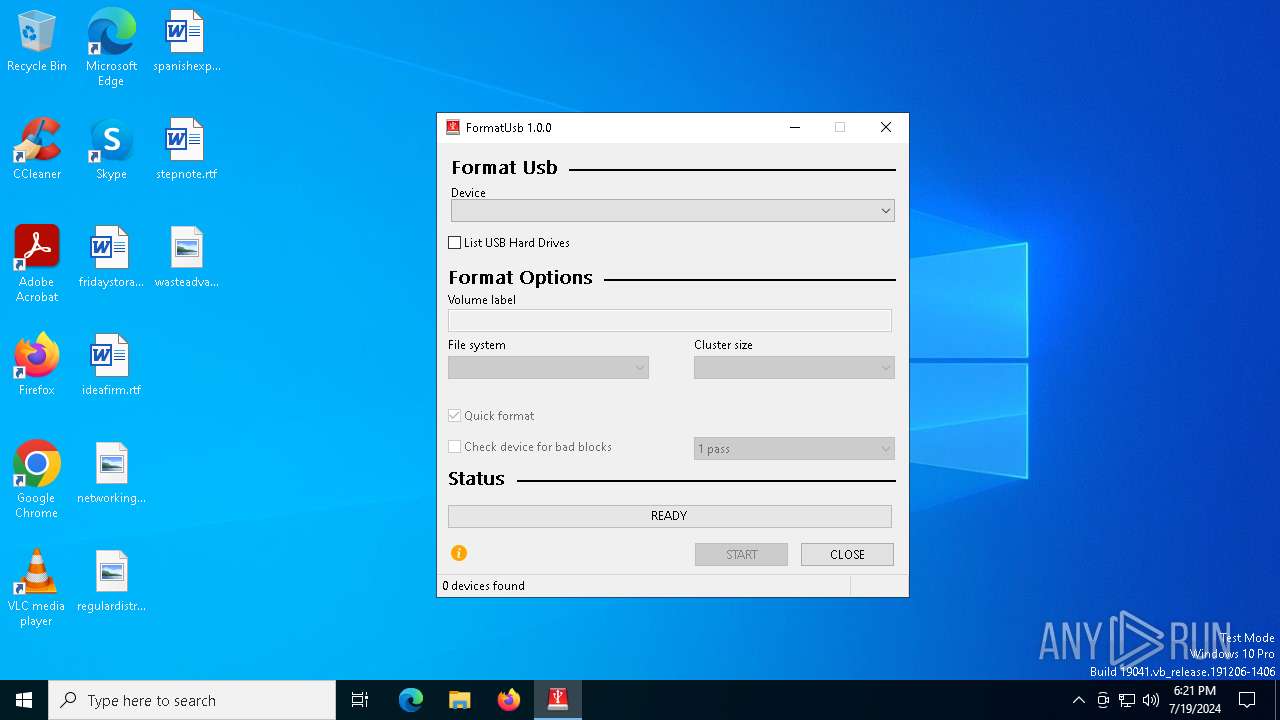
| File name: | formatusb_x64.exe |
| Full analysis: | https://app.any.run/tasks/a07b533c-e463-4887-a34e-5d7bff1ec9b2 |
| Verdict: | Malicious activity |
| Analysis date: | July 19, 2024, 18:21:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | B5A209CDADB41D7959F1FD013F89E4E4 |
| SHA1: | C32CA647A880A65C3164B81BD6A2F906992FA468 |
| SHA256: | 658CB937213BF2F2FA397CBDAD1540B1C45EC8720BD5CD336BF441CFD3390841 |
| SSDEEP: | 49152:PlpbZHFj4Db7Nw3+K7Xha2S304SB8LcsPSdAXHohhhhhhhhhhhhhhhhhhhhhhhhg:Pl7HFjQNwuQXhTSN4rdACYGvEz9aTnYc |
MALICIOUS
Drops the executable file immediately after the start
- formatusb_x64.exe (PID: 2768)
Changes the Windows auto-update feature
- formatusb_x64.exe (PID: 2768)
SUSPICIOUS
No suspicious indicators.INFO
Reads the computer name
- formatusb_x64.exe (PID: 2768)
Process checks whether UAC notifications are on
- formatusb_x64.exe (PID: 2768)
Checks supported languages
- formatusb_x64.exe (PID: 2768)
Create files in a temporary directory
- formatusb_x64.exe (PID: 2768)
UPX packer has been detected
- formatusb_x64.exe (PID: 2768)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 1999:07:06 02:48:42+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.28 |
| CodeSize: | 737280 |
| InitializedDataSize: | 1432576 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x87e18 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | https://formatusb.com |
| CompanyName: | FormatUsb |
| FileDescription: | FormatUsb |
| FileVersion: | 1 |
| InternalName: | FormatUsb |
| LegalCopyright: | © 2021 FormatUsb (GPL v3) |
| LegalTrademarks: | https://www.gnu.org/licenses/gpl-3.0.html |
| OriginalFileName: | formatusb.exe |
| ProductName: | FormatUsb |
| ProductVersion: | 1 |
Total processes
145
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1668 | "C:\Users\admin\AppData\Local\Temp\formatusb_x64.exe" | C:\Users\admin\AppData\Local\Temp\formatusb_x64.exe | — | explorer.exe | |||||||||||
User: admin Company: FormatUsb Integrity Level: MEDIUM Description: FormatUsb Exit code: 3221226540 Version: 1.0 Modules
| |||||||||||||||
| 2768 | "C:\Users\admin\AppData\Local\Temp\formatusb_x64.exe" | C:\Users\admin\AppData\Local\Temp\formatusb_x64.exe | explorer.exe | ||||||||||||
User: admin Company: FormatUsb Integrity Level: HIGH Description: FormatUsb Version: 1.0 Modules
| |||||||||||||||
| 7816 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
445
Read events
384
Write events
29
Delete events
32
Modification events
| (PID) Process: | (2768) formatusb_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{C72E11D7-F512-439F-9F7D-2AA89CC80A9B}Machine\Software\Policies\Microsoft\AppHVSI |
| Operation: | write | Name: | AllowAppHVSI_ProviderSet |
Value: 0 | |||
| (PID) Process: | (2768) formatusb_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{C72E11D7-F512-439F-9F7D-2AA89CC80A9B}Machine\Software\Policies\Microsoft\EdgeUpdate |
| Operation: | write | Name: | UpdateDefault |
Value: 0 | |||
| (PID) Process: | (2768) formatusb_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{C72E11D7-F512-439F-9F7D-2AA89CC80A9B}Machine\Software\Policies\Microsoft\Windows\Network Connections |
| Operation: | write | Name: | NC_DoNotShowLocalOnlyIcon |
Value: 1 | |||
| (PID) Process: | (2768) formatusb_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{C72E11D7-F512-439F-9F7D-2AA89CC80A9B}Machine\Software\Policies\Microsoft\Windows\Windows Feeds |
| Operation: | write | Name: | EnableFeeds |
Value: 0 | |||
| (PID) Process: | (2768) formatusb_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{C72E11D7-F512-439F-9F7D-2AA89CC80A9B}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | WUServer |
Value: http://neverupdatewindows10.com | |||
| (PID) Process: | (2768) formatusb_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{C72E11D7-F512-439F-9F7D-2AA89CC80A9B}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | WUStatusServer |
Value: http://neverupdatewindows10.com | |||
| (PID) Process: | (2768) formatusb_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{C72E11D7-F512-439F-9F7D-2AA89CC80A9B}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | UpdateServiceUrlAlternate |
Value: http://neverupdatewindows10.com | |||
| (PID) Process: | (2768) formatusb_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{C72E11D7-F512-439F-9F7D-2AA89CC80A9B}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate |
| Operation: | write | Name: | **del.FillEmptyContentUrls |
Value: | |||
| (PID) Process: | (2768) formatusb_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{C72E11D7-F512-439F-9F7D-2AA89CC80A9B}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate\AU |
| Operation: | write | Name: | UseWUServer |
Value: 1 | |||
| (PID) Process: | (2768) formatusb_x64.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy Objects\{C72E11D7-F512-439F-9F7D-2AA89CC80A9B}Machine\Software\Policies\Microsoft\Windows\WindowsUpdate\AU |
| Operation: | write | Name: | NoAutoUpdate |
Value: 0 | |||
Executable files
0
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2768 | formatusb_x64.exe | C:\WINDOWS\System32\GroupPolicy\gpt.ini | text | |
MD5:3D89F23265C9E30A0CF055C3EB4D637C | SHA256:806582F6221C79BD4C7EACDC4B63E937CE247EEE2BA159F55C545CDFB2B1C25B | |||
| 2768 | formatusb_x64.exe | C:\WINDOWS\System32\GroupPolicy\Machine\Registry.pol | binary | |
MD5:0C014C71A70DC7758BFDC822E974F1F3 | SHA256:8EBD915268E16B55A3ABDE6F612363576FAB5DF656F955D672CCE8889C5FF9CA | |||
| 2768 | formatusb_x64.exe | C:\Users\admin\AppData\Local\Temp\For9019.tmp | text | |
MD5:58E668ADA4EBA9648E3797FB9D39B51F | SHA256:E65999EC992DE64010B663EB1EDB2DD231F1141800D60AB3E7C581A8A9F9A229 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
33
DNS requests
14
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5620 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4716 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7856 | svchost.exe | 4.209.32.67:443 | licensing.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2168 | svchost.exe | 224.0.0.251:5353 | — | — | — | unknown |
2168 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2760 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4716 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
licensing.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |