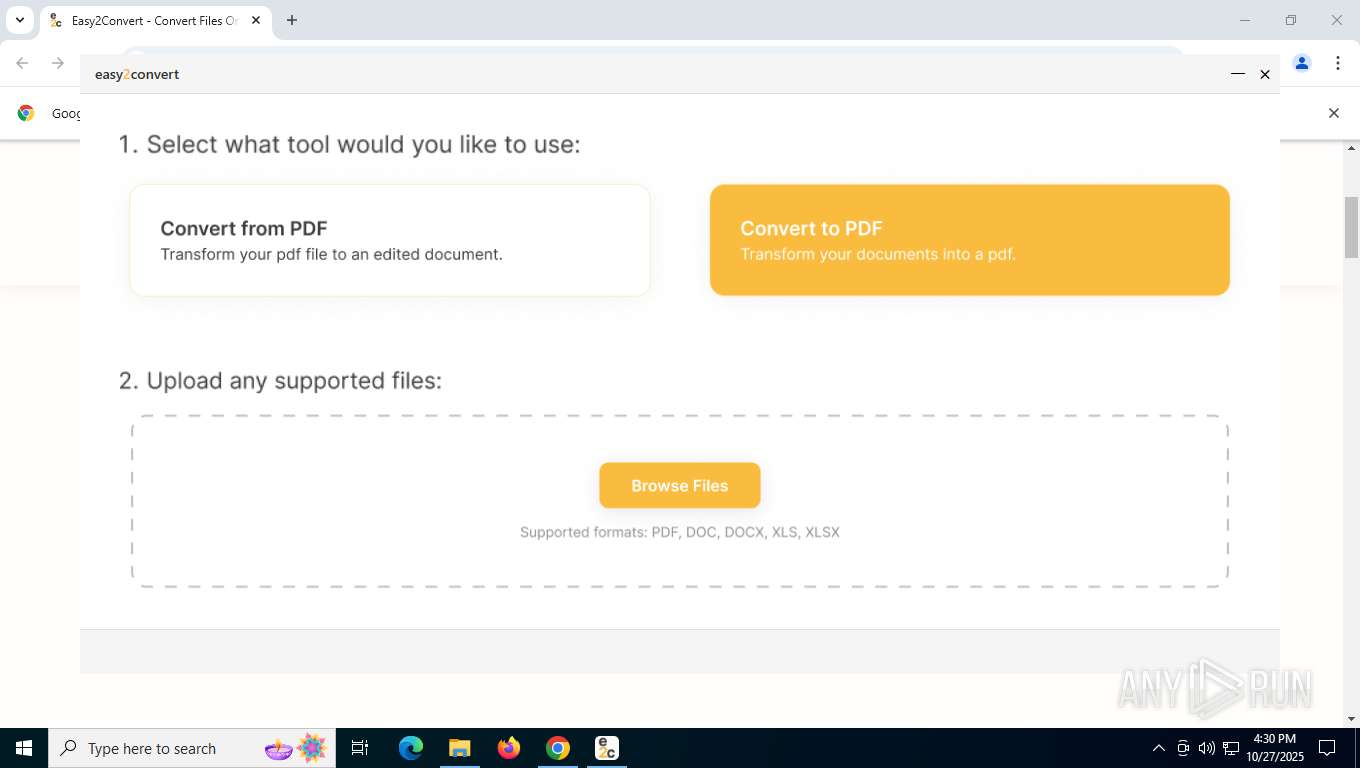
| URL: | ez2convertapp.com |
| Full analysis: | https://app.any.run/tasks/d5f2ad1a-b2cd-45b8-ba6a-7e003c7d61f0 |
| Verdict: | Malicious activity |
| Analysis date: | October 27, 2025, 16:29:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MD5: | 7B54EAC8EA85BB648437B153D189DE2D |
| SHA1: | 65BEBF735DE5675DA8F456262313B49F2433EBC1 |
| SHA256: | 658AA0A910EF98CAB7B2C96711598100D8BBDB5A5F95B9B54460FEDB6F02ED9D |
| SSDEEP: | 3:6Nn6KI:6t6KI |
MALICIOUS
No malicious indicators.SUSPICIOUS
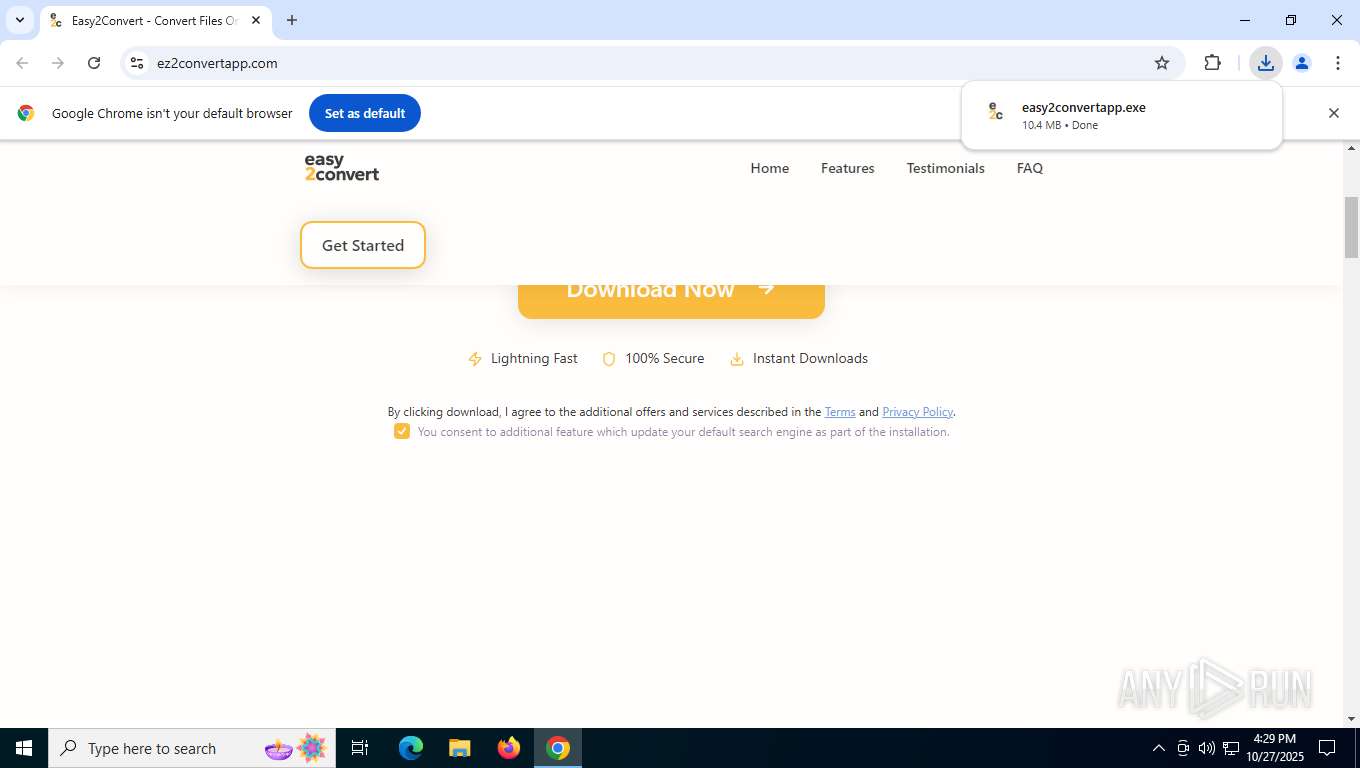
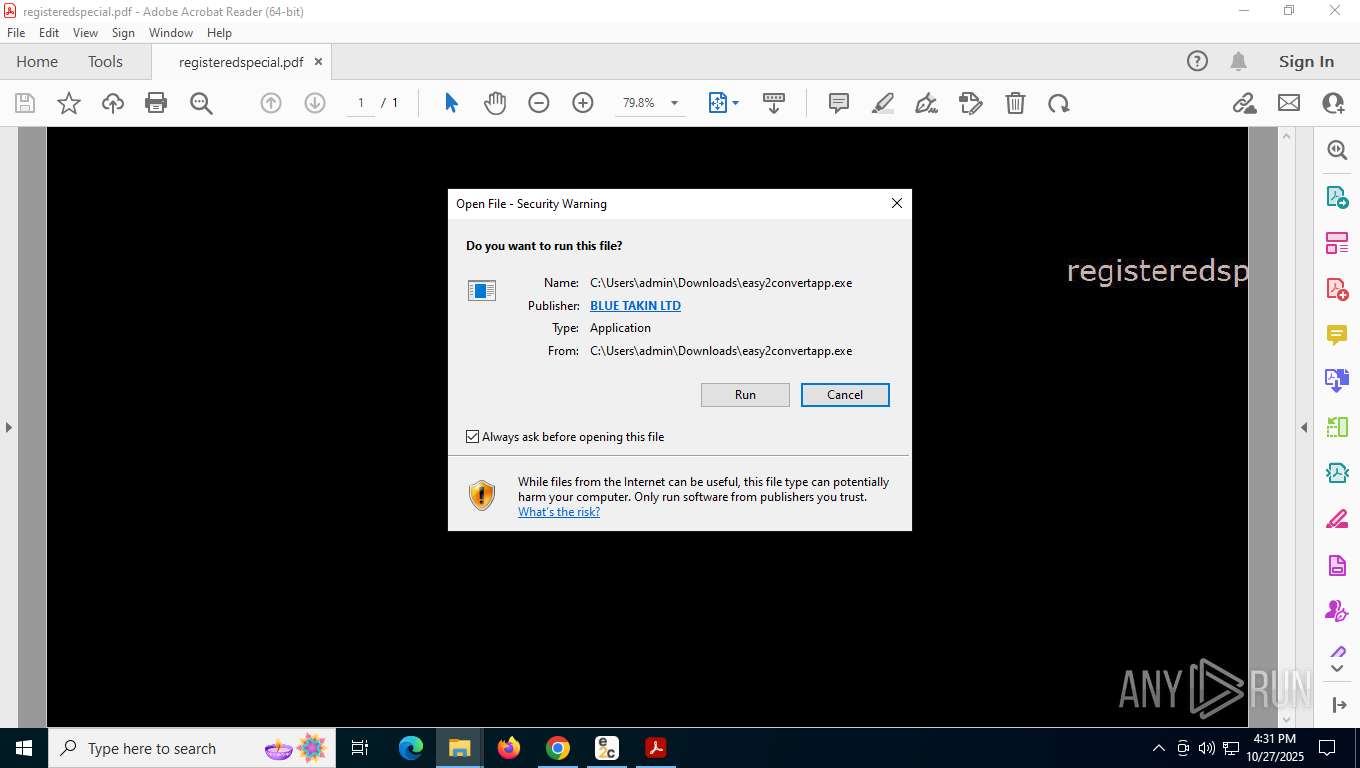
Process drops legitimate windows executable
- easy2convertapp.exe (PID: 2492)
Executable content was dropped or overwritten
- easy2convertapp.exe (PID: 2492)
Reads security settings of Internet Explorer
- Easy2Convert.exe (PID: 6376)
- Easy2Convert.exe (PID: 7408)
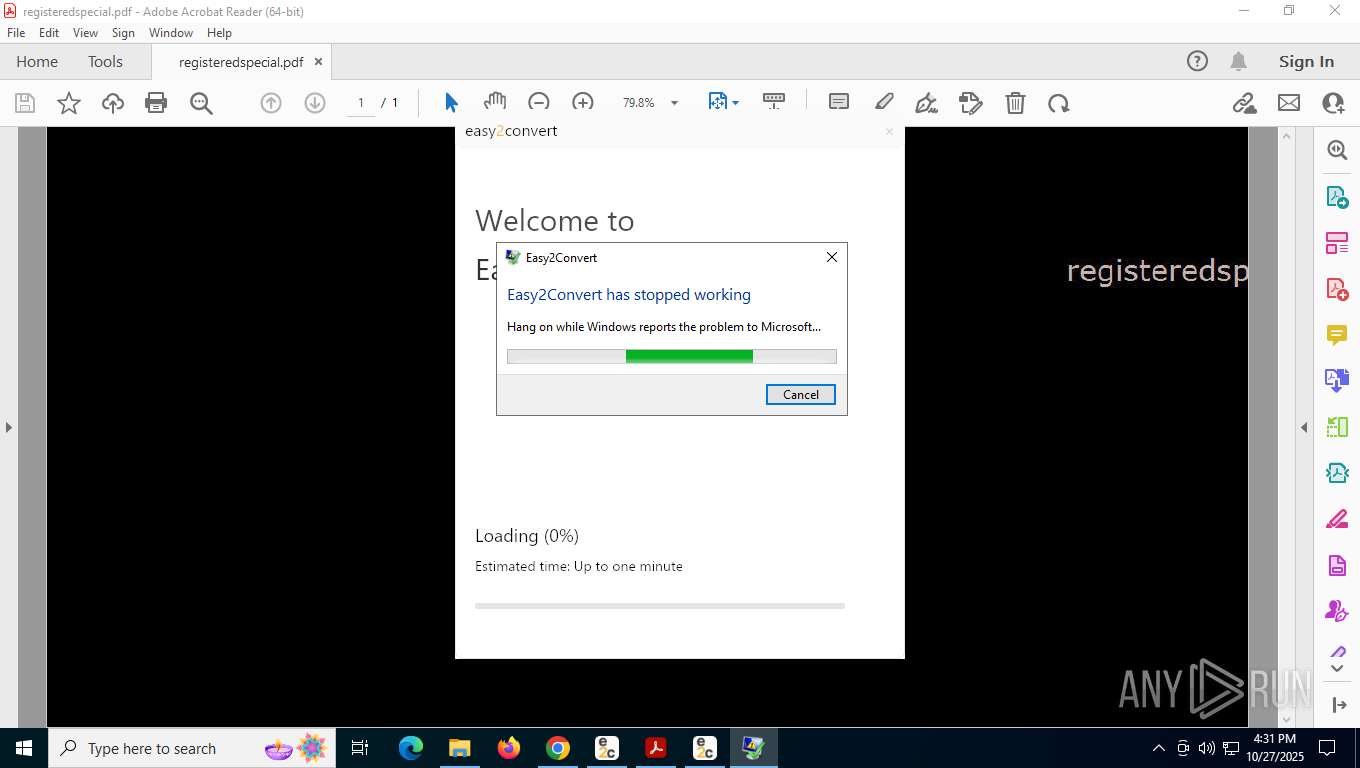
Executes application which crashes
- easy2convertapp.exe (PID: 5956)
INFO
Reads the software policy settings
- easy2convertapp.exe (PID: 2492)
- Easy2Convert.exe (PID: 6376)
- slui.exe (PID: 1928)
- easy2convertapp.exe (PID: 5956)
- WerFault.exe (PID: 5512)
- Easy2Convert.exe (PID: 7408)
Application launched itself
- chrome.exe (PID: 7508)
- Acrobat.exe (PID: 2180)
- AcroCEF.exe (PID: 4220)
- AcroCEF.exe (PID: 3144)
- Acrobat.exe (PID: 896)
- Acrobat.exe (PID: 4464)
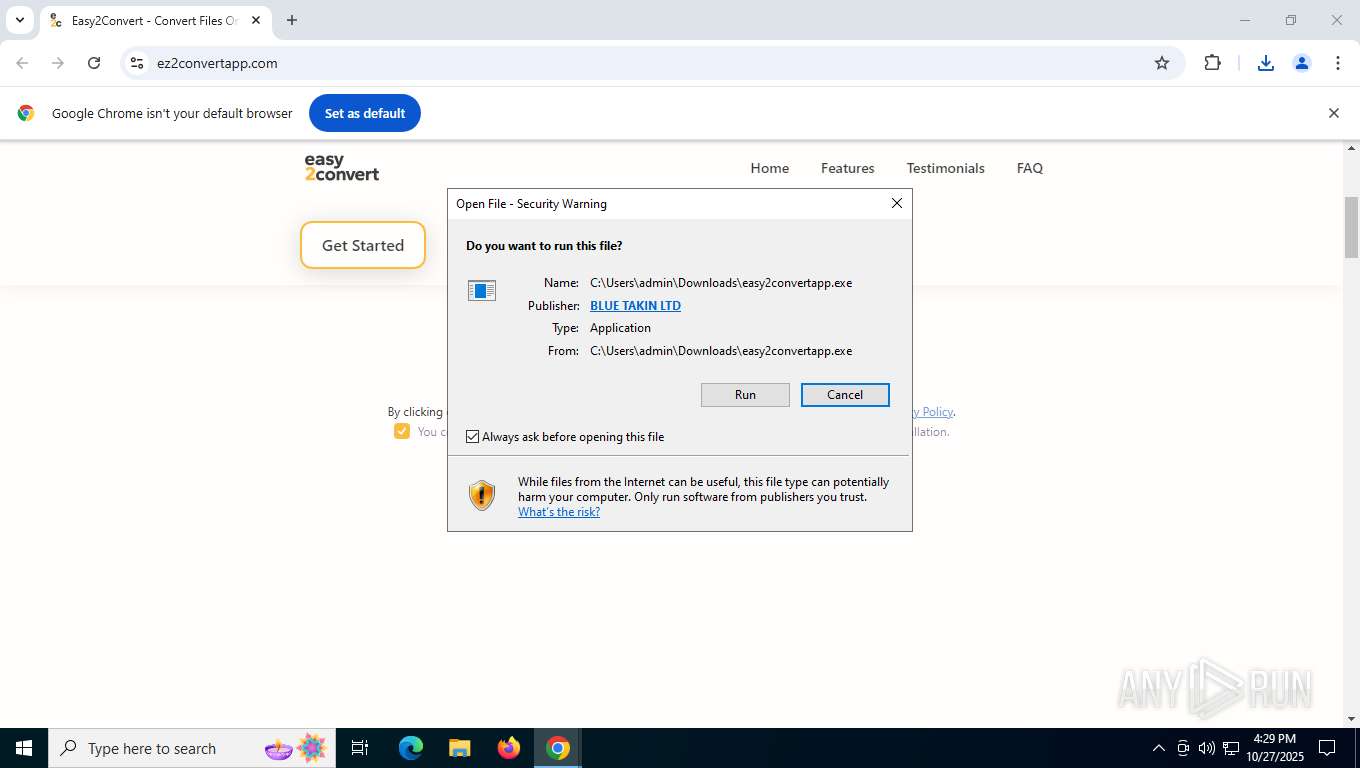
Launching a file from the Downloads directory
- chrome.exe (PID: 7508)
Reads the machine GUID from the registry
- easy2convertapp.exe (PID: 2492)
- Easy2Convert.exe (PID: 6376)
- easy2convertapp.exe (PID: 5956)
- Easy2Convert.exe (PID: 7408)
Checks supported languages
- easy2convertapp.exe (PID: 2492)
- Easy2Convert.exe (PID: 6376)
- Easy2Convert.exe (PID: 7408)
- easy2convertapp.exe (PID: 5956)
Executable content was dropped or overwritten
- chrome.exe (PID: 7508)
Reads the computer name
- easy2convertapp.exe (PID: 2492)
- Easy2Convert.exe (PID: 6376)
- easy2convertapp.exe (PID: 5956)
- Easy2Convert.exe (PID: 7408)
Checks proxy server information
- easy2convertapp.exe (PID: 2492)
- Easy2Convert.exe (PID: 6376)
- easy2convertapp.exe (PID: 5956)
- WerFault.exe (PID: 5512)
- slui.exe (PID: 1928)
- Easy2Convert.exe (PID: 7408)
Creates a software uninstall entry
- easy2convertapp.exe (PID: 2492)
Creates files or folders in the user directory
- easy2convertapp.exe (PID: 2492)
- WerFault.exe (PID: 5512)
Disables trace logs
- Easy2Convert.exe (PID: 6376)
- Easy2Convert.exe (PID: 7408)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6140)
Manual execution by a user
- Acrobat.exe (PID: 896)
- easy2convertapp.exe (PID: 5956)
- Easy2Convert.exe (PID: 7408)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 6140)
Process checks computer location settings
- Easy2Convert.exe (PID: 7408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
199
Monitored processes
52
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --field-trial-handle=3712,i,13219770930080657308,17383734088570931171,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3624 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 800 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=5696,i,13219770930080657308,17383734088570931171,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5628 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 896 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" C:\Users\admin\Downloads\registeredspecial.pdf | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1160 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2072 --field-trial-handle=1564,i,6491901009960051763,14228038402035457019,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1300 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" --type=renderer /prefetch:1 "C:\Users\admin\Downloads\titleswater.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1576 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2124 --field-trial-handle=1564,i,6491901009960051763,14228038402035457019,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | AcroCEF.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=3076,i,13219770930080657308,17383734088570931171,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=4728 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1844 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --first-renderer-process --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=3 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2288 --field-trial-handle=1584,i,6108217015446858823,14164269129555502994,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1928 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2180 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" "C:\Users\admin\Downloads\registeredspecial.pdf" | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Exit code: 1 Version: 23.1.20093.0 Modules
| |||||||||||||||
Total events
50 397
Read events
49 735
Write events
624
Delete events
38
Modification events
| (PID) Process: | (2492) easy2convertapp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Easy2Convert |
| Operation: | write | Name: | DisplayName |
Value: Easy2Convert | |||
| (PID) Process: | (2492) easy2convertapp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Easy2Convert |
| Operation: | write | Name: | Publisher |
Value: Company | |||
| (PID) Process: | (2492) easy2convertapp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Easy2Convert |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\Easy2Convert | |||
| (PID) Process: | (2492) easy2convertapp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Easy2Convert |
| Operation: | write | Name: | UninstallString |
Value: C:\Users\admin\AppData\Local\Easy2Convert\Uninstall.exe | |||
| (PID) Process: | (6376) Easy2Convert.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (6376) Easy2Convert.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 04000000030000001200000000000000110000000E000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
| (PID) Process: | (6376) Easy2Convert.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\4 |
| Operation: | write | Name: | MRUListEx |
Value: 04000000060000000500000000000000030000000200000001000000FFFFFFFF | |||
| (PID) Process: | (6376) Easy2Convert.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\119\Shell |
| Operation: | write | Name: | SniffedFolderType |
Value: Documents | |||
| (PID) Process: | (6376) Easy2Convert.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | GlobalAssocChangedCounter |
Value: 136 | |||
| (PID) Process: | (6376) Easy2Convert.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0E0000000400000003000000120000000000000011000000100000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
Executable files
11
Suspicious files
418
Text files
47
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RFfb721.TMP | — | |
MD5:— | SHA256:— | |||
| 7508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RFfb712.TMP | — | |
MD5:— | SHA256:— | |||
| 7508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RFfb721.TMP | — | |
MD5:— | SHA256:— | |||
| 7508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RFfb721.TMP | — | |
MD5:— | SHA256:— | |||
| 7508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old~RFfb721.TMP | — | |
MD5:— | SHA256:— | |||
| 7508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Segmentation Platform\SegmentInfoDB\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7508 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
84
DNS requests
82
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7788 | chrome.exe | GET | 200 | 142.250.185.238:80 | http://clients2.google.com/time/1/current?cup2key=8:OPsmwGq2QmOCnmzCbmWFJfWIiSg8g_wH7_YciQTnkoE&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
6380 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7508 | chrome.exe | GET | 200 | 151.101.66.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
7508 | chrome.exe | GET | 200 | 151.101.66.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDApgR96pRBQVJ9heJA%3D%3D | unknown | — | — | whitelisted |
7508 | chrome.exe | GET | 200 | 151.101.66.133:80 | http://ocsp.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGEJFcIpBz28BuO60qVQ%3D | unknown | — | — | whitelisted |
8064 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.3.crl | unknown | — | — | whitelisted |
5348 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzFkOTU2ODctM2JiNS00NDJhLTg2ZmEtYjM0ODZiM2YxNmVm/1.0.0.19_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
8064 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.3.crl | unknown | — | — | whitelisted |
8064 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | — | — | whitelisted |
5348 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzFkOTU2ODctM2JiNS00NDJhLTg2ZmEtYjM0ODZiM2YxNmVm/1.0.0.19_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5488 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5596 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4644 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7788 | chrome.exe | 142.250.185.238:80 | clients2.google.com | GOOGLE | US | whitelisted |
7788 | chrome.exe | 142.250.185.138:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
7788 | chrome.exe | 74.125.133.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7788 | chrome.exe | 104.18.30.155:443 | ez2convertapp.com | CLOUDFLARENET | — | unknown |
7788 | chrome.exe | 34.107.218.251:443 | dev.visualwebsiteoptimizer.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
ez2convertapp.com |
| unknown |
accounts.google.com |
| whitelisted |
www.ez2convertapp.com |
| unknown |
dev.visualwebsiteoptimizer.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
cdn.builder.io |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7788 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
7788 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
7788 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
— | — | Misc activity | ET INFO EXE - Served Attached HTTP |
— | — | A Network Trojan was detected | ET HUNTING PNG in HTTP POST (Outbound) |