| File name: | P.exe |
| Full analysis: | https://app.any.run/tasks/d36e9697-60dc-480a-9ba4-c030b56c2c9b |
| Verdict: | Malicious activity |
| Analysis date: | November 09, 2023, 12:08:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 08C87F0CFC72026FF8D62C6DD617C49A |
| SHA1: | 5115074AB8231015519233AE081675CD9B7C8571 |
| SHA256: | 6597C7C5C4F70F7F92163232BCD06894DC6825B3D92172AF02A0353F98486EEC |
| SSDEEP: | 3072:zcYQcwGuA5RmZeDUZe2BWM5MnCO90dRcKKi1wzVPx+WTyZP:jAGUnBdO9ERcTiuDyZP |
MALICIOUS
Actions looks like stealing of personal data
- P.exe (PID: 3404)
- P.exe (PID: 3504)
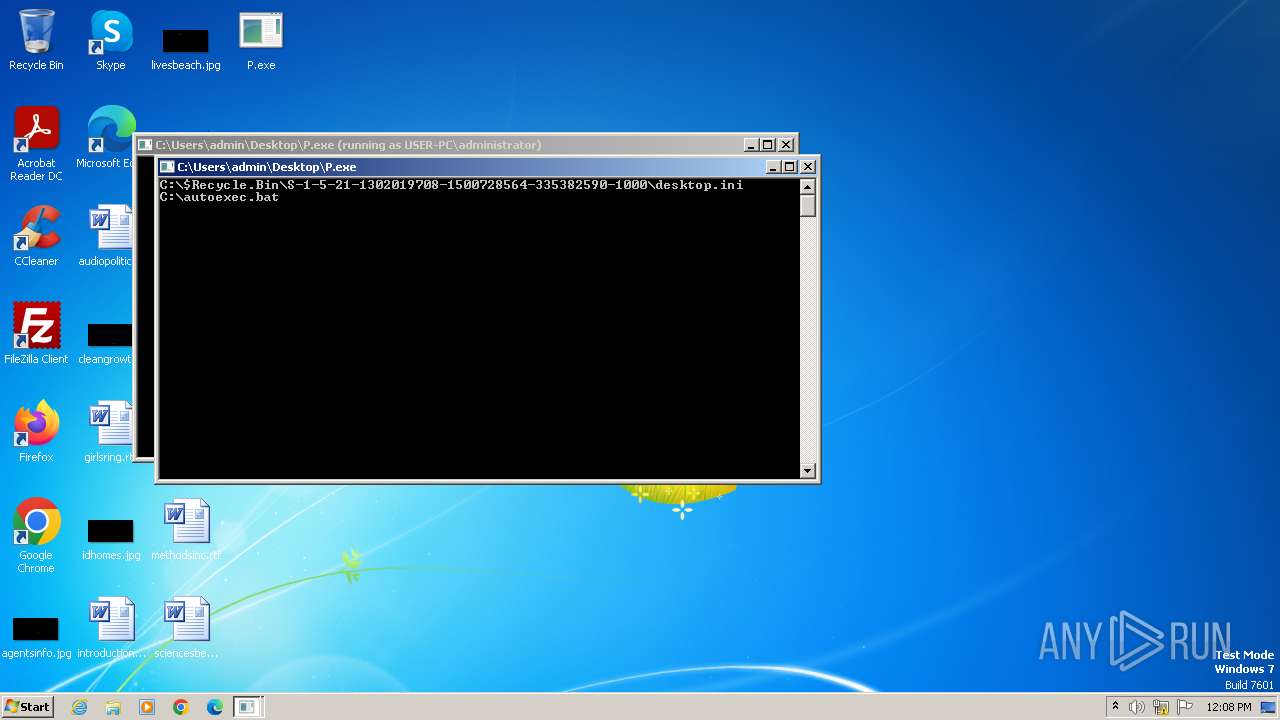
Drops the executable file immediately after the start
- P.exe (PID: 3404)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- P.exe (PID: 3404)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3876)
- P.exe (PID: 3404)
Checks supported languages
- P.exe (PID: 3404)
- P.exe (PID: 3504)
- wmpnscfg.exe (PID: 3876)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3876)
Reads the computer name
- wmpnscfg.exe (PID: 3876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:11:09 13:08:08+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 48640 |
| InitializedDataSize: | 13086208 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x494d |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
Total processes
42
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3404 | "C:\Users\admin\Desktop\P.exe" | C:\Users\admin\Desktop\P.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3460 | "C:\Windows\System32\runas.exe" /user:administrator C:\Users\admin\Desktop\P.exe | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3504 | C:\Users\admin\Desktop\P.exe | C:\Users\admin\Desktop\P.exe | runas.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Exit code: 3221225786 Modules
| |||||||||||||||
| 3876 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
52
Read events
49
Write events
0
Delete events
3
Modification events
| (PID) Process: | (3876) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{F8413BEE-5986-4D02-8464-3F165808C92E}\{45BFB7A9-7D09-4EF4-BF26-4408977D921B} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3876) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{F8413BEE-5986-4D02-8464-3F165808C92E} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3876) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{F41DF772-75C5-4392-AB61-9667513AB578} |
| Operation: | delete key | Name: | (default) |
Value: | |||
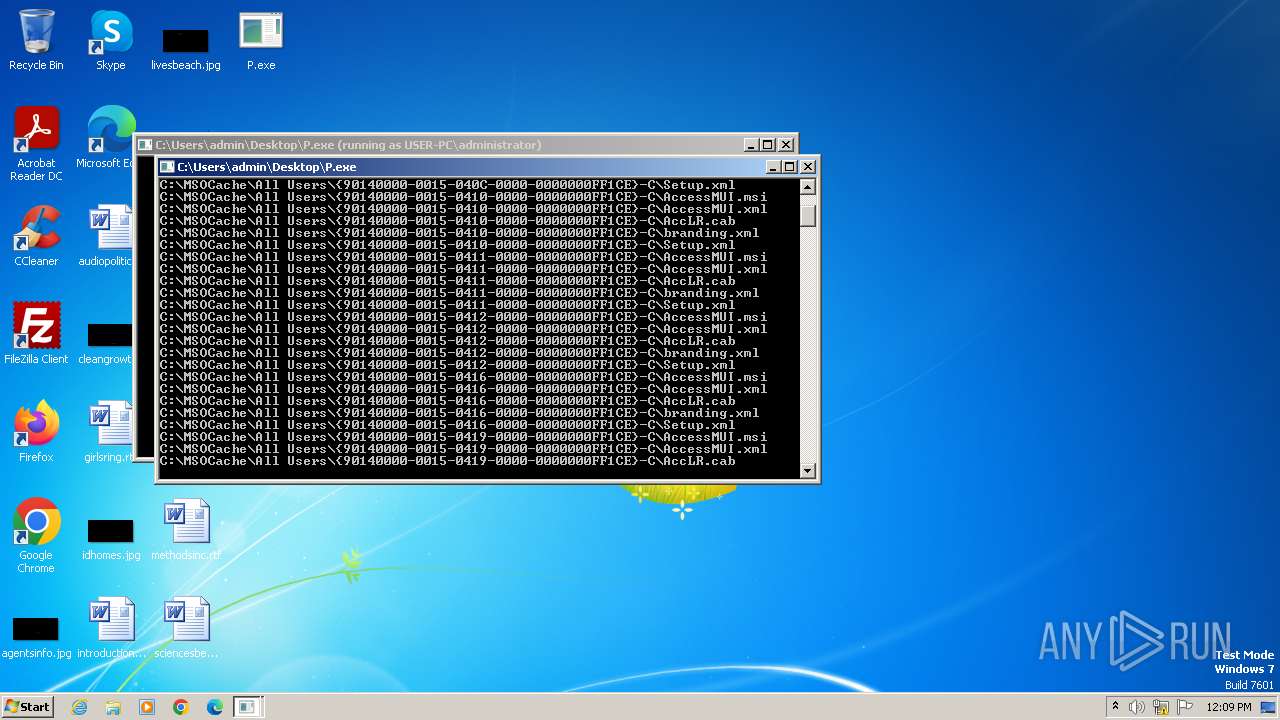
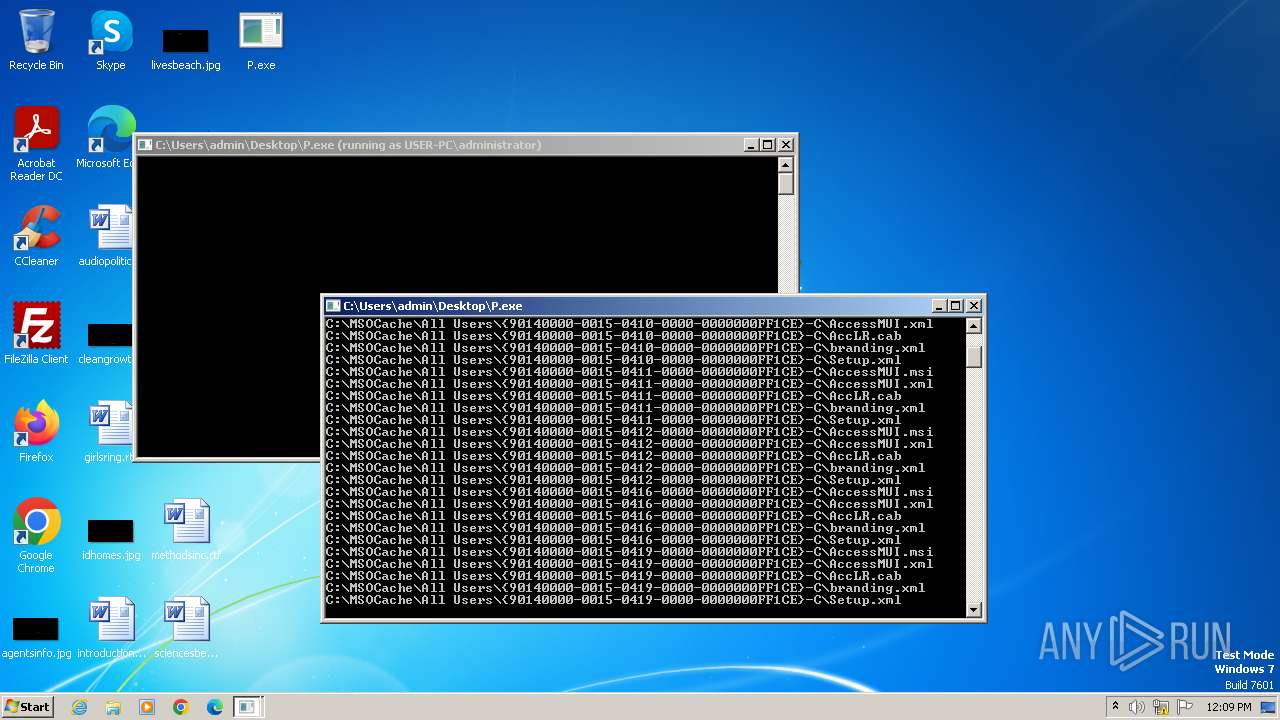
Executable files
1
Suspicious files
671
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
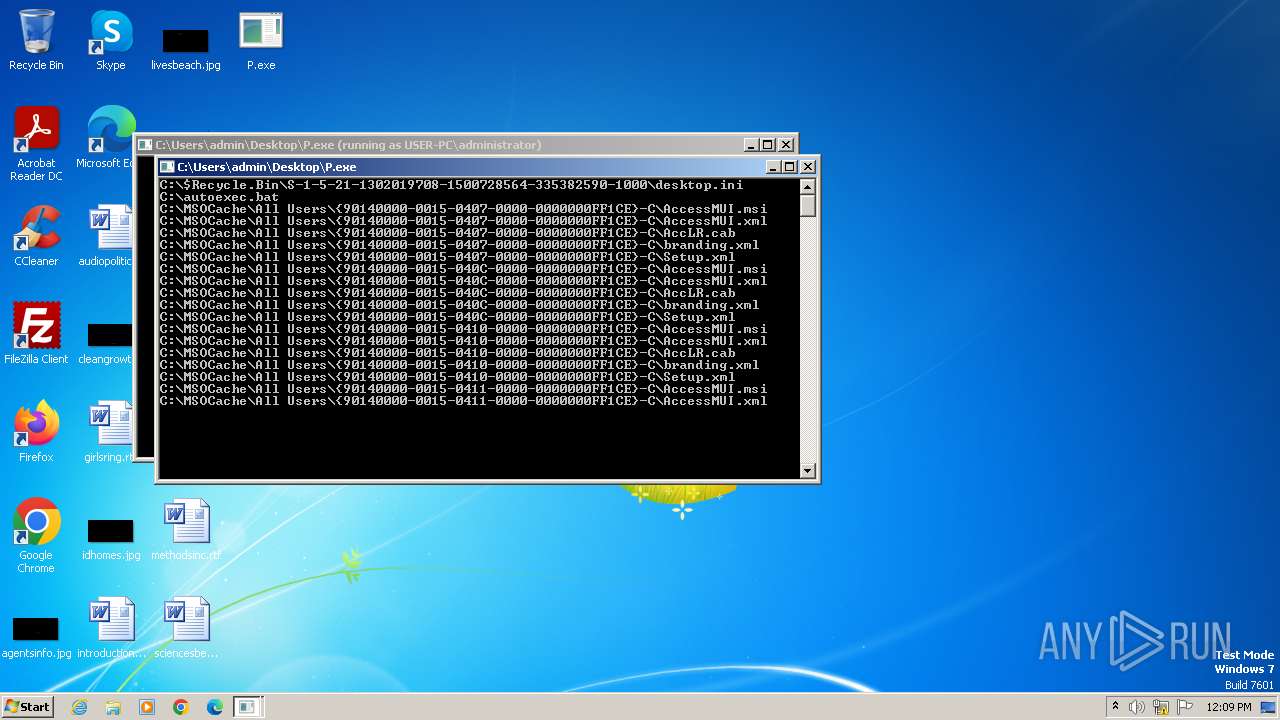
| 3404 | P.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccLR.cab | — | |
MD5:— | SHA256:— | |||
| 3404 | P.exe | C:\MSOCache\All Users\{90140000-0015-040C-0000-0000000FF1CE}-C\AccLR.cab | — | |
MD5:— | SHA256:— | |||
| 3404 | P.exe | C:\MSOCache\All Users\{90140000-0015-0410-0000-0000000FF1CE}-C\AccLR.cab | — | |
MD5:— | SHA256:— | |||
| 3404 | P.exe | C:\MSOCache\All Users\{90140000-0015-040C-0000-0000000FF1CE}-C\Setup.xml | binary | |
MD5:86E3F6E08874E420E99A80D45CDE4DEE | SHA256:076966860A886AC02C0DE8E2961B453B7E33C7FBCCC8ADC85E4EBF21013512C9 | |||
| 3404 | P.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\AccessMUI.msi | binary | |
MD5:3F7DFA5A3DBF298D64189742C0DE2005 | SHA256:0AA0EF785536E56C28AE83F20714B007EC5AB56BD0673FF6BF401B1448BF6CB8 | |||
| 3404 | P.exe | C:\MSOCache\All Users\{90140000-0015-0411-0000-0000000FF1CE}-C\AccLR.cab | — | |
MD5:— | SHA256:— | |||
| 3404 | P.exe | C:\MSOCache\All Users\{90140000-0015-0410-0000-0000000FF1CE}-C\AccessMUI.xml | binary | |
MD5:833061B1CE092555B0C55386C7393311 | SHA256:16F1C4C927D24DE5BC4EF722378F8A41BEB2B72FAB4FE0306E2101F4411ACE71 | |||
| 3404 | P.exe | C:\$Recycle.Bin\S-1-5-21-1302019708-1500728564-335382590-1000\desktop.ini | binary | |
MD5:27D5C97A51173DB6257D6BFA4008676A | SHA256:CFA331AEDC7F0734E29E6EA5A4042B7D015E81AC04F62702B86943EE5F964F66 | |||
| 3404 | P.exe | C:\MSOCache\All Users\{90140000-0015-040C-0000-0000000FF1CE}-C\AccessMUI.msi | binary | |
MD5:669E869F1B41A738757DDB43C577A1A6 | SHA256:0D3CD083A6588F9694BA6FCFB6E67E7CAE89BB6E818846F2E2AACE38B100340B | |||
| 3404 | P.exe | C:\MSOCache\All Users\{90140000-0015-0407-0000-0000000FF1CE}-C\Setup.xml | binary | |
MD5:E378639639898683AC41139375D964E0 | SHA256:2E834F92D5C9B2CDE6C180AB708A2FEB67A23957A7051F5536D46BC1BFB31E7F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |