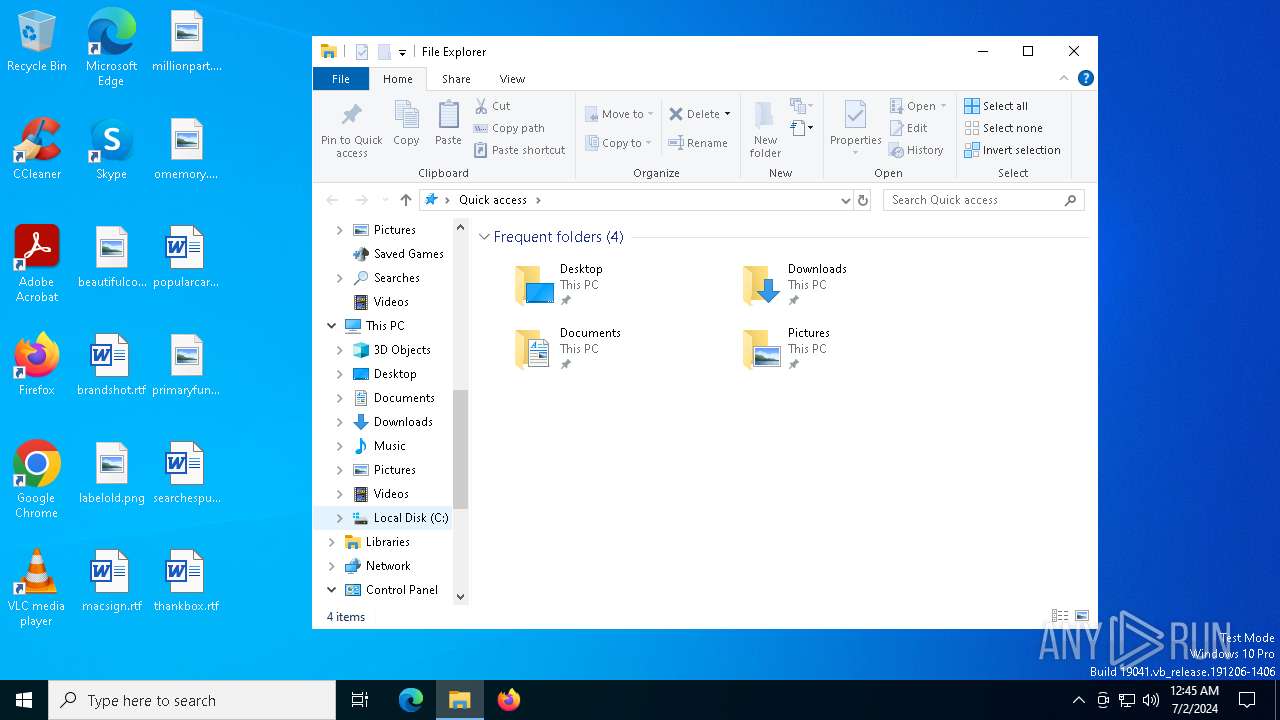
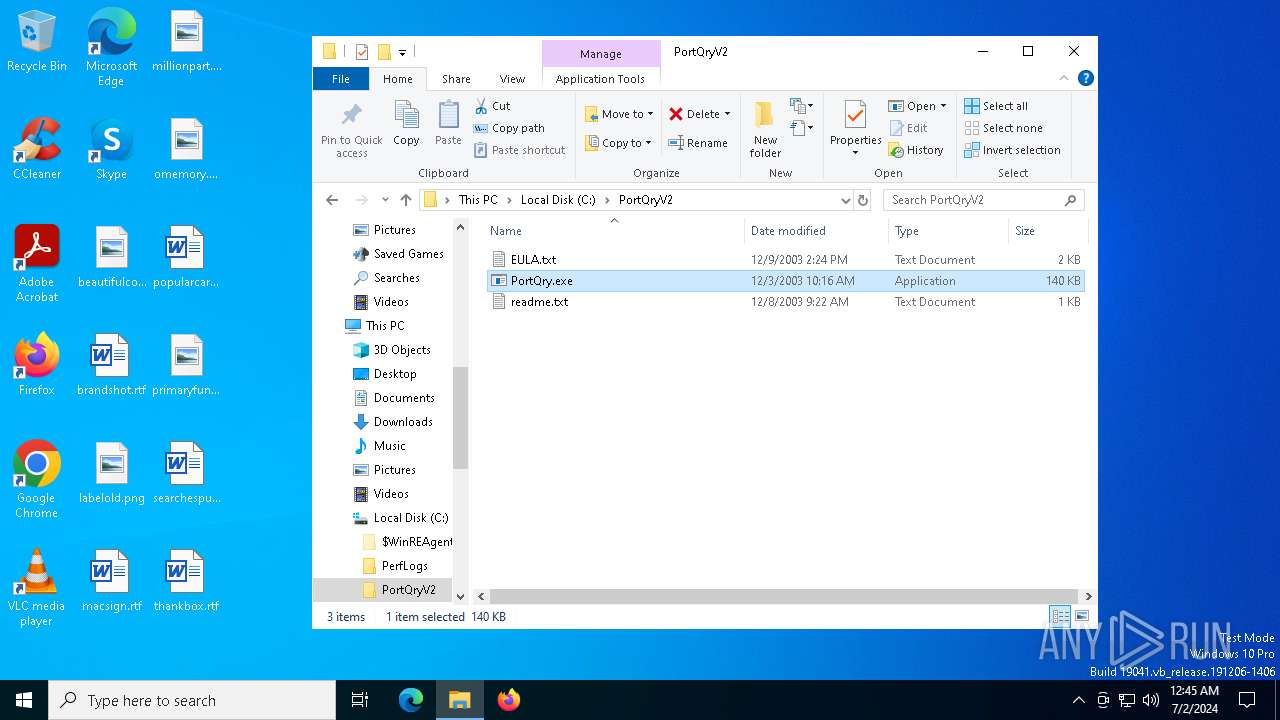
| File name: | PortQryV2.exe |
| Full analysis: | https://app.any.run/tasks/b898781a-de3b-4aba-abc4-034e94fb0cc8 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2024, 00:44:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
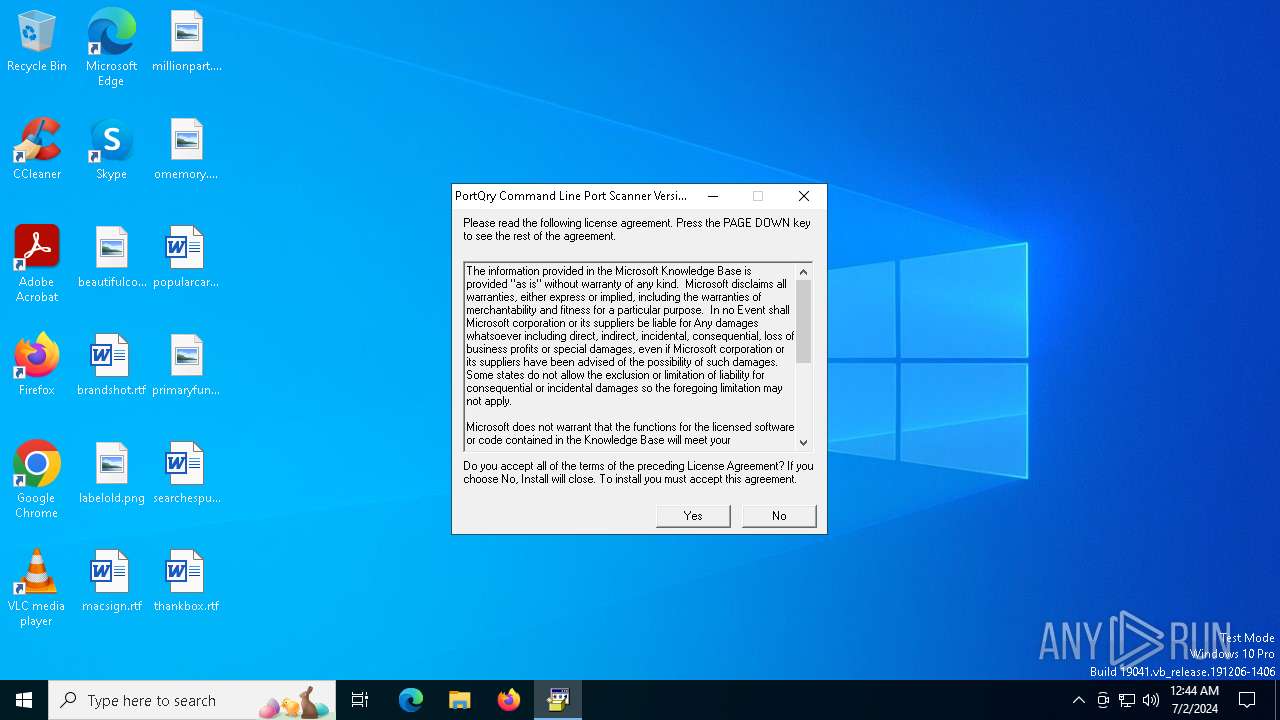
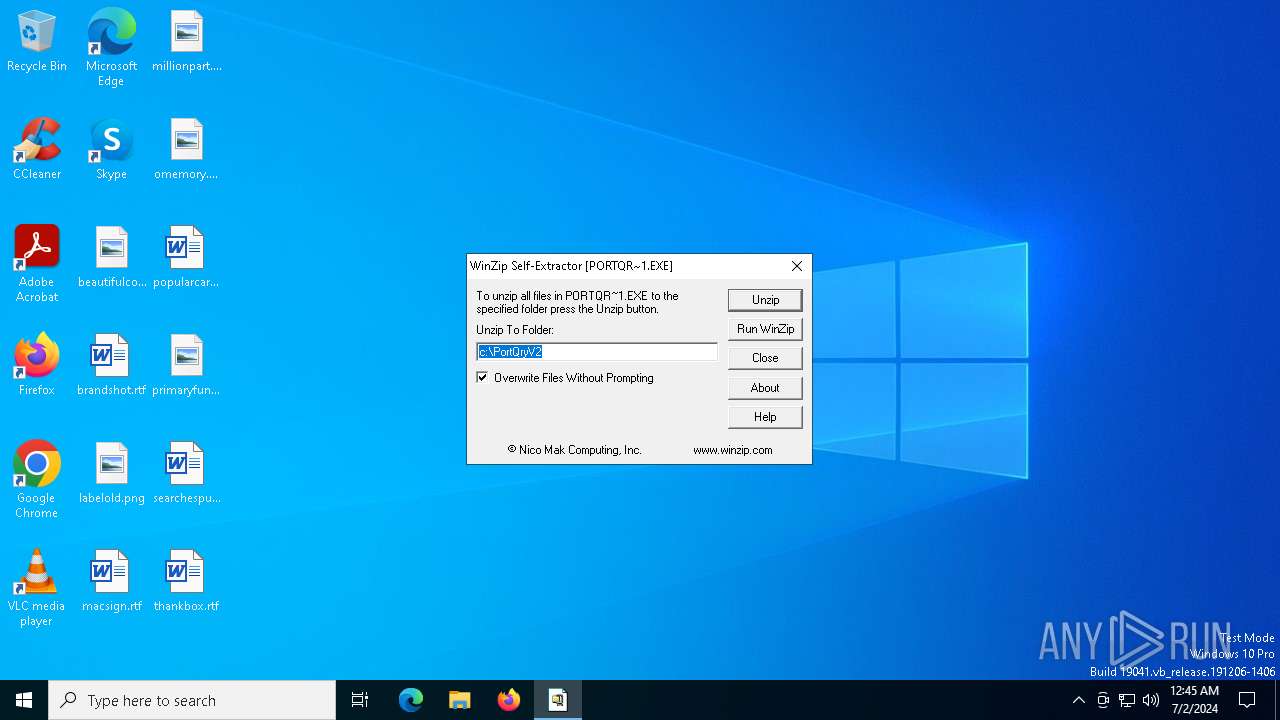
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, MS CAB-Installer self-extracting archive |
| MD5: | 8989182873E865E4D04FBC3C87E2F520 |
| SHA1: | 015612749867D3A91AF13AEFB138E2DB89EFF227 |
| SHA256: | 6471C5190A99E3D1F337FCFEF1FC410E8D487B66E093F924700E186CBD398DC0 |
| SSDEEP: | 3072:RydJq5oyVzs+h0J05ieO4X/gsjnx9yr6AOWEQnYVDZILCIl3WSYgStb:kW2+POmYsz2UWHYHECGLHSh |
MALICIOUS
Changes the autorun value in the registry
- PortQryV2.exe (PID: 4220)
Drops the executable file immediately after the start
- PortQryV2.exe (PID: 4220)
- PORTQR~1.EXE (PID: 3992)
SUSPICIOUS
Process drops legitimate windows executable
- PortQryV2.exe (PID: 4220)
Executable content was dropped or overwritten
- PortQryV2.exe (PID: 4220)
- PORTQR~1.EXE (PID: 3992)
Starts a Microsoft application from unusual location
- PortQryV2.exe (PID: 4220)
INFO
Checks supported languages
- PortQryV2.exe (PID: 4220)
- PORTQR~1.EXE (PID: 3992)
- PortQry.exe (PID: 3828)
Reads the computer name
- PortQryV2.exe (PID: 4220)
- PORTQR~1.EXE (PID: 3992)
Create files in a temporary directory
- PortQryV2.exe (PID: 4220)
Manual execution by a user
- PortQry.exe (PID: 3828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 MS Cabinet Self-Extractor (WExtract stub) (80.4) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (8.2) |
| .exe | | | Win64 Executable (generic) (7.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.7) |
| .exe | | | Win32 Executable (generic) (1.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2002:08:29 08:25:42+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7 |
| CodeSize: | 34816 |
| InitializedDataSize: | 105984 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5ae4 |
| OSVersion: | 5.1 |
| ImageVersion: | 5.1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.0.2800.1106 |
| ProductVersionNumber: | 6.0.2800.1106 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Win32 Cabinet Self-Extractor |
| FileVersion: | 6.00.2800.1106 (xpsp1.020828-1920) |
| InternalName: | Wextract |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | WEXTRACT.EXE |
| ProductName: | Microsoft® Windows® Operating System |
| ProductVersion: | 6.00.2800.1106 |
Total processes
136
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2556 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3828 | "C:\PortQryV2\PortQry.exe" | C:\PortQryV2\PortQry.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 99 Modules
| |||||||||||||||
| 3992 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\PORTQR~1.EXE | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\PORTQR~1.EXE | PortQryV2.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 4020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PortQry.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4220 | "C:\Users\admin\AppData\Local\Temp\PortQryV2.exe" | C:\Users\admin\AppData\Local\Temp\PortQryV2.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 6.00.2800.1106 (xpsp1.020828-1920) Modules
| |||||||||||||||
Total events
387
Read events
385
Write events
1
Delete events
1
Modification events
| (PID) Process: | (4220) PortQryV2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | wextract_cleanup0 |
Value: rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\" | |||
| (PID) Process: | (4220) PortQryV2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | wextract_cleanup0 |
Value: | |||
Executable files
2
Suspicious files
0
Text files
2
Unknown types
0
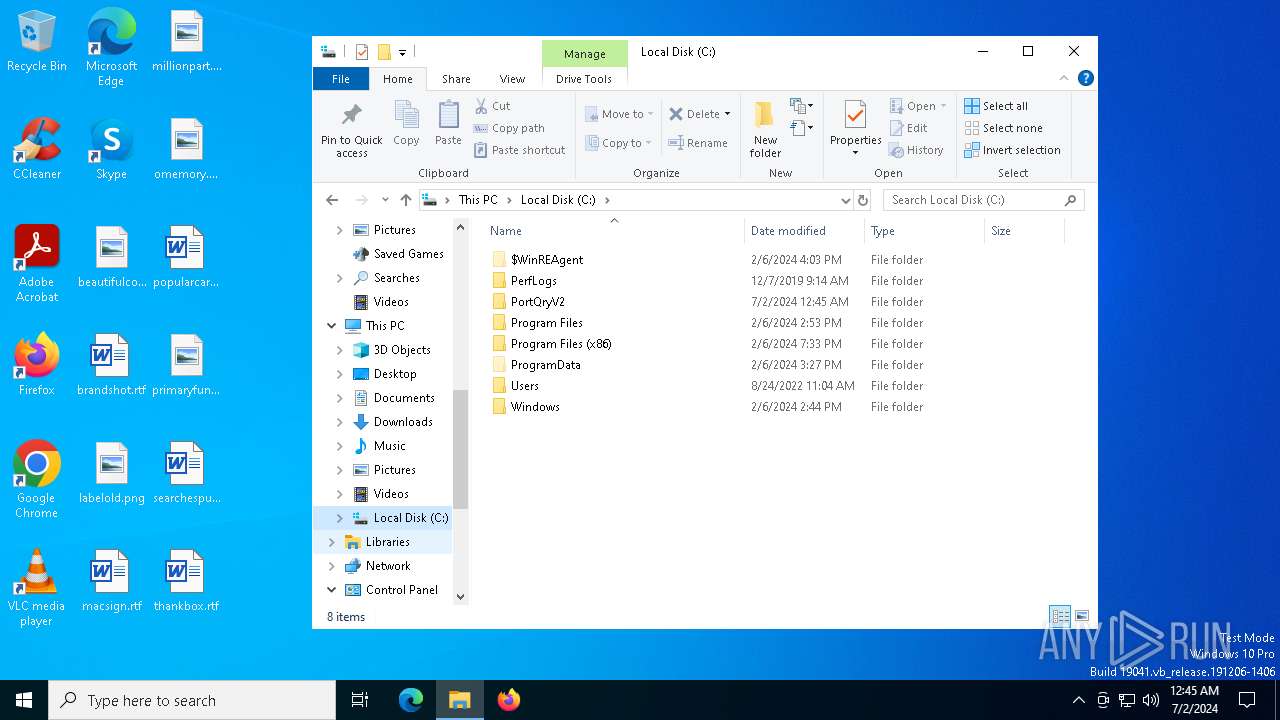
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3992 | PORTQR~1.EXE | C:\PortQryV2\PortQry.exe | executable | |
MD5:C6AC67F4076CA431ACC575912C194245 | SHA256:FB6CEBADD49D202C8C7B5CDD641BD16AAC8258429E8FACE365A94BD32E253B00 | |||
| 4220 | PortQryV2.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\PORTQR~1.EXE | executable | |
MD5:84BF1A69D5B301DDD97FF4F5B9384164 | SHA256:F2B523CA6D92F1F4DB72A0BB86B911C12DB51C894016A2A3ACECC064F6324C8D | |||
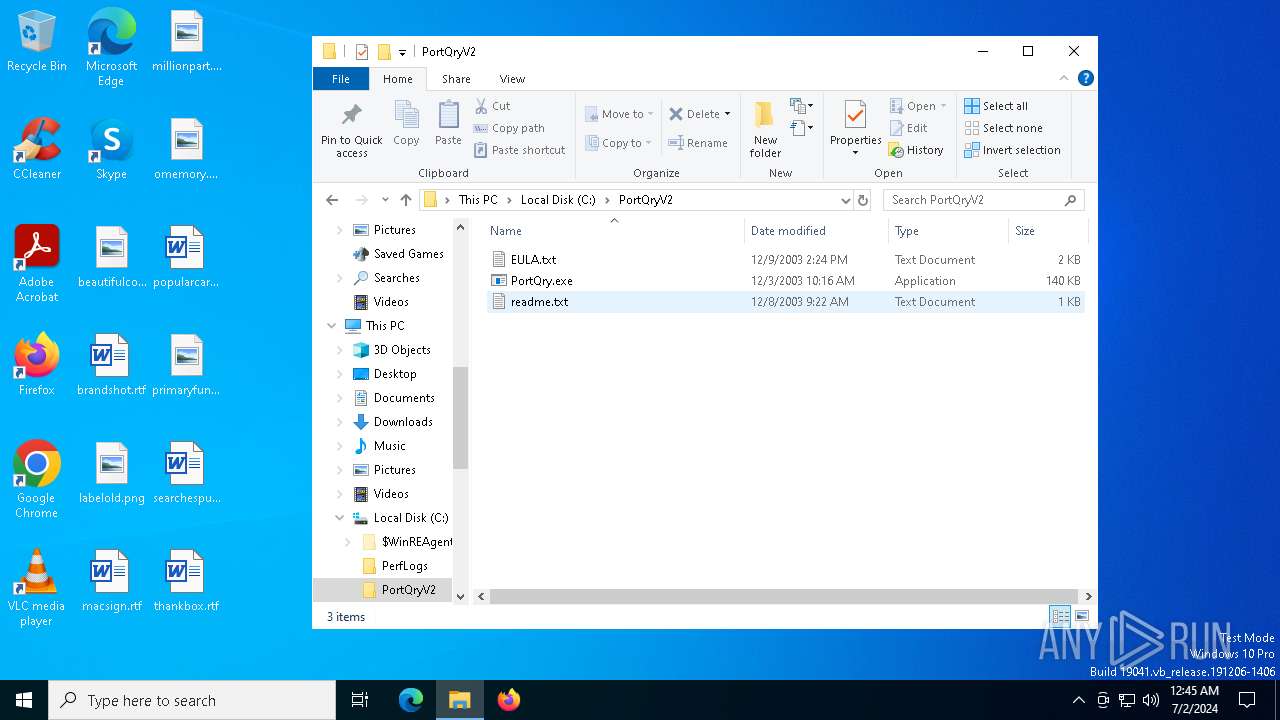
| 3992 | PORTQR~1.EXE | C:\PortQryV2\EULA.txt | text | |
MD5:216B42886A531F92E9F5B31F02874405 | SHA256:6976881B637E1422F8403C64483C0D025074E1892A7F30B641F5C247CD6AB816 | |||
| 3992 | PORTQR~1.EXE | C:\PortQryV2\readme.txt | text | |
MD5:B265400F1284079326D9D4E9A5CBA4A4 | SHA256:150CBAA0FBD9154ECC43A3A0D74F35018CF5EA1721C22C3427C43D1EF997DDB4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
54
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4072 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
5080 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
4072 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
2652 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4820 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3516 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6004 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4656 | SearchApp.exe | 104.126.37.131:443 | — | Akamai International B.V. | DE | unknown |
1544 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
1544 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
1060 | svchost.exe | 184.30.17.189:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
3040 | OfficeClickToRun.exe | 13.89.179.13:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |