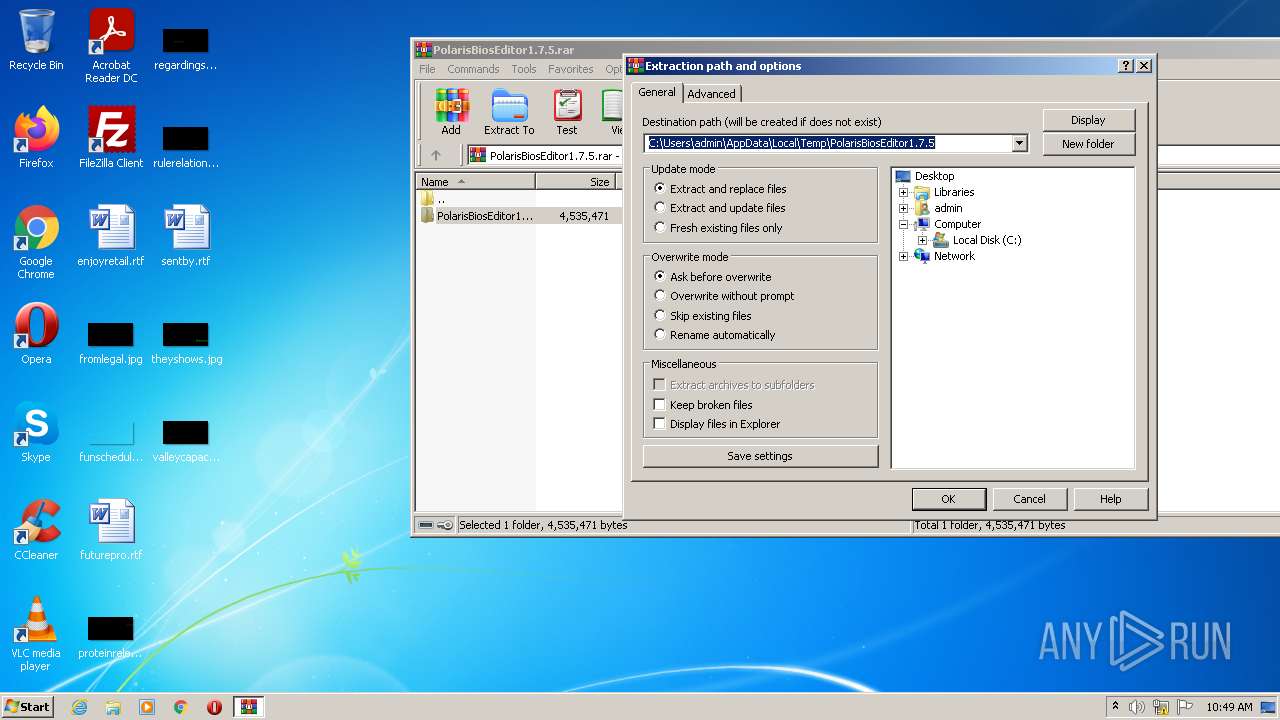
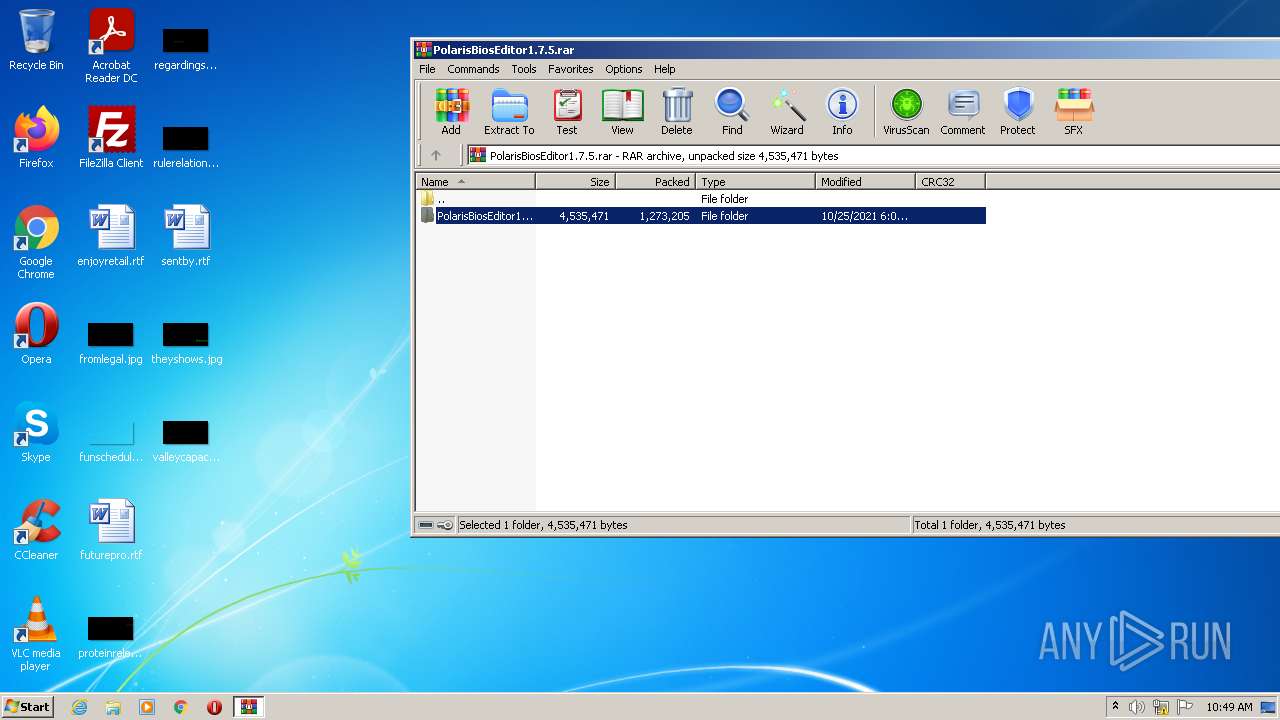
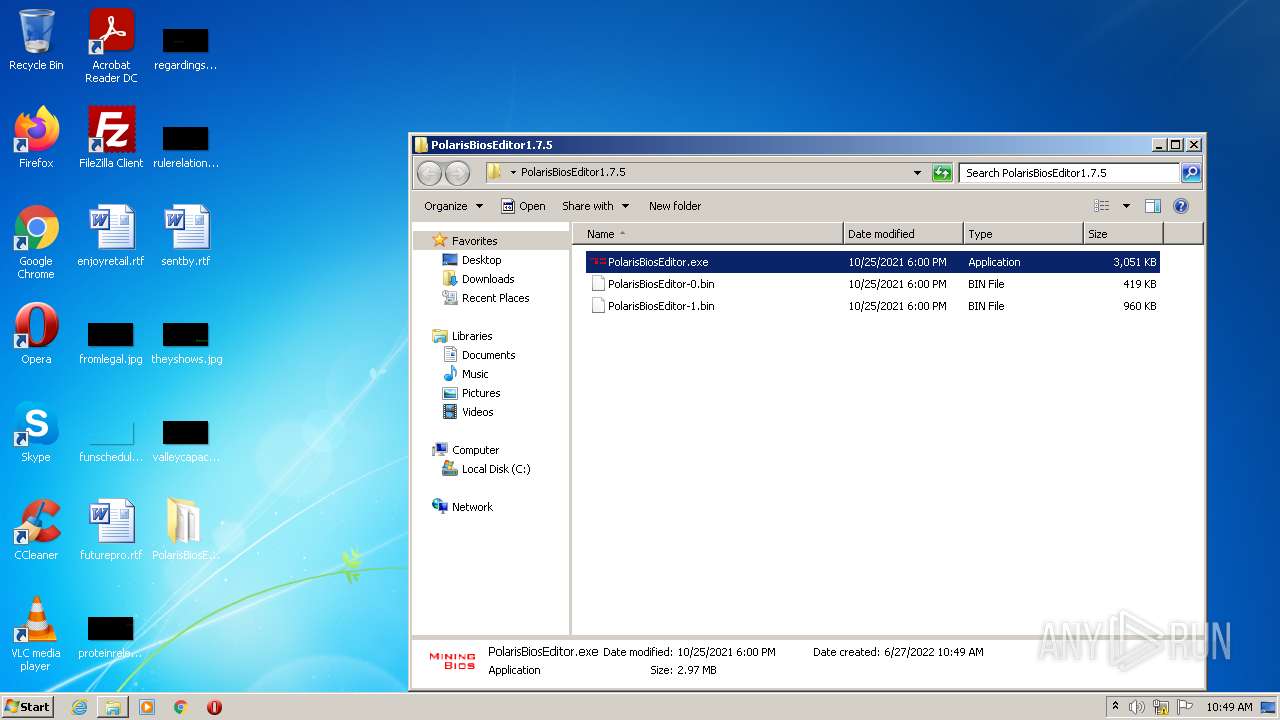
| File name: | PolarisBiosEditor1.7.5.rar |
| Full analysis: | https://app.any.run/tasks/edb0fed6-952e-4fd0-a37e-a7b84a59d316 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 09:48:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | B6A1B510035EE0BFA562F938775741FD |
| SHA1: | C6436E2C432B804157FB86C5ADF9D0C16952112F |
| SHA256: | 6517511BE249FC9B2DA3A56A477C49A0EFF3CFDECAD318321583EAF397045DF3 |
| SSDEEP: | 24576:vCULr0lnG0xrTjK9VW4OcpKRtePsMw/5MpAxEuei3iHe5gBiPu5evN1Bmtc/Tixl:vLr0vhW7OcpecPvw/5MsiHsgBiPu5mHe |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 2492)
- PolarisBiosEditor.exe (PID: 1400)
Application was dropped or rewritten from another process
- PolarisBiosEditor.exe (PID: 1400)
- PolarisBiosEditor.exe (PID: 3244)
- PolarisBiosEditor.exe (PID: 3444)
- wsqmcons.exe (PID: 2904)
- PolarisBiosEditor.exe (PID: 2608)
Runs app for hidden code execution
- wsqmcons.exe (PID: 2904)
SUSPICIOUS
Drops a file with a compile date too recent
- WinRAR.exe (PID: 2492)
- PolarisBiosEditor.exe (PID: 1400)
Checks supported languages
- WinRAR.exe (PID: 2492)
- PolarisBiosEditor.exe (PID: 3244)
- PolarisBiosEditor.exe (PID: 1400)
- PolarisBiosEditor.exe (PID: 3444)
- wsqmcons.exe (PID: 2904)
- PolarisBiosEditor.exe (PID: 2608)
- cmd.exe (PID: 3284)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2492)
- PolarisBiosEditor.exe (PID: 1400)
Reads the computer name
- PolarisBiosEditor.exe (PID: 3444)
- WinRAR.exe (PID: 2492)
- PolarisBiosEditor.exe (PID: 3244)
- PolarisBiosEditor.exe (PID: 2608)
- cmd.exe (PID: 3284)
- PolarisBiosEditor.exe (PID: 1400)
Reads Windows owner or organization settings
- PolarisBiosEditor.exe (PID: 3244)
- PolarisBiosEditor.exe (PID: 1400)
Application launched itself
- PolarisBiosEditor.exe (PID: 3444)
- PolarisBiosEditor.exe (PID: 3244)
Reads the Windows organization settings
- PolarisBiosEditor.exe (PID: 3244)
- PolarisBiosEditor.exe (PID: 1400)
Reads Environment values
- PolarisBiosEditor.exe (PID: 2608)
Creates files in the user directory
- PolarisBiosEditor.exe (PID: 1400)
Creates files in the program directory
- PolarisBiosEditor.exe (PID: 1400)
Starts CMD.EXE for commands execution
- wsqmcons.exe (PID: 2904)
INFO
Manual execution by user
- PolarisBiosEditor.exe (PID: 3444)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
47
Monitored processes
7
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1400 | "C:\Users\admin\Desktop\PolarisBiosEditor1.7.5\PolarisBiosEditor.exe" /VERYSILENT | C:\Users\admin\Desktop\PolarisBiosEditor1.7.5\PolarisBiosEditor.exe | PolarisBiosEditor.exe | ||||||||||||
User: admin Company: PolarisBiosEditor Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2492 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\PolarisBiosEditor1.7.5.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2608 | "C:\Users\admin\AppData\Roaming\PolarisBiosEditor.exe" | C:\Users\admin\AppData\Roaming\PolarisBiosEditor.exe | PolarisBiosEditor.exe | ||||||||||||
User: admin Company: https://mining-bios.eu Integrity Level: HIGH Description: PolarisBiosEditor Exit code: 0 Version: 1.7.5.0 Modules
| |||||||||||||||
| 2904 | "C:\Users\admin\AppData\Roaming\wsqmcons.exe" | C:\Users\admin\AppData\Roaming\wsqmcons.exe | — | PolarisBiosEditor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows SQM Consolidator Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3244 | "C:\Users\admin\Desktop\PolarisBiosEditor1.7.5\PolarisBiosEditor.exe" /SPAWNWND=$101B0 /NOTIFYWND=$101B0 | C:\Users\admin\Desktop\PolarisBiosEditor1.7.5\PolarisBiosEditor.exe | PolarisBiosEditor.exe | ||||||||||||
User: admin Company: PolarisBiosEditor Integrity Level: HIGH Description: Setup/Uninstall Exit code: 1 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3284 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | wsqmcons.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3444 | "C:\Users\admin\Desktop\PolarisBiosEditor1.7.5\PolarisBiosEditor.exe" | C:\Users\admin\Desktop\PolarisBiosEditor1.7.5\PolarisBiosEditor.exe | — | Explorer.EXE | |||||||||||
User: admin Company: PolarisBiosEditor Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 1 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
3 949
Read events
3 840
Write events
98
Delete events
11
Modification events
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PolarisBiosEditor1.7.5.rar | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2492) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
7
Suspicious files
4
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2492 | WinRAR.exe | C:\Users\admin\Desktop\PolarisBiosEditor1.7.5\PolarisBiosEditor-0.bin | binary | |
MD5:— | SHA256:— | |||
| 2492 | WinRAR.exe | C:\Users\admin\Desktop\PolarisBiosEditor1.7.5\PolarisBiosEditor-1.bin | binary | |
MD5:— | SHA256:— | |||
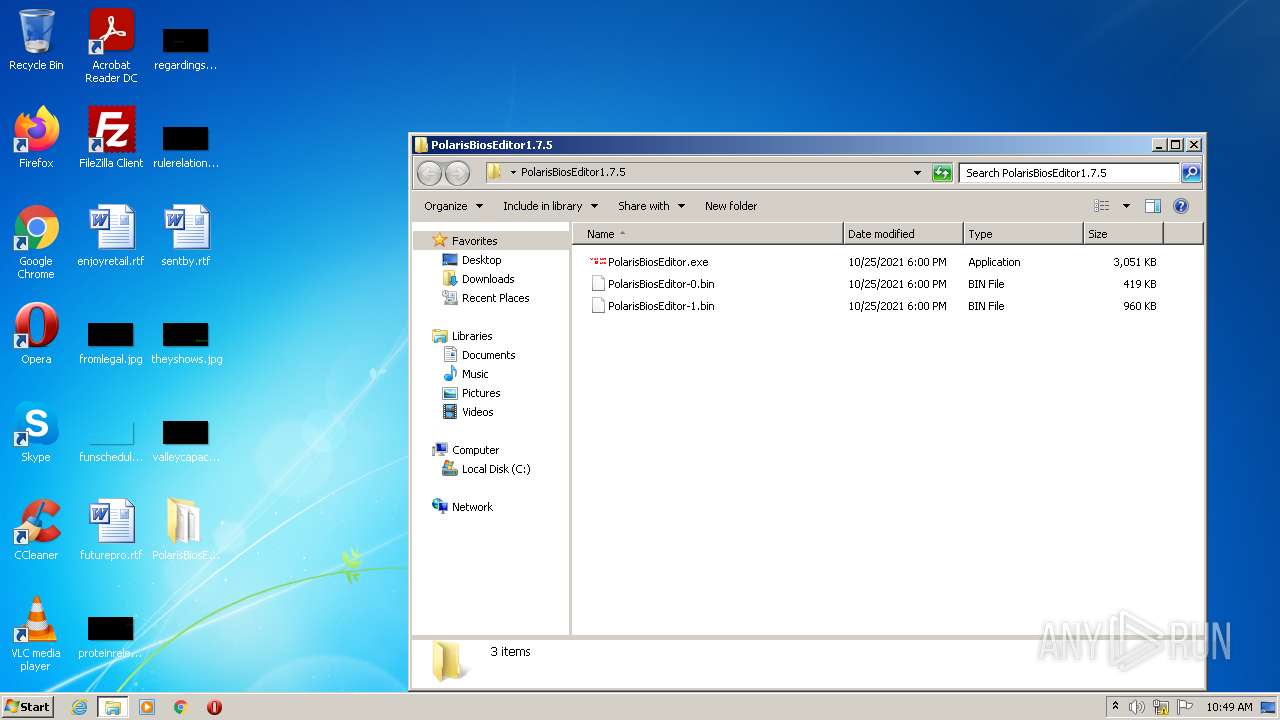
| 2492 | WinRAR.exe | C:\Users\admin\Desktop\PolarisBiosEditor1.7.5\PolarisBiosEditor.exe | executable | |
MD5:— | SHA256:— | |||
| 1400 | PolarisBiosEditor.exe | C:\Users\admin\AppData\Roaming\is-U7VUE.tmp | executable | |
MD5:— | SHA256:— | |||
| 1400 | PolarisBiosEditor.exe | C:\Users\admin\AppData\Roaming\u.txt | text | |
MD5:— | SHA256:— | |||
| 1400 | PolarisBiosEditor.exe | C:\Users\admin\AppData\Roaming\z.txt | text | |
MD5:— | SHA256:— | |||
| 1400 | PolarisBiosEditor.exe | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Windows NT\Version_PolarisBiosEditor.lnk | lnk | |
MD5:— | SHA256:— | |||
| 1400 | PolarisBiosEditor.exe | C:\Users\admin\AppData\Roaming\is-FV2DD.tmp | text | |
MD5:— | SHA256:— | |||
| 1400 | PolarisBiosEditor.exe | C:\Users\admin\AppData\Roaming\tdh.dll | executable | |
MD5:— | SHA256:— | |||
| 1400 | PolarisBiosEditor.exe | C:\Users\admin\AppData\Roaming\is-GAA54.tmp | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
3
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2608 | PolarisBiosEditor.exe | 185.199.111.133:443 | raw.githubusercontent.com | GitHub, Inc. | NL | suspicious |
880 | svchost.exe | 151.139.128.11:443 | imagizer.imageshack.com | Highwinds Network Group, Inc. | US | malicious |
— | — | 151.139.128.11:443 | imagizer.imageshack.com | Highwinds Network Group, Inc. | US | malicious |
3284 | cmd.exe | 151.139.128.11:443 | imagizer.imageshack.com | Highwinds Network Group, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
imagizer.imageshack.com |
| whitelisted |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
880 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |