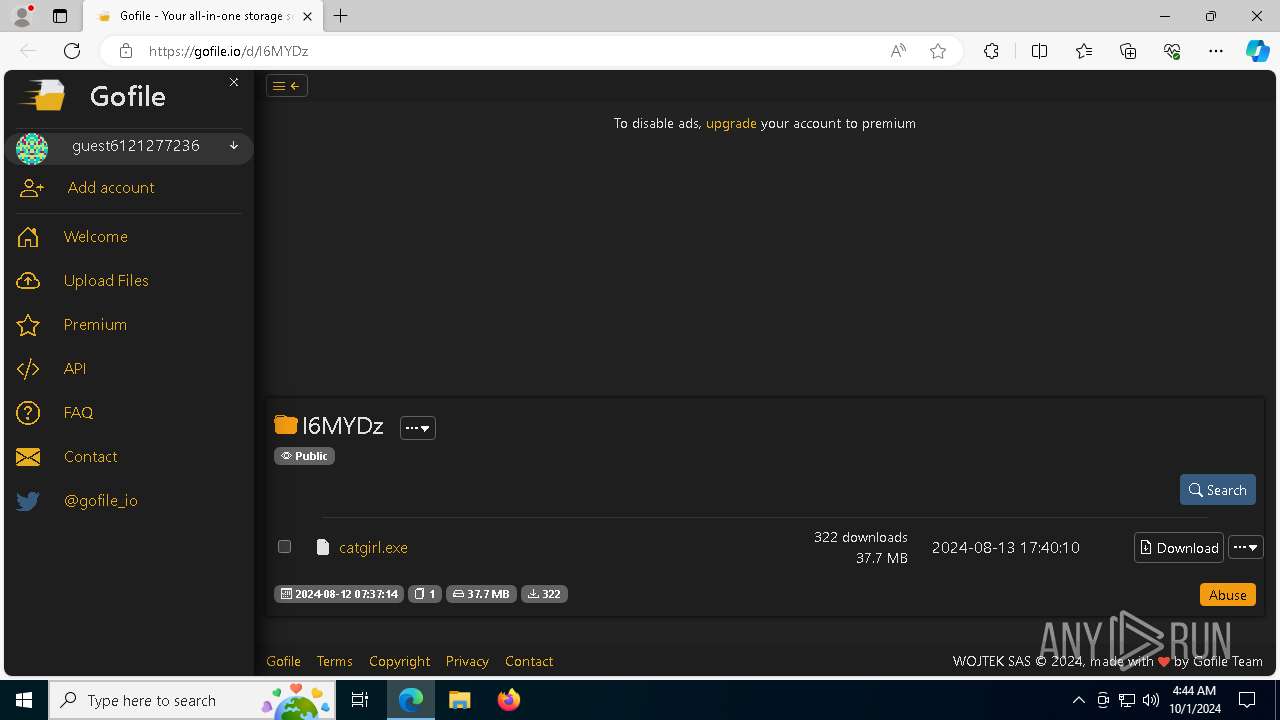
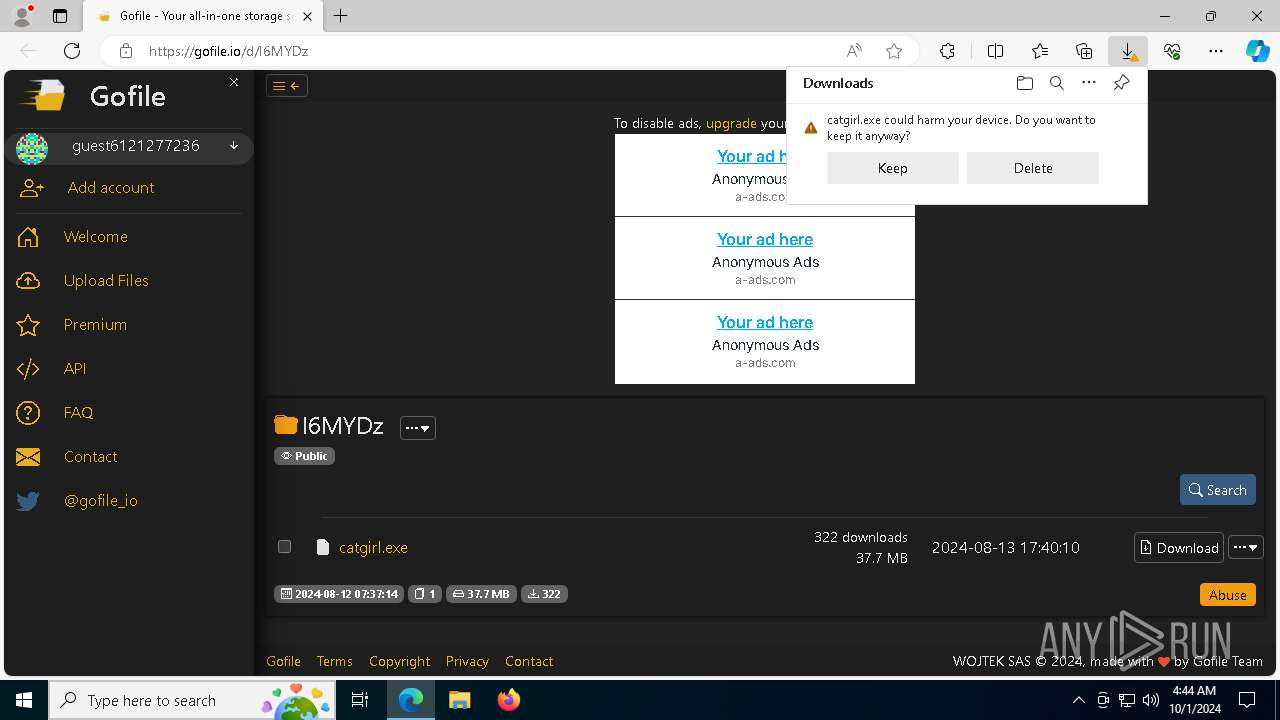
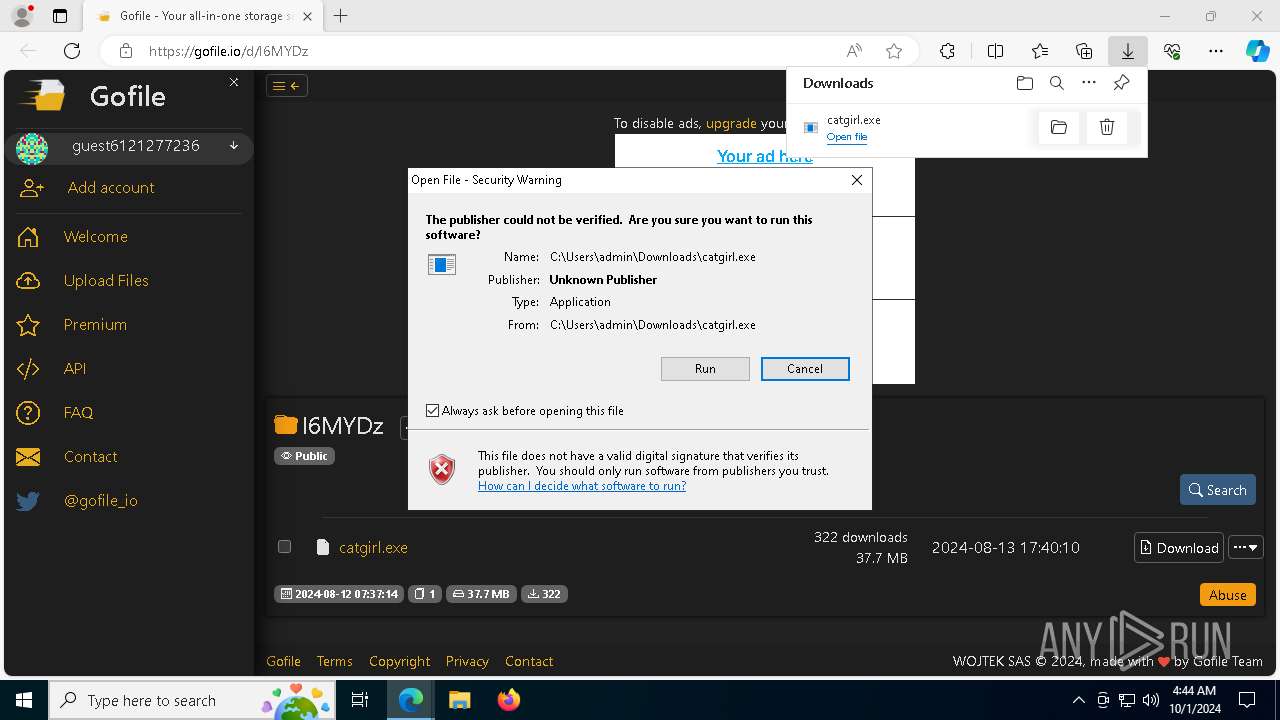
| URL: | https://gofile.io/d/I6MYDz |
| Full analysis: | https://app.any.run/tasks/b1d47882-6a25-4ce2-a465-3f6fe56e2660 |
| Verdict: | Malicious activity |
| Analysis date: | October 01, 2024, 04:44:07 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 04347FF95D62E0AB128A79389E3B7308 |
| SHA1: | DCBA8D1350E955357F09AB4E7752D9F6C4C66325 |
| SHA256: | 648245FFF25256F297858FB83191820632B0D8D6DC902FA2538B70BC97AAC441 |
| SSDEEP: | 3:N8rxL14J:2ZqJ |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
- cmd.exe (PID: 8888)
- cmd.exe (PID: 19276)
- cmd.exe (PID: 23184)
- cmd.exe (PID: 23600)
- cmd.exe (PID: 22804)
- cmd.exe (PID: 26420)
- cmd.exe (PID: 26332)
- cmd.exe (PID: 26708)
- cmd.exe (PID: 26652)
- cmd.exe (PID: 24976)
- cmd.exe (PID: 24996)
- cmd.exe (PID: 9928)
- cmd.exe (PID: 30152)
SUSPICIOUS
Executable content was dropped or overwritten
- catgirl.exe (PID: 8156)
- catgirl.exe (PID: 5612)
- uwu.exe (PID: 8068)
- uwu.exe (PID: 1144)
- uwu.exe (PID: 5940)
- uwu.exe (PID: 8000)
- uwu.exe (PID: 1072)
- uwu.exe (PID: 2468)
- uwu.exe (PID: 692)
- uwu.exe (PID: 6524)
- uwu.exe (PID: 7392)
- uwu.exe (PID: 8028)
- uwu.exe (PID: 8132)
- uwu.exe (PID: 2340)
- uwu.exe (PID: 7588)
- uwu.exe (PID: 6008)
- uwu.exe (PID: 8216)
- uwu.exe (PID: 4748)
- uwu.exe (PID: 8300)
- uwu.exe (PID: 8268)
- uwu.exe (PID: 8396)
- uwu.exe (PID: 8488)
- uwu.exe (PID: 8476)
- uwu.exe (PID: 8568)
- uwu.exe (PID: 8708)
- uwu.exe (PID: 8616)
- uwu.exe (PID: 8768)
- uwu.exe (PID: 8388)
- uwu.exe (PID: 8828)
- uwu.exe (PID: 8808)
- uwu.exe (PID: 8672)
- uwu.exe (PID: 8912)
- uwu.exe (PID: 19512)
- uwu.exe (PID: 20448)
- uwu.exe (PID: 10804)
- uwu.exe (PID: 16788)
- uwu.exe (PID: 29000)
- uwu.exe (PID: 19304)
- uwu.exe (PID: 9372)
- uwu.exe (PID: 11592)
- uwu.exe (PID: 12164)
- uwu.exe (PID: 26960)
- uwu.exe (PID: 9052)
- uwu.exe (PID: 10596)
- uwu.exe (PID: 26712)
- uwu.exe (PID: 16916)
- uwu.exe (PID: 30552)
- uwu.exe (PID: 9092)
- uwu.exe (PID: 16148)
- uwu.exe (PID: 28832)
- uwu.exe (PID: 1156)
- uwu.exe (PID: 19172)
- uwu.exe (PID: 15168)
- uwu.exe (PID: 10488)
- uwu.exe (PID: 24208)
- uwu.exe (PID: 24112)
Process drops python dynamic module
- catgirl.exe (PID: 8156)
- uwu.exe (PID: 1144)
- uwu.exe (PID: 8068)
- uwu.exe (PID: 5940)
- uwu.exe (PID: 8000)
- uwu.exe (PID: 1072)
- uwu.exe (PID: 692)
- uwu.exe (PID: 6524)
- uwu.exe (PID: 4748)
- uwu.exe (PID: 7392)
- uwu.exe (PID: 8028)
- uwu.exe (PID: 8132)
- uwu.exe (PID: 2340)
- uwu.exe (PID: 7588)
- uwu.exe (PID: 2468)
- uwu.exe (PID: 6008)
- uwu.exe (PID: 8216)
- uwu.exe (PID: 8300)
- uwu.exe (PID: 8268)
- uwu.exe (PID: 8388)
- uwu.exe (PID: 8396)
- uwu.exe (PID: 8476)
- uwu.exe (PID: 8488)
- uwu.exe (PID: 8568)
- uwu.exe (PID: 8708)
- uwu.exe (PID: 8616)
- uwu.exe (PID: 8768)
- uwu.exe (PID: 8808)
- uwu.exe (PID: 8672)
- uwu.exe (PID: 8828)
- uwu.exe (PID: 8912)
- uwu.exe (PID: 20448)
- uwu.exe (PID: 19304)
- uwu.exe (PID: 19512)
- uwu.exe (PID: 16788)
- uwu.exe (PID: 9372)
- uwu.exe (PID: 29000)
- uwu.exe (PID: 11592)
- uwu.exe (PID: 12164)
- uwu.exe (PID: 26960)
- uwu.exe (PID: 10596)
- uwu.exe (PID: 26712)
- uwu.exe (PID: 16916)
- uwu.exe (PID: 9052)
- uwu.exe (PID: 15168)
- uwu.exe (PID: 16148)
- uwu.exe (PID: 10804)
- uwu.exe (PID: 9092)
- uwu.exe (PID: 30552)
- uwu.exe (PID: 28832)
- uwu.exe (PID: 19172)
- uwu.exe (PID: 10488)
- uwu.exe (PID: 24208)
- uwu.exe (PID: 24112)
The process drops C-runtime libraries
- catgirl.exe (PID: 8156)
- uwu.exe (PID: 8068)
- uwu.exe (PID: 1144)
- uwu.exe (PID: 8000)
- uwu.exe (PID: 5940)
- uwu.exe (PID: 1072)
- uwu.exe (PID: 2468)
- uwu.exe (PID: 6524)
- uwu.exe (PID: 4748)
- uwu.exe (PID: 7392)
- uwu.exe (PID: 8028)
- uwu.exe (PID: 8132)
- uwu.exe (PID: 2340)
- uwu.exe (PID: 692)
- uwu.exe (PID: 7588)
- uwu.exe (PID: 6008)
- uwu.exe (PID: 8216)
- uwu.exe (PID: 8300)
- uwu.exe (PID: 8268)
- uwu.exe (PID: 8396)
- uwu.exe (PID: 8388)
- uwu.exe (PID: 8476)
- uwu.exe (PID: 8488)
- uwu.exe (PID: 8672)
- uwu.exe (PID: 8616)
- uwu.exe (PID: 8568)
- uwu.exe (PID: 8708)
- uwu.exe (PID: 8808)
- uwu.exe (PID: 8912)
- uwu.exe (PID: 8828)
- uwu.exe (PID: 8768)
- uwu.exe (PID: 26960)
Starts CMD.EXE for commands execution
- catgirl.exe (PID: 5612)
- uwu.exe (PID: 4016)
- uwu.exe (PID: 3648)
- uwu.exe (PID: 5612)
- uwu.exe (PID: 1156)
- uwu.exe (PID: 4668)
- uwu.exe (PID: 7400)
- uwu.exe (PID: 5144)
- uwu.exe (PID: 4032)
- uwu.exe (PID: 8512)
- uwu.exe (PID: 8340)
- uwu.exe (PID: 8584)
- uwu.exe (PID: 8320)
- uwu.exe (PID: 7620)
Application launched itself
- uwu.exe (PID: 8068)
- uwu.exe (PID: 1144)
- uwu.exe (PID: 5940)
- uwu.exe (PID: 8000)
- uwu.exe (PID: 1072)
- catgirl.exe (PID: 8156)
- uwu.exe (PID: 692)
- uwu.exe (PID: 2468)
- uwu.exe (PID: 6524)
- uwu.exe (PID: 4748)
- uwu.exe (PID: 7392)
- uwu.exe (PID: 8028)
- uwu.exe (PID: 8132)
- uwu.exe (PID: 2340)
- uwu.exe (PID: 7588)
- uwu.exe (PID: 8216)
- uwu.exe (PID: 8268)
- uwu.exe (PID: 6008)
- uwu.exe (PID: 8388)
- uwu.exe (PID: 8396)
- uwu.exe (PID: 8476)
- uwu.exe (PID: 8300)
- uwu.exe (PID: 8568)
- uwu.exe (PID: 8768)
- uwu.exe (PID: 8808)
- uwu.exe (PID: 8708)
- uwu.exe (PID: 8828)
- uwu.exe (PID: 8912)
- uwu.exe (PID: 8672)
- uwu.exe (PID: 8488)
- uwu.exe (PID: 8616)
The executable file from the user directory is run by the CMD process
- uwu.exe (PID: 1144)
- uwu.exe (PID: 5940)
- uwu.exe (PID: 8000)
- uwu.exe (PID: 1072)
- uwu.exe (PID: 692)
- uwu.exe (PID: 2468)
- uwu.exe (PID: 6524)
- uwu.exe (PID: 4748)
- uwu.exe (PID: 7392)
- uwu.exe (PID: 8028)
- uwu.exe (PID: 8132)
- uwu.exe (PID: 2340)
- uwu.exe (PID: 7588)
- uwu.exe (PID: 6008)
- uwu.exe (PID: 8216)
- uwu.exe (PID: 8268)
- uwu.exe (PID: 8300)
- uwu.exe (PID: 8396)
- uwu.exe (PID: 8388)
- uwu.exe (PID: 8476)
- uwu.exe (PID: 8488)
- uwu.exe (PID: 8568)
- uwu.exe (PID: 8616)
- uwu.exe (PID: 8708)
- uwu.exe (PID: 8672)
- uwu.exe (PID: 8768)
- uwu.exe (PID: 8808)
- uwu.exe (PID: 8828)
- uwu.exe (PID: 8912)
- uwu.exe (PID: 9372)
- uwu.exe (PID: 12164)
- uwu.exe (PID: 20448)
- uwu.exe (PID: 10804)
- uwu.exe (PID: 19304)
- uwu.exe (PID: 19172)
- uwu.exe (PID: 11592)
- uwu.exe (PID: 30552)
- uwu.exe (PID: 16788)
- uwu.exe (PID: 19512)
- uwu.exe (PID: 26712)
- uwu.exe (PID: 24208)
- uwu.exe (PID: 10488)
- uwu.exe (PID: 16148)
- uwu.exe (PID: 16916)
- uwu.exe (PID: 29000)
- uwu.exe (PID: 28832)
- uwu.exe (PID: 10596)
- uwu.exe (PID: 15168)
- uwu.exe (PID: 26960)
- uwu.exe (PID: 9052)
- uwu.exe (PID: 9092)
- uwu.exe (PID: 24112)
Process drops legitimate windows executable
- uwu.exe (PID: 1144)
- uwu.exe (PID: 8068)
- uwu.exe (PID: 5940)
- uwu.exe (PID: 8000)
- uwu.exe (PID: 1072)
- uwu.exe (PID: 2468)
- uwu.exe (PID: 692)
- catgirl.exe (PID: 8156)
- uwu.exe (PID: 6524)
- uwu.exe (PID: 4748)
- uwu.exe (PID: 7392)
- uwu.exe (PID: 8028)
- uwu.exe (PID: 8132)
- uwu.exe (PID: 2340)
- uwu.exe (PID: 7588)
- uwu.exe (PID: 6008)
- uwu.exe (PID: 8216)
- uwu.exe (PID: 8300)
- uwu.exe (PID: 8268)
- uwu.exe (PID: 8396)
- uwu.exe (PID: 8476)
- uwu.exe (PID: 8388)
- uwu.exe (PID: 8488)
- uwu.exe (PID: 8672)
- uwu.exe (PID: 8616)
- uwu.exe (PID: 8568)
- uwu.exe (PID: 8708)
- uwu.exe (PID: 8808)
- uwu.exe (PID: 8768)
- uwu.exe (PID: 8912)
- uwu.exe (PID: 8828)
- uwu.exe (PID: 26960)
Found strings related to reading or modifying Windows Defender settings
- uwu.exe (PID: 1156)
- uwu.exe (PID: 4016)
- uwu.exe (PID: 3648)
- uwu.exe (PID: 5612)
- uwu.exe (PID: 4668)
- uwu.exe (PID: 7400)
- uwu.exe (PID: 4032)
- uwu.exe (PID: 7620)
- uwu.exe (PID: 8320)
- uwu.exe (PID: 5144)
- uwu.exe (PID: 8340)
- uwu.exe (PID: 8512)
- uwu.exe (PID: 8584)
Hides command output
- cmd.exe (PID: 8920)
- cmd.exe (PID: 8936)
- cmd.exe (PID: 8928)
- cmd.exe (PID: 8960)
- cmd.exe (PID: 8976)
- cmd.exe (PID: 8944)
- cmd.exe (PID: 9156)
- cmd.exe (PID: 8952)
- cmd.exe (PID: 9008)
- cmd.exe (PID: 9184)
- cmd.exe (PID: 9204)
- cmd.exe (PID: 8548)
- cmd.exe (PID: 8924)
- cmd.exe (PID: 8748)
- cmd.exe (PID: 8980)
- cmd.exe (PID: 8940)
- cmd.exe (PID: 8964)
- cmd.exe (PID: 9148)
- cmd.exe (PID: 8936)
- cmd.exe (PID: 9116)
- cmd.exe (PID: 8948)
- cmd.exe (PID: 9180)
- cmd.exe (PID: 8988)
- cmd.exe (PID: 8232)
- cmd.exe (PID: 9140)
- cmd.exe (PID: 8880)
- cmd.exe (PID: 8532)
- cmd.exe (PID: 9208)
- cmd.exe (PID: 8872)
- cmd.exe (PID: 9144)
- cmd.exe (PID: 8652)
- cmd.exe (PID: 9160)
- cmd.exe (PID: 9020)
- cmd.exe (PID: 9036)
- cmd.exe (PID: 9056)
- cmd.exe (PID: 9032)
- cmd.exe (PID: 9092)
- cmd.exe (PID: 8976)
- cmd.exe (PID: 9228)
- cmd.exe (PID: 9236)
- cmd.exe (PID: 9280)
- cmd.exe (PID: 9272)
- cmd.exe (PID: 9288)
- cmd.exe (PID: 9320)
- cmd.exe (PID: 9348)
- cmd.exe (PID: 9300)
- cmd.exe (PID: 9356)
- cmd.exe (PID: 9332)
- cmd.exe (PID: 9368)
- cmd.exe (PID: 9388)
- cmd.exe (PID: 9376)
- cmd.exe (PID: 9424)
- cmd.exe (PID: 9396)
- cmd.exe (PID: 9404)
- cmd.exe (PID: 9412)
- cmd.exe (PID: 9452)
- cmd.exe (PID: 9432)
- cmd.exe (PID: 9440)
- cmd.exe (PID: 9460)
- cmd.exe (PID: 9476)
- cmd.exe (PID: 9484)
- cmd.exe (PID: 9468)
- cmd.exe (PID: 9492)
- cmd.exe (PID: 9552)
- cmd.exe (PID: 9580)
- cmd.exe (PID: 9500)
- cmd.exe (PID: 9516)
- cmd.exe (PID: 9588)
- cmd.exe (PID: 9600)
- cmd.exe (PID: 9524)
- cmd.exe (PID: 9540)
- cmd.exe (PID: 9612)
- cmd.exe (PID: 9564)
- cmd.exe (PID: 9572)
- cmd.exe (PID: 9620)
- cmd.exe (PID: 9628)
- cmd.exe (PID: 9640)
- cmd.exe (PID: 9648)
- cmd.exe (PID: 9668)
- cmd.exe (PID: 9656)
- cmd.exe (PID: 9696)
- cmd.exe (PID: 9680)
- cmd.exe (PID: 9688)
- cmd.exe (PID: 9712)
- cmd.exe (PID: 9720)
- cmd.exe (PID: 9704)
- cmd.exe (PID: 9728)
- cmd.exe (PID: 9736)
- cmd.exe (PID: 9744)
- cmd.exe (PID: 9760)
- cmd.exe (PID: 9752)
- cmd.exe (PID: 9784)
- cmd.exe (PID: 9768)
- cmd.exe (PID: 9776)
- cmd.exe (PID: 9804)
- cmd.exe (PID: 9796)
- cmd.exe (PID: 9824)
- cmd.exe (PID: 9832)
- cmd.exe (PID: 9120)
- cmd.exe (PID: 8968)
- cmd.exe (PID: 9848)
- cmd.exe (PID: 9880)
- cmd.exe (PID: 9888)
- cmd.exe (PID: 9856)
- cmd.exe (PID: 9840)
- cmd.exe (PID: 9868)
- cmd.exe (PID: 9896)
- cmd.exe (PID: 9904)
- cmd.exe (PID: 9940)
- cmd.exe (PID: 9932)
- cmd.exe (PID: 9916)
- cmd.exe (PID: 9924)
- cmd.exe (PID: 9948)
- cmd.exe (PID: 9956)
- cmd.exe (PID: 9964)
- cmd.exe (PID: 9972)
- cmd.exe (PID: 9984)
- cmd.exe (PID: 10000)
- cmd.exe (PID: 9992)
- cmd.exe (PID: 10008)
- cmd.exe (PID: 10040)
- cmd.exe (PID: 10016)
- cmd.exe (PID: 10032)
- cmd.exe (PID: 10048)
- cmd.exe (PID: 10024)
- cmd.exe (PID: 10056)
- cmd.exe (PID: 10088)
- cmd.exe (PID: 10096)
- cmd.exe (PID: 10072)
- cmd.exe (PID: 10080)
- cmd.exe (PID: 10064)
- cmd.exe (PID: 10104)
- cmd.exe (PID: 10112)
- cmd.exe (PID: 10120)
- cmd.exe (PID: 10128)
- cmd.exe (PID: 10156)
- cmd.exe (PID: 10136)
- cmd.exe (PID: 10176)
- cmd.exe (PID: 10164)
- cmd.exe (PID: 10184)
- cmd.exe (PID: 10148)
- cmd.exe (PID: 10208)
- cmd.exe (PID: 10216)
- cmd.exe (PID: 10192)
- cmd.exe (PID: 10200)
- cmd.exe (PID: 10228)
- cmd.exe (PID: 8968)
- cmd.exe (PID: 8972)
- cmd.exe (PID: 9128)
- cmd.exe (PID: 10236)
- cmd.exe (PID: 9264)
- cmd.exe (PID: 9312)
- cmd.exe (PID: 9152)
- cmd.exe (PID: 9344)
- cmd.exe (PID: 9296)
- cmd.exe (PID: 9328)
- cmd.exe (PID: 9316)
- cmd.exe (PID: 8928)
- cmd.exe (PID: 9072)
- cmd.exe (PID: 9024)
- cmd.exe (PID: 9144)
- cmd.exe (PID: 9308)
- cmd.exe (PID: 8956)
- cmd.exe (PID: 9560)
- cmd.exe (PID: 9040)
- cmd.exe (PID: 9608)
- cmd.exe (PID: 10256)
- cmd.exe (PID: 10248)
- cmd.exe (PID: 10264)
- cmd.exe (PID: 10280)
- cmd.exe (PID: 10288)
- cmd.exe (PID: 10296)
- cmd.exe (PID: 10312)
- cmd.exe (PID: 10304)
- cmd.exe (PID: 10356)
- cmd.exe (PID: 10364)
- cmd.exe (PID: 10336)
- cmd.exe (PID: 10320)
- cmd.exe (PID: 10372)
- cmd.exe (PID: 10380)
- cmd.exe (PID: 10396)
- cmd.exe (PID: 10348)
- cmd.exe (PID: 10404)
- cmd.exe (PID: 10388)
- cmd.exe (PID: 10428)
- cmd.exe (PID: 10420)
- cmd.exe (PID: 10412)
- cmd.exe (PID: 10444)
- cmd.exe (PID: 10452)
- cmd.exe (PID: 10460)
- cmd.exe (PID: 10436)
- cmd.exe (PID: 10484)
- cmd.exe (PID: 10468)
- cmd.exe (PID: 10492)
- cmd.exe (PID: 10528)
- cmd.exe (PID: 10504)
- cmd.exe (PID: 10536)
- cmd.exe (PID: 10476)
- cmd.exe (PID: 10512)
- cmd.exe (PID: 10520)
- cmd.exe (PID: 10544)
- cmd.exe (PID: 10568)
- cmd.exe (PID: 9816)
- cmd.exe (PID: 10560)
- cmd.exe (PID: 10852)
- cmd.exe (PID: 10608)
- cmd.exe (PID: 10584)
- cmd.exe (PID: 10592)
- cmd.exe (PID: 10600)
- cmd.exe (PID: 10616)
- cmd.exe (PID: 10624)
- cmd.exe (PID: 10744)
- cmd.exe (PID: 10780)
- cmd.exe (PID: 10792)
- cmd.exe (PID: 10800)
- cmd.exe (PID: 10808)
- cmd.exe (PID: 10816)
- cmd.exe (PID: 10824)
- cmd.exe (PID: 10836)
- cmd.exe (PID: 10844)
- cmd.exe (PID: 10576)
- cmd.exe (PID: 10952)
- cmd.exe (PID: 10868)
- cmd.exe (PID: 10888)
- cmd.exe (PID: 10880)
- cmd.exe (PID: 10920)
- cmd.exe (PID: 10912)
- cmd.exe (PID: 10944)
- cmd.exe (PID: 10928)
- cmd.exe (PID: 10936)
- cmd.exe (PID: 10960)
- cmd.exe (PID: 10972)
- cmd.exe (PID: 10988)
- cmd.exe (PID: 10980)
- cmd.exe (PID: 10860)
- cmd.exe (PID: 11012)
- cmd.exe (PID: 11020)
- cmd.exe (PID: 11028)
- cmd.exe (PID: 11036)
- cmd.exe (PID: 11044)
- cmd.exe (PID: 11052)
- cmd.exe (PID: 11080)
- cmd.exe (PID: 11060)
- cmd.exe (PID: 11072)
- cmd.exe (PID: 11104)
- cmd.exe (PID: 11088)
- cmd.exe (PID: 11096)
- cmd.exe (PID: 11112)
- cmd.exe (PID: 11120)
- cmd.exe (PID: 11132)
- cmd.exe (PID: 11152)
- cmd.exe (PID: 10996)
- cmd.exe (PID: 11004)
- cmd.exe (PID: 11160)
- cmd.exe (PID: 11168)
- cmd.exe (PID: 11188)
- cmd.exe (PID: 11196)
- cmd.exe (PID: 11212)
- cmd.exe (PID: 11204)
- cmd.exe (PID: 11220)
- cmd.exe (PID: 11228)
- cmd.exe (PID: 11236)
- cmd.exe (PID: 11244)
- cmd.exe (PID: 11252)
- cmd.exe (PID: 9812)
- cmd.exe (PID: 11260)
- cmd.exe (PID: 10224)
- cmd.exe (PID: 11272)
- cmd.exe (PID: 10272)
- cmd.exe (PID: 11280)
- cmd.exe (PID: 11288)
- cmd.exe (PID: 11348)
- cmd.exe (PID: 11380)
- cmd.exe (PID: 11364)
- cmd.exe (PID: 11372)
- cmd.exe (PID: 11408)
- cmd.exe (PID: 11420)
- cmd.exe (PID: 11432)
- cmd.exe (PID: 11444)
- cmd.exe (PID: 11464)
- cmd.exe (PID: 11484)
- cmd.exe (PID: 11564)
- cmd.exe (PID: 11496)
- cmd.exe (PID: 11516)
- cmd.exe (PID: 11528)
- cmd.exe (PID: 11536)
- cmd.exe (PID: 11544)
- cmd.exe (PID: 11552)
- cmd.exe (PID: 11572)
- cmd.exe (PID: 11356)
- cmd.exe (PID: 11580)
- cmd.exe (PID: 11588)
- cmd.exe (PID: 11624)
- cmd.exe (PID: 11596)
- cmd.exe (PID: 11604)
- cmd.exe (PID: 11612)
- cmd.exe (PID: 11688)
- cmd.exe (PID: 11632)
- cmd.exe (PID: 11664)
- cmd.exe (PID: 11640)
- cmd.exe (PID: 11648)
- cmd.exe (PID: 11656)
- cmd.exe (PID: 11672)
- cmd.exe (PID: 11696)
- cmd.exe (PID: 11716)
- cmd.exe (PID: 11744)
- cmd.exe (PID: 10552)
- cmd.exe (PID: 11760)
- cmd.exe (PID: 11772)
- cmd.exe (PID: 11732)
- cmd.exe (PID: 11804)
- cmd.exe (PID: 11812)
- cmd.exe (PID: 11820)
- cmd.exe (PID: 11836)
- cmd.exe (PID: 11828)
- cmd.exe (PID: 11844)
- cmd.exe (PID: 11852)
- cmd.exe (PID: 11868)
- cmd.exe (PID: 11904)
- cmd.exe (PID: 11876)
- cmd.exe (PID: 11884)
- cmd.exe (PID: 11896)
- cmd.exe (PID: 11912)
- cmd.exe (PID: 11928)
- cmd.exe (PID: 11944)
- cmd.exe (PID: 11784)
- cmd.exe (PID: 11796)
- cmd.exe (PID: 11860)
- cmd.exe (PID: 11972)
- cmd.exe (PID: 11988)
- cmd.exe (PID: 12004)
- cmd.exe (PID: 11996)
- cmd.exe (PID: 12012)
- cmd.exe (PID: 12028)
- cmd.exe (PID: 12020)
- cmd.exe (PID: 12040)
- cmd.exe (PID: 12096)
- cmd.exe (PID: 12048)
- cmd.exe (PID: 12056)
- cmd.exe (PID: 12064)
- cmd.exe (PID: 12088)
- cmd.exe (PID: 12080)
- cmd.exe (PID: 11952)
- cmd.exe (PID: 11964)
- cmd.exe (PID: 11980)
- cmd.exe (PID: 12072)
- cmd.exe (PID: 12120)
- cmd.exe (PID: 12128)
- cmd.exe (PID: 12136)
- cmd.exe (PID: 12184)
- cmd.exe (PID: 12176)
- cmd.exe (PID: 12160)
- cmd.exe (PID: 12168)
- cmd.exe (PID: 12192)
- cmd.exe (PID: 12224)
- cmd.exe (PID: 12200)
- cmd.exe (PID: 12216)
- cmd.exe (PID: 12208)
- cmd.exe (PID: 12232)
- cmd.exe (PID: 12104)
- cmd.exe (PID: 12112)
- cmd.exe (PID: 12144)
- cmd.exe (PID: 12152)
- cmd.exe (PID: 12248)
- cmd.exe (PID: 12268)
- cmd.exe (PID: 12276)
- cmd.exe (PID: 12376)
- cmd.exe (PID: 12284)
- cmd.exe (PID: 12304)
- cmd.exe (PID: 12320)
- cmd.exe (PID: 12336)
- cmd.exe (PID: 12348)
- cmd.exe (PID: 12356)
- cmd.exe (PID: 12368)
- cmd.exe (PID: 12384)
- cmd.exe (PID: 12588)
- cmd.exe (PID: 12260)
- cmd.exe (PID: 12612)
- cmd.exe (PID: 12620)
- cmd.exe (PID: 12660)
- cmd.exe (PID: 12672)
- cmd.exe (PID: 12680)
- cmd.exe (PID: 12736)
- cmd.exe (PID: 12692)
- cmd.exe (PID: 12708)
- cmd.exe (PID: 12756)
- cmd.exe (PID: 12792)
- cmd.exe (PID: 12784)
- cmd.exe (PID: 12804)
- cmd.exe (PID: 12812)
- cmd.exe (PID: 12820)
- cmd.exe (PID: 12596)
- cmd.exe (PID: 12604)
- cmd.exe (PID: 12632)
- cmd.exe (PID: 12648)
- cmd.exe (PID: 12772)
- cmd.exe (PID: 12844)
- cmd.exe (PID: 12868)
- cmd.exe (PID: 12852)
- cmd.exe (PID: 12888)
- cmd.exe (PID: 12876)
- cmd.exe (PID: 12896)
- cmd.exe (PID: 12908)
- cmd.exe (PID: 12928)
- cmd.exe (PID: 12916)
- cmd.exe (PID: 12948)
- cmd.exe (PID: 12940)
- cmd.exe (PID: 12964)
- cmd.exe (PID: 12976)
- cmd.exe (PID: 12832)
- cmd.exe (PID: 13116)
- cmd.exe (PID: 13136)
- cmd.exe (PID: 13144)
- cmd.exe (PID: 13152)
- cmd.exe (PID: 13272)
- cmd.exe (PID: 13212)
- cmd.exe (PID: 13240)
- cmd.exe (PID: 13220)
- cmd.exe (PID: 13248)
- cmd.exe (PID: 13280)
- cmd.exe (PID: 13256)
- cmd.exe (PID: 12984)
- cmd.exe (PID: 13072)
- cmd.exe (PID: 13080)
- cmd.exe (PID: 13088)
- cmd.exe (PID: 13100)
- cmd.exe (PID: 13108)
- cmd.exe (PID: 13204)
- cmd.exe (PID: 13288)
- cmd.exe (PID: 13308)
- cmd.exe (PID: 13340)
- cmd.exe (PID: 13380)
- cmd.exe (PID: 13348)
- cmd.exe (PID: 13364)
- cmd.exe (PID: 13356)
- cmd.exe (PID: 13372)
- cmd.exe (PID: 13428)
- cmd.exe (PID: 13388)
- cmd.exe (PID: 13396)
- cmd.exe (PID: 13404)
- cmd.exe (PID: 13468)
- cmd.exe (PID: 13412)
- cmd.exe (PID: 13452)
- cmd.exe (PID: 13420)
- cmd.exe (PID: 13476)
- cmd.exe (PID: 13484)
- cmd.exe (PID: 13296)
- cmd.exe (PID: 13516)
- cmd.exe (PID: 13544)
- cmd.exe (PID: 13528)
- cmd.exe (PID: 13568)
- cmd.exe (PID: 13536)
- cmd.exe (PID: 13560)
- cmd.exe (PID: 13552)
- cmd.exe (PID: 13576)
- cmd.exe (PID: 13584)
- cmd.exe (PID: 13608)
- cmd.exe (PID: 13592)
- cmd.exe (PID: 13600)
- cmd.exe (PID: 13620)
- cmd.exe (PID: 13632)
- cmd.exe (PID: 13640)
- cmd.exe (PID: 13648)
- cmd.exe (PID: 13656)
- cmd.exe (PID: 13496)
- cmd.exe (PID: 13504)
- cmd.exe (PID: 13672)
- cmd.exe (PID: 13680)
- cmd.exe (PID: 13696)
- cmd.exe (PID: 13720)
- cmd.exe (PID: 13704)
- cmd.exe (PID: 13712)
- cmd.exe (PID: 13736)
- cmd.exe (PID: 13752)
- cmd.exe (PID: 13760)
- cmd.exe (PID: 13768)
- cmd.exe (PID: 13776)
- cmd.exe (PID: 13784)
- cmd.exe (PID: 13792)
- cmd.exe (PID: 13800)
- cmd.exe (PID: 13664)
- cmd.exe (PID: 13688)
- cmd.exe (PID: 13728)
- cmd.exe (PID: 13744)
- cmd.exe (PID: 13828)
- cmd.exe (PID: 13840)
- cmd.exe (PID: 13884)
- cmd.exe (PID: 13848)
- cmd.exe (PID: 13928)
- cmd.exe (PID: 13872)
- cmd.exe (PID: 13936)
- cmd.exe (PID: 13904)
- cmd.exe (PID: 13912)
- cmd.exe (PID: 13996)
- cmd.exe (PID: 13948)
- cmd.exe (PID: 13984)
- cmd.exe (PID: 13808)
- cmd.exe (PID: 13820)
- cmd.exe (PID: 13864)
- cmd.exe (PID: 13960)
- cmd.exe (PID: 13972)
- cmd.exe (PID: 14056)
- cmd.exe (PID: 14048)
- cmd.exe (PID: 14268)
- cmd.exe (PID: 14328)
- cmd.exe (PID: 14276)
- cmd.exe (PID: 6360)
- cmd.exe (PID: 13336)
- cmd.exe (PID: 8892)
- cmd.exe (PID: 9508)
- cmd.exe (PID: 9016)
- cmd.exe (PID: 7936)
- cmd.exe (PID: 9204)
- cmd.exe (PID: 14004)
- cmd.exe (PID: 14012)
- cmd.exe (PID: 14020)
- cmd.exe (PID: 14036)
- cmd.exe (PID: 14028)
- cmd.exe (PID: 14352)
- cmd.exe (PID: 14376)
- cmd.exe (PID: 14368)
- cmd.exe (PID: 14384)
- cmd.exe (PID: 14392)
- cmd.exe (PID: 14456)
- cmd.exe (PID: 14432)
- cmd.exe (PID: 14440)
- cmd.exe (PID: 14448)
- cmd.exe (PID: 14464)
- cmd.exe (PID: 14472)
- cmd.exe (PID: 9156)
- cmd.exe (PID: 9008)
- cmd.exe (PID: 14344)
- cmd.exe (PID: 14360)
- cmd.exe (PID: 14400)
- cmd.exe (PID: 14416)
- cmd.exe (PID: 14500)
- cmd.exe (PID: 14516)
- cmd.exe (PID: 14524)
- cmd.exe (PID: 14532)
- cmd.exe (PID: 14540)
- cmd.exe (PID: 14548)
- cmd.exe (PID: 14556)
- cmd.exe (PID: 14564)
- cmd.exe (PID: 14572)
- cmd.exe (PID: 14580)
- cmd.exe (PID: 14588)
- cmd.exe (PID: 14596)
- cmd.exe (PID: 14604)
- cmd.exe (PID: 14480)
- cmd.exe (PID: 14492)
- cmd.exe (PID: 14508)
- cmd.exe (PID: 14628)
- cmd.exe (PID: 14636)
- cmd.exe (PID: 14652)
- cmd.exe (PID: 14660)
- cmd.exe (PID: 14668)
- cmd.exe (PID: 14676)
- cmd.exe (PID: 14684)
- cmd.exe (PID: 14692)
- cmd.exe (PID: 14704)
- cmd.exe (PID: 14716)
- cmd.exe (PID: 14740)
- cmd.exe (PID: 14748)
- cmd.exe (PID: 14764)
- cmd.exe (PID: 14612)
- cmd.exe (PID: 14620)
- cmd.exe (PID: 14644)
- cmd.exe (PID: 14732)
- cmd.exe (PID: 14756)
- cmd.exe (PID: 14808)
- cmd.exe (PID: 14924)
- cmd.exe (PID: 14816)
- cmd.exe (PID: 14824)
- cmd.exe (PID: 14908)
- cmd.exe (PID: 14836)
- cmd.exe (PID: 14864)
- cmd.exe (PID: 14892)
- cmd.exe (PID: 14884)
- cmd.exe (PID: 14940)
- cmd.exe (PID: 14916)
- cmd.exe (PID: 14956)
- cmd.exe (PID: 14932)
- cmd.exe (PID: 14948)
- cmd.exe (PID: 14776)
- cmd.exe (PID: 14788)
- cmd.exe (PID: 14856)
- cmd.exe (PID: 14980)
- cmd.exe (PID: 14988)
- cmd.exe (PID: 14996)
- cmd.exe (PID: 15004)
- cmd.exe (PID: 15084)
- cmd.exe (PID: 15052)
- cmd.exe (PID: 15028)
- cmd.exe (PID: 15036)
- cmd.exe (PID: 15044)
- cmd.exe (PID: 15060)
- cmd.exe (PID: 15068)
- cmd.exe (PID: 15076)
- cmd.exe (PID: 15100)
- cmd.exe (PID: 15092)
- cmd.exe (PID: 15108)
- cmd.exe (PID: 14964)
- cmd.exe (PID: 14972)
- cmd.exe (PID: 15012)
- cmd.exe (PID: 15020)
- cmd.exe (PID: 15124)
- cmd.exe (PID: 15148)
- cmd.exe (PID: 15140)
- cmd.exe (PID: 15156)
- cmd.exe (PID: 15220)
- cmd.exe (PID: 15188)
- cmd.exe (PID: 15172)
- cmd.exe (PID: 15180)
- cmd.exe (PID: 15196)
- cmd.exe (PID: 15212)
- cmd.exe (PID: 15228)
- cmd.exe (PID: 15236)
- cmd.exe (PID: 15252)
- cmd.exe (PID: 15116)
- cmd.exe (PID: 15132)
- cmd.exe (PID: 15164)
- cmd.exe (PID: 15244)
- cmd.exe (PID: 15324)
- cmd.exe (PID: 15292)
- cmd.exe (PID: 15300)
- cmd.exe (PID: 15308)
- cmd.exe (PID: 15336)
- cmd.exe (PID: 15348)
- cmd.exe (PID: 15356)
- cmd.exe (PID: 3028)
- cmd.exe (PID: 15368)
- cmd.exe (PID: 15384)
- cmd.exe (PID: 15260)
- cmd.exe (PID: 15268)
- cmd.exe (PID: 15276)
- cmd.exe (PID: 15284)
- cmd.exe (PID: 15316)
- cmd.exe (PID: 6536)
- cmd.exe (PID: 15424)
- cmd.exe (PID: 15432)
- cmd.exe (PID: 15480)
- cmd.exe (PID: 15440)
- cmd.exe (PID: 15452)
- cmd.exe (PID: 15460)
- cmd.exe (PID: 15472)
- cmd.exe (PID: 15488)
- cmd.exe (PID: 15496)
- cmd.exe (PID: 15504)
- cmd.exe (PID: 15512)
- cmd.exe (PID: 15392)
- cmd.exe (PID: 15400)
- cmd.exe (PID: 15408)
- cmd.exe (PID: 15416)
- cmd.exe (PID: 15552)
- cmd.exe (PID: 15560)
- cmd.exe (PID: 15568)
- cmd.exe (PID: 15608)
- cmd.exe (PID: 15592)
- cmd.exe (PID: 15600)
- cmd.exe (PID: 15616)
- cmd.exe (PID: 15636)
- cmd.exe (PID: 15628)
- cmd.exe (PID: 15676)
- cmd.exe (PID: 15644)
- cmd.exe (PID: 15660)
- cmd.exe (PID: 15652)
- cmd.exe (PID: 15668)
- cmd.exe (PID: 15520)
- cmd.exe (PID: 15528)
- cmd.exe (PID: 15536)
- cmd.exe (PID: 15544)
- cmd.exe (PID: 15744)
- cmd.exe (PID: 15752)
- cmd.exe (PID: 15936)
- cmd.exe (PID: 15768)
- cmd.exe (PID: 15776)
- cmd.exe (PID: 15784)
- cmd.exe (PID: 15792)
- cmd.exe (PID: 15800)
- cmd.exe (PID: 15808)
- cmd.exe (PID: 15820)
- cmd.exe (PID: 15828)
- cmd.exe (PID: 15988)
- cmd.exe (PID: 15972)
- cmd.exe (PID: 15980)
- cmd.exe (PID: 15716)
- cmd.exe (PID: 15728)
- cmd.exe (PID: 15736)
- cmd.exe (PID: 15760)
- cmd.exe (PID: 16020)
- cmd.exe (PID: 16028)
- cmd.exe (PID: 16036)
- cmd.exe (PID: 16080)
- cmd.exe (PID: 16072)
- cmd.exe (PID: 16048)
- cmd.exe (PID: 16088)
- cmd.exe (PID: 16104)
- cmd.exe (PID: 16120)
- cmd.exe (PID: 16112)
- cmd.exe (PID: 16128)
- cmd.exe (PID: 16144)
- cmd.exe (PID: 16136)
- cmd.exe (PID: 16004)
- cmd.exe (PID: 16012)
- cmd.exe (PID: 16056)
- cmd.exe (PID: 16096)
- cmd.exe (PID: 16196)
- cmd.exe (PID: 16188)
- cmd.exe (PID: 16240)
- cmd.exe (PID: 16208)
- cmd.exe (PID: 16232)
- cmd.exe (PID: 16224)
- cmd.exe (PID: 16296)
- cmd.exe (PID: 16248)
- cmd.exe (PID: 16256)
- cmd.exe (PID: 16264)
- cmd.exe (PID: 16272)
- cmd.exe (PID: 16280)
- cmd.exe (PID: 16288)
- cmd.exe (PID: 16152)
- cmd.exe (PID: 16164)
- cmd.exe (PID: 16172)
- cmd.exe (PID: 16180)
- cmd.exe (PID: 16216)
- cmd.exe (PID: 16348)
- cmd.exe (PID: 16332)
- cmd.exe (PID: 16340)
- cmd.exe (PID: 16436)
- cmd.exe (PID: 16356)
- cmd.exe (PID: 16396)
- cmd.exe (PID: 16364)
- cmd.exe (PID: 16372)
- cmd.exe (PID: 16388)
- cmd.exe (PID: 16420)
- cmd.exe (PID: 16404)
- cmd.exe (PID: 16412)
- cmd.exe (PID: 16428)
- cmd.exe (PID: 16444)
- cmd.exe (PID: 16452)
- cmd.exe (PID: 16304)
- cmd.exe (PID: 16312)
- cmd.exe (PID: 16500)
- cmd.exe (PID: 16484)
- cmd.exe (PID: 16492)
- cmd.exe (PID: 16588)
- cmd.exe (PID: 16580)
- cmd.exe (PID: 16532)
- cmd.exe (PID: 16572)
- cmd.exe (PID: 16548)
- cmd.exe (PID: 16556)
- cmd.exe (PID: 16600)
- cmd.exe (PID: 16616)
- cmd.exe (PID: 16608)
- cmd.exe (PID: 16624)
- cmd.exe (PID: 16468)
- cmd.exe (PID: 16460)
- cmd.exe (PID: 16476)
- cmd.exe (PID: 16508)
- cmd.exe (PID: 16516)
- cmd.exe (PID: 16540)
- cmd.exe (PID: 16700)
- cmd.exe (PID: 16672)
- cmd.exe (PID: 16648)
- cmd.exe (PID: 16664)
- cmd.exe (PID: 16728)
- cmd.exe (PID: 16684)
- cmd.exe (PID: 16692)
- cmd.exe (PID: 16720)
- cmd.exe (PID: 16796)
- cmd.exe (PID: 16740)
- cmd.exe (PID: 16804)
- cmd.exe (PID: 16812)
- cmd.exe (PID: 16632)
- cmd.exe (PID: 16640)
- cmd.exe (PID: 16656)
- cmd.exe (PID: 16712)
- cmd.exe (PID: 16980)
- cmd.exe (PID: 16932)
- cmd.exe (PID: 16944)
- cmd.exe (PID: 16968)
- cmd.exe (PID: 17004)
- cmd.exe (PID: 17012)
- cmd.exe (PID: 17020)
- cmd.exe (PID: 17032)
- cmd.exe (PID: 17044)
- cmd.exe (PID: 17052)
- cmd.exe (PID: 16836)
- cmd.exe (PID: 16860)
- cmd.exe (PID: 16868)
- cmd.exe (PID: 16876)
- cmd.exe (PID: 16888)
- cmd.exe (PID: 16988)
- cmd.exe (PID: 16996)
- cmd.exe (PID: 17100)
- cmd.exe (PID: 17108)
- cmd.exe (PID: 17116)
- cmd.exe (PID: 17124)
- cmd.exe (PID: 17132)
- cmd.exe (PID: 17236)
- cmd.exe (PID: 17164)
- cmd.exe (PID: 17224)
- cmd.exe (PID: 17256)
- cmd.exe (PID: 17244)
- cmd.exe (PID: 17068)
- cmd.exe (PID: 17076)
- cmd.exe (PID: 17084)
- cmd.exe (PID: 17092)
- cmd.exe (PID: 17140)
- cmd.exe (PID: 17172)
- cmd.exe (PID: 17300)
- cmd.exe (PID: 17308)
- cmd.exe (PID: 17316)
- cmd.exe (PID: 17324)
- cmd.exe (PID: 17332)
- cmd.exe (PID: 17340)
- cmd.exe (PID: 17348)
- cmd.exe (PID: 17356)
- cmd.exe (PID: 17364)
- cmd.exe (PID: 17372)
- cmd.exe (PID: 17380)
- cmd.exe (PID: 17388)
- cmd.exe (PID: 17396)
- cmd.exe (PID: 17404)
- cmd.exe (PID: 17264)
- cmd.exe (PID: 17272)
- cmd.exe (PID: 17280)
- cmd.exe (PID: 17288)
- cmd.exe (PID: 17448)
- cmd.exe (PID: 17480)
- cmd.exe (PID: 17456)
- cmd.exe (PID: 17472)
- cmd.exe (PID: 17464)
- cmd.exe (PID: 17488)
- cmd.exe (PID: 17500)
- cmd.exe (PID: 17508)
- cmd.exe (PID: 17524)
- cmd.exe (PID: 17516)
- cmd.exe (PID: 17532)
- cmd.exe (PID: 17564)
- cmd.exe (PID: 17540)
- cmd.exe (PID: 17552)
- cmd.exe (PID: 17584)
- cmd.exe (PID: 17576)
- cmd.exe (PID: 17412)
- cmd.exe (PID: 17420)
- cmd.exe (PID: 17428)
- cmd.exe (PID: 17436)
- cmd.exe (PID: 17616)
- cmd.exe (PID: 17592)
- cmd.exe (PID: 17688)
- cmd.exe (PID: 17648)
- cmd.exe (PID: 17640)
- cmd.exe (PID: 17664)
- cmd.exe (PID: 17656)
- cmd.exe (PID: 17672)
- cmd.exe (PID: 17680)
- cmd.exe (PID: 17696)
- cmd.exe (PID: 17724)
- cmd.exe (PID: 17704)
- cmd.exe (PID: 17712)
- cmd.exe (PID: 17732)
- cmd.exe (PID: 17752)
- cmd.exe (PID: 17744)
- cmd.exe (PID: 17768)
- cmd.exe (PID: 17760)
- cmd.exe (PID: 17604)
- cmd.exe (PID: 17632)
- cmd.exe (PID: 17780)
- cmd.exe (PID: 17792)
- cmd.exe (PID: 17800)
- cmd.exe (PID: 17812)
- cmd.exe (PID: 17820)
- cmd.exe (PID: 17928)
- cmd.exe (PID: 17836)
- cmd.exe (PID: 17828)
- cmd.exe (PID: 17876)
- cmd.exe (PID: 17844)
- cmd.exe (PID: 17852)
- cmd.exe (PID: 17860)
- cmd.exe (PID: 17868)
- cmd.exe (PID: 17884)
- cmd.exe (PID: 17936)
- cmd.exe (PID: 17892)
- cmd.exe (PID: 17900)
- cmd.exe (PID: 17912)
- cmd.exe (PID: 17920)
- cmd.exe (PID: 17996)
- cmd.exe (PID: 17980)
- cmd.exe (PID: 18056)
- cmd.exe (PID: 18044)
- cmd.exe (PID: 17988)
- cmd.exe (PID: 18004)
- cmd.exe (PID: 18020)
- cmd.exe (PID: 18028)
- cmd.exe (PID: 18036)
- cmd.exe (PID: 18116)
- cmd.exe (PID: 18096)
- cmd.exe (PID: 18124)
- cmd.exe (PID: 18108)
- cmd.exe (PID: 18144)
- cmd.exe (PID: 18132)
- cmd.exe (PID: 18152)
- cmd.exe (PID: 17944)
- cmd.exe (PID: 17956)
- cmd.exe (PID: 17964)
- cmd.exe (PID: 17972)
- cmd.exe (PID: 18160)
- cmd.exe (PID: 18172)
- cmd.exe (PID: 18180)
- cmd.exe (PID: 18272)
- cmd.exe (PID: 18240)
- cmd.exe (PID: 18188)
- cmd.exe (PID: 18228)
- cmd.exe (PID: 18204)
- cmd.exe (PID: 18212)
- cmd.exe (PID: 18220)
- cmd.exe (PID: 18248)
- cmd.exe (PID: 18256)
- cmd.exe (PID: 18264)
- cmd.exe (PID: 18280)
- cmd.exe (PID: 18288)
- cmd.exe (PID: 18196)
- cmd.exe (PID: 18296)
- cmd.exe (PID: 18304)
- cmd.exe (PID: 18312)
- cmd.exe (PID: 18320)
- cmd.exe (PID: 18328)
- cmd.exe (PID: 18384)
- cmd.exe (PID: 18392)
- cmd.exe (PID: 18340)
- cmd.exe (PID: 18416)
- cmd.exe (PID: 18408)
- cmd.exe (PID: 18428)
- cmd.exe (PID: 7700)
- cmd.exe (PID: 7684)
- cmd.exe (PID: 7648)
- cmd.exe (PID: 7628)
- cmd.exe (PID: 7708)
- cmd.exe (PID: 18436)
- cmd.exe (PID: 18444)
- cmd.exe (PID: 18452)
- cmd.exe (PID: 18468)
- cmd.exe (PID: 18460)
- cmd.exe (PID: 18476)
- cmd.exe (PID: 18568)
- cmd.exe (PID: 18492)
- cmd.exe (PID: 18532)
- cmd.exe (PID: 18520)
- cmd.exe (PID: 18540)
- cmd.exe (PID: 18548)
- cmd.exe (PID: 18556)
- cmd.exe (PID: 18584)
- cmd.exe (PID: 18576)
- cmd.exe (PID: 18596)
- cmd.exe (PID: 18604)
- cmd.exe (PID: 18484)
- cmd.exe (PID: 18508)
- cmd.exe (PID: 18640)
- cmd.exe (PID: 18712)
- cmd.exe (PID: 18648)
- cmd.exe (PID: 18656)
- cmd.exe (PID: 18664)
- cmd.exe (PID: 18680)
- cmd.exe (PID: 18688)
- cmd.exe (PID: 18728)
- cmd.exe (PID: 18720)
- cmd.exe (PID: 18736)
- cmd.exe (PID: 18620)
- cmd.exe (PID: 18628)
- cmd.exe (PID: 18704)
- cmd.exe (PID: 18780)
- cmd.exe (PID: 18772)
- cmd.exe (PID: 18788)
- cmd.exe (PID: 18796)
- cmd.exe (PID: 18804)
- cmd.exe (PID: 18812)
- cmd.exe (PID: 18820)
- cmd.exe (PID: 18828)
- cmd.exe (PID: 18864)
- cmd.exe (PID: 18836)
- cmd.exe (PID: 18844)
- cmd.exe (PID: 18852)
- cmd.exe (PID: 18888)
- cmd.exe (PID: 18880)
- cmd.exe (PID: 18900)
- cmd.exe (PID: 18744)
- cmd.exe (PID: 18752)
- cmd.exe (PID: 18872)
- cmd.exe (PID: 18976)
- cmd.exe (PID: 18924)
- cmd.exe (PID: 18932)
- cmd.exe (PID: 19016)
- cmd.exe (PID: 18940)
- cmd.exe (PID: 18948)
- cmd.exe (PID: 18956)
- cmd.exe (PID: 18964)
- cmd.exe (PID: 18992)
- cmd.exe (PID: 18984)
- cmd.exe (PID: 19000)
- cmd.exe (PID: 19008)
- cmd.exe (PID: 19024)
- cmd.exe (PID: 19032)
- cmd.exe (PID: 19040)
- cmd.exe (PID: 19048)
- cmd.exe (PID: 19056)
- cmd.exe (PID: 19072)
- cmd.exe (PID: 19080)
- cmd.exe (PID: 19088)
- cmd.exe (PID: 19064)
- cmd.exe (PID: 29192)
- cmd.exe (PID: 29164)
- cmd.exe (PID: 29200)
- cmd.exe (PID: 29208)
- cmd.exe (PID: 29216)
- cmd.exe (PID: 29224)
- cmd.exe (PID: 29736)
- cmd.exe (PID: 29824)
- cmd.exe (PID: 29832)
- cmd.exe (PID: 29848)
- cmd.exe (PID: 29840)
- cmd.exe (PID: 29856)
- cmd.exe (PID: 29888)
- cmd.exe (PID: 29864)
- cmd.exe (PID: 29904)
- cmd.exe (PID: 29896)
- cmd.exe (PID: 29912)
- cmd.exe (PID: 29928)
- cmd.exe (PID: 29240)
- cmd.exe (PID: 29248)
- cmd.exe (PID: 29728)
- cmd.exe (PID: 29744)
- cmd.exe (PID: 29752)
- cmd.exe (PID: 29964)
- cmd.exe (PID: 29972)
- cmd.exe (PID: 30000)
- cmd.exe (PID: 29980)
- cmd.exe (PID: 29988)
- cmd.exe (PID: 30388)
- cmd.exe (PID: 30716)
- cmd.exe (PID: 30572)
- cmd.exe (PID: 26704)
- cmd.exe (PID: 26112)
- cmd.exe (PID: 10676)
- cmd.exe (PID: 10696)
- cmd.exe (PID: 10772)
- cmd.exe (PID: 29920)
- cmd.exe (PID: 29936)
- cmd.exe (PID: 29956)
- cmd.exe (PID: 29948)
- cmd.exe (PID: 10776)
- cmd.exe (PID: 28676)
- cmd.exe (PID: 10700)
- cmd.exe (PID: 10668)
- cmd.exe (PID: 10692)
- cmd.exe (PID: 10680)
- cmd.exe (PID: 10688)
- cmd.exe (PID: 10656)
- cmd.exe (PID: 10180)
- cmd.exe (PID: 16132)
- cmd.exe (PID: 18092)
- cmd.exe (PID: 11460)
- cmd.exe (PID: 9740)
- cmd.exe (PID: 11512)
- cmd.exe (PID: 9756)
- cmd.exe (PID: 9980)
- cmd.exe (PID: 10652)
- cmd.exe (PID: 10636)
- cmd.exe (PID: 9480)
- cmd.exe (PID: 9900)
- cmd.exe (PID: 9936)
- cmd.exe (PID: 30016)
- cmd.exe (PID: 26200)
- cmd.exe (PID: 23780)
- cmd.exe (PID: 14424)
- cmd.exe (PID: 12716)
- cmd.exe (PID: 12744)
- cmd.exe (PID: 10440)
- cmd.exe (PID: 9860)
- cmd.exe (PID: 18076)
- cmd.exe (PID: 10124)
- cmd.exe (PID: 10908)
- cmd.exe (PID: 14648)
- cmd.exe (PID: 30148)
- cmd.exe (PID: 9556)
- cmd.exe (PID: 9124)
- cmd.exe (PID: 15852)
- cmd.exe (PID: 18252)
- cmd.exe (PID: 10932)
- cmd.exe (PID: 9408)
- cmd.exe (PID: 14160)
- cmd.exe (PID: 15844)
- cmd.exe (PID: 12220)
- cmd.exe (PID: 12972)
- cmd.exe (PID: 24220)
- cmd.exe (PID: 16844)
- cmd.exe (PID: 28804)
- cmd.exe (PID: 11540)
- cmd.exe (PID: 24080)
- cmd.exe (PID: 7676)
- cmd.exe (PID: 28548)
- cmd.exe (PID: 30460)
- cmd.exe (PID: 16756)
- cmd.exe (PID: 12456)
- cmd.exe (PID: 13044)
- cmd.exe (PID: 22864)
- cmd.exe (PID: 20364)
- cmd.exe (PID: 12372)
- cmd.exe (PID: 13276)
- cmd.exe (PID: 12480)
- cmd.exe (PID: 12364)
- cmd.exe (PID: 10204)
- cmd.exe (PID: 30532)
- cmd.exe (PID: 23300)
- cmd.exe (PID: 10588)
- cmd.exe (PID: 30472)
- cmd.exe (PID: 24240)
- cmd.exe (PID: 25080)
- cmd.exe (PID: 9568)
- cmd.exe (PID: 23672)
- cmd.exe (PID: 20616)
- cmd.exe (PID: 12848)
- cmd.exe (PID: 19736)
- cmd.exe (PID: 20032)
- cmd.exe (PID: 20200)
- cmd.exe (PID: 20580)
- cmd.exe (PID: 20660)
- cmd.exe (PID: 21224)
- cmd.exe (PID: 27392)
- cmd.exe (PID: 21584)
- cmd.exe (PID: 13392)
- cmd.exe (PID: 22684)
- cmd.exe (PID: 23140)
- cmd.exe (PID: 12584)
- cmd.exe (PID: 12684)
- cmd.exe (PID: 13612)
- cmd.exe (PID: 16252)
- cmd.exe (PID: 25124)
- cmd.exe (PID: 15832)
- cmd.exe (PID: 23640)
- cmd.exe (PID: 15648)
- cmd.exe (PID: 15048)
- cmd.exe (PID: 13780)
- cmd.exe (PID: 14560)
- cmd.exe (PID: 24060)
- cmd.exe (PID: 14372)
- cmd.exe (PID: 9692)
- cmd.exe (PID: 11908)
- cmd.exe (PID: 10408)
- cmd.exe (PID: 16536)
- cmd.exe (PID: 13216)
- cmd.exe (PID: 24068)
- cmd.exe (PID: 9100)
- cmd.exe (PID: 8944)
- cmd.exe (PID: 9700)
- cmd.exe (PID: 21944)
- cmd.exe (PID: 20072)
- cmd.exe (PID: 9960)
- cmd.exe (PID: 11740)
- cmd.exe (PID: 10472)
- cmd.exe (PID: 12644)
- cmd.exe (PID: 16628)
- cmd.exe (PID: 13104)
- cmd.exe (PID: 10572)
- cmd.exe (PID: 14208)
- cmd.exe (PID: 15328)
- cmd.exe (PID: 24632)
- cmd.exe (PID: 9188)
- cmd.exe (PID: 21384)
- cmd.exe (PID: 24804)
- cmd.exe (PID: 17096)
- cmd.exe (PID: 18504)
- cmd.exe (PID: 16292)
- cmd.exe (PID: 20336)
- cmd.exe (PID: 25776)
- cmd.exe (PID: 23836)
- cmd.exe (PID: 14876)
- cmd.exe (PID: 23324)
- cmd.exe (PID: 16472)
- cmd.exe (PID: 23652)
- cmd.exe (PID: 10400)
- cmd.exe (PID: 13916)
- cmd.exe (PID: 16392)
- cmd.exe (PID: 11216)
- cmd.exe (PID: 11776)
- cmd.exe (PID: 12000)
- cmd.exe (PID: 20108)
- cmd.exe (PID: 10480)
- cmd.exe (PID: 14820)
- cmd.exe (PID: 23544)
- cmd.exe (PID: 12140)
- cmd.exe (PID: 12124)
- cmd.exe (PID: 13160)
- cmd.exe (PID: 24140)
- cmd.exe (PID: 15332)
- cmd.exe (PID: 20836)
- cmd.exe (PID: 19652)
- cmd.exe (PID: 19820)
- cmd.exe (PID: 12108)
- cmd.exe (PID: 19768)
- cmd.exe (PID: 22788)
- cmd.exe (PID: 19712)
- cmd.exe (PID: 13724)
- cmd.exe (PID: 21904)
- cmd.exe (PID: 22960)
- cmd.exe (PID: 14060)
- cmd.exe (PID: 21356)
- cmd.exe (PID: 14688)
- cmd.exe (PID: 14664)
- cmd.exe (PID: 14040)
- cmd.exe (PID: 23168)
- cmd.exe (PID: 23588)
- cmd.exe (PID: 11824)
- cmd.exe (PID: 15120)
- cmd.exe (PID: 21044)
- cmd.exe (PID: 19828)
- cmd.exe (PID: 22772)
- cmd.exe (PID: 25184)
- cmd.exe (PID: 13032)
- cmd.exe (PID: 24716)
- cmd.exe (PID: 20636)
- cmd.exe (PID: 12436)
- cmd.exe (PID: 26568)
- cmd.exe (PID: 10820)
- cmd.exe (PID: 23252)
- cmd.exe (PID: 11880)
- cmd.exe (PID: 22532)
- cmd.exe (PID: 23144)
- cmd.exe (PID: 14436)
- cmd.exe (PID: 22752)
- cmd.exe (PID: 17816)
- cmd.exe (PID: 20668)
- cmd.exe (PID: 19716)
- cmd.exe (PID: 11404)
- cmd.exe (PID: 15924)
- cmd.exe (PID: 14252)
- cmd.exe (PID: 14228)
- cmd.exe (PID: 30076)
- cmd.exe (PID: 12532)
- cmd.exe (PID: 28820)
- cmd.exe (PID: 23428)
- cmd.exe (PID: 24160)
- cmd.exe (PID: 23296)
- cmd.exe (PID: 24484)
- cmd.exe (PID: 25552)
- cmd.exe (PID: 23612)
- cmd.exe (PID: 22892)
- cmd.exe (PID: 22716)
- cmd.exe (PID: 24180)
- cmd.exe (PID: 12712)
- cmd.exe (PID: 12608)
- cmd.exe (PID: 18528)
- cmd.exe (PID: 18348)
- cmd.exe (PID: 23936)
- cmd.exe (PID: 22540)
- cmd.exe (PID: 18012)
- cmd.exe (PID: 20604)
- cmd.exe (PID: 24216)
- cmd.exe (PID: 24500)
- cmd.exe (PID: 22904)
- cmd.exe (PID: 21116)
- cmd.exe (PID: 23648)
- cmd.exe (PID: 18052)
- cmd.exe (PID: 26548)
- cmd.exe (PID: 18072)
- cmd.exe (PID: 17612)
- cmd.exe (PID: 21656)
- cmd.exe (PID: 18360)
- cmd.exe (PID: 23940)
- cmd.exe (PID: 17624)
- cmd.exe (PID: 24168)
- cmd.exe (PID: 23028)
- cmd.exe (PID: 17720)
- cmd.exe (PID: 22840)
- cmd.exe (PID: 22976)
- cmd.exe (PID: 22688)
- cmd.exe (PID: 20828)
- cmd.exe (PID: 22900)
- cmd.exe (PID: 28120)
- cmd.exe (PID: 22896)
- cmd.exe (PID: 20620)
- cmd.exe (PID: 20776)
- cmd.exe (PID: 27052)
- cmd.exe (PID: 15548)
- cmd.exe (PID: 24584)
- cmd.exe (PID: 17808)
- cmd.exe (PID: 18064)
- cmd.exe (PID: 22700)
- cmd.exe (PID: 22592)
- cmd.exe (PID: 23292)
- cmd.exe (PID: 19640)
- cmd.exe (PID: 19568)
- cmd.exe (PID: 19532)
- cmd.exe (PID: 20128)
- cmd.exe (PID: 19576)
- cmd.exe (PID: 20148)
- cmd.exe (PID: 19644)
- cmd.exe (PID: 16000)
- cmd.exe (PID: 20028)
- cmd.exe (PID: 12324)
- cmd.exe (PID: 11032)
- cmd.exe (PID: 19992)
- cmd.exe (PID: 24404)
- cmd.exe (PID: 23680)
- cmd.exe (PID: 25004)
- cmd.exe (PID: 19556)
- cmd.exe (PID: 11848)
- cmd.exe (PID: 14444)
- cmd.exe (PID: 14992)
- cmd.exe (PID: 17296)
- cmd.exe (PID: 14860)
- cmd.exe (PID: 4364)
- cmd.exe (PID: 6400)
- cmd.exe (PID: 18236)
- cmd.exe (PID: 19596)
- cmd.exe (PID: 19648)
- cmd.exe (PID: 23356)
- cmd.exe (PID: 19764)
- cmd.exe (PID: 19816)
- cmd.exe (PID: 12068)
- cmd.exe (PID: 13492)
- cmd.exe (PID: 12148)
- cmd.exe (PID: 19936)
- cmd.exe (PID: 23232)
- cmd.exe (PID: 13952)
- cmd.exe (PID: 10748)
- cmd.exe (PID: 12092)
- cmd.exe (PID: 19600)
- cmd.exe (PID: 11976)
- cmd.exe (PID: 11900)
- cmd.exe (PID: 9160)
- cmd.exe (PID: 11736)
- cmd.exe (PID: 13832)
- cmd.exe (PID: 20876)
- cmd.exe (PID: 22832)
- cmd.exe (PID: 22668)
- cmd.exe (PID: 13472)
- cmd.exe (PID: 12856)
- cmd.exe (PID: 20352)
- cmd.exe (PID: 24256)
- cmd.exe (PID: 20296)
- cmd.exe (PID: 11788)
- cmd.exe (PID: 20988)
- cmd.exe (PID: 20372)
- cmd.exe (PID: 19960)
- cmd.exe (PID: 13480)
- cmd.exe (PID: 20788)
- cmd.exe (PID: 13456)
- cmd.exe (PID: 20980)
- cmd.exe (PID: 13908)
- cmd.exe (PID: 17832)
- cmd.exe (PID: 22972)
- cmd.exe (PID: 23156)
- cmd.exe (PID: 14752)
- cmd.exe (PID: 20780)
- cmd.exe (PID: 21900)
- cmd.exe (PID: 13324)
- cmd.exe (PID: 15940)
- cmd.exe (PID: 12836)
- cmd.exe (PID: 19772)
- cmd.exe (PID: 24144)
- cmd.exe (PID: 23816)
- cmd.exe (PID: 19824)
- cmd.exe (PID: 11300)
- cmd.exe (PID: 11764)
- cmd.exe (PID: 26240)
- cmd.exe (PID: 22608)
- cmd.exe (PID: 22852)
- cmd.exe (PID: 23208)
- cmd.exe (PID: 14720)
- cmd.exe (PID: 13700)
- cmd.exe (PID: 20196)
- cmd.exe (PID: 12616)
- cmd.exe (PID: 11468)
- cmd.exe (PID: 18352)
- cmd.exe (PID: 19388)
- cmd.exe (PID: 13368)
- cmd.exe (PID: 11616)
- cmd.exe (PID: 27444)
- cmd.exe (PID: 18912)
- cmd.exe (PID: 30044)
- cmd.exe (PID: 27288)
- cmd.exe (PID: 27408)
- cmd.exe (PID: 19272)
- cmd.exe (PID: 27568)
- cmd.exe (PID: 20312)
- cmd.exe (PID: 10132)
- cmd.exe (PID: 9268)
- cmd.exe (PID: 18080)
- cmd.exe (PID: 17204)
- cmd.exe (PID: 19996)
- cmd.exe (PID: 22616)
- cmd.exe (PID: 19860)
- cmd.exe (PID: 15080)
- cmd.exe (PID: 16328)
- cmd.exe (PID: 20036)
- cmd.exe (PID: 14204)
- cmd.exe (PID: 9148)
- cmd.exe (PID: 15136)
- cmd.exe (PID: 18084)
- cmd.exe (PID: 22876)
- cmd.exe (PID: 22208)
- cmd.exe (PID: 22888)
- cmd.exe (PID: 22628)
- cmd.exe (PID: 17148)
- cmd.exe (PID: 30580)
- cmd.exe (PID: 20080)
- cmd.exe (PID: 23676)
- cmd.exe (PID: 19592)
- cmd.exe (PID: 19780)
- cmd.exe (PID: 12872)
- cmd.exe (PID: 16160)
- cmd.exe (PID: 19572)
- cmd.exe (PID: 23276)
- cmd.exe (PID: 27652)
- cmd.exe (PID: 17572)
- cmd.exe (PID: 15144)
- cmd.exe (PID: 24408)
- cmd.exe (PID: 11652)
- cmd.exe (PID: 23148)
- cmd.exe (PID: 23068)
- cmd.exe (PID: 14760)
- cmd.exe (PID: 14528)
- cmd.exe (PID: 23124)
- cmd.exe (PID: 20380)
- cmd.exe (PID: 23132)
- cmd.exe (PID: 24792)
- cmd.exe (PID: 25172)
- cmd.exe (PID: 21864)
- cmd.exe (PID: 19748)
- cmd.exe (PID: 812)
- cmd.exe (PID: 20220)
- cmd.exe (PID: 19804)
- cmd.exe (PID: 27896)
- cmd.exe (PID: 14388)
- cmd.exe (PID: 13572)
- cmd.exe (PID: 27036)
- cmd.exe (PID: 17796)
- cmd.exe (PID: 13508)
- cmd.exe (PID: 16228)
- cmd.exe (PID: 17400)
- cmd.exe (PID: 17176)
- cmd.exe (PID: 16872)
- cmd.exe (PID: 17932)
- cmd.exe (PID: 27472)
- cmd.exe (PID: 13360)
- cmd.exe (PID: 23408)
- cmd.exe (PID: 22948)
- cmd.exe (PID: 26972)
- cmd.exe (PID: 27888)
- cmd.exe (PID: 18192)
- cmd.exe (PID: 17804)
- cmd.exe (PID: 17376)
- cmd.exe (PID: 18208)
- cmd.exe (PID: 17708)
- cmd.exe (PID: 17080)
- cmd.exe (PID: 17452)
- cmd.exe (PID: 24652)
- cmd.exe (PID: 17620)
- cmd.exe (PID: 27464)
- cmd.exe (PID: 16424)
- cmd.exe (PID: 17440)
- cmd.exe (PID: 16816)
- cmd.exe (PID: 30060)
- cmd.exe (PID: 15404)
- cmd.exe (PID: 18892)
- cmd.exe (PID: 14552)
- cmd.exe (PID: 16504)
- cmd.exe (PID: 17352)
- cmd.exe (PID: 17416)
- cmd.exe (PID: 17512)
- cmd.exe (PID: 25112)
- cmd.exe (PID: 18876)
- cmd.exe (PID: 17668)
- cmd.exe (PID: 19076)
- cmd.exe (PID: 18944)
- cmd.exe (PID: 15176)
- cmd.exe (PID: 17880)
