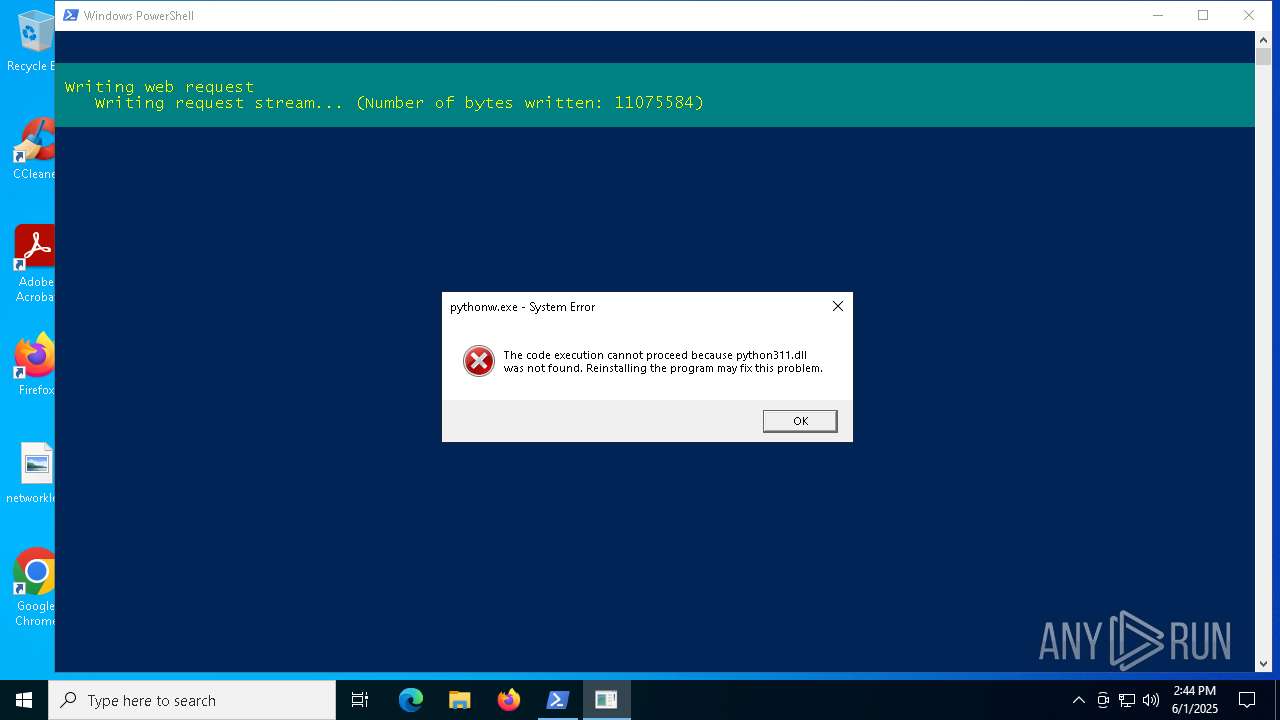
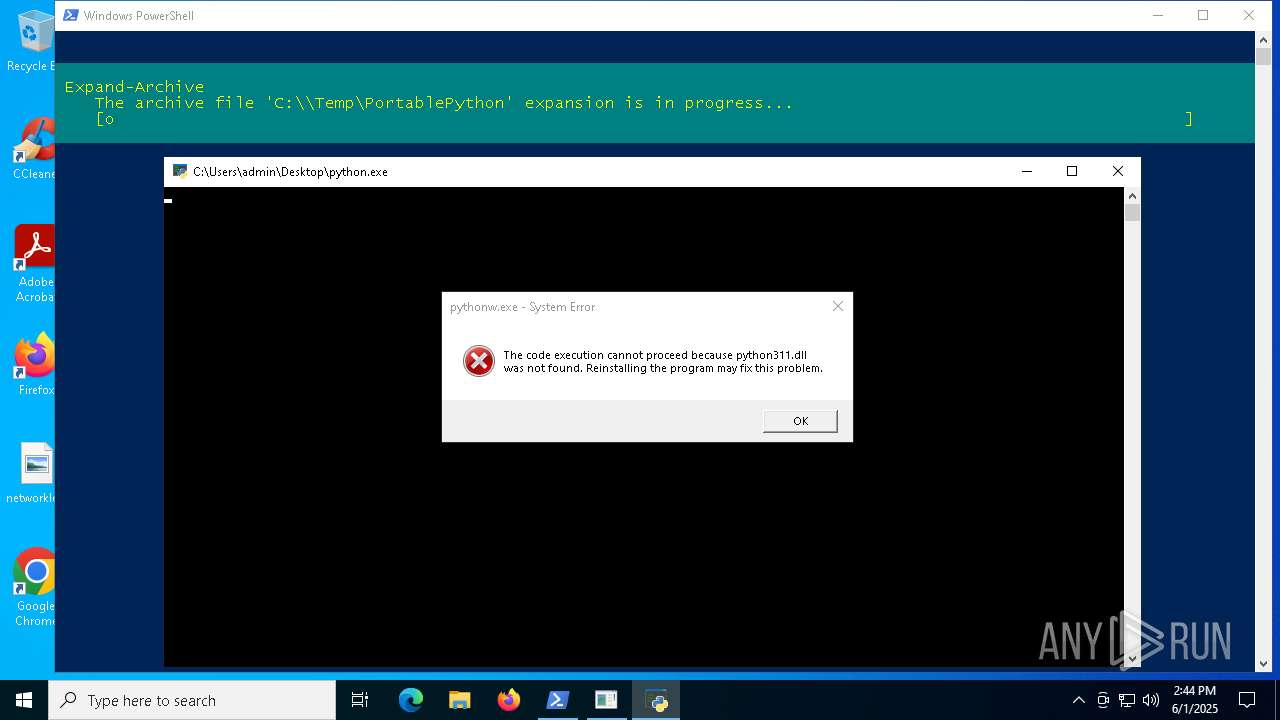
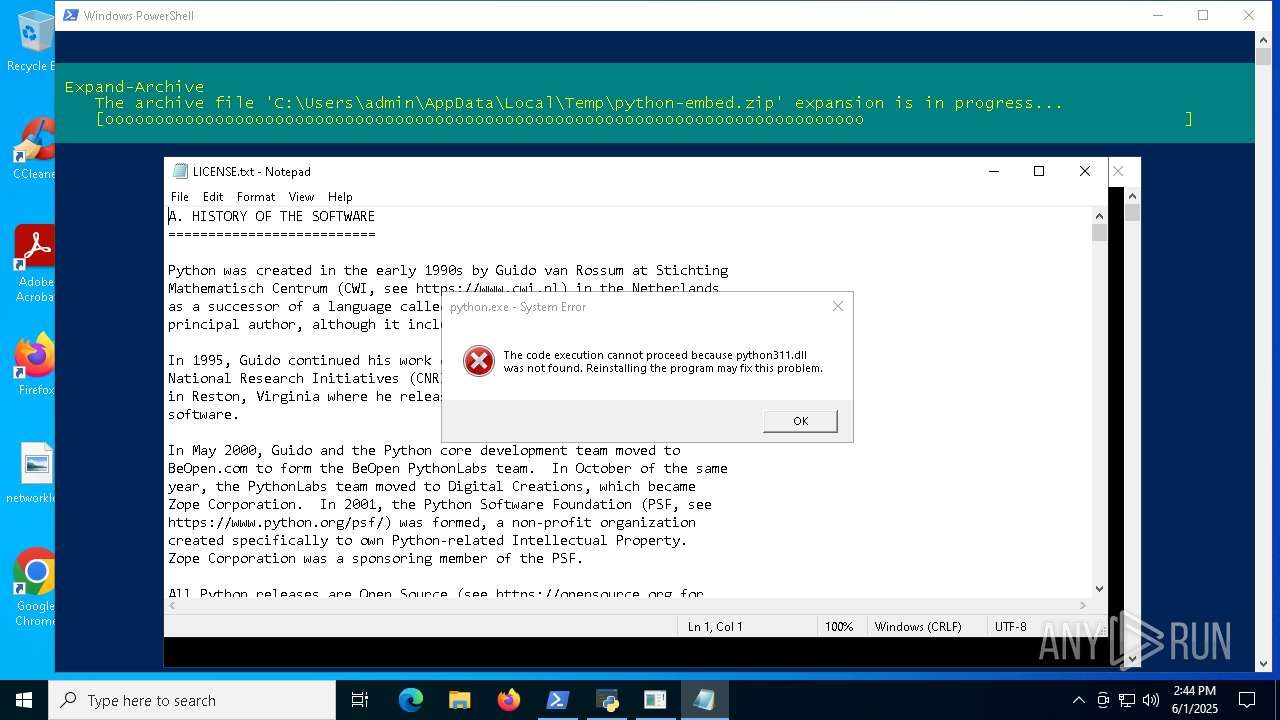
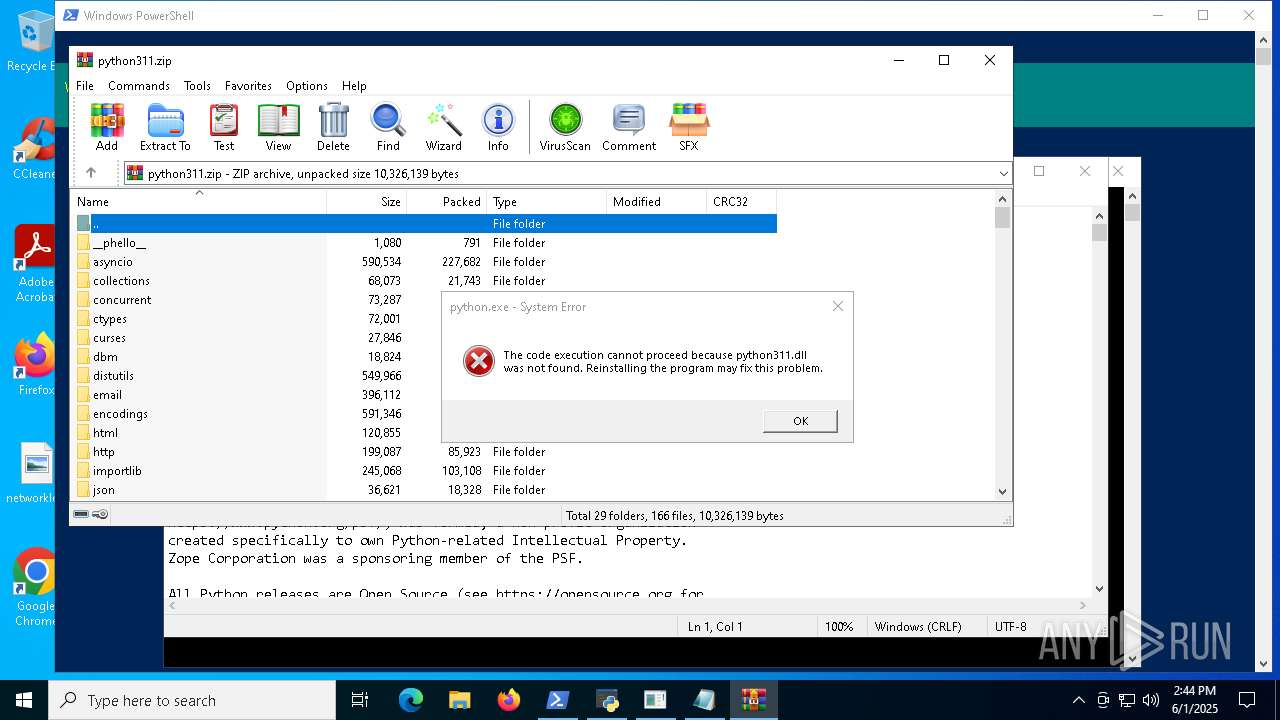
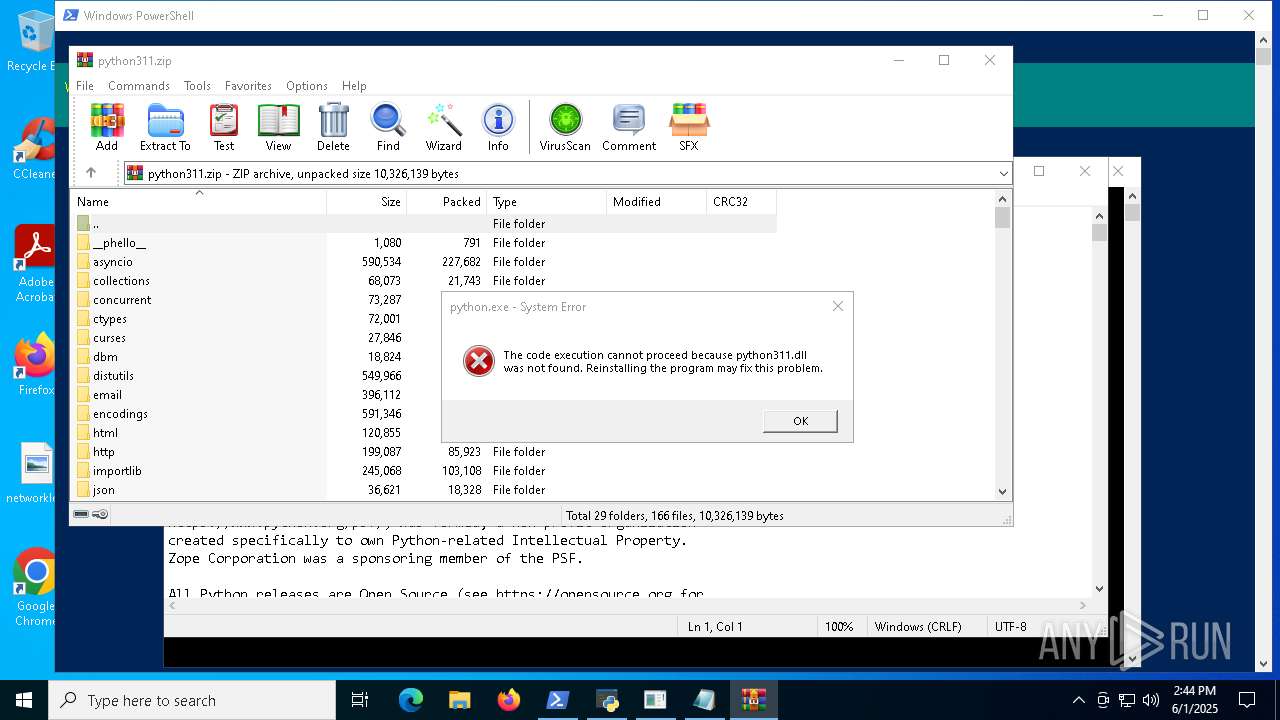
| File name: | 01062025_1437_1.ps1 |
| Full analysis: | https://app.any.run/tasks/936395ee-3e33-4e4d-8c99-e3dcc8233e5e |
| Verdict: | Malicious activity |
| Analysis date: | June 01, 2025, 14:43:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text |
| MD5: | 9303AF8A1310D4A66684A660ED286551 |
| SHA1: | 9ABC45F8D6A4C5CFC8F403AE529713DEA40FDF3A |
| SHA256: | 644D9AADA9EBE7D434753097BFA8875C4C41B545E8DD63E69EF54A6FEDE66624 |
| SSDEEP: | 48:Jh4DVNOdnBcii9AEG/PB5adXGS1qipIfnERyu5tG2RT2Ot+Em5Qv/9W/4OtXLr59:nNG90Udb1BgERyuK22m+15QX9g4OtXJ9 |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 6476)
SUSPICIOUS
Checks for external IP
- svchost.exe (PID: 2196)
- powershell.exe (PID: 6476)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6476)
The process drops C-runtime libraries
- powershell.exe (PID: 6476)
Process drops legitimate windows executable
- powershell.exe (PID: 6476)
Loads Python modules
- python.exe (PID: 7680)
Starts CMD.EXE for commands execution
- python.exe (PID: 7680)
Process drops python dynamic module
- powershell.exe (PID: 6476)
Executable content was dropped or overwritten
- powershell.exe (PID: 6476)
- python.exe (PID: 7680)
INFO
Disables trace logs
- powershell.exe (PID: 6476)
Checks proxy server information
- powershell.exe (PID: 6476)
- rundll32.exe (PID: 8040)
- python.exe (PID: 7680)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6476)
Manual execution by a user
- pythonw.exe (PID: 1284)
- python.exe (PID: 4756)
- notepad.exe (PID: 1676)
- WinRAR.exe (PID: 7576)
- rundll32.exe (PID: 8040)
- cmd.exe (PID: 8132)
- notepad.exe (PID: 7652)
- OpenWith.exe (PID: 3124)
- notepad.exe (PID: 7196)
- notepad.exe (PID: 3868)
- OpenWith.exe (PID: 6828)
- notepad.exe (PID: 7776)
- OpenWith.exe (PID: 7936)
- notepad.exe (PID: 4040)
Python executable
- pythonw.exe (PID: 1284)
- python.exe (PID: 4756)
- python.exe (PID: 7680)
The sample compiled with english language support
- powershell.exe (PID: 6476)
- python.exe (PID: 7680)
Checks operating system version
- python.exe (PID: 7680)
Reads the software policy settings
- rundll32.exe (PID: 8040)
- python.exe (PID: 7680)
Checks supported languages
- python.exe (PID: 7680)
Creates files or folders in the user directory
- rundll32.exe (PID: 8040)
- python.exe (PID: 7680)
Create files in a temporary directory
- python.exe (PID: 7680)
Drops encrypted JS script (Microsoft Script Encoder)
- python.exe (PID: 7680)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 6476)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1676)
- rundll32.exe (PID: 8040)
- notepad.exe (PID: 4040)
Reads the machine GUID from the registry
- python.exe (PID: 7680)
Reads the computer name
- python.exe (PID: 7680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
144
Monitored processes
23
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1284 | "C:\Users\admin\Desktop\pythonw.exe" | C:\Users\admin\Desktop\pythonw.exe | — | explorer.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 3221225781 Version: 3.11.8 Modules
| |||||||||||||||
| 1568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1676 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\LICENSE.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3124 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\fetch_macholib | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3868 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\entry_points.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\README.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4224 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4756 | "C:\Users\admin\Desktop\python.exe" | C:\Users\admin\Desktop\python.exe | — | explorer.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 3221225781 Version: 3.11.8 Modules
| |||||||||||||||
| 6156 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 722
Read events
20 714
Write events
8
Delete events
0
Modification events
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\python311.zip | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7576) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
44
Suspicious files
1 321
Text files
943
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6476 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF12044e.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 6476 | powershell.exe | C:\Users\admin\AppData\Local\Temp\python-embed.zip | compressed | |
MD5:9199879FBAD4884ED93DDF77E8764920 | SHA256:6347068CA56BF4DD6319F7EF5695F5A03F1ADE3E9AA2D6A095AB27FAA77A1290 | |||
| 6476 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_iyckfpdg.aub.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6476 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bg42revr.3ai.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6476 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\H2Y56ZB24AIHVX94DQOL.temp | binary | |
MD5:42C7D8EA103B136632E654DE841DB068 | SHA256:E423B0E91A312B8C0C885F818310C4409E2BD0F7FEF9ADE82AFC310E60ACD653 | |||
| 6476 | powershell.exe | C:\Temp\PortablePython\pythonw.exe | executable | |
MD5:837DD66E580DDC9B5DCC191156A202C2 | SHA256:E65ECC6B135F8C2269A2163F5C906376F2FEA3B61571D312D779F36F772CEAC1 | |||
| 6476 | powershell.exe | C:\Temp\PortablePython\select.pyd | executable | |
MD5:E07AE2F7F28305B81ADFD256716AE8C6 | SHA256:FB06AC13F8B444C3F7AE5D2AF15710A4E60A126C3C61A1F1E1683F05F685626C | |||
| 6476 | powershell.exe | C:\Temp\PortablePython\unicodedata.pyd | executable | |
MD5:5CC36A5DE45A2C16035ADE016B4348EB | SHA256:F28AC3E3AD02F9E1D8B22DF15FA30B2190B080261A9ADC6855248548CD870D20 | |||
| 6476 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:42C7D8EA103B136632E654DE841DB068 | SHA256:E423B0E91A312B8C0C885F818310C4409E2BD0F7FEF9ADE82AFC310E60ACD653 | |||
| 6476 | powershell.exe | C:\Temp\PortablePython\pyexpat.pyd | executable | |
MD5:D7ECC2746314FEC5CA46B64C964EA93E | SHA256:58B95F03A2D7EC49F5260E3E874D2B9FB76E95ECC80537E27ABEF0C74D03CB00 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
26
DNS requests
14
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7852 | RUXIMICS.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7852 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6476 | powershell.exe | GET | 200 | 34.160.111.145:80 | http://ifconfig.me/ip | unknown | — | — | shared |
— | — | GET | 200 | 151.101.0.223:443 | https://www.python.org/ftp/python/3.11.8/python-3.11.8-embed-amd64.zip | unknown | compressed | 10.6 Mb | whitelisted |
— | — | GET | 200 | 151.101.128.175:443 | https://bootstrap.pypa.io/get-pip.py | unknown | text | 2.17 Mb | whitelisted |
8040 | rundll32.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAcfFBuLMA0l8xTrIwzQ0d0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 151.101.192.223:443 | https://files.pythonhosted.org/packages/29/a2/d40fb2460e883eca5199c62cfc2463fd261f760556ae6290f88488c362c0/pip-25.1.1-py3-none-any.whl.metadata | unknown | text | 3.56 Kb | whitelisted |
— | — | GET | 200 | 151.101.64.223:443 | https://pypi.org/simple/setuptools/ | unknown | binary | 747 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7852 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
7852 | RUXIMICS.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7852 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6476 | powershell.exe | 34.160.111.145:80 | ifconfig.me | GOOGLE | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ifconfig.me |
| shared |
www.python.org |
| whitelisted |
bootstrap.pypa.io |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
pypi.org |
| whitelisted |
files.pythonhosted.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Lookup Domain (ifconfig .me) |
6476 | powershell.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain (ifconfig .me) |
6476 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
6476 | powershell.exe | Device Retrieving External IP Address Detected | SUSPICIOUS [ANY.RUN] An IP address was received from the server as a result of an HTTP request |
2196 | svchost.exe | Misc activity | ET FILE_SHARING File Hosting Service Domain Domain in DNS Lookup (files .pythonhosted .org) |
7680 | python.exe | Misc activity | ET INFO Observed File Hosting Service Domain (files .pythonhosted .org in TLS SNI) |