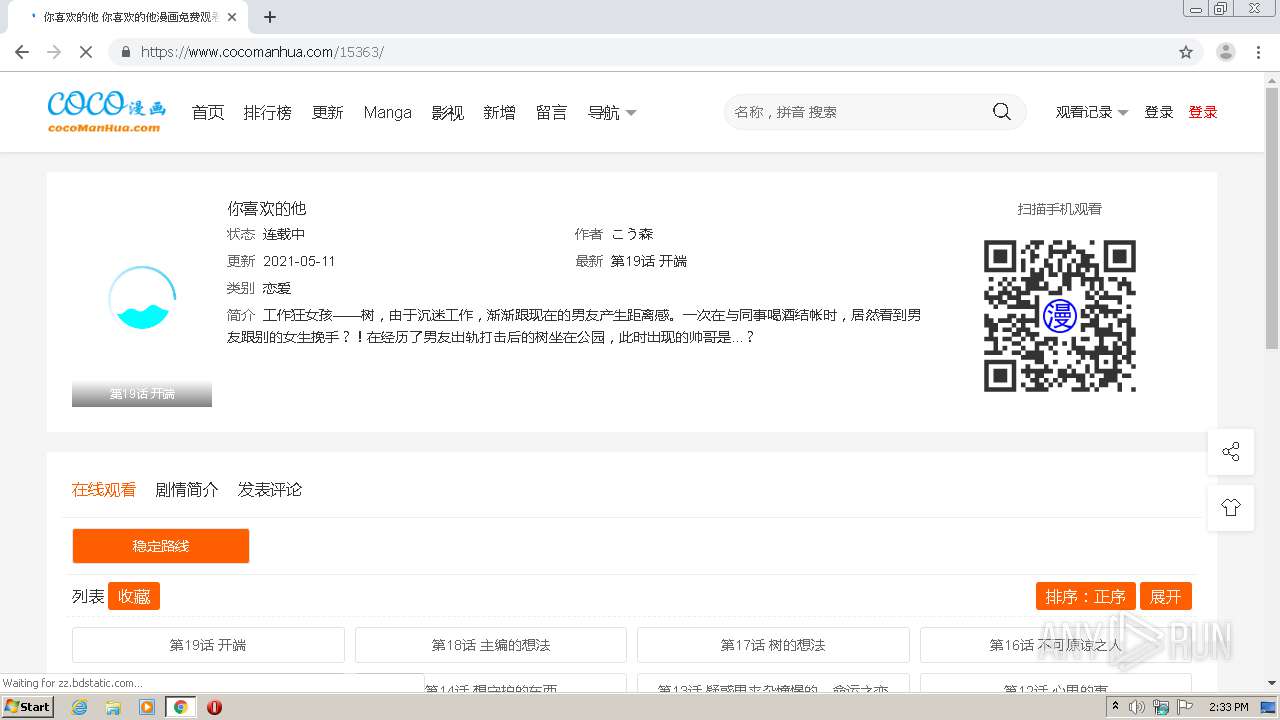
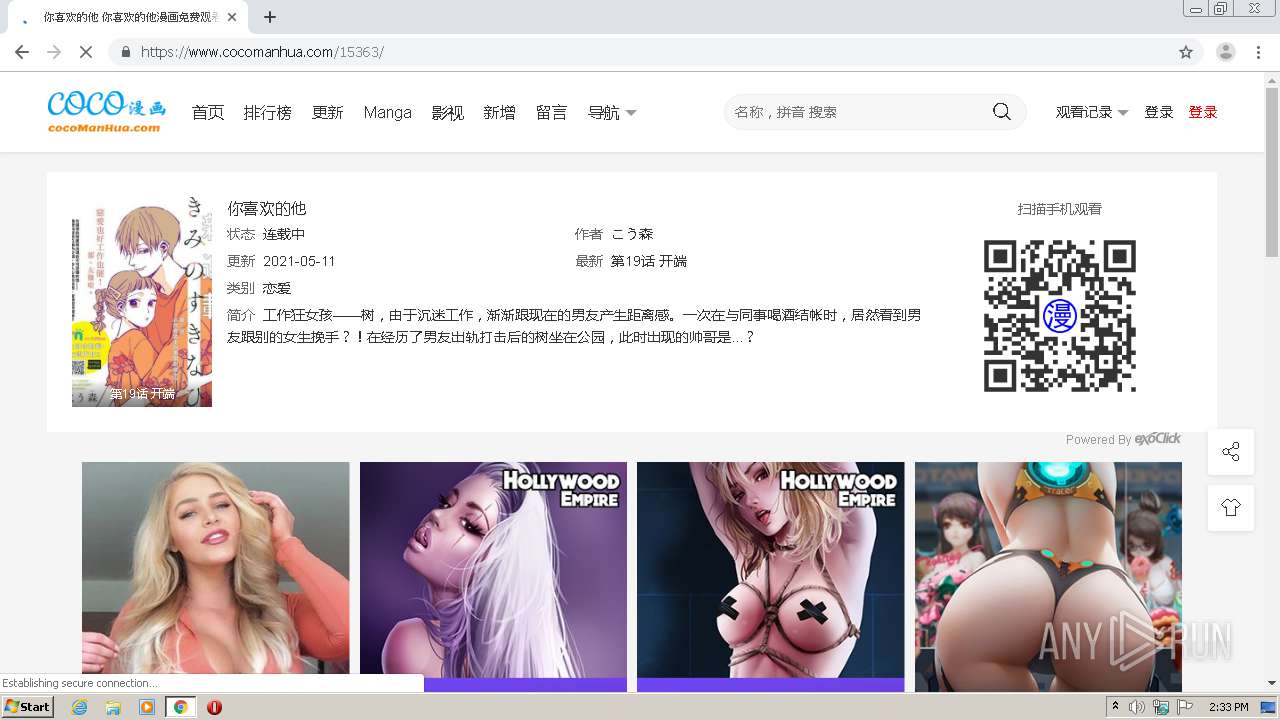
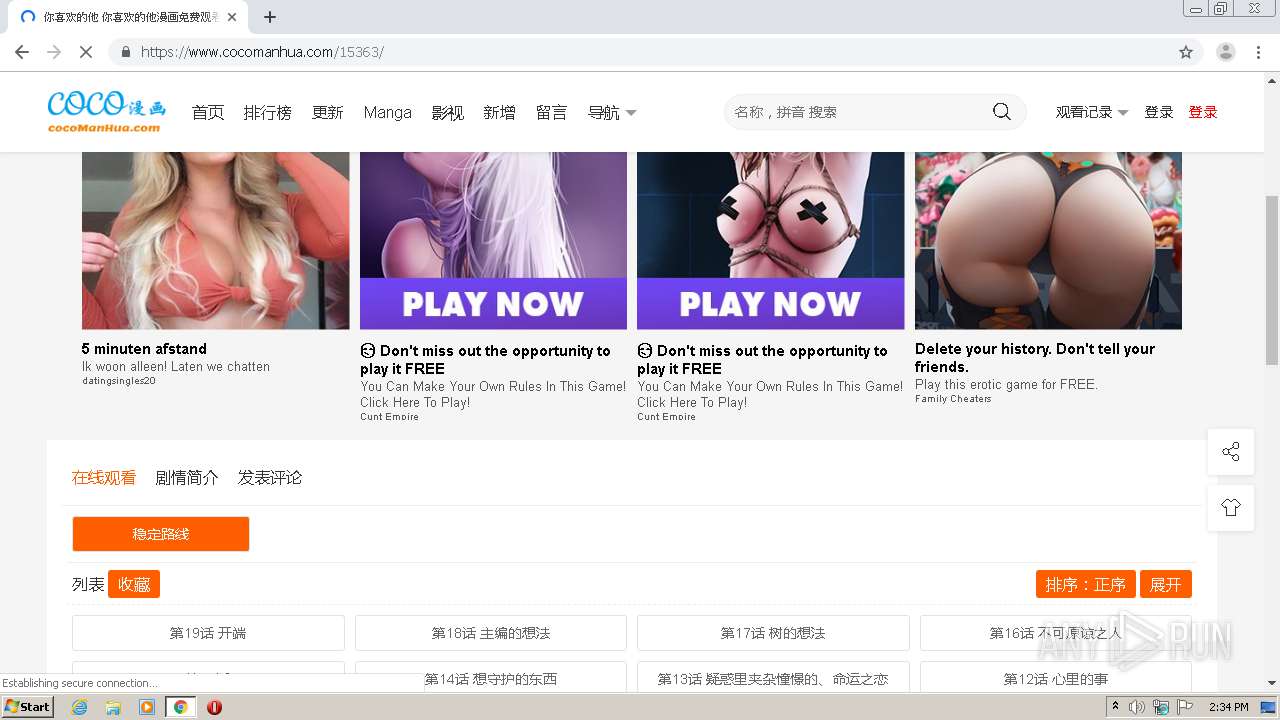
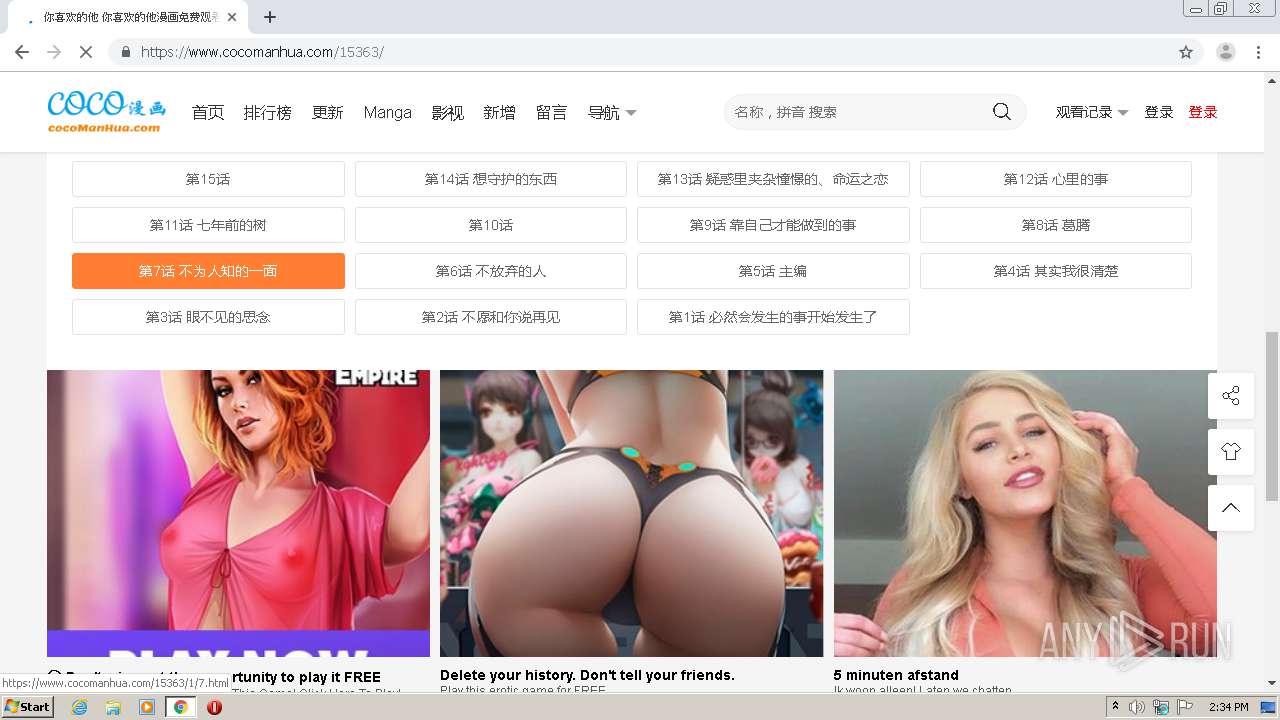
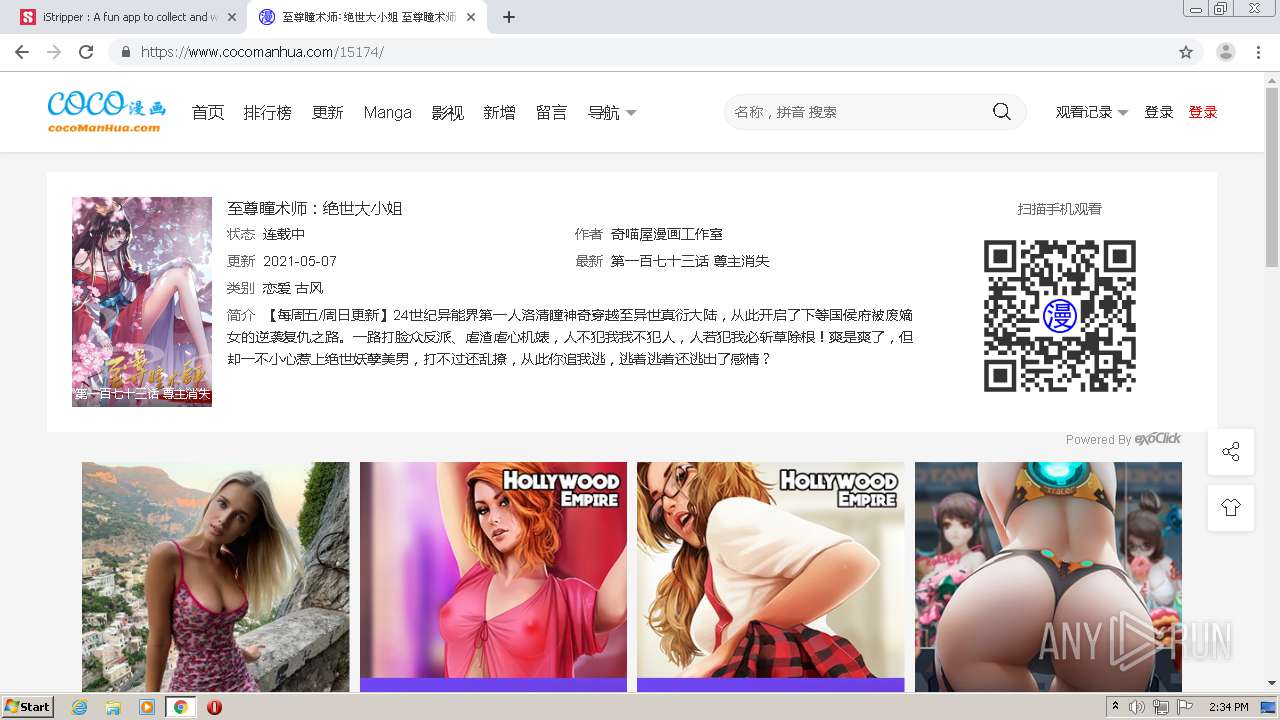
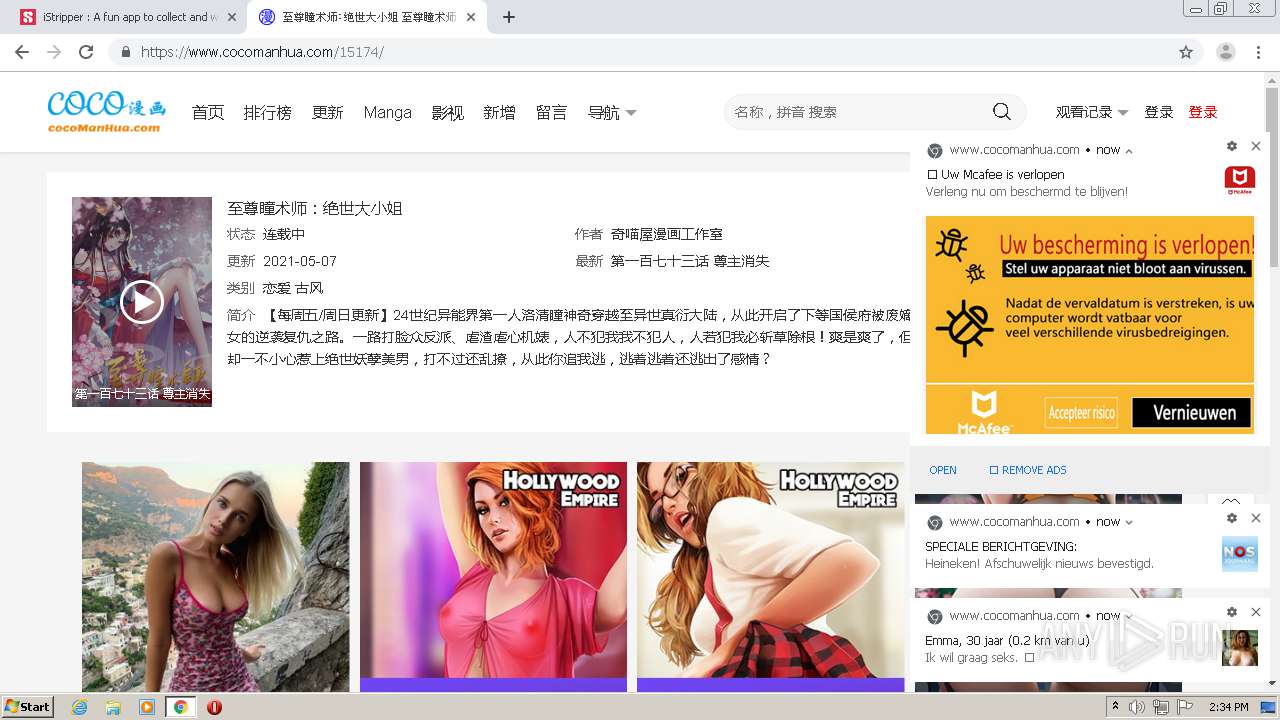
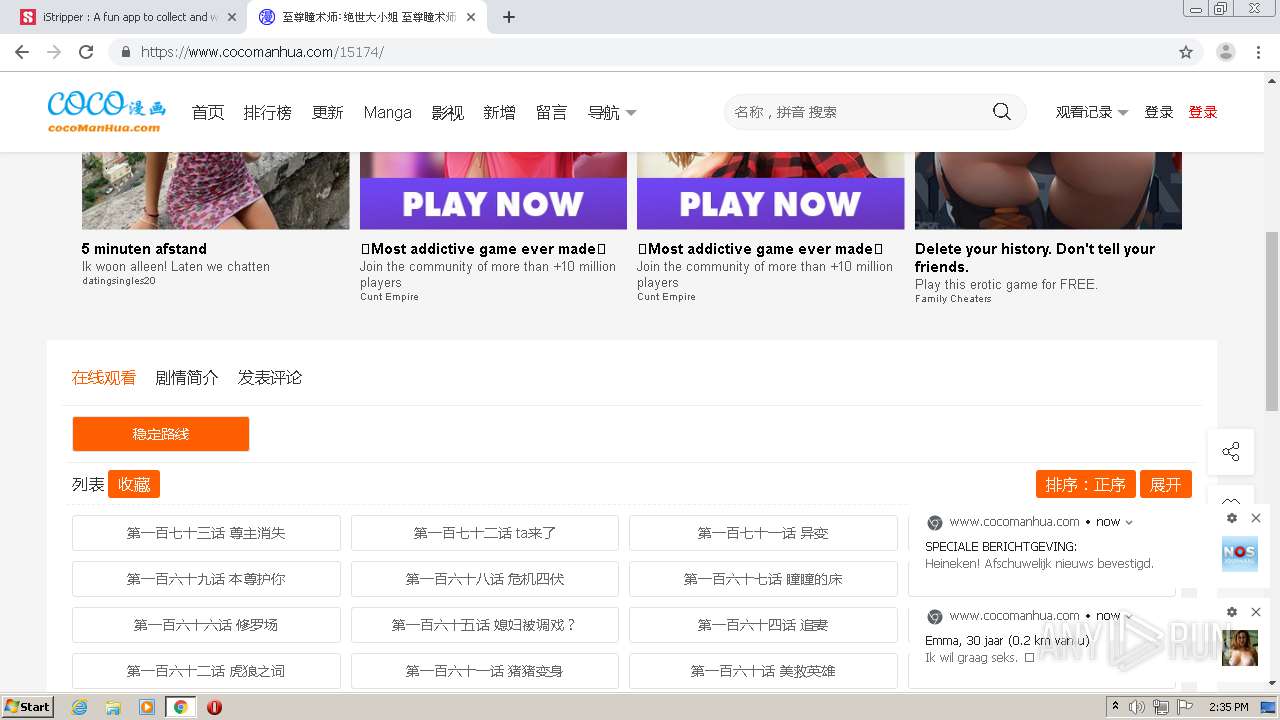
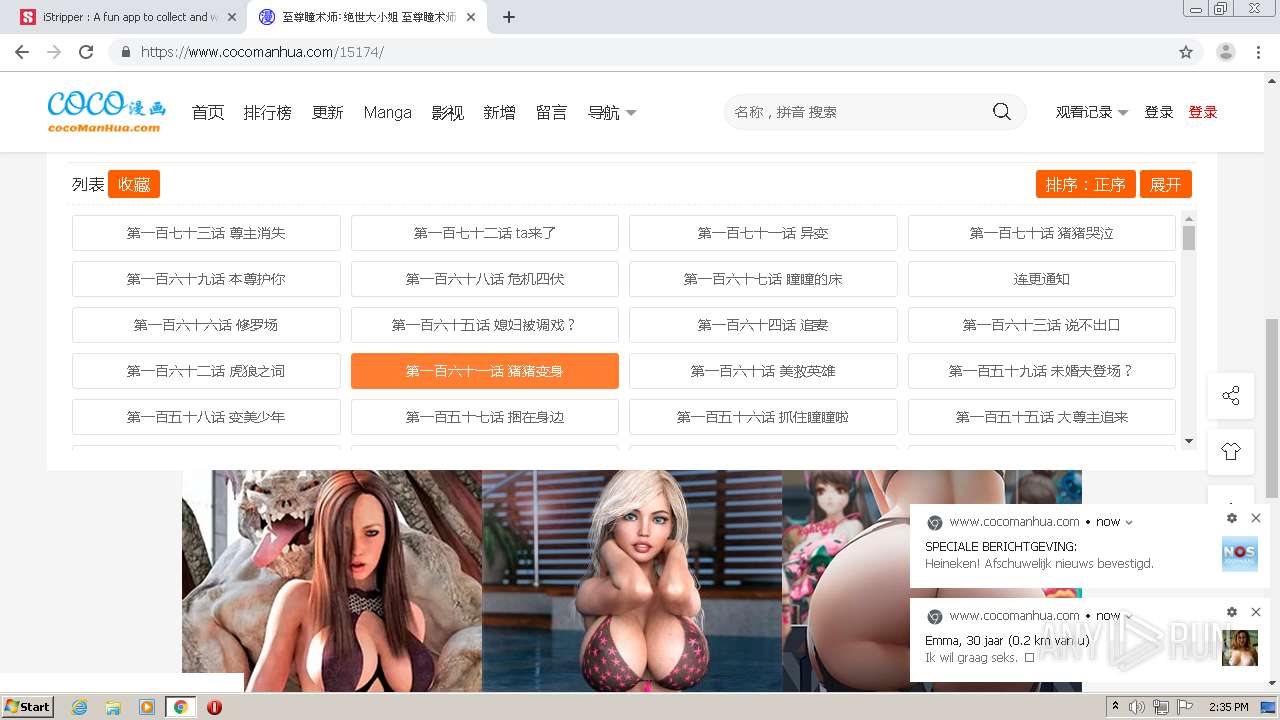
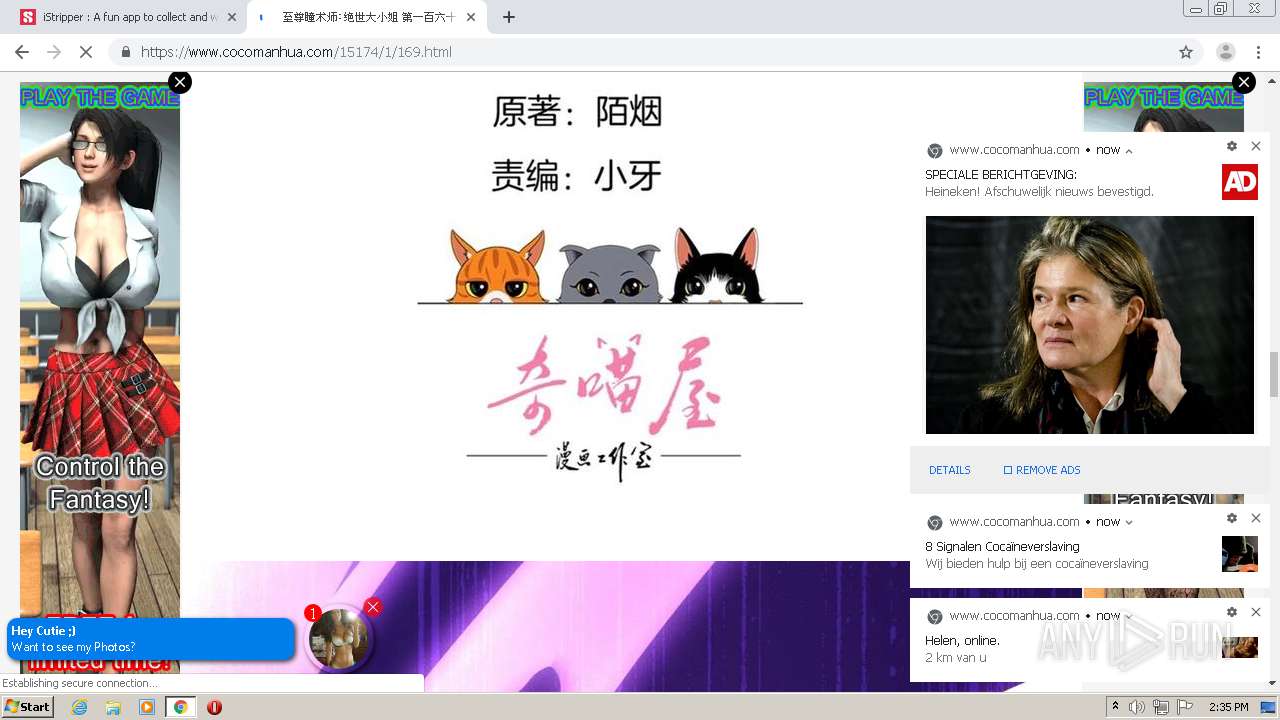
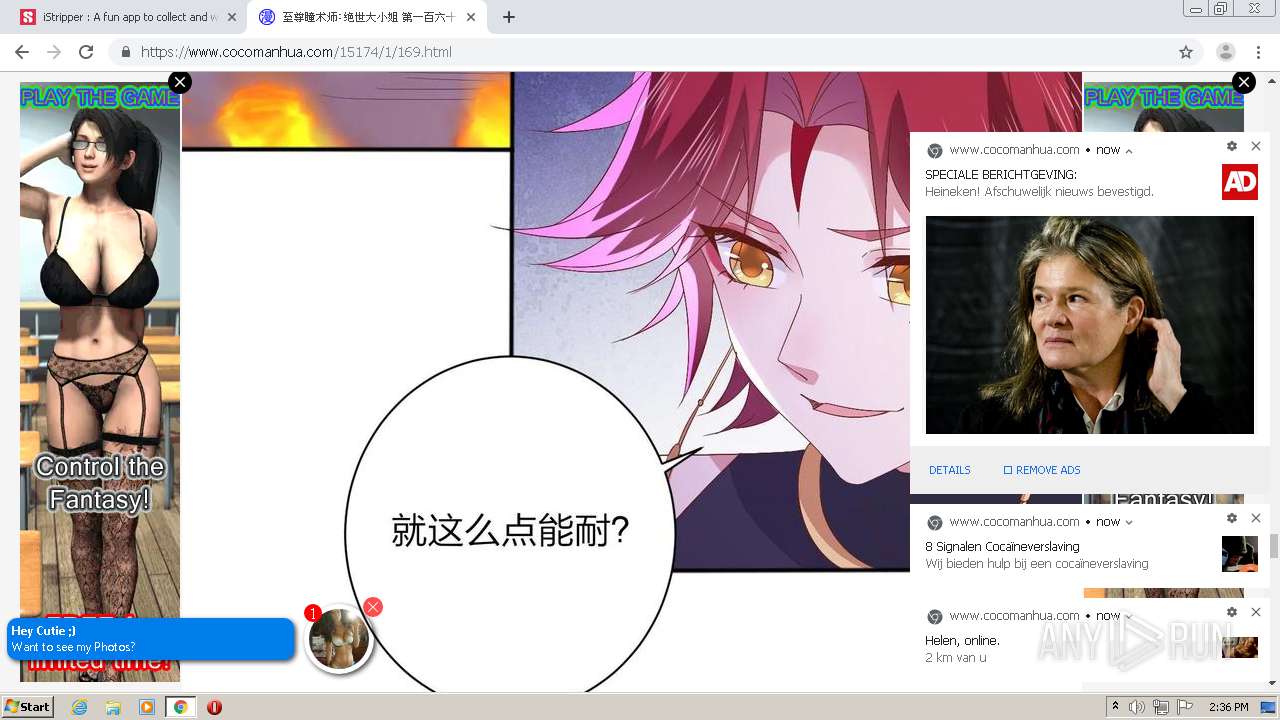
| URL: | https://www.cocomanhua.com/ |
| Full analysis: | https://app.any.run/tasks/c2fc7db6-97e5-4d02-bc37-6e5ba5f98c82 |
| Verdict: | Malicious activity |
| Analysis date: | May 11, 2021, 13:33:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | CA06712BC59AAE3FD3E9FFE9DC0BE327 |
| SHA1: | 4C01F8B62B4501A505C4590C1F931BD408B33AE5 |
| SHA256: | 648326194C63C59DBF898669CE86AD965D12604AE1EEDBB41B6F70CBCE7C3C22 |