- cmd.exe (PID: 16496)
- cmd.exe (PID: 16284)
- cmd.exe (PID: 20684)
- cmd.exe (PID: 16512)
- cmd.exe (PID: 17320)
- cmd.exe (PID: 17360)
- cmd.exe (PID: 17312)
- cmd.exe (PID: 17292)
- cmd.exe (PID: 17476)
- cmd.exe (PID: 17556)
- cmd.exe (PID: 17368)
- cmd.exe (PID: 15064)
Checks for external IP
- svchost.exe (PID: 2256)
- uwu.exe (PID: 1156)
- uwu.exe (PID: 3648)
- uwu.exe (PID: 5612)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 8900)
- cmd.exe (PID: 19284)
- cmd.exe (PID: 23264)
- cmd.exe (PID: 23616)
- cmd.exe (PID: 25012)
- cmd.exe (PID: 22880)
- cmd.exe (PID: 26440)
- cmd.exe (PID: 24984)
- cmd.exe (PID: 26756)
- cmd.exe (PID: 26344)
- cmd.exe (PID: 26664)
- cmd.exe (PID: 9884)
- uwu.exe (PID: 1156)
- cmd.exe (PID: 30156)
- cmd.exe (PID: 21204)
Uses NETSH.EXE to change the status of the firewall
- powershell.exe (PID: 19400)
- powershell.exe (PID: 13264)
Uses TASKKILL.EXE to kill Browsers
- cmd.exe (PID: 16804)
Uses WMIC.EXE to obtain operating system information
- uwu.exe (PID: 1156)
Suspicious files were dropped or overwritten
- uwu.exe (PID: 1156)
INFO
Attempting to use file storage service
- msedge.exe (PID: 6112)
Application launched itself
- msedge.exe (PID: 6412)
Executable content was dropped or overwritten
- msedge.exe (PID: 6412)
The Powershell gets current clipboard
- powershell.exe (PID: 13692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
1 898
Monitored processes
1 766
Malicious processes
32
Suspicious processes
68
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | C:\WINDOWS\system32\cmd.exe /c "C:\Users\admin\AppData\Local\Temp\_MEI81562\uwu.exe -m pip install pycryptodomex" | C:\Windows\System32\cmd.exe | — | uwu.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 368 | C:\WINDOWS\system32\cmd.exe /c "C:\Users\admin\AppData\Local\Temp\_MEI81562\uwu.exe -m pip install requests" | C:\Windows\System32\cmd.exe | — | uwu.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 692 | C:\Users\admin\AppData\Local\Temp\_MEI81562\uwu.exe -m pip install pycryptodomex | C:\Users\admin\AppData\Local\Temp\_MEI81562\uwu.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 812 | C:\WINDOWS\system32\cmd.exe /c "ta"sk"ki"ll /im d /t /f >nul 2>&1" | C:\Windows\System32\cmd.exe | — | uwu.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1072 | C:\Users\admin\AppData\Local\Temp\_MEI81562\uwu.exe -m pip install requests | C:\Users\admin\AppData\Local\Temp\_MEI81562\uwu.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1144 | C:\Users\admin\AppData\Local\Temp\_MEI81562\uwu.exe -m pip install requests | C:\Users\admin\AppData\Local\Temp\_MEI81562\uwu.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1156 | "C:\Users\admin\AppData\Local\Temp\_MEI81562\uwu.exe" | C:\Users\admin\AppData\Local\Temp\_MEI81562\uwu.exe | uwu.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 1236 | C:\WINDOWS\system32\cmd.exe /c "C:\Users\admin\AppData\Local\Temp\_MEI81562\uwu.exe -m pip install pycryptodomex" | C:\Windows\System32\cmd.exe | — | uwu.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1256 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=35 --mojo-platform-channel-handle=5932 --field-trial-handle=2396,i,10248723916609393204,15992552871860310338,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
66 477
Read events
66 446
Write events
31
Delete events
0
Modification events
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 2B2E8841F9812F00 | |||
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: A0628F41F9812F00 | |||
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590776 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {01B3BB67-2058-4ACE-838F-BC12567E037B} | |||
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590776 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {CE9F5B87-A3B8-4527-8DC2-21A25C295BD3} | |||
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590776 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {FBAEDA5C-DEDF-4662-A6C0-33F4F7B2E754} | |||
| (PID) Process: | (6412) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\590776 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3CF7D728-B226-4248-B2A6-8CAE90D32057} | |||
Executable files
4 180
Suspicious files
256
Text files
500
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF3f50ec.TMP | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF3f50ec.TMP | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF3f50ec.TMP | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF3f511b.TMP | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF3f511b.TMP | — | |
MD5:— | SHA256:— | |||
| 6412 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
112
DNS requests
99
Threats
28
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2464 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8136 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8136 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5388 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5920 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6412 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
gofile.io |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6112 | msedge.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
6112 | msedge.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
6112 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
6112 | msedge.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
6112 | msedge.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
6112 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
6112 | msedge.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
6112 | msedge.exe | Misc activity | ET INFO File Sharing Related Domain in TLS SNI (gofile .io) |
6112 | msedge.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
6112 | msedge.exe | Potentially Bad Traffic | ET INFO Online File Storage Domain in DNS Lookup (gofile .io) |
1 ETPRO signatures available at the full report