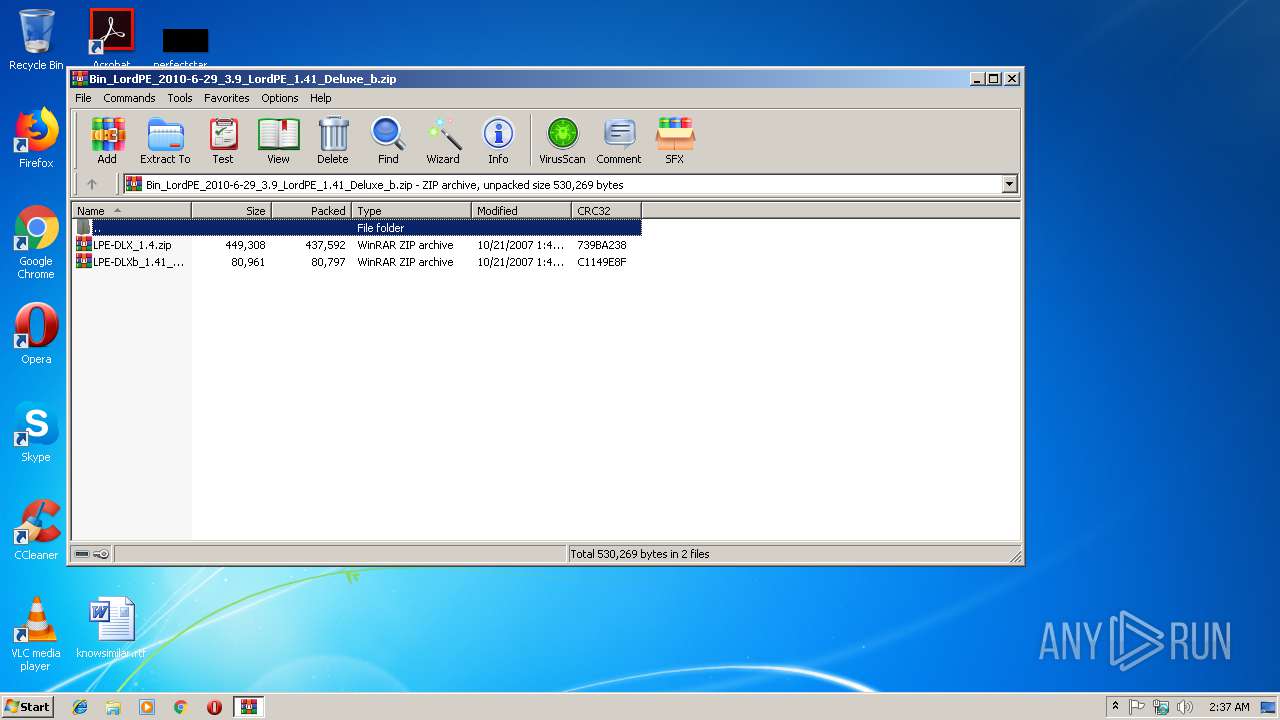
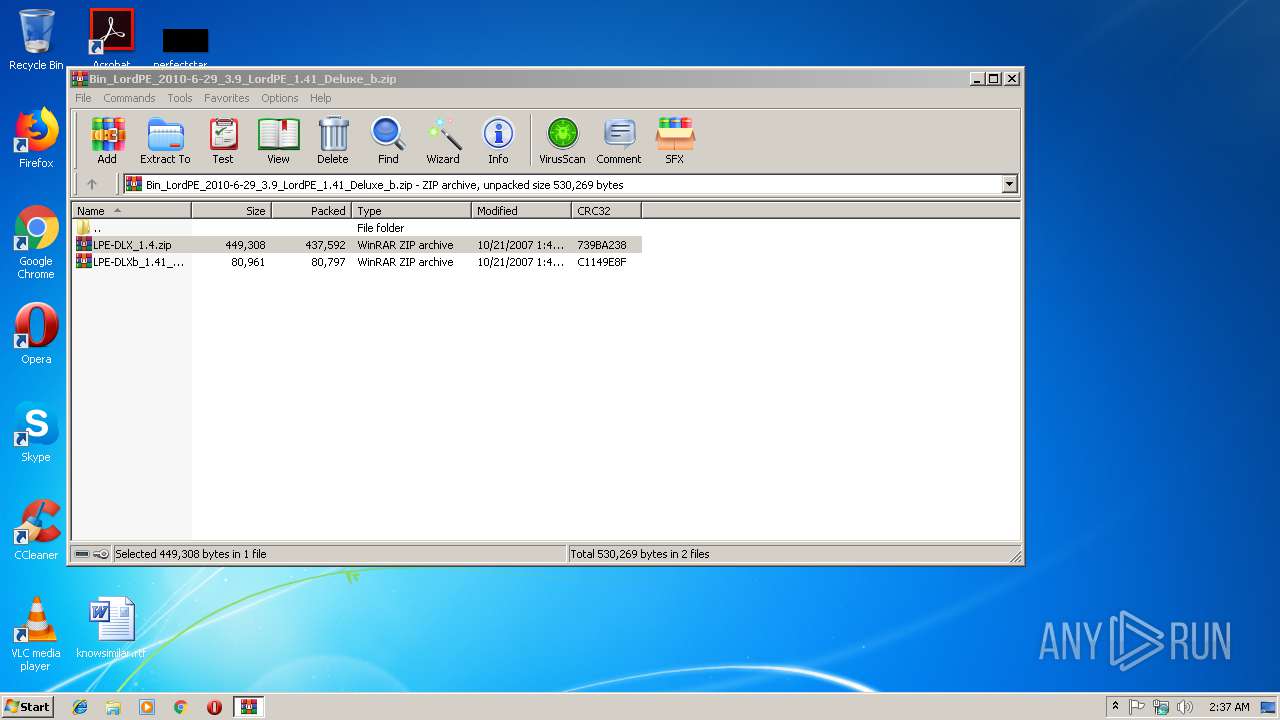
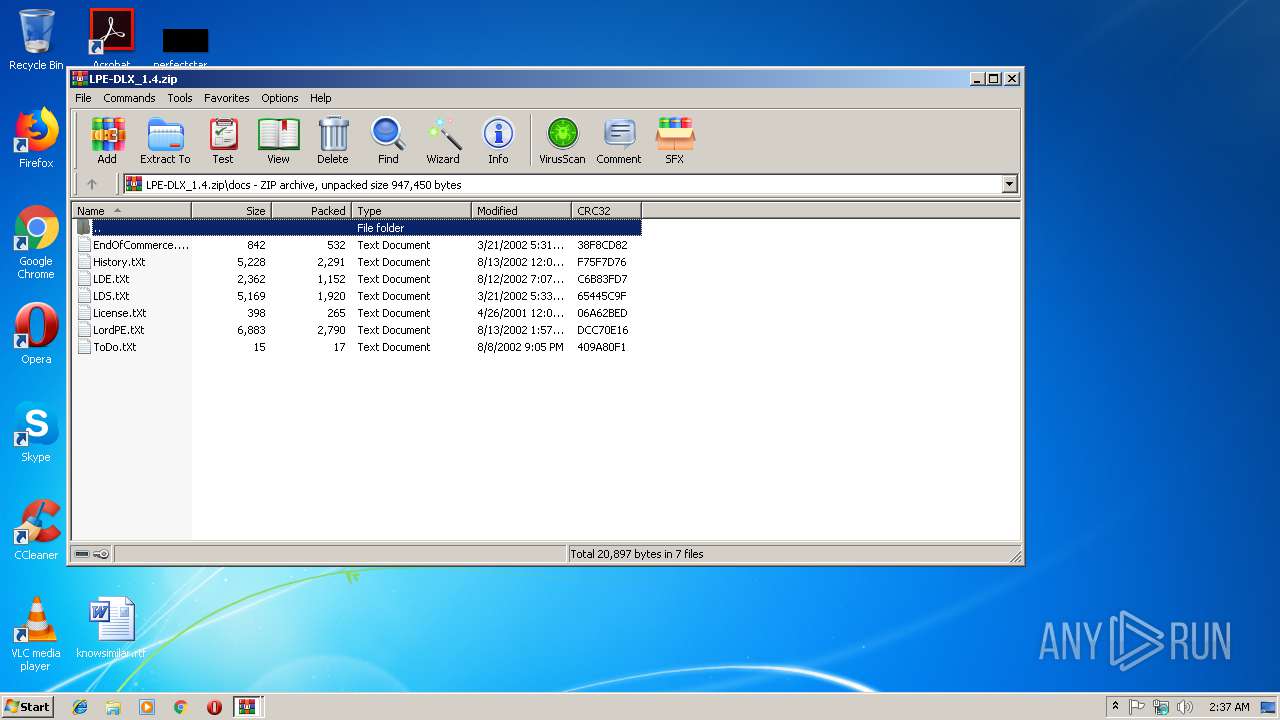
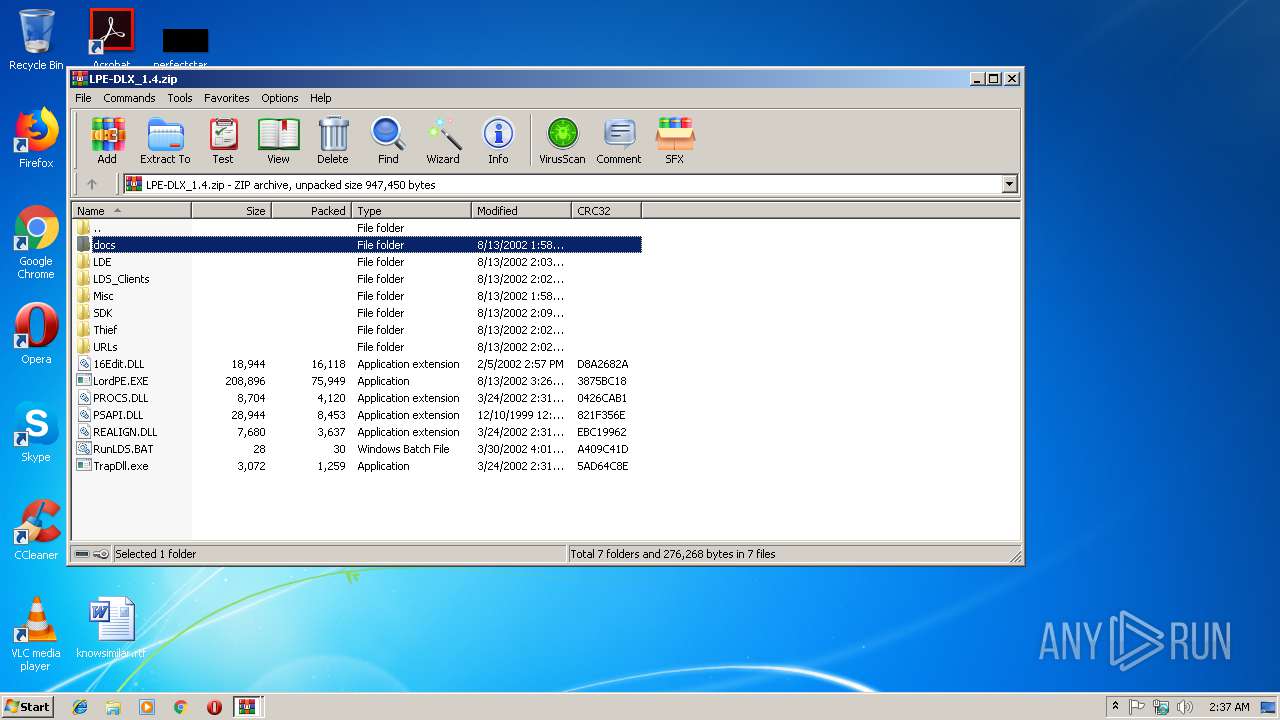
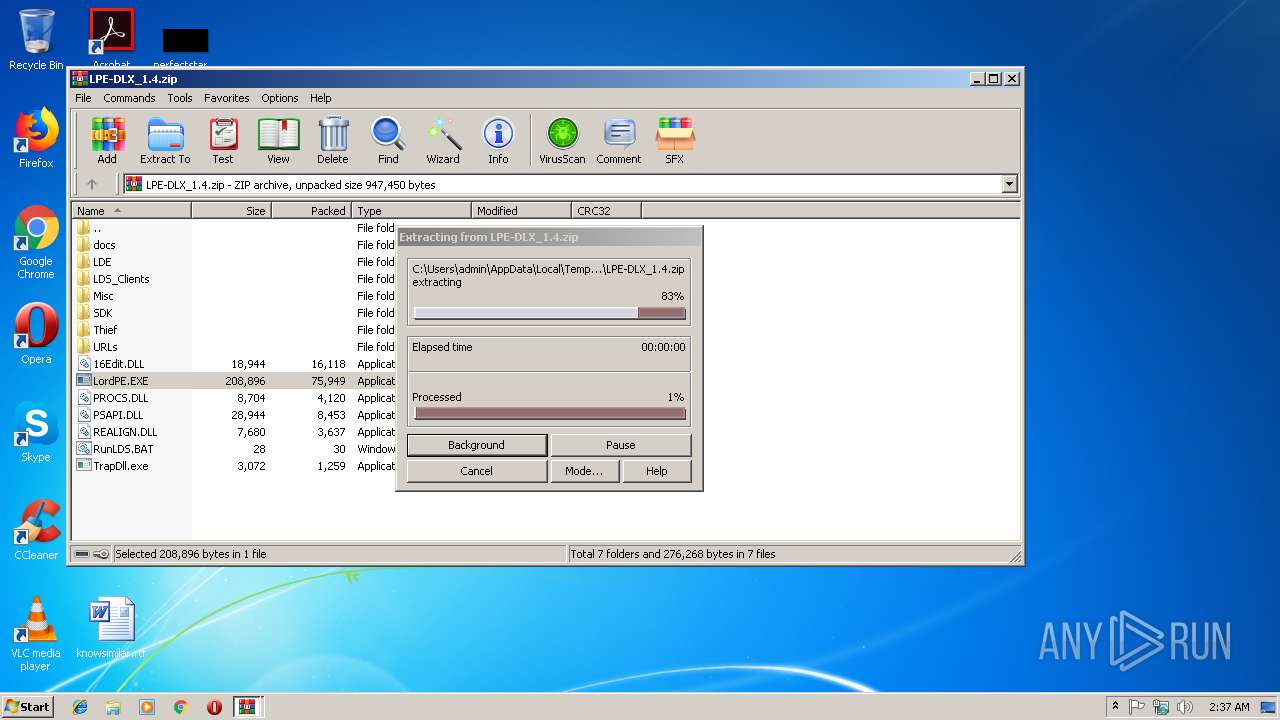
| download: | Bin_LordPE_2010-6-29_3.9_LordPE_1.41_Deluxe_b.zip |
| Full analysis: | https://app.any.run/tasks/63e2f962-2e93-4dec-9bc6-2d1504404af0 |
| Verdict: | Suspicious activity |
| Analysis date: | November 30, 2018, 02:36:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | A00CDB21300D88A7A863ED47F866AED9 |
| SHA1: | 6FED05F3BD80E78CB7F9851006FDFB5D5CADE61A |
| SHA256: | 64A94A6A415BD01AC6AB1DF49B8DCB880EC2CF0F8BFAC4AAAF2423BFD673678D |
| SSDEEP: | 12288:MIajIlgOdPJTHnwsFhF0K3Drt1P38tuUiPagKGkmp:FajItHwecKXt6QUzSp |
MALICIOUS
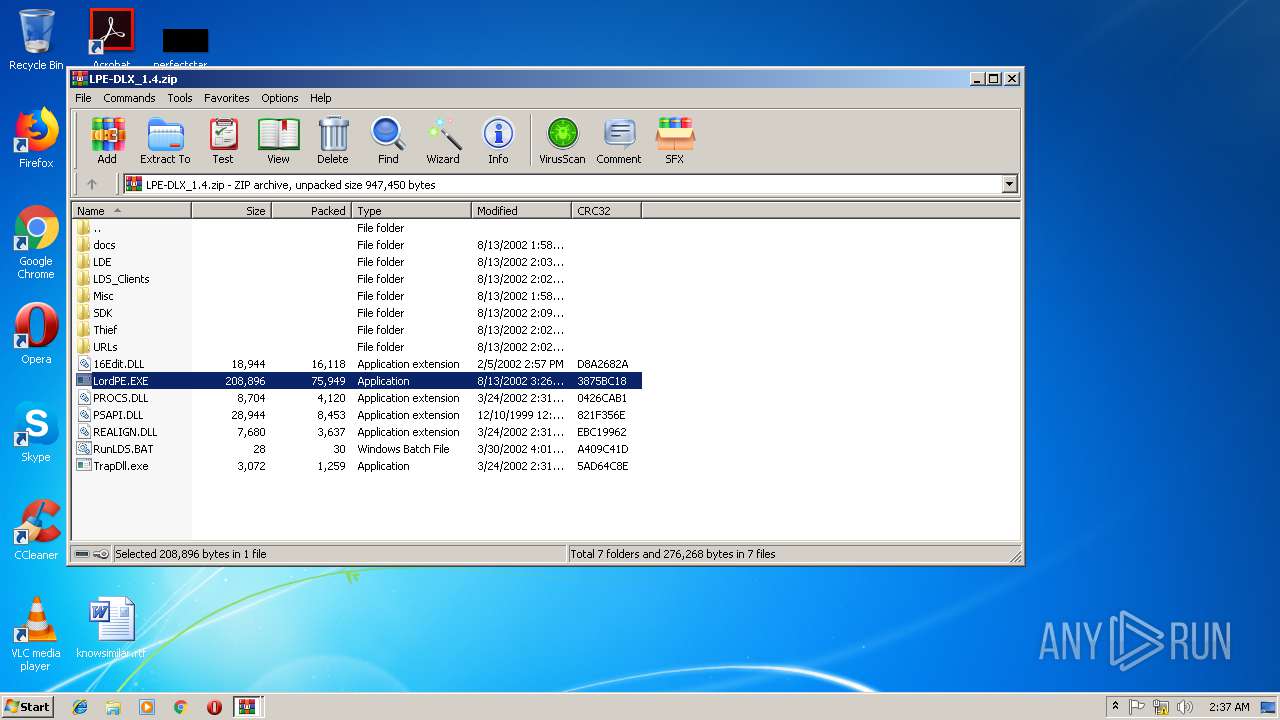
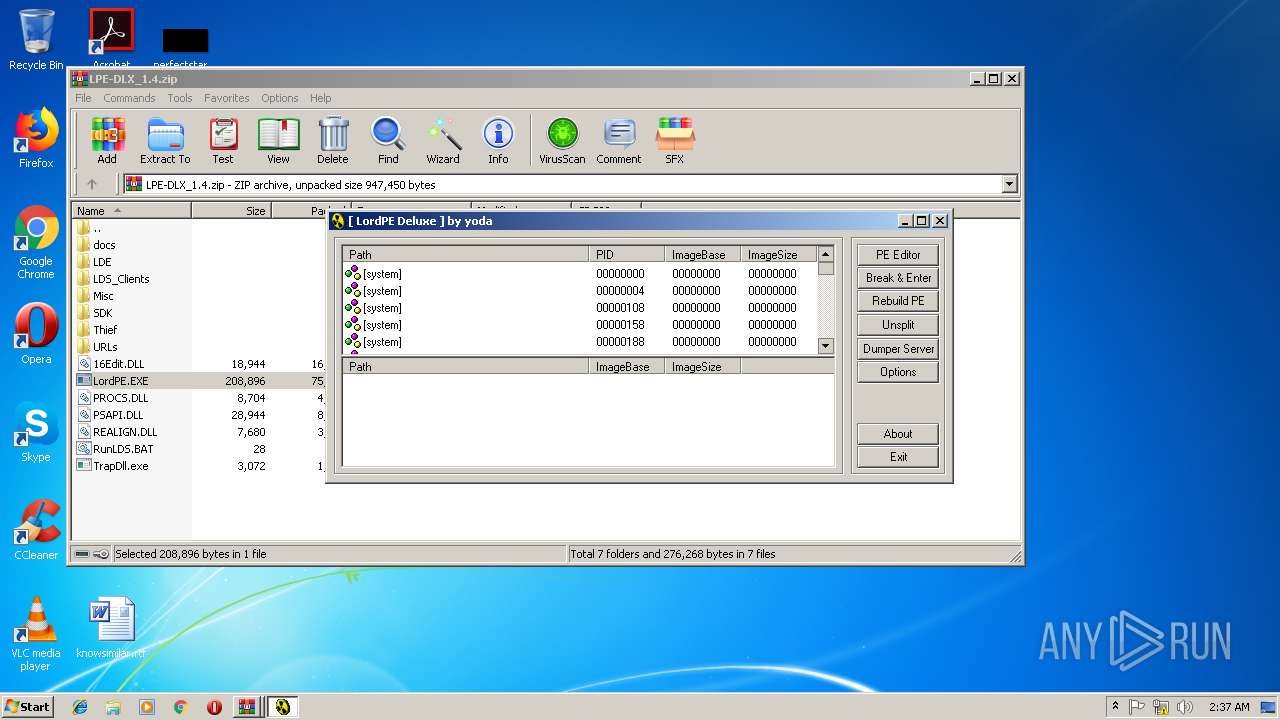
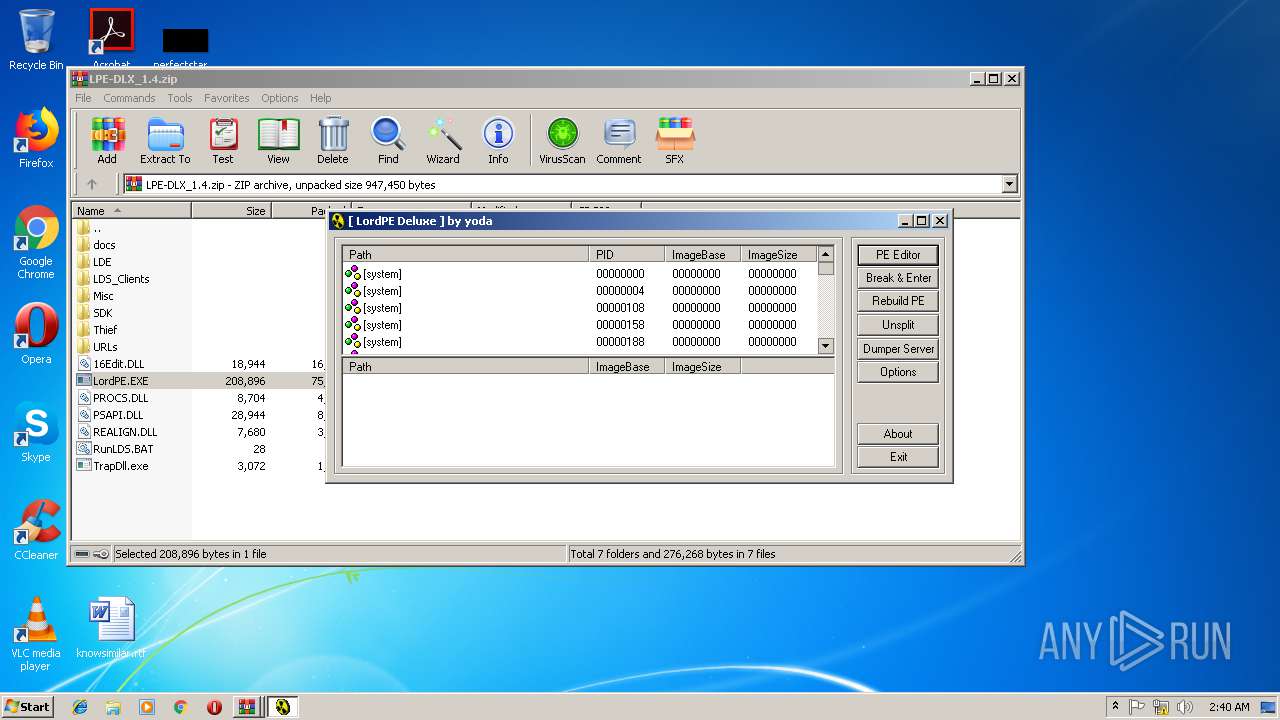
Loads dropped or rewritten executable
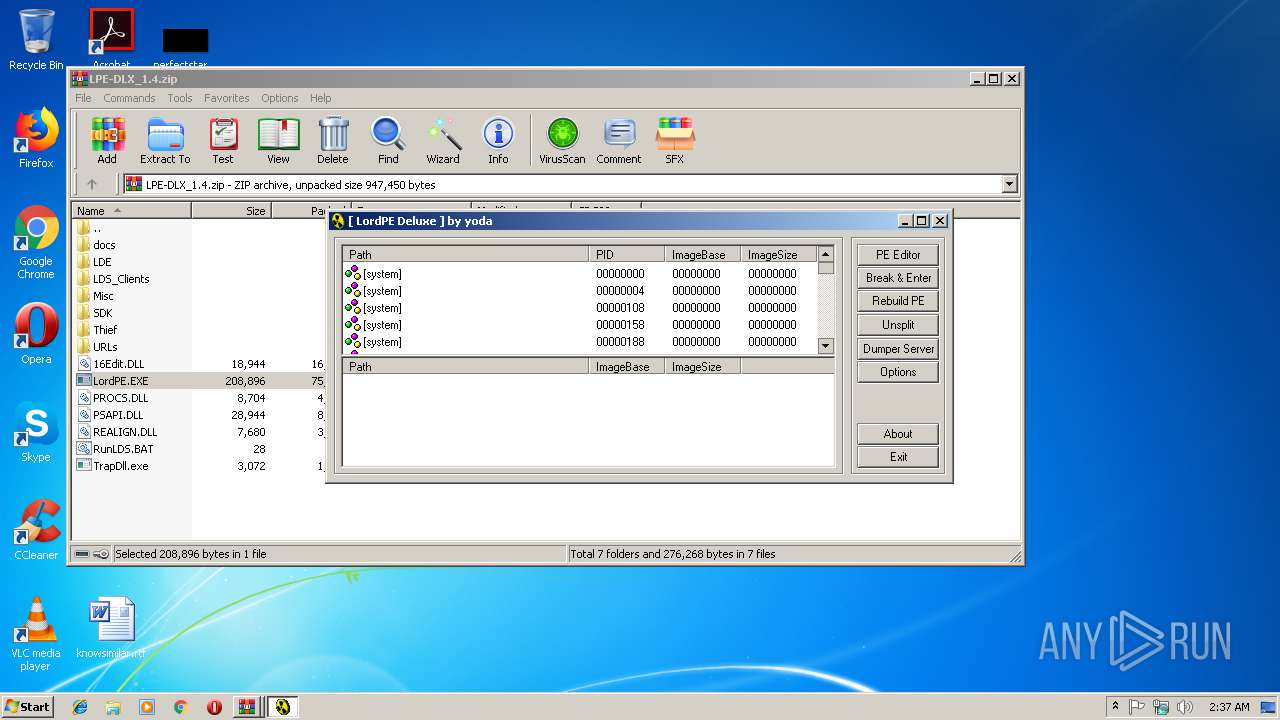
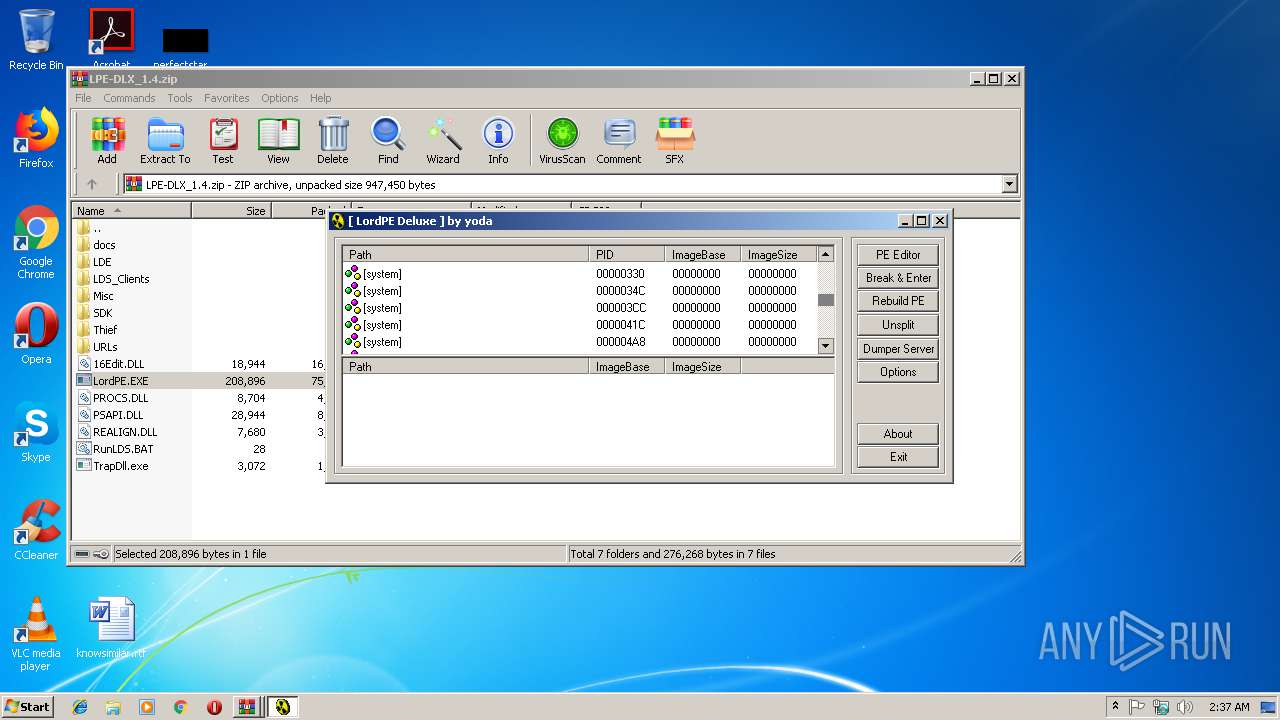
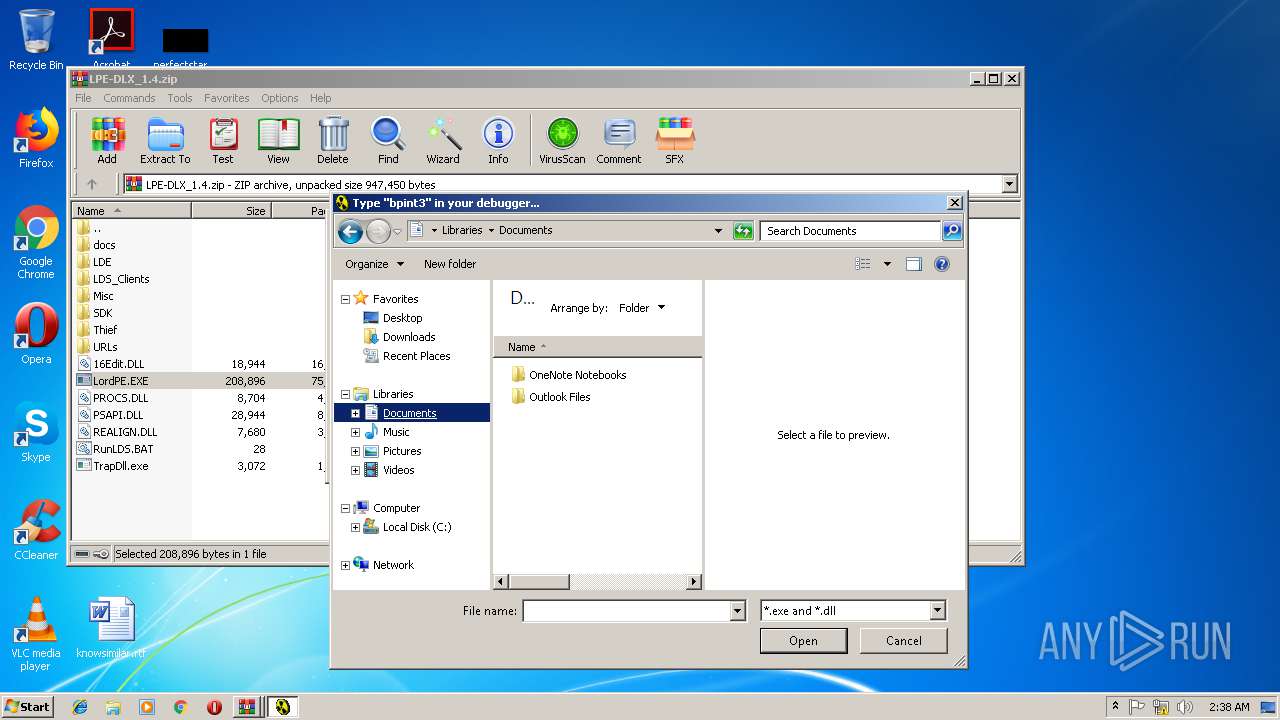
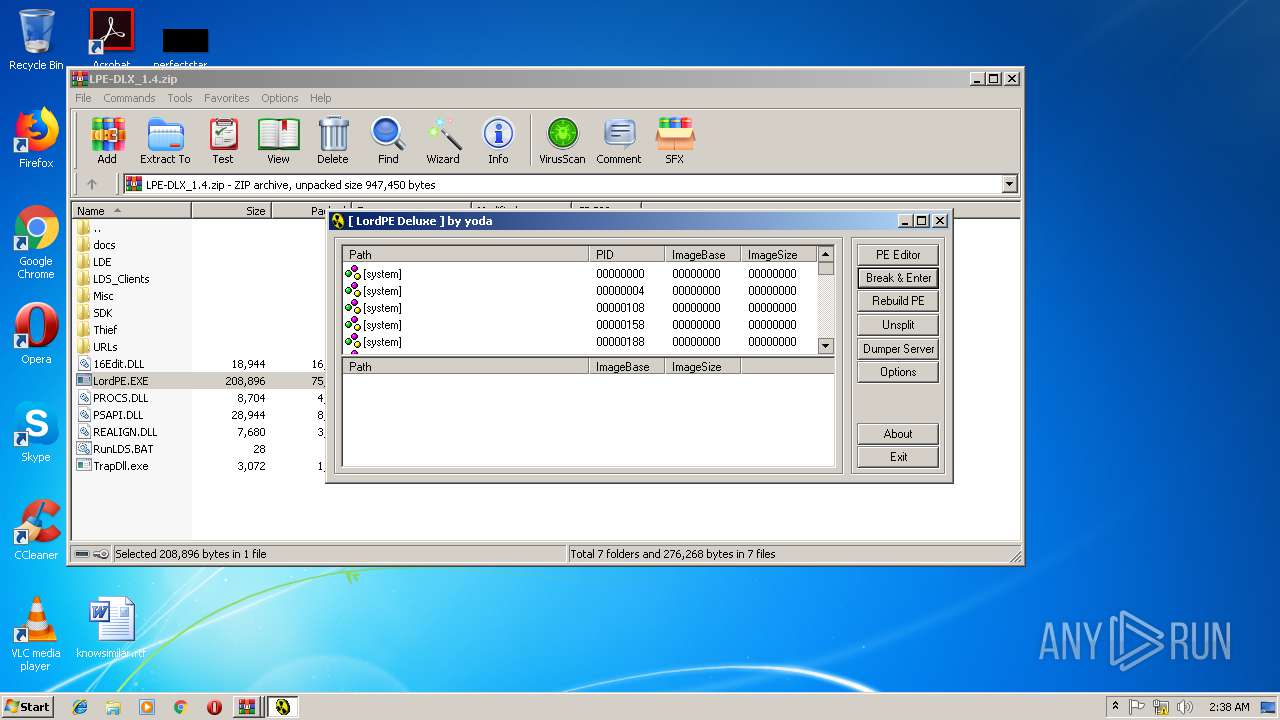
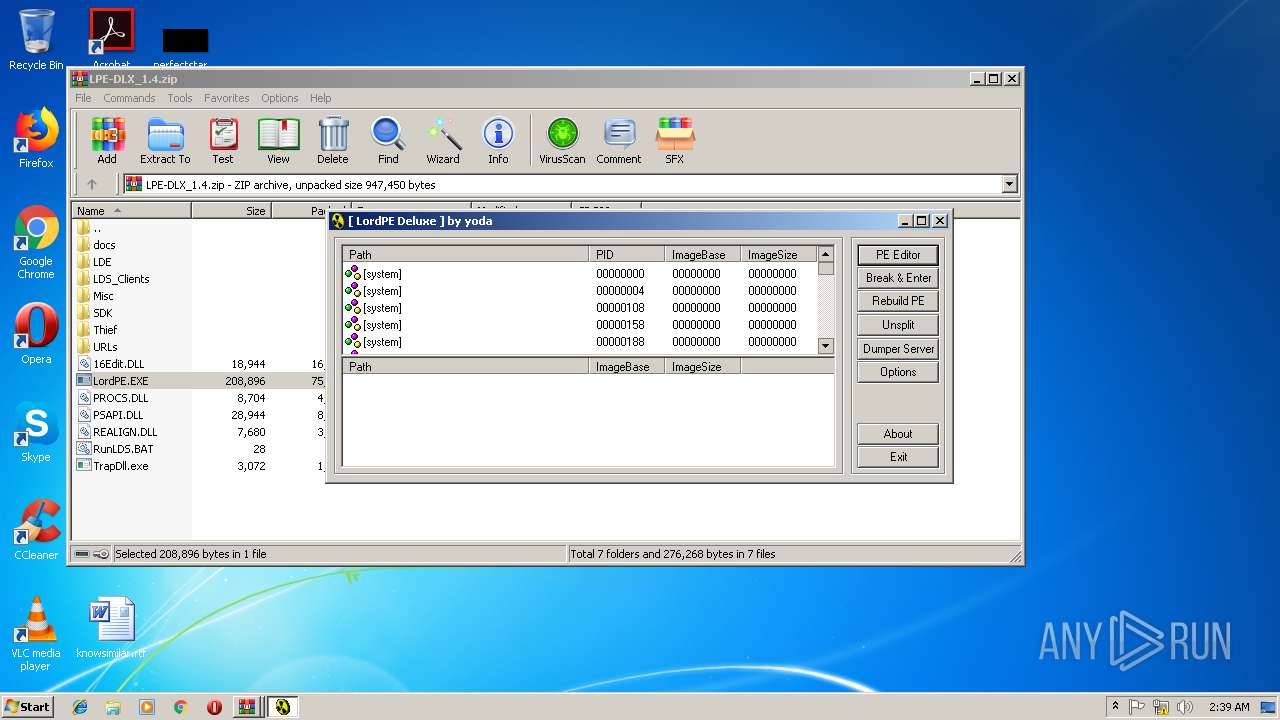
- LordPE.EXE (PID: 2200)
- LordPE.EXE (PID: 2952)
Application was dropped or rewritten from another process
- LordPE.EXE (PID: 2200)
- LordPE.EXE (PID: 2952)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 3448)
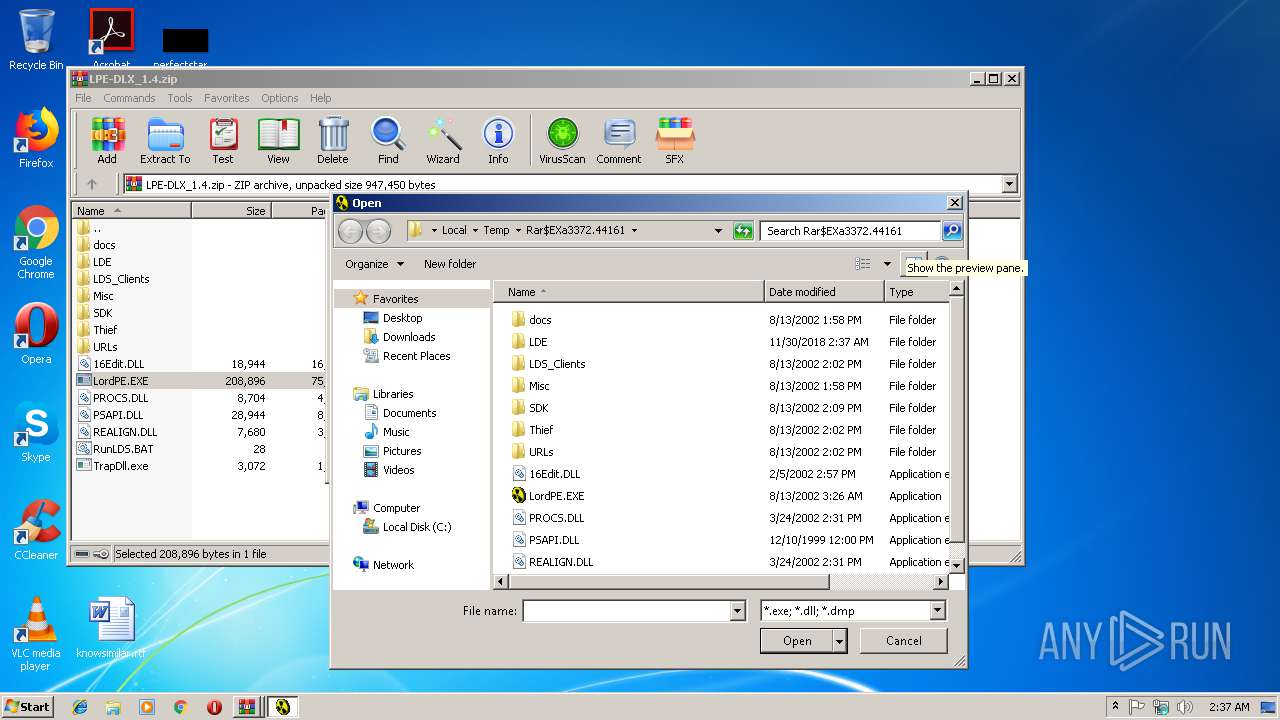
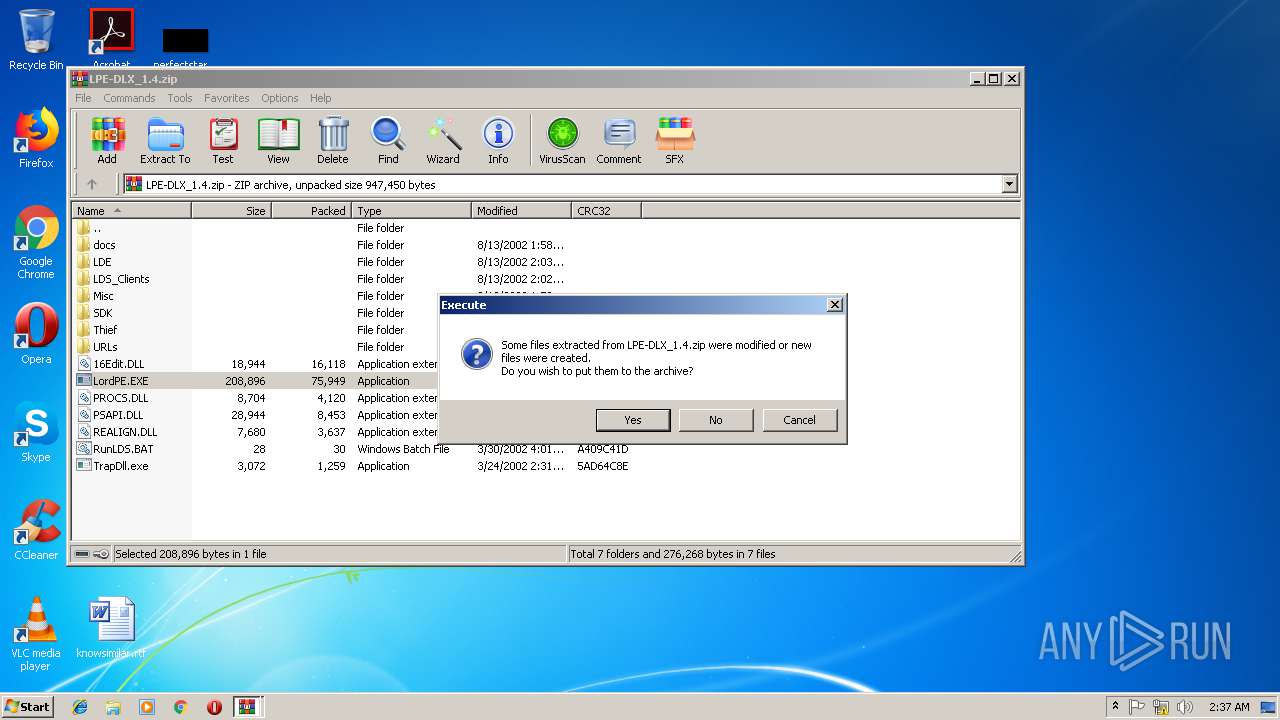
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3372)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3372)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2007:10:21 01:40:24 |
| ZipCRC: | 0x739ba238 |
| ZipCompressedSize: | 437592 |
| ZipUncompressedSize: | 449308 |
| ZipFileName: | LPE-DLX_1.4.zip |
Total processes
35
Monitored processes
4
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
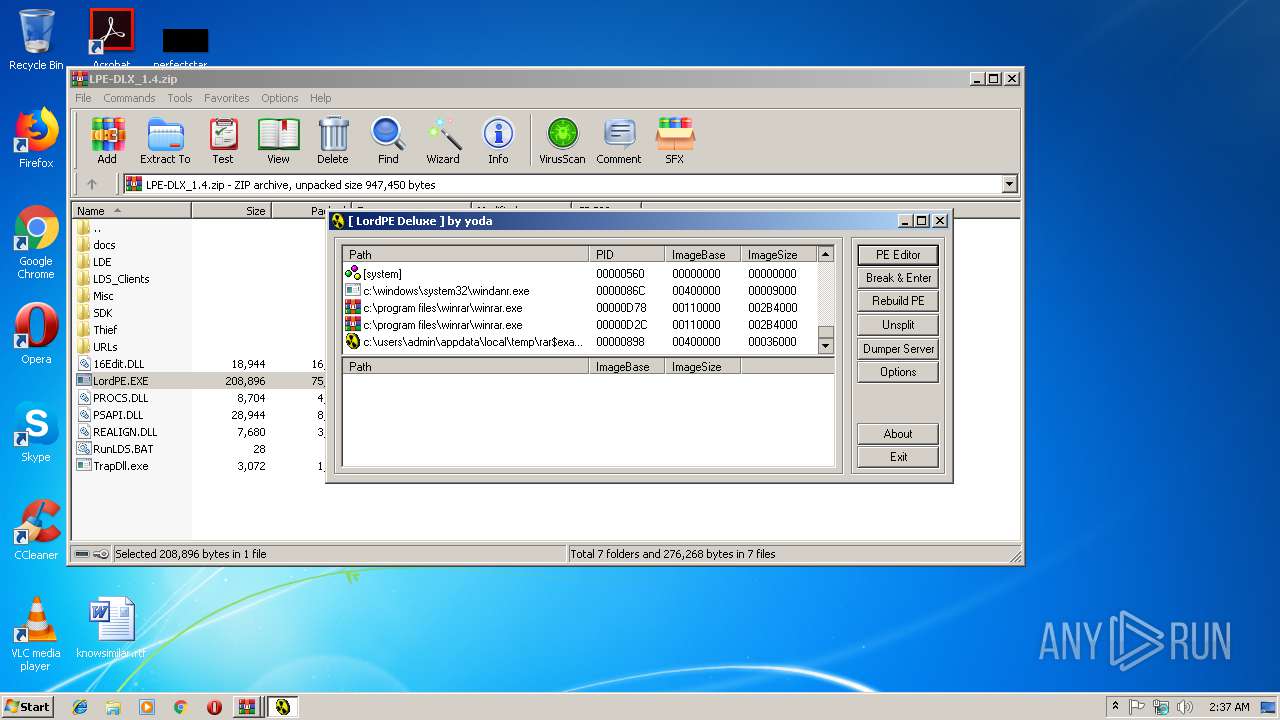
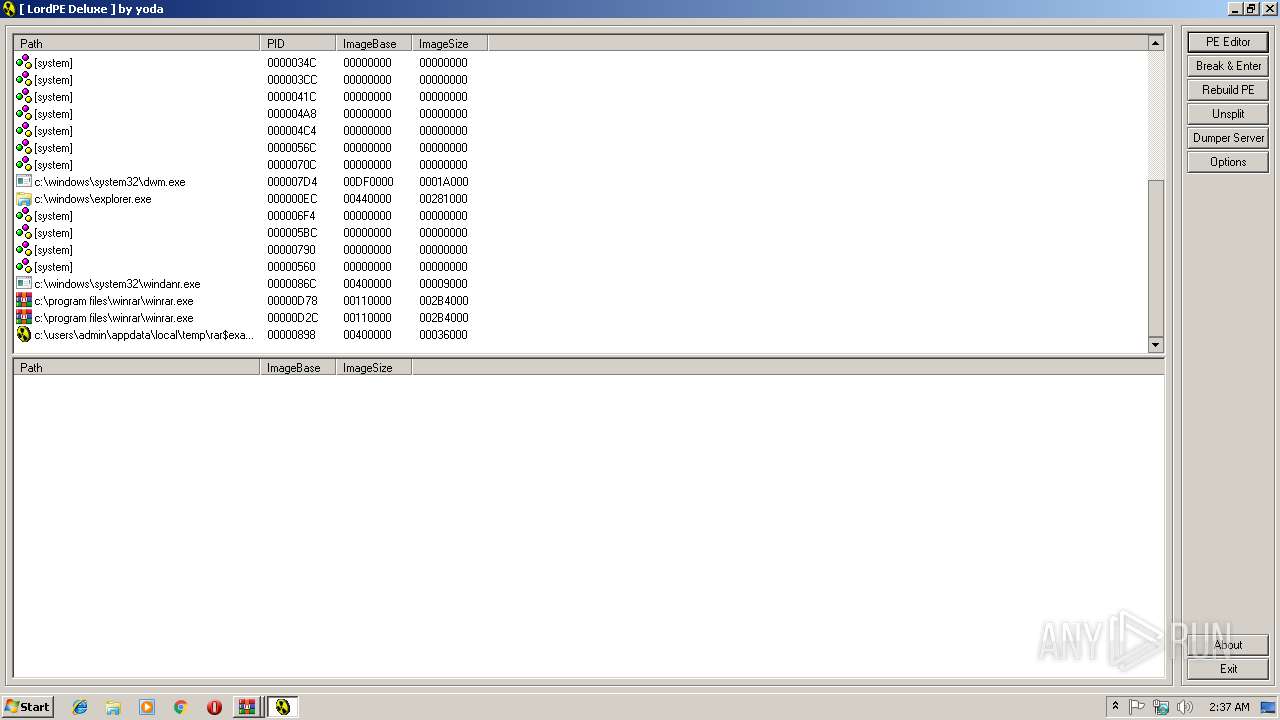
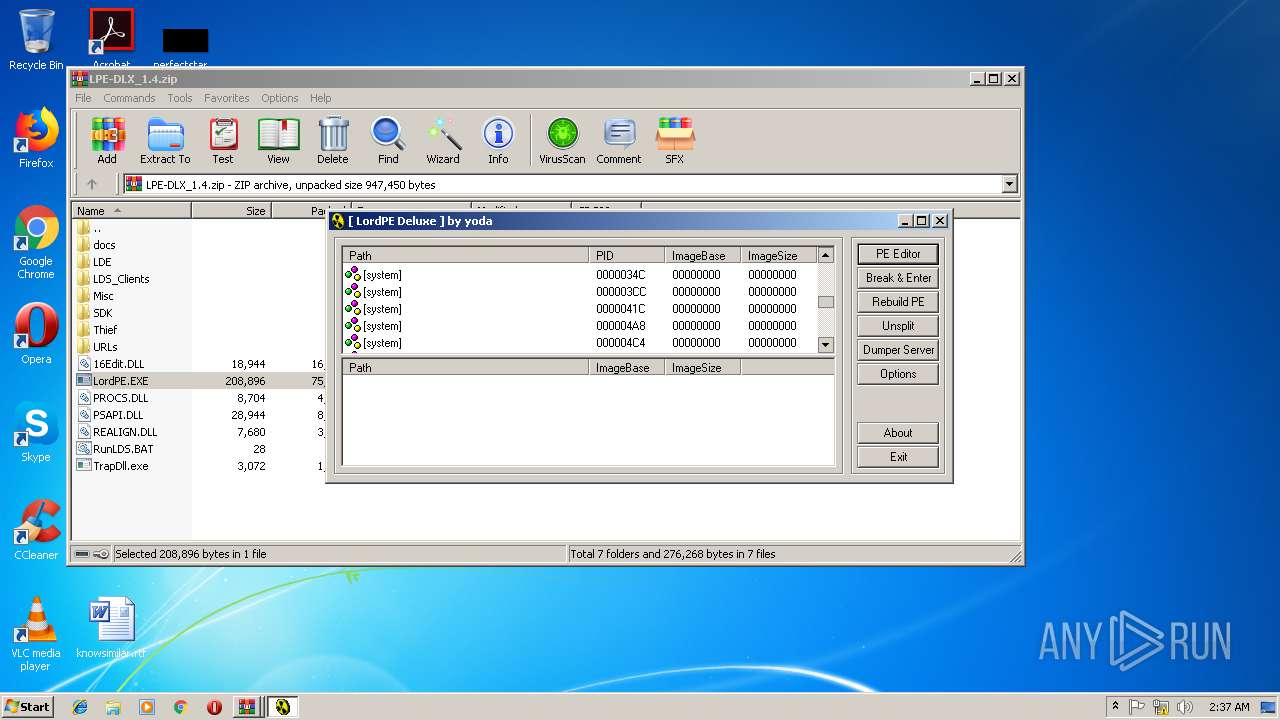
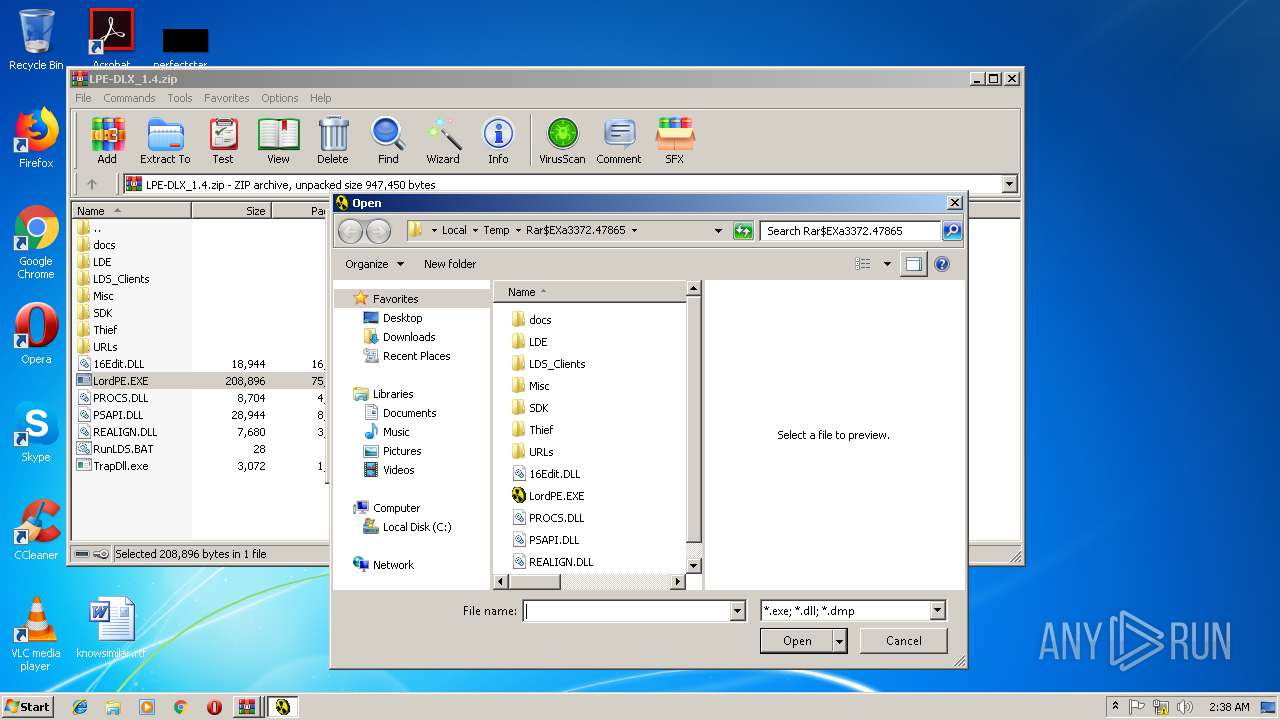
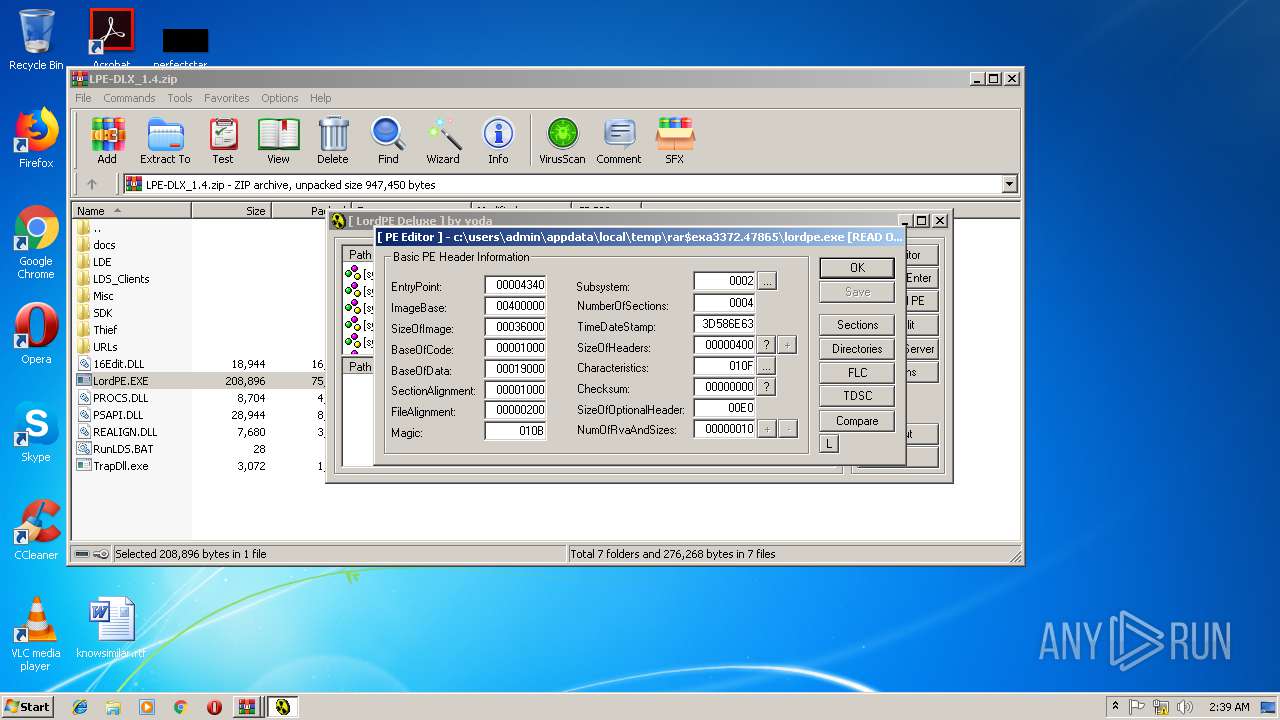
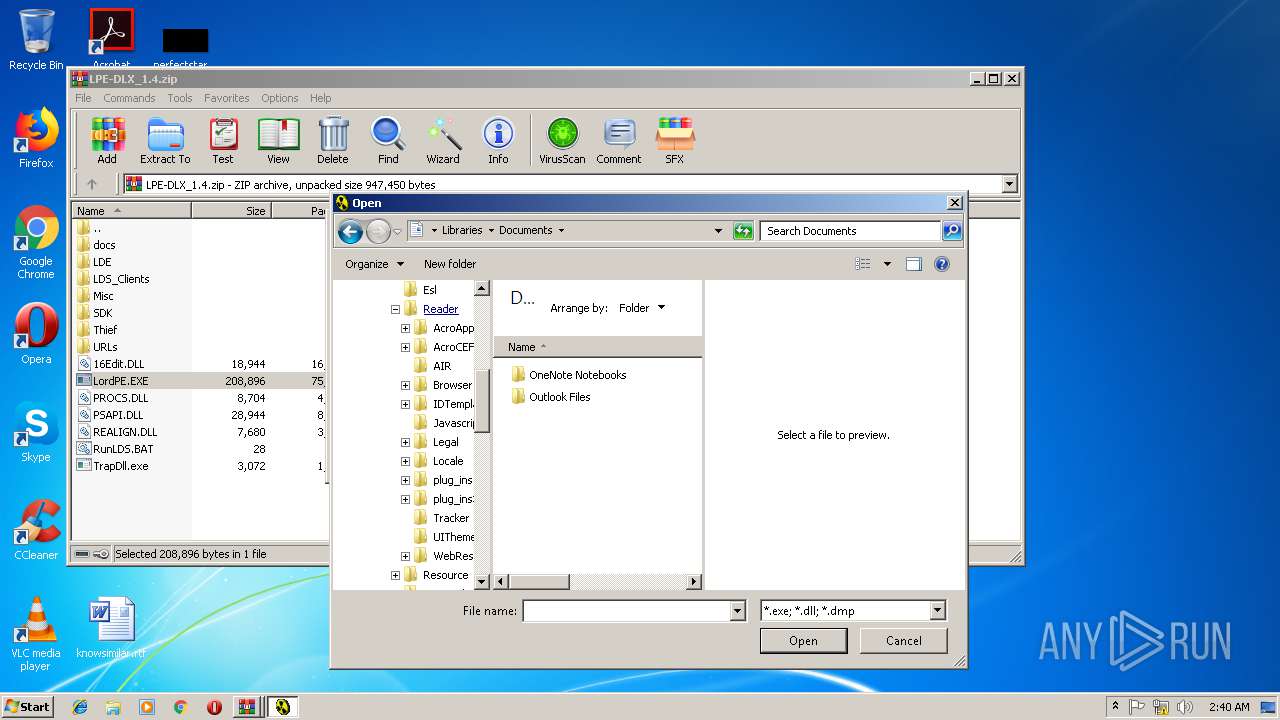
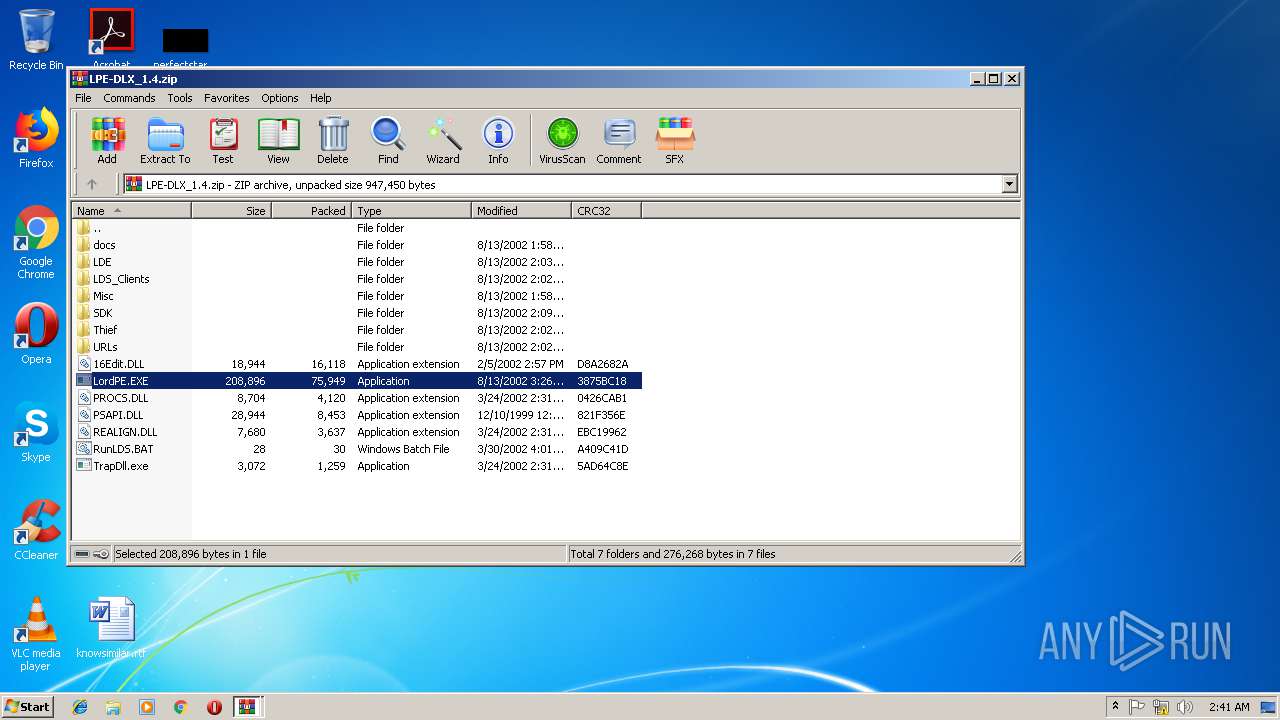
| 2200 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.44161\LordPE.EXE" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.44161\LordPE.EXE | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2952 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.47865\LordPE.EXE" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.47865\LordPE.EXE | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
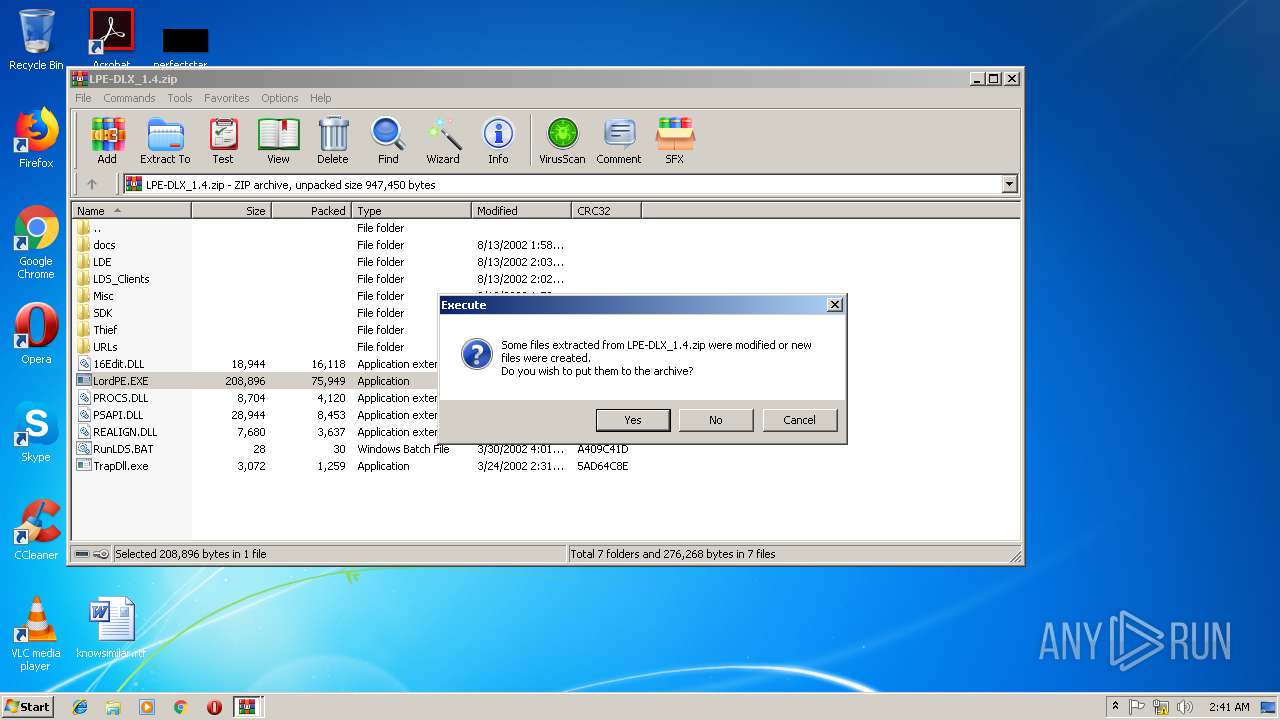
| 3372 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIa3448.43089\LPE-DLX_1.4.zip | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3448 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Bin_LordPE_2010-6-29_3.9_LordPE_1.41_Deluxe_b.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
2 554
Read events
2 177
Write events
368
Delete events
9
Modification events
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Bin_LordPE_2010-6-29_3.9_LordPE_1.41_Deluxe_b.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3372) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
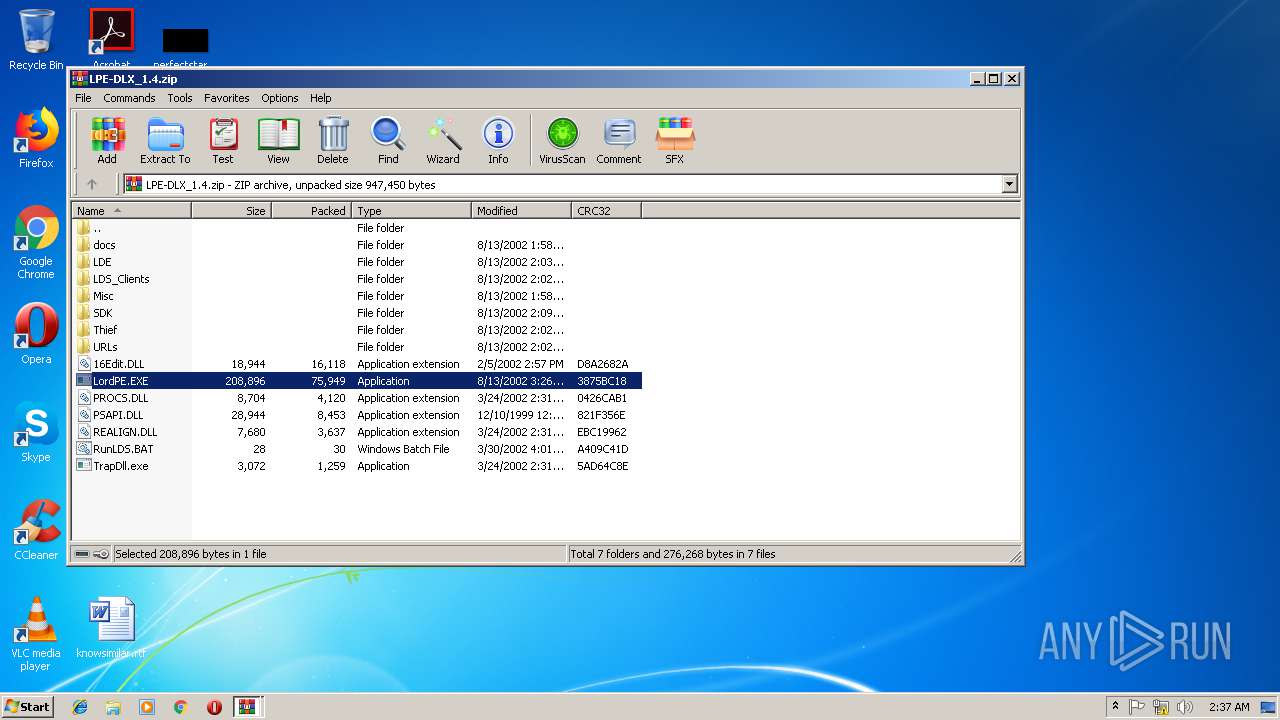
Executable files
62
Suspicious files
3
Text files
170
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.44161\docs\License.tXt | text | |
MD5:628C98D1B078591B76687EEA13CECD6D | SHA256:AA554F5FD76FEB3101723FBD29FAFC342A2BDC30690FA9F534A561E91E60ED0C | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3448.43089\LPE-DLX_1.4.zip | compressed | |
MD5:78434ABD881E6BA10CA4446ED1E13A43 | SHA256:1338B41B1E99A73EAEC6309EA5D426A0F56943F46CF288CE73D4D3111DA40555 | |||
| 3372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.44161\docs\LDE.tXt | text | |
MD5:2A4ED3109674F442BBC900AD3A0F43DC | SHA256:382389CEEDB84A4C4231083F8703DCAFB7A328E358CDC89D799798027F393237 | |||
| 3372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.44161\docs\EndOfCommerce.tXt | text | |
MD5:D328796B2502713D344B20F5C0F3B39D | SHA256:9A733FF019EBD9EBDD124E388CE38FAE299726FBD3AE589DC6D38D7854C54FD6 | |||
| 3372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.44161\docs\History.tXt | text | |
MD5:19EFF77EA75AC34EFD199A0D1CC551E5 | SHA256:A4C20F88DDAB18B88002BEAA716F1989D39BD7EC8CA905079B2AE10935B6112B | |||
| 3372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.44161\LDE\IntelliDump.LDE | executable | |
MD5:2E4206AEBC4F39A57915E5C53AD27DA2 | SHA256:F6D409742821F5DB40986B53291A4D5466D79C6600C89B6292FFAD19103C61CE | |||
| 3372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.44161\LDS_Clients\CoolDump1.4\Cooldump.exe | executable | |
MD5:83691BEE7FA65975EF50562FA7CEAD1A | SHA256:BE6C9444F6F7F3DF5107C3B914927CE97485D9A4BC688D394E45800E5CCF2730 | |||
| 3372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.44161\LDS_Clients\CoolDump1.4\File_id.diz | text | |
MD5:00D4B3A600A397BCC43B818B737AB245 | SHA256:BFB13DC0E7EB569B6500FC547180107E6910D9940DD0F3A2B30E1B012780471B | |||
| 3372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.44161\docs\LDS.tXt | text | |
MD5:28FCA52198A9571F491E0103F0B8CD05 | SHA256:4FCEAC6444C7BBEB26249D45CD28359C58AD629822097B8F35933C9A32A9C893 | |||
| 3372 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3372.44161\docs\ToDo.tXt | text | |
MD5:0470B29696CC57D19655B32A361B9C05 | SHA256:616E95DF0BC692F4E4F9BD9EDEB94D08E3A81367B7EE46AD7E402398A87C7846 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report