| SSDEEP: | 3:N8DSLjIEr2K:2OL0s2K |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- chrome.exe (PID: 3608)
Reads the hosts file
- chrome.exe (PID: 3608)
- chrome.exe (PID: 3376)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
55
Monitored processes
18
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 408 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,6305179804572709574,5035397248001706688,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10050097689618007208 --renderer-client-id=11 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2252 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 996 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,6305179804572709574,5035397248001706688,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=32284467438361117 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2168 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,6305179804572709574,5035397248001706688,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14236122138213789641 --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3540 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1348 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6df7a9d0,0x6df7a9e0,0x6df7a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,6305179804572709574,5035397248001706688,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16950482844267900335 --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2396 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1776 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,6305179804572709574,5035397248001706688,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=12668271740506961934 --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3468 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1024,6305179804572709574,5035397248001706688,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5936786613034483374 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2368 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2476 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1024,6305179804572709574,5035397248001706688,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=6452524269625632308 --mojo-platform-channel-handle=3108 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2612 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,6305179804572709574,5035397248001706688,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=6260966804423084023 --mojo-platform-channel-handle=3348 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2652 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1024,6305179804572709574,5035397248001706688,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=16206059757714330089 --mojo-platform-channel-handle=1032 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
592
Read events
522
Write events
67
Delete events
3
Modification events
| (PID) Process: | (3608) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3608) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3608) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3608) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3608) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3904) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3608-13265213612363250 |
Value: 259 | |||
| (PID) Process: | (3608) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3608) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3608) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (3608) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
0
Suspicious files
103
Text files
97
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3608 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-609A87AD-E18.pma | — | |
MD5:— | SHA256:— | |||
| 3608 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\b1eada08-f553-42ab-a2d7-02b249f649dd.tmp | — | |
MD5:— | SHA256:— | |||
| 3608 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3608 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3608 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3608 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old~RF480e4.TMP | text | |
MD5:— | SHA256:— | |||
| 3608 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3608 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Last Tabs | binary | |
MD5:— | SHA256:— | |||
| 3608 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3608 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF4829a.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
131
DNS requests
54
Threats
3
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3376 | chrome.exe | 142.250.74.195:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3376 | chrome.exe | 104.26.14.7:443 | www.cocomanhua.com | Cloudflare Inc | US | unknown |
3376 | chrome.exe | 172.217.18.109:443 | accounts.google.com | Google Inc. | US | suspicious |
3376 | chrome.exe | 93.184.220.45:443 | a.exdynsrv.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | suspicious |
3376 | chrome.exe | 119.188.176.48:443 | zz.bdstatic.com | CHINA UNICOM China169 Backbone | CN | unknown |
3376 | chrome.exe | 95.211.229.245:443 | syndication.exdynsrv.com | LeaseWeb Netherlands B.V. | NL | suspicious |
3376 | chrome.exe | 205.185.216.10:443 | ads.exoclick.com | Highwinds Network Group, Inc. | US | whitelisted |
3376 | chrome.exe | 52.84.169.84:443 | hinfectlyb.biz | Amazon.com, Inc. | US | unknown |
3376 | chrome.exe | 142.250.186.78:443 | android.clients.google.com | Google Inc. | US | whitelisted |
3376 | chrome.exe | 64.233.167.188:5228 | mtalk.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.cocomanhua.com |
| malicious |
accounts.google.com |
| shared |
v1.cnzz.com |
| whitelisted |
zz.bdstatic.com |
| whitelisted |
a.exdynsrv.com |
| suspicious |
syndication.exdynsrv.com |
| suspicious |
ads.exoclick.com |
| suspicious |
s3t3d2y7.ackcdn.net |
| suspicious |
clients1.google.com |
| whitelisted |
res.cocomanhua.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
3376 | chrome.exe | Potentially Bad Traffic | ET INFO Observed ZeroSSL SSL/TLS Certificate |