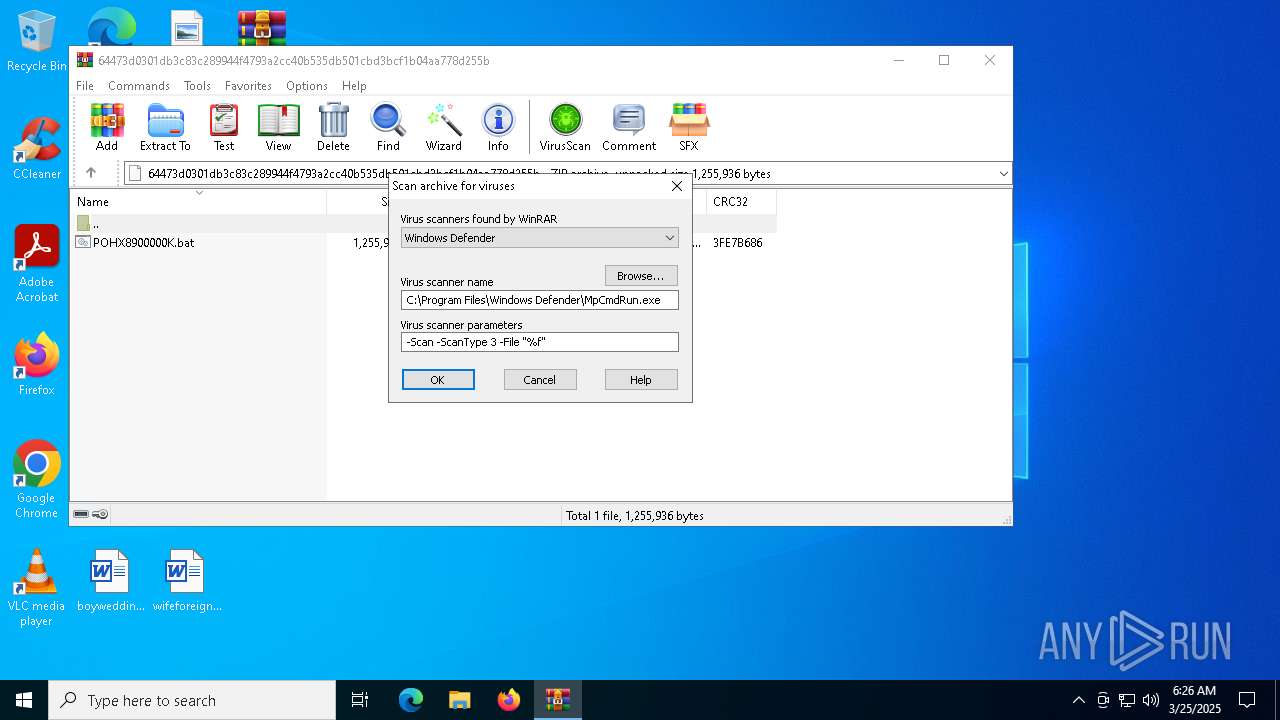
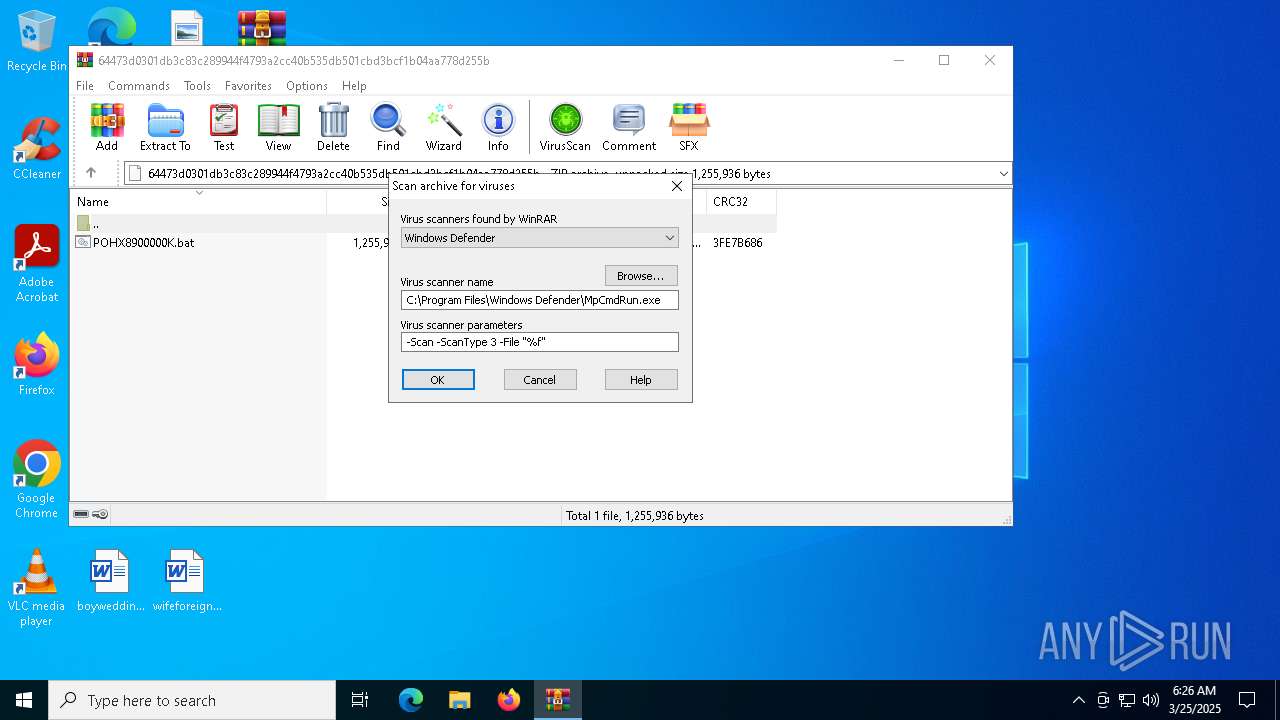
| File name: | 64473d0301db3c83c289944f4793a2cc40b535db501cbd3bcf1b04aa778d255b |
| Full analysis: | https://app.any.run/tasks/b00b60ea-9d6c-4154-836d-ff2c7c10e200 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 06:25:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
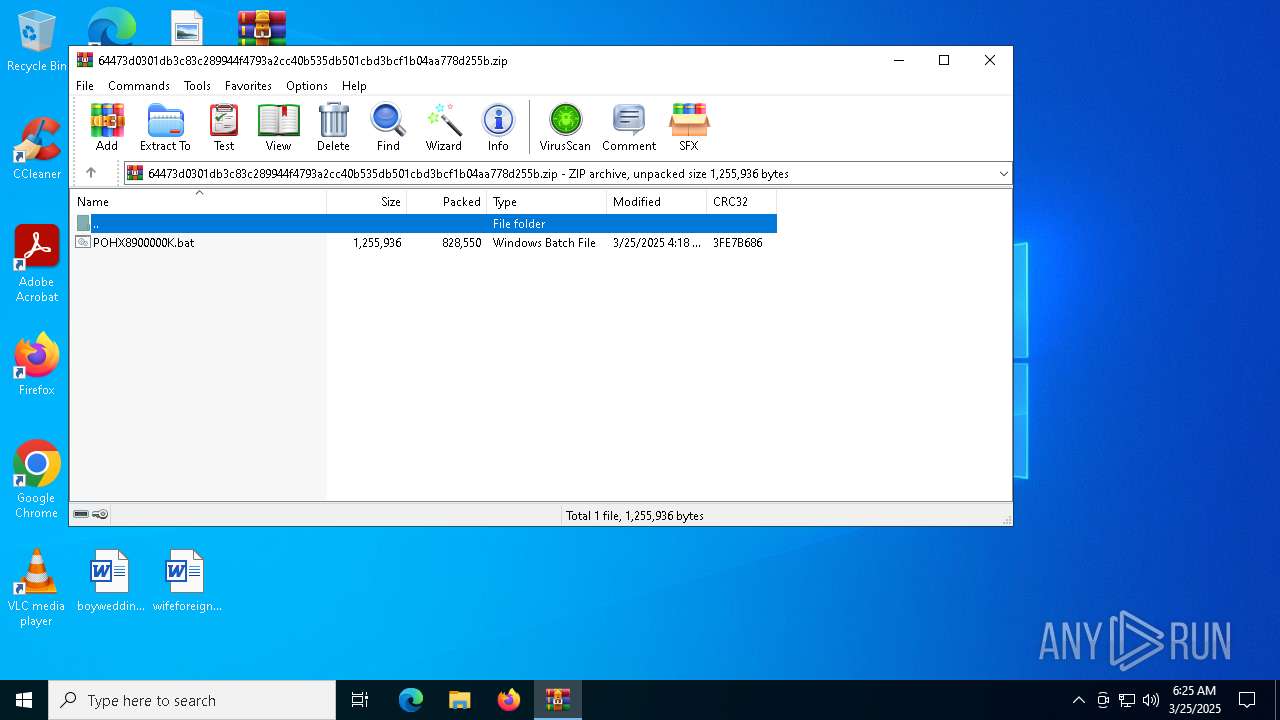
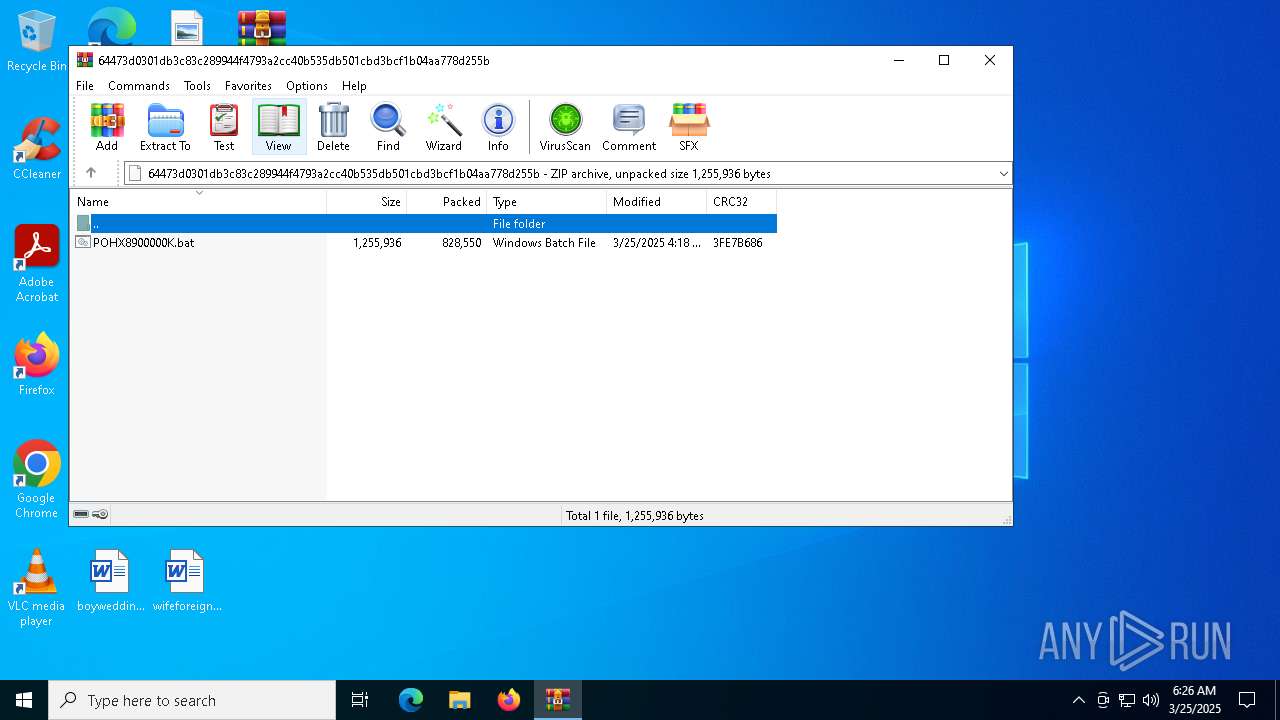
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | FAD8BD8DF6658E592ACE4480D9584E3E |
| SHA1: | 671D3C13D6BCEACCD4625A68D03C3B09E405B22C |
| SHA256: | 64473D0301DB3C83C289944F4793A2CC40B535DB501CBD3BCF1B04AA778D255B |
| SSDEEP: | 24576:laTbI/POFJJFy1y0ejzJq1fPyImtRnpGyphx3cdFSNaiUDIG/F1/L1YXZA6MJG2l:laTbI/PO/JFys0ejzJ6fPyftRnpGyphW |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6108)
Create files in the Startup directory
- drawlingly.exe (PID: 4120)
SUSPICIOUS
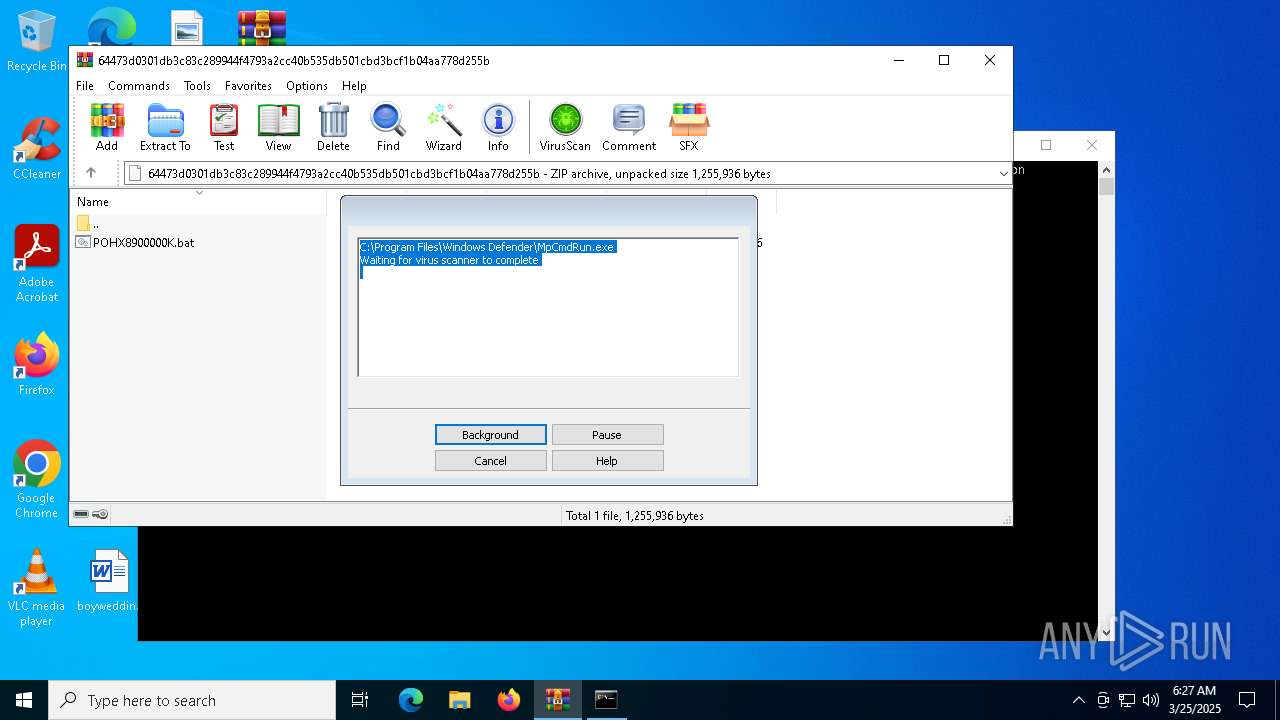
Executable content was dropped or overwritten
- POHX8900000K.bat (PID: 5116)
Starts itself from another location
- POHX8900000K.bat (PID: 5116)
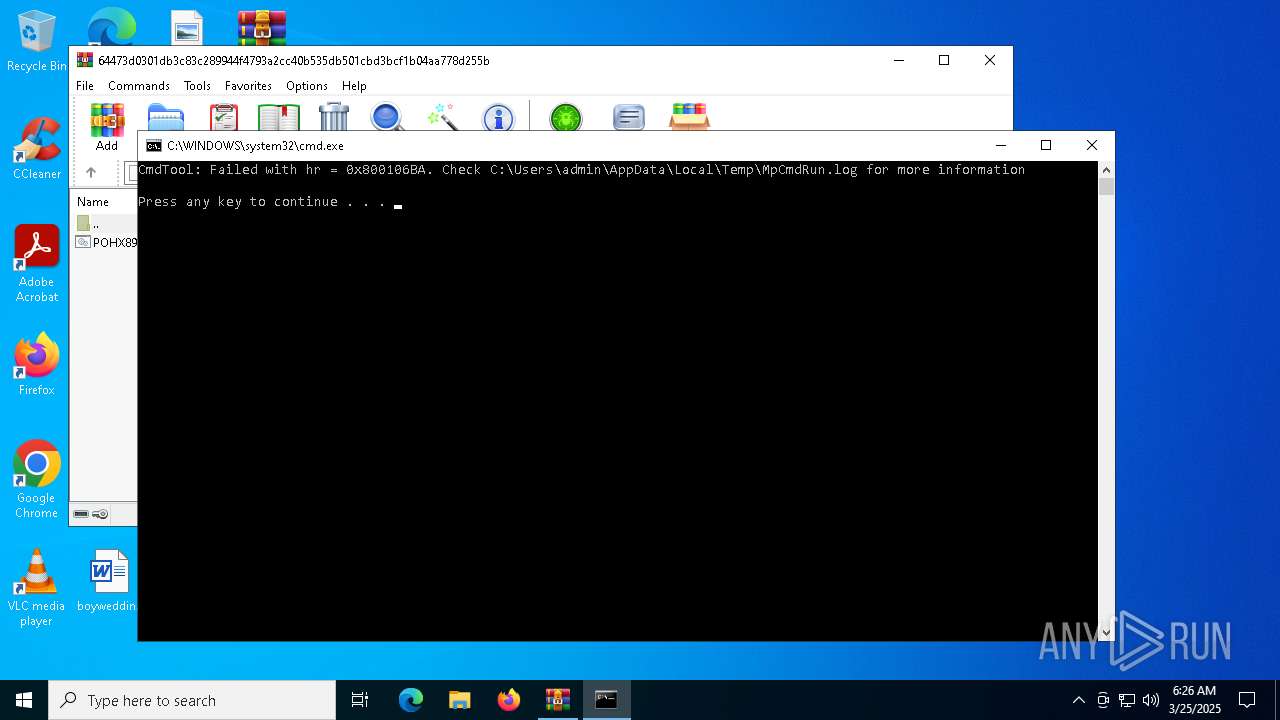
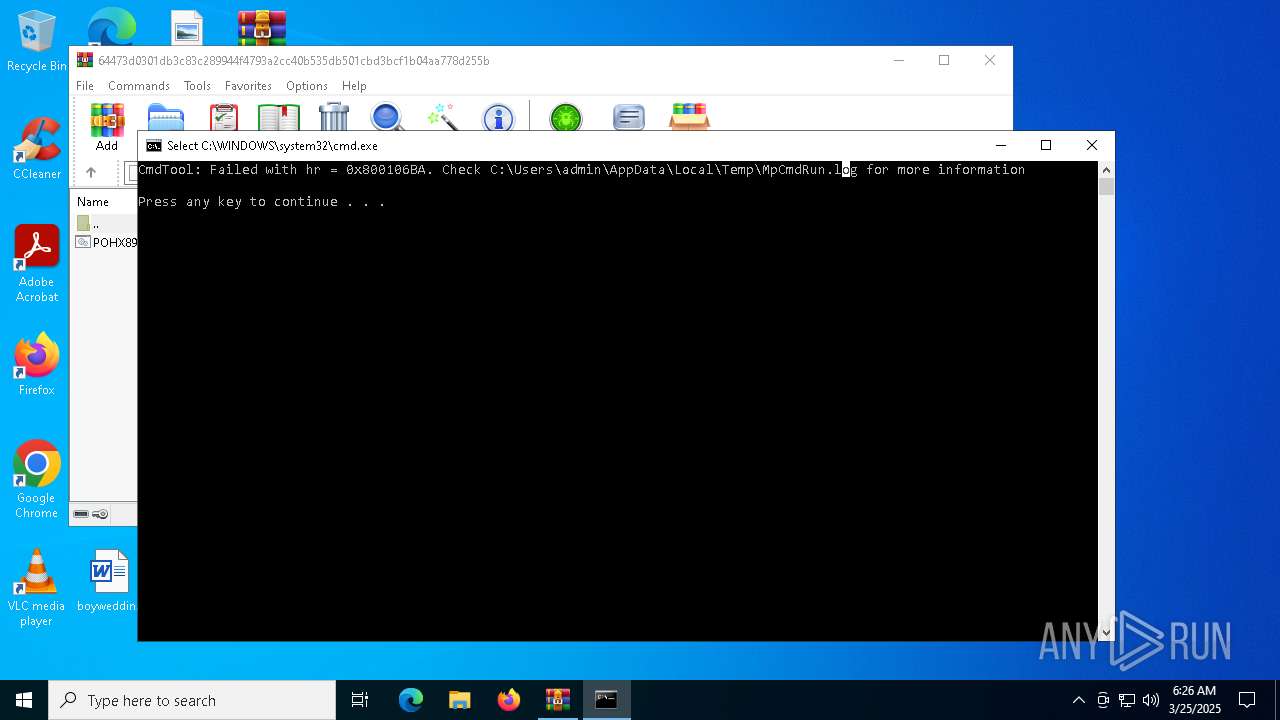
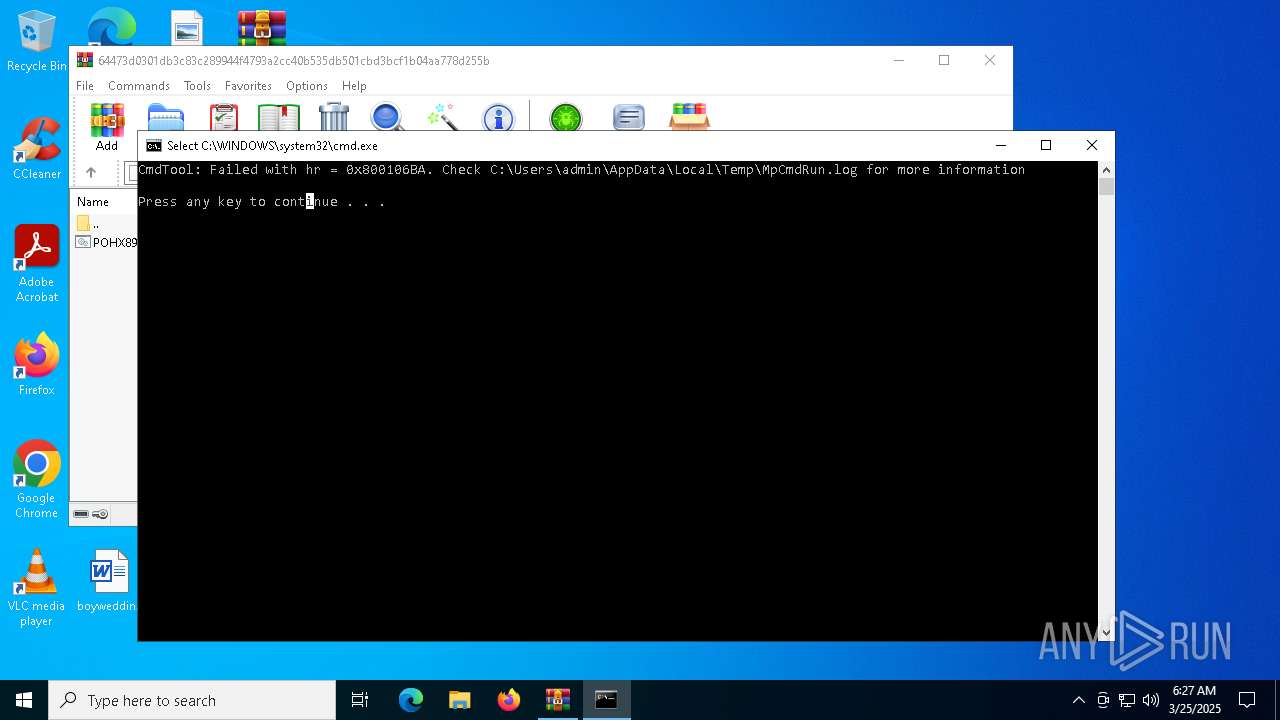
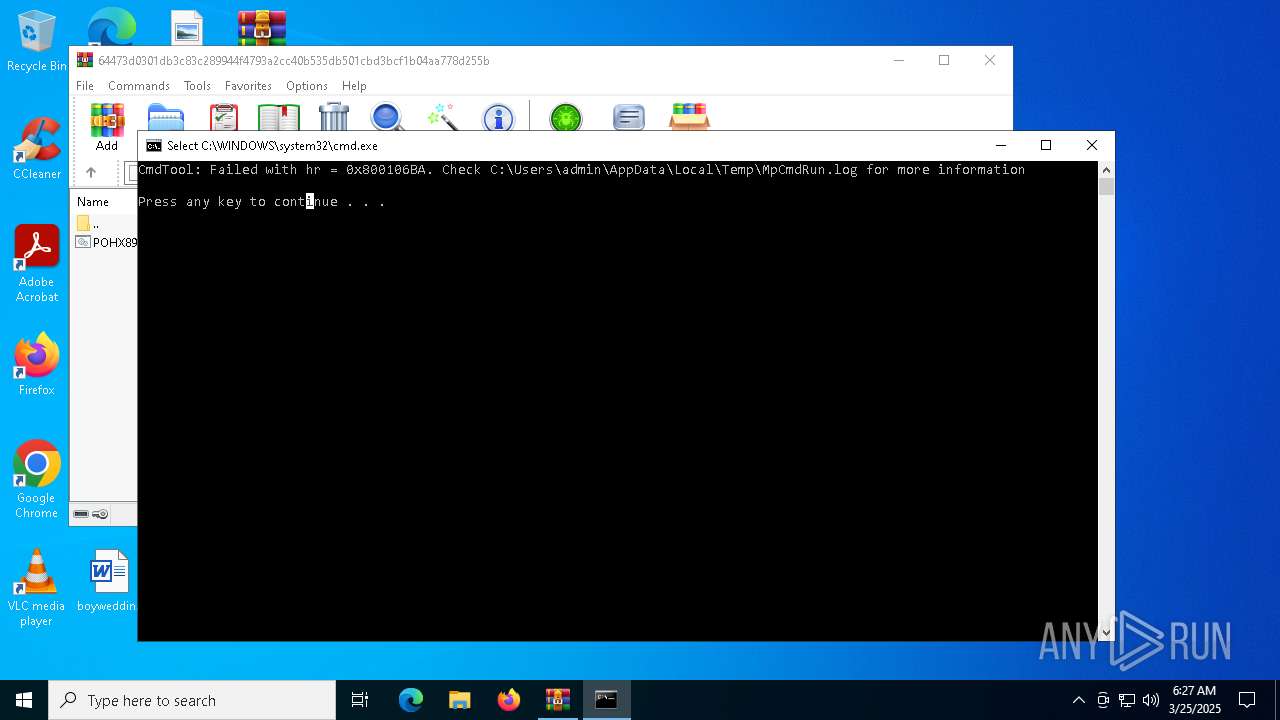
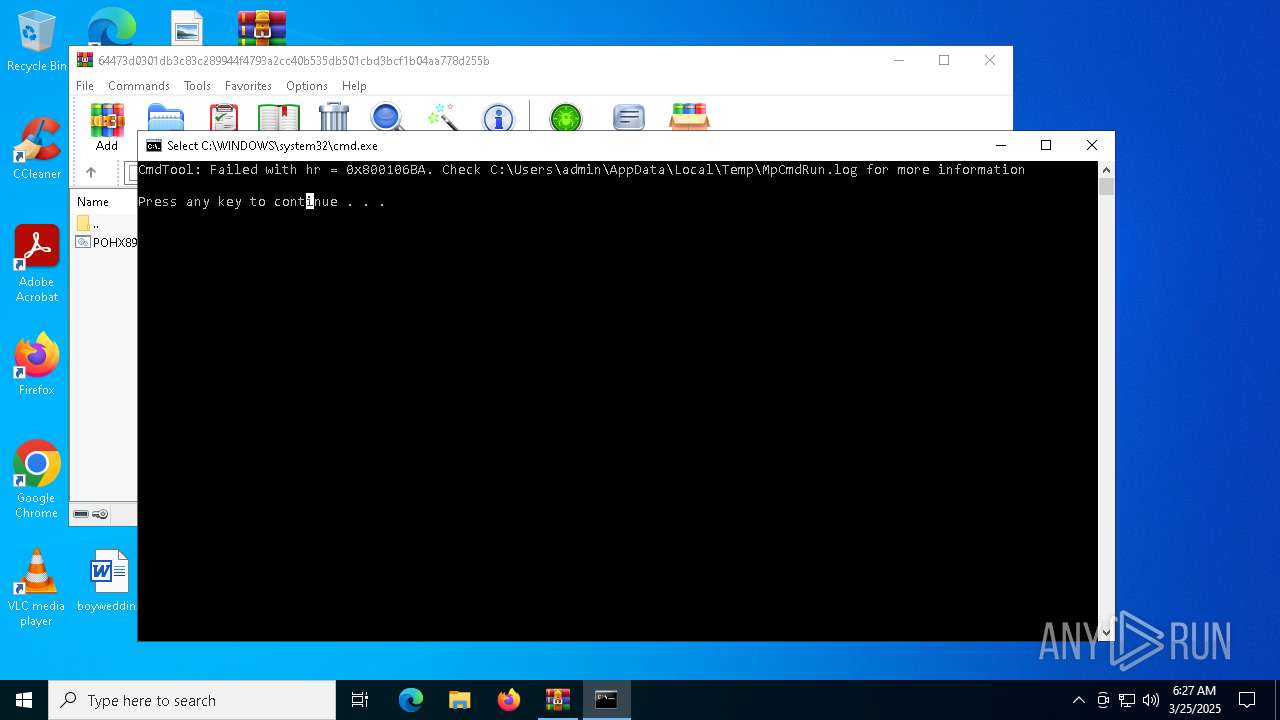
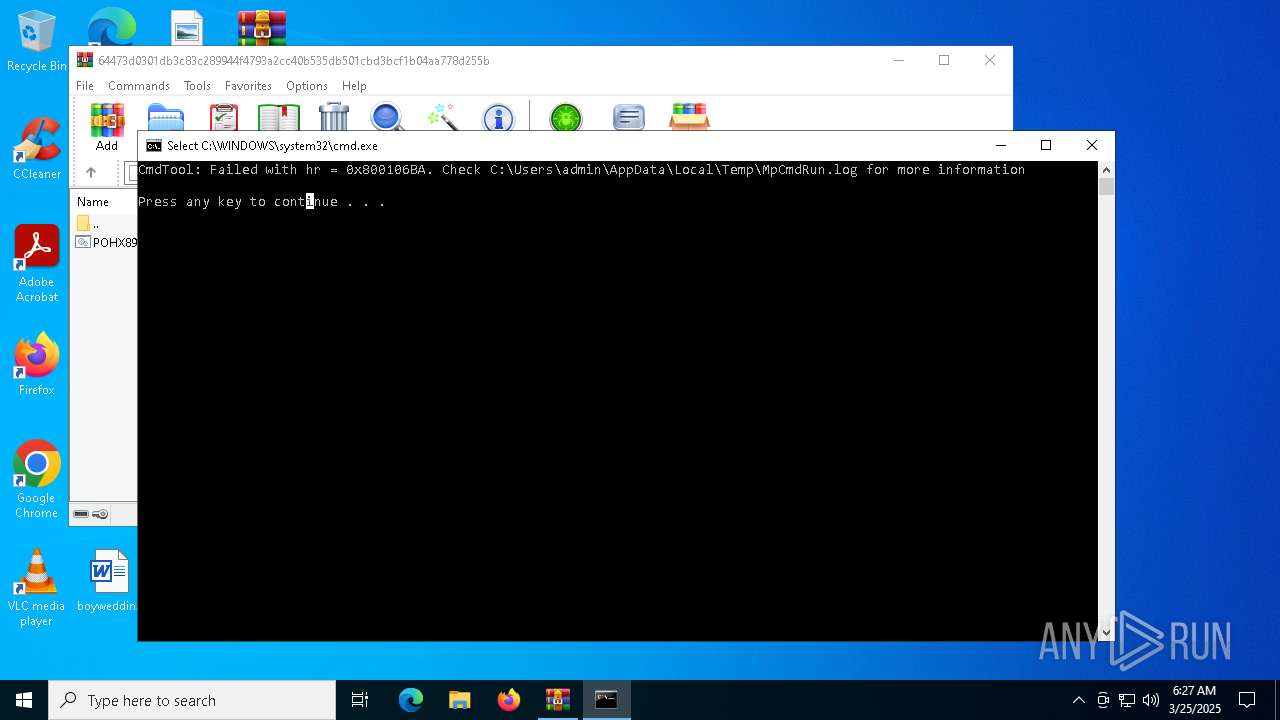
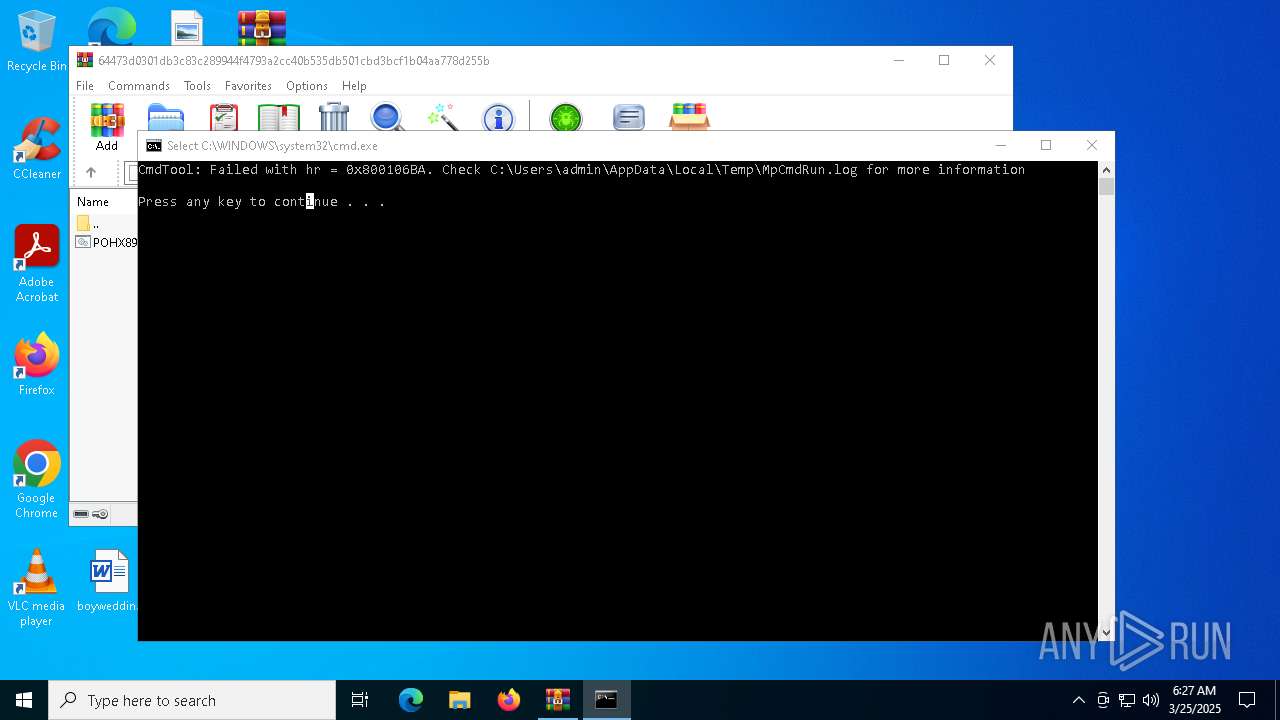
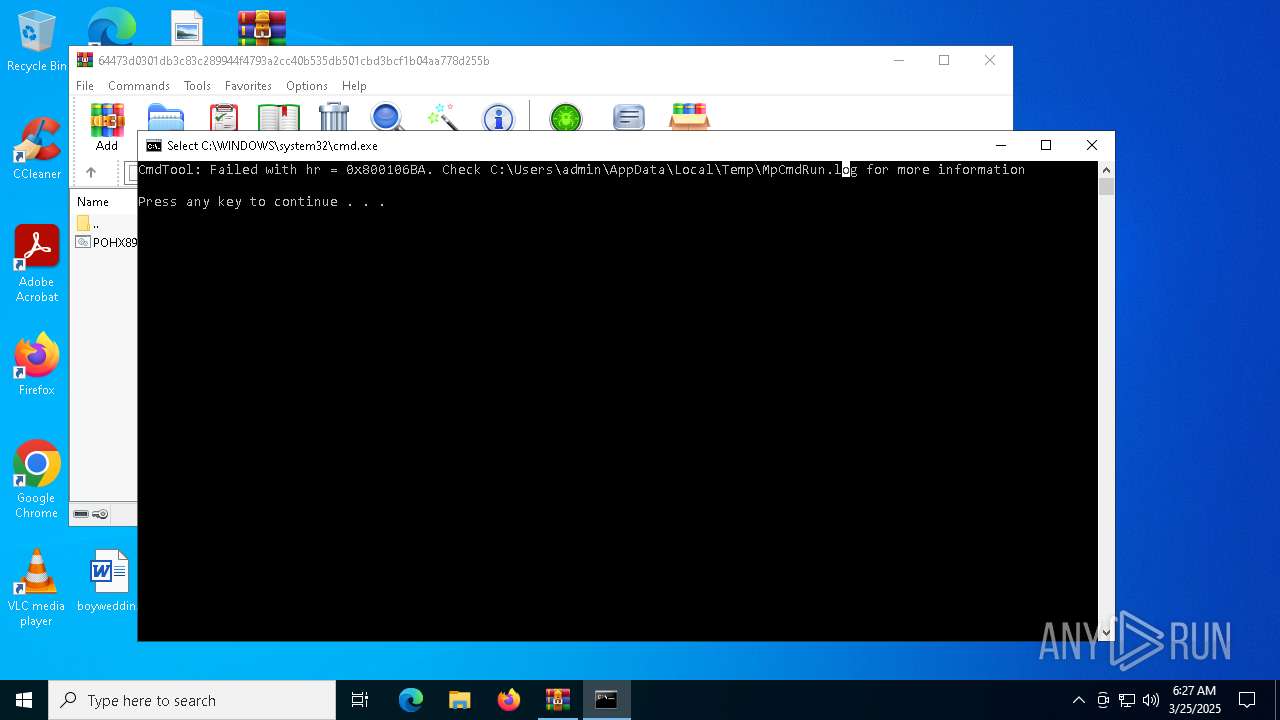
Executes application which crashes
- drawlingly.exe (PID: 4120)
- drawlingly.exe (PID: 3304)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6032)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6108)
Suspicious files were dropped or overwritten
- WinRAR.exe (PID: 6108)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6108)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6108)
INFO
Creates files or folders in the user directory
- POHX8900000K.bat (PID: 5116)
- drawlingly.exe (PID: 4120)
- WerFault.exe (PID: 6068)
- WerFault.exe (PID: 1164)
Create files in a temporary directory
- POHX8900000K.bat (PID: 5116)
- drawlingly.exe (PID: 4120)
- drawlingly.exe (PID: 3304)
- MpCmdRun.exe (PID: 5260)
Checks supported languages
- POHX8900000K.bat (PID: 5116)
- drawlingly.exe (PID: 4120)
- MpCmdRun.exe (PID: 5260)
- drawlingly.exe (PID: 3304)
Reads mouse settings
- POHX8900000K.bat (PID: 5116)
- drawlingly.exe (PID: 4120)
- drawlingly.exe (PID: 3304)
Reads the machine GUID from the registry
- POHX8900000K.bat (PID: 5116)
Manual execution by a user
- POHX8900000K.bat (PID: 5116)
- wscript.exe (PID: 6032)
The sample compiled with english language support
- POHX8900000K.bat (PID: 5116)
- WinRAR.exe (PID: 6108)
Autorun file from Startup directory
- drawlingly.exe (PID: 4120)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6108)
Reads the computer name
- MpCmdRun.exe (PID: 5260)
Checks proxy server information
- slui.exe (PID: 5548)
Reads the software policy settings
- slui.exe (PID: 5548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:25 04:18:22 |
| ZipCRC: | 0x3fe7b686 |
| ZipCompressedSize: | 828550 |
| ZipUncompressedSize: | 1255936 |
| ZipFileName: | POHX8900000K.bat |
Total processes
141
Monitored processes
13
Malicious processes
0
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 976 | "C:\Users\admin\AppData\Local\unprickled\drawlingly.exe" | C:\Windows\SysWOW64\svchost.exe | — | drawlingly.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1164 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 3304 -s 732 | C:\Windows\SysWOW64\WerFault.exe | — | drawlingly.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2108 | "C:\Users\admin\Desktop\POHX8900000K.bat" | C:\Windows\SysWOW64\svchost.exe | — | drawlingly.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 3304 | "C:\Users\admin\AppData\Local\unprickled\drawlingly.exe" | C:\Users\admin\AppData\Local\unprickled\drawlingly.exe | wscript.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 4120 | "C:\Users\admin\Desktop\POHX8900000K.bat" | C:\Users\admin\AppData\Local\unprickled\drawlingly.exe | POHX8900000K.bat | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 5116 | "C:\Users\admin\Desktop\POHX8900000K.bat" | C:\Users\admin\Desktop\POHX8900000K.bat | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5260 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR6108.30336" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5548 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6032 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\drawlingly.vbs" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
9 084
Read events
9 058
Write events
26
Delete events
0
Modification events
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\64473d0301db3c83c289944f4793a2cc40b535db501cbd3bcf1b04aa778d255b.zip | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (6108) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
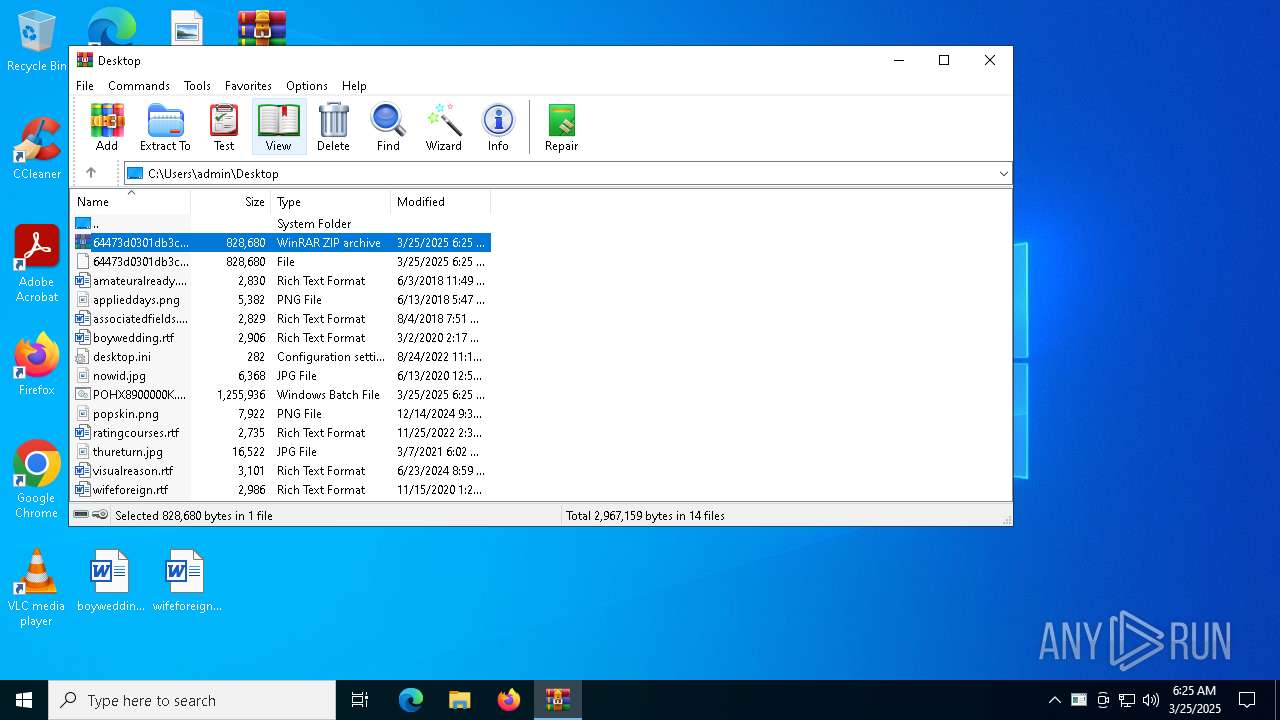
Executable files
2
Suspicious files
12
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6068 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_drawlingly.exe_1e7763cfd919fb99b55df133e8be743b135c8e_45cef90b_eedb9c46-0dca-4d1d-915e-63af32400e33\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1164 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_drawlingly.exe_1e7763cfd919fb99b55df133e8be743b135c8e_45cef90b_c3f9ed78-f064-48a7-a70f-51e9d08c0e73\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4120 | drawlingly.exe | C:\Users\admin\AppData\Local\Temp\autD6F9.tmp | binary | |
MD5:96CC33A835E0709F416648AEF57B13D5 | SHA256:E7998F589ECBC073B7CC1548714295AE863250F8E29ECF768280D4B5C6453E55 | |||
| 5116 | POHX8900000K.bat | C:\Users\admin\AppData\Local\Temp\autCD45.tmp | binary | |
MD5:96CC33A835E0709F416648AEF57B13D5 | SHA256:E7998F589ECBC073B7CC1548714295AE863250F8E29ECF768280D4B5C6453E55 | |||
| 5116 | POHX8900000K.bat | C:\Users\admin\AppData\Local\unprickled\drawlingly.exe | executable | |
MD5:7EB347055493F1CD8CFB703E0D8E28F7 | SHA256:89EB3DD9EFA5DF020443E934223D463B7A23F065627657D75B58846EDD928368 | |||
| 6068 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERDD06.tmp.xml | xml | |
MD5:77F1CB537E8C5EDAEE7AD297D5026543 | SHA256:05B4DFEE3AFF377CBC4EF511F83F08F20BD07E81BF335A6FA27E2BE1D1980622 | |||
| 1164 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERE13A.tmp.dmp | binary | |
MD5:06B24C657AE41E5CBDD43EF7C3675093 | SHA256:0A63B9078449CD9A93C5A9DA167FFAA0CB0C722F69AF0FCB4778A986138B00F3 | |||
| 6068 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERDCD6.tmp.WERInternalMetadata.xml | binary | |
MD5:56948FA4B2A686AFC4BB70EB9F38887D | SHA256:BE0918E5846D82E56FA347977ED95779CDBDE36BEF15DE545189A2E51D7F600B | |||
| 3304 | drawlingly.exe | C:\Users\admin\AppData\Local\Temp\autDDEE.tmp | binary | |
MD5:96CC33A835E0709F416648AEF57B13D5 | SHA256:E7998F589ECBC073B7CC1548714295AE863250F8E29ECF768280D4B5C6453E55 | |||
| 6108 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6108.30336\Rar$Scan77634.bat | text | |
MD5:36C5542627CEFBFD1DEF800260E0E7A2 | SHA256:8DDA695AEE06E1506598607B22960D5F6F6EFC58CD08213F42631592DA7FD9BE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
20
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6148 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2104 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 2.20.245.137:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5936 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5548 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |