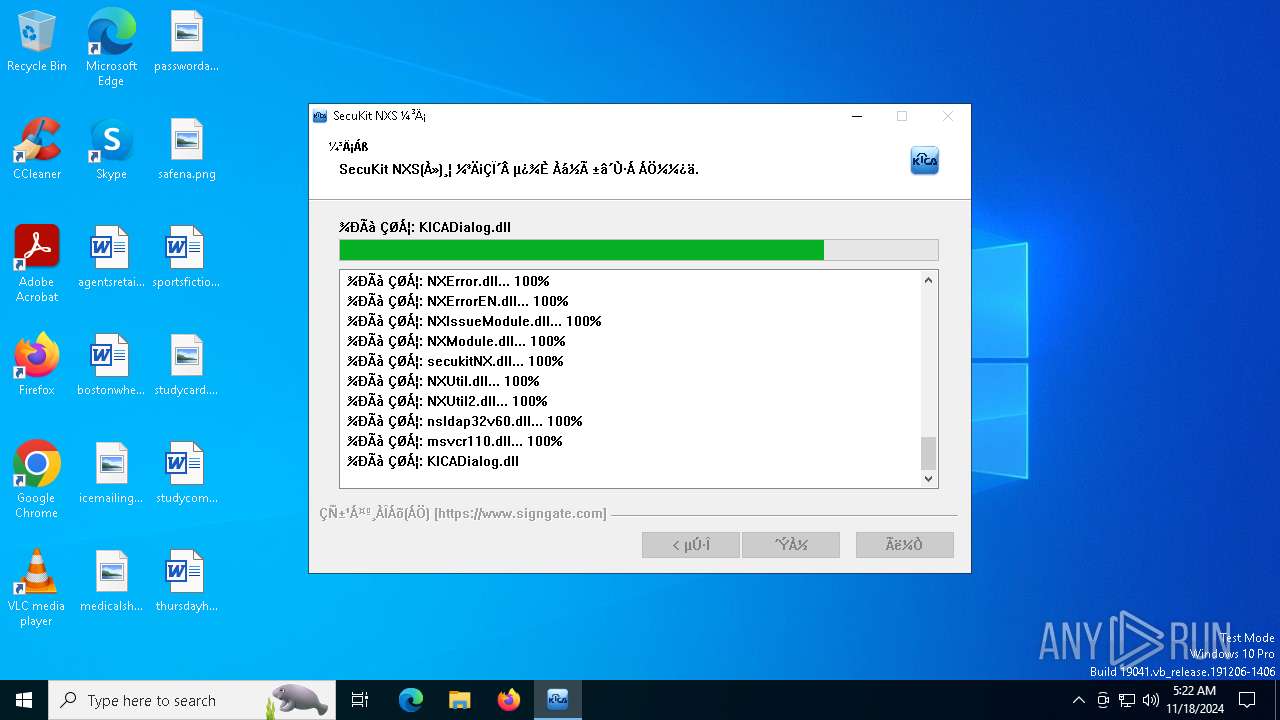
| File name: | SecuKitNXS.exe |
| Full analysis: | https://app.any.run/tasks/c65f874f-791b-4e04-80c5-b875a93c590c |
| Verdict: | Malicious activity |
| Analysis date: | November 18, 2024, 05:21:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | A25E2A5DA175218841FBEED5F3C77324 |
| SHA1: | 0431A669D682C2AF76732F2C0D24EBB49766AD86 |
| SHA256: | 64878AB75CD6548D7DFB7F824D9B926C7FF0E30318C6C8AF0BCAFE9A159B358F |
| SSDEEP: | 98304:B5I84Se958bPOOzaQN/Z9/W1I6stgJI65a+gI00eKAierEzZzDBSKpgiV6uqpQw6:B53QHvrTjn9 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- SecuKitNXS.exe (PID: 6220)
Process drops legitimate windows executable
- SecuKitNXS.exe (PID: 6220)
The process drops C-runtime libraries
- SecuKitNXS.exe (PID: 6220)
The process creates files with name similar to system file names
- SecuKitNXS.exe (PID: 6220)
Executable content was dropped or overwritten
- SecuKitNXS.exe (PID: 6220)
Executing commands from ".cmd" file
- SecuKitNXS.exe (PID: 6220)
Starts CMD.EXE for commands execution
- SecuKitNXS.exe (PID: 6220)
The executable file from the user directory is run by the CMD process
- certutil.exe (PID: 4144)
- certutil.exe (PID: 1732)
- certutil.exe (PID: 6024)
- certutil.exe (PID: 1068)
- certutil.exe (PID: 5592)
- certutil.exe (PID: 4072)
- certutil.exe (PID: 6564)
- certutil.exe (PID: 5952)
- certutil.exe (PID: 2620)
- certutil.exe (PID: 5584)
Executes as Windows Service
- kpmsvc.exe (PID: 1884)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3156)
INFO
Checks supported languages
- SecuKitNXS.exe (PID: 6220)
Create files in a temporary directory
- SecuKitNXS.exe (PID: 6220)
Reads the computer name
- SecuKitNXS.exe (PID: 6220)
Manual execution by a user
- OneDrive.exe (PID: 6336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:02 03:20:05+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 23552 |
| InitializedDataSize: | 120320 |
| UninitializedDataSize: | 1024 |
| EntryPoint: | 0x30fb |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.7.2 |
| ProductVersionNumber: | 1.0.7.2 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Korean |
| CharacterSet: | Windows, Korea (Shift - KSC 5601) |
| FileDescription: | SecuKit NXS Setup |
| FileVersion: | 1.0.7.2 |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| ProductName: | SecuKit NXS |
| ProductVersion: | 1.0.7.2 |
Total processes
152
Monitored processes
20
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
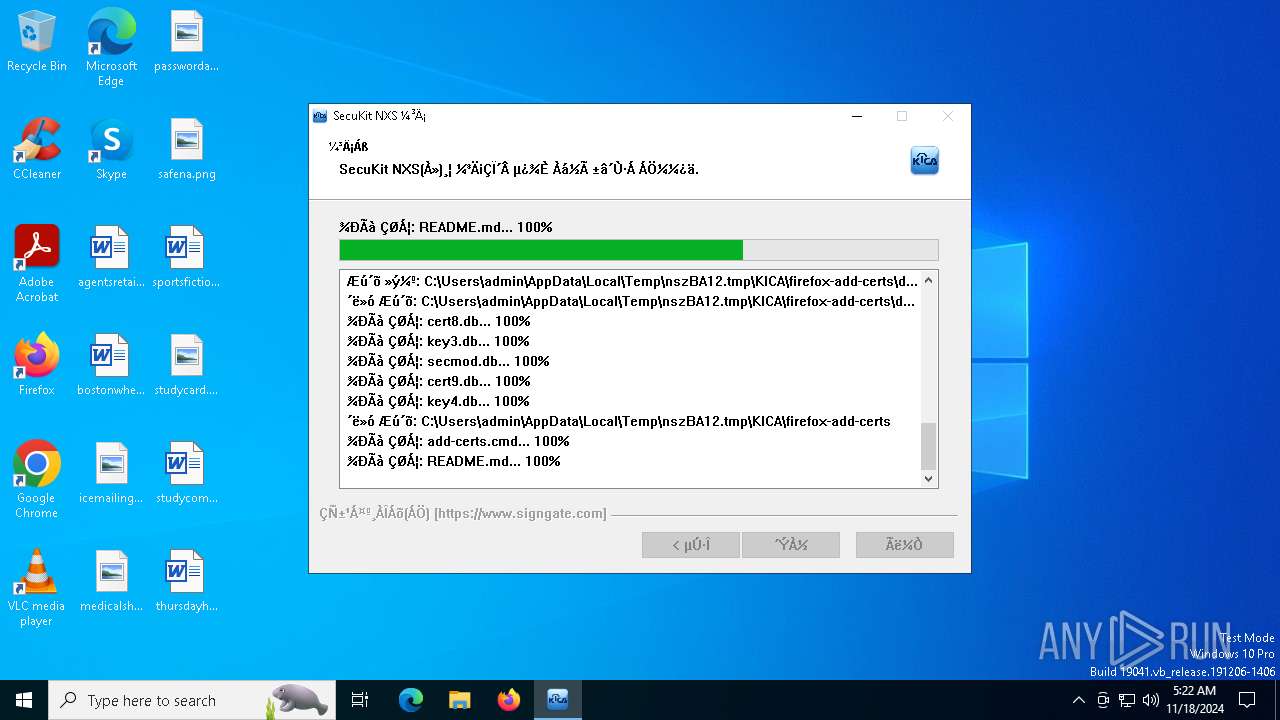
| 1068 | "C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\certutil.exe" -A -n "AddedByUser RootCA" -i "C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\cacert\RootCA.pem" -t "cTC,cTC,cTC", -d "dbm:C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\i17fj4h8.default" | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\certutil.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1732 | "C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\certutil.exe" -A -n "AddedByUser RootCA" -i "C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\cacert\RootCA.pem" -t "cTC,cTC,cTC", -d "sql:C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release" | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\certutil.