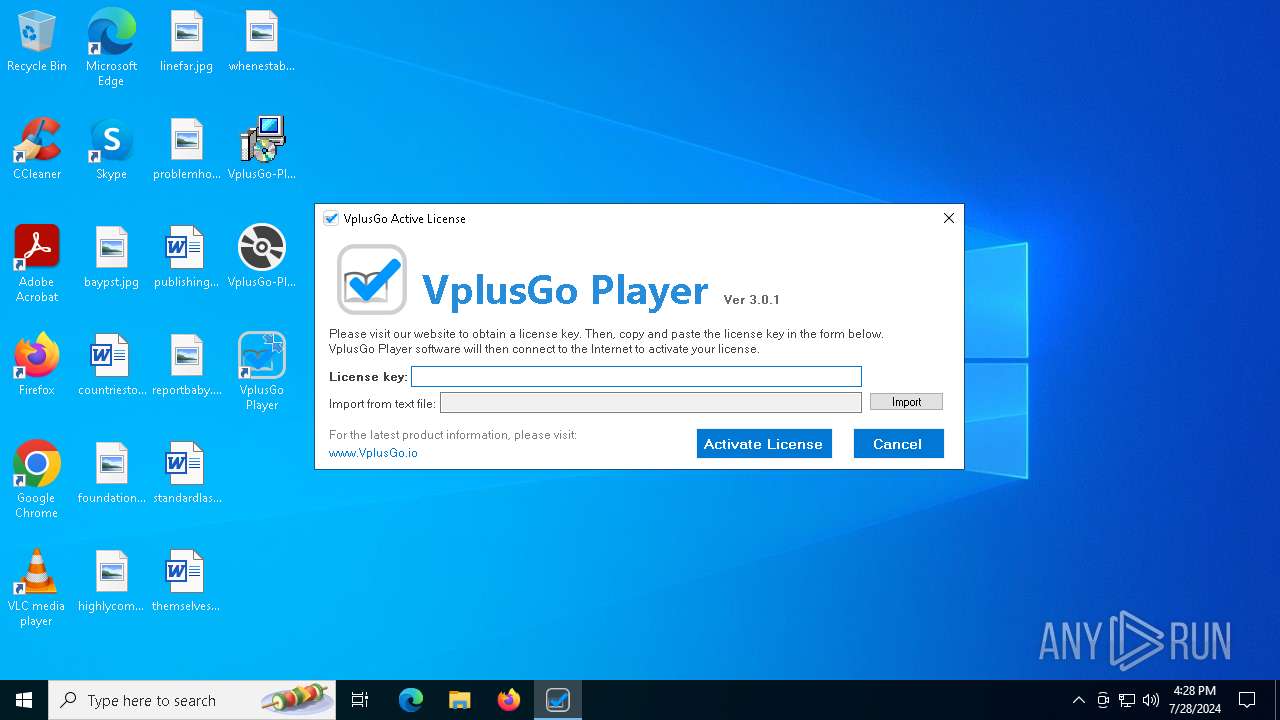
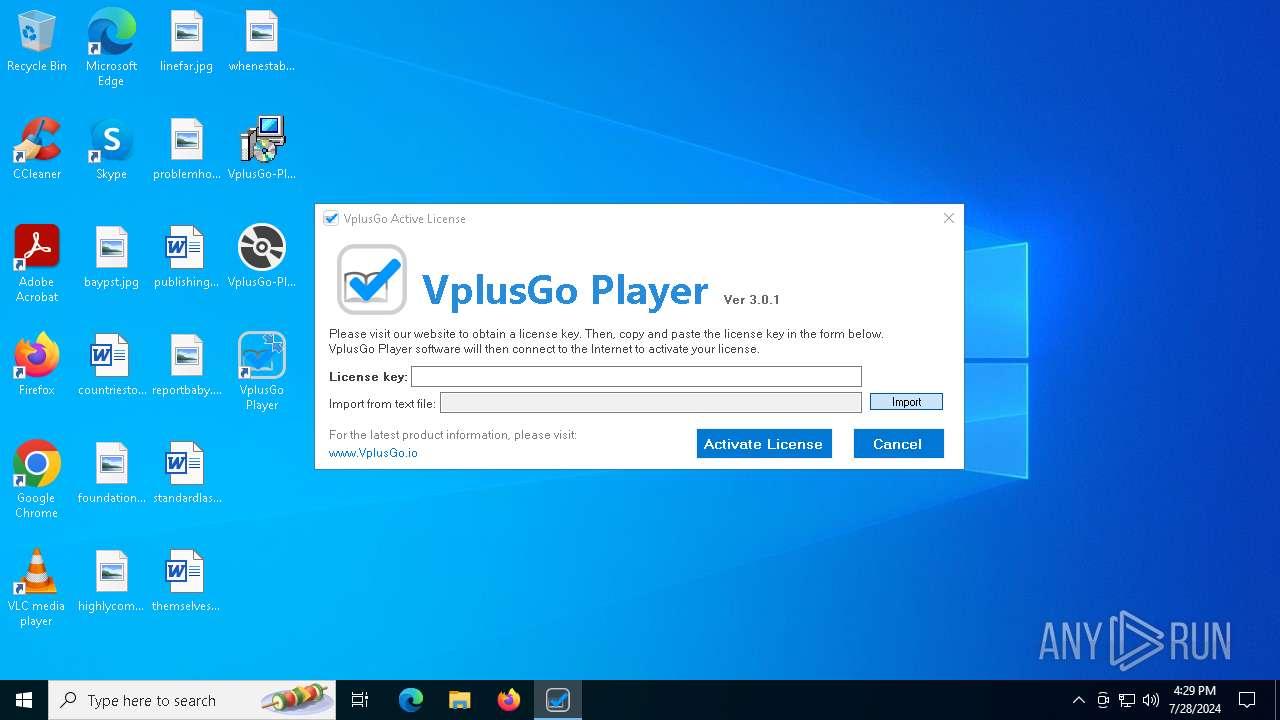
| File name: | VplusGo-Player-setup-3.0.1.exe |
| Full analysis: | https://app.any.run/tasks/ef29823a-3acc-40ef-b7dd-8603fbc3b0f4 |
| Verdict: | Malicious activity |
| Analysis date: | July 28, 2024, 16:27:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 4C903390553E3792F3DB4507F32760E8 |
| SHA1: | 3BC5AA329F1CCB52420FC7EFD24CD209FE179BF9 |
| SHA256: | 647670DE7CE0792885EA2BAA6CF22F2E5501033C6381B08499F56DCEDBB9D159 |
| SSDEEP: | 12288:En2eZ5GGRXv+V5ZI+JpeMcIcniV3tqZZrAttJVVVVVVVVVVVVVVVVVVVOVVVVVVc:En2QGGRfmbIGE2ZUL |
MALICIOUS
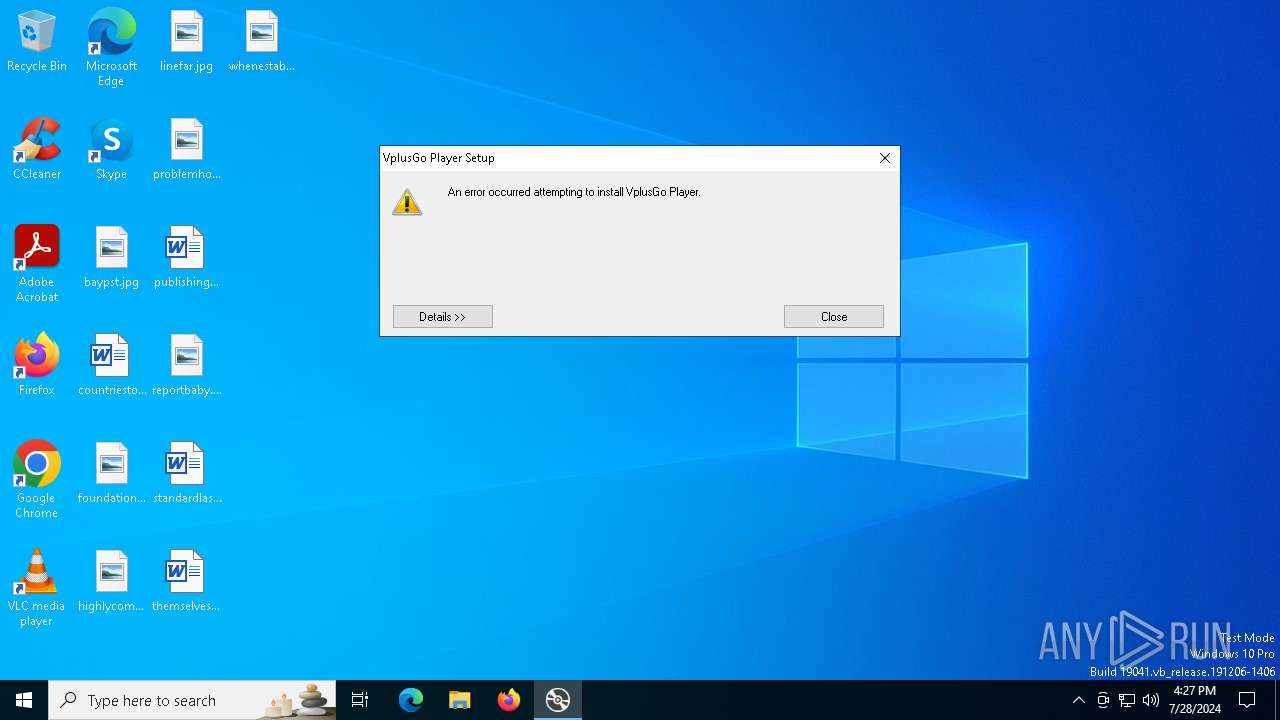
Drops the executable file immediately after the start
- VplusGo-Player-setup-3.0.1.exe (PID: 5040)
- msiexec.exe (PID: 6552)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 1128)
- msiexec.exe (PID: 6552)
Executes as Windows Service
- VSSVC.exe (PID: 6124)
The process creates files with name similar to system file names
- msiexec.exe (PID: 6552)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2944)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6552)
INFO
Checks supported languages
- VplusGo-Player-setup-3.0.1.exe (PID: 5040)
- msiexec.exe (PID: 6552)
- msiexec.exe (PID: 2592)
- msiexec.exe (PID: 624)
- Player.exe (PID: 5956)
- msiexec.exe (PID: 2944)
Create files in a temporary directory
- VplusGo-Player-setup-3.0.1.exe (PID: 5040)
- msiexec.exe (PID: 2592)
- msiexec.exe (PID: 624)
Manual execution by a user
- msiexec.exe (PID: 1128)
- Player.exe (PID: 5956)
Reads the computer name
- VplusGo-Player-setup-3.0.1.exe (PID: 5040)
- msiexec.exe (PID: 6552)
- msiexec.exe (PID: 2592)
- msiexec.exe (PID: 2944)
- Player.exe (PID: 5956)
- msiexec.exe (PID: 624)
Drops the executable file immediately after the start
- msiexec.exe (PID: 1128)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1128)
- msiexec.exe (PID: 6552)
Creates a software uninstall entry
- msiexec.exe (PID: 6552)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2944)
- Player.exe (PID: 5956)
Creates files in the program directory
- Player.exe (PID: 5956)
Checks proxy server information
- slui.exe (PID: 7028)
Reads the software policy settings
- slui.exe (PID: 7028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:07:27 20:06:14+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.34 |
| CodeSize: | 394240 |
| InitializedDataSize: | 168448 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3a320 |
| OSVersion: | 5.1 |
| ImageVersion: | 10 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 17.0.33927.210 |
| ProductVersionNumber: | 17.0.33927.210 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | - |
| FileDescription: | Setup |
| FileVersion: | 17.0.33927.210 built by: D17.7 |
| InternalName: | setup.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | setup.exe |
| ProductName: | - |
| ProductVersion: | 17.0.33927.210 |
Total processes
159
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 624 | C:\Windows\syswow64\MsiExec.exe -Embedding 690D4E4345AA13A93E958C31D82274E6 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | "C:\WINDOWS\System32\msiexec.exe" /i "C:\Users\admin\Desktop\VplusGo-Player-setup-3.0.1.msi" | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2592 | C:\Windows\syswow64\MsiExec.exe -Embedding 2B4977B9098B27E2C8A7A3F4680A919F C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2944 | C:\Windows\syswow64\MsiExec.exe -Embedding 8FBA035DEA841E6857FC7B63636CF509 E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4544 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5040 | "C:\Users\admin\AppData\Local\Temp\VplusGo-Player-setup-3.0.1.exe" | C:\Users\admin\AppData\Local\Temp\VplusGo-Player-setup-3.0.1.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup Exit code: 1603 Version: 17.0.33927.210 built by: D17.7 Modules
| |||||||||||||||
| 5956 | "C:\Program Files\VplusGo Exam Simulator\VplusGo Player\Player.exe" | C:\Program Files\VplusGo Exam Simulator\VplusGo Player\Player.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Player Version: 3.0.1 Modules
| |||||||||||||||
| 6124 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6552 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6704 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 730
Read events
10 353
Write events
356
Delete events
21
Modification events
| (PID) Process: | (6552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000054C46200BE1DA019819000074100000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000054C46200BE1DA019819000074100000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000016289C200BE1DA019819000074100000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000016289C200BE1DA019819000074100000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000DA909E200BE1DA019819000074100000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 480000000000000030A3A3200BE1DA019819000074100000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000BF1F2E210BE1DA019819000074100000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6552) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000DBFE2F210BE1DA0198190000C8160000E80300000100000000000000000000005DC155E6B713CF47B9924B7CF88E2E6300000000000000000000000000000000 | |||
| (PID) Process: | (6124) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000BF0743210BE1DA01EC170000281B0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
31
Suspicious files
21
Text files
6
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6552 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1128 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI8247.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 6552 | msiexec.exe | C:\Windows\Temp\~DF2CE85711B180ECCE.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 2592 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFG82F3.tmp | xml | |
MD5:68675E0D405C8C76102802FA624EB895 | SHA256:B839CDD1C3F55651CD4D0E54A679BCE5AC60ED7618A7B74BFC8EF8CA311E53ED | |||
| 6552 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{e655c15d-13b7-47cf-b992-4b7cf88e2e63}_OnDiskSnapshotProp | binary | |
MD5:99FBAD8DA7425CC3DB37BCE4CB960AEB | SHA256:ACD4FDBA724A6E9A9A10238BE3937B3B6A5E5CA7640D68A48225961F69E8F1BB | |||
| 1128 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI8303.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 6552 | msiexec.exe | C:\Windows\Temp\~DF01D8216763C9A261.TMP | binary | |
MD5:E96442075619B4D84C49248275D49CB8 | SHA256:D8B7ACD34580D89C411AD104E6397DE02D962DBDF9F66E45DB84EDF67E0646CB | |||
| 6552 | msiexec.exe | C:\Windows\Installer\MSIF4F8.tmp | binary | |
MD5:A0FB552C77FBC246CFDDEBF7B3091D4C | SHA256:0CCF7AF6F8FDCC416D81DBEF07E6D57F027AFD56326C112D90B7BB257389EBBB | |||
| 6552 | msiexec.exe | C:\Windows\Installer\MSIF3AE.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
| 6552 | msiexec.exe | C:\Windows\Installer\MSIF43C.tmp | executable | |
MD5:B77A2A2768B9CC78A71BBFFB9812B978 | SHA256:F74C97B1A53541B059D3BFAFE41A79005CE5065F8210D7DE9F1B600DC4E28AA0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
58
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4424 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3676 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
504 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4132 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4548 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 131.253.33.254:443 | a-ring-fallback.msedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 2.16.110.193:443 | www.bing.com | Akamai International B.V. | DE | unknown |
1108 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6064 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1044 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
t-ring-fdv2.msedge.net |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
a-ring-fallback.msedge.net |
| unknown |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fp-afd-nocache-ccp.azureedge.net |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |