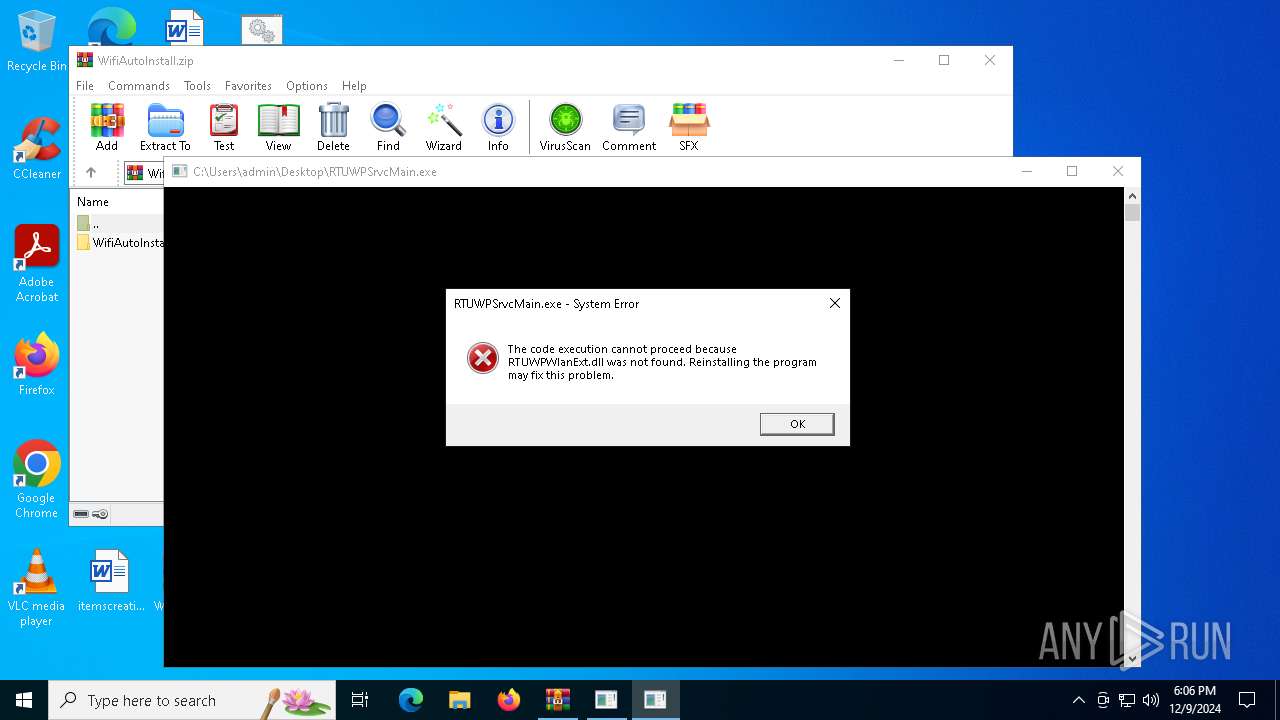
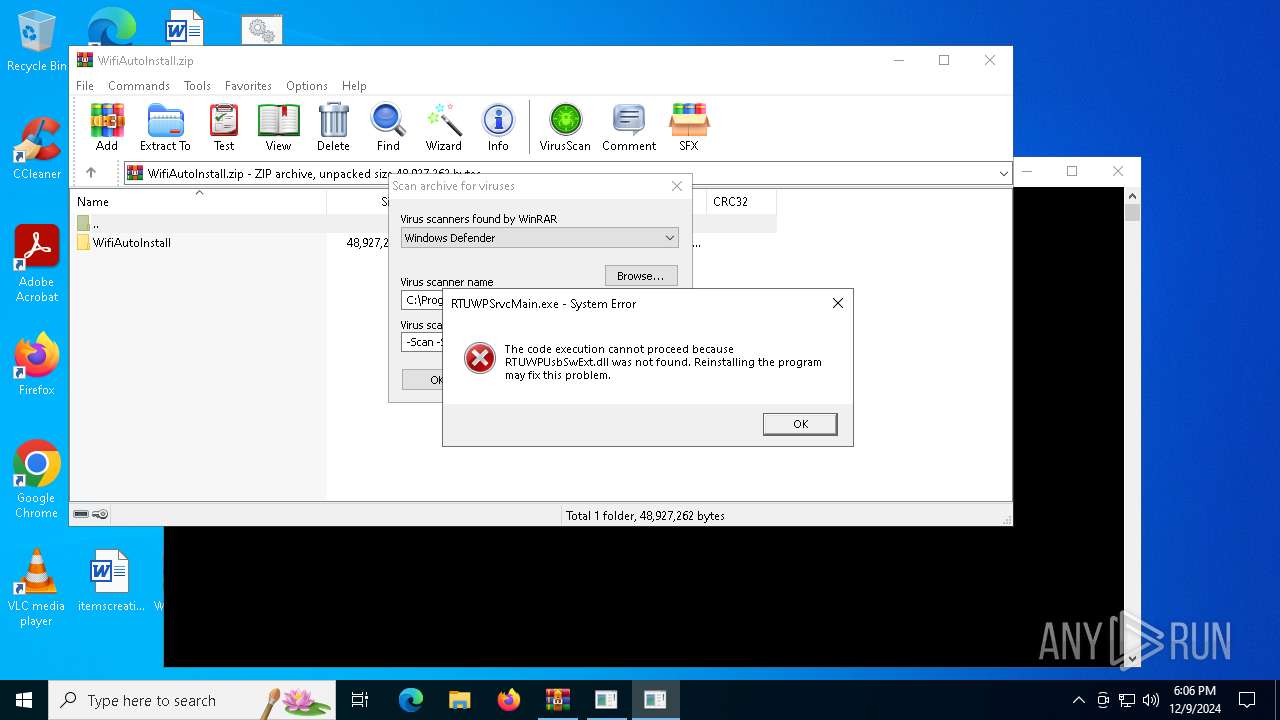
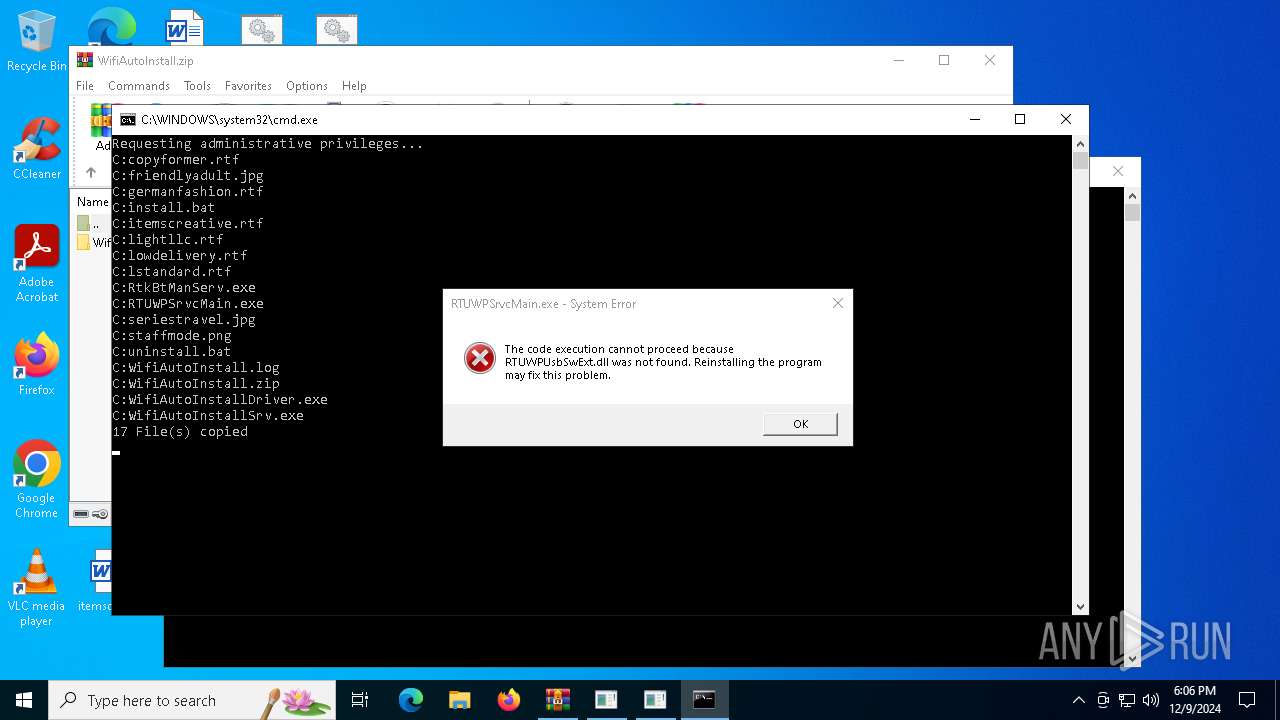
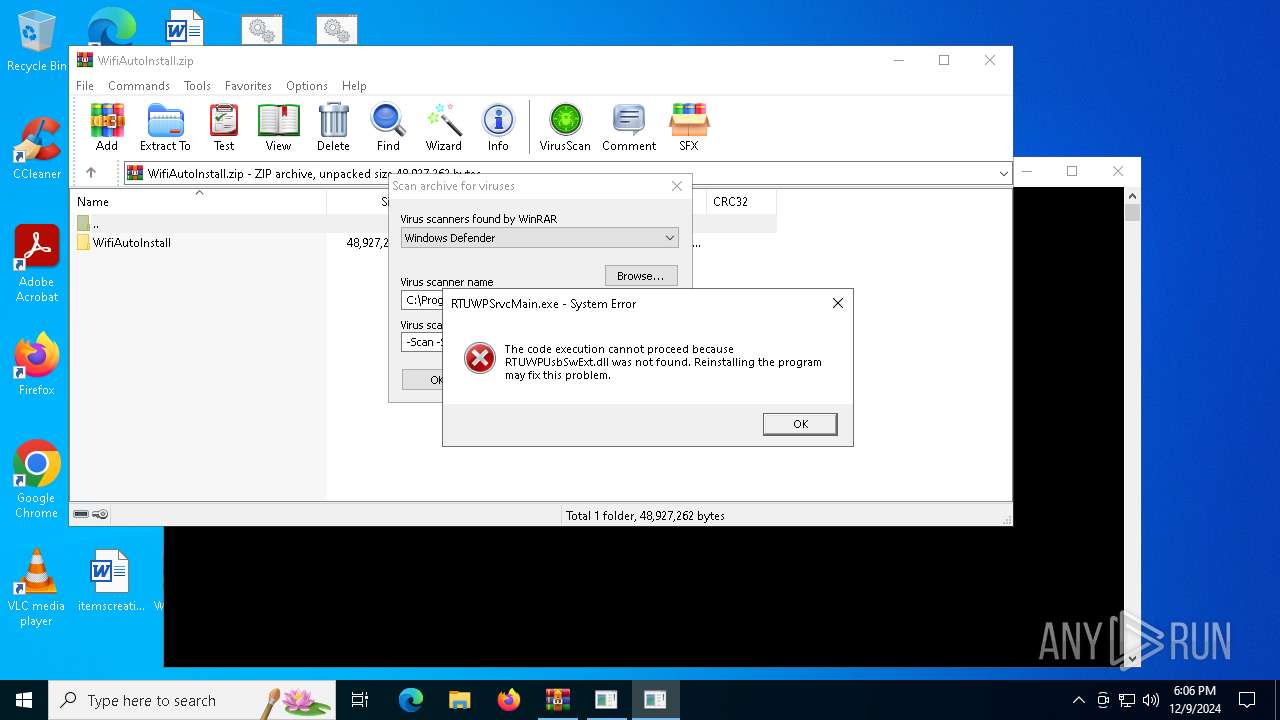
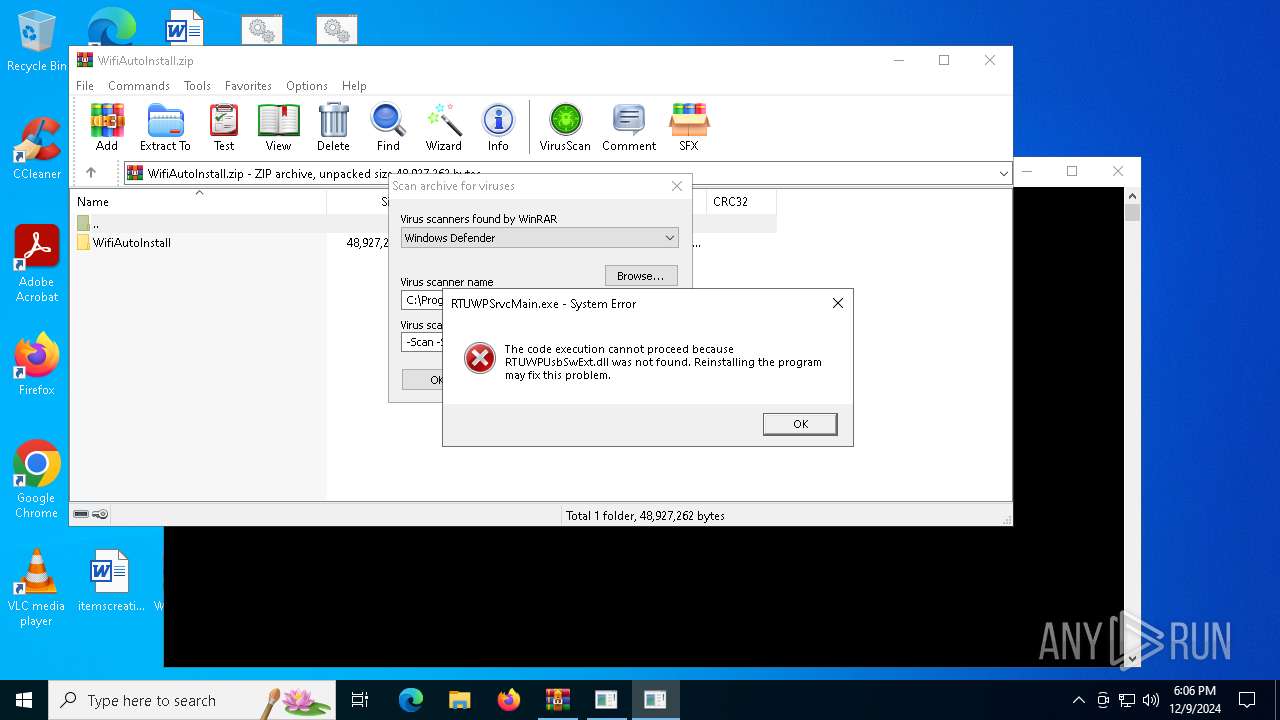
| File name: | WifiAutoInstall.zip |
| Full analysis: | https://app.any.run/tasks/bfbba583-9bf7-4124-b784-7e200519428e |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2024, 18:05:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | B35507076D30C363C41AE2FDE617BCAB |
| SHA1: | 803E6853AD5FE7B5BCC108D019BF8C8D20D76E33 |
| SHA256: | 643C1D74B0453159827E0835E9769FDD8C3B82F22A0771E408A48D83332BBD33 |
| SSDEEP: | 196608:GDd+IgXAxnA4AN3qCbIRThDEHQfyeZUKIG:I1gQxA4ANHIRpEHQfEG |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3612)
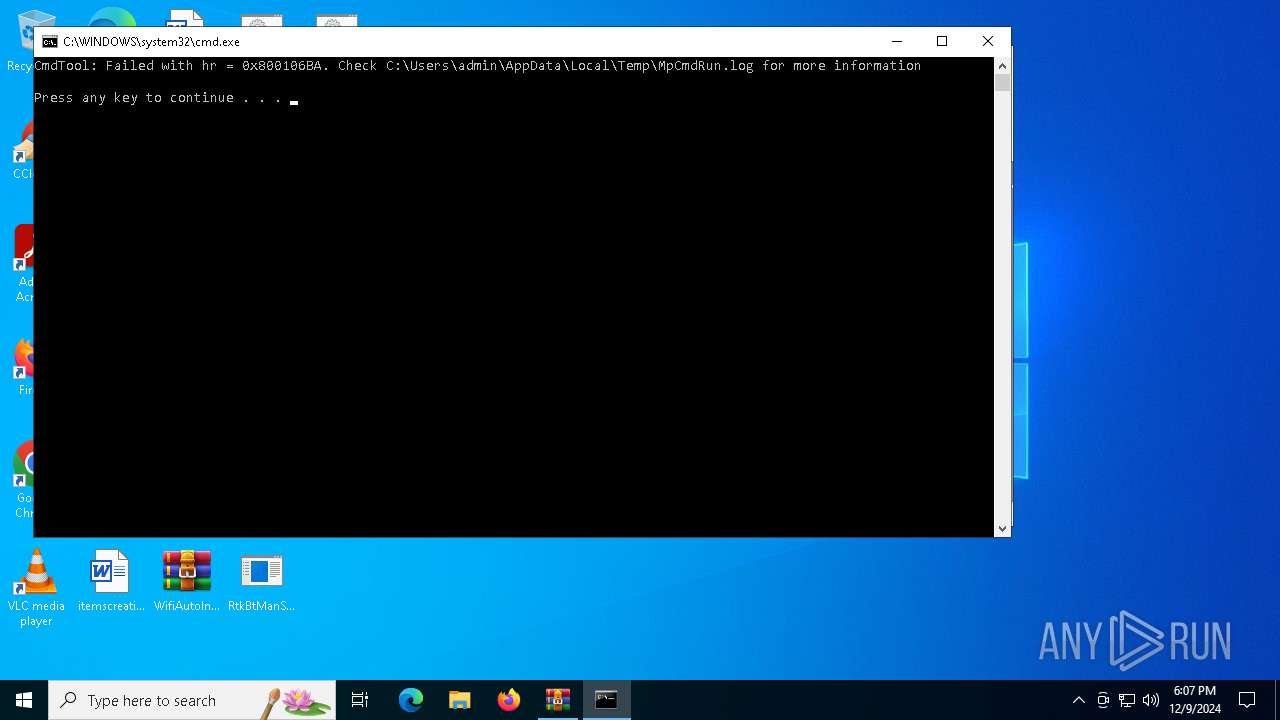
Antivirus name has been found in the command line (generic signature)
- MpCmdRun.exe (PID: 848)
SUSPICIOUS
Executing commands from a ".bat" file
- wscript.exe (PID: 5256)
- wscript.exe (PID: 5592)
- WinRAR.exe (PID: 3612)
Reads security settings of Internet Explorer
- WifiAutoInstallSrv.exe (PID: 5040)
- WifiAutoInstallDriver.exe (PID: 3420)
- WifiAutoInstallDriver.exe (PID: 2136)
- WinRAR.exe (PID: 3612)
The process executes VB scripts
- cmd.exe (PID: 3552)
- cmd.exe (PID: 1344)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 3552)
- cmd.exe (PID: 2424)
- cmd.exe (PID: 1344)
- cmd.exe (PID: 5868)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 5256)
- WinRAR.exe (PID: 3612)
- wscript.exe (PID: 5592)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5256)
- wscript.exe (PID: 5592)
Starts SC.EXE for service management
- cmd.exe (PID: 2424)
Application launched itself
- WifiAutoInstallSrv.exe (PID: 5040)
- WifiAutoInstallDriver.exe (PID: 3420)
- WifiAutoInstallDriver.exe (PID: 2136)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 2424)
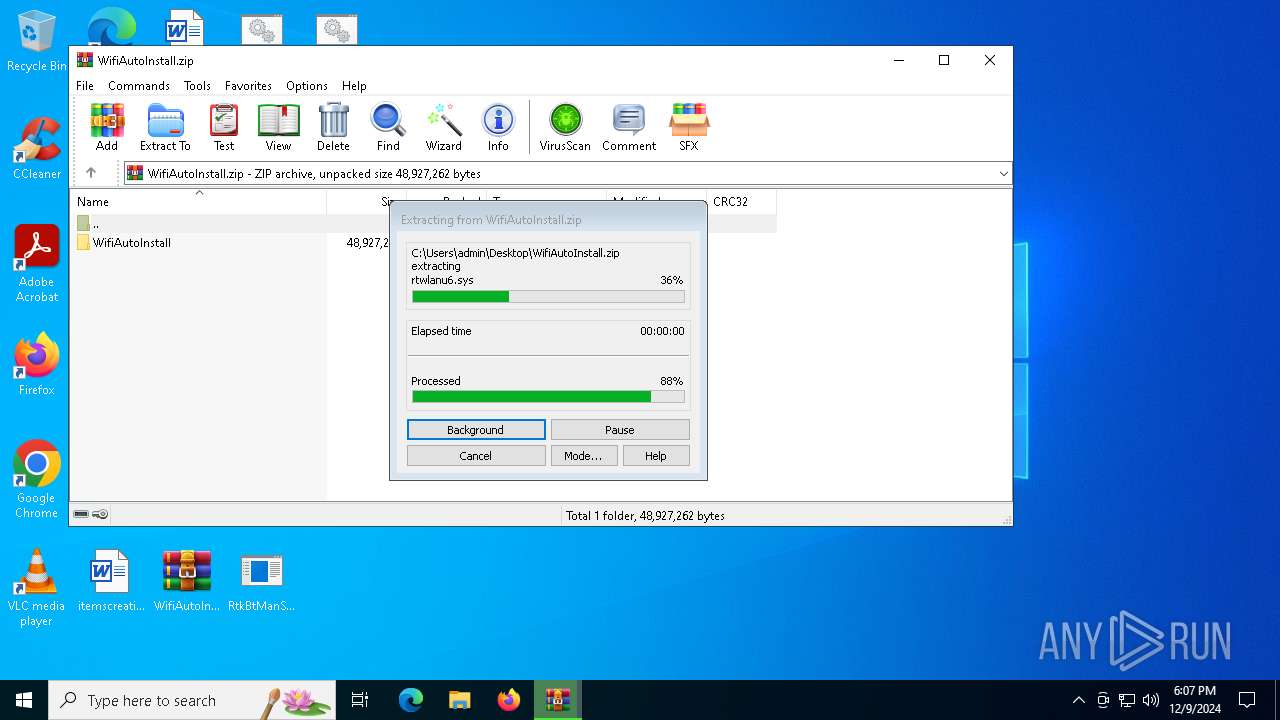
Executable content was dropped or overwritten
- xcopy.exe (PID: 5548)
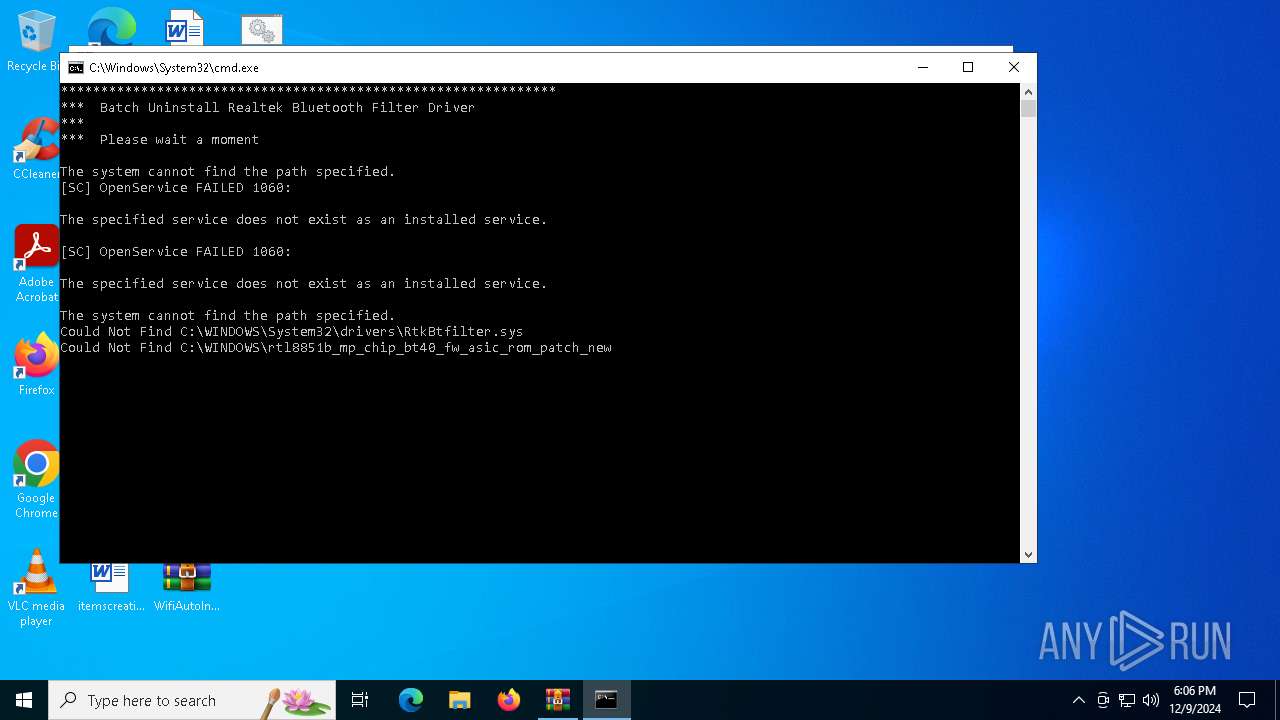
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 3612)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3612)
INFO
Sends debugging messages
- WifiAutoInstallSrv.exe (PID: 5040)
- WifiAutoInstallSrv.exe (PID: 5252)
- WifiAutoInstallDriver.exe (PID: 4824)
- WifiAutoInstallDriver.exe (PID: 3420)
- WifiAutoInstallDriver.exe (PID: 2136)
- RtkBtManServ.exe (PID: 3816)
- WifiAutoInstallDriver.exe (PID: 4204)
Reads the computer name
- WifiAutoInstallSrv.exe (PID: 5040)
- WifiAutoInstallDriver.exe (PID: 3420)
- WifiAutoInstallDriver.exe (PID: 2136)
- WifiAutoInstallSrv.exe (PID: 5252)
- RtkBtManServ.exe (PID: 3816)
- RtkBtManServ.exe (PID: 5092)
- MpCmdRun.exe (PID: 848)
Checks supported languages
- WifiAutoInstallSrv.exe (PID: 5040)
- WifiAutoInstallSrv.exe (PID: 5252)
- WifiAutoInstallDriver.exe (PID: 3420)
- WifiAutoInstallDriver.exe (PID: 4824)
- WifiAutoInstallDriver.exe (PID: 4204)
- RtkBtManServ.exe (PID: 3816)
- RtkBtManServ.exe (PID: 5092)
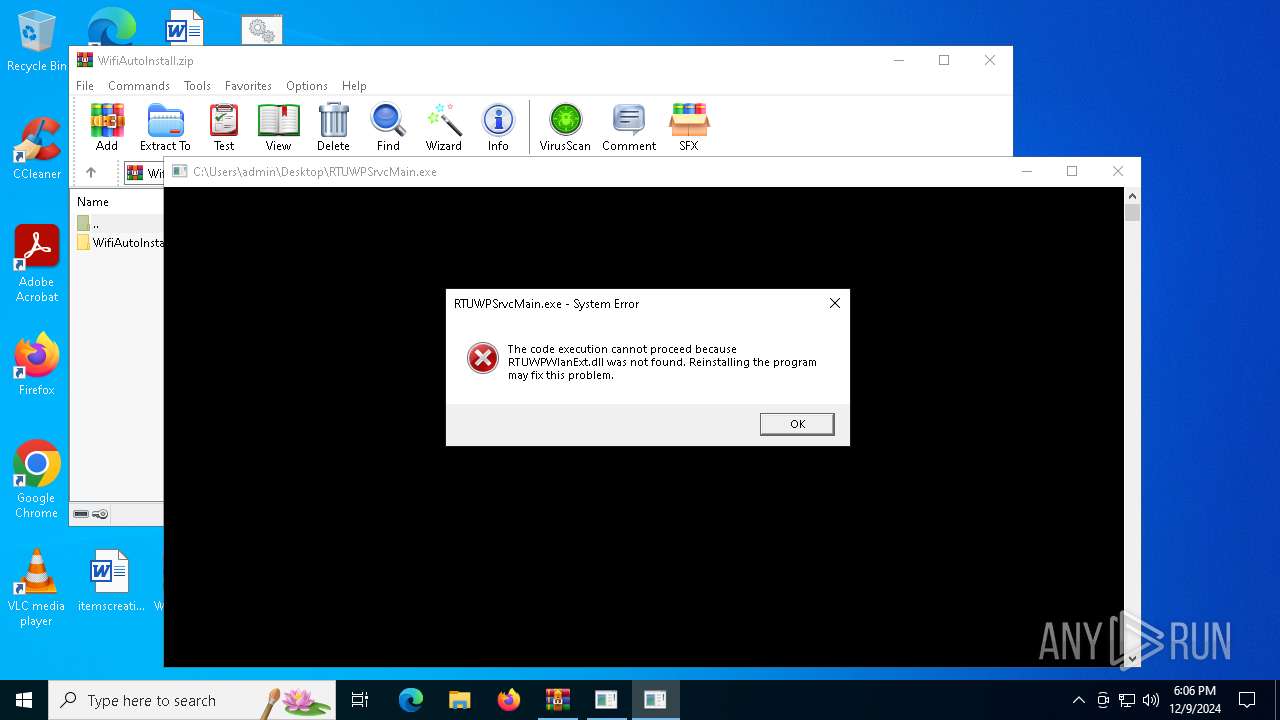
Manual execution by a user
- WifiAutoInstallSrv.exe (PID: 5040)
- cmd.exe (PID: 3552)
- WifiAutoInstallDriver.exe (PID: 3420)
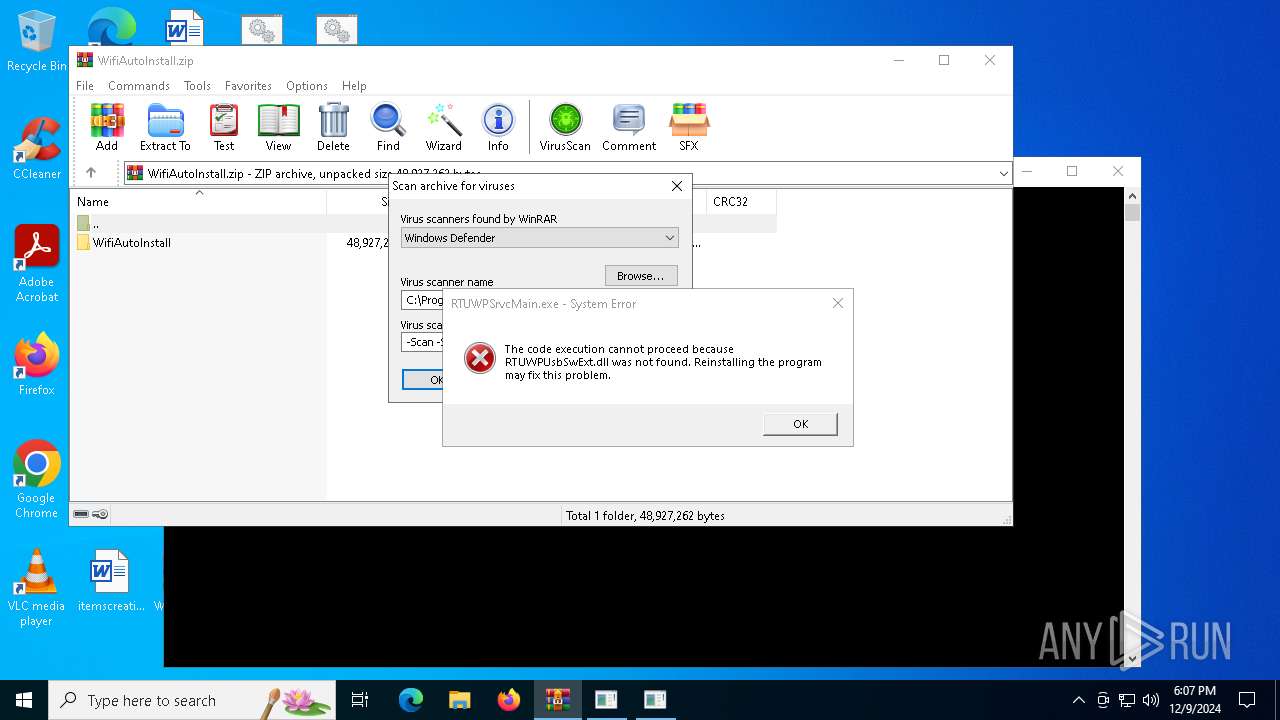
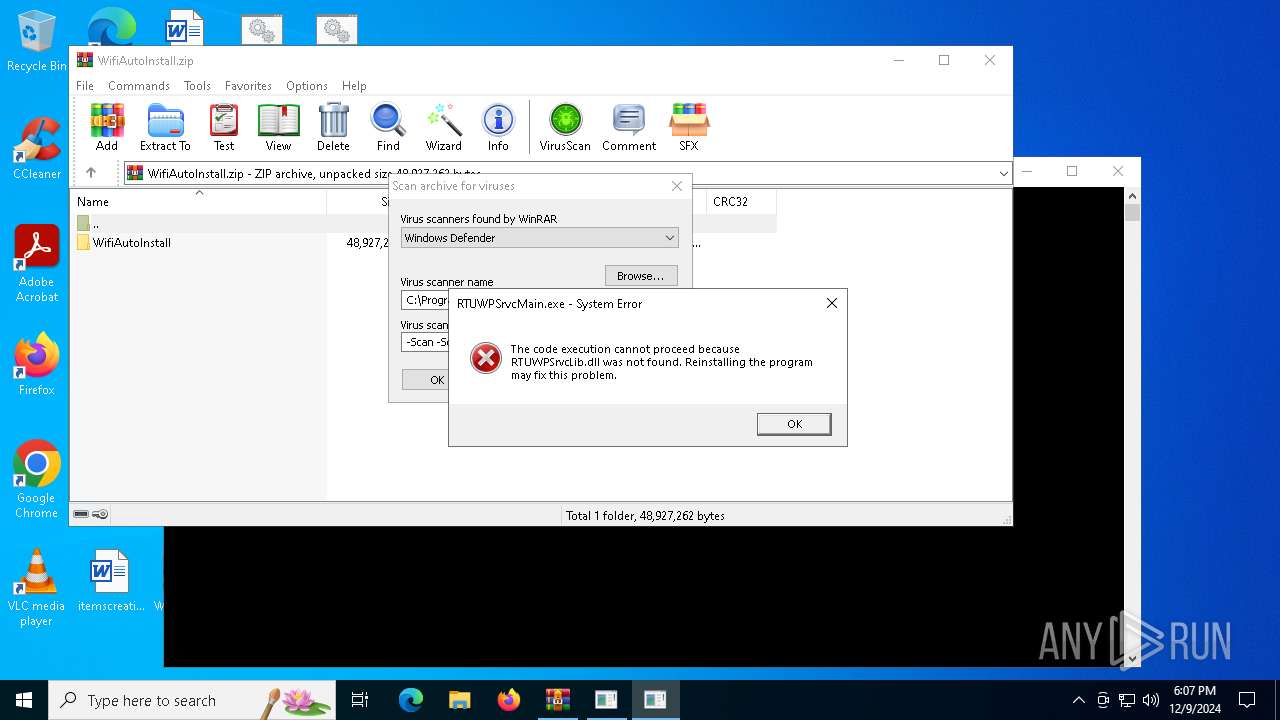
- RTUWPSrvcMain.exe (PID: 5576)
- RTUWPSrvcMain.exe (PID: 3260)
- WifiAutoInstallDriver.exe (PID: 2136)
- RtkBtManServ.exe (PID: 3816)
- cmd.exe (PID: 1344)
- RtkBtManServ.exe (PID: 5092)
Create files in a temporary directory
- xcopy.exe (PID: 5572)
- xcopy.exe (PID: 5548)
Process checks computer location settings
- WifiAutoInstallSrv.exe (PID: 5040)
- WifiAutoInstallDriver.exe (PID: 3420)
The process uses the downloaded file
- WifiAutoInstallSrv.exe (PID: 5040)
- WifiAutoInstallDriver.exe (PID: 3420)
- wscript.exe (PID: 5592)
- WifiAutoInstallDriver.exe (PID: 2136)
- WinRAR.exe (PID: 3612)
Creates files in the program directory
- RtkBtManServ.exe (PID: 5092)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | None |
| ZipModifyDate: | 2024:12:09 18:46:16 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | WifiAutoInstall/ |
Total processes
165
Monitored processes
43
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WifiAutoInstallSrv.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | ping -n 3 127.0.0.1 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RtkBtManServ.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR3612.45969" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1344 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\install.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1944 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RTUWPSrvcMain.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
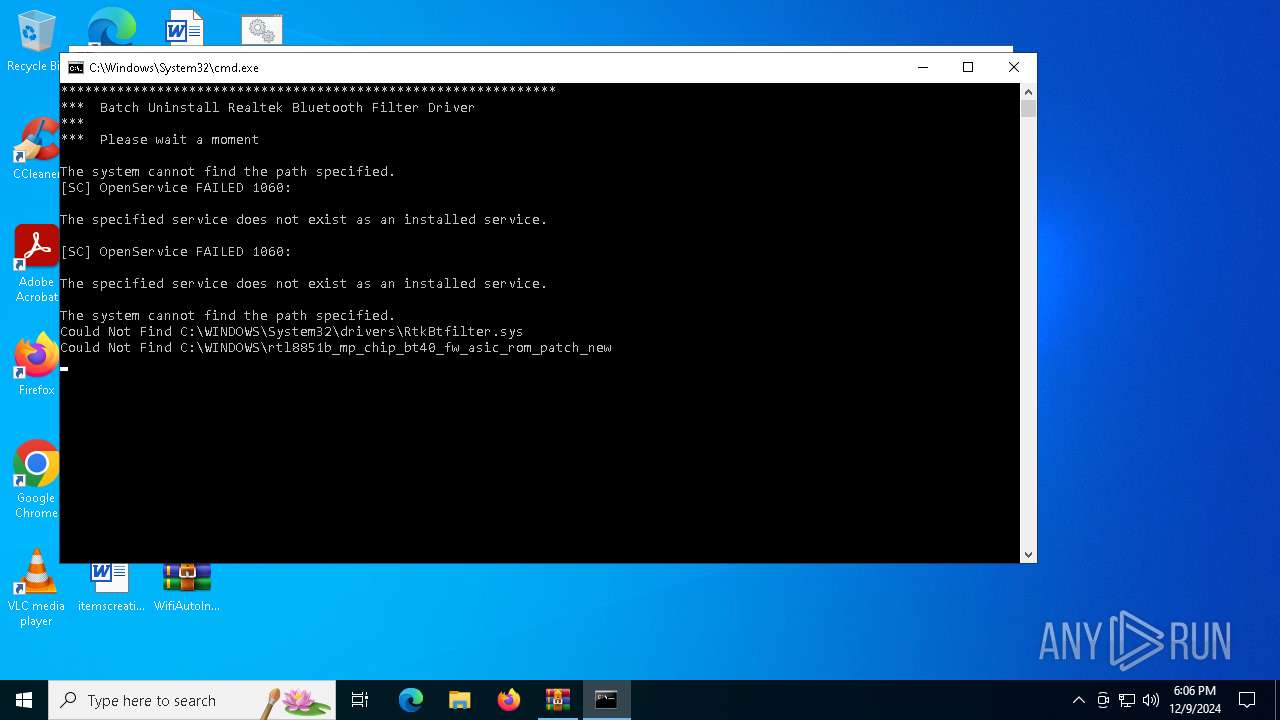
| 2136 | sc delete RtkBtManServ | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Users\admin\Desktop\WifiAutoInstallDriver.exe" | C:\Users\admin\Desktop\WifiAutoInstallDriver.exe | explorer.exe | ||||||||||||
User: admin Company: Realtek Integrity Level: MEDIUM Description: WifiAutoInstall Exit code: 1 Version: 2.0.1.0 Modules
| |||||||||||||||
| 2160 | "C:\WINDOWS\system32\cacls.exe" "C:\WINDOWS\system32\config\system" | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Control ACLs Program Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2160 | "C:\WINDOWS\system32\cacls.exe" "C:\WINDOWS\system32\config\system" | C:\Windows\System32\cacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Control ACLs Program Exit code: 5 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 228
Read events
5 217
Write events
11
Delete events
0
Modification events
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\WifiAutoInstall.zip | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3552) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
| (PID) Process: | (1344) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
Executable files
31
Suspicious files
14
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
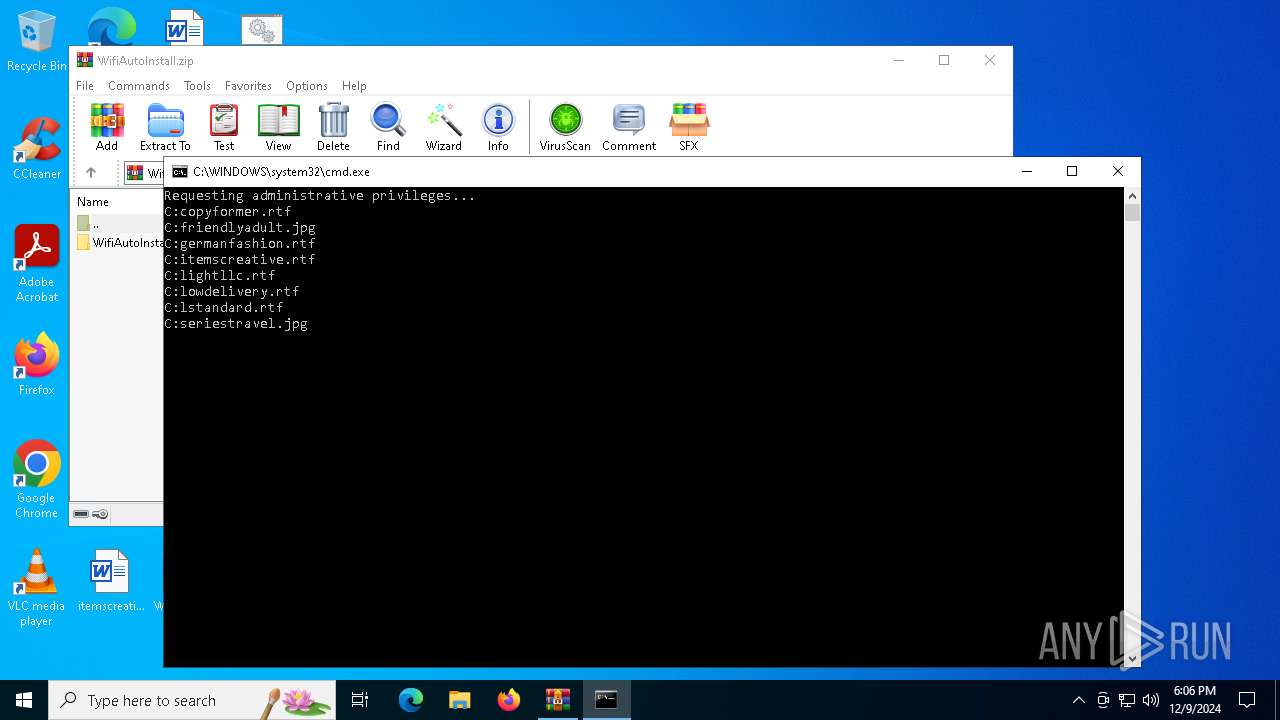
| 5572 | xcopy.exe | C:\Users\admin\AppData\Local\Temp\Bluetooth\lowdelivery.rtf | text | |
MD5:1B2C06424AE1775B7AF22C0D7AD4A7FA | SHA256:B6E9560107AAD03C8DAFCD9378EDC289E4676A8F39C31CD47462FF253F36684B | |||
| 5572 | xcopy.exe | C:\Users\admin\AppData\Local\Temp\Bluetooth\germanfashion.rtf | text | |
MD5:4B01EE976F512265903C9C92DD70EE2A | SHA256:9B8C2C0FB741577D856B04FD1A8AF89713A0F220CA773EF8E510D78BF931AB20 | |||
| 5572 | xcopy.exe | C:\Users\admin\AppData\Local\Temp\Bluetooth\lightllc.rtf | text | |
MD5:FF7E13B06FE437C51E27E82C6C5D930F | SHA256:2071ACDBCF45D7BCF90263C0F39C45A7A4E58812374E4DFB412F83DDE4EAEE59 | |||
| 5572 | xcopy.exe | C:\Users\admin\AppData\Local\Temp\Bluetooth\friendlyadult.jpg | image | |
MD5:6CFECA9D2857ADE7AA742A276CEDCEF3 | SHA256:1C57F88377683A7F18CE65CC717D3EC8718A5916211B8E99A374E061308BE9CC | |||
| 5572 | xcopy.exe | C:\Users\admin\AppData\Local\Temp\Bluetooth\itemscreative.rtf | text | |
MD5:8494DA4E48D7643926A0BF04F495A371 | SHA256:117AA35316168641E4C7E6F9D435C8D386260DE3E707B7D8C9321306ADFB27FB | |||
| 5572 | xcopy.exe | C:\Users\admin\AppData\Local\Temp\Bluetooth\copyformer.rtf | text | |
MD5:4B9BE1B57C022C3E71F8C91017D2C3F4 | SHA256:9718E68846F8881387366109869A6F420F6CCBB47A09CEE8A0350A7D07E8B07C | |||
| 5572 | xcopy.exe | C:\Users\admin\AppData\Local\Temp\Bluetooth\seriestravel.jpg | image | |
MD5:ADF81D6A804A21818374CB67C93FC6DE | SHA256:19CB505A7196B12E254FAB6B07E4C37DEBC3D255A3655693A2DE6C17028FEF2B | |||
| 5572 | xcopy.exe | C:\Users\admin\AppData\Local\Temp\Bluetooth\lstandard.rtf | text | |
MD5:485FA430F43993D514DABF0A68C9B8E9 | SHA256:9F1EB49DECD08186CA9ABF9D861C034444CE236DF9C19830CFCDD3576D1378AC | |||
| 5572 | xcopy.exe | C:\Users\admin\AppData\Local\Temp\Bluetooth\staffmode.png | image | |
MD5:E1BF4772FA6F174195166421408B027E | SHA256:22C05AC88AACD9B4654EDA1EDFA83EA0D2F142B2F4F74E040E04CC672AB8DA15 | |||
| 5548 | xcopy.exe | C:\Users\admin\AppData\Local\Temp\Bluetooth\install.bat | text | |
MD5:24A495CD48FF2106B9F73E453195DE94 | SHA256:5F5BE22EC35CB4D90BDF61A39CF0FFE755948673245345D23C204DC00DFB0189 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
19
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
448 | svchost.exe | GET | 200 | 2.16.164.96:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
448 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.96:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
448 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
448 | svchost.exe | 2.16.164.96:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.96:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
448 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WifiAutoInstallSrv.exe | Retry run C:\Users\admin\Desktop\WifiAutoInstallSrv.exe
|
WifiAutoInstallSrv.exe | sei.lpParameters = (null)
|
WifiAutoInstallSrv.exe | _tmain() Option = |
WifiAutoInstallDriver.exe | sei.lpParameters = (null)
|
WifiAutoInstallDriver.exe | Retry run C:\Users\admin\Desktop\WifiAutoInstallDriver.exe
|
WifiAutoInstallDriver.exe | _tmain() Option = |
WifiAutoInstallDriver.exe | sei.lpParameters = (null)
|
WifiAutoInstallDriver.exe | Retry run C:\Users\admin\Desktop\WifiAutoInstallDriver.exe
|
WifiAutoInstallDriver.exe | _tmain() Option = |
RtkBtManServ.exe | _tfopen , GetLastError=0x0 |