by a user
- instalarparapegar.exe (PID: 924)
- TFM Hack.exe (PID: 2412)
- wmpnscfg.exe (PID: 2452)
Checks proxy server information
- TFM Hack.exe (PID: 2640)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3740)
.NET Reactor protector has been detected
- TFM Hack.exe (PID: 2412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:06:25 10:38:24+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 200704 |
| InitializedDataSize: | 254976 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1ea80 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
73
Monitored processes
21
Malicious processes
2
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 924 | "C:\Users\admin\Desktop\TFM Hack\instalarparapegar.exe" | C:\Users\admin\Desktop\TFM Hack\instalarparapegar.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe AIR Installer Exit code: 0 Version: 33.1.1.385 Modules
| |||||||||||||||
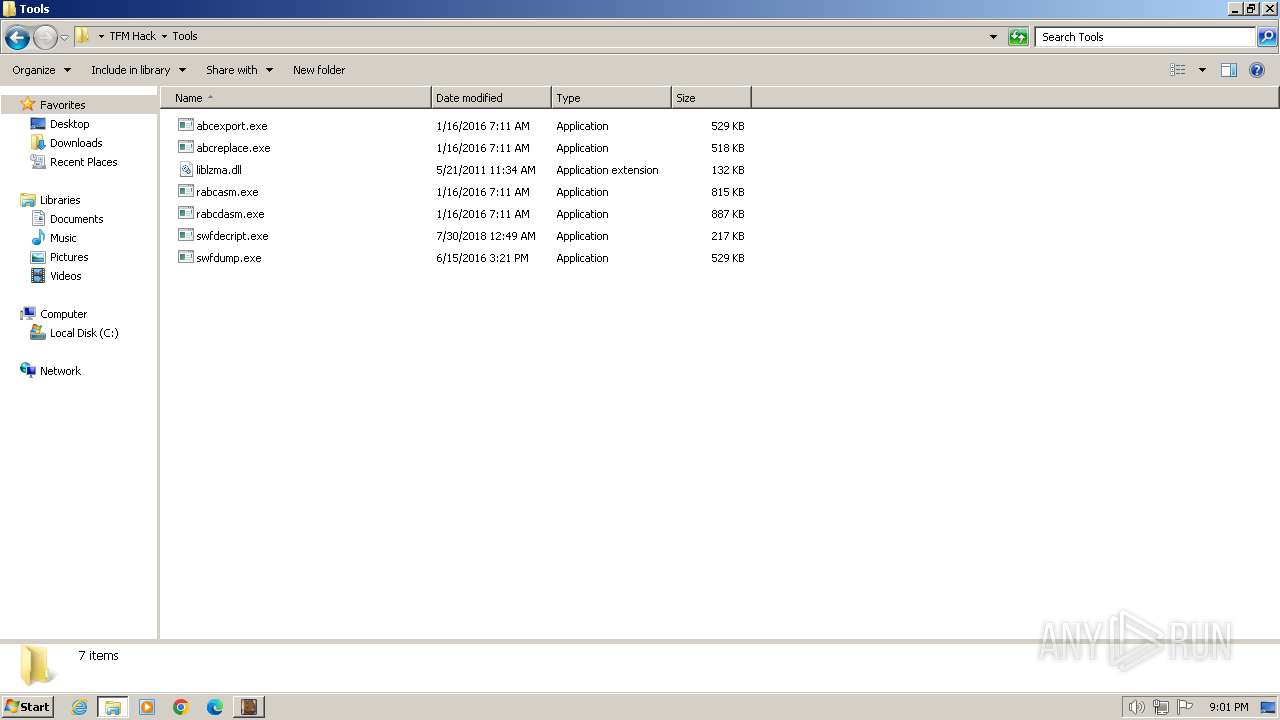
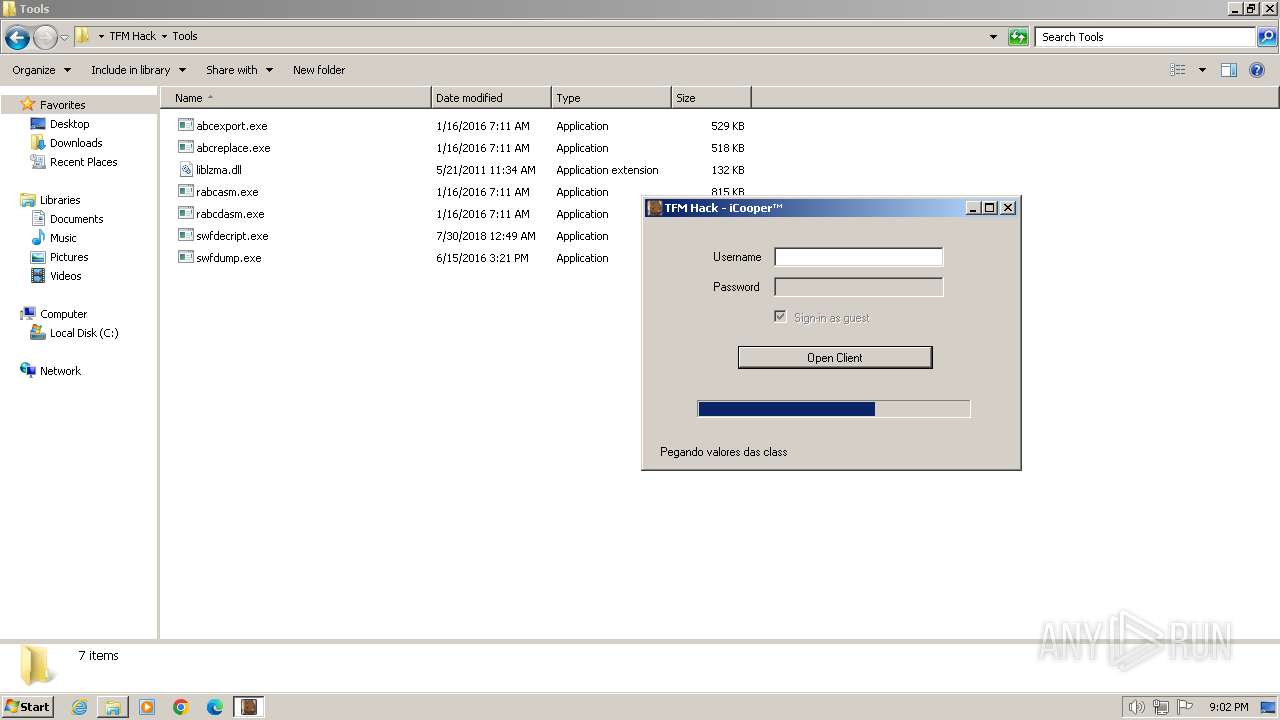
| 1144 | "C:\Users\admin\Desktop\TFM Hack\Tools\swfdecript.exe" Transformice.swf Transformice.swf | C:\Users\admin\Desktop\TFM Hack\Tools\swfdecript.exe | — | TFM Hack.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 | |||||||||||||||
| 1368 | "C:\Users\admin\Desktop\TFM Hack\Tools\abcexport.exe" ChargeurTransformice.swf | C:\Users\admin\Desktop\TFM Hack\Tools\abcexport.exe | — | TFM Hack.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 1468 | "C:\Users\admin\Desktop\TFM Hack\Tools\rabcdasm.exe" ChargeurTransformice-0.abc | C:\Users\admin\Desktop\TFM Hack\Tools\rabcdasm.exe | — | TFM Hack.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 1808 | "C:\Users\admin\AppData\Local\Temp\{9B30E029-AEF9-4DDC-B160-19815B1102D2}\AIRInstaller.exe" | C:\Users\admin\AppData\Local\Temp\{9B30E029-AEF9-4DDC-B160-19815B1102D2}\AIRInstaller.exe | instalarparapegar.exe | ||||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe AIR Installer Exit code: 0 Version: 33.1.1.385 Modules
| |||||||||||||||
| 1984 | "swfdump.exe" -a "C:\Users\admin\AppData\Roaming\iCooper\IC\Transformice.swf" | C:\Users\admin\Desktop\TFM Hack\Tools\swfdump.exe | — | swfdecript.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
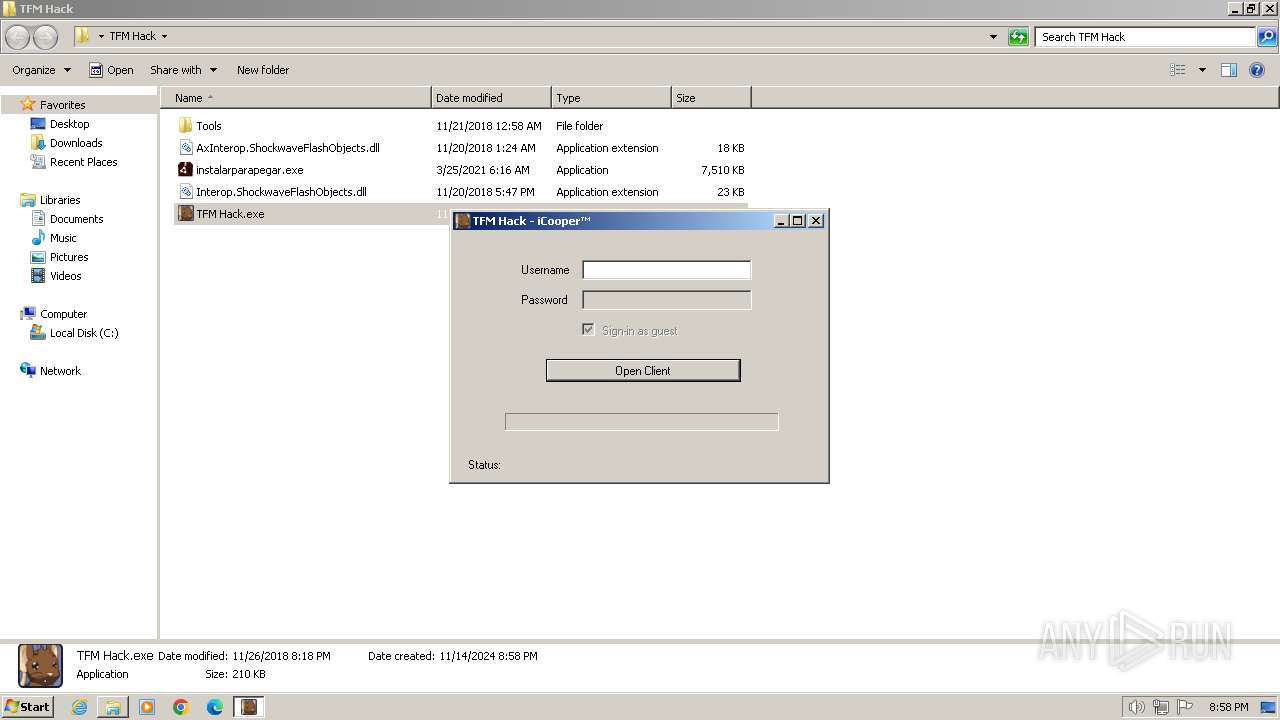
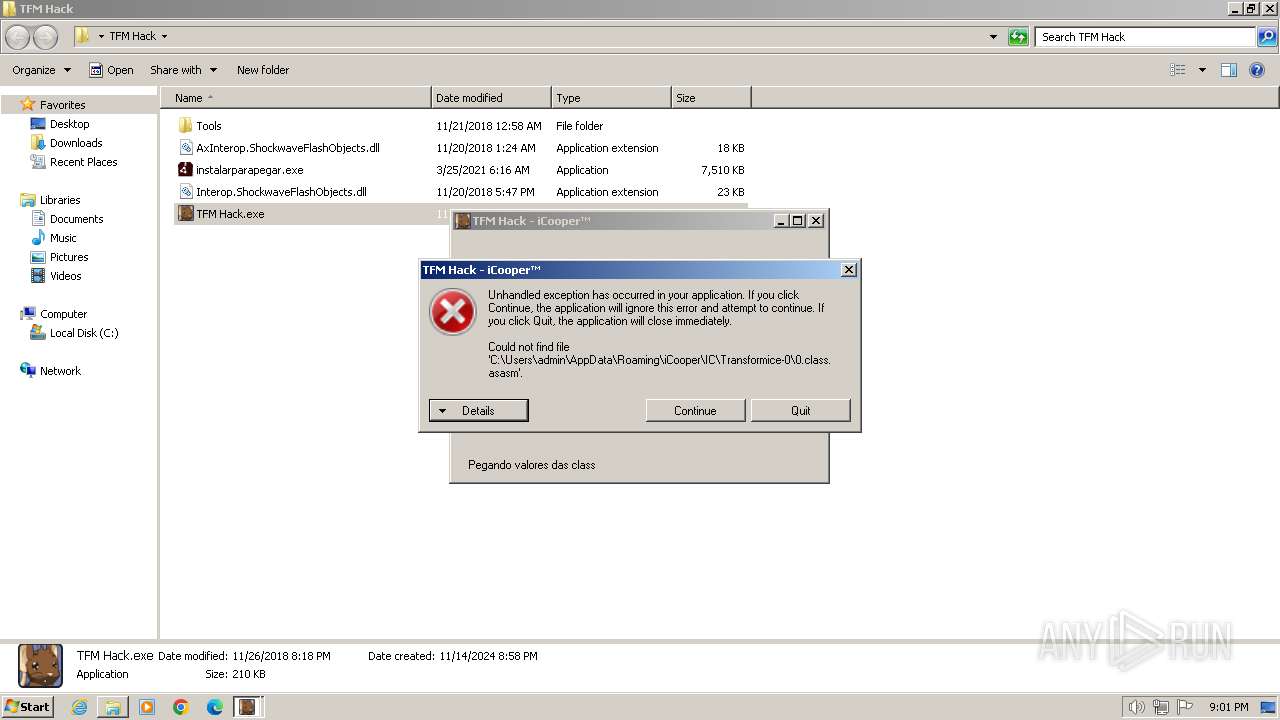
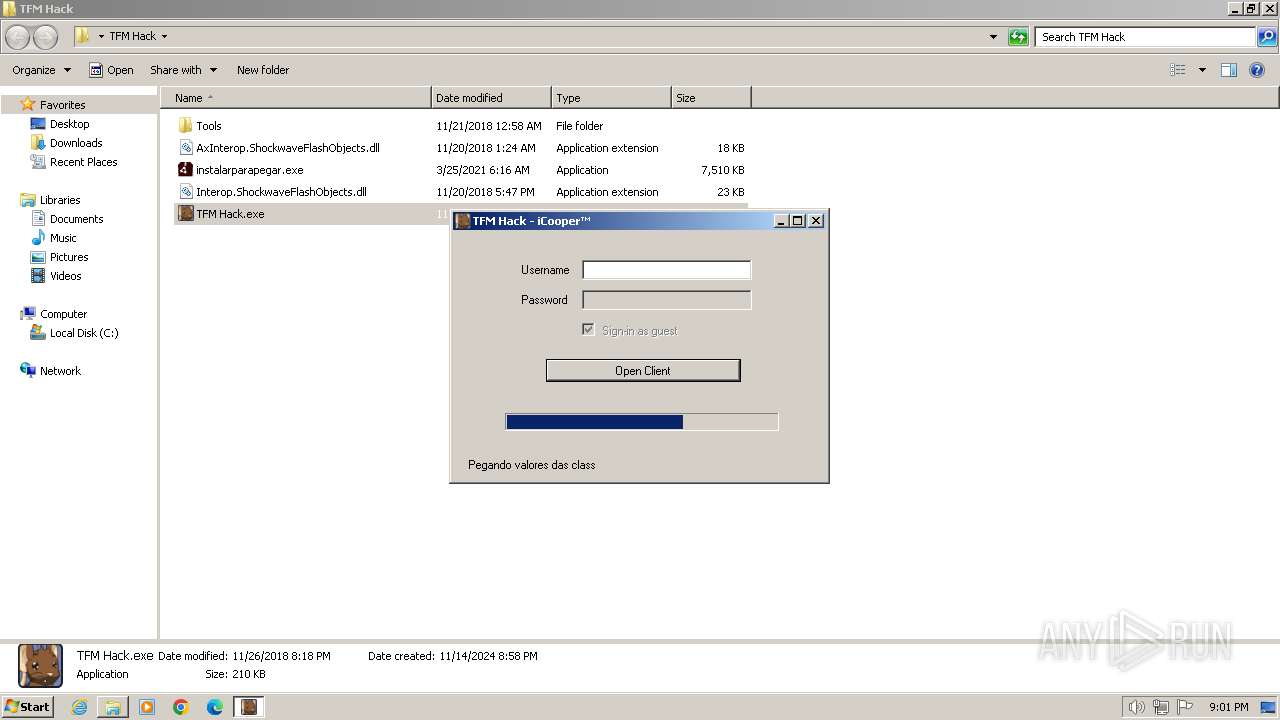
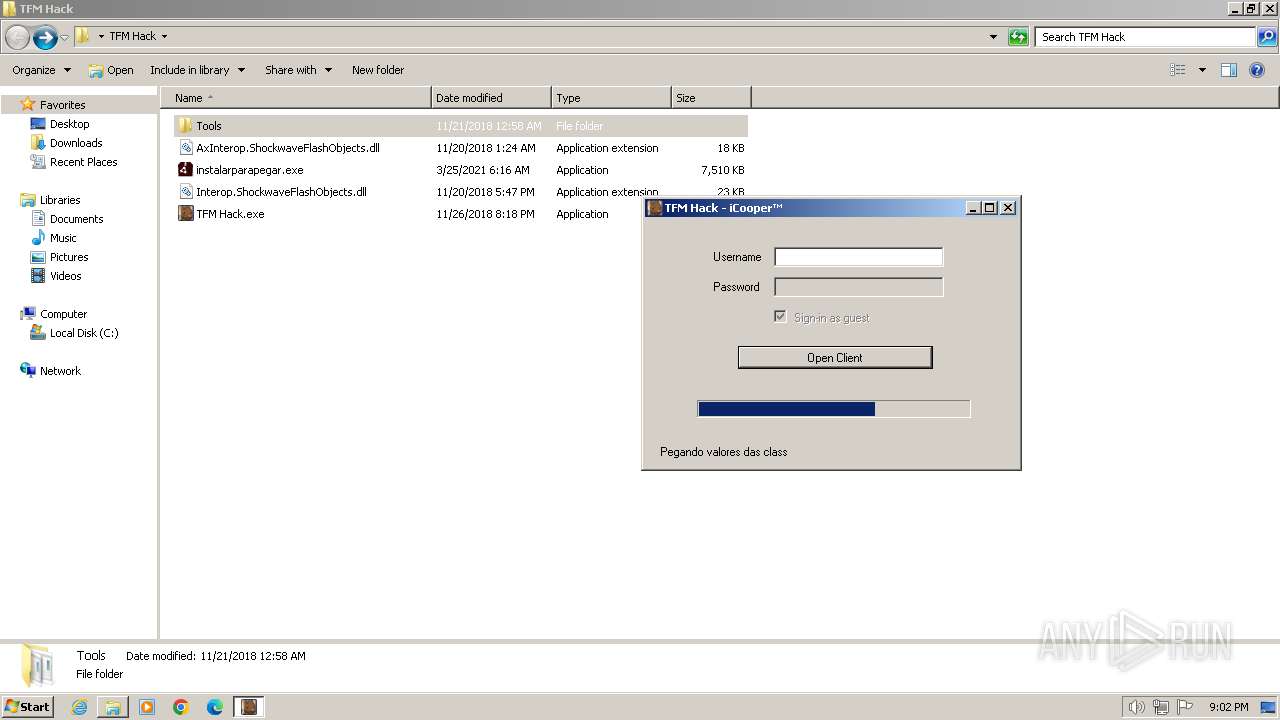
| 2412 | "C:\Users\admin\Desktop\TFM Hack\TFM Hack.exe" | C:\Users\admin\Desktop\TFM Hack\TFM Hack.exe | — | explorer.exe | |||||||||||
User: admin Company: iCooper™ Integrity Level: MEDIUM Description: TFM Hack Version: 1.0.0.0 | |||||||||||||||
| 2452 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) | |||||||||||||||
| 2532 | "c:\Program Files\Common Files\Adobe AIR\Versions\1.0\Resources\Adobe AIR Updater.exe" -installupdatecheck | C:\Program Files\Common Files\Adobe AIR\Versions\1.0\Resources\Adobe AIR Updater.exe | — | Adobe AIR Installer.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe AIR Installer Exit code: 0 Version: 33.1.1.385 | |||||||||||||||
| 2556 | "C:\Users\admin\Desktop\TFM Hack\Tools\swfdecript.exe" Transformice.swf Transformice.swf | C:\Users\admin\Desktop\TFM Hack\Tools\swfdecript.exe | — | TFM Hack.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.0 | |||||||||||||||
Total events
2 611
Read events
2 579
Write events
30
Delete events
2
Modification events
| (PID) Process: | (2640) TFM Hack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2640) TFM Hack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2640) TFM Hack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2640) TFM Hack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2640) TFM Hack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2640) TFM Hack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2640) TFM Hack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2640) TFM Hack.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2640) TFM Hack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
| (PID) Process: | (2640) TFM Hack.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Height |
Value: 288 | |||
Executable files
40
Suspicious files
52
Text files
3 687
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2640 | TFM Hack.exe | C:\Users\admin\Desktop\TFM Hack\Interop.ShockwaveFlashObjects.dll | executable | |
MD5:13D2402E7F83EA1ABB7A5EDF1DDD256A | SHA256:49CA4839C5B44DA53EC193BBC2888B588E5EE87594071FBD79B0D5CB75D9EFFC | |||
| 2640 | TFM Hack.exe | C:\Users\admin\Desktop\TFM Hack\Tools\swfdump.exe | executable | |
MD5:5BBFD38940063BB3ED78FC2137958B0A | SHA256:E803453FE8816CF26B62DBE77AB23EBBDED35C0871E0BF78D86631BF3A034522 | |||
| 2640 | TFM Hack.exe | C:\Users\admin\Desktop\TFM Hack\Tools\rabcasm.exe | executable | |
MD5:A71C93BB550C24DB1EDB27212783EE6F | SHA256:C02A62FA65831F0D165AAD63F9CF589BCB3800A9C1391050A076049014FCBDAC | |||
| 2640 | TFM Hack.exe | C:\Users\admin\Desktop\TFM Hack\Tools\swfdecript.exe | executable | |
MD5:B2838DF135FE035279E47343492B0DB5 | SHA256:FAEF2860350CCF11B3F4BA1A39C194B461F022044814B5CDF68BF2EC47C94F4D | |||
| 2640 | TFM Hack.exe | C:\Users\admin\Desktop\TFM Hack\Tools\rabcdasm.exe | executable | |
MD5:1D285582CE38618A958212E87D06FCC3 | SHA256:F74EAF1822B20B599276A172AF874C2E98BC8CE5A4CAB0A7468AC577F86181B9 | |||
| 2640 | TFM Hack.exe | C:\Users\admin\Desktop\TFM Hack\TFM Hack.exe | executable | |
MD5:3574DBF0EFF99AF5801BFEFF6F61BFE5 | SHA256:4E179769438363BE15F3DD9272658B92881D9729DC533F1522BFDA8C5D68E7E2 | |||
| 2640 | TFM Hack.exe | C:\Users\admin\Desktop\TFM Hack\Tools\abcreplace.exe | executable | |
MD5:4DD89AF63CF75832ED61CB0FD5FD5650 | SHA256:D20B874C050950A1D400694CC6D440B4BCB07E9DB21E65444E5B9F6C3072EC80 | |||
| 1808 | AIRInstaller.exe | C:\Users\admin\AppData\Local\Temp\AIR28AB.tmp\Adobe AIR\Versions\1.0\Adobe AIR Application Installer.swf | swf | |
MD5:9C9D13B4EBCE6056466C3ECED7A60631 | SHA256:54C854CB8DE91C1FCC05BF9ACE5EE71E98E7ECDC80D234EFF54AC1318C43CC9F | |||
| 924 | instalarparapegar.exe | C:\Users\admin\AppData\Local\Temp\{9B30E029-AEF9-4DDC-B160-19815B1102D2}\AIRInstaller.exe | executable | |
MD5:CE0059C94FD5F8099E54F85FF204B511 | SHA256:D5C8659A712145CC19B4E23FF0C731C87FEFC5C100D98C963A2689C5FD97A96C | |||
| 2640 | TFM Hack.exe | C:\Users\admin\Desktop\TFM Hack\Tools\liblzma.dll | executable | |
MD5:0E5D3BC6FF20B7F7C82824E1D5E3512C | SHA256:4F920F7AC2904171CB0F265239EE2225ACB19769D3D438566C0D43E857DEE8A9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
18
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 23.50.131.222:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b790f096f5ab6f97 | unknown | — | — | whitelisted |
— | — | GET | 304 | 23.50.131.207:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a766e13b9e9f695b | unknown | — | — | whitelisted |
— | — | GET | 200 | 18.66.142.79:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 18.66.142.79:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkpLy9ROx7U76vGUhC06D6E%3D | unknown | — | — | unknown |
— | — | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m02.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRmbQtwnInkvkvr7BNFR%2BS2lTYPjAQUwDFSzVpQw4J8dHHOy%2Bmc%2BXrrguICEAwFwxCr3ApB8mRgRstqbKo%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 51.75.128.119:80 | http://transformice.com/Transformice.swf | unknown | — | — | whitelisted |
— | — | GET | 200 | 51.75.128.119:80 | http://transformice.com/Transformice.swf | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.50.131.222:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3c4d1c7aa342ad0e | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
— | — | 34.225.143.41:443 | airsdk.harman.com | AMAZON-AES | US | whitelisted |
— | — | 23.50.131.207:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
— | — | 18.66.142.79:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | whitelisted |
— | — | 18.245.65.219:80 | ocsp.r2m02.amazontrust.com | — | US | whitelisted |
— | — | 142.250.185.78:443 | docs.google.com | GOOGLE | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
airsdk.harman.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.r2m02.amazontrust.com |
| whitelisted |
docs.google.com |
| shared |
drive.usercontent.google.com |
| whitelisted |
transformice.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |