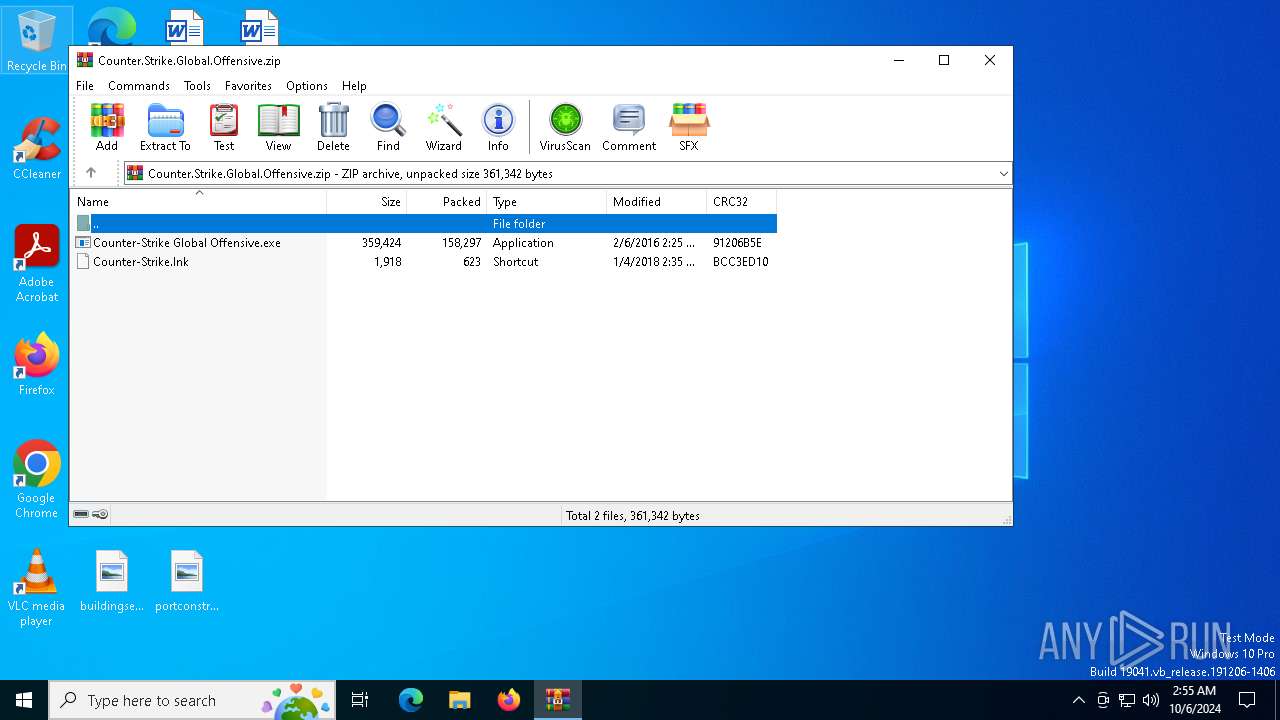
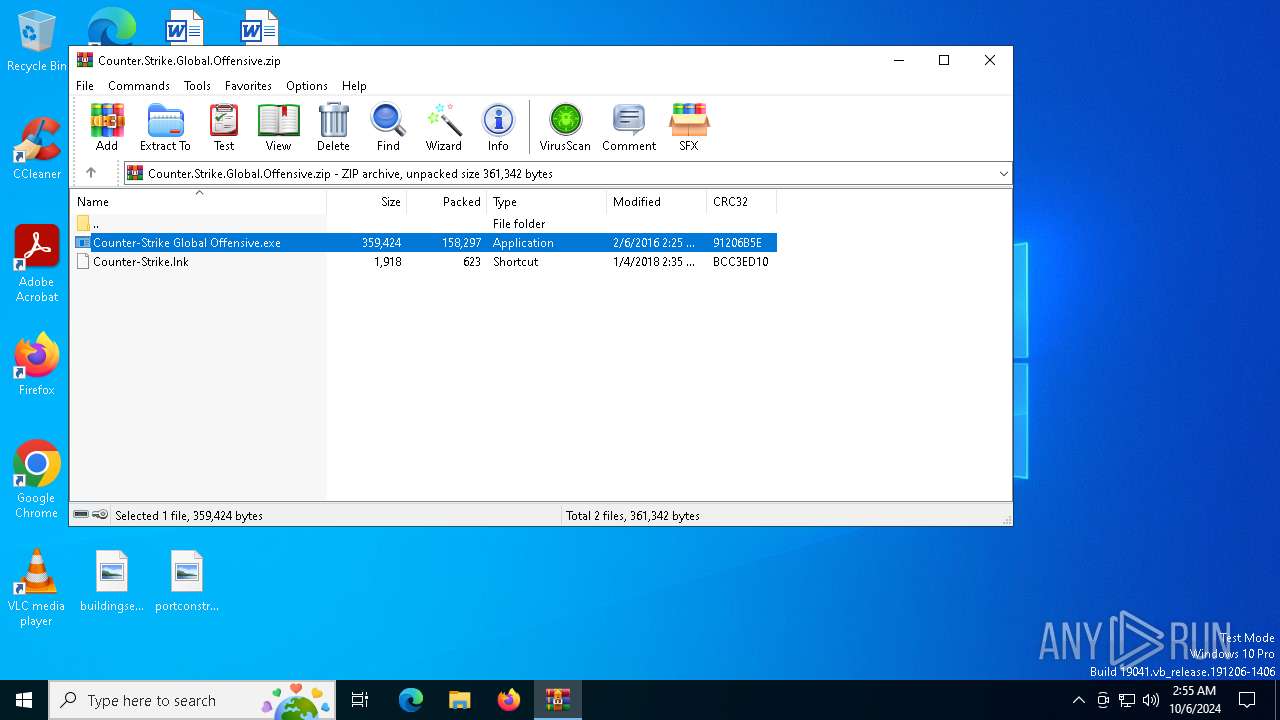
| File name: | Counter.Strike.Global.Offensive.zip |
| Full analysis: | https://app.any.run/tasks/79350abd-7208-4260-b914-e1b44b54af1d |
| Verdict: | Malicious activity |
| Analysis date: | October 06, 2024, 02:55:35 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C3917519F59CB260C89A86DAD34AE797 |
| SHA1: | E4B86141A6D53E346D2EA4D8451849A524451641 |
| SHA256: | 644DC229B3D4C86C9D9231B16516CAB1B9C6DCB463AD9D9957922A662815782B |
| SSDEEP: | 3072:lbwz3bNE0tS7nSya4P1E2DXlzo4wNBAnPhmktj1/9F5dPSh4/2tYkgBfX5u:5wPNFtSDtDe2DX/zPJ1vzPM4wgBfXk |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- Counter-Strike Global Offensive.exe (PID: 6668)
Checks Windows Trust Settings
- Counter-Strike Global Offensive.exe (PID: 6668)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4804)
The process uses the downloaded file
- WinRAR.exe (PID: 4804)
Manual execution by a user
- Counter-Strike Global Offensive.exe (PID: 6668)
Checks proxy server information
- Counter-Strike Global Offensive.exe (PID: 6668)
Reads the machine GUID from the registry
- Counter-Strike Global Offensive.exe (PID: 6668)
Checks supported languages
- Counter-Strike Global Offensive.exe (PID: 6668)
Creates files or folders in the user directory
- Counter-Strike Global Offensive.exe (PID: 6668)
Reads the computer name
- Counter-Strike Global Offensive.exe (PID: 6668)
Reads the software policy settings
- Counter-Strike Global Offensive.exe (PID: 6668)
Create files in a temporary directory
- Counter-Strike Global Offensive.exe (PID: 6668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:02:06 15:25:46 |
| ZipCRC: | 0x91206b5e |
| ZipCompressedSize: | 158297 |
| ZipUncompressedSize: | 359424 |
| ZipFileName: | Counter-Strike Global Offensive.exe |
Total processes
135
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
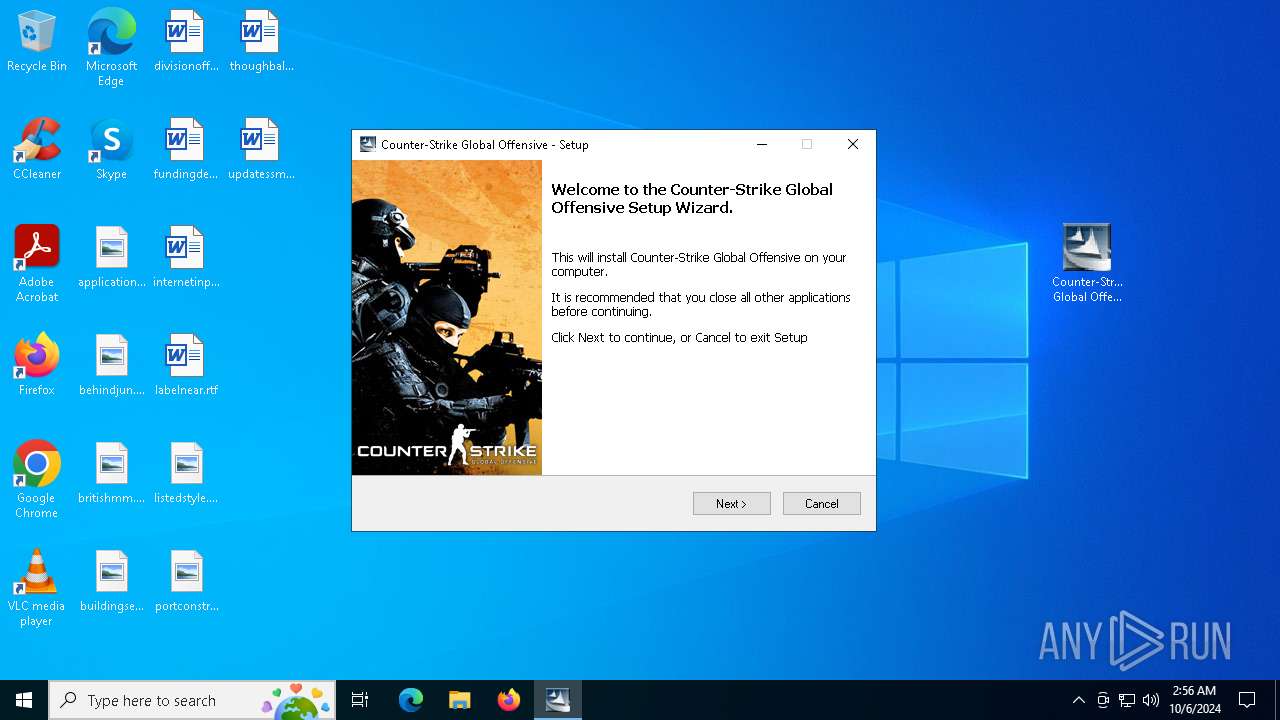
| 4804 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Counter.Strike.Global.Offensive.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6668 | "C:\Users\admin\Desktop\Counter-Strike Global Offensive.exe" | C:\Users\admin\Desktop\Counter-Strike Global Offensive.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
2 170
Read events
2 151
Write events
19
Delete events
0
Modification events
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Counter.Strike.Global.Offensive.zip | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4804) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
1
Suspicious files
6
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6668 | Counter-Strike Global Offensive.exe | C:\Users\admin\AppData\Local\Temp\~DF63C00786376BB822.TMP | binary | |
MD5:6221A608A813DC0105C13E70F286E7B8 | SHA256:08C39C0C486A913983DE28E95A27E05FFD939AA92510FC4A73DF3AA1EF429EEC | |||
| 6668 | Counter-Strike Global Offensive.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\Counter-Strike%20Global%20Offensive[1].htm | text | |
MD5:D90ABA5DBBB419D74BC323F00CB9F61C | SHA256:C6CE374BCF9C200A2A212777E4DCFB24F90FC3E9FC8495282D85B419AB023526 | |||
| 6668 | Counter-Strike Global Offensive.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:3DFCA46E00FFA4795C72A41375F159D3 | SHA256:DCBA1A505396539BAC40A7253C9F5DCCF06CBB79957E21D56305E1FC3AF5F40E | |||
| 6668 | Counter-Strike Global Offensive.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\installshield[1].jpg | image | |
MD5:077B94674FBD9CE83ABDA5C7B7392361 | SHA256:26A6DDC3F195E39EFC9F4E0B18D08A8EAD9D44A922C3C1C13724BB3126CFE3F2 | |||
| 6668 | Counter-Strike Global Offensive.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\installshield[1].htm | html | |
MD5:5D8D79C3CB9AF023240B1BE6F5057AAA | SHA256:E8B101A7C7F64AAD528CC734513CBEB02243C0AF37930DC0F3239749CFF184B6 | |||
| 6668 | Counter-Strike Global Offensive.exe | C:\Users\admin\AppData\Local\Temp\~DF20C23793A358921B.TMP | binary | |
MD5:8797831DC476E0500E4045D8E378240A | SHA256:079F2074402C4EC40B7B20C9B5DA9FA04BB773CEF09E7534049BA091D38ED0BA | |||
| 4804 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4804.16777\Counter-Strike Global Offensive.exe | executable | |
MD5:D0E96F86C1E2F9943E200AFA9C1A4FD7 | SHA256:688C99E92C2B800EC772655CDA9AD5DFB8EB92C4591DCA583D6C729BDA8BC7AA | |||
| 6668 | Counter-Strike Global Offensive.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\icon2[1].ico | image | |
MD5:53ACFA78281DFF62B57C4059675B2851 | SHA256:2EEB7233EE0576C8BA9B9FBAC202B29E84E50E1FEBD5D345A0E079B109020DA3 | |||
| 6668 | Counter-Strike Global Offensive.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\Counter-Strike%20Global%20Offensive[1].htm | html | |
MD5:5D8D79C3CB9AF023240B1BE6F5057AAA | SHA256:E8B101A7C7F64AAD528CC734513CBEB02243C0AF37930DC0F3239749CFF184B6 | |||
| 6668 | Counter-Strike Global Offensive.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\icon2[1].htm | html | |
MD5:5D8D79C3CB9AF023240B1BE6F5057AAA | SHA256:E8B101A7C7F64AAD528CC734513CBEB02243C0AF37930DC0F3239749CFF184B6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
51
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6668 | Counter-Strike Global Offensive.exe | GET | 301 | 91.223.82.132:80 | http://www.heydown.com/gen/1/Counter-Strike%20Global%20Offensive.jpg | unknown | — | — | malicious |
6668 | Counter-Strike Global Offensive.exe | GET | 301 | 91.223.82.132:80 | http://www.heydown.com/gen/1/installshield.jpg | unknown | — | — | malicious |
6668 | Counter-Strike Global Offensive.exe | GET | 301 | 91.223.82.132:80 | http://www.heydown.com/gen/1/key.bmp | unknown | — | — | malicious |
6668 | Counter-Strike Global Offensive.exe | GET | 301 | 91.223.82.132:80 | http://www.heydown.com/gen/1/folder.jpg | unknown | — | — | malicious |
840 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4596 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4596 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2968 | svchost.exe | GET | 304 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
3160 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6668 | Counter-Strike Global Offensive.exe | GET | 301 | 91.223.82.132:80 | http://www.heydown.com/gen/1/Counter-Strike%20Global%20Offensive.html | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5388 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4324 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3160 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3160 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.heydown.com |
| malicious |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |