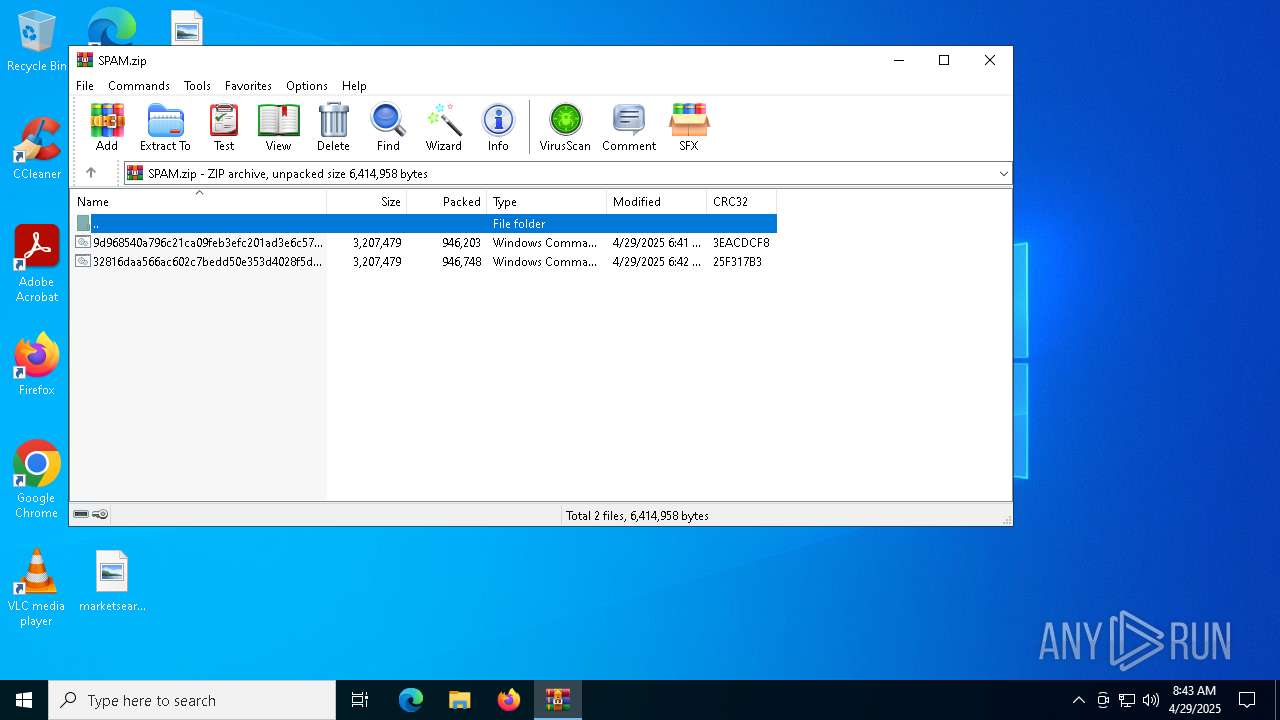
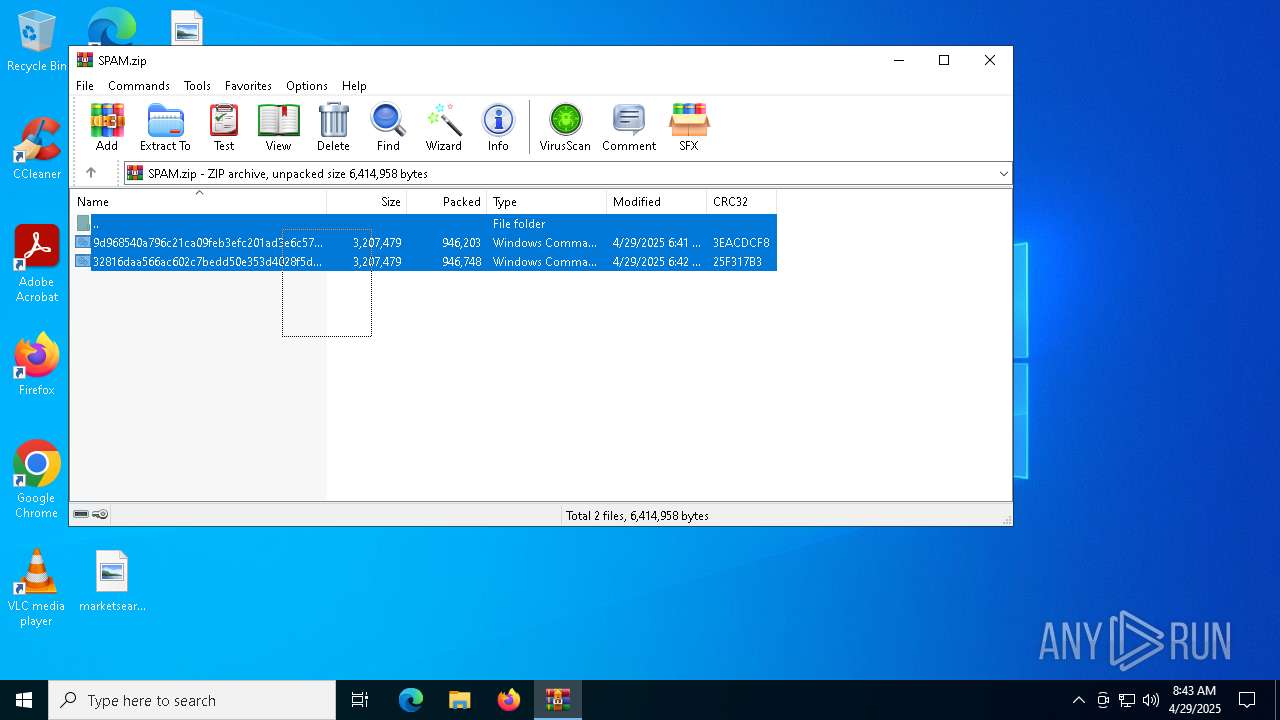
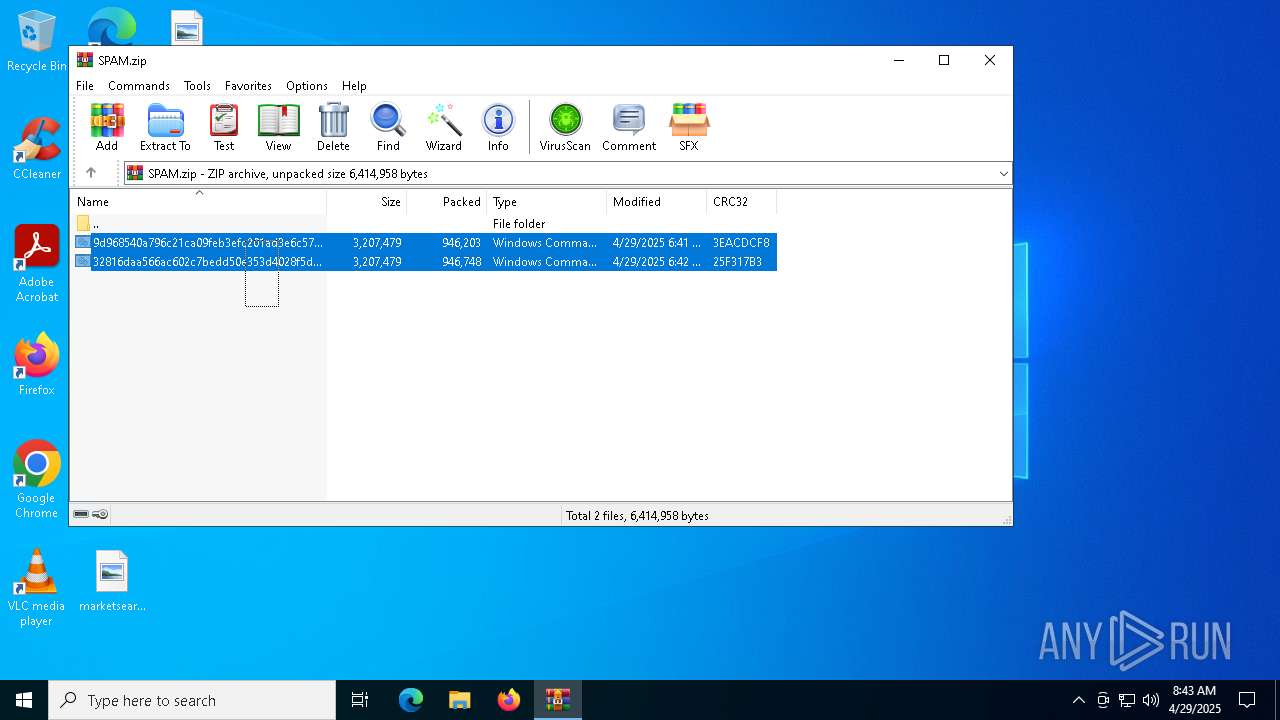
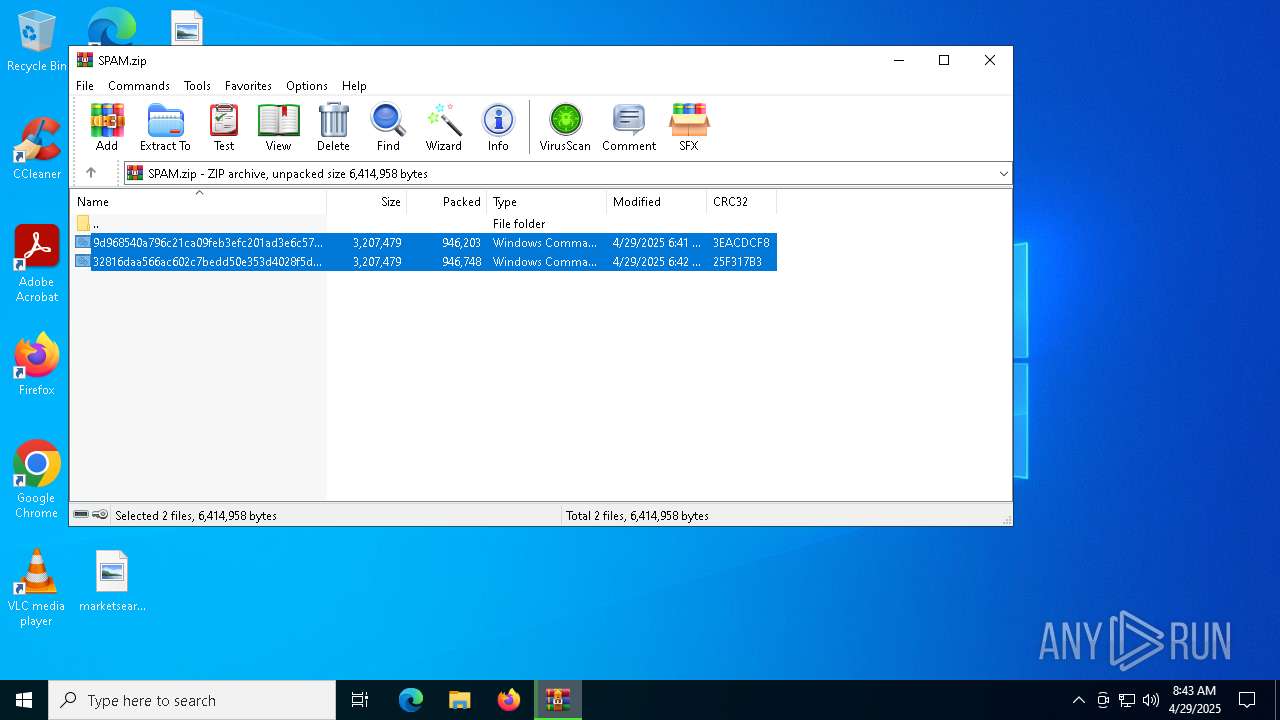
| File name: | SPAM.zip |
| Full analysis: | https://app.any.run/tasks/16ff55bc-4a49-4d41-a2f1-c96930d5c2e9 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 08:43:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 06A3256501936448026A6C91B0D227F9 |
| SHA1: | 251FBA2FD359BB71C04D0F7A68CAC1BA31F20A1E |
| SHA256: | 6484BD162B09F19383F6A67E8C2B94610EBDBE662102868AAEB6F17A29E08AED |
| SSDEEP: | 98304:KacwEiAHBE9Y82k7HKQ3P06YReIh2DuPK6vtJbNUP7/htacwEiAHBE9Y82k7HKQZ:uWi |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7204)
SUSPICIOUS
Drops a file with a rarely used extension (PIF)
- extrac32.exe (PID: 7716)
- expha.pif (PID: 7740)
- expha.pif (PID: 7764)
- expha.pif (PID: 7788)
- ghf.pif (PID: 7872)
- extrac32.exe (PID: 8124)
- expha.pif (PID: 8184)
- expha.pif (PID: 5956)
- expha.pif (PID: 8160)
- chrome.PIF (PID: 7988)
Executable content was dropped or overwritten
- extrac32.exe (PID: 7716)
- expha.pif (PID: 7740)
- expha.pif (PID: 7764)
- expha.pif (PID: 7788)
- ghf.pif (PID: 7872)
- extrac32.exe (PID: 8124)
- expha.pif (PID: 8184)
- expha.pif (PID: 8160)
- expha.pif (PID: 5956)
Process drops legitimate windows executable
- extrac32.exe (PID: 7716)
- expha.pif (PID: 7740)
- expha.pif (PID: 7764)
- extrac32.exe (PID: 8124)
- expha.pif (PID: 8160)
- expha.pif (PID: 8184)
Starts application with an unusual extension
- cmd.exe (PID: 7652)
- alpha.pif (PID: 7856)
- alpha.pif (PID: 7812)
- rdha.pif (PID: 7952)
- cmd.exe (PID: 8060)
- alpha.pif (PID: 5576)
- alpha.pif (PID: 5556)
- rdha.pif (PID: 1660)
Process drops legitimate windows executable (CertUtil.exe)
- expha.pif (PID: 7788)
- expha.pif (PID: 5956)
Starts itself from another location
- cmd.exe (PID: 7652)
- cmd.exe (PID: 8060)
Reads security settings of Internet Explorer
- rdha.pif (PID: 7952)
- rdha.pif (PID: 1660)
- chrome.PIF (PID: 7988)
- chrome.PIF (PID: 6272)
Runs PING.EXE to delay simulation
- alpha.pif (PID: 7900)
- alpha.pif (PID: 4608)
Reads the date of Windows installation
- rdha.pif (PID: 7952)
- rdha.pif (PID: 1660)
Application launched itself
- cmd.exe (PID: 7652)
- cmd.exe (PID: 8060)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 7652)
- cmd.exe (PID: 8060)
There is functionality for taking screenshot (YARA)
- chrome.PIF (PID: 7988)
- chrome.PIF (PID: 6272)
INFO
Manual execution by a user
- cmd.exe (PID: 7652)
- cmd.exe (PID: 8060)
Checks supported languages
- extrac32.exe (PID: 7716)
- expha.pif (PID: 7740)
- expha.pif (PID: 7764)
- ghf.pif (PID: 7872)
- alpha.pif (PID: 7812)
- ghf.pif (PID: 7828)
- rdha.pif (PID: 7952)
- alpha.pif (PID: 7900)
- chrome.PIF (PID: 7988)
- extrac32.exe (PID: 8124)
- expha.pif (PID: 8160)
- expha.pif (PID: 8184)
- expha.pif (PID: 5956)
- alpha.pif (PID: 5576)
- expha.pif (PID: 7788)
- ghf.pif (PID: 2432)
- alpha.pif (PID: 5556)
- ghf.pif (PID: 4868)
- alpha.pif (PID: 4608)
- rdha.pif (PID: 1660)
- alpha.pif (PID: 7856)
- chrome.PIF (PID: 6272)
Reads the computer name
- extrac32.exe (PID: 7716)
- ghf.pif (PID: 7828)
- ghf.pif (PID: 7872)
- rdha.pif (PID: 7952)
- extrac32.exe (PID: 8124)
- ghf.pif (PID: 4868)
- ghf.pif (PID: 2432)
- rdha.pif (PID: 1660)
- chrome.PIF (PID: 7988)
- chrome.PIF (PID: 6272)
The sample compiled with english language support
- expha.pif (PID: 7740)
- extrac32.exe (PID: 7716)
- expha.pif (PID: 7764)
- expha.pif (PID: 7788)
- extrac32.exe (PID: 8124)
- expha.pif (PID: 8160)
- expha.pif (PID: 8184)
- expha.pif (PID: 5956)
Creates files in the program directory
- expha.pif (PID: 7764)
- extrac32.exe (PID: 7716)
- expha.pif (PID: 7740)
- expha.pif (PID: 7788)
- ghf.pif (PID: 7872)
- ghf.pif (PID: 7828)
- extrac32.exe (PID: 8124)
- expha.pif (PID: 8160)
- expha.pif (PID: 8184)
- expha.pif (PID: 5956)
- ghf.pif (PID: 4868)
Process checks computer location settings
- rdha.pif (PID: 7952)
- rdha.pif (PID: 1660)
Reads the machine GUID from the registry
- chrome.PIF (PID: 7988)
- chrome.PIF (PID: 6272)
Reads the software policy settings
- chrome.PIF (PID: 7988)
- chrome.PIF (PID: 6272)
- slui.exe (PID: 2268)
Compiled with Borland Delphi (YARA)
- chrome.PIF (PID: 7988)
- chrome.PIF (PID: 6272)
Checks proxy server information
- chrome.PIF (PID: 7988)
- chrome.PIF (PID: 6272)
- slui.exe (PID: 2268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:29 08:42:14 |
| ZipCRC: | 0x25f317b3 |
| ZipCompressedSize: | 946748 |
| ZipUncompressedSize: | 3207479 |
| ZipFileName: | 32816daa566ac602c7bedd50e353d4028f5dc0baef3efc4a2f22a78f5cb52c4d.cmd |
Total processes
182
Monitored processes
37
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1660 | C:\\ProgramData\\rdha.pif zipfldr.dll,RouteTheCall C:\\ProgramData\\chrome.PIF | C:\ProgramData\rdha.pif | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | PING -n 1 127.0.0.1 | C:\Windows\System32\PING.EXE | — | alpha.pif | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2092 | "C:\WINDOWS\system32\UCPDMgr.exe" | C:\Windows\System32\UCPDMgr.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: User Choice Protection Manager Exit code: 0 Version: 1.0.0.414301 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2268 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2432 | C:\\ProgramData\\ghf.pif -decodehex -f "C:\\ProgramData\\donex.avi" "C:\\ProgramData\\chrome.PIF" 12 | C:\ProgramData\ghf.pif | — | alpha.pif | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 2147942432 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2656 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4608 | C:\\ProgramData\\alpha.pif /c PING -n 1 127.0.0.1 | C:\ProgramData\alpha.pif | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4868 | C:\\ProgramData\\ghf.pif -decodehex -f "C:\Users\admin\Desktop\9d968540a796c21ca09feb3efc201ad3e6c57fce267ba05a08a337dd1e14aacf.cmd" "C:\\ProgramData\\donex.avi" 9 | C:\ProgramData\ghf.pif | — | alpha.pif | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5556 | C:\\ProgramData\\alpha.pif /C C:\\ProgramData\\ghf.pif -decodehex -f "C:\\ProgramData\\donex.avi" "C:\\ProgramData\\chrome.PIF" 12 | C:\ProgramData\alpha.pif | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 2147942432 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 568
Read events
13 548
Write events
20
Delete events
0
Modification events
| (PID) Process: | (7204) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7204) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7204) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7204) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SPAM.zip | |||
| (PID) Process: | (7204) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7204) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7204) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7204) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7204) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (7204) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
9
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7988 | chrome.PIF | C:\Users\admin\Links\ahgqwnzH.pif | — | |
MD5:— | SHA256:— | |||
| 7716 | extrac32.exe | C:\ProgramData\expha.pif | executable | |
MD5:41330D97BF17D07CD4308264F3032547 | SHA256:A224559FD6621066347A5BA8F4AEECEEA8A0A7A881A71BD36DE69ACEB52E9DF7 | |||
| 7204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7204.3134\32816daa566ac602c7bedd50e353d4028f5dc0baef3efc4a2f22a78f5cb52c4d.cmd | text | |
MD5:6CC316407815CB436004FA3233BE7067 | SHA256:32816DAA566AC602C7BEDD50E353D4028F5DC0BAEF3EFC4A2F22A78F5CB52C4D | |||
| 4868 | ghf.pif | C:\ProgramData\donex.avi | text | |
MD5:C351D470389095B4D9FF905027D47303 | SHA256:4A6217650FD04F7A3BA1CC105F7FD3A5A4398A24FF8644EE7395283BDC623183 | |||
| 7204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7204.3134\9d968540a796c21ca09feb3efc201ad3e6c57fce267ba05a08a337dd1e14aacf.cmd | text | |
MD5:00B10A741EB8F2C914F83CB048DD174D | SHA256:9D968540A796C21CA09FEB3EFC201AD3E6C57FCE267BA05A08A337DD1E14AACF | |||
| 7764 | expha.pif | C:\ProgramData\rdha.pif | executable | |
MD5:100F56A73211E0B2BCD076A55E6393FD | SHA256:00BE065F405E93233CC2F0012DEFDCBB1D6817B58969D5FFD9FD72FC4783C6F4 | |||
| 8124 | extrac32.exe | C:\ProgramData\expha.pif | executable | |
MD5:41330D97BF17D07CD4308264F3032547 | SHA256:A224559FD6621066347A5BA8F4AEECEEA8A0A7A881A71BD36DE69ACEB52E9DF7 | |||
| 8184 | expha.pif | C:\ProgramData\rdha.pif | executable | |
MD5:100F56A73211E0B2BCD076A55E6393FD | SHA256:00BE065F405E93233CC2F0012DEFDCBB1D6817B58969D5FFD9FD72FC4783C6F4 | |||
| 7788 | expha.pif | C:\ProgramData\ghf.pif | executable | |
MD5:A7A5B67EC704EAC6D6E6AF0489353F42 | SHA256:BF072F9A6A15B550B13AE86A4FBD3FA809D2A13236847AE9FA9A68F41386106E | |||
| 7872 | ghf.pif | C:\ProgramData\chrome.PIF | executable | |
MD5:35DC1AE3A76A35A4BBEA41CE8CDEC76C | SHA256:676122E3483CF9D3BBF0407FD8B3C4A5E3EED475D59F45DDC1FE17192F96F48B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
62
TCP/UDP connections
102
DNS requests
28
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6436 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
— | — | GET | 200 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 304 | 172.202.163.200:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 20.3.187.198:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
7468 | SIHClient.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7468 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7468 | SIHClient.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
7468 | SIHClient.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.20:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
6436 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2516 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6436 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
link.storjshare.io |
| malicious |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7988 | chrome.PIF | Potentially Bad Traffic | ET INFO Observed File Sharing Service Domain (link .storjshare .io in TLS SNI) |
2196 | svchost.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Service Domain in DNS Lookup (link .storjshare .io) |
2196 | svchost.exe | Misc activity | ET TA_ABUSED_SERVICES Commonly Actor Abused Online Service Domain (storjshare .io) |
7988 | chrome.PIF | Misc activity | ET TA_ABUSED_SERVICES Observed Commonly Actor Abused Online Service Domain (storjshare .io in TLS SNI) |
6272 | chrome.PIF | Potentially Bad Traffic | ET INFO Observed File Sharing Service Domain (link .storjshare .io in TLS SNI) |
6272 | chrome.PIF | Misc activity | ET TA_ABUSED_SERVICES Observed Commonly Actor Abused Online Service Domain (storjshare .io in TLS SNI) |