| File name: | eicar-standard-antivirus-test-files.zip |
| Full analysis: | https://app.any.run/tasks/8c1761e8-7869-4611-baa0-dac96e793ee1 |
| Verdict: | Malicious activity |
| Analysis date: | December 04, 2024, 20:44:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 2C0639649B894A0845BC0601FA67B3C7 |
| SHA1: | DCB53D4FB45650FE1E49AADA7178972065C4E1DC |
| SHA256: | 648EB3DD8252073B53F16887084C5415F56E90877AEE69D29393EFE1382679B4 |
| SSDEEP: | 24576:miWuDHeKr7hfHRLE3Ks5rOpA1p+YnaDtk5jC1me7Kd:miW+HeKrpRLE3KSrOpA1pxaDtk5jC1mB |
MALICIOUS
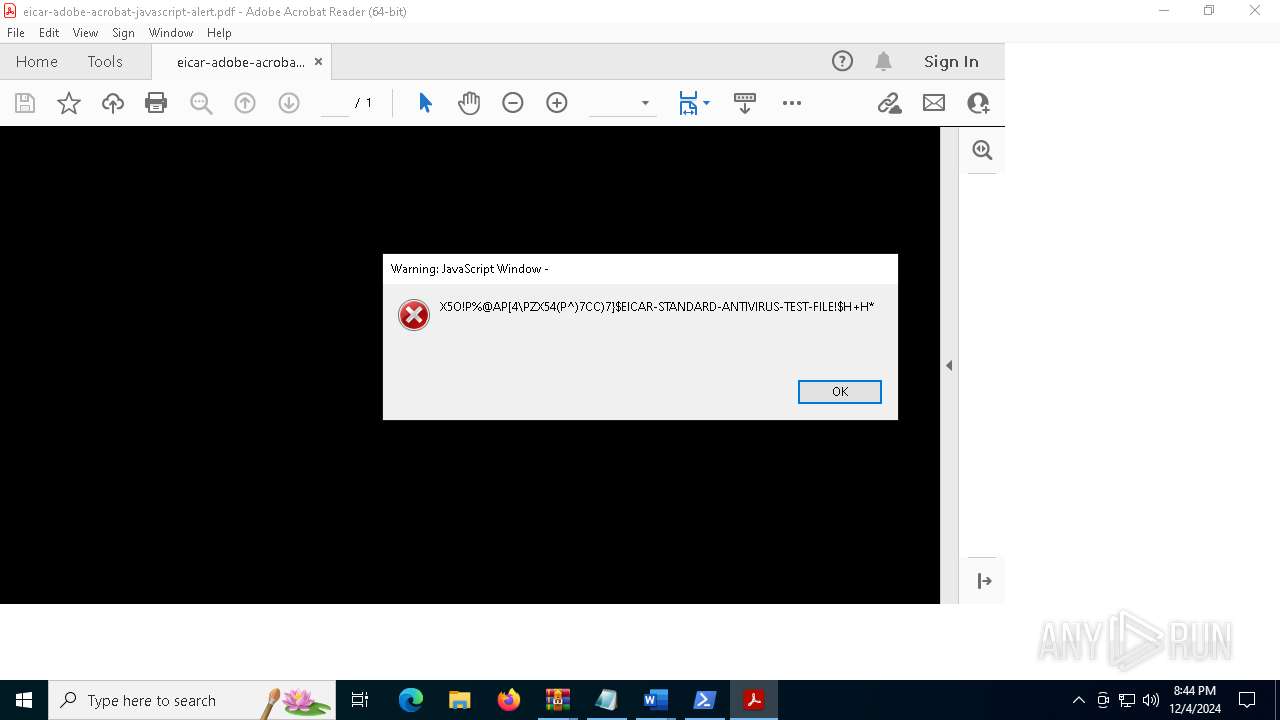
The EICAR Standard Anti-Virus Test File is detected
- WINWORD.EXE (PID: 5208)
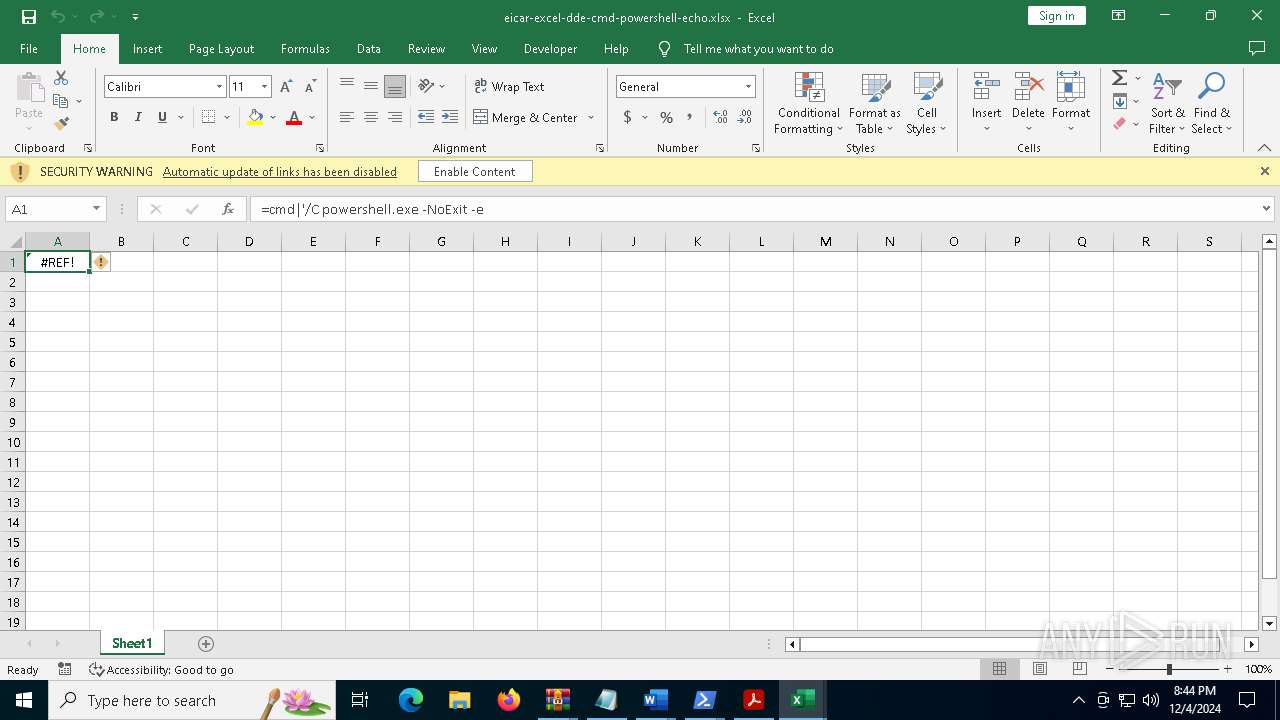
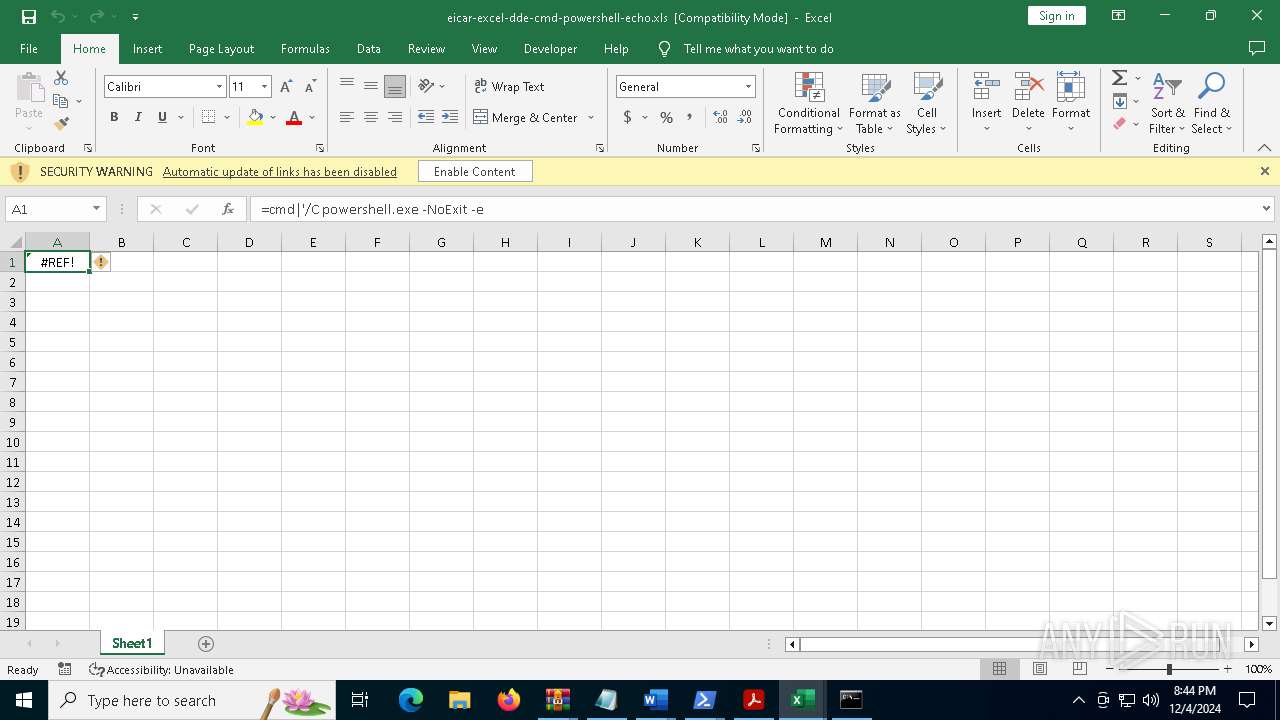
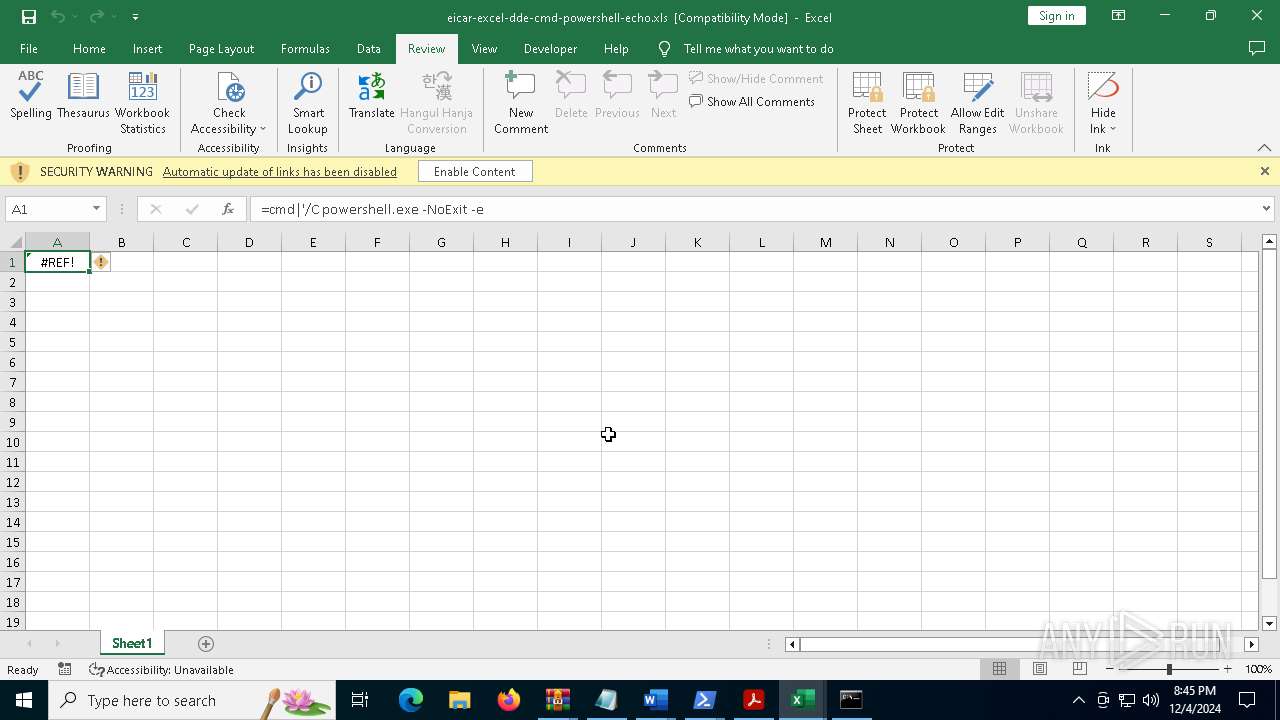
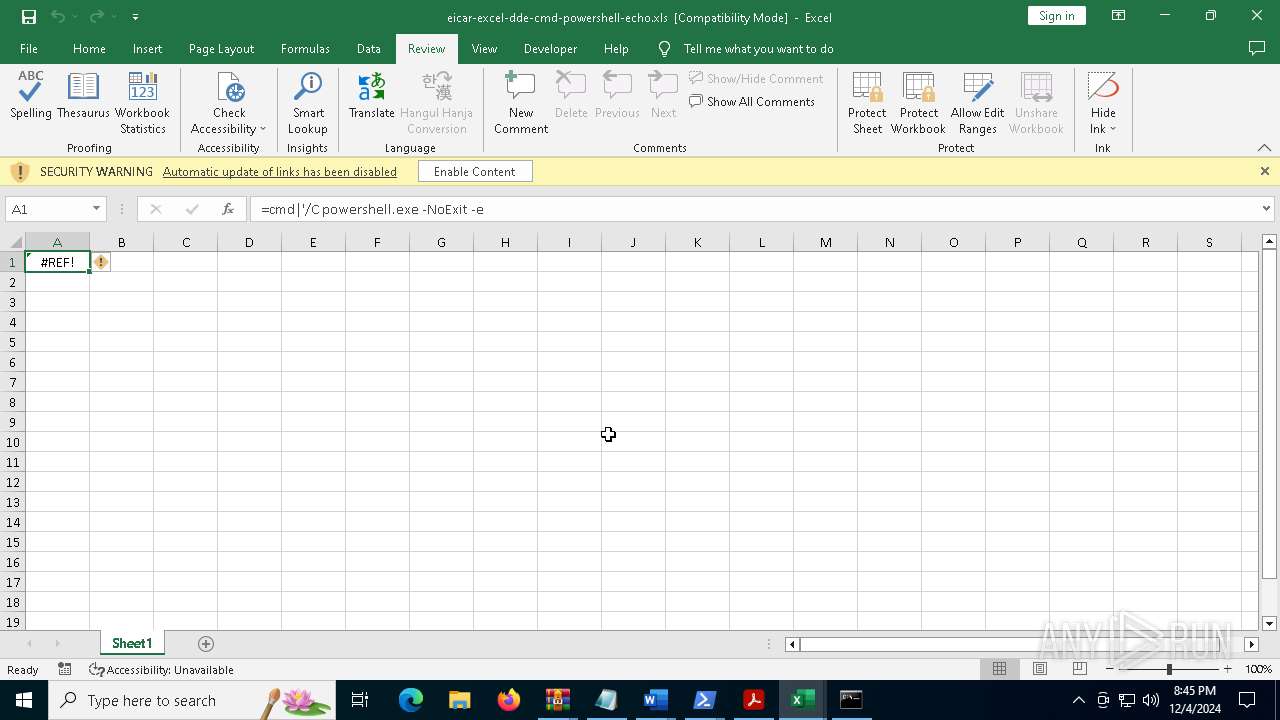
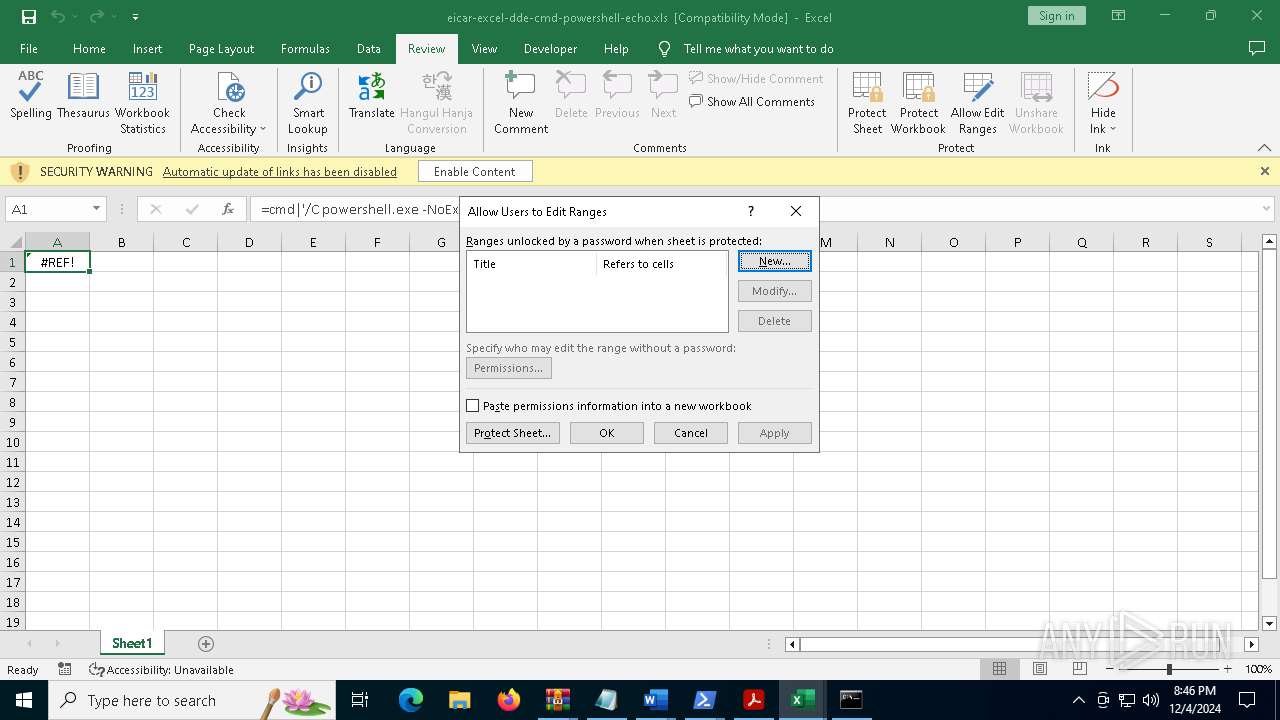
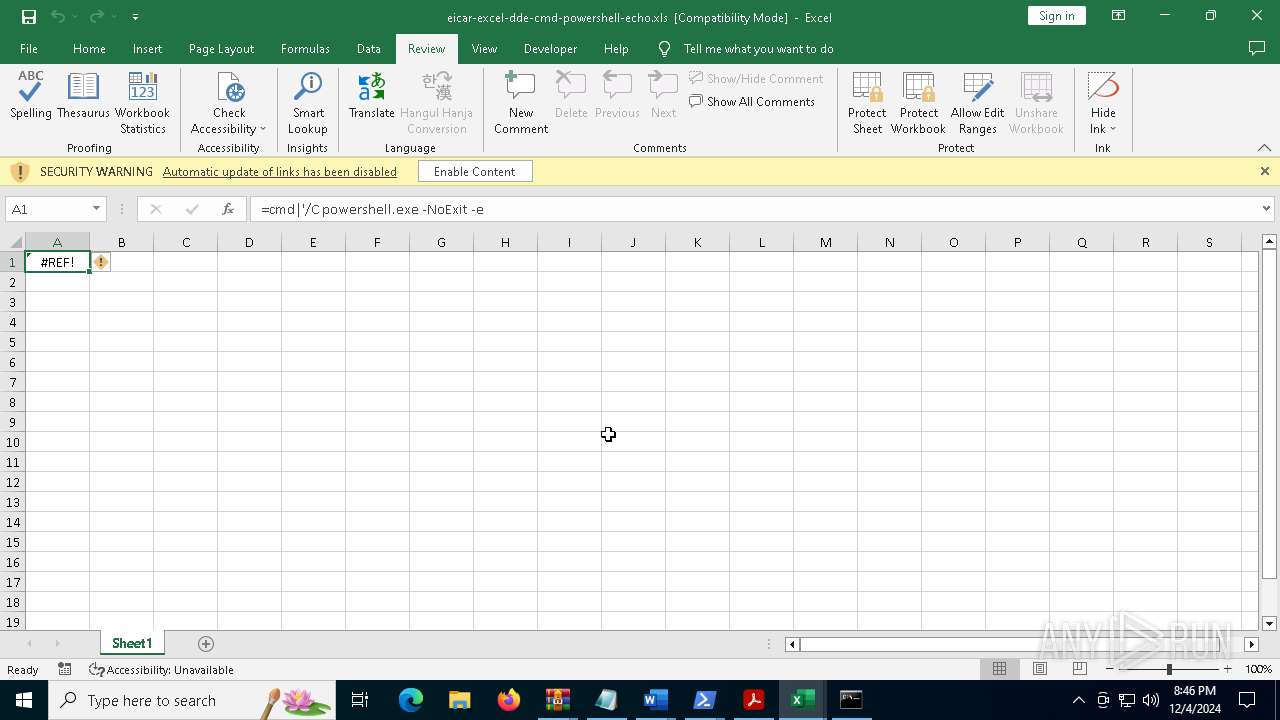
Microsoft Office executes commands via PowerShell or Cmd
- EXCEL.EXE (PID: 3420)
- WINWORD.EXE (PID: 5208)
Unusual execution from MS Office
- EXCEL.EXE (PID: 3420)
- WINWORD.EXE (PID: 5208)
Starts POWERSHELL.EXE for commands execution
- EXCEL.EXE (PID: 3420)
- WINWORD.EXE (PID: 5208)
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 3420)
SUSPICIOUS
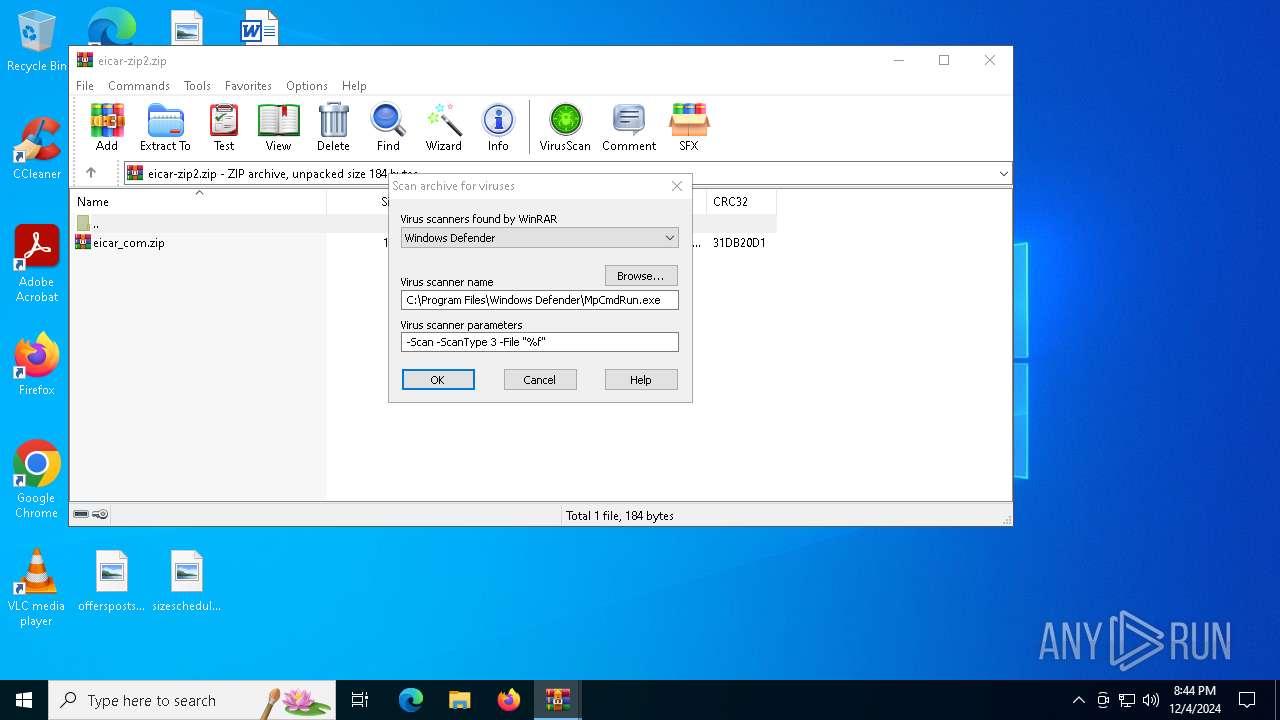
Generic archive extractor
- WinRAR.exe (PID: 4384)
Base64-obfuscated command line is found
- EXCEL.EXE (PID: 3420)
- WINWORD.EXE (PID: 5208)
BASE64 encoded PowerShell command has been detected
- EXCEL.EXE (PID: 3420)
- WINWORD.EXE (PID: 5208)
INFO
Manual execution by a user
- WinRAR.exe (PID: 3724)
- WINWORD.EXE (PID: 5208)
- WinRAR.exe (PID: 5548)
- notepad.exe (PID: 5464)
- WinRAR.exe (PID: 5568)
- EXCEL.EXE (PID: 3420)
- EXCEL.EXE (PID: 1140)
- Acrobat.exe (PID: 6148)
- WINWORD.EXE (PID: 6560)
- EXCEL.EXE (PID: 6772)
- EXCEL.EXE (PID: 6724)
Application launched itself
- Acrobat.exe (PID: 6148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:04 15:39:20 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | eicar-standard-antivirus-test-files/ |
Total processes
142
Monitored processes
20
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 776 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "80E63BC6-E8BD-40EA-86C3-9BC4772E12DA" "33DB714C-E981-481C-B567-CE8472DF9003" "5208" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 1140 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" C:\Users\admin\Desktop\eicar-excel-dde-cmd-powershell-echo.xlsx | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 3420 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" C:\Users\admin\Desktop\eicar-excel-macro-powershell-echo.xls | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 3724 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\eicar_com.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4384 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\eicar-standard-antivirus-test-files.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
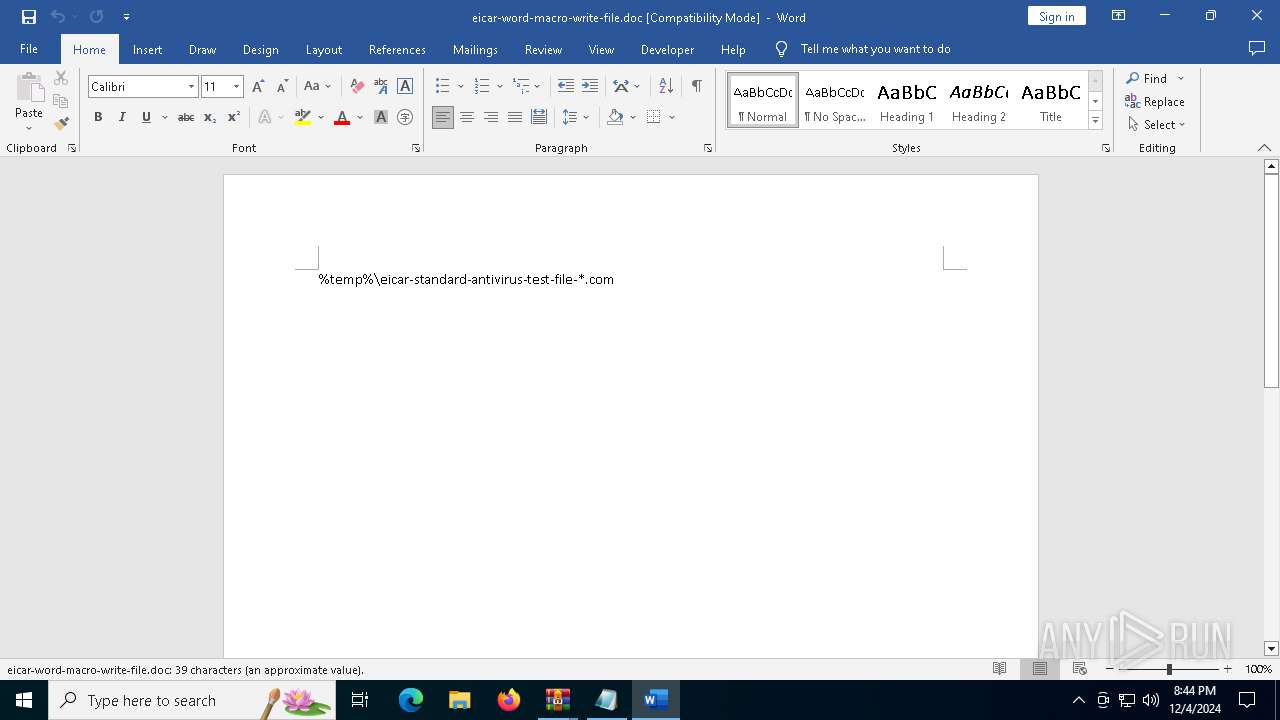
| 5208 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\Desktop\eicar-word-macro-write-file.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5464 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\eicar-test.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5548 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\eicar-zip2.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5568 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\eicar-zip.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6148 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe" C:\Users\admin\Desktop\eicar-adobe-acrobat-javascript-alert.pdf | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.exe | — | explorer.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Version: 23.1.20093.0 Modules
| |||||||||||||||
Total events
49 569
Read events
48 727
Write events
770
Delete events
72
Modification events
| (PID) Process: | (4384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\eicar-standard-antivirus-test-files.zip | |||
| (PID) Process: | (4384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3724) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
2
Suspicious files
159
Text files
57
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5208 | WINWORD.EXE | C:\Users\admin\Desktop\~$car-word-macro-write-file.doc | pgc | |
MD5:D4C57BBCB22D4E43882DAB839EE632DC | SHA256:CE12D73DAB40C8B09015F88903410CAC49D7E5F5F75F9E11DA4C651978E1BFA9 | |||
| 5208 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\D4E1D1D3-3A9A-4B62-BFF2-8E1F023C8EE2 | xml | |
MD5:EDD2DEBF27CB284CD805FBE03237DC3D | SHA256:2F2E59EDE909EE9D6051F499BC9B53D1F40AB409F8EA0C34DF13295DF2725383 | |||
| 5208 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:C705E9E6C7AA89EAA20536C84E21BEF5 | SHA256:4C37684ACE4FBDBF8C55142F41389DE4C6F45EDBF650C87B4352AE7AFEF8CF07 | |||
| 5208 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:0C5756276F9DE2E1B726830E1827168D | SHA256:5AFCE03CBEB066DF612E1E2DC702412FE5BC7C96A7ED777201D48EFF8D800DB7 | |||
| 5208 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\eicar-standard-antivirus-test-file-20241204204443.com | text | |
MD5:44D88612FEA8A8F36DE82E1278ABB02F | SHA256:275A021BBFB6489E54D471899F7DB9D1663FC695EC2FE2A2C4538AABF651FD0F | |||
| 5208 | WINWORD.EXE | C:\Users\admin\Desktop\~$car-word-macro-powershell-echo.doc | pgc | |
MD5:00D548E30FBE4E6692EE10F7E73C71EC | SHA256:534371E2068DE9EA43085CB195DDE0F874CF0127031C7FFF7F6A1B7EFEDBEEB7 | |||
| 5208 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Word\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:F689C150A33975167DB25DE6B06E336B | SHA256:5757A38E736EC56F3858287A819B3EBBB5969895609E9A509866C710FFD7C5E4 | |||
| 3420 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\eicar-excel-macro-powershell-echo.xls.LNK | lnk | |
MD5:1D46198319D20B28359C40DF3AC1F1BD | SHA256:D0DF77FD05FD515588115E0EAD99AAD0EFDA08360FB98F5D1E2D38EA36536887 | |||
| 5208 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:43F65654D06710D7251B53B7D18344FC | SHA256:9E7983EF0DD1B83392837B3263D9CC1C9171A6AE10994B23B25F877FD1BF3A0F | |||
| 1140 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Diagnostics\EXCEL\App1733345090481841600_9DE7395B-F66C-41B4-9881-77832C8D32C9.log | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
80
TCP/UDP connections
90
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5776 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.113.194.132:443 | https://ecs.office.com/config/v2/Office/word/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=word&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=winword.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7b76C973B9-FEFB-45BB-B49E-486DD327E4C6%7d&LabMachine=false | unknown | binary | 381 Kb | whitelisted |
— | — | GET | 200 | 52.111.236.4:443 | https://messaging.lifecycle.office.com/getcustommessage16?app=0&ui=en-US&src=BizBar&messagetype=BizBar&hwid=04111-083-043729&ver=16.0.16026&lc=en-US&platform=10%3A0%3A19045%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA720%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7B76C973B9-FEFB-45BB-B49E-486DD327E4C6%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofsh6c2b1tla1a31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%2Cofpioygfqmufst31%2Cofjhlwlmoc1pz531%22%7D | unknown | text | 542 b | whitelisted |
— | — | GET | 200 | 2.16.10.172:443 | https://omex.cdn.office.net/addinclassifier/officesharedentities | unknown | text | 314 Kb | whitelisted |
— | — | GET | 200 | 52.113.194.132:443 | https://ecs.office.com/config/v2/Office/excel/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=excel&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=excel.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7b9DE7395B-F66C-41B4-9881-77832C8D32C9%7d&LabMachine=false | unknown | binary | 370 Kb | whitelisted |
— | — | GET | 200 | 52.109.32.97:443 | https://officeclient.microsoft.com/config16/?lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3 | unknown | xml | 177 Kb | whitelisted |
— | — | GET | 200 | 52.113.194.132:443 | https://ecs.office.com/config/v2/Office/excel/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=excel&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=excel.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7b8F49EA23-7394-47B8-9ED9-03946D257FAB%7d&LabMachine=false | unknown | binary | 370 Kb | whitelisted |
— | — | GET | 200 | 23.32.238.225:443 | https://binaries.templates.cdn.office.net/support/templates/en-us/tp02851221.cab | unknown | compressed | 30.8 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5776 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.209.176:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5776 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5776 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5776 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
ecs.office.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|