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1884 | "C:\Program Files (x86)\KICA\Common\kpmsvc\kpmsvc.exe" | C:\Program Files (x86)\KICA\Common\kpmsvc\kpmsvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: KICA Inc. Integrity Level: SYSTEM Description: KICA Prosess Manager Service 1.1.5.0 Version: 1.1.5.2 Modules
| |||||||||||||||
| 2620 | "C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\certutil.exe" -L -d "C:\Program Files (x86)\Mozilla Firefox\browser\defaults\Profile" | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\certutil.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3156 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\add-certs.cmd"" | C:\Windows\SysWOW64\cmd.exe | — | SecuKitNXS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4072 | "C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\certutil.exe" -A -n "AddedByUser RootCA" -i "C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\cacert\RootCA.pem" -t "cTC,cTC,cTC", -d "sql:C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release" | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\certutil.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 4144 | "C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\certutil.exe" -A -n "AddedByUser RootCA" -i "C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\cacert\RootCA.pem" -t "cTC,cTC,cTC", -d "C:\Program Files (x86)\Mozilla Firefox\browser\defaults\Profile" | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\certutil.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 5356 | "C:\Program Files (x86)\KICA\Common\kpmsvc\kpmcnt.exe" | C:\Program Files (x86)\KICA\Common\kpmsvc\kpmcnt.exe | — | kpmsvc.exe | |||||||||||
User: admin Company: KICA Inc. Integrity Level: HIGH Description: KICA Process Manager Service Version: 1.1.5.8 Modules
| |||||||||||||||
| 5584 | "C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\certutil.exe" -A -n "AddedByUser RootCA" -i "C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\cacert\RootCA.pem" -t "cTC,cTC,cTC", -d "sql:C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\i17fj4h8.default" | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\certutil.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
5 034
Read events
4 865
Write events
161
Delete events
8
Modification events
| (PID) Process: | (6220) SecuKitNXS.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates |
| Operation: | delete value | Name: | 68C232D21D4B44F3403B0A5F8C92ED88E32804D3 |
Value: | |||
| (PID) Process: | (6220) SecuKitNXS.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\ROOT\Certificates\68C232D21D4B44F3403B0A5F8C92ED88E32804D3 |
| Operation: | write | Name: | Blob |
Value: 03000000010000001400000068C232D21D4B44F3403B0A5F8C92ED88E32804D320000000010000004C0300003082034830820230A003020102020101300D06092A864886F70D01010B0500303C310B3009060355040613024B5231123010060355040A0C094B49434120496E632E3119301706035504030C104B494341204E585320526F6F74204341301E170D3136303732363036313135335A170D3336303732313036313135335A303C310B3009060355040613024B5231123010060355040A0C094B49434120496E632E3119301706035504030C104B494341204E585320526F6F7420434130820122300D06092A864886F70D01010105000382010F003082010A0282010100A34806795010E27E7E86CD41442711DC7082903DC0044D50409FA2DF2817FECB6823A030BD731186D5B2947BEAB7555C416E92A36CD3166EDF736ACB5E252F8C0C047223A2C5418542C52E6F329CCB4CFD0B93C49EA20D8DFEB19ADB3415986055E5DED62D761A6C0952C7FD789A8B7902294431682569BE77C2F5FF63BC301B5AD1B8FEF7834A5002FFD65888283F7B92A4DFEAD5F352A5CE9AC7FFB02AA4BB677943CF671A65816194E8967FA2FB94D56A955A96B34976692E9FD20550D3DD40773FFE12F23203C20E21CFE6A3FE7F2CB56C63DE3C5C59FF56A8983DCF699CFA276134F984E8985B374196FB79BDFAAFFCB750F02C93316D23F4FC93AC20230203010001A355305330120603551D130101FF040830060101FF020100301D0603551D0E04160414048CC68BC2DC763BE33BEA388FE64DFA25E9F8AE300B0603551D0F040403020106301106096086480186F8420101040403020007300D06092A864886F70D01010B050003820101006BCD1E8F7F980AEC3E8F8E42A8D9D989541BF7A144AACB9A54E5AA0B47A93BBFC005C9ED2C33195423B1489C9E56F876E4D436B13D3E89C3A5E4D629D0DF811481190783F5F43B74A062B89B23F4E98D16DEA176F3256CBDDB823F9F624764564FF7395BCD63D7223E280370135D0C4F95C2878FD1D45F7D8D94AB756F3D435D50615D2EB63D937C3FDF723689F9B9B8C0642901B16EF9F77526C22204B2C034716F744DE5E3CFF84480B3CCAD619946C424A0B7E710000AE4D29518B62FAD1E0A8A75C0F17EFF723695077EE80D93F9651AC79865885931DA2AC2CCE6B42404B260FB6DE6CD790A812F676AC6AD6A07849E9EDC46E9448F0215797A74371197 | |||
| (PID) Process: | (6220) SecuKitNXS.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\SecuKit NXS |
| Operation: | write | Name: | DisplayName |
Value: SecuKit NXS | |||
| (PID) Process: | (6220) SecuKitNXS.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\SecuKit NXS |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\KICA\SecuKitNXS\NXUnInst.exe | |||
| (PID) Process: | (6220) SecuKitNXS.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\SecuKit NXS |
| Operation: | write | Name: | DisplayVersion |
Value: 1.0.7.2 | |||
| (PID) Process: | (6220) SecuKitNXS.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\SecuKit NXS |
| Operation: | write | Name: | URLInfoAbout |
Value: https://www.signgate.com | |||
| (PID) Process: | (6220) SecuKitNXS.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\SecuKit NXS |
| Operation: | write | Name: | Publisher |
Value: Çѱ¹Á¤º¸ÀÎÁõ(ÁÖ) | |||
| (PID) Process: | (6220) SecuKitNXS.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | kpmcnt.exe |
Value: C:\Program Files (x86)\KICA\Common\kpmsvc\kpmcnt.exe | |||
| (PID) Process: | (6336) OneDrive.exe | Key: | HKEY_CLASSES_ROOT\AppID\OneDrive.EXE |
| Operation: | write | Name: | AppID |
Value: {EEABD3A3-784D-4334-AAFC-BB13234F17CF} | |||
| (PID) Process: | (6336) OneDrive.exe | Key: | HKEY_CLASSES_ROOT\FileSyncClient.AutoPlayHandler\shell\import\DropTarget |
| Operation: | write | Name: | CLSID |
Value: {5999E1EE-711E-48D2-9884-851A709F543D} | |||
Executable files
33
Suspicious files
45
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6220 | SecuKitNXS.exe | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\nsDialogs.dll | executable | |
MD5:F832E4279C8FF9029B94027803E10E1B | SHA256:4CD17F660560934A001FC8E6FDCEA50383B78CA129FB236623A9666FCBD13061 | |||
| 6220 | SecuKitNXS.exe | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\COPYING | text | |
MD5:BDDEDB773E17C5704ACA39EAC9F71FA4 | SHA256:8D795AEAC957C8B6556B2ACA5E0A5A8B0B3254365D488BC62E280CB3255D441A | |||
| 6220 | SecuKitNXS.exe | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\sqlite3.dll | executable | |
MD5:3A58690AFF7051BB18EA9D764A450551 | SHA256:D2D0B729837574D2EB6ADAC4F819BC4F8534AC9A43B17663942B2401A02DB02A | |||
| 6220 | SecuKitNXS.exe | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\nsProcess.dll | executable | |
MD5:FAA7F034B38E729A983965C04CC70FC1 | SHA256:579A034FF5AB9B732A318B1636C2902840F604E8E664F5B93C07A99253B3C9CF | |||
| 6220 | SecuKitNXS.exe | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\LICENSE | text | |
MD5:17C0970E8C7B6A6BD33E0C66FE6DC514 | SHA256:112F7B1A5C192DD892F2D2092DF46109185AD9F5EB729EAC9770F48C352887DF | |||
| 6220 | SecuKitNXS.exe | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\nspr4.dll | executable | |
MD5:BD0E897DBC2DCC0CF1287FFD7C734CF0 | SHA256:2D2096447B366D6640F2670EDB474AB208D8D85B5650DB5E80CC985D1189F911 | |||
| 6220 | SecuKitNXS.exe | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\certutil.exe | executable | |
MD5:F8DA06687FB47CA2C355C38CA2766262 | SHA256:64AD18F4D9BEF01B86E39CA1E774DFA37DB46BC8267453C418DD7F723D6D014C | |||
| 6220 | SecuKitNXS.exe | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\freebl3.dll | executable | |
MD5:F474DD91BB12F230209EC3163CE7E6C4 | SHA256:F63B2CAB4B77AC63A1BECA66872A991E1F8233F2C513D42460DBF28C733B138C | |||
| 6220 | SecuKitNXS.exe | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\KICA\firefox-add-certs\bin\nssdbm3.dll | executable | |
MD5:8CC6A31974A175A65D6C090FEED39F42 | SHA256:F64111FAA9966D7B7859C6467BEDBD64559284B049F55FFADC54DFC50A3A4264 | |||
| 6220 | SecuKitNXS.exe | C:\Users\admin\AppData\Local\Temp\nszBA12.tmp\modern-wizard.bmp | image | |
MD5:A24AE230ACF3965DD4A191C8E2E49B7D | SHA256:B21EEADCAECE07CBC25CC17C5C9F915245771A3A79F5D5F6C627C5C290FCBDBF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
39
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
944 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6336 | OneDrive.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6676 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6676 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6336 | OneDrive.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6844 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2464 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4360 | SearchApp.exe | 104.126.37.139:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
944 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
944 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4360 | SearchApp.exe | 104.126.37.131:443 | th.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |