| File name: | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin |
| Full analysis: | https://app.any.run/tasks/3be58764-a582-42f1-bffa-ac6379128de8 |
| Verdict: | Malicious activity |
| Analysis date: | May 28, 2025, 20:43:25 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 10 sections |
| MD5: | 3B60028D0E729E5354EAC2AB03750920 |
| SHA1: | D3245C14F51D2259A35E0BA57B30AD336305800D |
| SHA256: | 659283AEDC8E66FD3ECF7C6C7185260895B87BB309819E15BFA4B9AC71F274A3 |
| SSDEEP: | 786432:Xw2NMCTMF9PuO629q4aHtCncb4Vmz0YEfuZ5:nNM35uO6gq4aNCncb4sYfuZ5 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe (PID: 4812)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe (PID: 1708)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3756)
Reads security settings of Internet Explorer
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3884)
Reads the Internet Settings
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3884)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3756)
Reads the Windows owner or organization settings
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3756)
Process drops legitimate windows executable
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3756)
The process drops C-runtime libraries
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3756)
Reads settings of System Certificates
- YouTubeToMP3.exe (PID: 3348)
Detected use of alternative data streams (AltDS)
- YouTubeToMP3.exe (PID: 3348)
There is functionality for taking screenshot (YARA)
- YouTubeToMP3.exe (PID: 3348)
Found regular expressions for crypto-addresses (YARA)
- YouTubeToMP3.exe (PID: 3348)
INFO
Checks supported languages
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe (PID: 4812)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3884)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe (PID: 1708)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3756)
- YouTubeToMP3.exe (PID: 3348)
- ffmpeg.exe (PID: 4012)
- QtWebEngineProcess.exe (PID: 804)
Reads the computer name
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3884)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3756)
- YouTubeToMP3.exe (PID: 3348)
- QtWebEngineProcess.exe (PID: 804)
Create files in a temporary directory
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe (PID: 4812)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe (PID: 1708)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3756)
- YouTubeToMP3.exe (PID: 3348)
Creates files in the program directory
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3756)
The sample compiled with english language support
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3756)
Detects InnoSetup installer (YARA)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe (PID: 4812)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3884)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe (PID: 1708)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3756)
Compiled with Borland Delphi (YARA)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3884)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe (PID: 1708)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3756)
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe (PID: 4812)
Creates a software uninstall entry
- 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp (PID: 3756)
Creates files or folders in the user directory
- YouTubeToMP3.exe (PID: 3348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
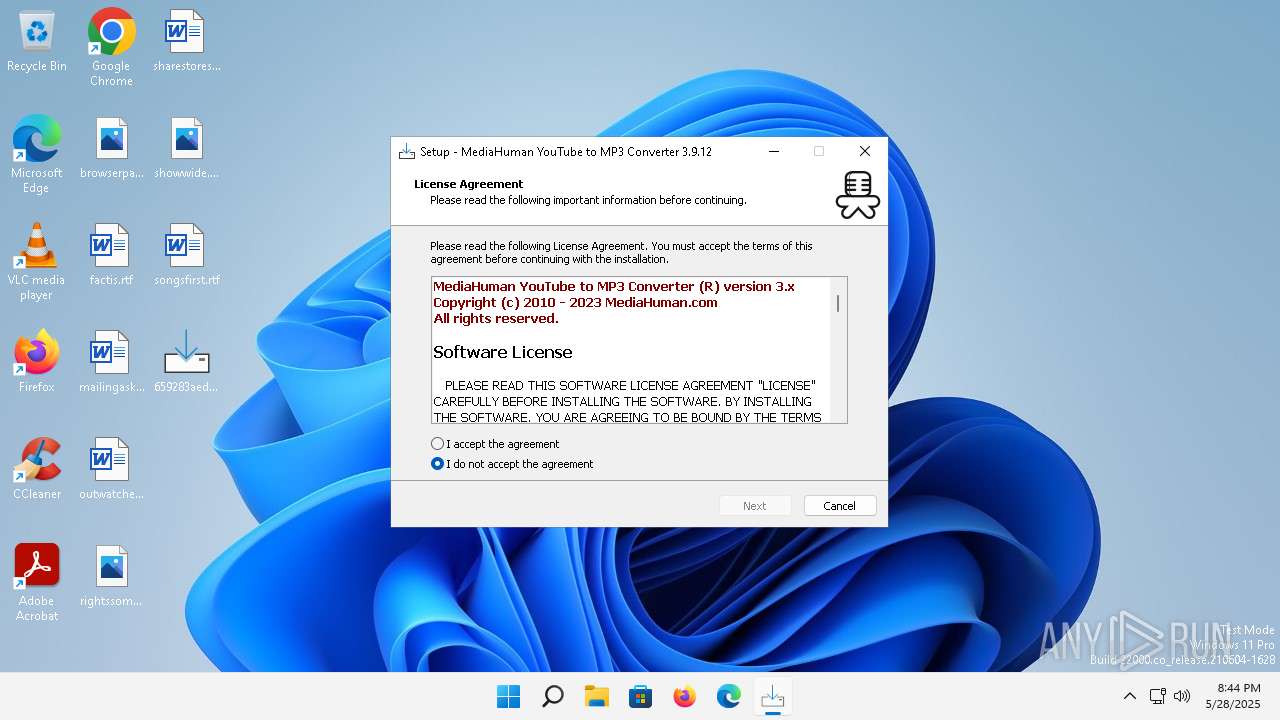
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | MediaHuman |
| FileDescription: | MediaHuman YouTube to MP3 Converter Setup |
| FileVersion: | |
| LegalCopyright: | Copyright © 2010-2025 MediaHuman, Inc. |
| OriginalFileName: | |
| ProductName: | MediaHuman YouTube to MP3 Converter |
| ProductVersion: | 3.9.12 |
Total processes
112
Monitored processes
8
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 804 | "C:\Program Files\MediaHuman\YouTube to MP3 Converter\QtWebEngineProcess.exe" --type=renderer --disable-speech-api --enable-threaded-compositing --enable-features=AllowContentInitiatedDataUrlNavigations,NetworkServiceInProcess,TracingServiceInProcess --disable-features=BackgroundFetch,ConsolidatedMovementXY,DnsOverHttpsUpgrade,InstalledApp,MojoVideoCapture,PictureInPicture,SmsReceiver,UseSkiaRenderer,WebPayments,WebUSB --disable-gpu-compositing --lang=en --webengine-schemes=qrc:sLV --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=2 --mojo-platform-channel-handle=3248 /prefetch:1 | C:\Program Files\MediaHuman\YouTube to MP3 Converter\QtWebEngineProcess.exe | — | YouTubeToMP3.exe | |||||||||||
User: admin Company: The Qt Company Ltd. Integrity Level: LOW Description: C++ Application Development Framework Version: 5.15.18.0 Modules
| |||||||||||||||
| 1708 | "C:\Users\admin\Desktop\659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe" /SPAWNWND=$401FA /NOTIFYWND=$40222 | C:\Users\admin\Desktop\659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | ||||||||||||
User: admin Company: MediaHuman Integrity Level: HIGH Description: MediaHuman YouTube to MP3 Converter Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 3348 | "C:\Program Files\MediaHuman\YouTube to MP3 Converter\YouTubeToMp3.exe" | C:\Program Files\MediaHuman\YouTube to MP3 Converter\YouTubeToMP3.exe | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | ||||||||||||
User: admin Integrity Level: MEDIUM Version: 3.9.12.0 Modules
| |||||||||||||||
| 3756 | "C:\Users\admin\AppData\Local\Temp\is-N8471.tmp\659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp" /SL5="$70040,79684101,832512,C:\Users\admin\Desktop\659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe" /SPAWNWND=$401FA /NOTIFYWND=$40222 | C:\Users\admin\AppData\Local\Temp\is-N8471.tmp\659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe | ||||||||||||
User: admin Company: MediaHuman Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3884 | "C:\Users\admin\AppData\Local\Temp\is-2H7H6.tmp\659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp" /SL5="$40222,79684101,832512,C:\Users\admin\Desktop\659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe" | C:\Users\admin\AppData\Local\Temp\is-2H7H6.tmp\659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | — | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe | |||||||||||
User: admin Company: MediaHuman Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 4012 | "C:\Program Files\MediaHuman\YouTube to MP3 Converter\ffmpeg\ffmpeg" -codecs | C:\Program Files\MediaHuman\YouTube to MP3 Converter\ffmpeg\ffmpeg.exe | — | YouTubeToMP3.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4812 | "C:\Users\admin\Desktop\659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe" | C:\Users\admin\Desktop\659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe | explorer.exe | ||||||||||||
User: admin Company: MediaHuman Integrity Level: MEDIUM Description: MediaHuman YouTube to MP3 Converter Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 4924 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ffmpeg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 720
Read events
3 661
Write events
53
Delete events
6
Modification events
| (PID) Process: | (3756) 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: AC0E0000A113B24111D0DB01 | |||
| (PID) Process: | (3756) 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 6DA6CE031960EC6767D8260AF51D38B89914E7398367286984F329B0C6DA8DD9 | |||
| (PID) Process: | (3756) 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3756) 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | Key: | HKEY_CURRENT_USER\Software\MediaHuman\OrganizationDefaults |
| Operation: | write | Name: | id |
Value: edbcab3a-3e73-437b-774c-4d652dd8e730 | |||
| (PID) Process: | (3756) 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\MediaHuman\YouTube to MP3 Converter\api-ms-win-core-file-l1-2-0.dll | |||
| (PID) Process: | (3756) 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 3DB407975408B23F7ED34BBFDF4676A435299639C3C3C07309F959C339591C40 | |||
| (PID) Process: | (3756) 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\yt2mp3 |
| Operation: | write | Name: | URL Protocol |
Value: | |||
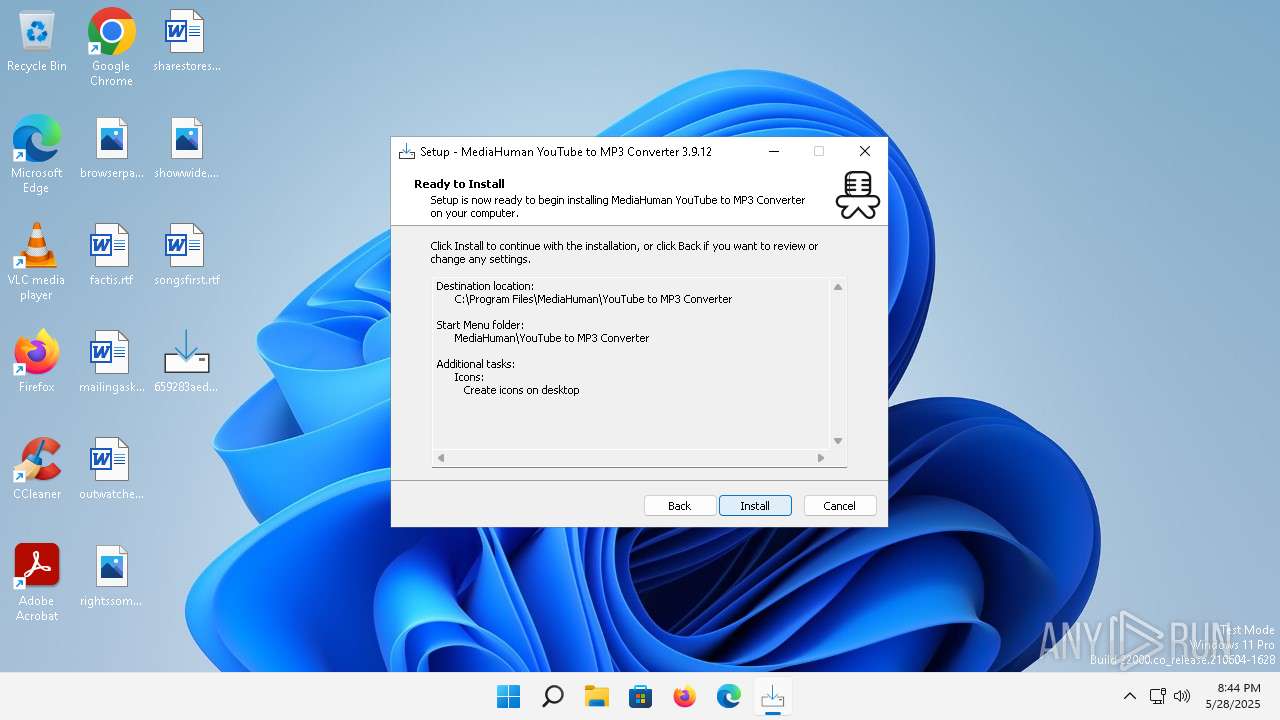
| (PID) Process: | (3756) 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\MediaHuman YouTube to MP3 Converter_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.2 | |||
| (PID) Process: | (3756) 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\MediaHuman YouTube to MP3 Converter_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
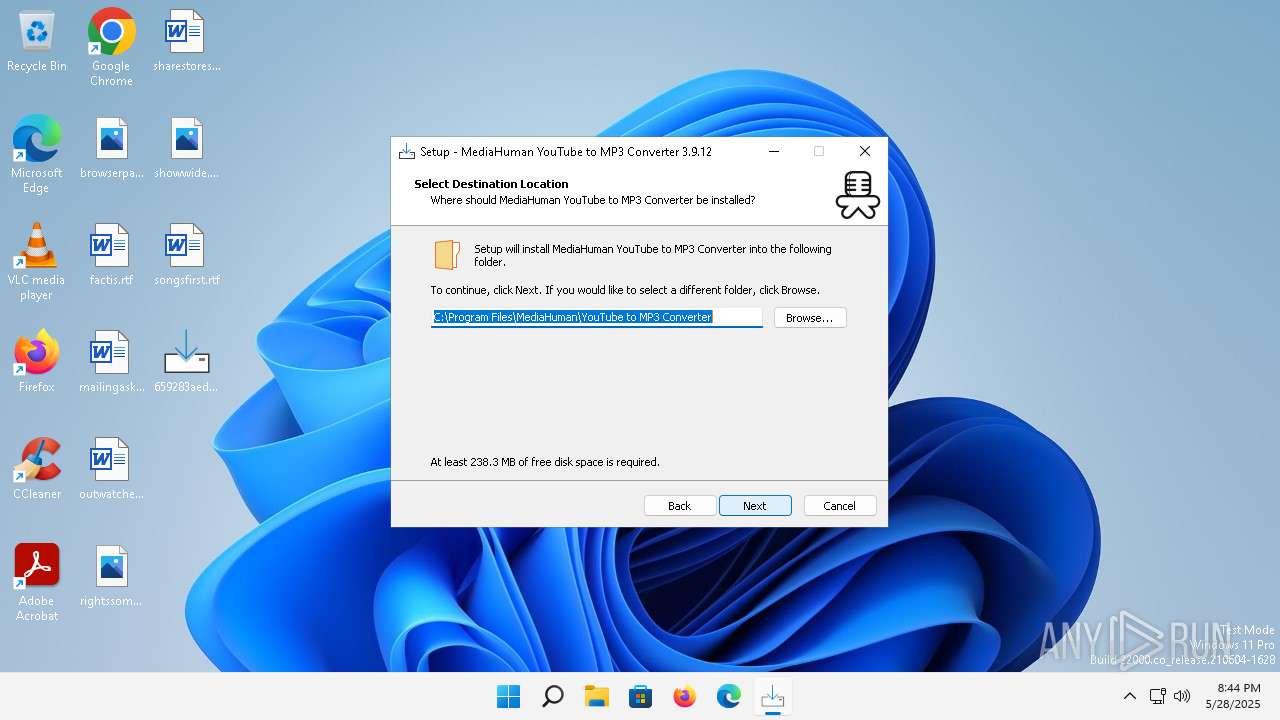
Value: C:\Program Files\MediaHuman\YouTube to MP3 Converter | |||
| (PID) Process: | (3756) 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\MediaHuman YouTube to MP3 Converter_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\MediaHuman\YouTube to MP3 Converter\ | |||
Executable files
211
Suspicious files
418
Text files
460
Unknown types
168
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1708 | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe | C:\Users\admin\AppData\Local\Temp\is-N8471.tmp\659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | executable | |
MD5:406B580CEEEB6E8C534DFC99C2D479DC | SHA256:9AF5466440C048A1B95C33EBEE77FCECD5FBB4206E0D3AA4C869F62DE08566B6 | |||
| 3756 | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | C:\Users\admin\AppData\Local\Temp\is-IPRP6.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 3756 | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | C:\Program Files\MediaHuman\YouTube to MP3 Converter\is-PFNHS.tmp | executable | |
MD5:406B580CEEEB6E8C534DFC99C2D479DC | SHA256:9AF5466440C048A1B95C33EBEE77FCECD5FBB4206E0D3AA4C869F62DE08566B6 | |||
| 3756 | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | C:\Program Files\MediaHuman\YouTube to MP3 Converter\is-NQHTK.tmp | executable | |
MD5:6A55A7E284B51B086B63CC6F2061CE8B | SHA256:D9973270A952B4CE615104520051E847B26E4B1CC330A5A95BA1AE128F0DFDEB | |||
| 4812 | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.exe | C:\Users\admin\AppData\Local\Temp\is-2H7H6.tmp\659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | executable | |
MD5:406B580CEEEB6E8C534DFC99C2D479DC | SHA256:9AF5466440C048A1B95C33EBEE77FCECD5FBB4206E0D3AA4C869F62DE08566B6 | |||
| 3756 | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | C:\Program Files\MediaHuman\YouTube to MP3 Converter\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:6A55A7E284B51B086B63CC6F2061CE8B | SHA256:D9973270A952B4CE615104520051E847B26E4B1CC330A5A95BA1AE128F0DFDEB | |||
| 3756 | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | C:\Program Files\MediaHuman\YouTube to MP3 Converter\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:6E38A6BED88E1C27155E4DC428188EF0 | SHA256:144D3A28E43E47FC1CCE956255CC80467D4A6FBBB8F612EC6D85F62DE030A924 | |||
| 3756 | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | C:\Program Files\MediaHuman\YouTube to MP3 Converter\is-RJDJE.tmp | executable | |
MD5:2AC1289E4DBAB076B332869BEF26D3CE | SHA256:6475F20F46814D28845C2FA73E9C283A8504483FA16D911325588C778CF76C26 | |||
| 3756 | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | C:\Program Files\MediaHuman\YouTube to MP3 Converter\api-ms-win-core-processthreads-l1-1-1.dll | executable | |
MD5:1AF2A91DC0A4E48BAB0CA123073ADF30 | SHA256:AE574C9B8A2467C3EE0AC3E862255E93A02627BCE146AD7B720B99905DC224FC | |||
| 3756 | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | C:\Program Files\MediaHuman\YouTube to MP3 Converter\unins000.exe | executable | |
MD5:406B580CEEEB6E8C534DFC99C2D479DC | SHA256:9AF5466440C048A1B95C33EBEE77FCECD5FBB4206E0D3AA4C869F62DE08566B6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
38
DNS requests
15
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1352 | svchost.exe | GET | 200 | 184.25.50.104:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
2564 | smartscreen.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a82c960e8cbf4904 | unknown | — | — | whitelisted |
3640 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2564 | smartscreen.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?08d15ef3f08c448e | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a15406f647700ee0 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?9a78fd978e6e7371 | unknown | — | — | whitelisted |
2988 | OfficeClickToRun.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
3756 | 659283aedc8e66fd3ecf7c6c7185260895b87bb309819e15bfa4b9ac71f274a3.bin.tmp | POST | 200 | 142.250.185.142:80 | http://www.google-analytics.com/collect | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?2efe063e74f19306 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 184.25.50.48:80 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2564 | smartscreen.exe | 4.231.66.184:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1352 | svchost.exe | 184.25.50.104:80 | — | Akamai International B.V. | DE | unknown |
2564 | smartscreen.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
2564 | smartscreen.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4976 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4956 | svchost.exe | 184.29.199.32:443 | fs.microsoft.com | AKAMAI-AS | NL | whitelisted |
3640 | svchost.exe | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
www.youtube.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1352 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |