| File name: | KMSpico-setup.exe |
| Full analysis: | https://app.any.run/tasks/53a33b9b-bd98-487f-bae3-50d1fb58660b |
| Verdict: | Malicious activity |
| Analysis date: | August 23, 2024, 15:31:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A02164371A50C5FF9FA2870EF6E8CFA3 |
| SHA1: | 060614723F8375ECAAD8B249FF07E3BE082D7F25 |
| SHA256: | 64C731ADBE1B96CB5765203B1E215093DCF268D020B299445884A4AE62ED2D3A |
| SSDEEP: | 98304:CgbTbhBxCLS0Kx/XRCsFlPsKh9ApbeicTkxchy6pA32b7SuzWl:rxBxCLS3xZCsFyBzxcE6pAGbq |
MALICIOUS
Uses Task Scheduler to run other applications
- cmd.exe (PID: 7004)
Changes image file execution options
- AutoPico.exe (PID: 7052)
- KMSELDI.exe (PID: 1048)
- KMSELDI.exe (PID: 5556)
Application was injected by another process
- rundll32.exe (PID: 6988)
SUSPICIOUS
Reads security settings of Internet Explorer
- KMSpico-setup.tmp (PID: 6760)
Reads the date of Windows installation
- KMSpico-setup.tmp (PID: 6760)
- SystemSettings.exe (PID: 6384)
Drops the executable file immediately after the start
- KMSpico-setup.exe (PID: 6740)
- KMSpico-setup.exe (PID: 6836)
- KMSpico-setup.tmp (PID: 6864)
- KMSELDI.exe (PID: 1048)
Executable content was dropped or overwritten
- KMSpico-setup.exe (PID: 6740)
- KMSpico-setup.exe (PID: 6836)
- KMSpico-setup.tmp (PID: 6864)
- KMSELDI.exe (PID: 1048)
Reads the Windows owner or organization settings
- KMSpico-setup.tmp (PID: 6864)
Starts SC.EXE for service management
- cmd.exe (PID: 6980)
Modifies the phishing filter of IE
- KMSpico-setup.tmp (PID: 6864)
Starts CMD.EXE for commands execution
- KMSpico-setup.tmp (PID: 6864)
Executing commands from ".cmd" file
- KMSpico-setup.tmp (PID: 6864)
Process drops legitimate windows executable
- KMSpico-setup.tmp (PID: 6864)
INFO
Create files in a temporary directory
- KMSpico-setup.exe (PID: 6740)
- KMSpico-setup.exe (PID: 6836)
- KMSpico-setup.tmp (PID: 6864)
Reads the computer name
- KMSpico-setup.tmp (PID: 6760)
- KMSpico-setup.tmp (PID: 6864)
- KMSELDI.exe (PID: 1048)
- AutoPico.exe (PID: 7052)
- KMSELDI.exe (PID: 5556)
- SystemSettings.exe (PID: 6384)
Process checks computer location settings
- KMSpico-setup.tmp (PID: 6760)
Checks supported languages
- KMSpico-setup.tmp (PID: 6760)
- KMSpico-setup.exe (PID: 6740)
- KMSpico-setup.exe (PID: 6836)
- KMSpico-setup.tmp (PID: 6864)
- UninsHs.exe (PID: 6892)
- KMSELDI.exe (PID: 1048)
- SECOH-QAD.exe (PID: 2728)
- KMSELDI.exe (PID: 5556)
- AutoPico.exe (PID: 7052)
- SystemSettings.exe (PID: 6384)
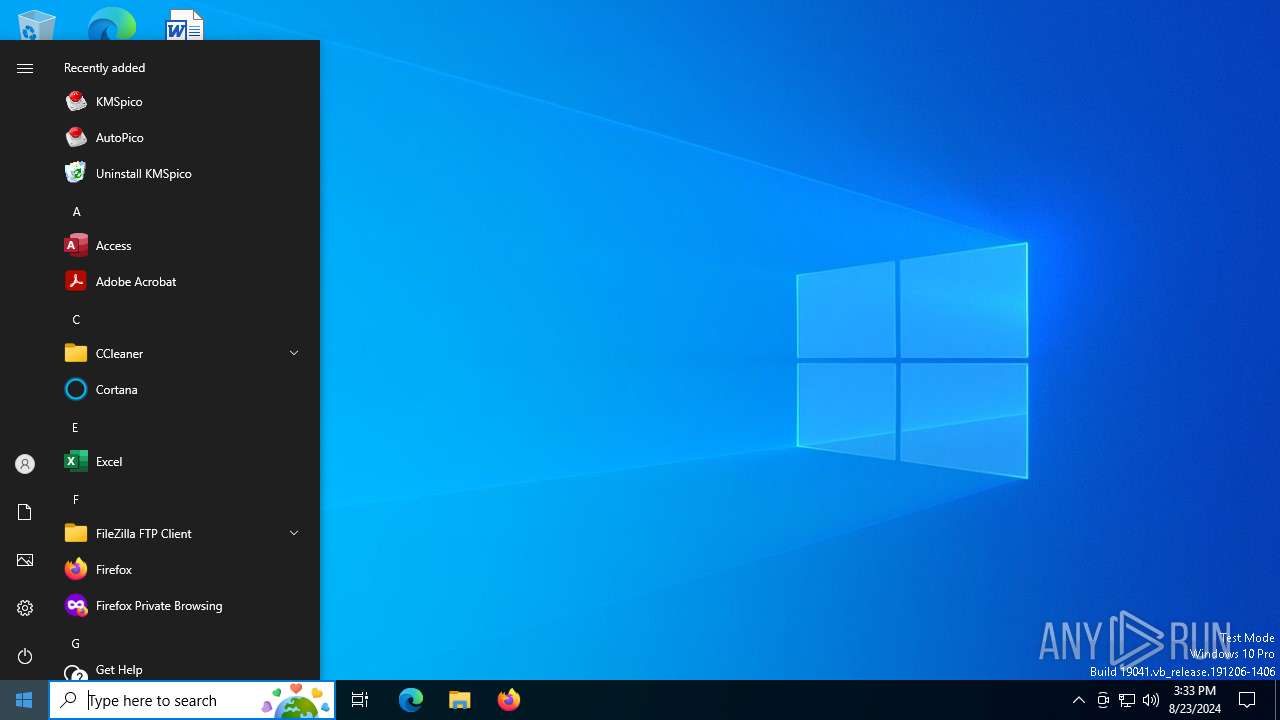
Creates files in the program directory
- KMSpico-setup.tmp (PID: 6864)
- AutoPico.exe (PID: 7052)
- KMSELDI.exe (PID: 1048)
- KMSELDI.exe (PID: 5556)
Creates a software uninstall entry
- KMSpico-setup.tmp (PID: 6864)
Reads the machine GUID from the registry
- KMSELDI.exe (PID: 1048)
- AutoPico.exe (PID: 7052)
- KMSELDI.exe (PID: 5556)
- SystemSettings.exe (PID: 6384)
Reads product name
- KMSELDI.exe (PID: 1048)
- AutoPico.exe (PID: 7052)
- KMSELDI.exe (PID: 5556)
Reads Microsoft Office registry keys
- KMSELDI.exe (PID: 1048)
- AutoPico.exe (PID: 7052)
- KMSELDI.exe (PID: 5556)
Reads Environment values
- AutoPico.exe (PID: 7052)
- KMSELDI.exe (PID: 1048)
- KMSELDI.exe (PID: 5556)
Manual execution by a user
- KMSELDI.exe (PID: 5160)
- KMSELDI.exe (PID: 5556)
Reads the software policy settings
- SystemSettings.exe (PID: 6384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (71.1) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (9.1) |
| .scr | | | Windows screen saver (8.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.2) |
| .exe | | | Win32 Executable (generic) (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 40448 |
| InitializedDataSize: | 27648 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa5f8 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 10.2.0.0 |
| ProductVersionNumber: | 10.2.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | KMSpico Setup |
| FileVersion: | 10.2.0 |
| LegalCopyright: | ByELDI |
| ProductName: | KMSpico |
| ProductVersion: | 10.2.0 |
Total processes
160
Monitored processes
19
Malicious processes
4
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 872 | SCHTASKS /Create /TN "AutoPico Daily Restart" /TR "'C:\Program Files\KMSpico\AutoPico.exe' /silent" /SC DAILY /ST 23:59:59 /RU "NT AUTHORITY\SYSTEM" /RL Highest /F | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1044 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | SECOH-QAD.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
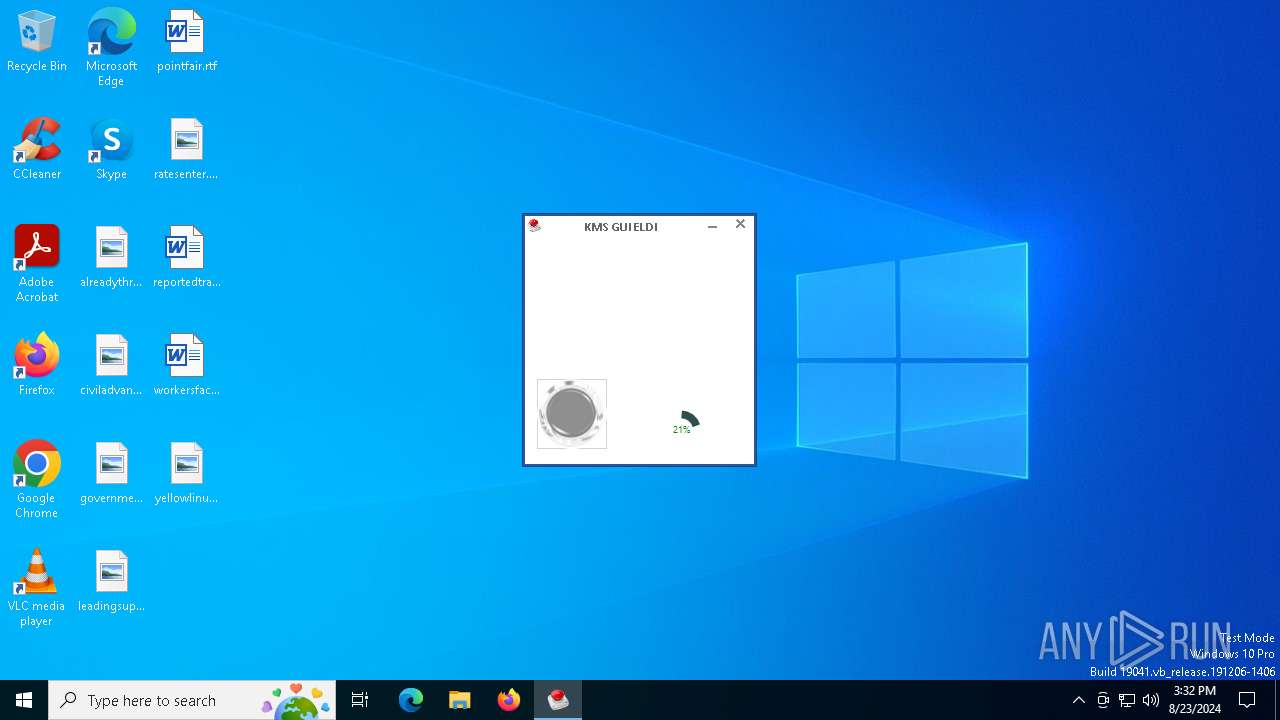
| 1048 | "C:\Program Files\KMSpico\KMSELDI.exe" /silent /backup | C:\Program Files\KMSpico\KMSELDI.exe | KMSpico-setup.tmp | ||||||||||||
User: admin Company: @ByELDI Integrity Level: HIGH Description: KMS GUI ELDI Exit code: 4294967295 Version: 37.1.0.0 Modules
| |||||||||||||||
| 1636 | sc create "Service KMSELDI" binPath= "C:\Program Files\KMSpico\Service_KMS.exe" type= own error= normal start= auto DisplayName= "Service KMSELDI" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2728 | C:\WINDOWS\SECOH-QAD.exe C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\SECOH-QAD.exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Integrity Level: SYSTEM Exit code: 4294967295 Modules
| |||||||||||||||
| 5160 | "C:\Program Files\KMSpico\KMSELDI.exe" | C:\Program Files\KMSpico\KMSELDI.exe | — | explorer.exe | |||||||||||
User: admin Company: @ByELDI Integrity Level: MEDIUM Description: KMS GUI ELDI Exit code: 3221226540 Version: 37.1.0.0 Modules
| |||||||||||||||
| 5556 | "C:\Program Files\KMSpico\KMSELDI.exe" | C:\Program Files\KMSpico\KMSELDI.exe | explorer.exe | ||||||||||||
User: admin Company: @ByELDI Integrity Level: HIGH Description: KMS GUI ELDI Exit code: 0 Version: 37.1.0.0 Modules
| |||||||||||||||
| 6384 | "C:\Windows\ImmersiveControlPanel\SystemSettings.exe" -ServerName:microsoft.windows.immersivecontrolpanel | C:\Windows\ImmersiveControlPanel\SystemSettings.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Settings Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6740 | "C:\Users\admin\AppData\Local\Temp\KMSpico-setup.exe" | C:\Users\admin\AppData\Local\Temp\KMSpico-setup.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: KMSpico Setup Exit code: 0 Version: 10.2.0 Modules
| |||||||||||||||
| 6760 | "C:\Users\admin\AppData\Local\Temp\is-DEIT5.tmp\KMSpico-setup.tmp" /SL5="$6025A,2952592,69120,C:\Users\admin\AppData\Local\Temp\KMSpico-setup.exe" | C:\Users\admin\AppData\Local\Temp\is-DEIT5.tmp\KMSpico-setup.tmp | — | KMSpico-setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
Total events
20 295
Read events
20 125
Write events
157
Delete events
13
Modification events
| (PID) Process: | (6864) KMSpico-setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: D01A00008F94759171F5DA01 | |||
| (PID) Process: | (6864) KMSpico-setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 9A16DD8F33500A2D0A430E84D40FA0553D65A177857282CDCFB09DF59F4B58C9 | |||
| (PID) Process: | (6864) KMSpico-setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6864) KMSpico-setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\KMSpico\AutoPico.exe | |||
| (PID) Process: | (6864) KMSpico-setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 21CD5593EC6FF27C8F28F463A9F0803AB9BFBF9EF5BF08A400DA3A64A39ABA39 | |||
| (PID) Process: | (6864) KMSpico-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | delete value | Name: | EnableSmartScreen |
Value: | |||
| (PID) Process: | (6864) KMSpico-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | EnableSmartScreen |
Value: 0 | |||
| (PID) Process: | (6864) KMSpico-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | delete value | Name: | SmartScreenEnabled |
Value: Off | |||
| (PID) Process: | (6864) KMSpico-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SmartScreenEnabled |
Value: Off | |||
| (PID) Process: | (6864) KMSpico-setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\PhishingFilter |
| Operation: | delete value | Name: | EnabledV9 |
Value: | |||
Executable files
26
Suspicious files
38
Text files
716
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6864 | KMSpico-setup.tmp | C:\Program Files\KMSpico\is-UV2UT.tmp | executable | |
MD5:30C7E8E918403B9247315249A8842CE5 | SHA256:6D4FA6727CA952B7B44FA9F3538D84B64E06C76908C76FADE7846532A7115A49 | |||
| 6864 | KMSpico-setup.tmp | C:\Program Files\KMSpico\is-52A10.tmp | executable | |
MD5:CFE1C391464C446099A5EB33276F6D57 | SHA256:4A714D98CE40F5F3577C306A66CB4A6B1FF3FD01047C7F4581F8558F0BCDF5FA | |||
| 6864 | KMSpico-setup.tmp | C:\Users\admin\AppData\Local\Temp\is-9HGKB.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 6836 | KMSpico-setup.exe | C:\Users\admin\AppData\Local\Temp\is-RUO8U.tmp\KMSpico-setup.tmp | executable | |
MD5:1778C1F66FF205875A6435A33229AB3C | SHA256:95C06ACAC4FE4598840E5556F9613D43AA1039C52DAC64536F59E45A70F79DA6 | |||
| 6864 | KMSpico-setup.tmp | C:\Windows\System32\Vestris.ResourceLib.dll | executable | |
MD5:3D733144477CADCF77009EF614413630 | SHA256:392D73617FD0A55218261572ECE2F50301E0CFA29B5ED24C3F692130AA406AF3 | |||
| 6864 | KMSpico-setup.tmp | C:\Windows\System32\is-68D65.tmp | executable | |
MD5:3D733144477CADCF77009EF614413630 | SHA256:392D73617FD0A55218261572ECE2F50301E0CFA29B5ED24C3F692130AA406AF3 | |||
| 6864 | KMSpico-setup.tmp | C:\Program Files\KMSpico\unins000.exe | executable | |
MD5:30C7E8E918403B9247315249A8842CE5 | SHA256:6D4FA6727CA952B7B44FA9F3538D84B64E06C76908C76FADE7846532A7115A49 | |||
| 6864 | KMSpico-setup.tmp | C:\Program Files\KMSpico\Vestris.ResourceLib.dll | executable | |
MD5:3D733144477CADCF77009EF614413630 | SHA256:392D73617FD0A55218261572ECE2F50301E0CFA29B5ED24C3F692130AA406AF3 | |||
| 6864 | KMSpico-setup.tmp | C:\Program Files\KMSpico\DevComponents.DotNetBar2.dll | executable | |
MD5:1397B23F30681F97049DF61F94F54D05 | SHA256:FA76151A783250014AC8FA55D4C833100A623FCAD1D6E2DDADCDE259F5709609 | |||
| 6864 | KMSpico-setup.tmp | C:\Program Files\KMSpico\is-QJHOD.tmp | executable | |
MD5:3D733144477CADCF77009EF614413630 | SHA256:392D73617FD0A55218261572ECE2F50301E0CFA29B5ED24C3F692130AA406AF3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
56
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5744 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5744 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5744 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7096 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6804 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1028 | SystemSettings.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2368 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3916 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5744 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5744 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
7096 | backgroundTaskHost.exe | 20.31.169.57:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
7096 | backgroundTaskHost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6804 | SIHClient.exe | 20.114.59.183:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
3.pool.ntp.org |
| whitelisted |