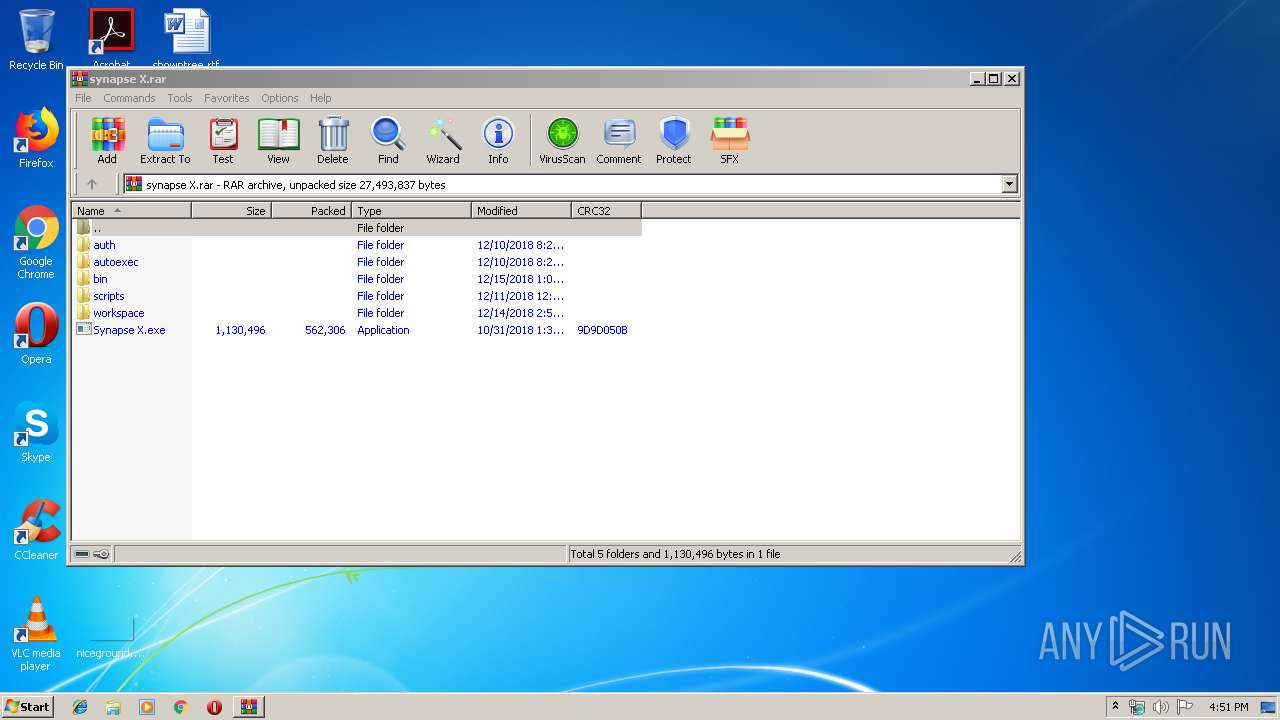
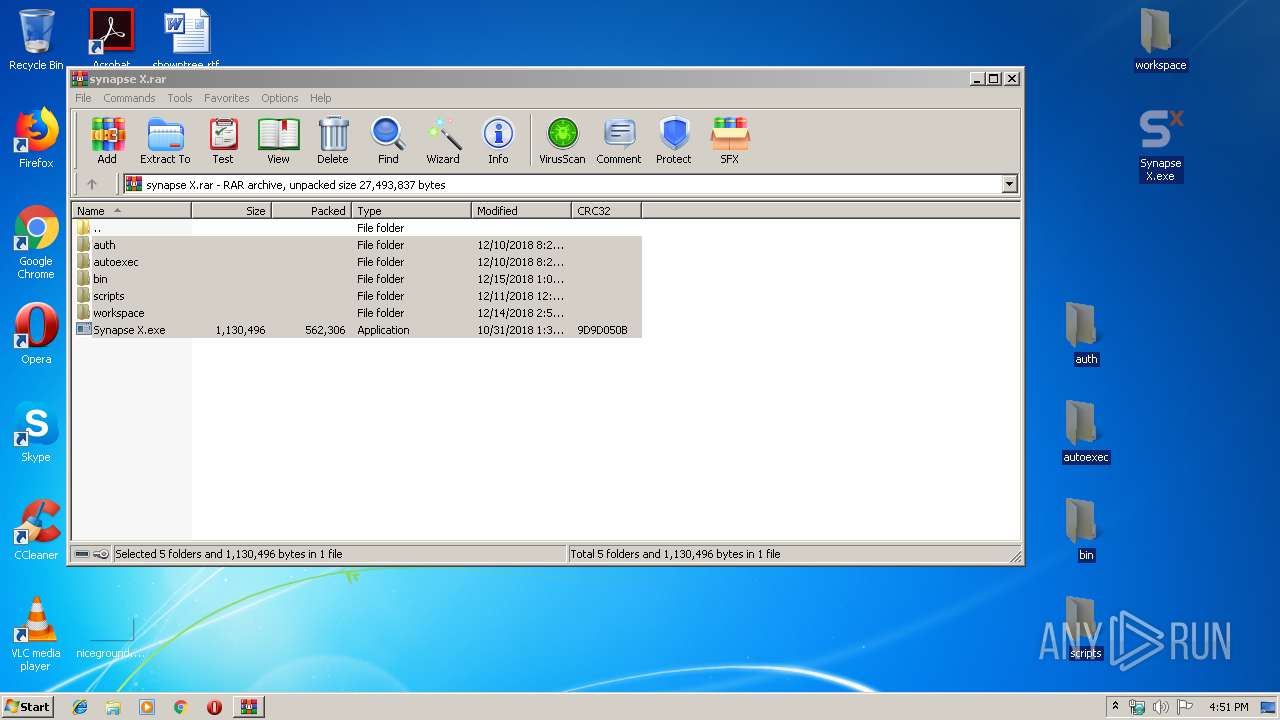
| File name: | synapse X.rar |
| Full analysis: | https://app.any.run/tasks/dcb4e85e-41fb-47de-862b-072e094f4678 |
| Verdict: | Malicious activity |
| Analysis date: | September 18, 2019, 15:50:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 6FCA5B4A7BC097ADC31FCCAC30A33B0E |
| SHA1: | 8E0069E54BE8C273B971305A2BDE63BE4287DE2C |
| SHA256: | 6474CCBE9FB70F4664AB6754EADB2A574012426E66B2FB91666A9BAE61712C71 |
| SSDEEP: | 393216:PsC5SDznkacZI/fXB6tNxNbvvR9nj5fo4baukHCBds:PsLznXci0NxB3R9OBiB2 |
MALICIOUS
Application was dropped or rewritten from another process
- Synapse X.exe (PID: 2448)
- Synapse X.exe (PID: 3320)
- C7FB8689DFEAC65B.bin (PID: 3716)
- C7FB8689DFEAC65B.bin (PID: 3804)
Loads dropped or rewritten executable
- C7FB8689DFEAC65B.bin (PID: 3716)
- SearchProtocolHost.exe (PID: 1000)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3852)
- Synapse X.exe (PID: 2448)
Starts application with an unusual extension
- Synapse X.exe (PID: 2448)
- Synapse X.exe (PID: 3320)
Reads the BIOS version
- C7FB8689DFEAC65B.bin (PID: 3716)
Reads Environment values
- C7FB8689DFEAC65B.bin (PID: 3716)
INFO
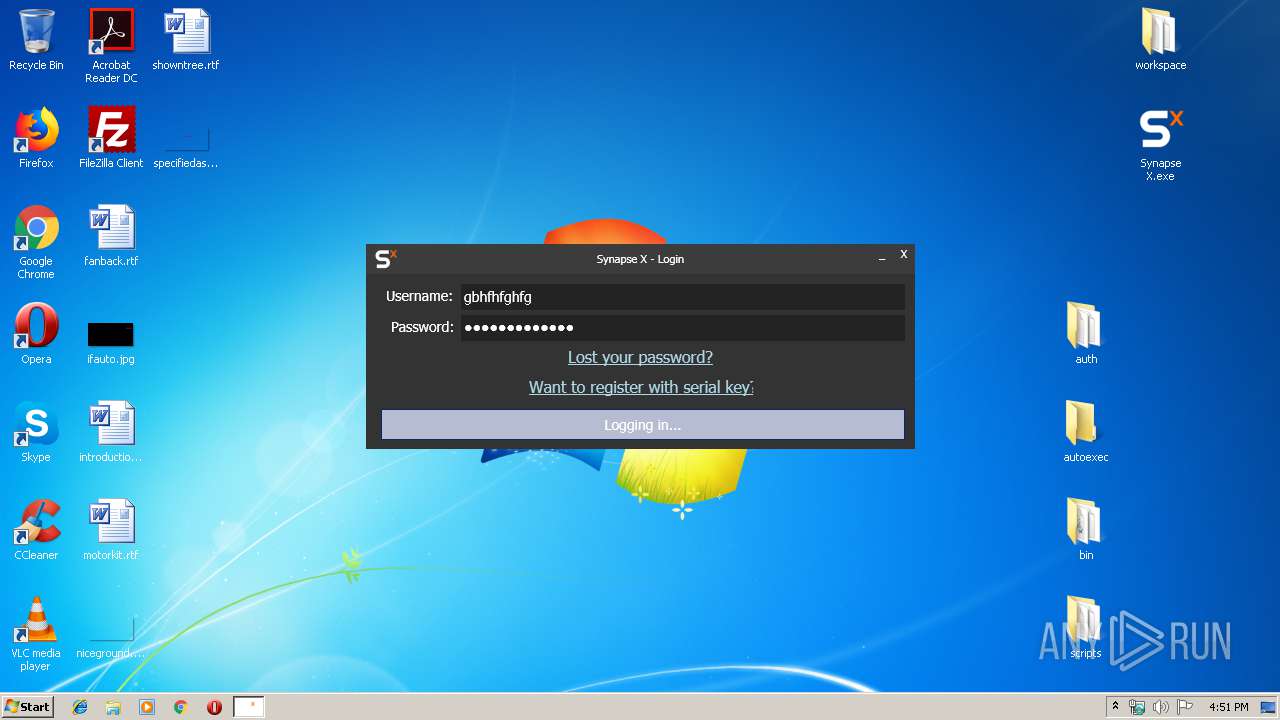
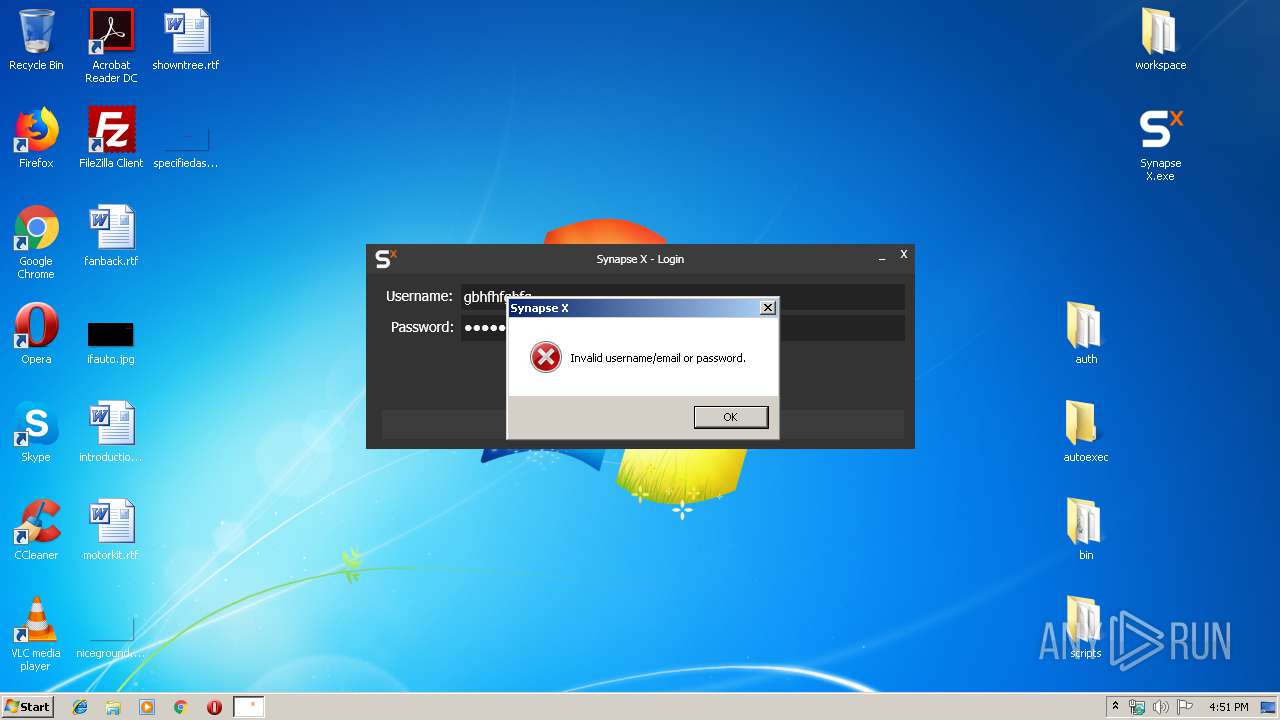
Manual execution by user
- Synapse X.exe (PID: 2448)
- Synapse X.exe (PID: 3320)
Reads settings of System Certificates
- C7FB8689DFEAC65B.bin (PID: 3716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
39
Monitored processes
6
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1000 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
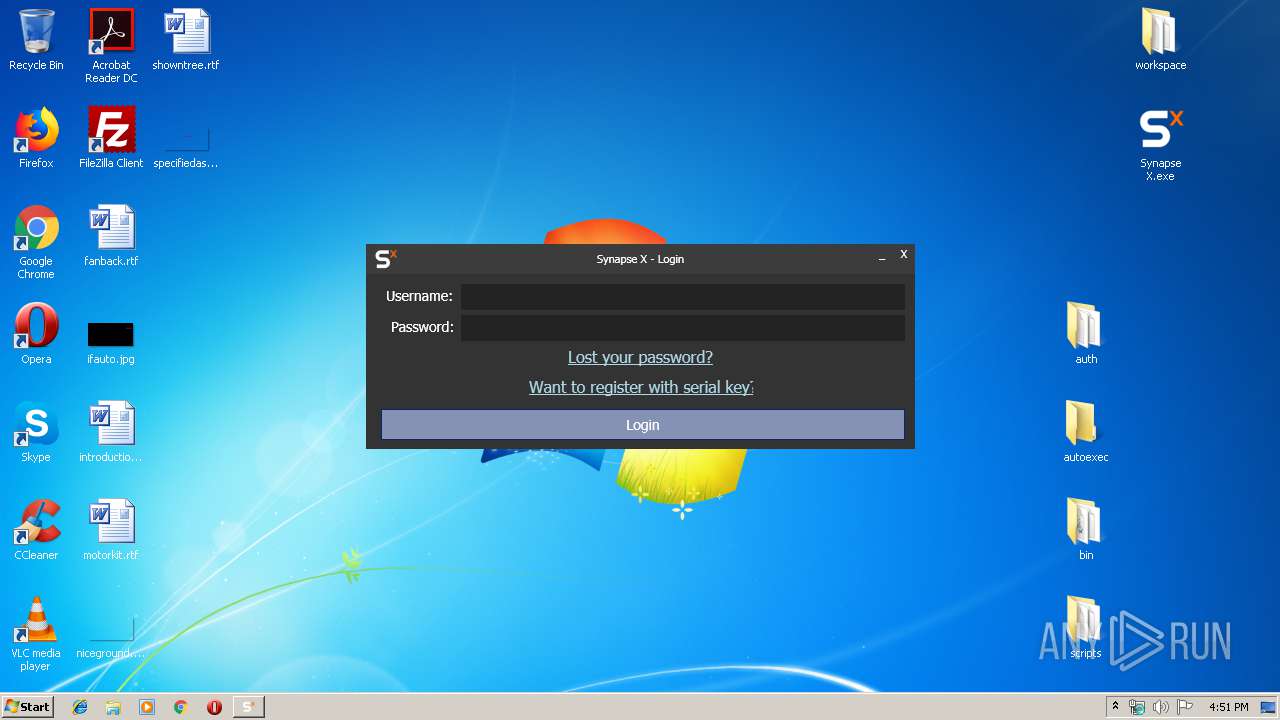
| 2448 | "C:\Users\admin\Desktop\Synapse X.exe" | C:\Users\admin\Desktop\Synapse X.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Synapse Bootstrapper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3320 | "C:\Users\admin\Desktop\Synapse X.exe" | C:\Users\admin\Desktop\Synapse X.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Synapse Bootstrapper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3716 | "bin\C7FB8689DFEAC65B.bin" | C:\Users\admin\Desktop\bin\C7FB8689DFEAC65B.bin | Synapse X.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Synapse UI WPF Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3804 | "bin\C7FB8689DFEAC65B.bin" | C:\Users\admin\Desktop\bin\C7FB8689DFEAC65B.bin | — | Synapse X.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Synapse UI WPF Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3852 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\synapse X.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
937
Read events
855
Write events
82
Delete events
0
Modification events
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\synapse X.rar | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3852) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
8
Suspicious files
0
Text files
84
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3852.37009\bin\4EF437B6217B677D.dll | executable | |
MD5:— | SHA256:— | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3852.37009\bin\theme.json | text | |
MD5:— | SHA256:— | |||
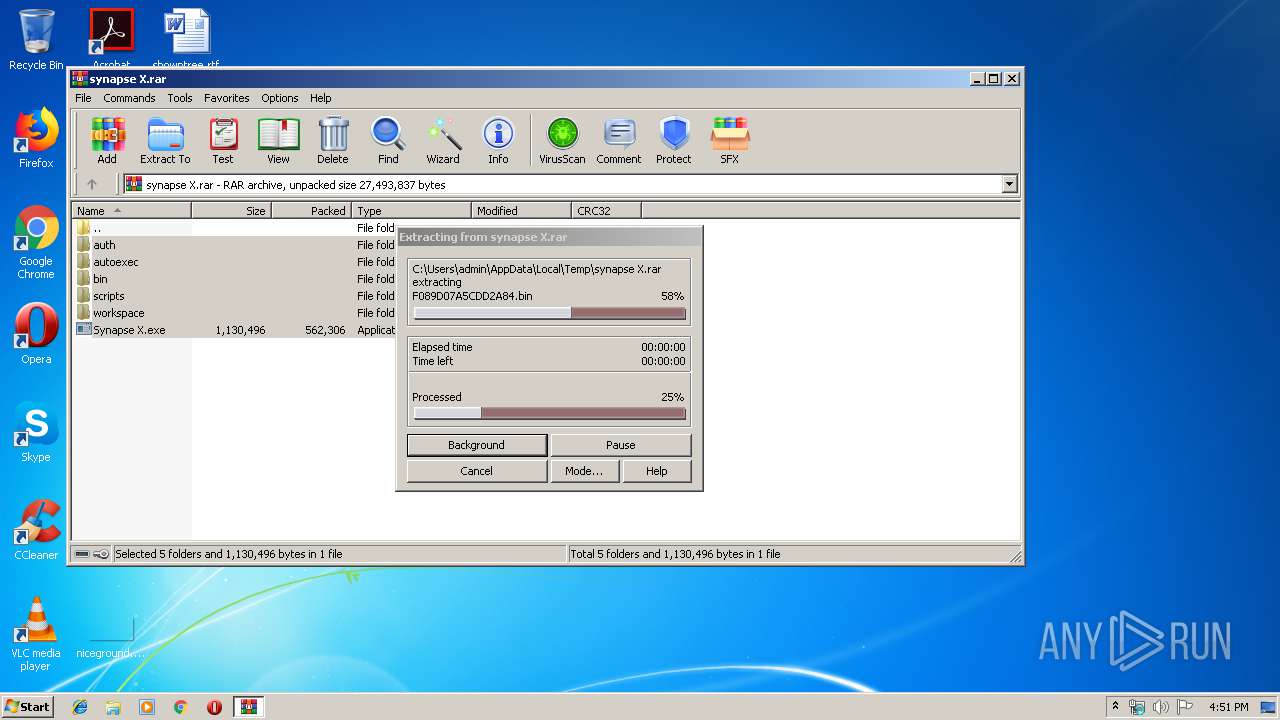
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3852.37009\bin\F089D07A5CDD2A84.bin | executable | |
MD5:— | SHA256:— | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3852.37009\bin\SynapseInjector.dll | executable | |
MD5:— | SHA256:— | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3852.37009\bin\Monaco.html | html | |
MD5:999896134BD43CEFA865F37E514BA62F | SHA256:1ECDD9529EF5487F92736894D94FF680F6C32EE821615D29C0FC814F3A310B4A | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3852.37009\bin\vs\base\worker\workerMain.js | text | |
MD5:27EAD90C7702154755785E0E53398755 | SHA256:BDF9433692A08851E13DD58504EEF19F51BD2EC7241923A68EDF5772E0E53AF5 | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3852.37009\bin\vs\basic-languages\bat\bat.js | text | |
MD5:4CB475399C4490EEA41982DCD6D9653E | SHA256:9BCA42394FE8922FEC24B768EEB8CE04692DE6FAD82F9052D5B7E70F5C6B0F40 | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3852.37009\bin\vs\basic-languages\coffee\coffee.js | text | |
MD5:9D0C4AC1691EED0A480C3E9246490D29 | SHA256:E706C9F8E5C5A0CB01B2F4E4879EC34A050D6EB2A8840284EB7BADD9D78099F9 | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3852.37009\bin\vs\basic-languages\css\css.js | text | |
MD5:49AD30F1151CFD7A74677FDC6DD13DA9 | SHA256:BD331FD3BD2C37B0C3150035325F163AC9266BF6D942310764815E676D856D91 | |||
| 3852 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3852.37009\bin\vs\basic-languages\cpp\cpp.js | text | |
MD5:0A16509E6CD0155FB622E785CFE976C7 | SHA256:A7C2BEA7CA3D9E203A3A286735945FE010C8F4F8D46620386EE8BEFC6A78B32B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
2
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2448 | Synapse X.exe | 104.20.166.135:443 | synapse.to | Cloudflare Inc | US | shared |
2448 | Synapse X.exe | 104.20.165.135:443 | synapse.to | Cloudflare Inc | US | shared |
3320 | Synapse X.exe | 104.20.166.135:443 | synapse.to | Cloudflare Inc | US | shared |
3716 | C7FB8689DFEAC65B.bin | 104.20.166.135:443 | synapse.to | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
synapse.to |
| whitelisted |
cdn.synapse.to |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |
1060 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |