| File name: | MyGov (1).apk |
| Full analysis: | https://app.any.run/tasks/060a659b-9a9e-4b7e-b680-1d8751ec7d0e |
| Verdict: | Malicious activity |
| Analysis date: | March 20, 2025, 09:13:57 |
| OS: | Android 14 |
| MIME: | application/vnd.android.package-archive |
| File info: | Android package (APK), with AndroidManifest.xml, with APK Signing Block |
| MD5: | 91090FE77C0DFDBB1C0E2F7C86B23D06 |
| SHA1: | EAF3C9C6D4B1245E1F8F151865AEF2991129EF4C |
| SHA256: | 64BAA5606A1749CE0822F41AA8E564D574CFB9AC8F58314B687A0B80C7870DB7 |
| SSDEEP: | 98304:Ld2ZrssFejJwj97NMmrszlXqqe8ntp4T6irxfpAGDSvl5NWck0AG3AwT4asCpWjR:NTch |
MALICIOUS
No malicious indicators.SUSPICIOUS
Retrieves installed applications on device
- app_process64 (PID: 2214)
Accesses system-level resources
- app_process64 (PID: 2214)
Collects data about the device's environment (JVM version)
- app_process64 (PID: 2214)
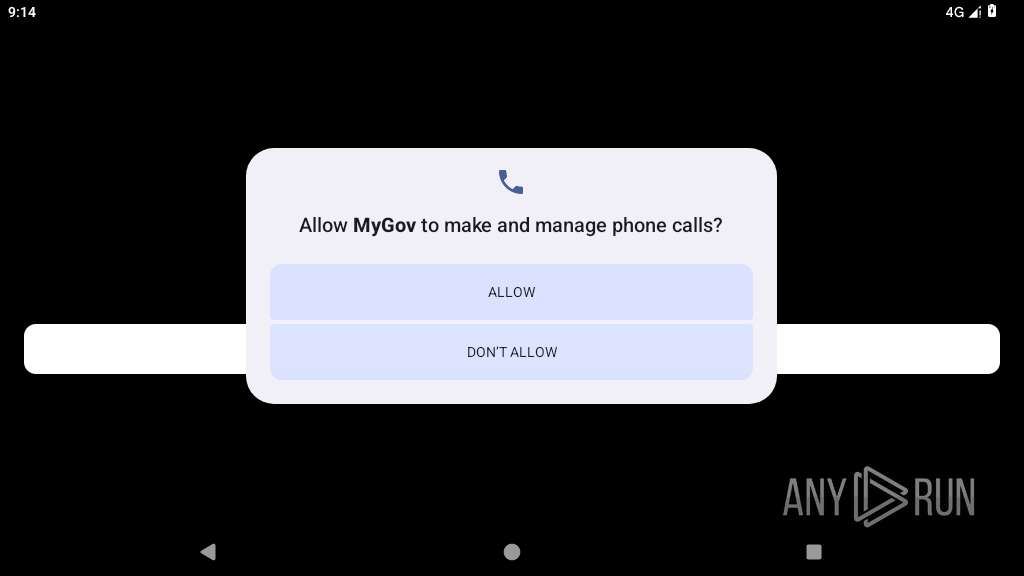
Reads messages from SMS inbox
- app_process64 (PID: 2214)
Retrieves the MCC and MNC of the SIM card operator
- app_process64 (PID: 2214)
Updates data in the storage of application settings (SharedPreferences)
- app_process64 (PID: 2214)
Retrieves the ISO country code of the current SIM card
- app_process64 (PID: 2214)
Connects to unusual port
- app_process64 (PID: 2214)
INFO
Gets the display metrics associated with the device's screen
- app_process64 (PID: 2214)
Gets file name without full path
- app_process64 (PID: 2214)
Dynamically loads a class in Java
- app_process64 (PID: 2214)
Dynamically registers broadcast event listeners
- app_process64 (PID: 2214)
Dynamically inspects or modifies classes, methods, and fields at runtime
- app_process64 (PID: 2214)
Retrieves data from storage of application settings (SharedPreferences)
- app_process64 (PID: 2214)
Verifies presence of SIM card
- app_process64 (PID: 2214)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Unknown (26000) |
| ZipModifyDate: | 2025:03:19 16:48:46 |
| ZipCRC: | 0xfdb83f57 |
| ZipCompressedSize: | 3298 |
| ZipUncompressedSize: | 9424 |
| ZipFileName: | AndroidManifest.xml |
Total processes
125
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 344 | /system/bin/netd | /system/bin/netd | init | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 2214 | com.testtest.qwizzserial | /system/bin/app_process64 | app_process64 | |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
Total events
0
Read events
0
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2214 | app_process64 | /storage/emulated/0/Android/data/com.testtest.qwizzserial/files/uzbbcdda77fd4d4f1798728623ff34f6f2_sms_messages.zip | — | |
MD5:— | SHA256:— | |||
| 2214 | app_process64 | /data/data/com.testtest.qwizzserial/shared_prefs/mainPrefs.xml | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
31
DNS requests
11
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
827 | app_process64 | GET | 404 | 142.250.185.228:80 | http://www.google.com/gen_204 | unknown | — | — | whitelisted |
827 | app_process64 | GET | 404 | 172.217.16.195:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
827 | app_process64 | GET | 404 | 172.217.16.195:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
827 | app_process64 | GET | 404 | 142.250.185.228:80 | http://www.google.com/gen_204 | unknown | — | — | whitelisted |
827 | app_process64 | GET | 404 | 172.217.16.195:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
827 | app_process64 | GET | 404 | 216.239.38.223:80 | http://play.googleapis.com/generate_204 | unknown | — | — | whitelisted |
827 | app_process64 | GET | 404 | 172.217.16.195:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
827 | app_process64 | GET | 404 | 142.250.185.228:80 | http://www.google.com/gen_204 | unknown | — | — | whitelisted |
827 | app_process64 | GET | 404 | 142.250.185.228:80 | http://www.google.com/gen_204 | unknown | — | — | whitelisted |
827 | app_process64 | GET | 404 | 172.217.16.195:80 | http://connectivitycheck.gstatic.com/generate_204 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 8.8.8.8:853 | — | GOOGLE | US | malicious |
448 | mdnsd | 224.0.0.251:5353 | — | — | — | unknown |
344 | netd | 8.8.8.8:443 | — | — | — | malicious |
827 | app_process64 | 142.250.185.228:80 | www.google.com | GOOGLE | US | whitelisted |
827 | app_process64 | 142.250.185.228:443 | www.google.com | GOOGLE | US | whitelisted |
827 | app_process64 | 172.217.16.195:80 | connectivitycheck.gstatic.com | GOOGLE | US | whitelisted |
827 | app_process64 | 216.239.38.223:80 | play.googleapis.com | GOOGLE | US | whitelisted |
2214 | app_process64 | 147.45.44.229:4001 | — | OOO FREEnet Group | RU | unknown |
577 | app_process64 | 216.239.35.12:123 | time.android.com | — | — | whitelisted |
577 | app_process64 | 216.239.35.0:123 | time.android.com | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivitycheck.gstatic.com |
| whitelisted |
www.google.com |
| whitelisted |
google.com |
| whitelisted |
play.googleapis.com |
| whitelisted |
time.android.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
827 | app_process64 | Misc activity | ET INFO Android Device Connectivity Check |
827 | app_process64 | Misc activity | ET INFO Android Device Connectivity Check |
827 | app_process64 | Misc activity | ET INFO Android Device Connectivity Check |
827 | app_process64 | Misc activity | ET INFO Android Device Connectivity Check |
827 | app_process64 | Misc activity | ET INFO Android Device Connectivity Check |
827 | app_process64 | Misc activity | ET INFO Android Device Connectivity Check |
827 | app_process64 | Misc activity | ET INFO Android Device Connectivity Check |