| File name: | t.exe |
| Full analysis: | https://app.any.run/tasks/11c2ae70-c936-4ec3-9804-d95071fd2cbd |
| Verdict: | Malicious activity |
| Analysis date: | May 13, 2025, 18:29:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 05F2CAA03D965D5A9D00BEFE6F29E538 |
| SHA1: | C48615A5FF0E6812A432FBA0B464D12C0B886305 |
| SHA256: | 65C04AADAB715D8DFAC3A4F5EEA780BC2984FA3C4DB7DD13CEA8F05DF0AEFD58 |
| SSDEEP: | 98304:GKCCxu7ZyqLoxTMjjZwhqbeATQchet9WkAQItuK/JVKHrioMs8MzowjRkKoy4PQn:C7l06/s6I |
MALICIOUS
No malicious indicators.SUSPICIOUS
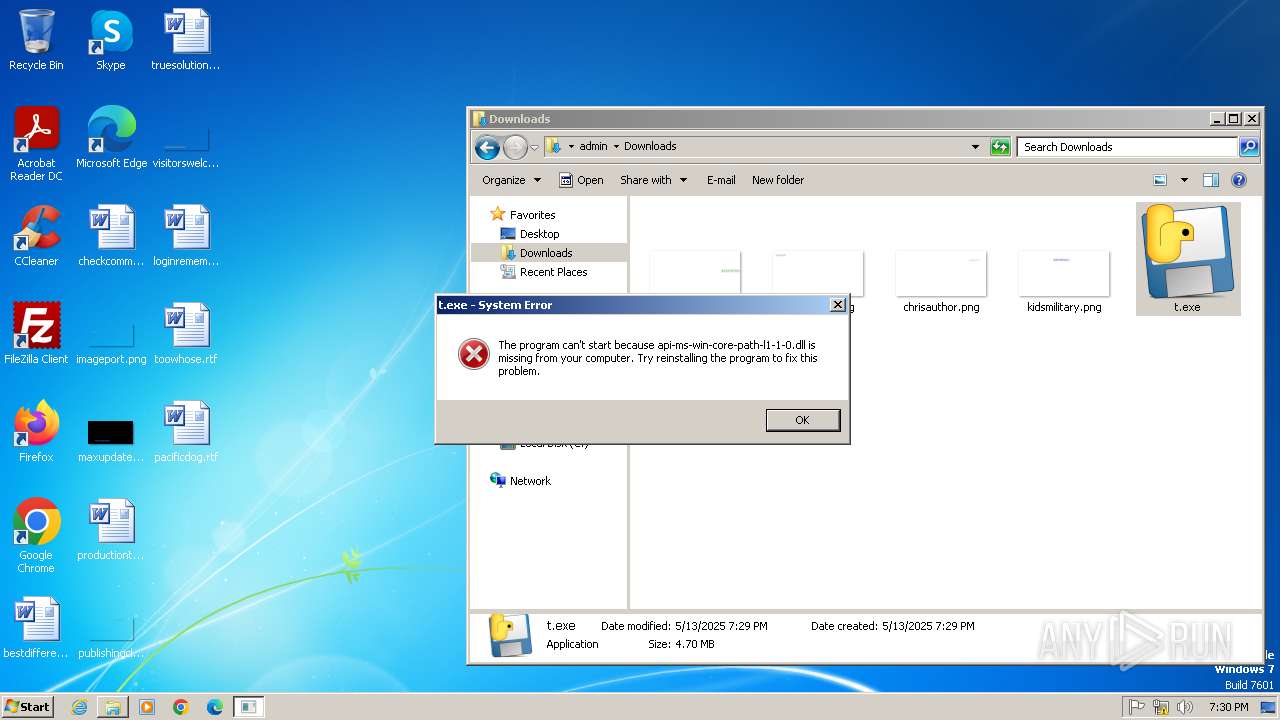
The process drops C-runtime libraries
- t.exe (PID: 1964)
- t.exe (PID: 2960)
- t.exe (PID: 1548)
Loads Python modules
- t.exe (PID: 2236)
- t.exe (PID: 3880)
- t.exe (PID: 704)
Application launched itself
- t.exe (PID: 1964)
- t.exe (PID: 2960)
- t.exe (PID: 1548)
Process drops legitimate windows executable
- t.exe (PID: 1964)
- t.exe (PID: 2960)
- t.exe (PID: 1548)
Executable content was dropped or overwritten
- t.exe (PID: 1964)
- t.exe (PID: 2960)
- t.exe (PID: 1548)
Process drops python dynamic module
- t.exe (PID: 1964)
- t.exe (PID: 2960)
- t.exe (PID: 1548)
There is functionality for taking screenshot (YARA)
- t.exe (PID: 1964)
- t.exe (PID: 2236)
- t.exe (PID: 2960)
INFO
Reads the computer name
- t.exe (PID: 1964)
- t.exe (PID: 2960)
- t.exe (PID: 1548)
Checks supported languages
- t.exe (PID: 1964)
- t.exe (PID: 2236)
- t.exe (PID: 3880)
- t.exe (PID: 1548)
- t.exe (PID: 2960)
- t.exe (PID: 704)
Create files in a temporary directory
- t.exe (PID: 1964)
- t.exe (PID: 2960)
- t.exe (PID: 1548)
The sample compiled with english language support
- t.exe (PID: 1964)
- t.exe (PID: 2960)
- t.exe (PID: 1548)
PyInstaller has been detected (YARA)
- t.exe (PID: 1964)
- t.exe (PID: 2236)
- t.exe (PID: 2960)
Manual execution by a user
- explorer.exe (PID: 2272)
- t.exe (PID: 2960)
- t.exe (PID: 1548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | InstallShield setup (50.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (32.2) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.6) |
| .exe | | | Win32 Executable (generic) (5.2) |
| .exe | | | Generic Win/DOS Executable (2.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:05:13 18:28:07+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.43 |
| CodeSize: | 162816 |
| InitializedDataSize: | 143872 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xcaa0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
44
Monitored processes
7
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 704 | "C:\Users\admin\Downloads\t.exe" | C:\Users\admin\Downloads\t.exe | t.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1548 | "C:\Users\admin\Downloads\t.exe" | C:\Users\admin\Downloads\t.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1964 | "C:\Users\admin\Downloads\t.exe" | C:\Users\admin\Downloads\t.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 2236 | "C:\Users\admin\Downloads\t.exe" | C:\Users\admin\Downloads\t.exe | t.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 4294967295 Modules
| |||||||||||||||
| 2272 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2960 | "C:\Users\admin\Downloads\t.exe" | C:\Users\admin\Downloads\t.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3880 | "C:\Users\admin\Downloads\t.exe" | C:\Users\admin\Downloads\t.exe | t.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
174
Read events
174
Write events
0
Delete events
0
Modification events
Executable files
29
Suspicious files
699
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1964 | t.exe | C:\Users\admin\AppData\Local\Temp\_MEI19642\VCRUNTIME140.dll | executable | |
MD5:1A84957B6E681FCA057160CD04E26B27 | SHA256:9FAEAA45E8CC986AF56F28350B38238B03C01C355E9564B849604B8D690919C5 | |||
| 1964 | t.exe | C:\Users\admin\AppData\Local\Temp\_MEI19642\_compression.pyc | binary | |
MD5:8E3CC75502E54444740C6124977B76C8 | SHA256:52A28668D2EB543DF48A84B70AD0D07D8739D4D63F28287A97C879EB4B1CA989 | |||
| 1964 | t.exe | C:\Users\admin\AppData\Local\Temp\_MEI19642\_collections_abc.pyc | binary | |
MD5:E5B16A015424401D611F329E238E46A3 | SHA256:AA07F621E3ED78D27E2E8A5DAFCC1D099565006D2E9384C4533A66AD76EE0267 | |||
| 1964 | t.exe | C:\Users\admin\AppData\Local\Temp\_MEI19642\_decimal.pyd | executable | |
MD5:327BB8AD9E4E30C079C184B960E747F8 | SHA256:382AD65BE697BCCCE12B0826C2601BA05E45D936651BA834B545B3D7261D2A87 | |||
| 1964 | t.exe | C:\Users\admin\AppData\Local\Temp\_MEI19642\_hashlib.pyd | executable | |
MD5:23DBE8A452F43C2ACDF0B3E218CDBD9A | SHA256:205D849071DC8039755E8E37679B09D736D6F1F65B0367762B1E50BBA5AE7D07 | |||
| 1964 | t.exe | C:\Users\admin\AppData\Local\Temp\_MEI19642\_pydecimal.pyc | binary | |
MD5:D09E723500685D6131DFE5B4F3DAE1A7 | SHA256:A860126C2F5B75274085B867F0939DCC8C46FD4EC44CF0C43EB58E4BDADFD904 | |||
| 1964 | t.exe | C:\Users\admin\AppData\Local\Temp\_MEI19642\_bootlocale.pyc | binary | |
MD5:4C0AAE28945D5B73F49C7CD73F0EC896 | SHA256:3F307C14EA872D737BEA625EDAEE2CA57130557C35D18ACD81CCB1136F78681D | |||
| 1964 | t.exe | C:\Users\admin\AppData\Local\Temp\_MEI19642\_weakrefset.pyc | binary | |
MD5:42CFF130B793C937BFB4D774D20F7A7C | SHA256:ED8F7D7C7C80BCCFF61634E21594F435A0AC5F45DC7D1DFD48F569113DF07698 | |||
| 1964 | t.exe | C:\Users\admin\AppData\Local\Temp\_MEI19642\_lzma.pyd | executable | |
MD5:AD2A12AFC53B1EC6556EFFF903AE4613 | SHA256:10DD3ED8F47D77DA0B6FD9A46165620C0234598BAB16A1ED64752FBE551C5747 | |||
| 1964 | t.exe | C:\Users\admin\AppData\Local\Temp\_MEI19642\_threading_local.pyc | binary | |
MD5:47903BB00628EF40BC1480A627982560 | SHA256:430198EC66FA425ADA612BEA8EC60375F29065675DE35152E647EE677D366A6E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
Threats
Process | Message |
|---|---|
t.exe | [PYI-1964:DEBUG] LOADER: archive file: C:\Users\admin\Downloads\t.exe
|
t.exe | [PYI-1964:DEBUG] LOADER: process level = 0
|
t.exe | [PYI-1964:DEBUG] LOADER: attempting to open archive C:\Users\admin\Downloads\t.exe
|
t.exe | [PYI-1964:DEBUG] LOADER: creating temporary directory (runtime_tmpdir=(null))...
|
t.exe | [PYI-1964:DEBUG] LOADER: executable file: C:\Users\admin\Downloads\t.exe
|
t.exe | [PYI-1964:DEBUG] LOADER: initializing security descriptor from string: D:(A;;FA;;;S-1-5-21-1302019708-1500728564-335382590-1000)
|
t.exe | [PYI-1964:DEBUG] LOADER: argv[0]: C:\Users\admin\Downloads\t.exe
|
t.exe | [PYI-1964:DEBUG] LOADER: trying to load executable-embedded archive...
|
t.exe | [PYI-1964:DEBUG] LOADER: this is parent process of onefile application.
|
t.exe | [PYI-1964:DEBUG] LOADER: attempting to create temporary application directory under C:\Users\admin\AppData\Local\Temp\
|