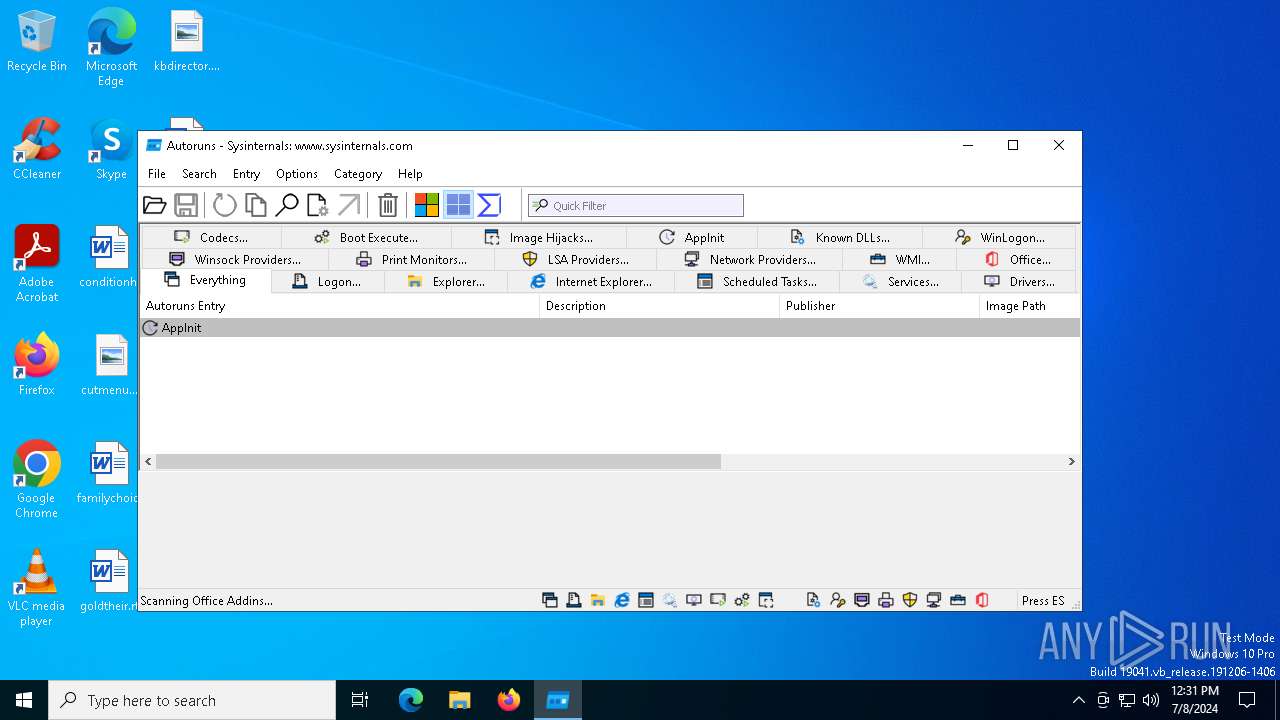
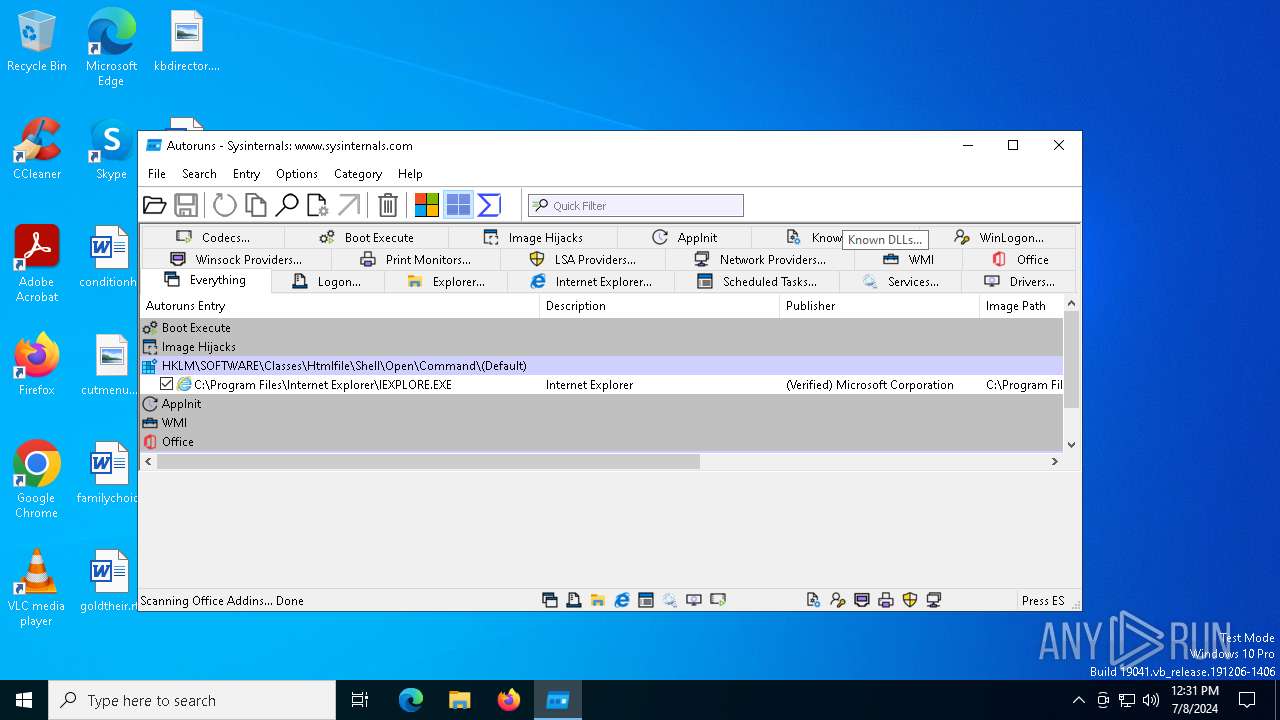
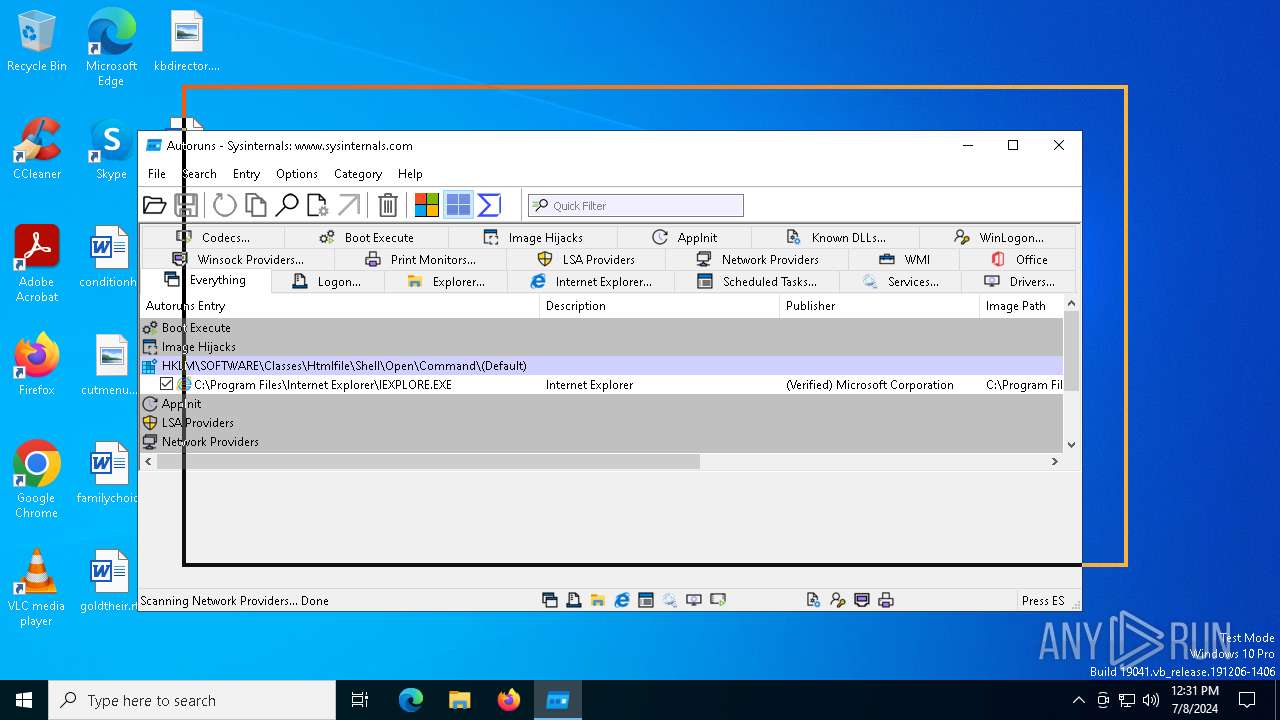
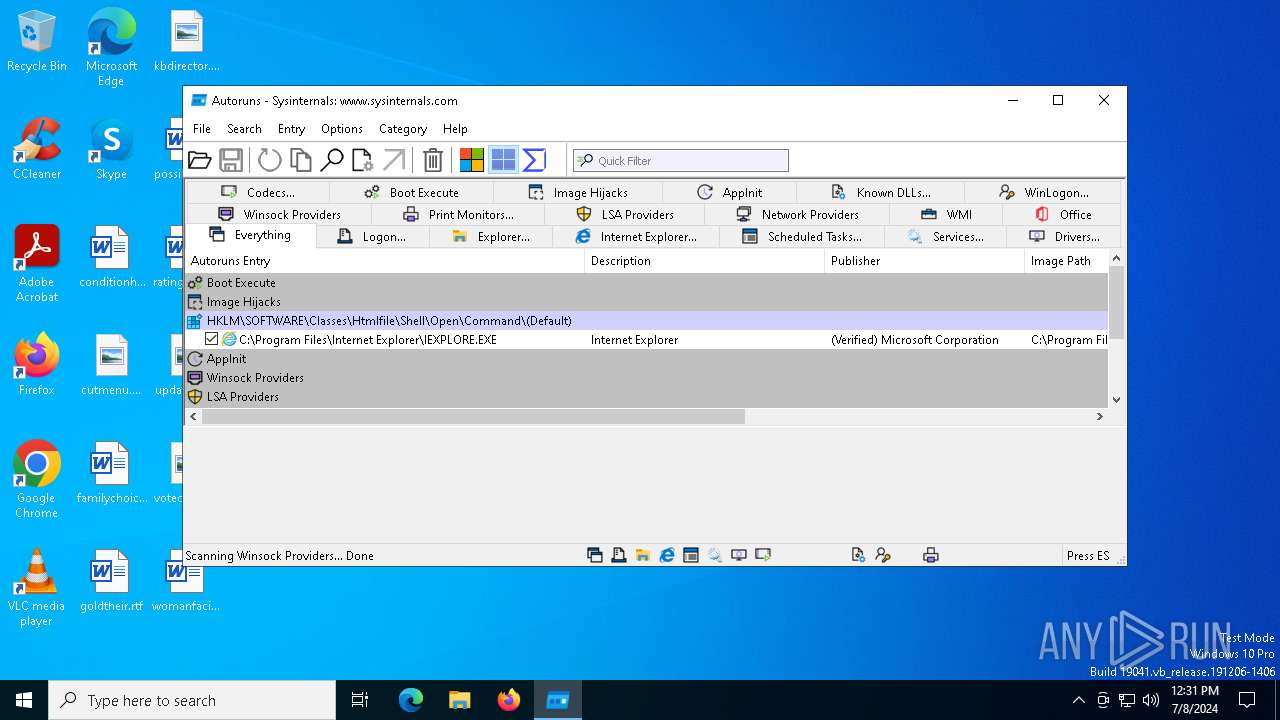
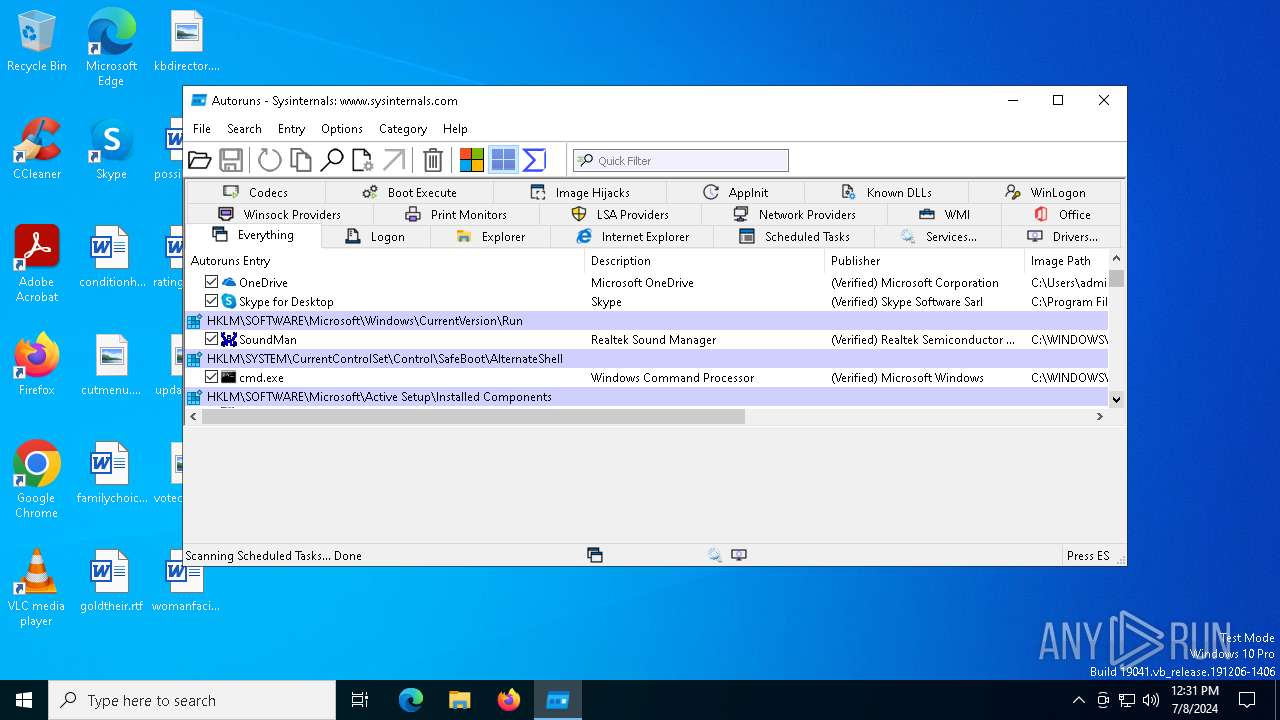
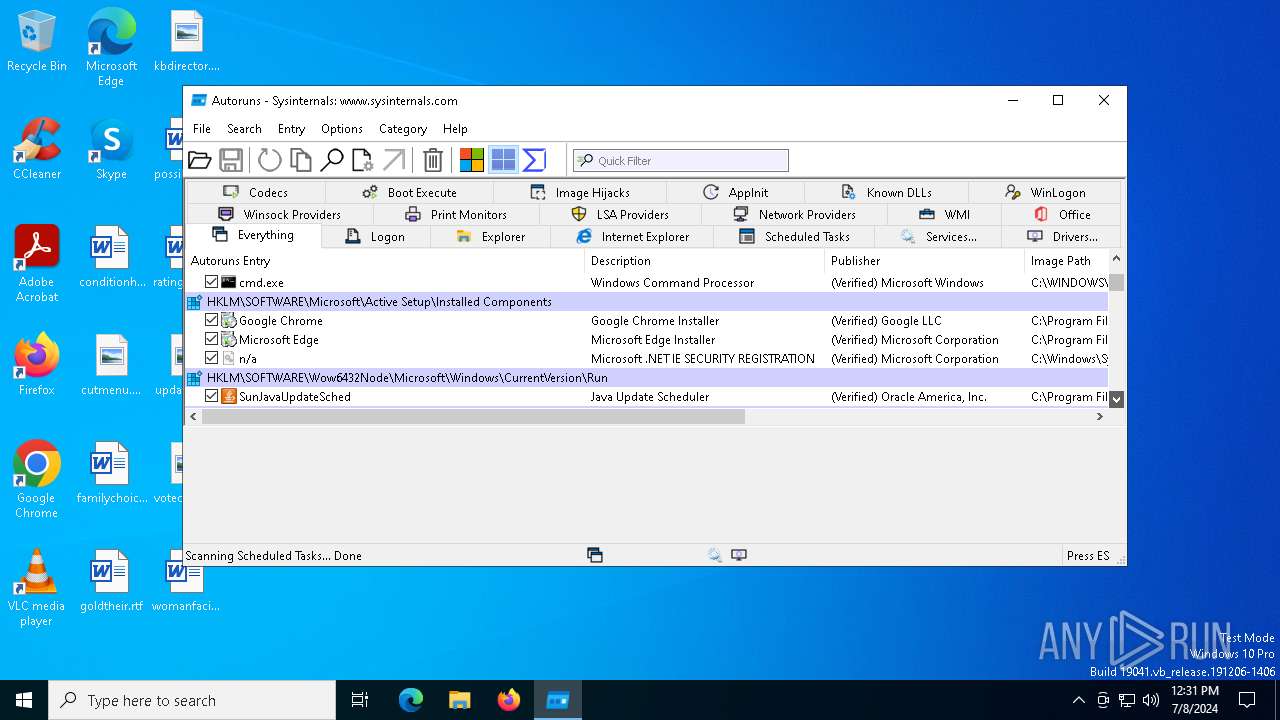
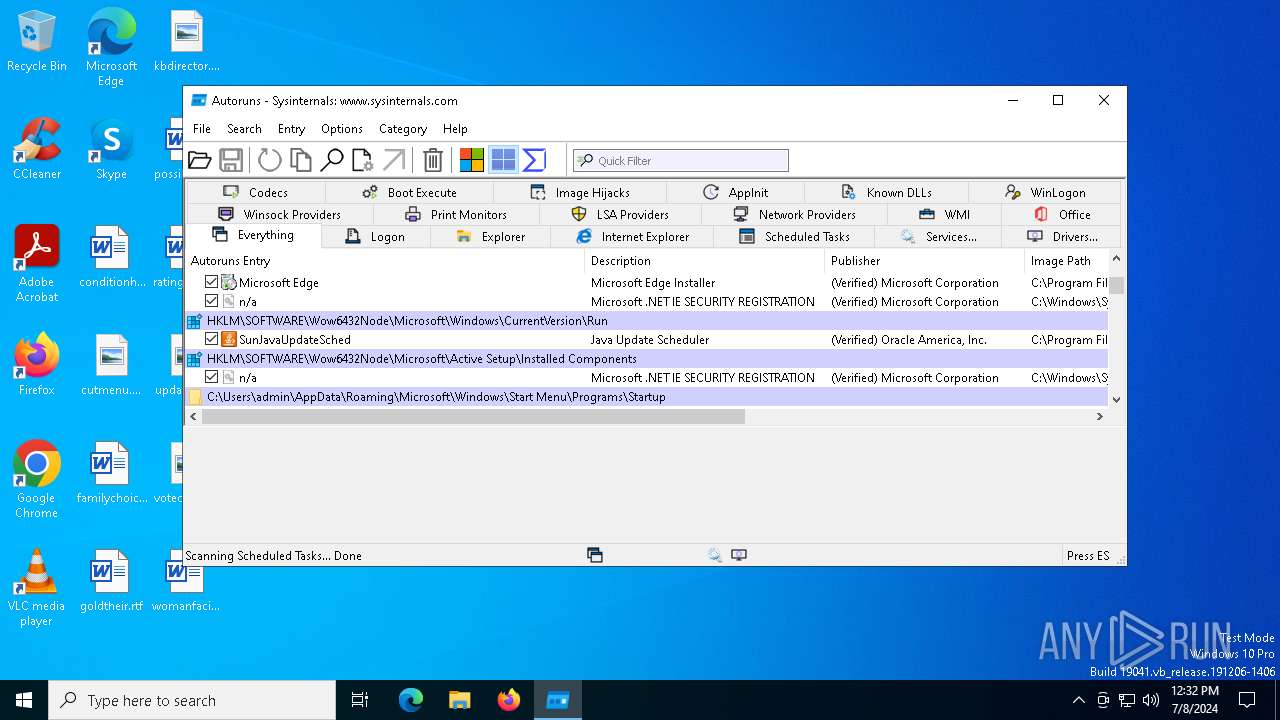
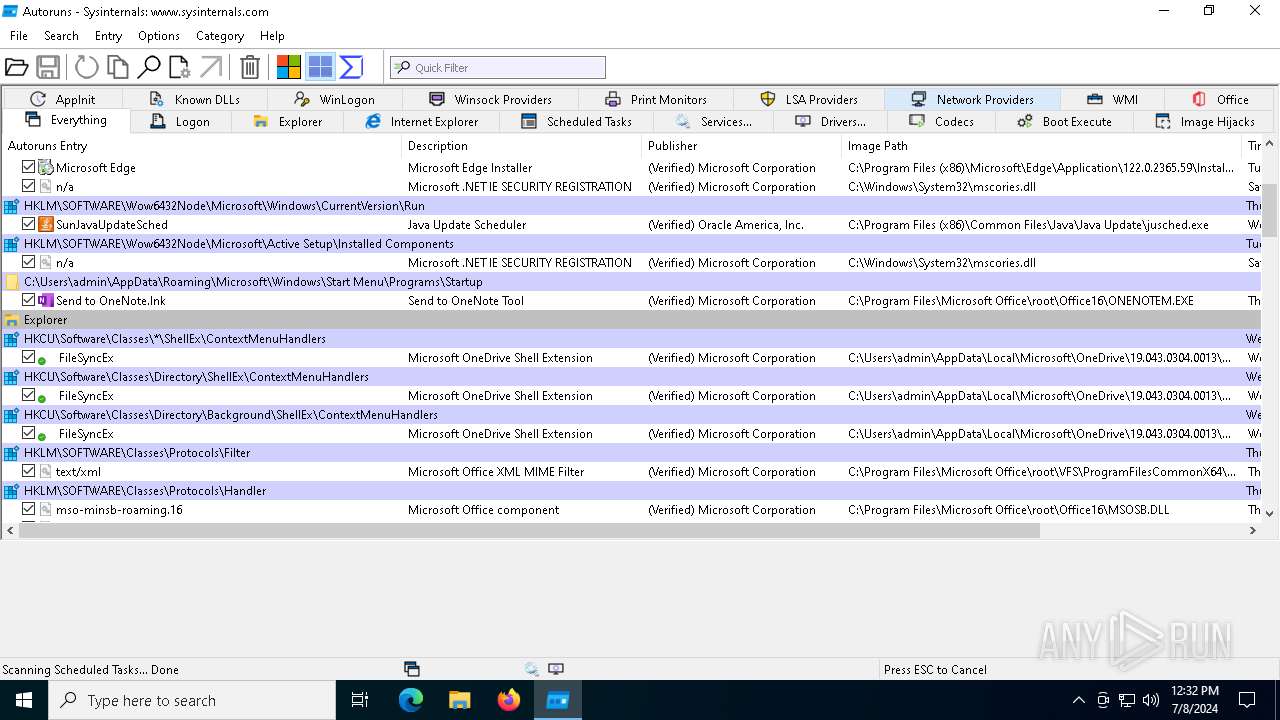
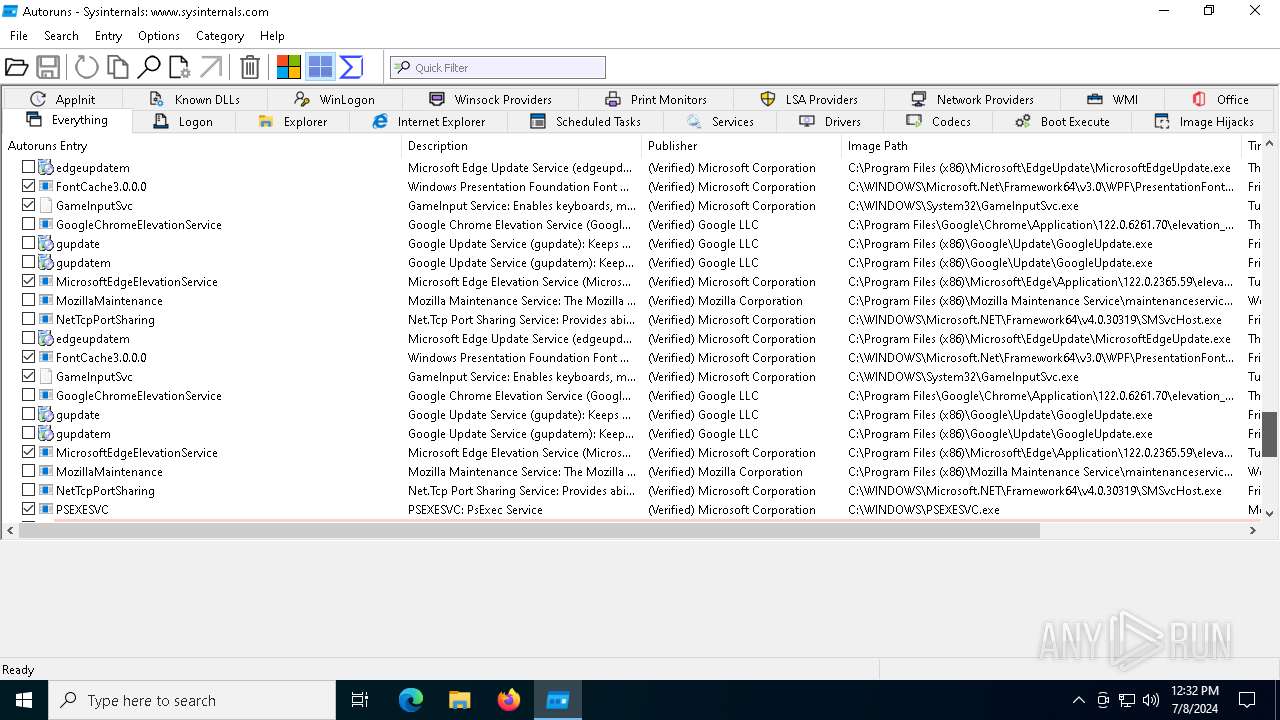
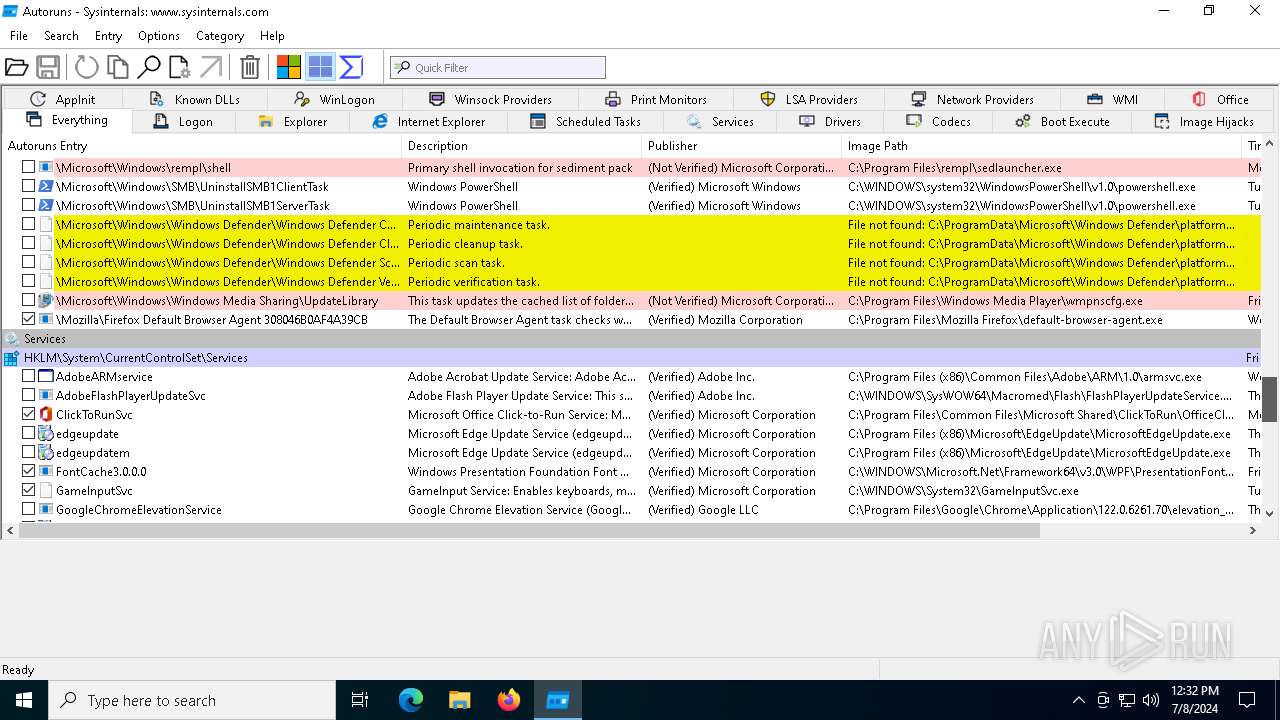
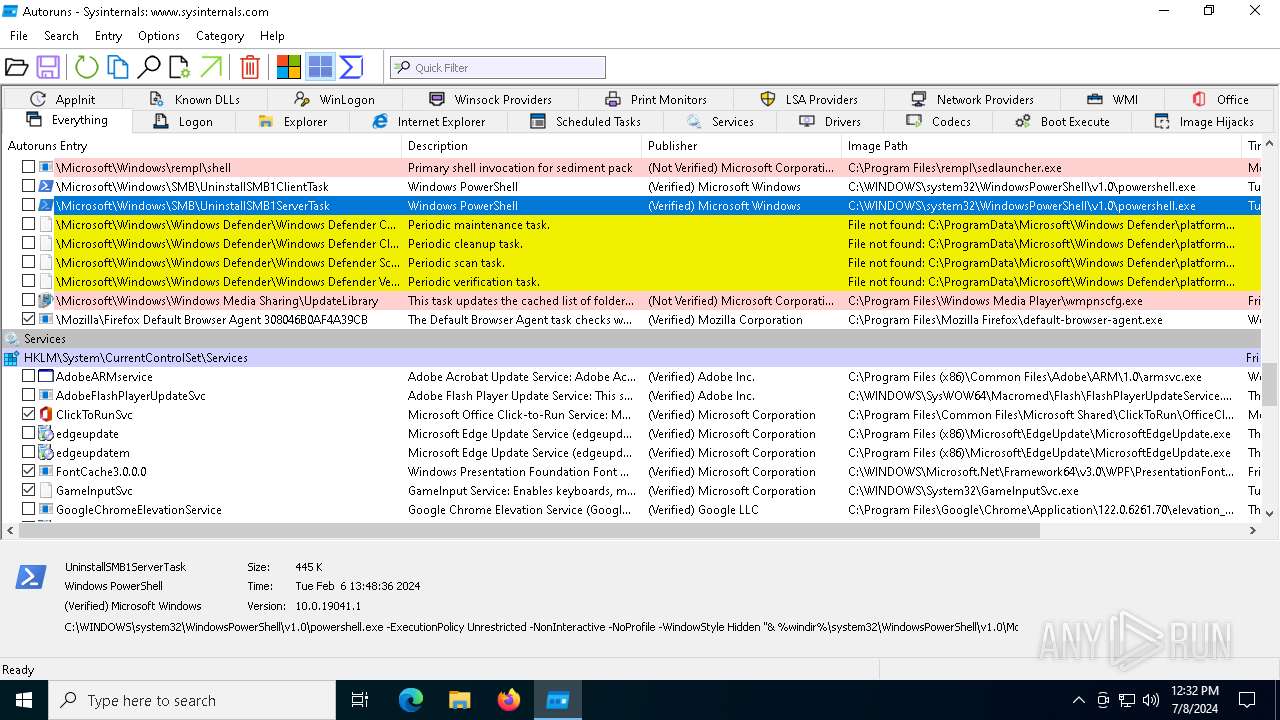
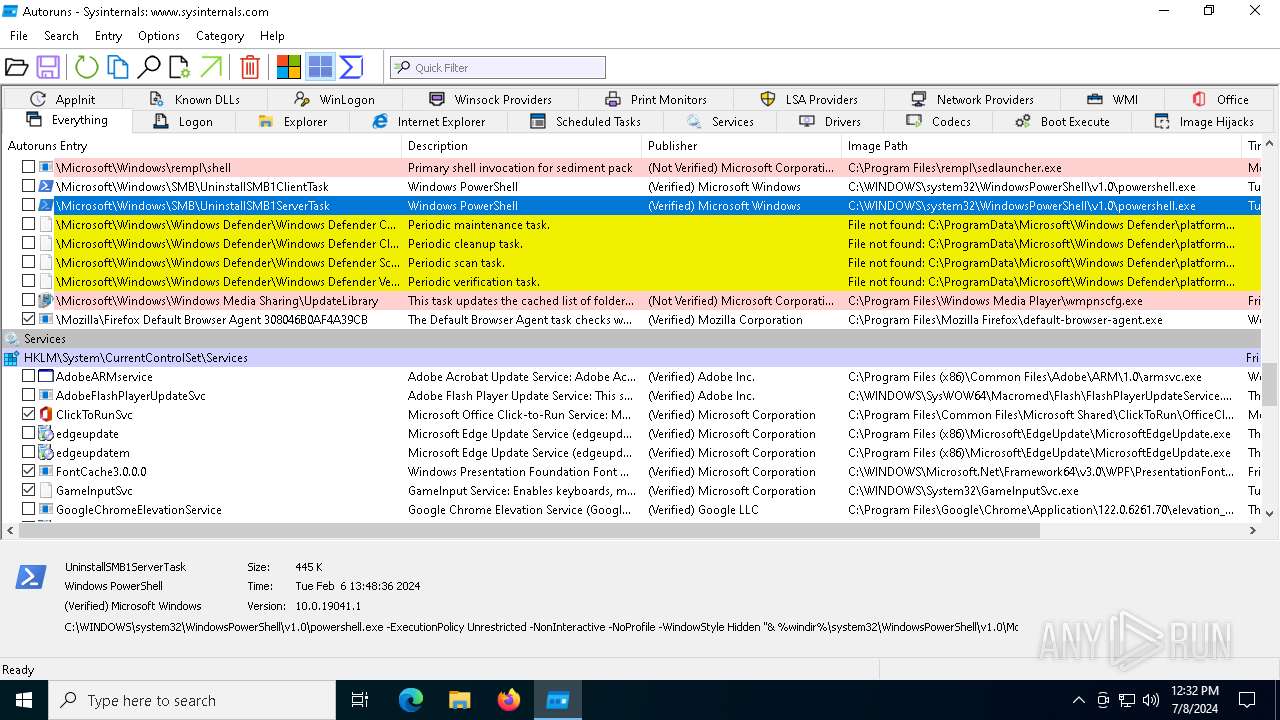
| File name: | autoruns.exe |
| Full analysis: | https://app.any.run/tasks/bc5547e5-3de7-4a8b-a4f4-97901181947a |
| Verdict: | Malicious activity |
| Analysis date: | July 08, 2024, 12:31:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 583ED542BE17B83F3C102D49FE984E26 |
| SHA1: | 142FC798C0E89B55198C3DFC5CAAB8A10D9AA150 |
| SHA256: | 64D490783ABD017AC36A017B9CB7DCFC2FCEE85F7AE8EE203A0C898DA6D37533 |
| SSDEEP: | 49152:wjLCJSLYIujU519eCvepXi/Wsqo69n1lme8CeD3p:wjLCJSLYdjkrWsqo691lmJ |
MALICIOUS
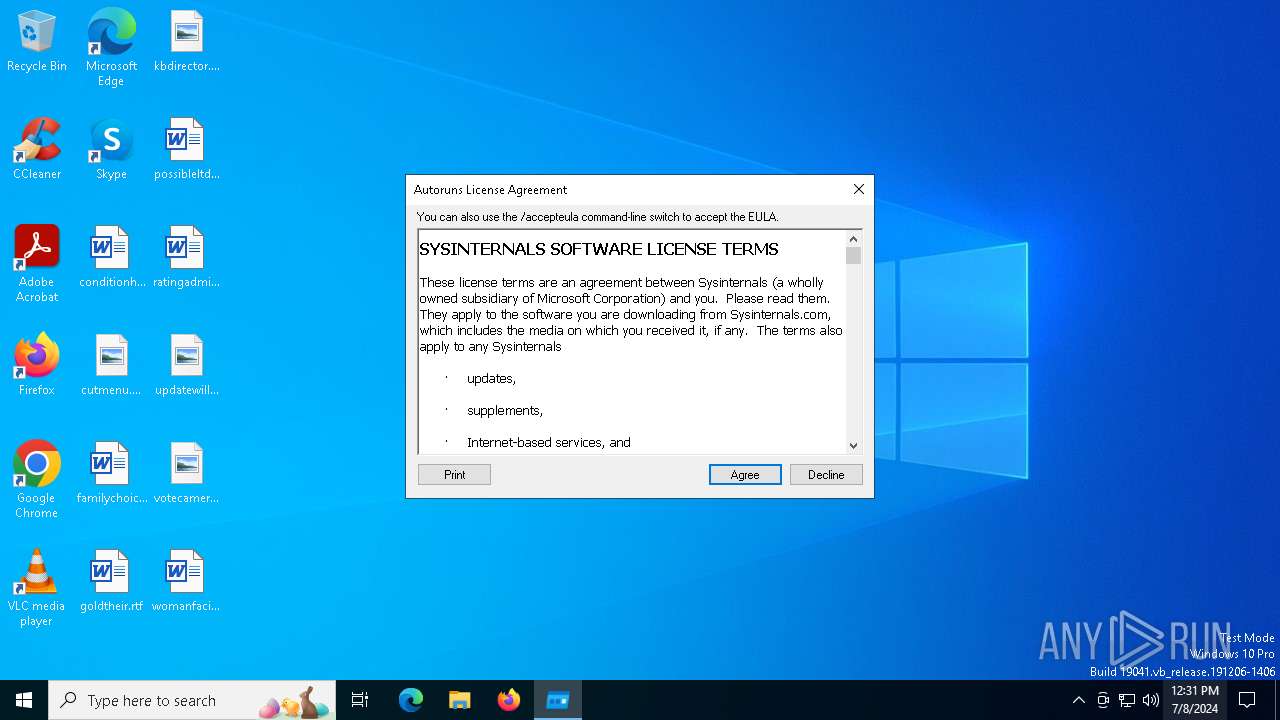
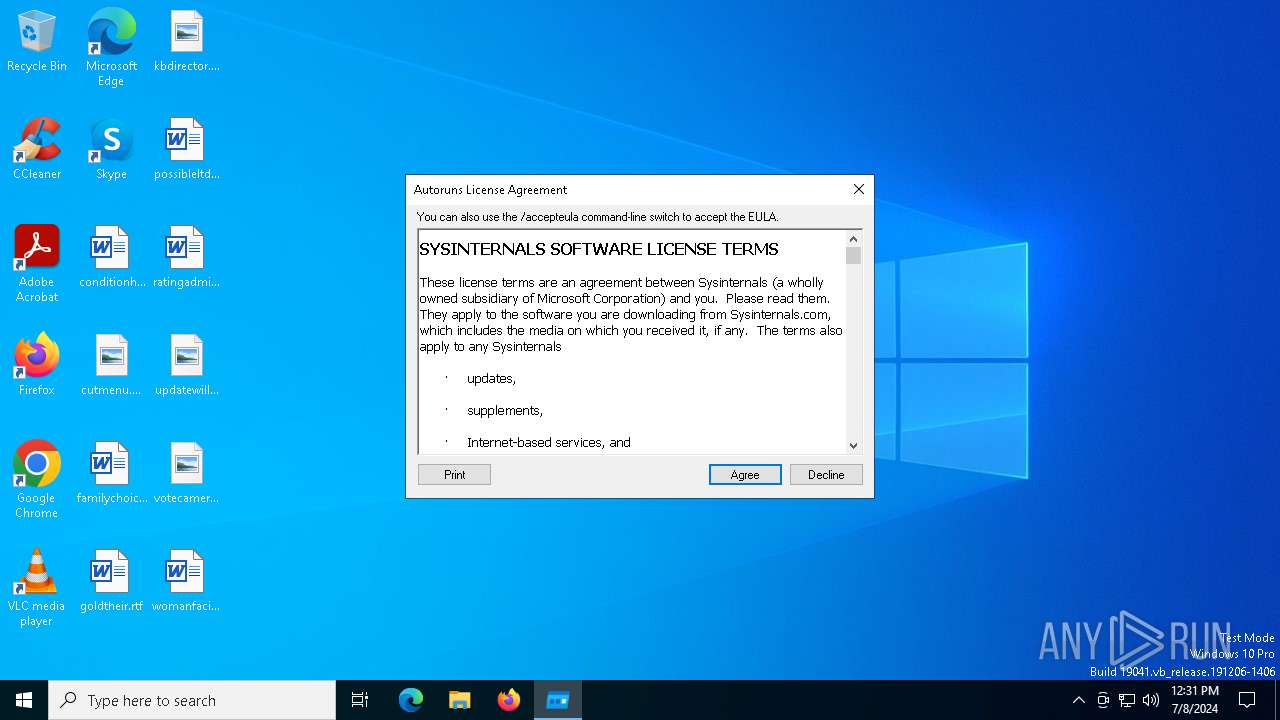
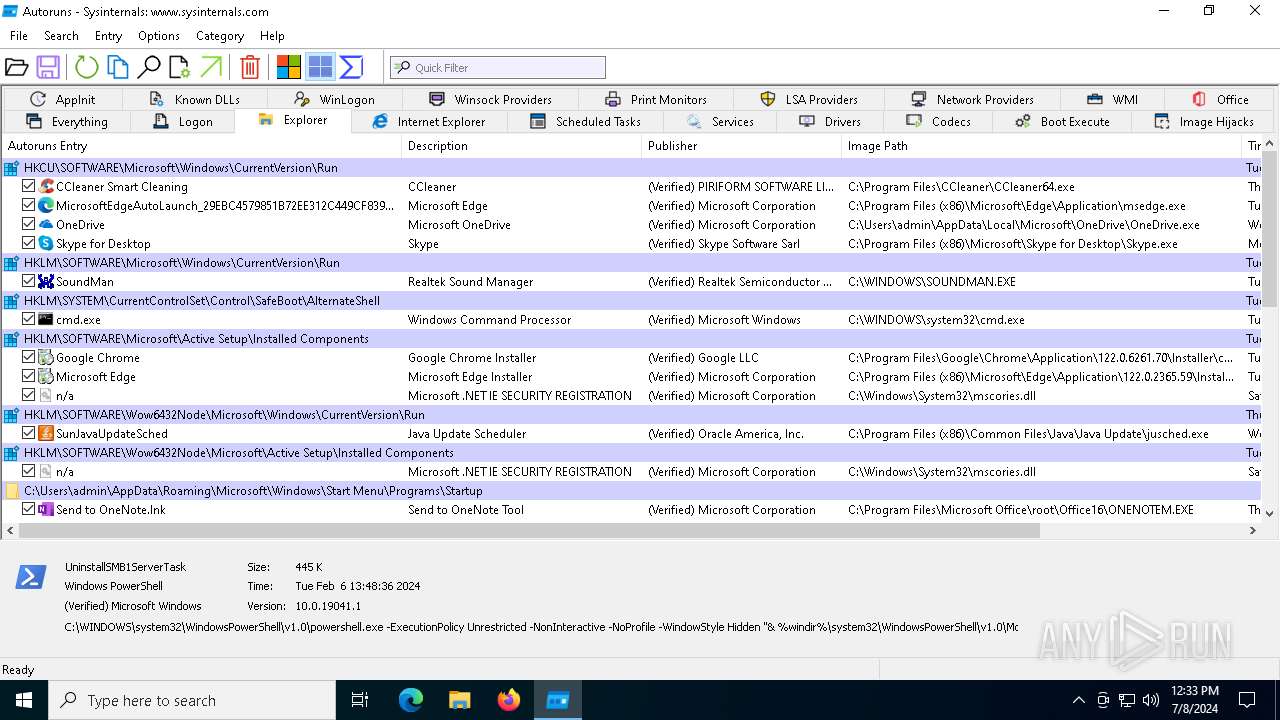
Drops the executable file immediately after the start
- autoruns.exe (PID: 4860)
SUSPICIOUS
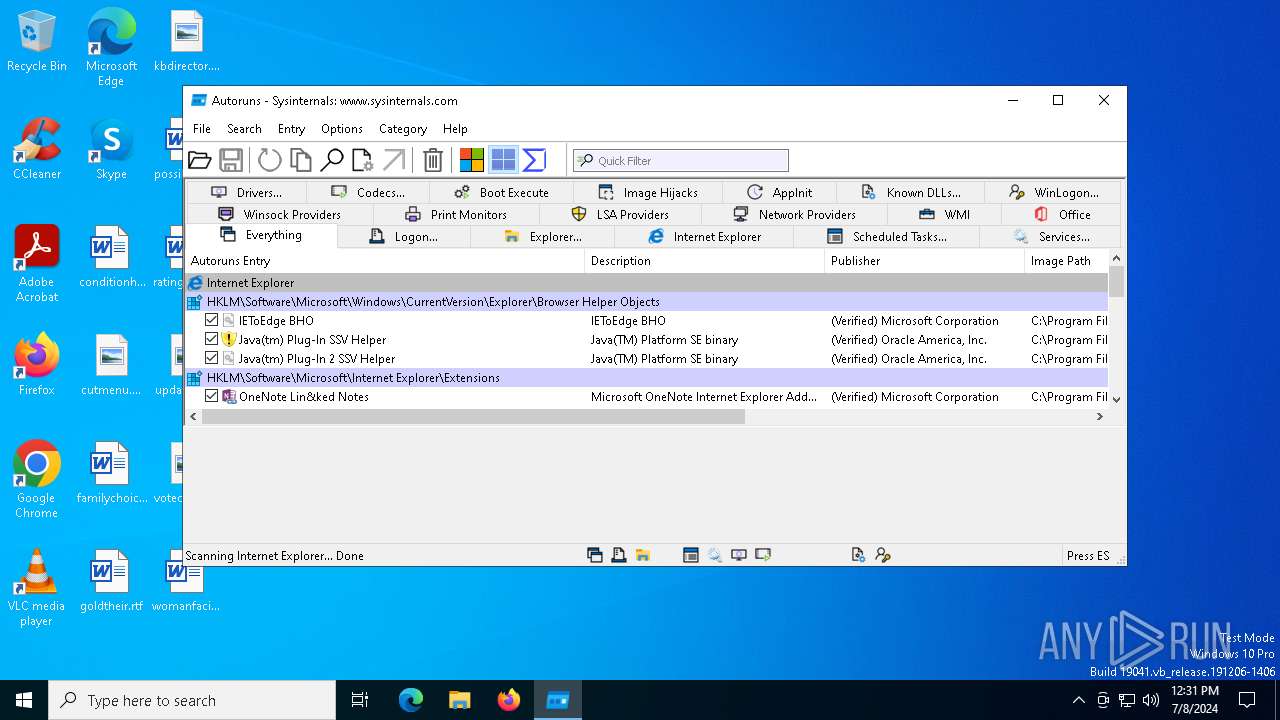
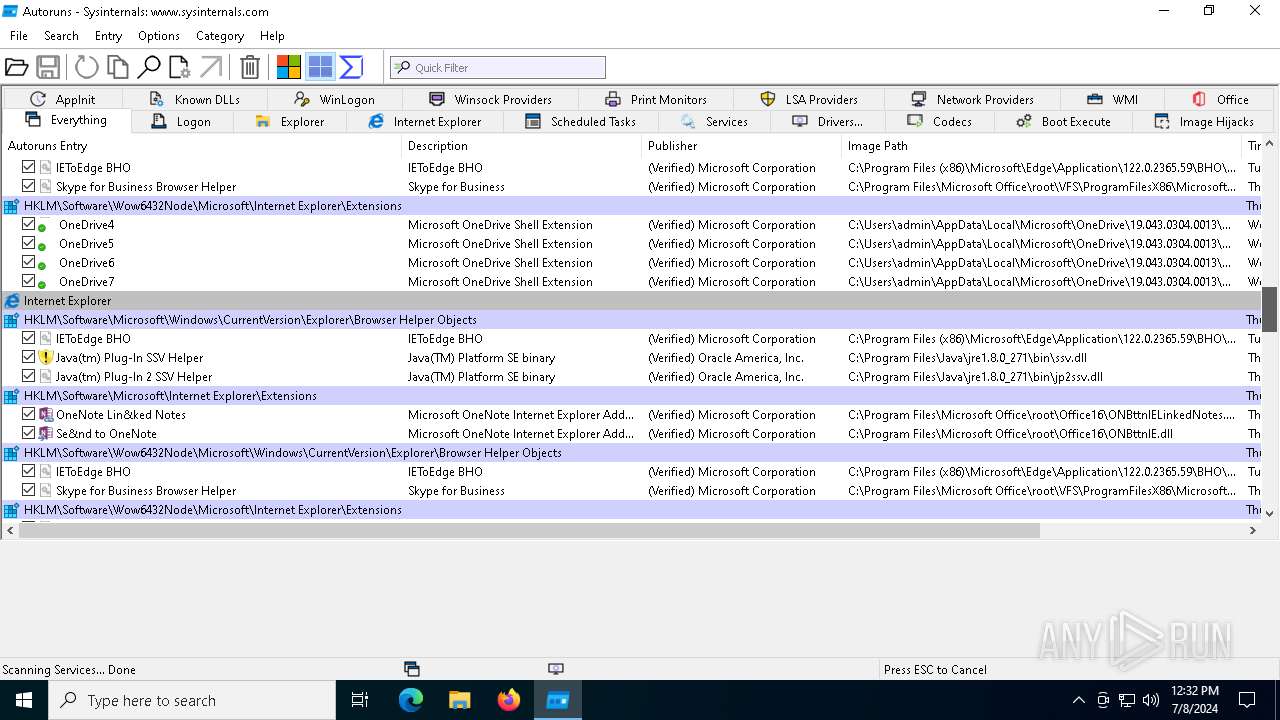
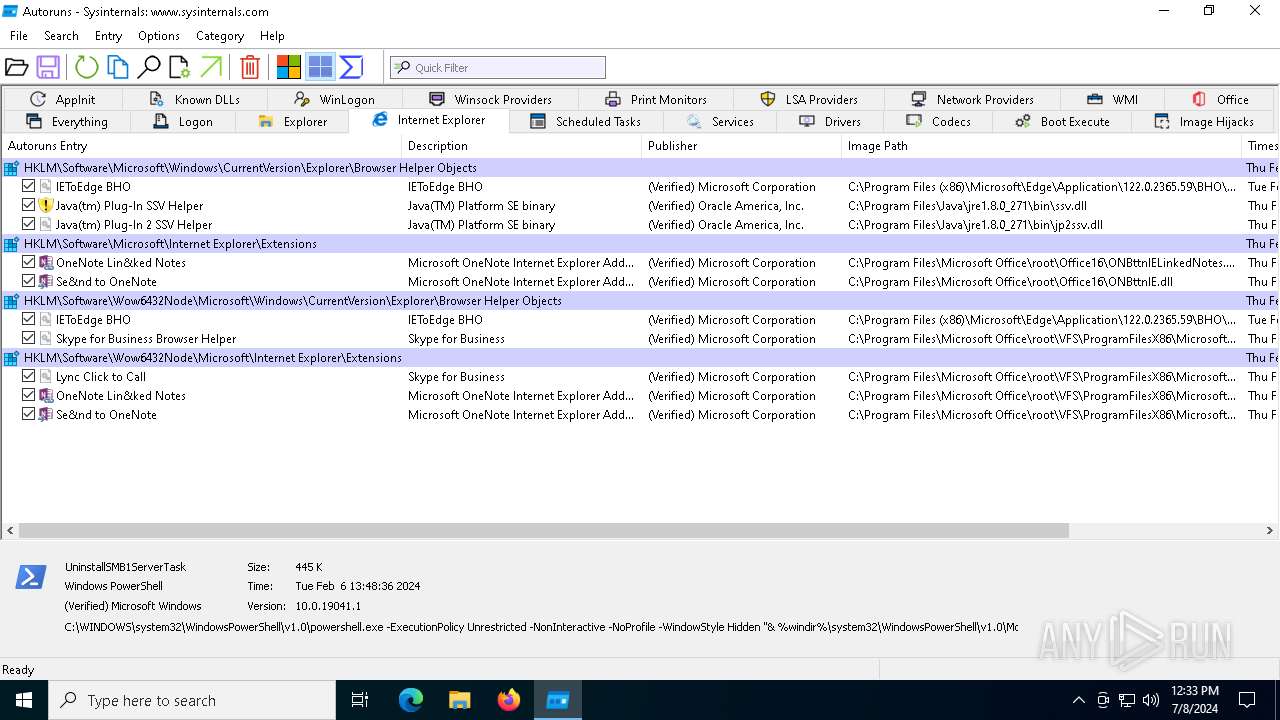
Reads security settings of Internet Explorer
- autoruns.exe (PID: 4860)
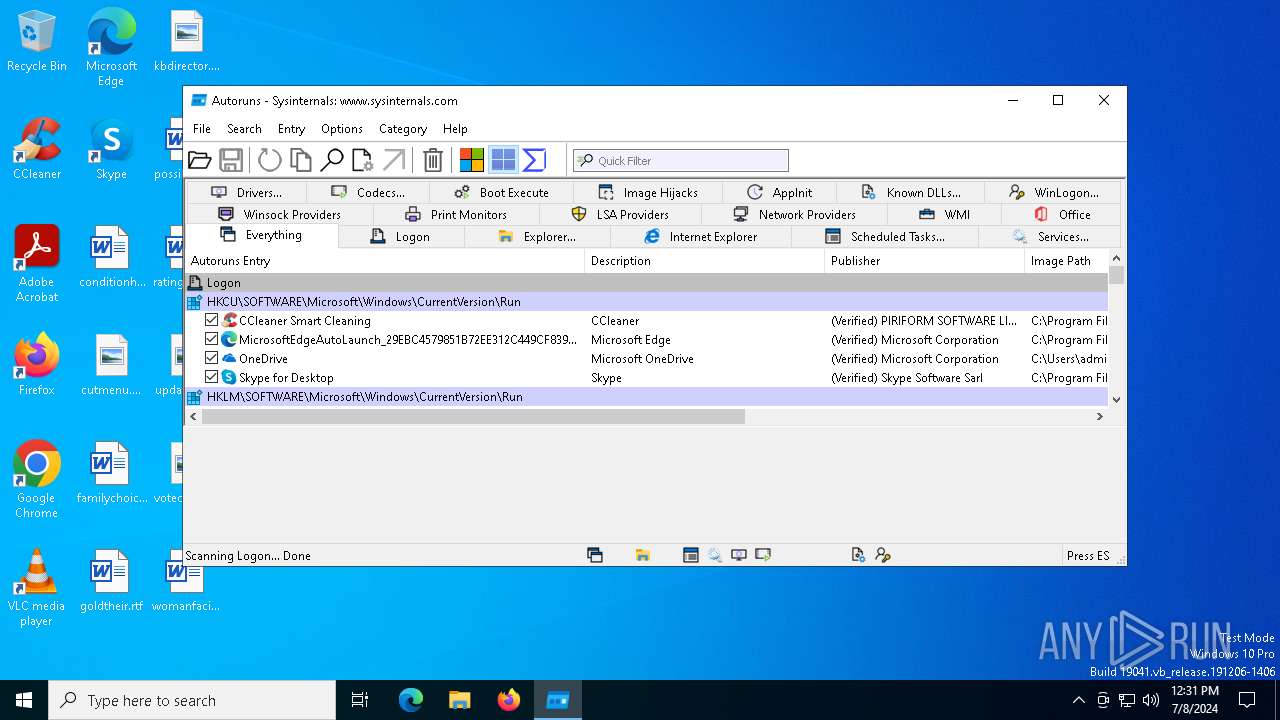
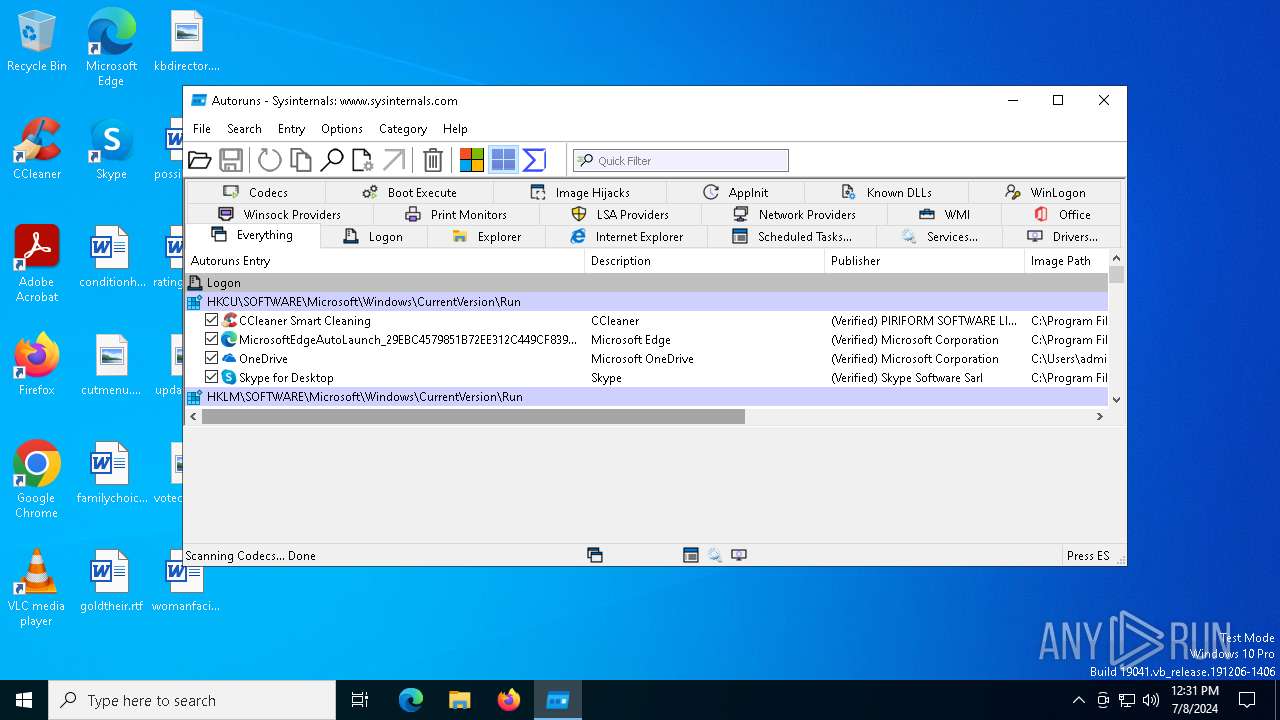
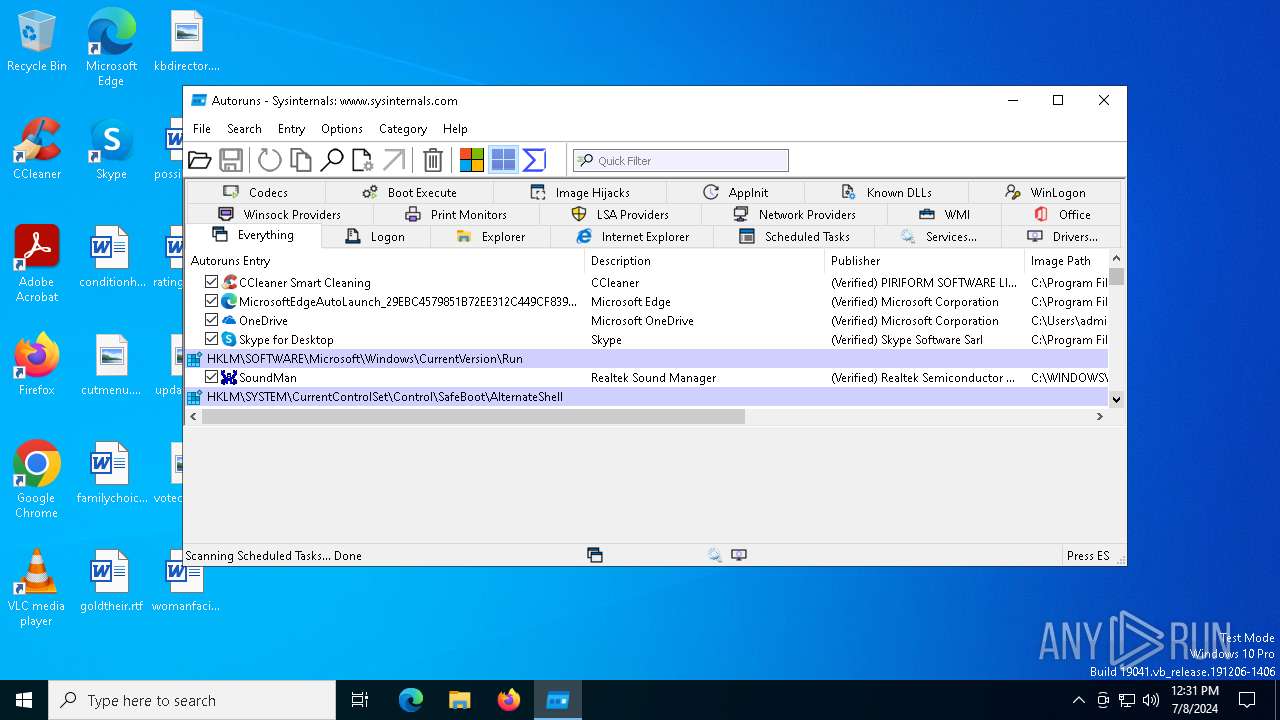
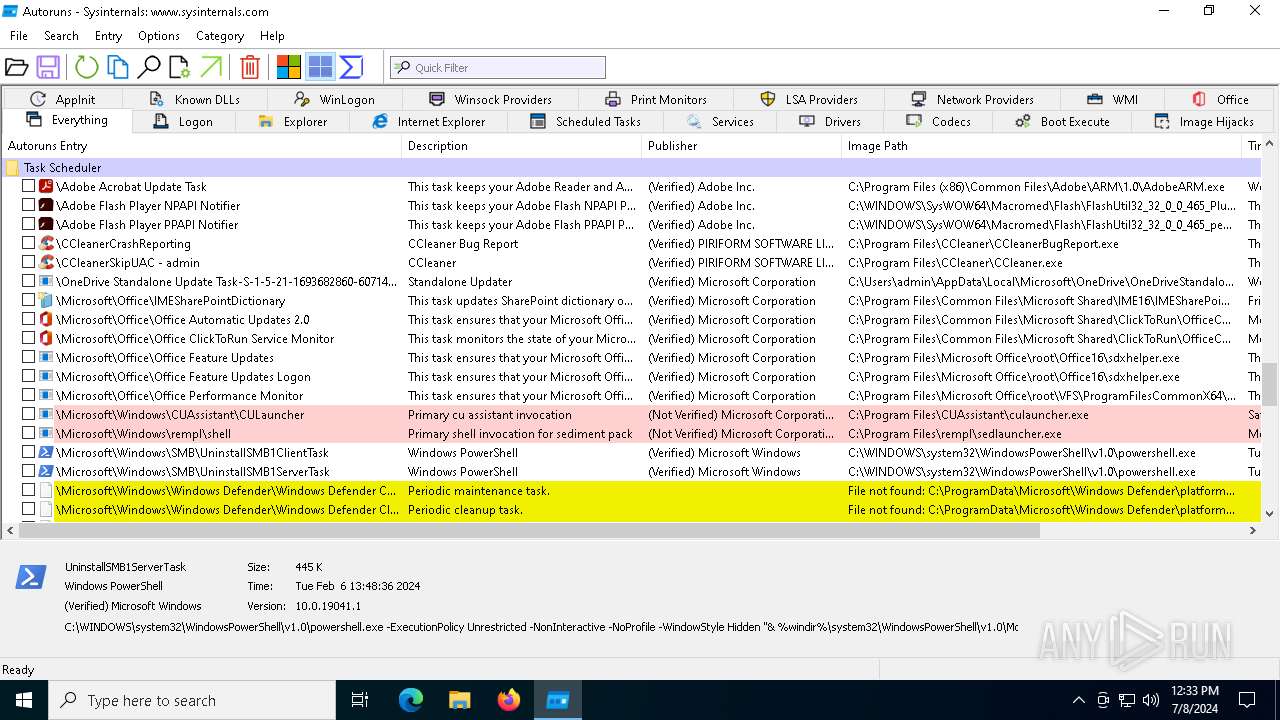
Read startup parameters
- autoruns.exe (PID: 4860)
Checks Windows Trust Settings
- autoruns.exe (PID: 4860)
INFO
Checks supported languages
- autoruns.exe (PID: 4860)
Reads the machine GUID from the registry
- autoruns.exe (PID: 4860)
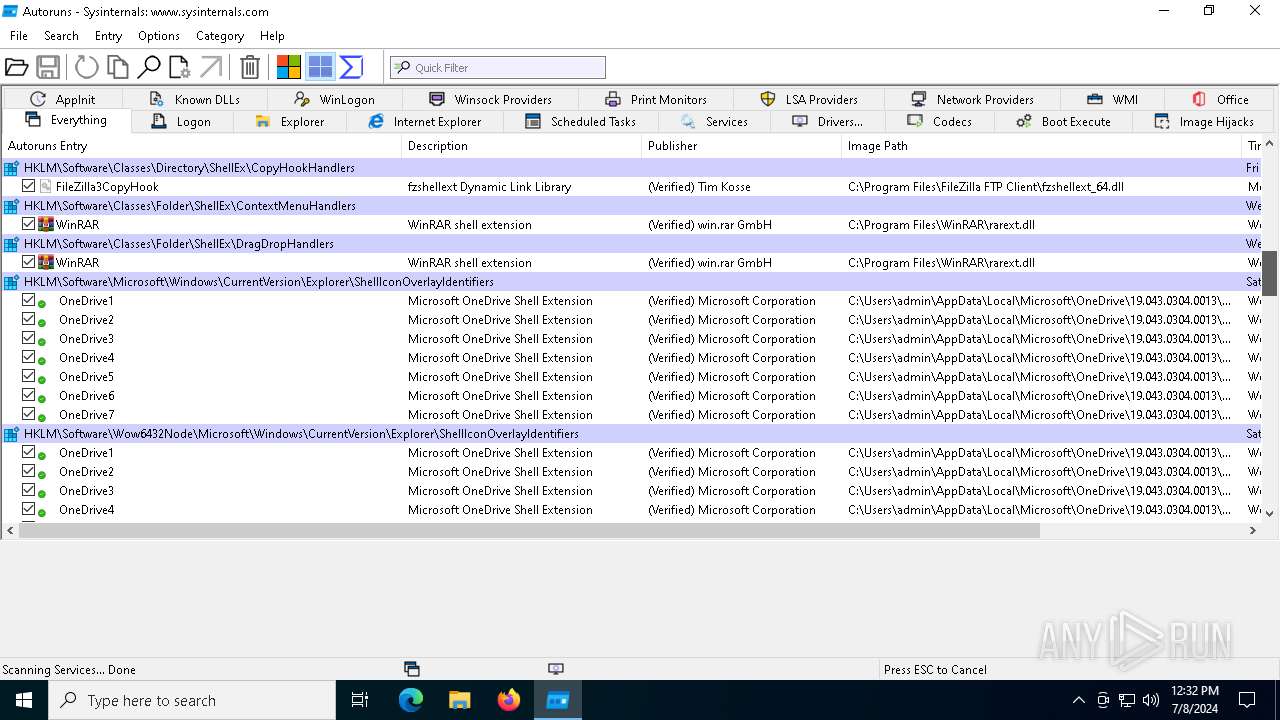
Reads Microsoft Office registry keys
- autoruns.exe (PID: 4860)
Creates files or folders in the user directory
- autoruns.exe (PID: 4860)
Reads the computer name
- autoruns.exe (PID: 4860)
Checks proxy server information
- autoruns.exe (PID: 4860)
Reads Environment values
- autoruns.exe (PID: 4860)
Reads the software policy settings
- autoruns.exe (PID: 4860)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:02:14 20:13:32+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 1309184 |
| InitializedDataSize: | 1189888 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xd36ae |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 14.0.9.0 |
| ProductVersionNumber: | 14.0.9.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Sysinternals - www.sysinternals.com |
| FileDescription: | Autostart program viewer |
| FileVersion: | 14.09 |
| InternalName: | Sysinternals Autoruns |
| LegalCopyright: | Copyright (C) 2002-2022 Mark Russinovich |
| OriginalFileName: | autoruns.exe |
| ProductName: | Sysinternals autoruns |
| ProductVersion: | 14.09 |
Total processes
134
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4860 | "C:\Users\admin\AppData\Local\Temp\autoruns.exe" | C:\Users\admin\AppData\Local\Temp\autoruns.exe | explorer.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Autostart program viewer Version: 14.09 Modules
| |||||||||||||||
Total events
45 452
Read events
45 398
Write events
54
Delete events
0
Modification events
| (PID) Process: | (4860) autoruns.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Sysinternals\Autoruns |
| Operation: | write | Name: | EulaAccepted |
Value: 1 | |||
| (PID) Process: | (4860) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\mswsock.dll,-60100 |
Value: MSAFD Tcpip [TCP/IP] | |||
| (PID) Process: | (4860) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\mswsock.dll,-60101 |
Value: MSAFD Tcpip [UDP/IP] | |||
| (PID) Process: | (4860) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\mswsock.dll,-60102 |
Value: MSAFD Tcpip [RAW/IP] | |||
| (PID) Process: | (4860) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\mswsock.dll,-60200 |
Value: MSAFD Tcpip [TCP/IPv6] | |||
| (PID) Process: | (4860) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\mswsock.dll,-60201 |
Value: MSAFD Tcpip [UDP/IPv6] | |||
| (PID) Process: | (4860) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\mswsock.dll,-60202 |
Value: MSAFD Tcpip [RAW/IPv6] | |||
| (PID) Process: | (4860) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wshqos.dll,-100 |
Value: RSVP TCPv6 Service Provider | |||
| (PID) Process: | (4860) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wshqos.dll,-101 |
Value: RSVP TCP Service Provider | |||
| (PID) Process: | (4860) autoruns.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\wshqos.dll,-102 |
Value: RSVP UDPv6 Service Provider | |||
Executable files
0
Suspicious files
58
Text files
0
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4860 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\45AE547469FB7137480E06153457A2DD | binary | |
MD5:F7D30DE70649E2211C4F9C7FC8242DD1 | SHA256:9BA3B2DD74E67B7CCDB70BC96F37CC946EC4E7748645A4B0C2B146902D29A691 | |||
| 4860 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\45AE547469FB7137480E06153457A2DD | binary | |
MD5:6B769DB3020C81D2E526159023B9859E | SHA256:1E929D06F06A034171AB4F6C015C97C8927E5FB43C6DA2FDE645AD16CAE7CDEF | |||
| 4860 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\36AC0BE60E1243344AE145F746D881FE | binary | |
MD5:A20961D8BD1A5A7D241026D0011751FB | SHA256:4D6AE5BBEF0EACFDC09D5ADE4D145E883CF41B131E4C6988738769F1D32E12F3 | |||
| 4860 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:16CA6BA6C40A0AF999DB5E69ADB317FD | SHA256:52432C84D33C90526184DD4AFFA5E960A1A0F0810EC22B1D9183AB861486F243 | |||
| 4860 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4C7F163ED126D5C3CB9457F68EC64E9E | binary | |
MD5:1AD5F25419B60337F276A68FEFFB826C | SHA256:0B2CCA39C77DB566F0009D0D5FB1F79B1167D2CC955EAD2B7F6DB2B96F5FA03A | |||
| 4860 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\36AC0BE60E1243344AE145F746D881FE | binary | |
MD5:B4B5F6994EF26A1DF463D8BBA6E03D63 | SHA256:FB182DE0BFFA5E643F7DCC2309A3AB3E93D996B9C67AEB1EF50F86326E90F7CF | |||
| 4860 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0B8A20E1F3F4D73D52A19929F922C892 | binary | |
MD5:09E5AA2B1903859E6FA248FC0EE3B3B4 | SHA256:A963DA4FCDC475B2B367819A3F54002864E22BEF83C1D5BCEACB2A9B66B69F65 | |||
| 4860 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:148C0AE23D31B795166AC6ED31C0AD6F | SHA256:C9750FD018A5B66DC4AD13E3950BDD8D155E0F21FCC90BC8E5474D85571CFD57 | |||
| 4860 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0B8A20E1F3F4D73D52A19929F922C892 | binary | |
MD5:AB8508CE5BB034E895357B71E5C4A30E | SHA256:817A13BE52F0436FF291390A430C65AC1946A28924B3AE3D447AB828FDB55C65 | |||
| 4860 | autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:94A884307C1CEC1C090A17990C4C637C | SHA256:D17B7DC124CEDD72ED7EDF6949E31DFE50D3E657F90E8D7F12E7E34513D49263 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
83
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2808 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4860 | autoruns.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAPxtOFfOoLxFJZ4s9fYR1w%3D | unknown | — | — | unknown |
4860 | autoruns.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAQJGBtf1btmdVNDtW%2BVUAg%3D | unknown | — | — | unknown |
4860 | autoruns.exe | GET | 200 | 192.229.221.95:80 | http://crl.verisign.com/pca3.crl | unknown | — | — | unknown |
4860 | autoruns.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnR4FoxLLkI7vkvsUIFlZt%2BlGH3gQUWsS5eyoKo6XqcQPAYPkt9mV1DlgCEAkQWITrlZ07yLmU%2BRintu4%3D | unknown | — | — | unknown |
4860 | autoruns.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAV14ffsm9imej9hicY%2Bl7s%3D | unknown | — | — | unknown |
4860 | autoruns.exe | GET | 200 | 152.199.19.74:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FxkCfyHfJr7GQ6M658NRZ4SHo%2FAQUCPVR6Pv%2BPT1kNnxoz1t4qN%2B5xTcCEF5t3Ic3UIKEWBT0QtHYKiU%3D | unknown | — | — | unknown |
1616 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
4860 | autoruns.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | unknown |
4860 | autoruns.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4656 | SearchApp.exe | 104.126.37.186:443 | — | Akamai International B.V. | DE | unknown |
1828 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1220 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2808 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2808 | svchost.exe | 192.229.221.95:80 | crl.verisign.com | EDGECAST | US | whitelisted |
4656 | SearchApp.exe | 104.126.37.128:443 | — | Akamai International B.V. | DE | unknown |
1060 | svchost.exe | 23.213.166.81:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 52.111.227.13:443 | nexusrules.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.verisign.com |
| whitelisted |
ocsp.verisign.com |
| whitelisted |
csc3-2004-crl.verisign.com |
| unknown |