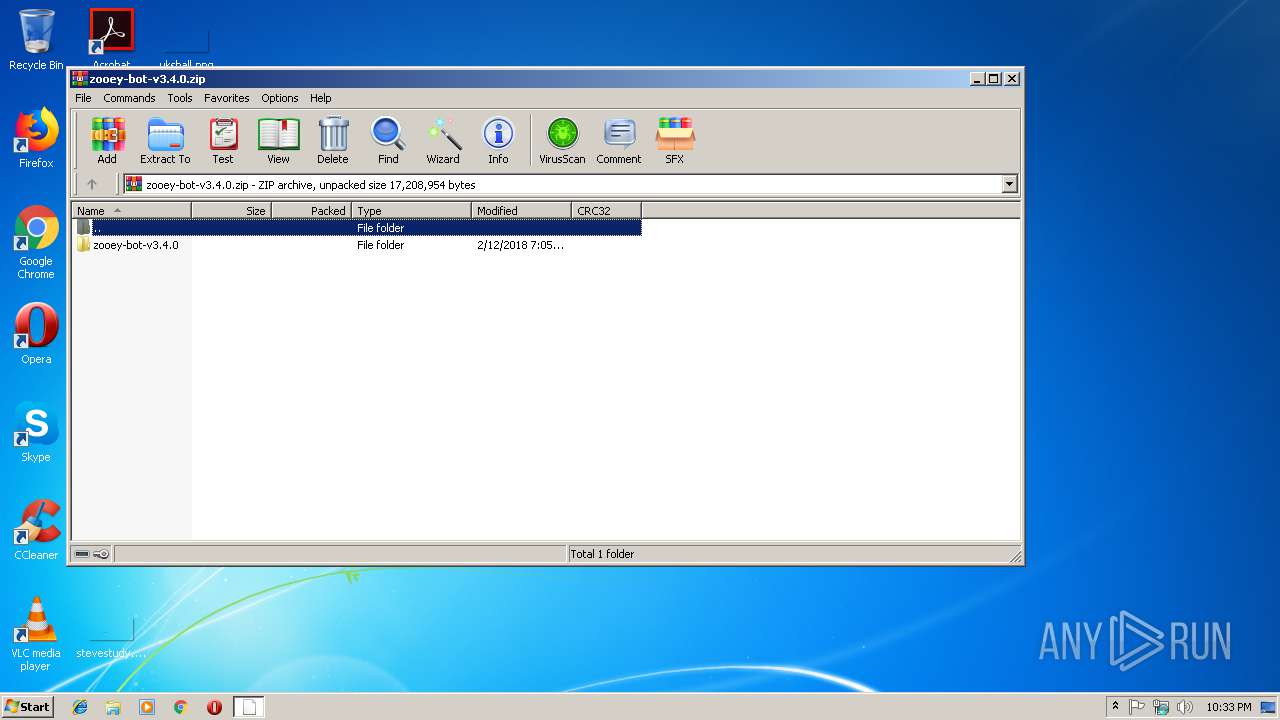
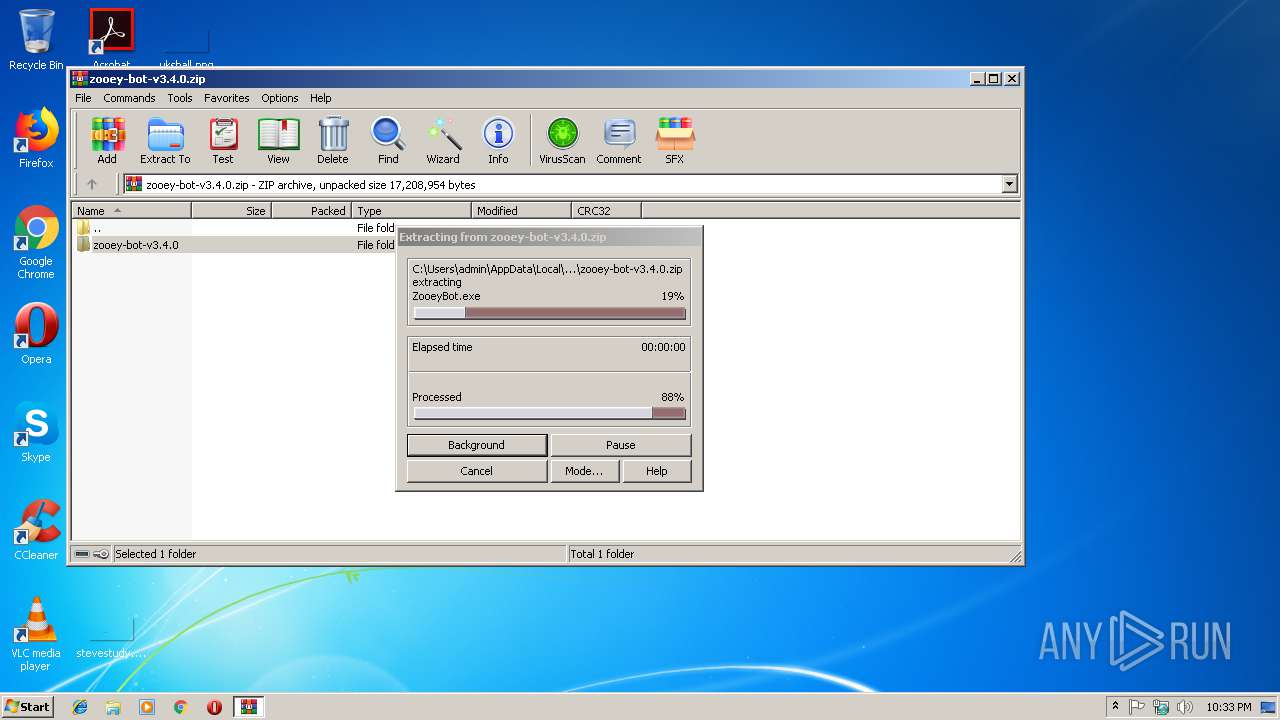
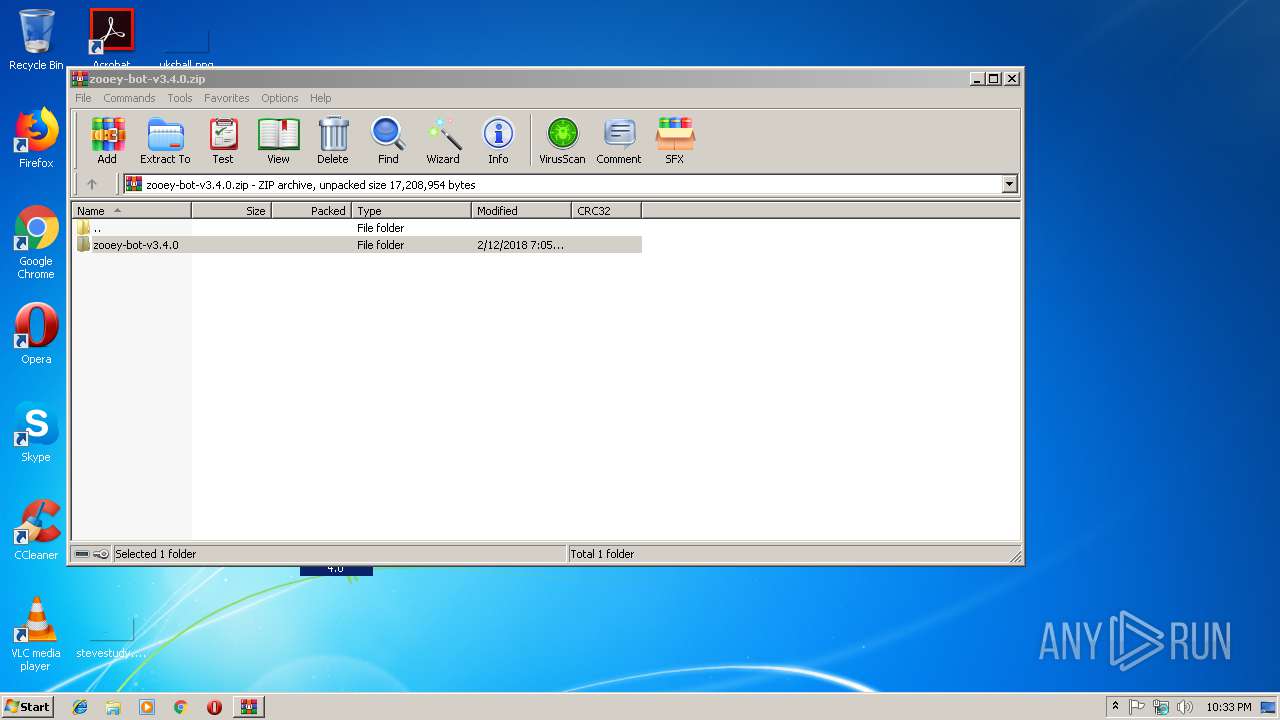
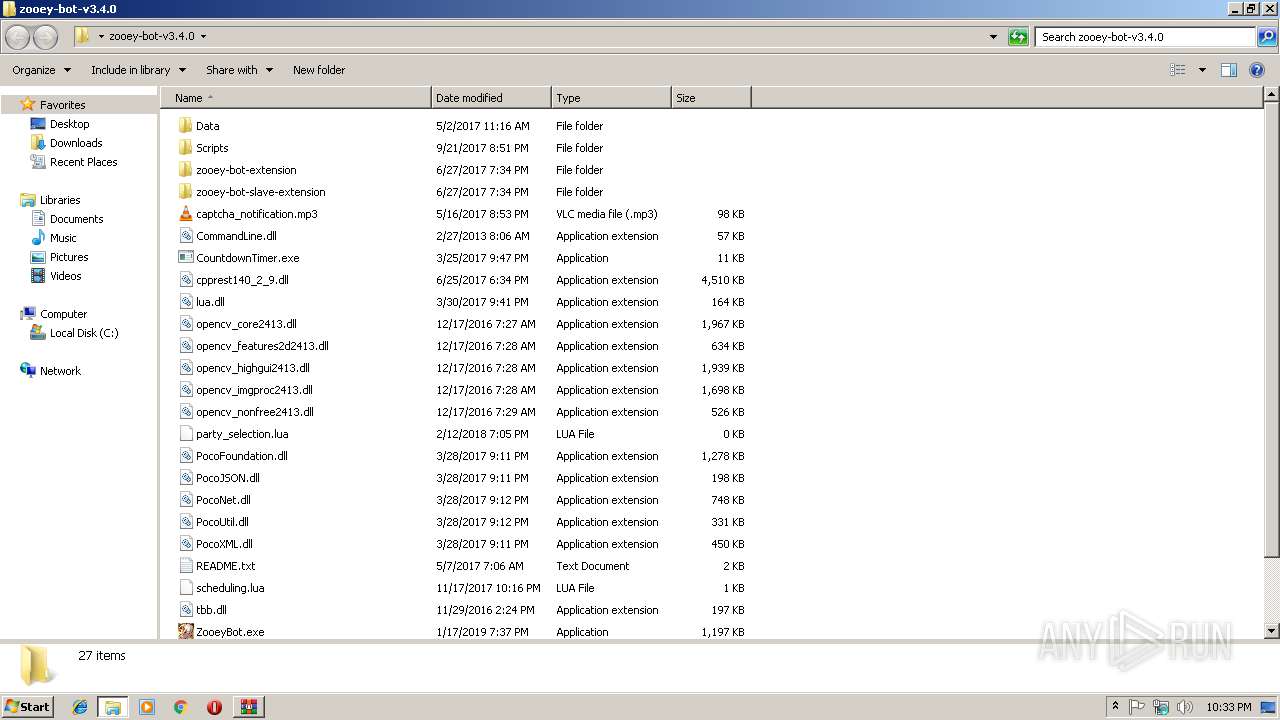
| download: | zooey-bot-v3.4.0.zip |
| Full analysis: | https://app.any.run/tasks/853a7775-9ca8-4408-b518-8271c962e7e9 |
| Verdict: | Malicious activity |
| Analysis date: | February 14, 2019, 22:32:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 7490831FA7EF70CD885EF4BD510F0BA6 |
| SHA1: | D14A172FF3AFD5D5BE7C475A470B95DCF141B5EF |
| SHA256: | 649CFE73A6DD2D62BC0BD5B984AB4616CC2105EA9755AEB790AE4C610588D32B |
| SSDEEP: | 98304:tCN2NtPdxNAHf3wxntZrAp92HUVh+nZ6j95HcVjwkoPEpjIdr8E95gs8uyiLo:02xOfQy9FyZ6j95wwfPEpa39qRiM |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1832)
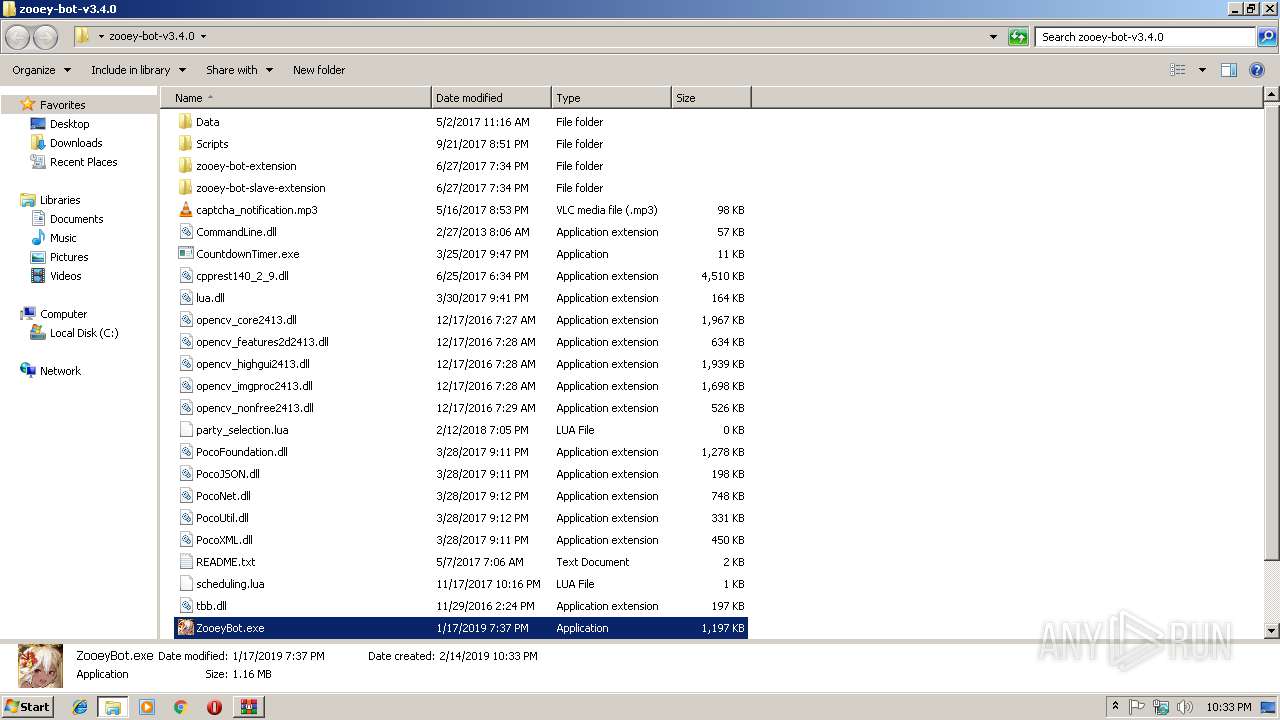
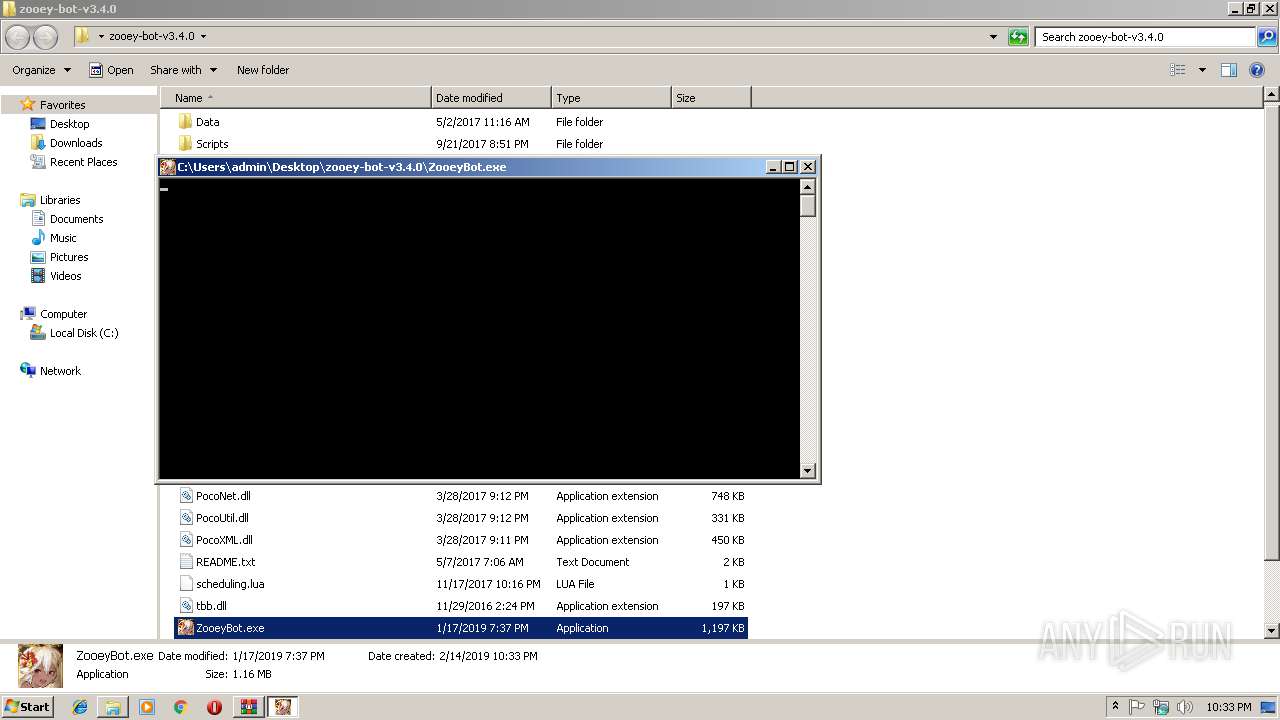
- ZooeyBot.exe (PID: 3080)
Application was dropped or rewritten from another process
- ZooeyBot.exe (PID: 3080)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3040)
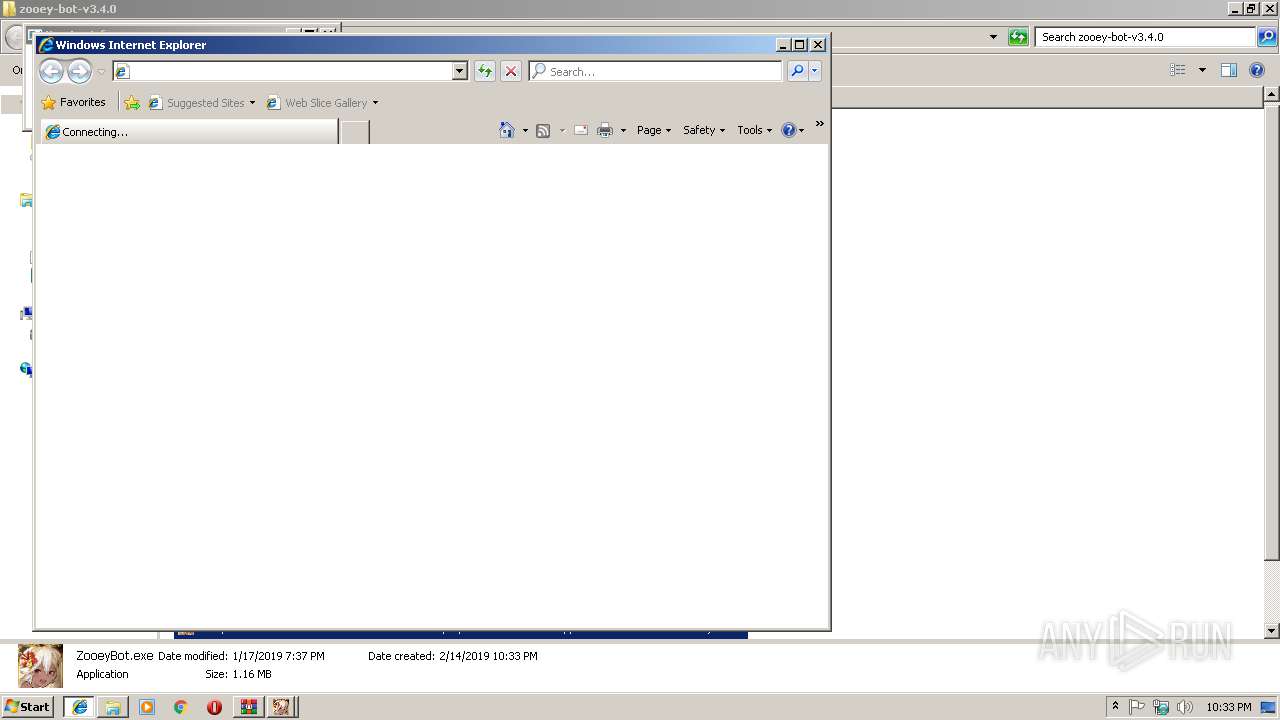
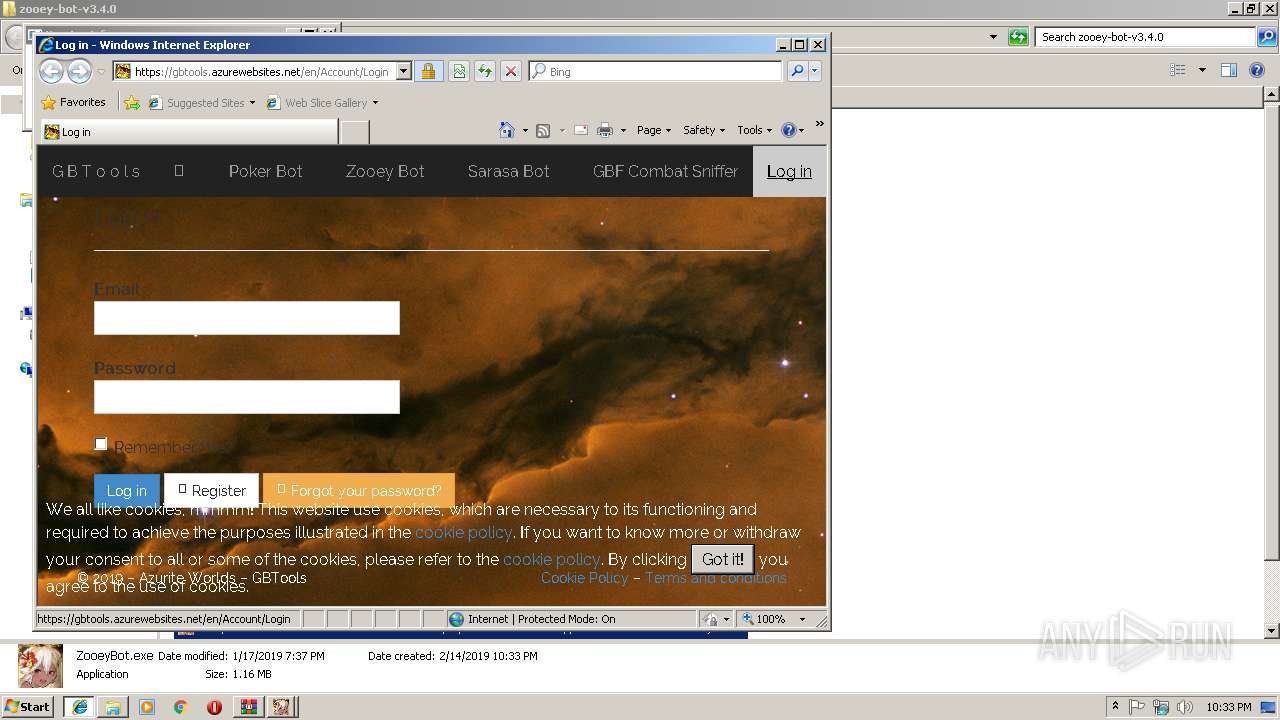
Starts Internet Explorer
- ZooeyBot.exe (PID: 3080)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 1916)
Changes internet zones settings
- iexplore.exe (PID: 3848)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3040)
Reads internet explorer settings
- iexplore.exe (PID: 1916)
Creates files in the user directory
- iexplore.exe (PID: 1916)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3652)
Reads settings of System Certificates
- iexplore.exe (PID: 3848)
Changes settings of System certificates
- iexplore.exe (PID: 3848)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:02:12 19:05:01 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | zooey-bot-v3.4.0/ |
Total processes
37
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1832 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1916 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3848 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3040 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\zooey-bot-v3.4.0.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3080 | "C:\Users\admin\Desktop\zooey-bot-v3.4.0\ZooeyBot.exe" | C:\Users\admin\Desktop\zooey-bot-v3.4.0\ZooeyBot.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3652 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 3848 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | ZooeyBot.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 347
Read events
1 202
Write events
141
Delete events
4
Modification events
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\zooey-bot-v3.4.0.zip | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1832) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1832) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\wshext.dll,-4804 |
Value: JScript Script File | |||
Executable files
18
Suspicious files
0
Text files
49
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.9955\zooey-bot-v3.4.0\Data\home_button_jp.png | image | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.9955\zooey-bot-v3.4.0\lua.dll | executable | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.9955\zooey-bot-v3.4.0\opencv_imgproc2413.dll | executable | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.9955\zooey-bot-v3.4.0\README.txt | text | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.9955\zooey-bot-v3.4.0\PocoJSON.dll | executable | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.9955\zooey-bot-v3.4.0\scheduling.lua | text | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.9955\zooey-bot-v3.4.0\Scripts\do_nothing.lua | text | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.9955\zooey-bot-v3.4.0\captcha_notification.mp3 | mp3 | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.9955\zooey-bot-v3.4.0\Data\home_button.png | image | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3040.9955\zooey-bot-v3.4.0\CountdownTimer.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
19
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3848 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3080 | ZooeyBot.exe | 203.104.248.7:80 | game.granbluefantasy.jp | AS for DATAHOTEL, which is one of iDC in Japan | JP | unknown |
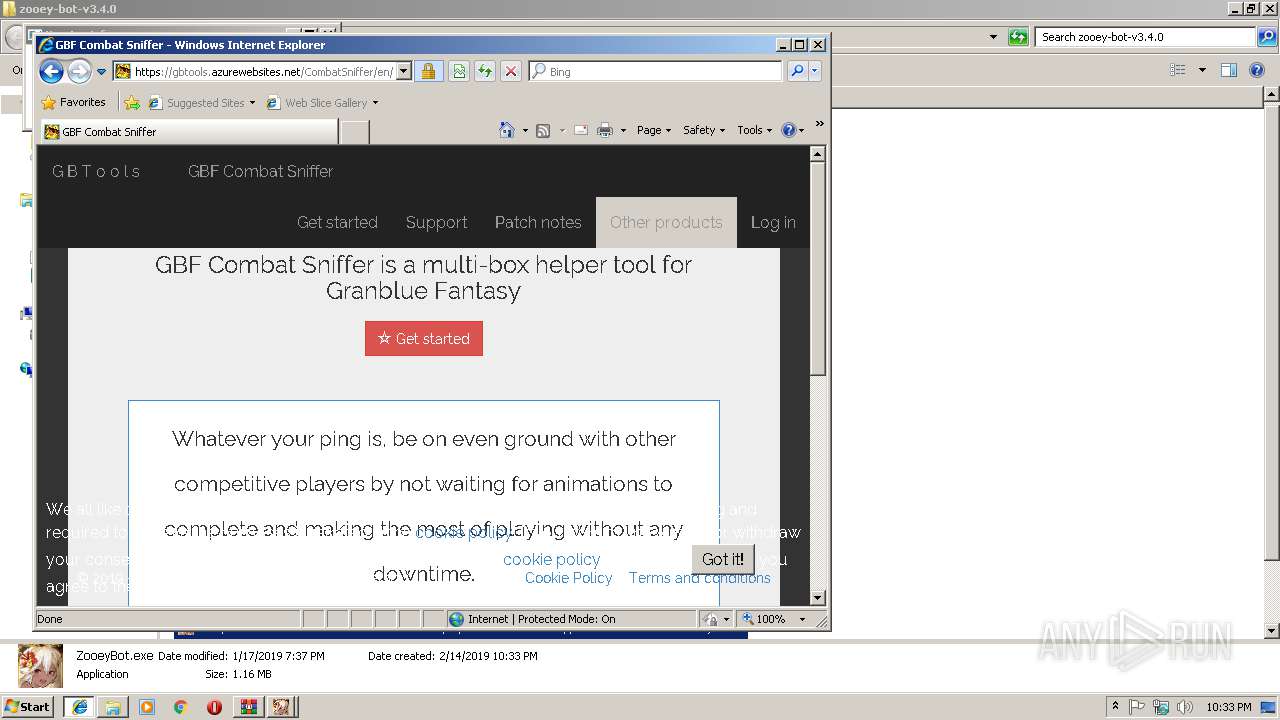
3080 | ZooeyBot.exe | 104.40.147.216:443 | gbtools.azurewebsites.net | Microsoft Corporation | NL | suspicious |
3848 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1916 | iexplore.exe | 104.40.147.216:443 | gbtools.azurewebsites.net | Microsoft Corporation | NL | suspicious |
1916 | iexplore.exe | 192.229.133.221:443 | www.w3schools.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1916 | iexplore.exe | 172.217.16.174:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
1916 | iexplore.exe | 152.199.19.160:443 | az416426.vo.msecnd.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1916 | iexplore.exe | 40.71.12.231:443 | dc.services.visualstudio.com | Microsoft Corporation | US | unknown |
3848 | iexplore.exe | 104.40.147.216:443 | gbtools.azurewebsites.net | Microsoft Corporation | NL | suspicious |
1916 | iexplore.exe | 172.217.18.163:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
game.granbluefantasy.jp |
| unknown |
gbtools.azurewebsites.net |
| whitelisted |
www.bing.com |
| whitelisted |
www.w3schools.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
use.fontawesome.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
az416426.vo.msecnd.net |
| whitelisted |
www.google-analytics.com |
| whitelisted |
dc.services.visualstudio.com |
| whitelisted |