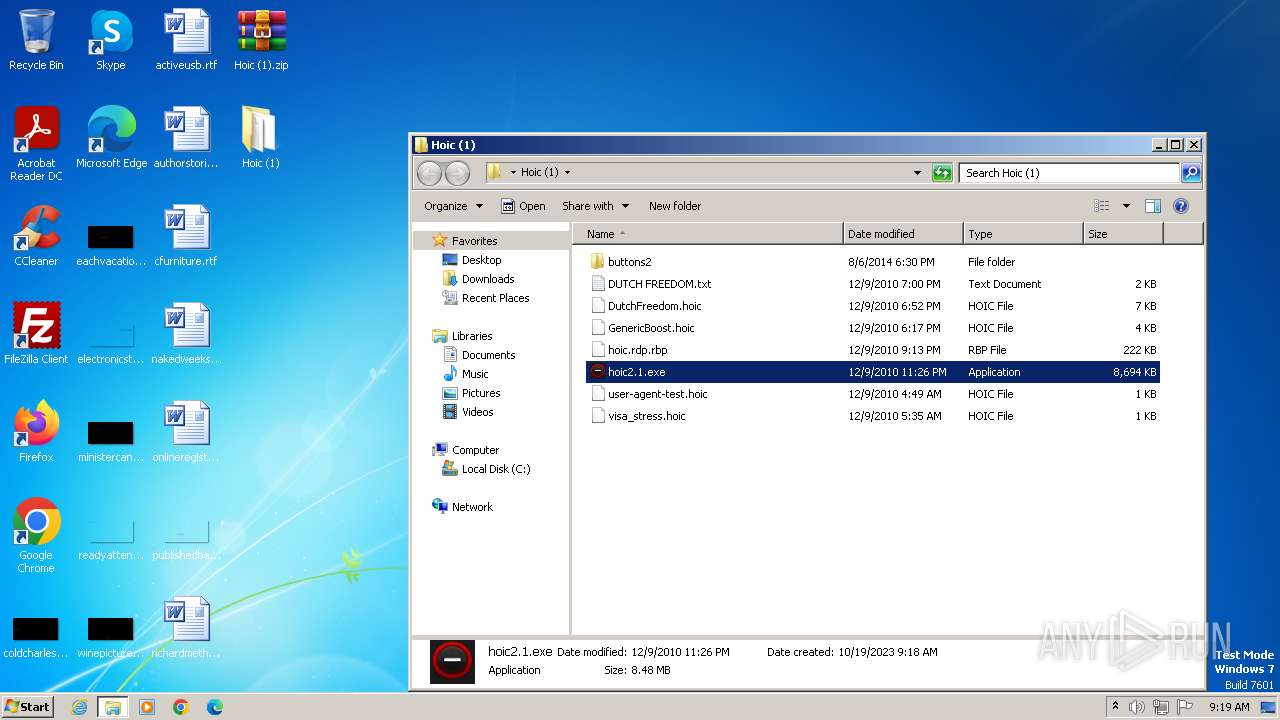
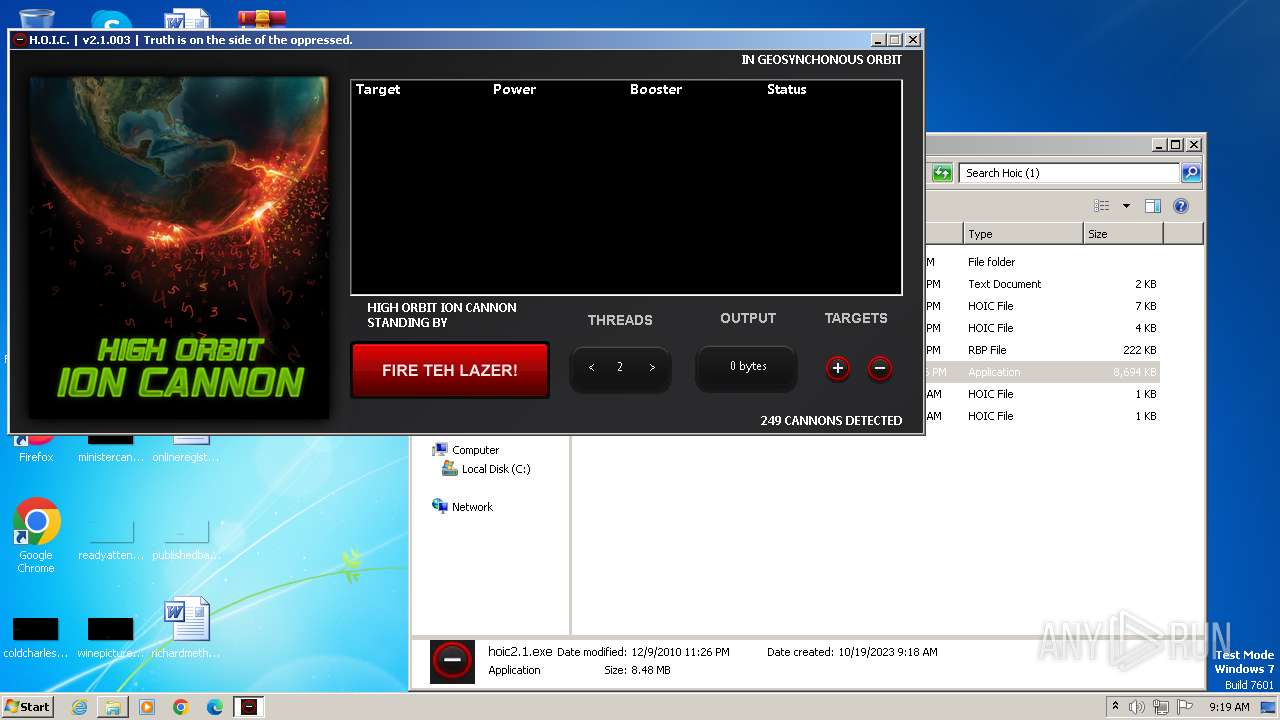
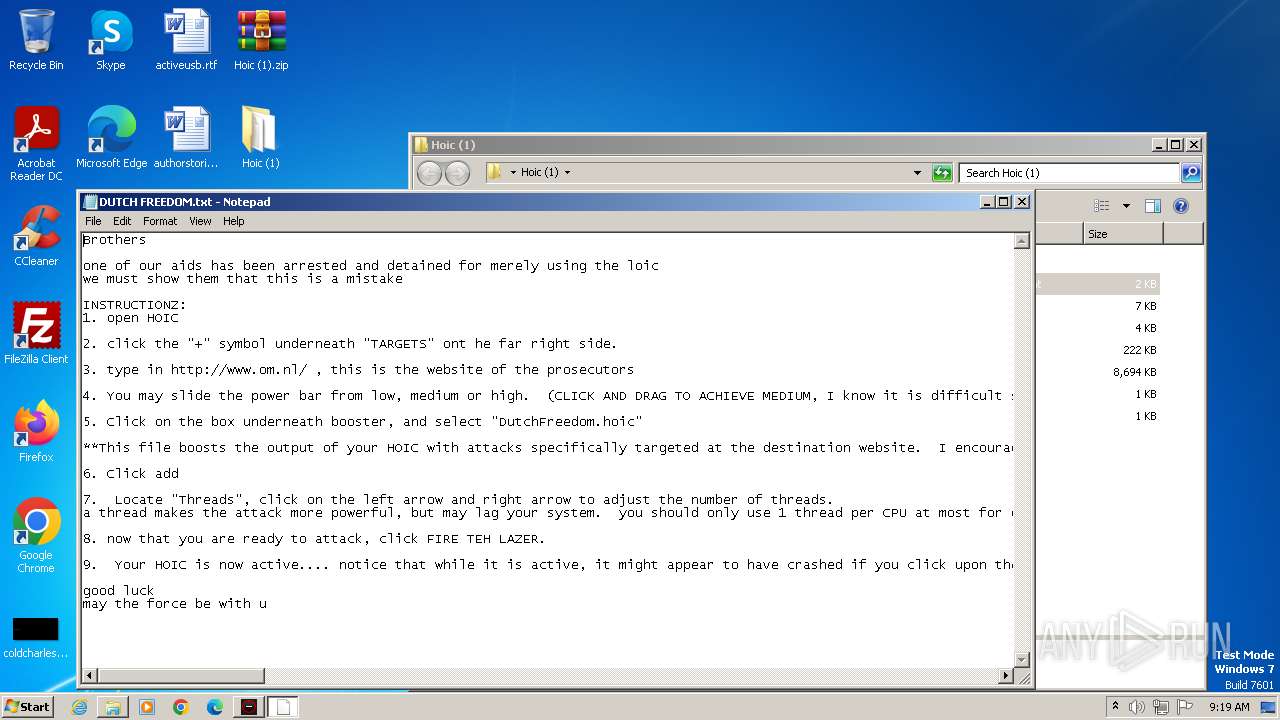
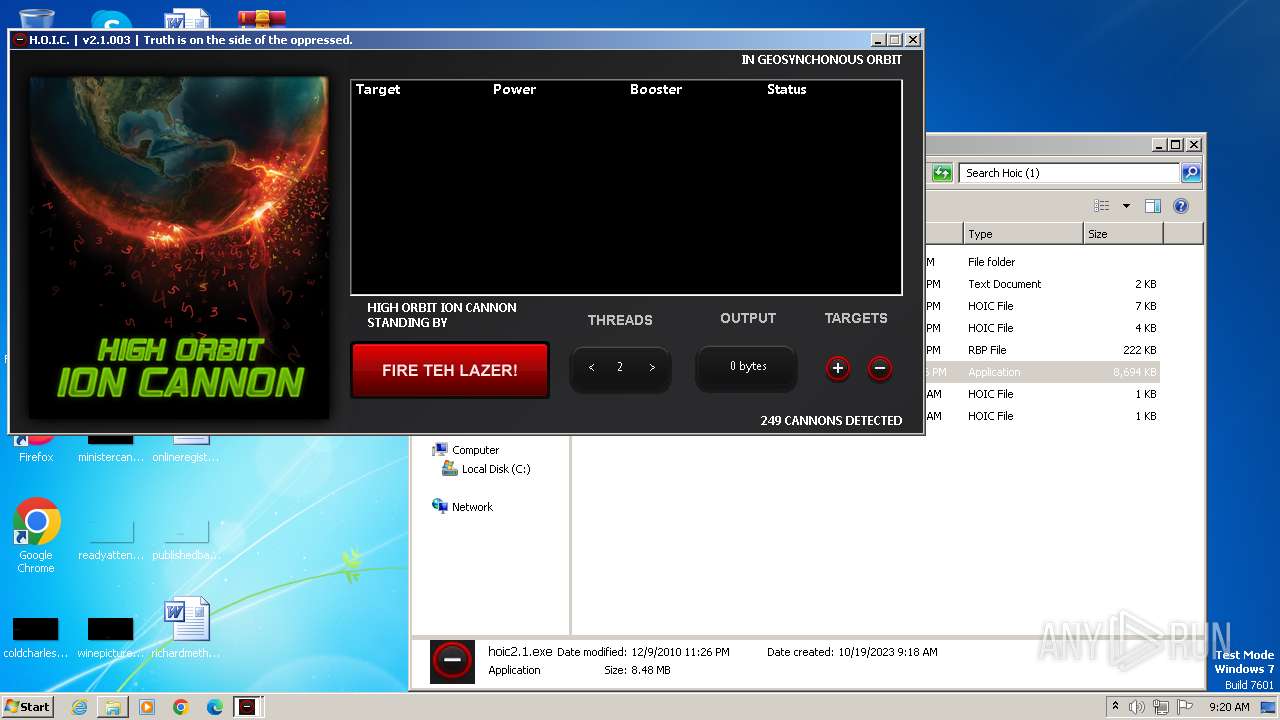
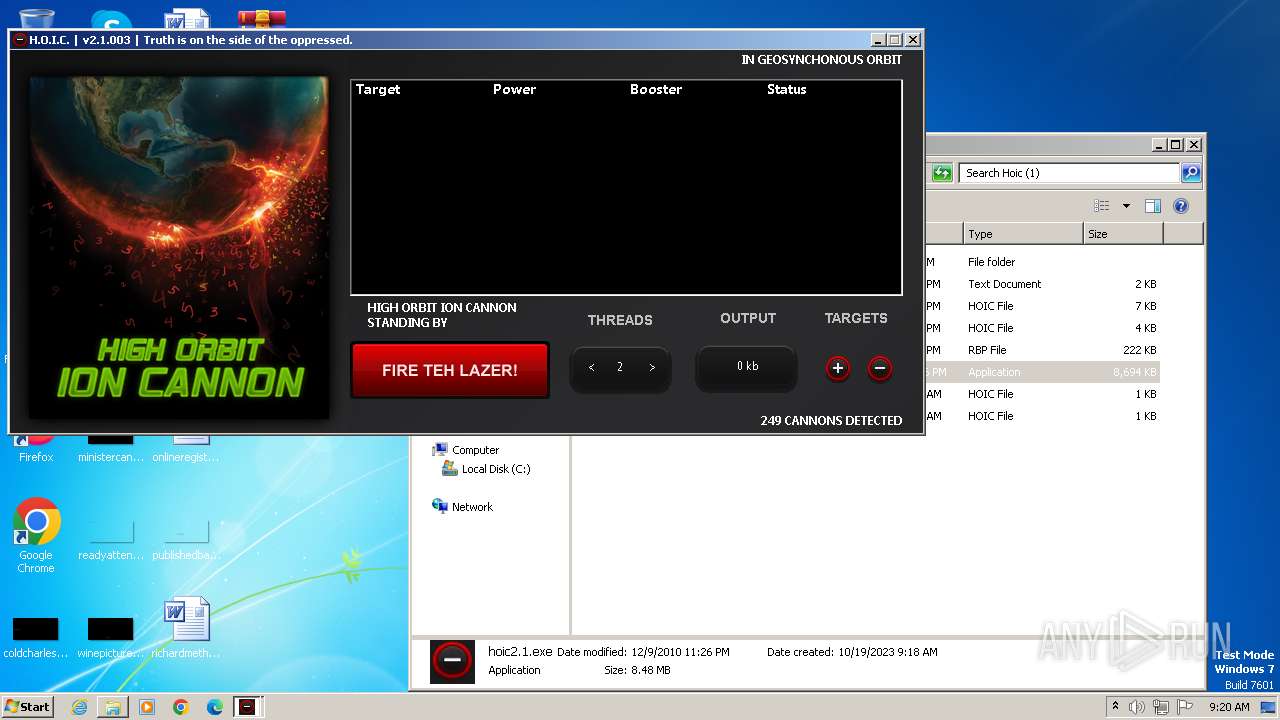
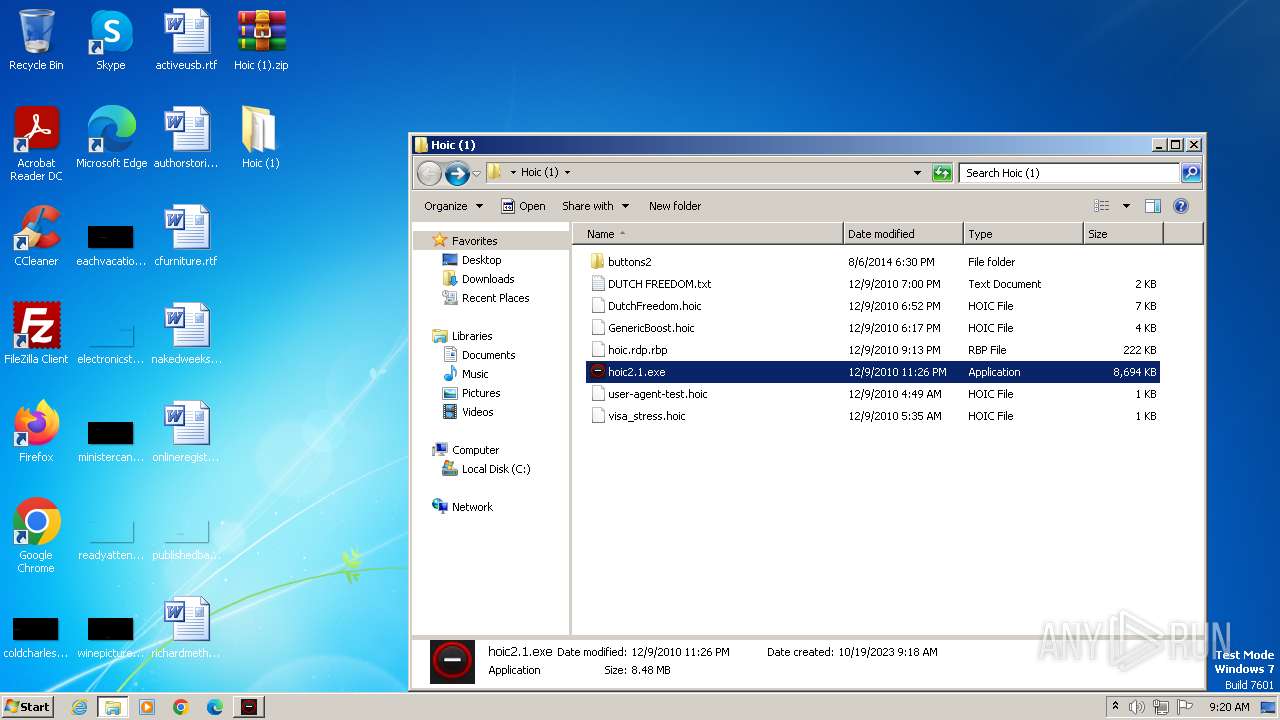
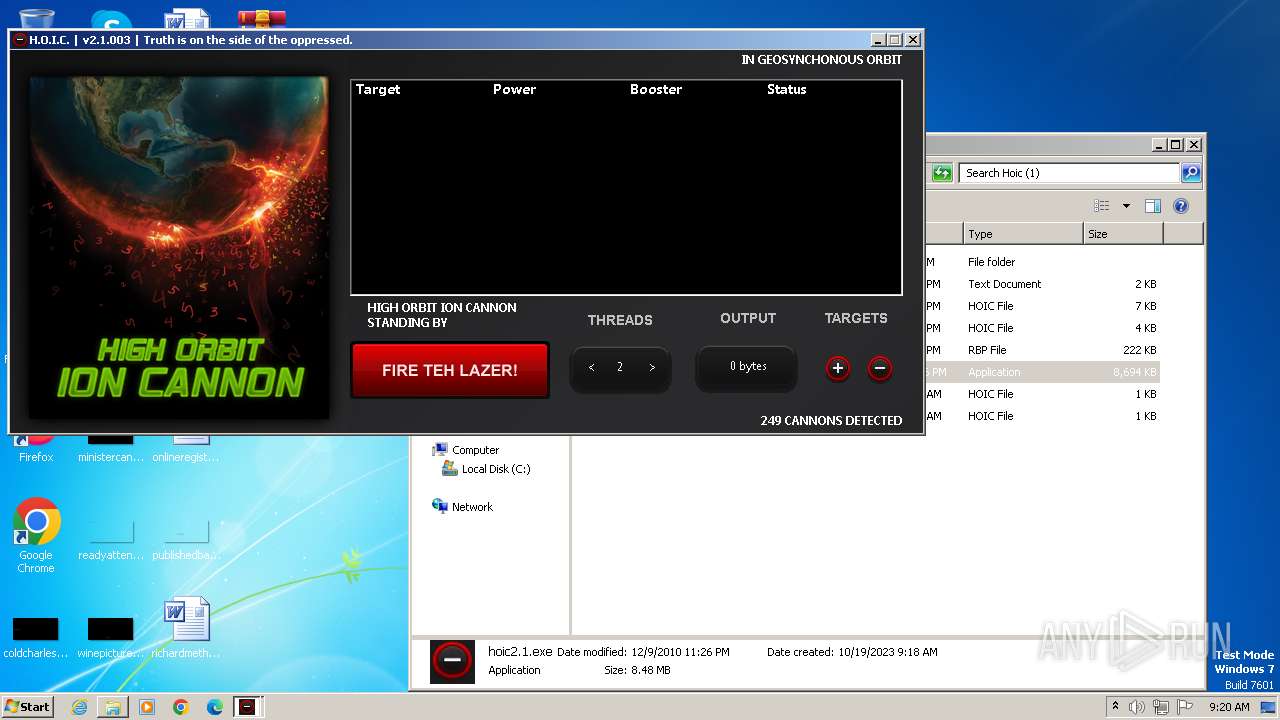
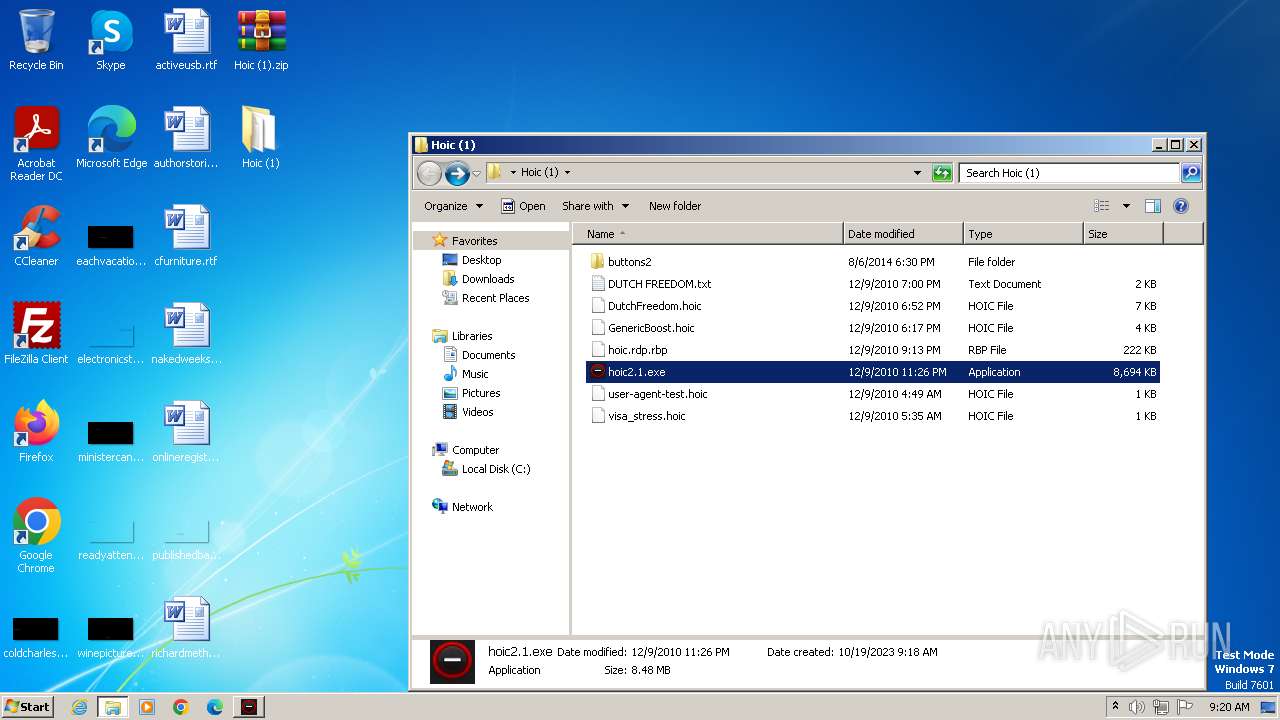
| File name: | Hoic (1).zip |
| Full analysis: | https://app.any.run/tasks/5d70caf4-87d5-4ffe-bbec-9d2cc2c0211b |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2023, 08:17:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 41D5D976B25E666BF56CAC445E9A9BE3 |
| SHA1: | 869CABAFA4B24AFCCF49A37912F8A8303009CAB3 |
| SHA256: | 64884C9C81E2B6E190349EF32D56B3D8910A52EEB2C061480CC76E9F2A9B56B0 |
| SSDEEP: | 98304:Q6ZFXGhlmIKxvw1wK8a60OxantBFOyvyFXw8GOvZPFL8U+9WT2+fV9D5LRnUnD0z:+xM |
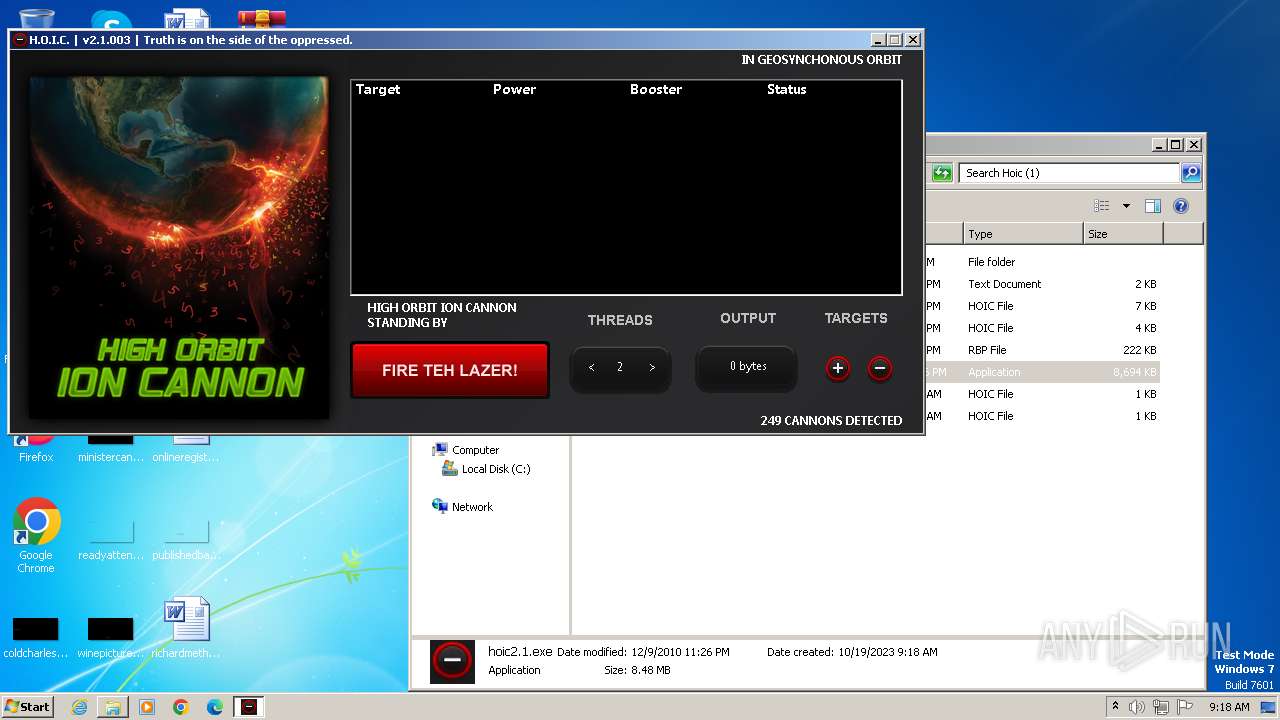
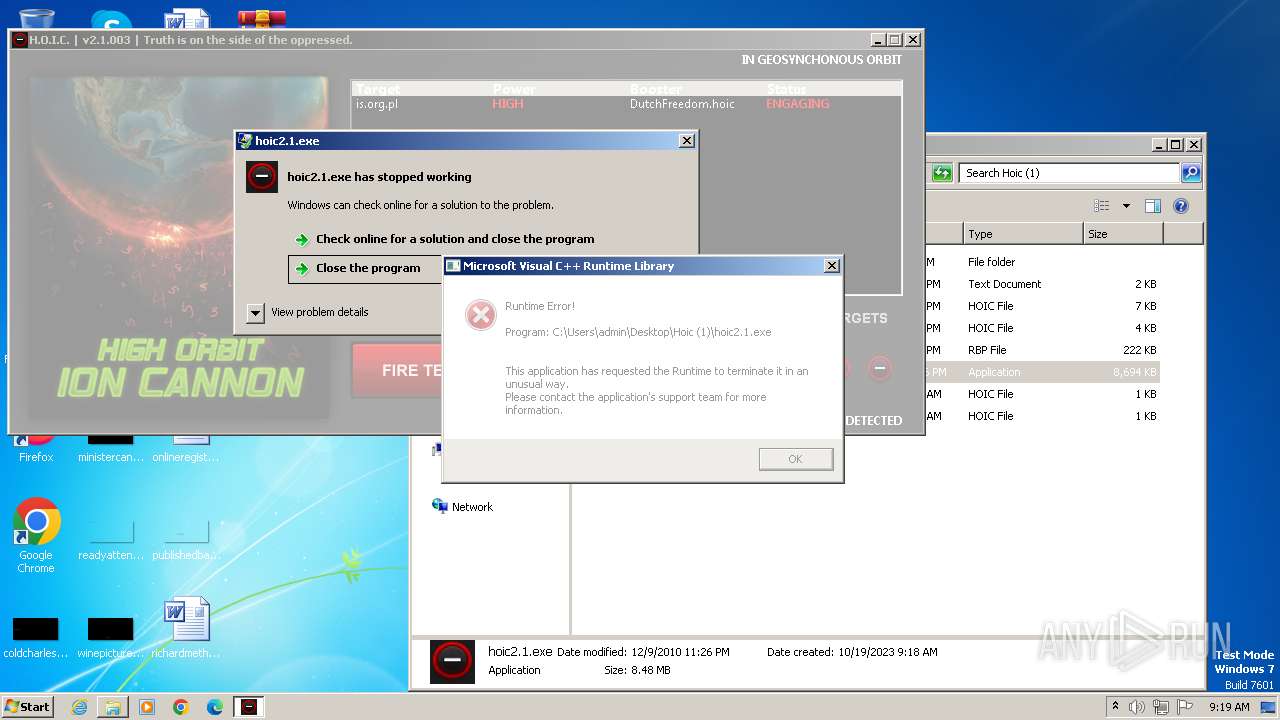
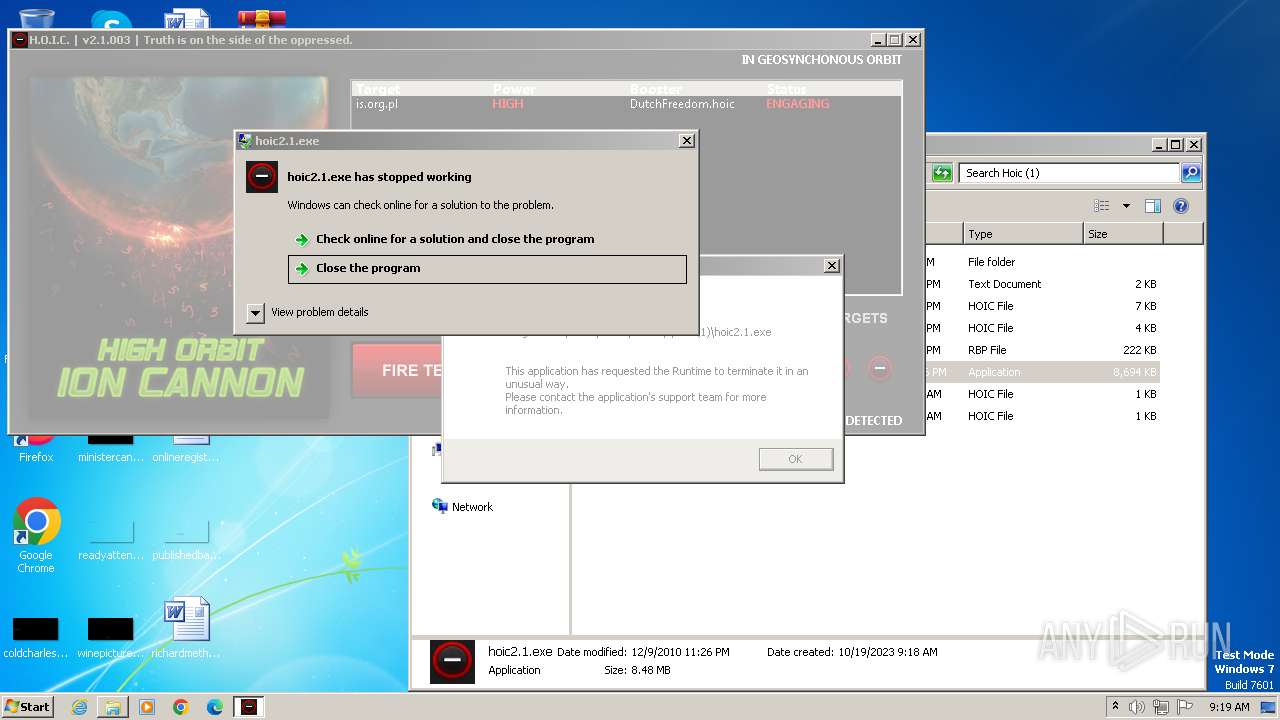
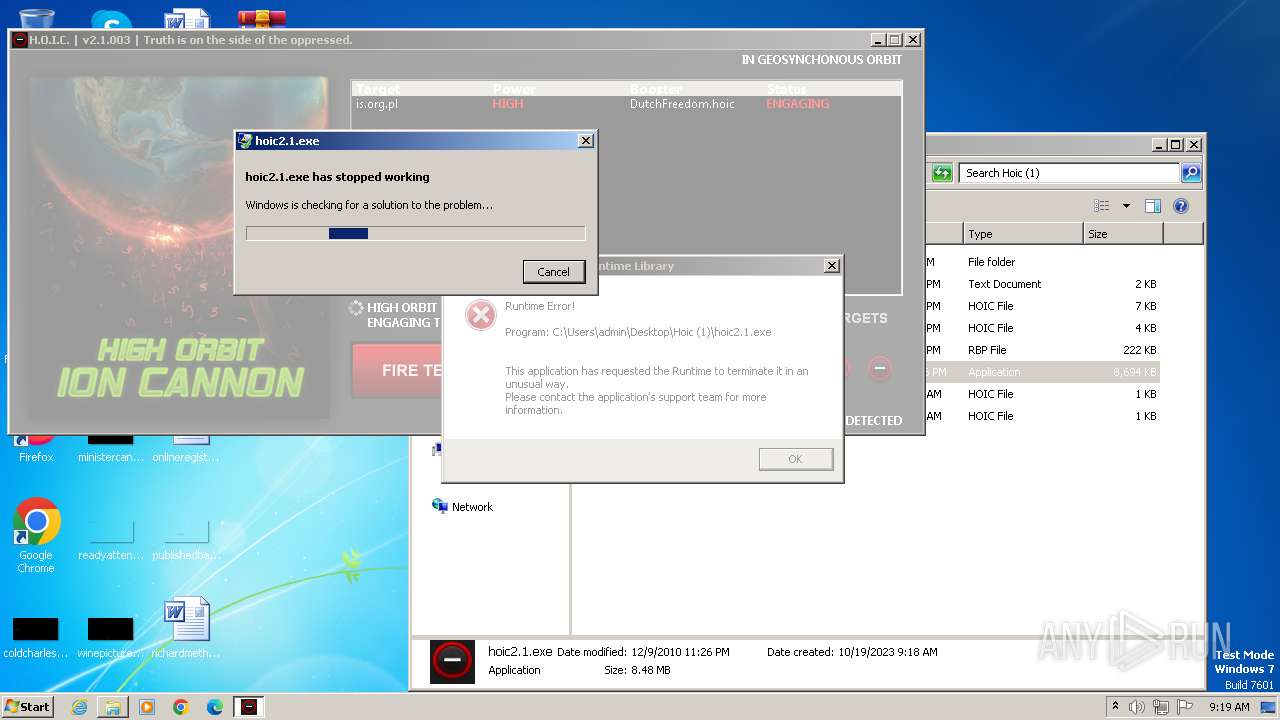
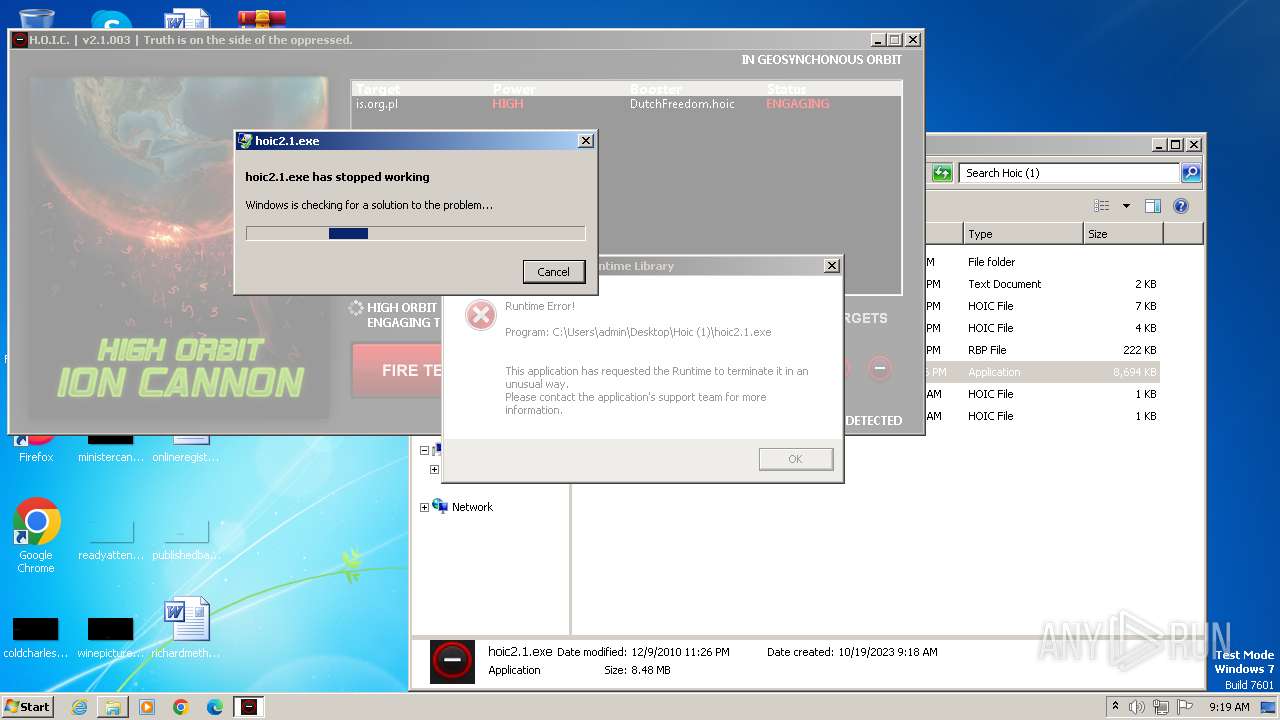
MALICIOUS
Application was dropped or rewritten from another process
- hoic2.1.exe (PID: 3800)
- hoic2.1.exe (PID: 3104)
- hoic2.1.exe (PID: 3664)
- hoic2.1.exe (PID: 3540)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- hoic2.1.exe (PID: 3800)
- hoic2.1.exe (PID: 3104)
- hoic2.1.exe (PID: 3664)
- hoic2.1.exe (PID: 3540)
Manual execution by a user
- hoic2.1.exe (PID: 3800)
- hoic2.1.exe (PID: 3104)
- hoic2.1.exe (PID: 3664)
- notepad.exe (PID: 2748)
- hoic2.1.exe (PID: 3540)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2980)
Reads the computer name
- hoic2.1.exe (PID: 3800)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2023:10:18 21:26:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Hoic (1)/ |
Total processes
49
Monitored processes
6
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2748 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\Hoic (1)\DUTCH FREEDOM.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2980 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Hoic (1).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3104 | "C:\Users\admin\Desktop\Hoic (1)\hoic2.1.exe" | C:\Users\admin\Desktop\Hoic (1)\hoic2.1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3540 | "C:\Users\admin\Desktop\Hoic (1)\hoic2.1.exe" | C:\Users\admin\Desktop\Hoic (1)\hoic2.1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3664 | "C:\Users\admin\Desktop\Hoic (1)\hoic2.1.exe" | C:\Users\admin\Desktop\Hoic (1)\hoic2.1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
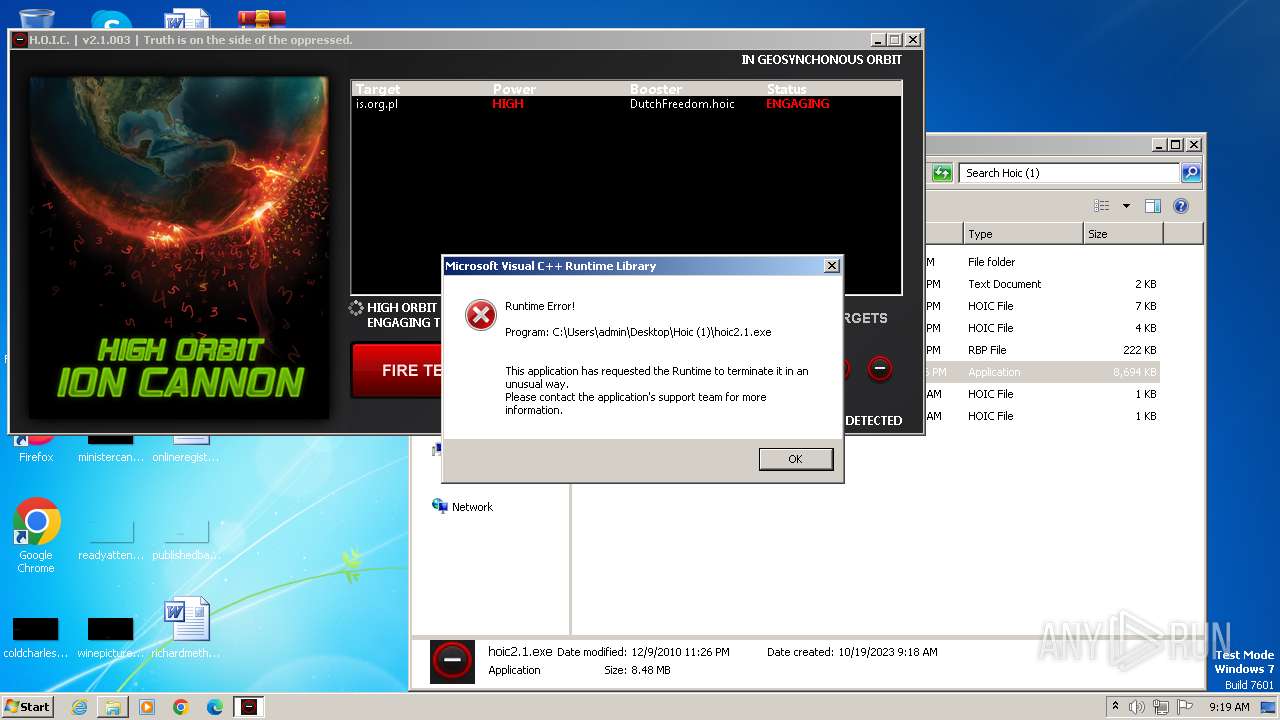
| 3800 | "C:\Users\admin\Desktop\Hoic (1)\hoic2.1.exe" | C:\Users\admin\Desktop\Hoic (1)\hoic2.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3765269347 Modules
| |||||||||||||||
Total events
1 320
Read events
1 300
Write events
20
Delete events
0
Modification events
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2980) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
1
Suspicious files
3
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2980 | WinRAR.exe | C:\Users\admin\Desktop\Hoic (1)\buttons2\buttons\removeqw.png | image | |
MD5:FFAB67111F3D2AB27A9AE03C37B36EDB | SHA256:2F6EA1BDF9F12B6895556EA29F711FB841E3943AAE1474EF204490EA97AE562C | |||
| 2980 | WinRAR.exe | C:\Users\admin\Desktop\Hoic (1)\buttons2\buttons\button5y.png | image | |
MD5:01DCD72AB51E145129EC54CAE7CBF1E5 | SHA256:0CFC00FEE98B9E9560F2BF5EDA15F664FB8AD73343E1FE6E3F99AB3A8CE0DC34 | |||
| 2980 | WinRAR.exe | C:\Users\admin\Desktop\Hoic (1)\buttons2\buttons\turbo2.png | image | |
MD5:FA31B0CF31B92BE8700F0C8C4059AE03 | SHA256:88B2530D9C727E79A143281D4BD9AEDEE7B9361EC30A73BA88633FC6D2C5AA99 | |||
| 2980 | WinRAR.exe | C:\Users\admin\Desktop\Hoic (1)\buttons2\buttons\add.png | image | |
MD5:8ADE13213352F64D34E561D2E0A0F454 | SHA256:720EDC5F500B86904DA5161206834EE942D3B60040A856898BD95F61DA53B2DA | |||
| 2980 | WinRAR.exe | C:\Users\admin\Desktop\Hoic (1)\buttons2\buttons\6666.png | image | |
MD5:B63B5663149586F34127FD3C47D26CCA | SHA256:6A914E505DD3613F634204F57C35AB1FAA8CFCDDB30C5585BA7EE843451AEDF2 | |||
| 2980 | WinRAR.exe | C:\Users\admin\Desktop\Hoic (1)\buttons2\buttons\add2.png | image | |
MD5:D98F80EDFA546F413106FAC5B1DE9877 | SHA256:CEBC482785696D2814F5ADB747BD0D5FA5A172186E1872D4F2253EBB05F43373 | |||
| 2980 | WinRAR.exe | C:\Users\admin\Desktop\Hoic (1)\buttons2\buttons\button - Copy.png | image | |
MD5:3E759A1FDC0A9CB94239284AF36AE651 | SHA256:F094C46AAB2663470C88BF883E8B641941DE70FF4D198C56A568D0EF74EEF94F | |||
| 2980 | WinRAR.exe | C:\Users\admin\Desktop\Hoic (1)\buttons2\buttons\button.png | image | |
MD5:3E759A1FDC0A9CB94239284AF36AE651 | SHA256:F094C46AAB2663470C88BF883E8B641941DE70FF4D198C56A568D0EF74EEF94F | |||
| 2980 | WinRAR.exe | C:\Users\admin\Desktop\Hoic (1)\buttons2\buttons\button4.png | image | |
MD5:01DCD72AB51E145129EC54CAE7CBF1E5 | SHA256:0CFC00FEE98B9E9560F2BF5EDA15F664FB8AD73343E1FE6E3F99AB3A8CE0DC34 | |||
| 2980 | WinRAR.exe | C:\Users\admin\Desktop\Hoic (1)\buttons2\buttons\lazer.png | image | |
MD5:5DFC0A47F6309048AE3A68208685C3B8 | SHA256:4D9D71BFF3429CA055DFFF9DADE55CADA219C495153B51D8F1D7831B7C66ECB5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1 036
TCP/UDP connections
2 003
DNS requests
3
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
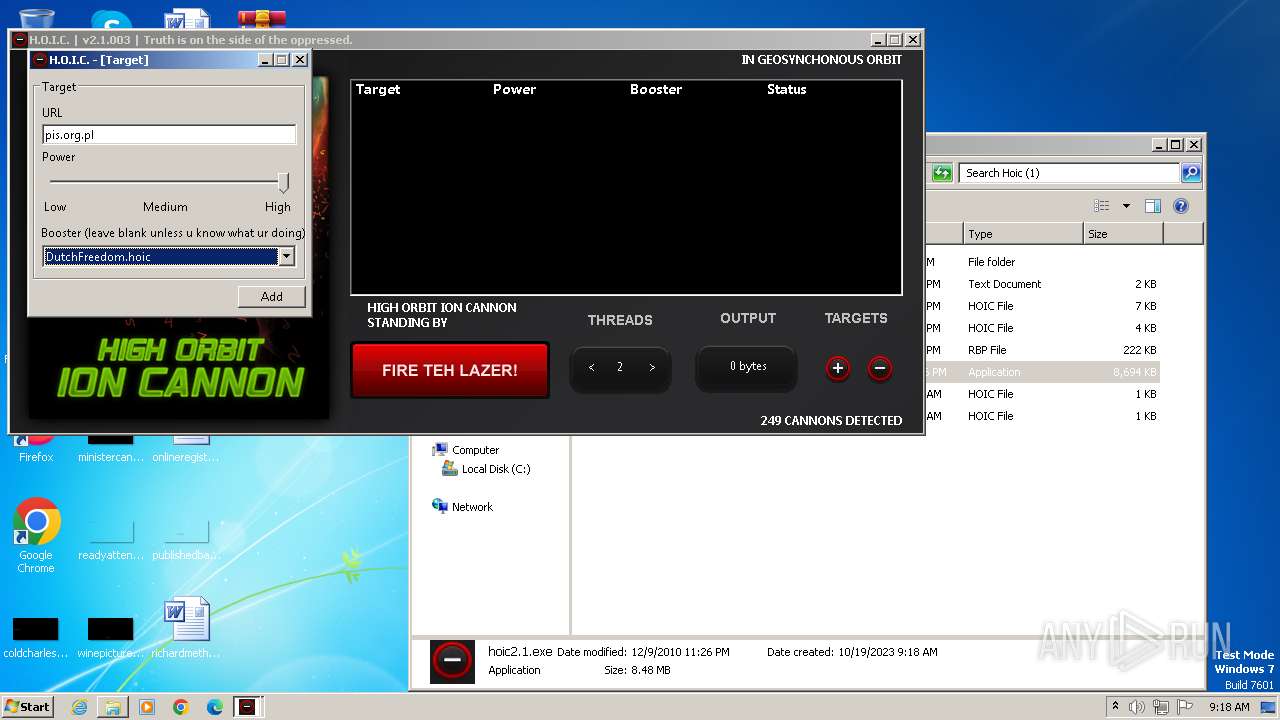
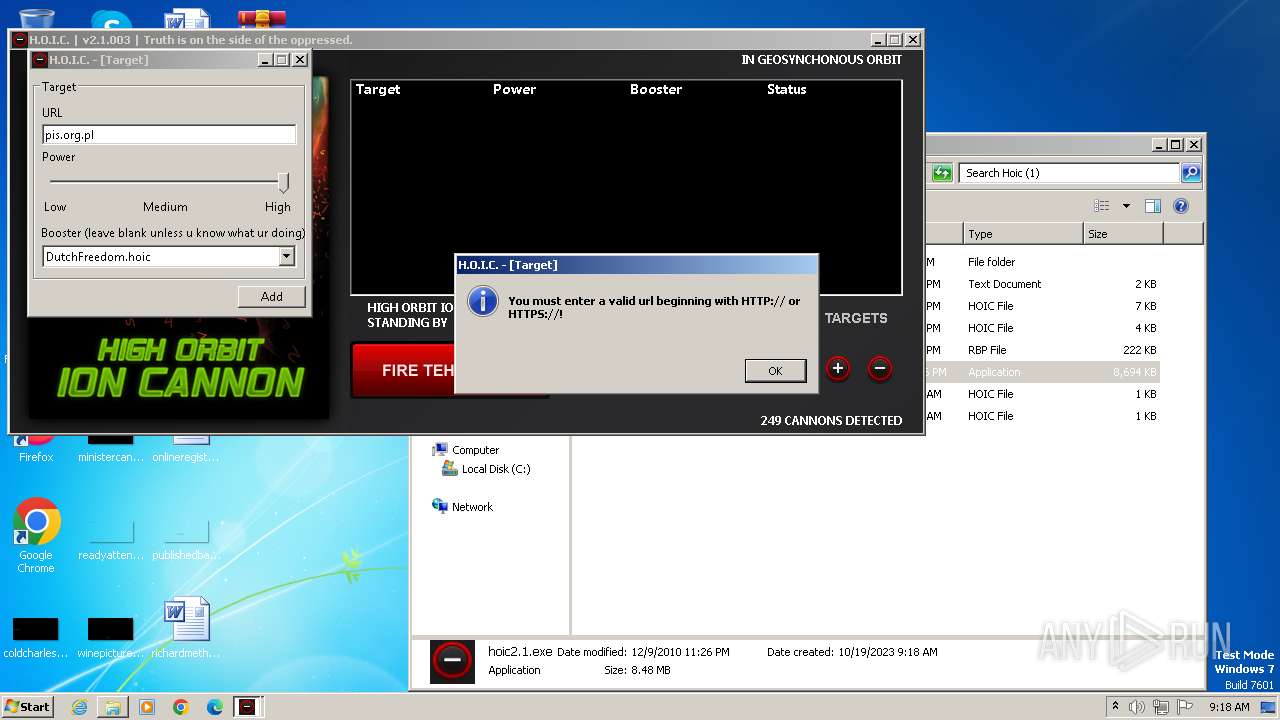
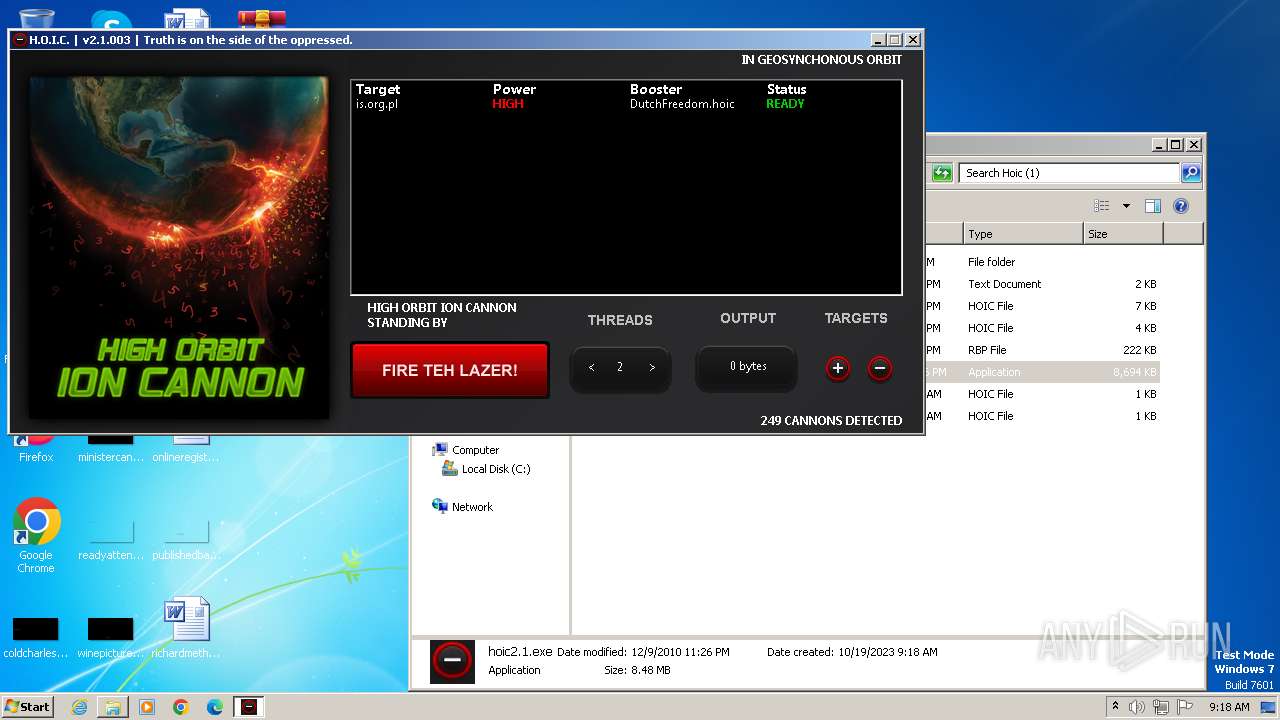
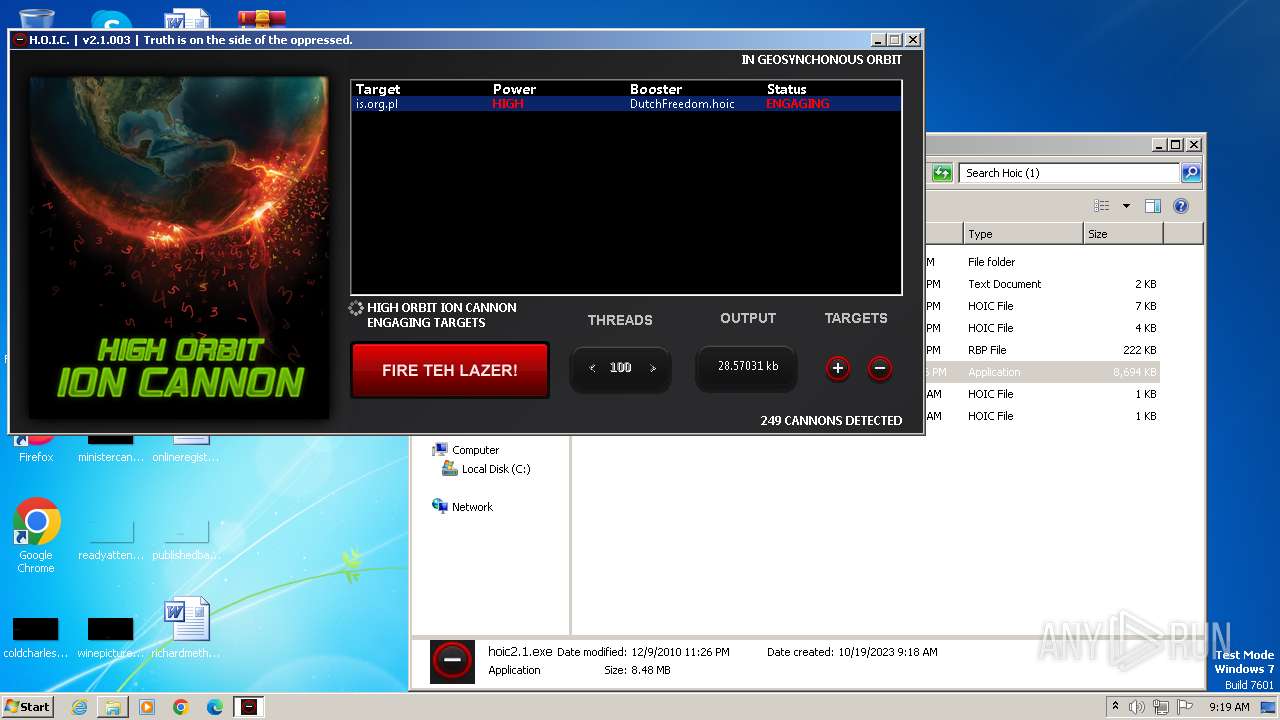
3800 | hoic2.1.exe | GET | 301 | 89.161.255.58:80 | http://pis.org.pl/ | unknown | html | 567 b | unknown |
3800 | hoic2.1.exe | GET | 301 | 89.161.255.58:80 | http://pis.org.pl/ | unknown | html | 567 b | unknown |
3800 | hoic2.1.exe | GET | 301 | 89.161.255.58:80 | http://pis.org.pl/ | unknown | html | 567 b | unknown |
3800 | hoic2.1.exe | GET | 301 | 89.161.255.58:80 | http://pis.org.pl/ | unknown | html | 567 b | unknown |
3800 | hoic2.1.exe | GET | 301 | 89.161.255.58:80 | http://pis.org.pl/ | unknown | html | 567 b | unknown |
3800 | hoic2.1.exe | GET | 301 | 89.161.255.58:80 | http://pis.org.pl/ | unknown | html | 567 b | unknown |
3800 | hoic2.1.exe | GET | 301 | 89.161.255.58:80 | http://pis.org.pl/ | unknown | html | 567 b | unknown |
3800 | hoic2.1.exe | GET | 301 | 89.161.255.58:80 | http://pis.org.pl/ | unknown | html | 567 b | unknown |
3800 | hoic2.1.exe | GET | 301 | 89.161.255.58:80 | http://pis.org.pl/ | unknown | html | 567 b | unknown |
3800 | hoic2.1.exe | GET | 301 | 89.161.255.58:80 | http://pis.org.pl/ | unknown | html | 567 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3800 | hoic2.1.exe | 89.161.255.58:80 | pis.org.pl | home.pl S.A. | PL | unknown |
3800 | hoic2.1.exe | 178.22.85.191:80 | www.om.nl | Prolocation B.V. | NL | unknown |
3724 | WerFault.exe | 104.208.16.93:443 | watson.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pis.org.pl |
| unknown |
www.om.nl |
| unknown |
watson.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3800 | hoic2.1.exe | A Network Trojan was detected | ET DOS HOIC with booster outbound |