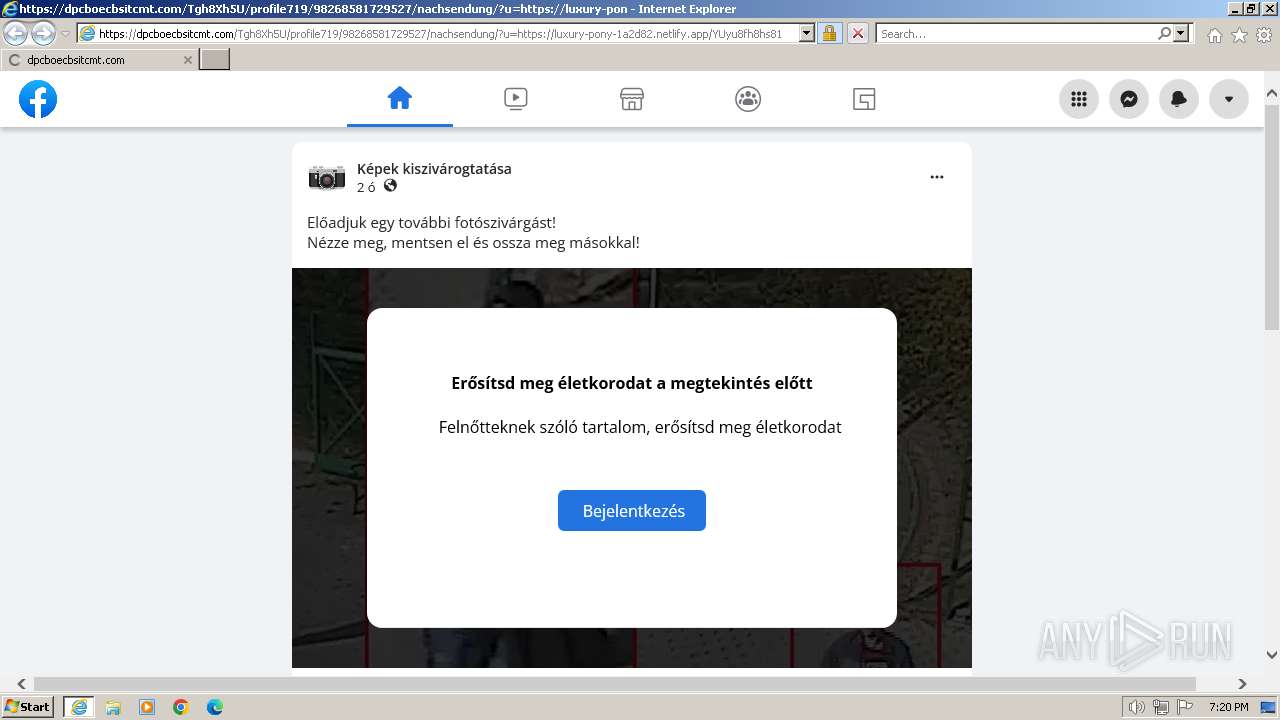
| URL: | dpcboecbsitcmt.com/Tgh8Xh5U/profile719/98268581729527??741158=828882? |
| Full analysis: | https://app.any.run/tasks/687f0b06-6802-4525-be35-77829de8009d |
| Verdict: | Malicious activity |
| Analysis date: | January 01, 2024, 19:19:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 42F61D5B867CF23447CAD6CEA6A2572E |
| SHA1: | D5BFD6774C0B6033EF43D5DF89ACA16410129220 |
| SHA256: | 6446480462494C25F3FFC708FA84CBC0EA20AF546684C769E4B614989A7CDA3A |
| SSDEEP: | 3:sbQLgIDU44cKsqjhCbdYdXfw:sbQcIDUf7sqjhCbdwXY |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Internet Explorer\iexplore.exe" "dpcboecbsitcmt.com/Tgh8Xh5U/profile719/98268581729527??741158=828882?" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 324 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:116 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
12 408
Read events
12 341
Write events
65
Delete events
2
Modification events
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (116) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
39
Text files
42
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_9F6005AF34C7906F717D420F892FD6D0 | binary | |
MD5:DCCA61BB85DF37A74CFB25BD55CCA586 | SHA256:E7E6EF37818CD278CB38DBDD06419A21CA67F7D24462AC5AD1B38AF302F0233C | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\98268581729527[1].htm | html | |
MD5:5584CD241A762D7A7488F14D5409293C | SHA256:56FD937F2948B7FC1B223FC1DA61E781A93F6B4C74CFD88E1115BB74418C7DFF | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:663C6837FC263259F7CCB20B9B85B643 | SHA256:F01121E17F2B2CCF702A8BC26607411E8A5598CA7F6FCAE0C2142002771B52F4 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\nachsendung[1].htm | html | |
MD5:A7252C141C5AA181C841E39763F781EA | SHA256:FC120F0FEF26FBCF511A641DA5E3B60303BED9EED8491B89C5446C7D42470E33 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:593F8BA26C4B846D1C8C6D80FA6DAD27 | SHA256:3C20C3C1BA0365DD21BFDA5048AF667F67DB4248624DB4A6C8E5BCB7A6E68608 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\50CD3D75D026C82E2E718570BD6F44D0_C37035B57D12BC5A8CC6DAA7D402E8E8 | binary | |
MD5:7DC7C3B8B218A02287106ED4BE50A9DC | SHA256:BD7114C37FB841029C96F185BE8AEE03417C8655B139EFDD8BFA569A308514C6 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\YUyu8fh8hs81[1].htm | compressed | |
MD5:D1F47514F59083943A04F7962FD5D3F9 | SHA256:15C34FA9B9E0EB9B5DE62032D7C2DE42F706C110856E0F038DFB58BCDBEB05EC | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\50CD3D75D026C82E2E718570BD6F44D0_C37035B57D12BC5A8CC6DAA7D402E8E8 | binary | |
MD5:7DC70CE32E4282B1A2B27B630BC7FA90 | SHA256:AA327B620C0034F6EB8E51F46FCDA04669BF525ADA0894A5D6EE74DE17653952 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\yuyu8fh8hs81[1].htm | html | |
MD5:C3051DF8275533F71BD187A7553E9313 | SHA256:77AEC2047A08F3C7C202BCBD00F3920808641940C03CF07E7E45D78B861174C0 | |||
| 324 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\thumb-up-dark[1].png | image | |
MD5:D343E8D42C53BC22D2A8F878501DD4C6 | SHA256:3E3CC9A361E2AF0C2B9DD8864C79D768BE5DD7D1C1CE6DB77848B6FB91535CC9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
49
DNS requests
17
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
324 | iexplore.exe | GET | 301 | 20.105.216.34:80 | http://dpcboecbsitcmt.com/Tgh8Xh5U/profile719/98268581729527??741158=828882? | unknown | — | — | unknown |
324 | iexplore.exe | GET | 200 | 23.32.238.89:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2f131cf452408714 | unknown | compressed | 4.66 Kb | unknown |
324 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEA9iL28hwv9dUh9yOh1H1i0%3D | unknown | binary | 471 b | unknown |
324 | iexplore.exe | GET | 301 | 20.105.216.34:80 | http://dpcboecbsitcmt.com/Tgh8Xh5U/profile719/98268581729527/??741158=828882? | unknown | — | — | unknown |
324 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | binary | 471 b | unknown |
324 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAJaYQ9Y64TxrVOuA9yphHo%3D | unknown | binary | 313 b | unknown |
324 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
324 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
324 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
324 | iexplore.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEA1uFYrLabZxEtE2U5X5DGM%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
324 | iexplore.exe | 20.105.216.34:80 | dpcboecbsitcmt.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
324 | iexplore.exe | 20.105.216.34:443 | dpcboecbsitcmt.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
324 | iexplore.exe | 23.32.238.89:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
324 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
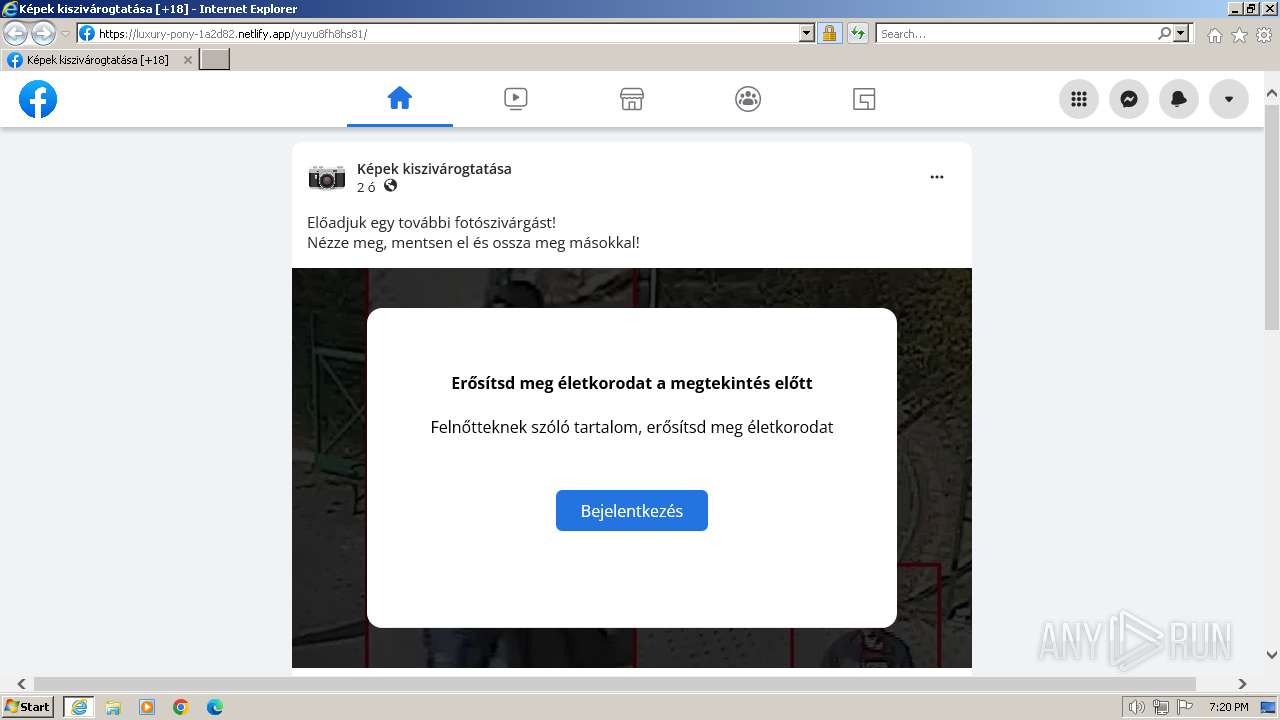
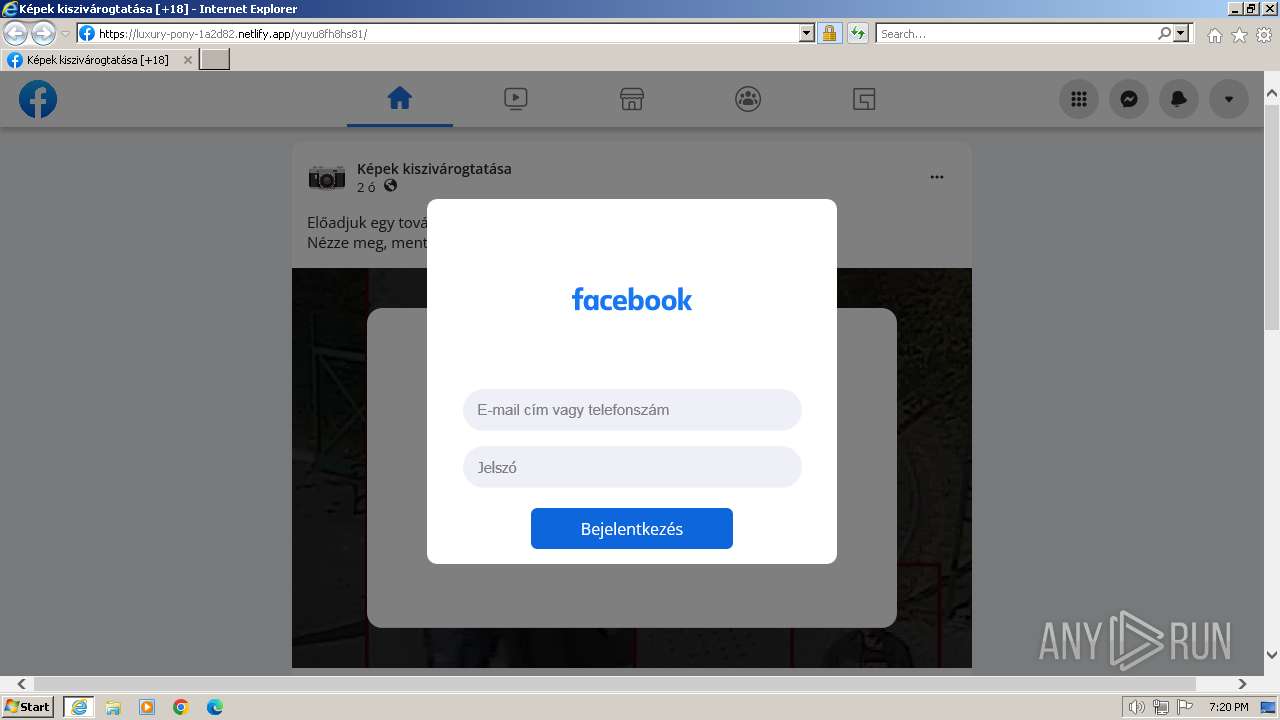
324 | iexplore.exe | 3.72.140.173:443 | luxury-pony-1a2d82.netlify.app | AMAZON-02 | DE | unknown |
324 | iexplore.exe | 104.17.25.14:443 | cdnjs.cloudflare.com | CLOUDFLARENET | — | unknown |
324 | iexplore.exe | 142.250.184.202:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dpcboecbsitcmt.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
luxury-pony-1a2d82.netlify.app |
| unknown |
cdnjs.cloudflare.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
code.jquery.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Netlify Hosted DNS Request - Possible Phishing Landing |
324 | iexplore.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Netlify Hosted TLS SNI Request - Possible Phishing Landing |
324 | iexplore.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Netlify Hosted TLS SNI Request - Possible Phishing Landing |
324 | iexplore.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Netlify Hosted TLS SNI Request - Possible Phishing Landing |
324 | iexplore.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Netlify Hosted TLS SNI Request - Possible Phishing Landing |
324 | iexplore.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Netlify Hosted TLS SNI Request - Possible Phishing Landing |
324 | iexplore.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Netlify Hosted TLS SNI Request - Possible Phishing Landing |
324 | iexplore.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
324 | iexplore.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Netlify Hosted TLS SNI Request - Possible Phishing Landing |
324 | iexplore.exe | Possible Social Engineering Attempted | ET HUNTING Suspicious Netlify Hosted TLS SNI Request - Possible Phishing Landing |