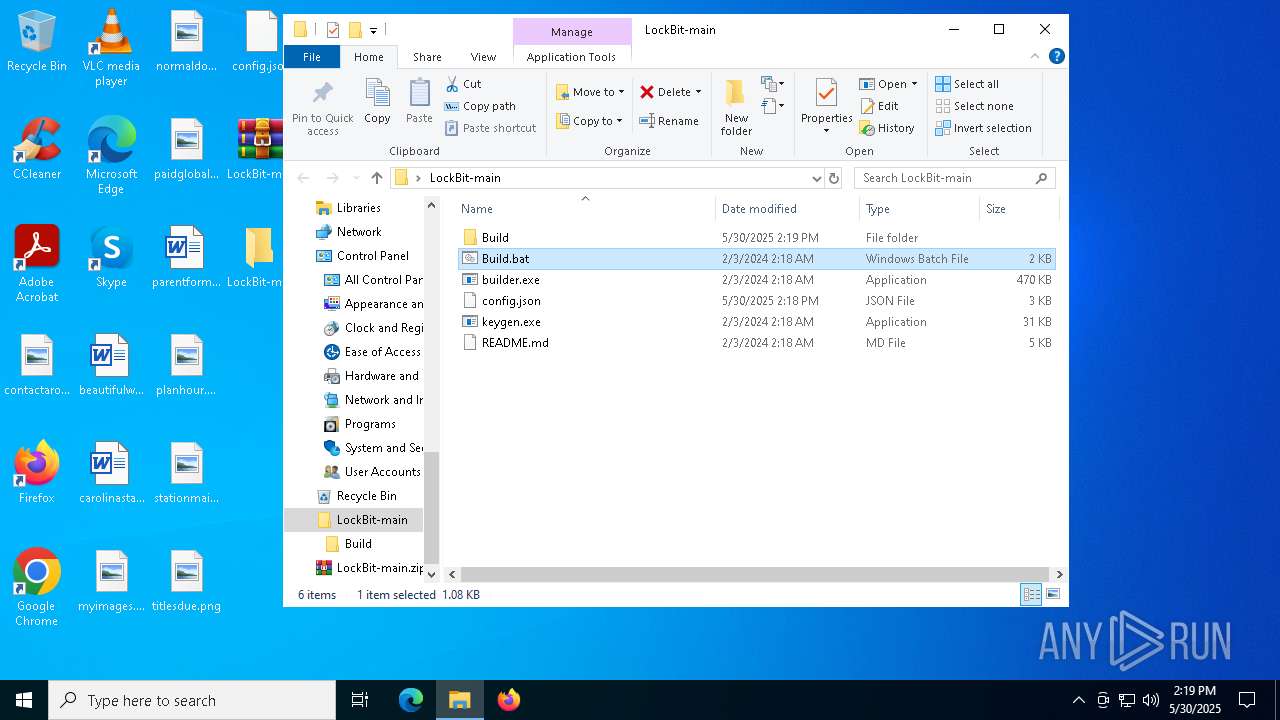
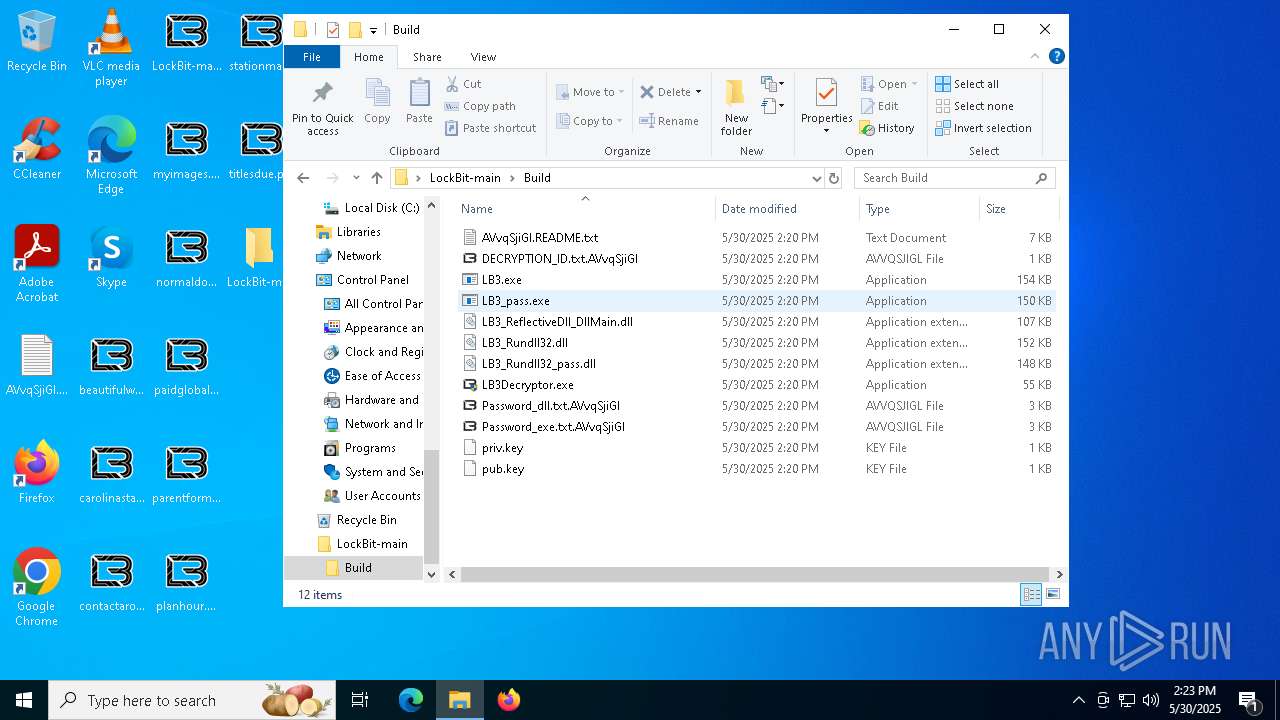
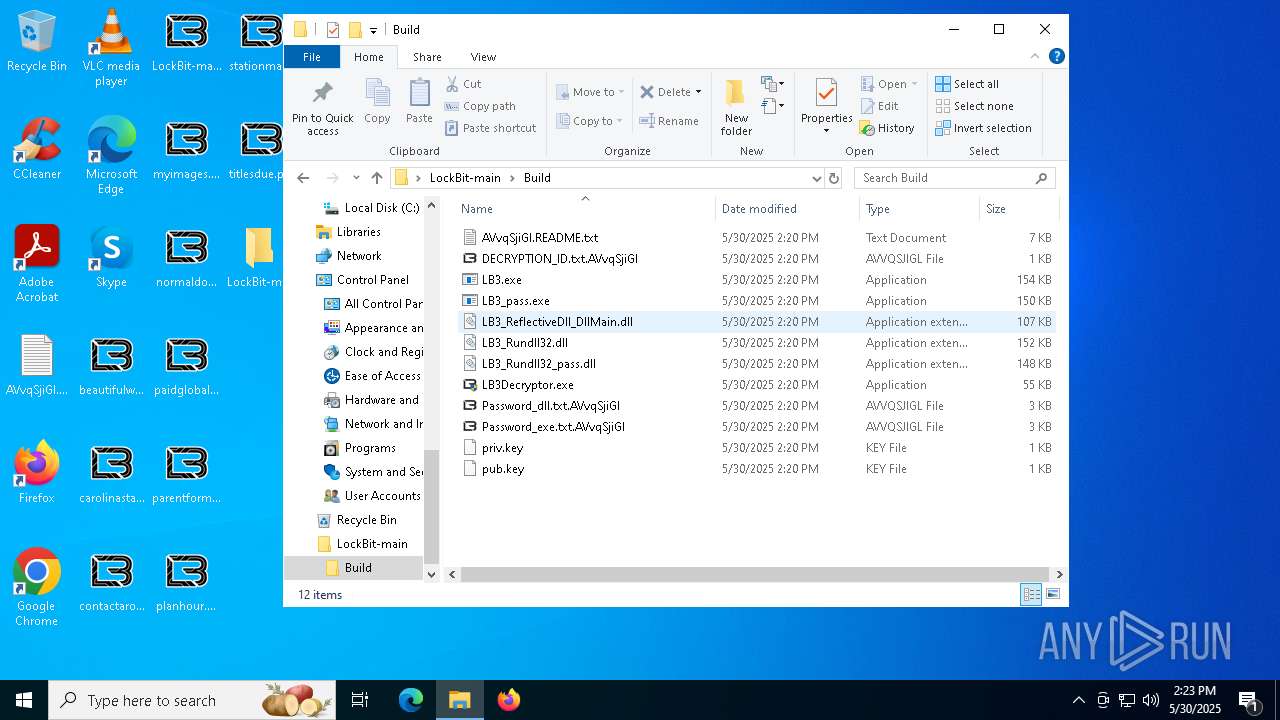
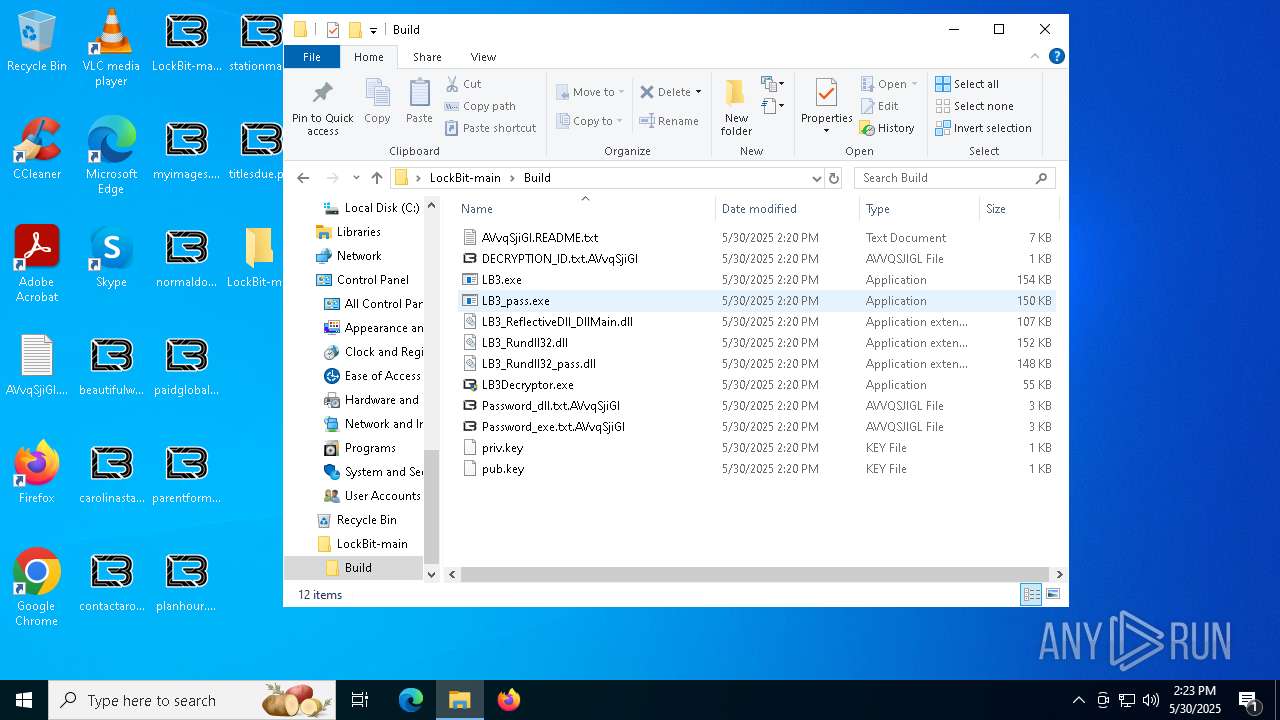
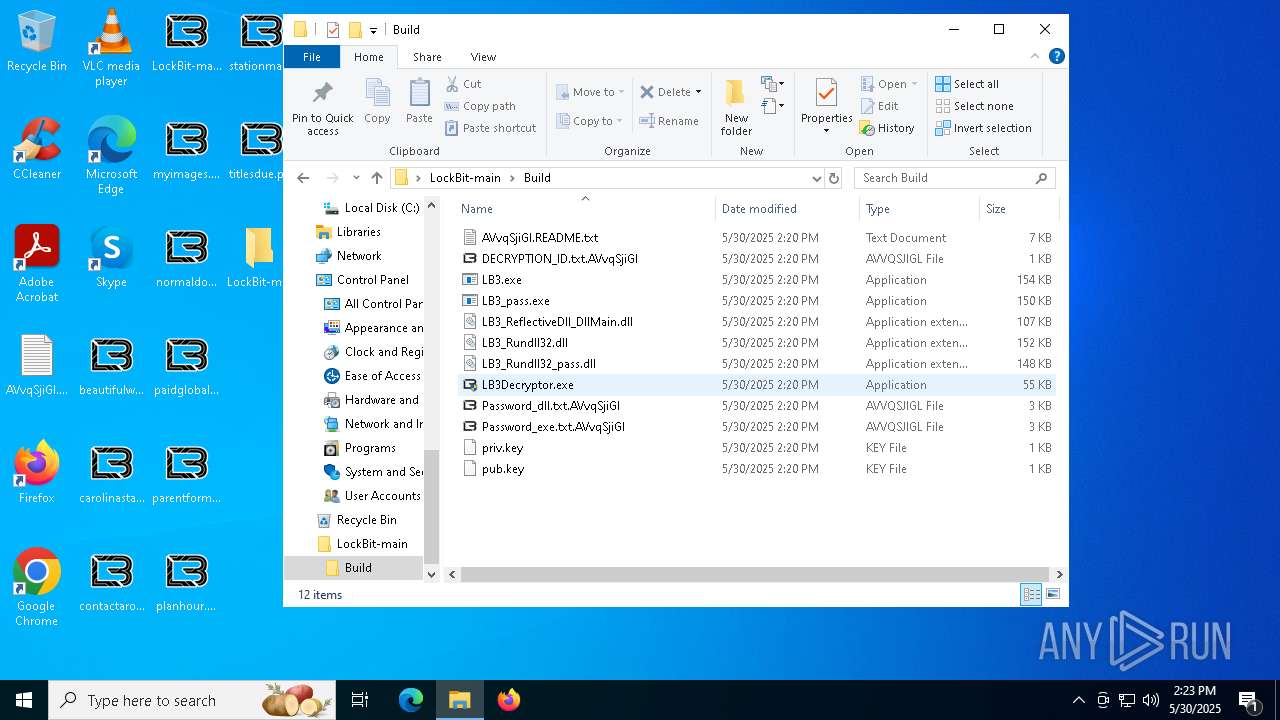
| File name: | 5-27-2025_1-09_35323.jpg |
| Full analysis: | https://app.any.run/tasks/a4082e43-d0d5-4bfa-823a-513736ab92f4 |
| Verdict: | Malicious activity |
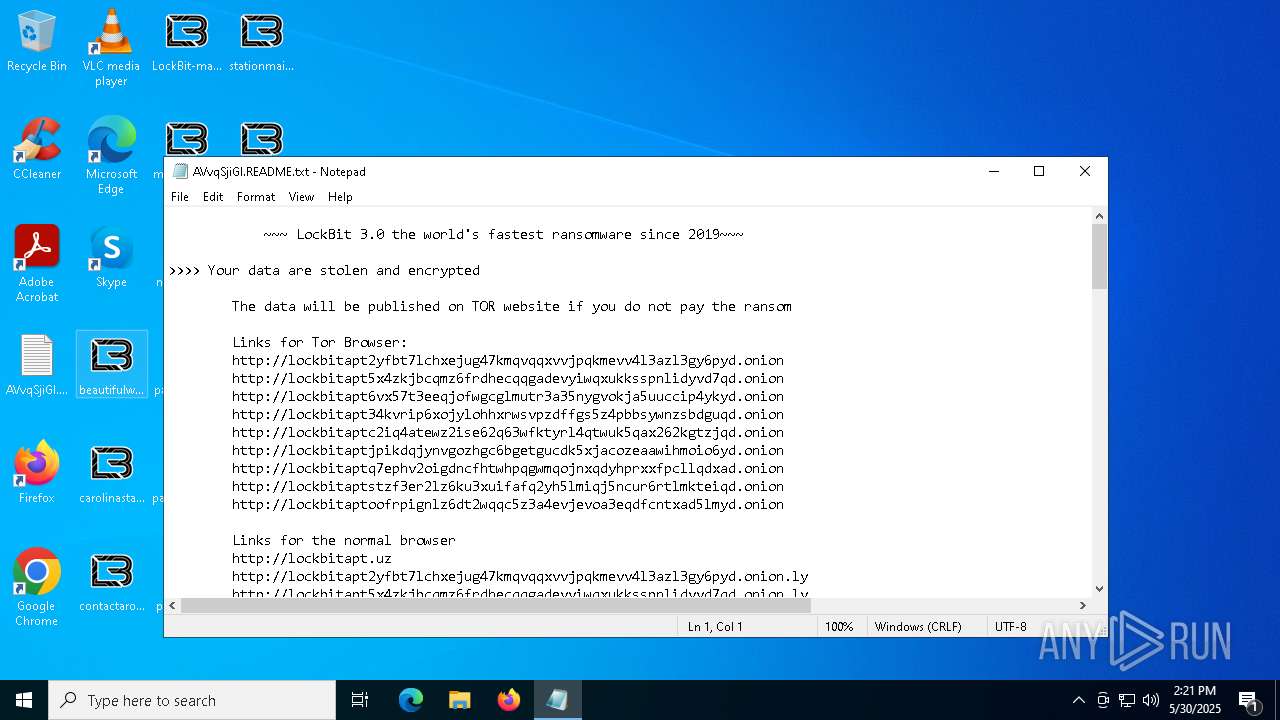
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | May 30, 2025, 14:18:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | image/jpeg |
| File info: | JPEG image data, JFIF standard 1.01, resolution (DPI), density 120x120, segment length 16, baseline, precision 8, 640x480, components 3 |
| MD5: | DEAC84D1DAF5059C4EF706A2D62394F9 |
| SHA1: | 592F48D51EF8958978074B8427563816B24756C1 |
| SHA256: | 643AC3B398032BD4CCA48619648CD188F0D52AD837946A78AA26D41DFBBF0882 |
| SSDEEP: | 1536:kfHLx5fXJoMMGjUOwInvxZ2RAqdLzzJj4tgjXA3xU7r9:arziFGjeInJZ2RA8LZj4QaxM9 |
MALICIOUS
[YARA] LockBit is detected
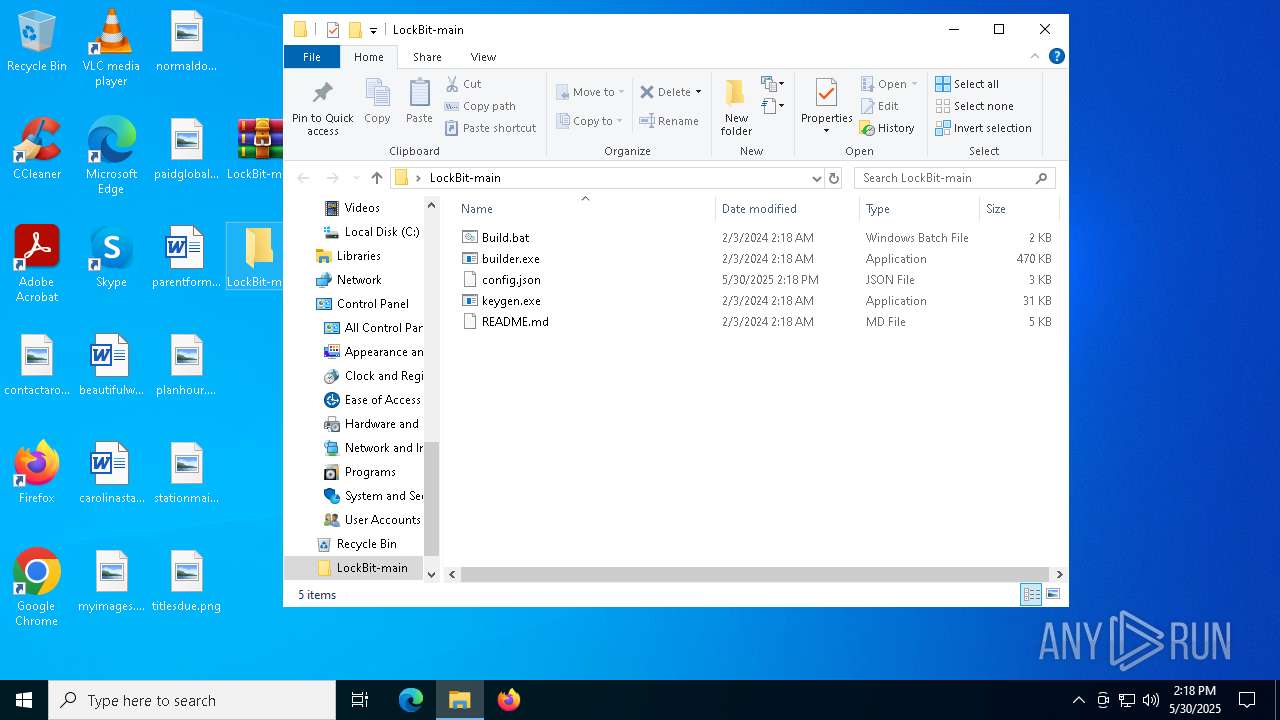
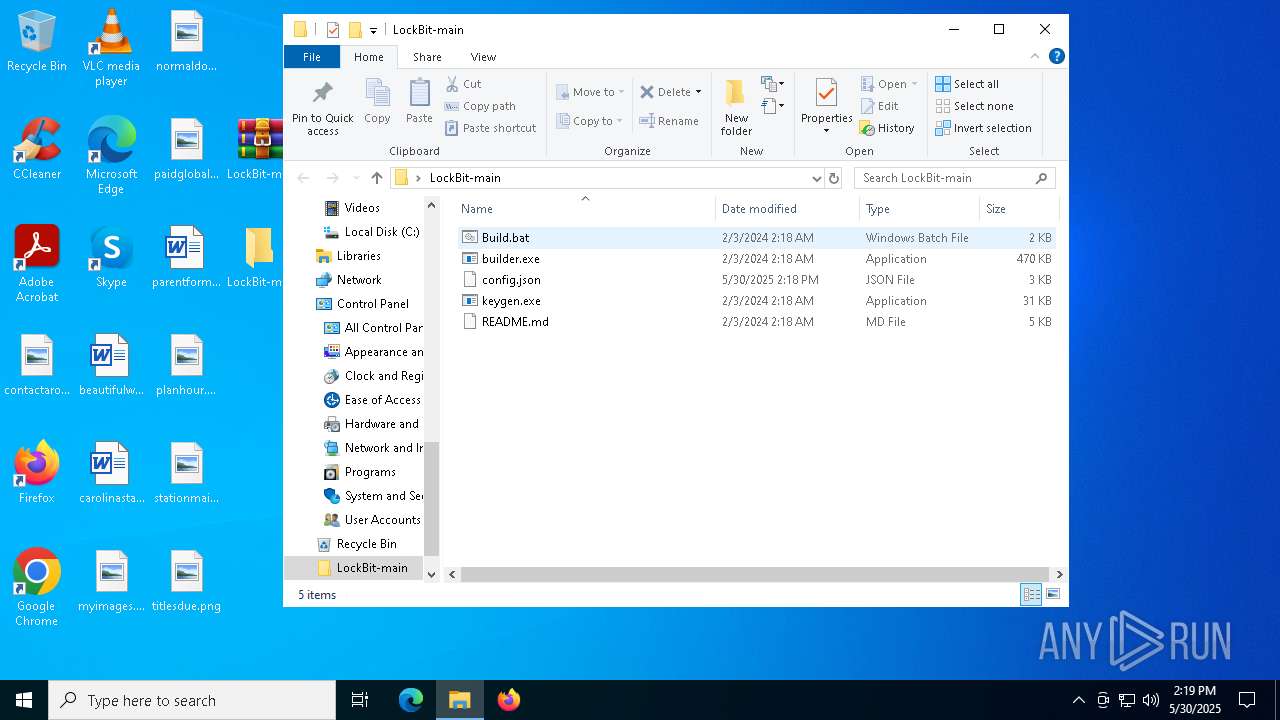
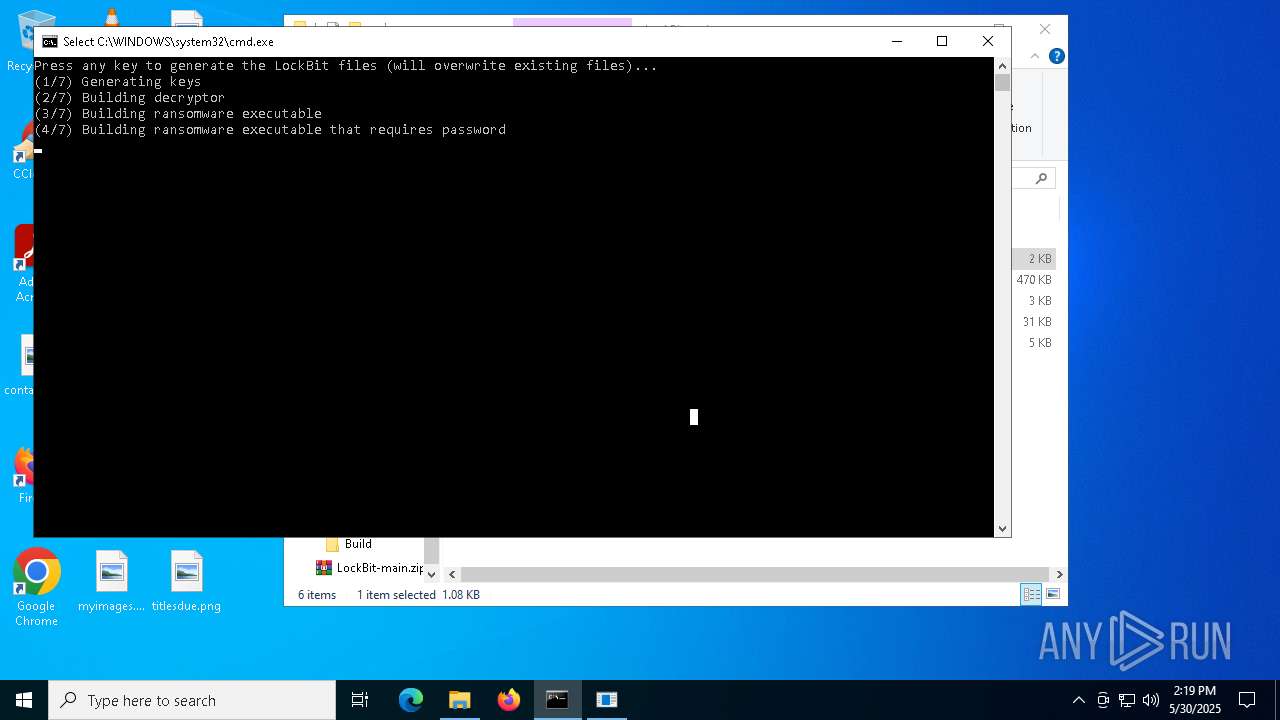
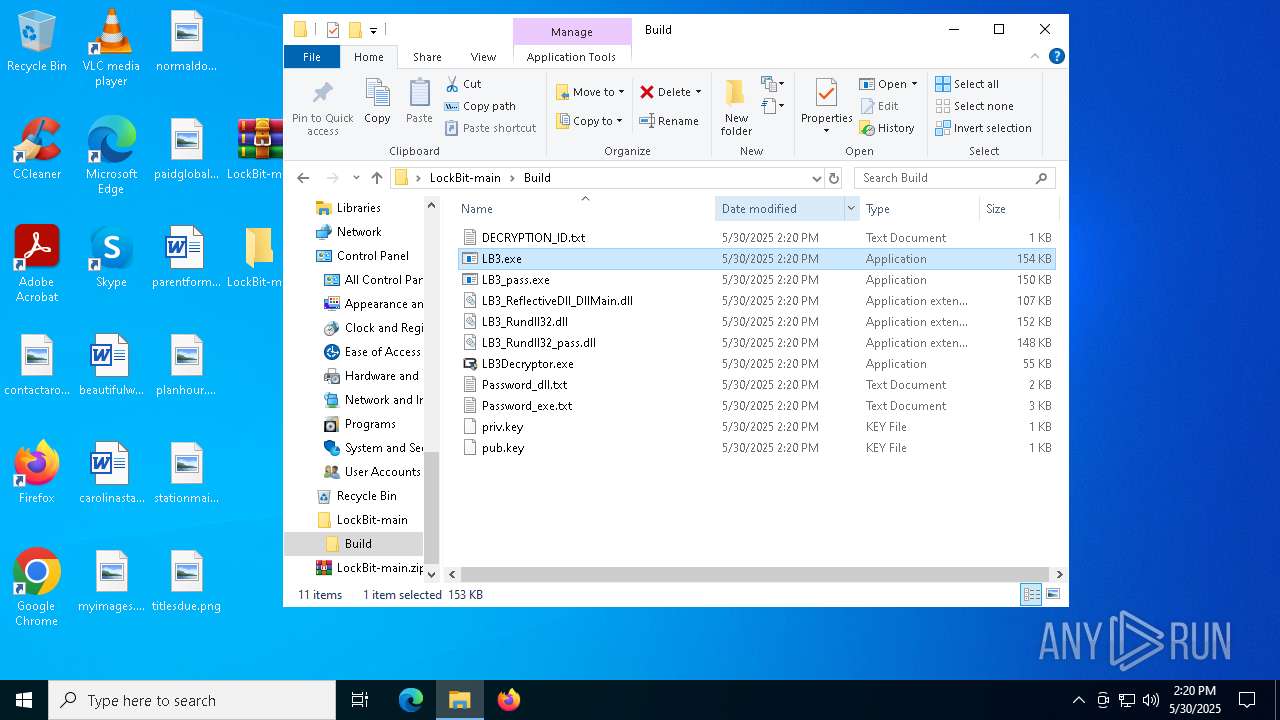
- builder.exe (PID: 1568)
- LB3.exe (PID: 7564)
Known privilege escalation attack
- dllhost.exe (PID: 8088)
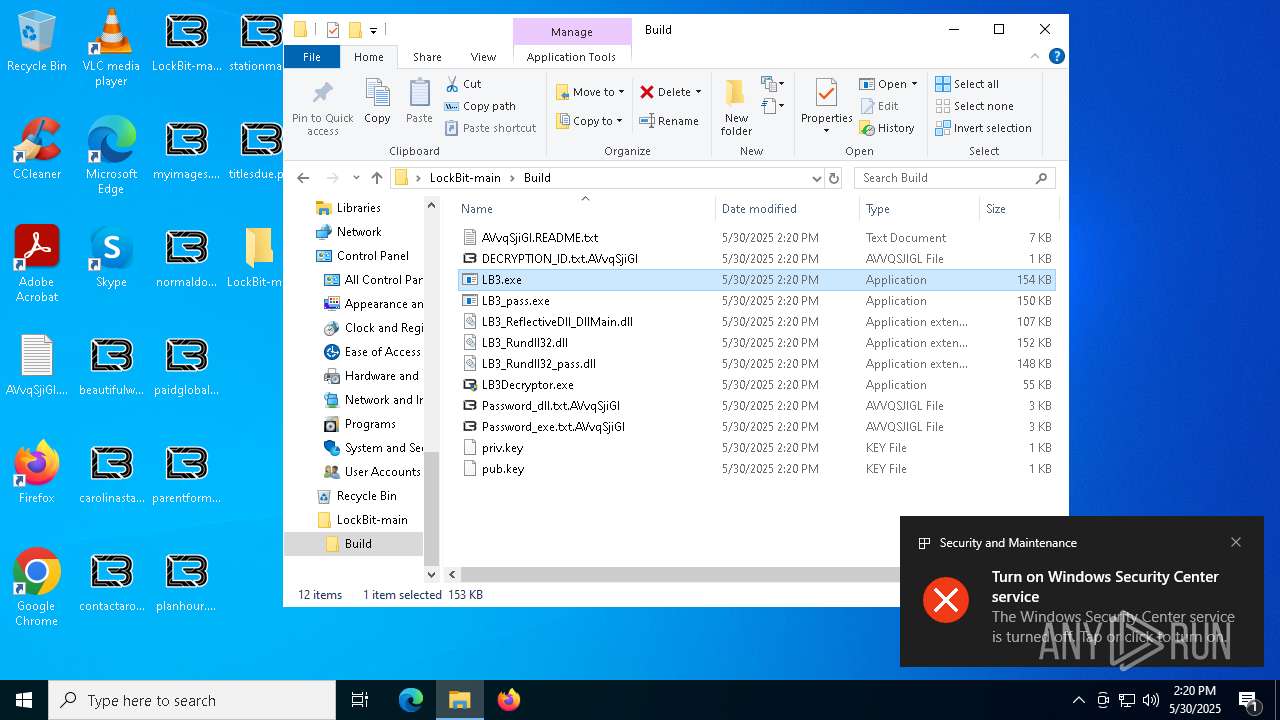
Renames files like ransomware
- LB3.exe (PID: 7564)
RANSOMWARE has been detected
- LB3.exe (PID: 7564)
LOCKBIT3 has been detected
- 5C3F.tmp (PID: 2404)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- builder.exe (PID: 1568)
- LB3.exe (PID: 7564)
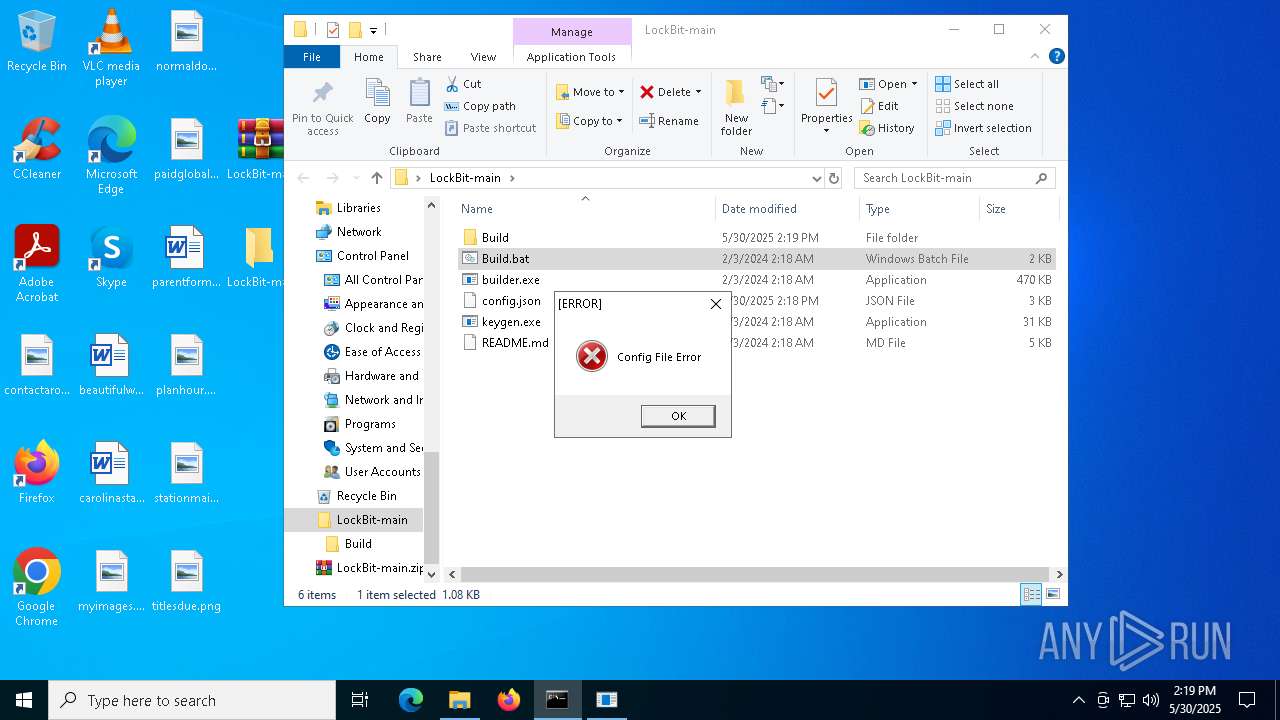
Executable content was dropped or overwritten
- builder.exe (PID: 7584)
- builder.exe (PID: 7928)
- builder.exe (PID: 7608)
- builder.exe (PID: 7804)
- builder.exe (PID: 7408)
- builder.exe (PID: 720)
- LB3.exe (PID: 7564)
The process creates files with name similar to system file names
- builder.exe (PID: 7804)
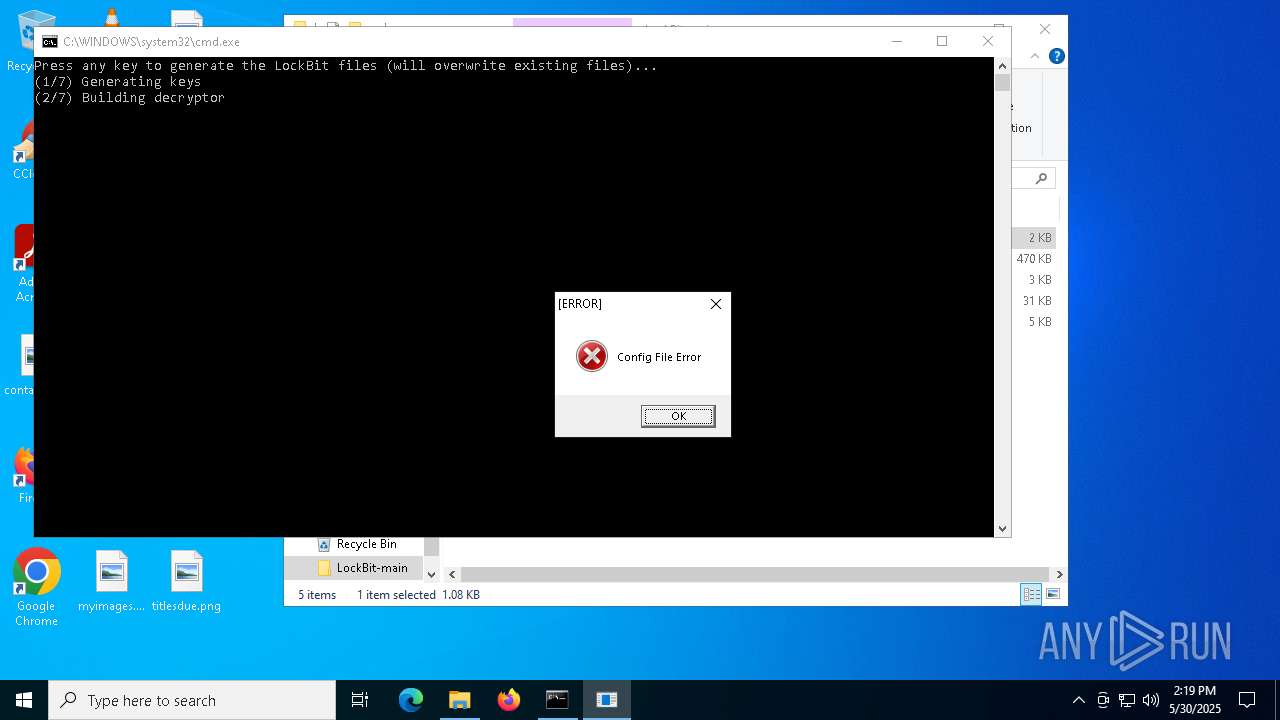
Executes application which crashes
- LB3_pass.exe (PID: 1116)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 7652)
Write to the desktop.ini file (may be used to cloak folders)
- LB3.exe (PID: 7564)
Starts application with an unusual extension
- LB3.exe (PID: 7564)
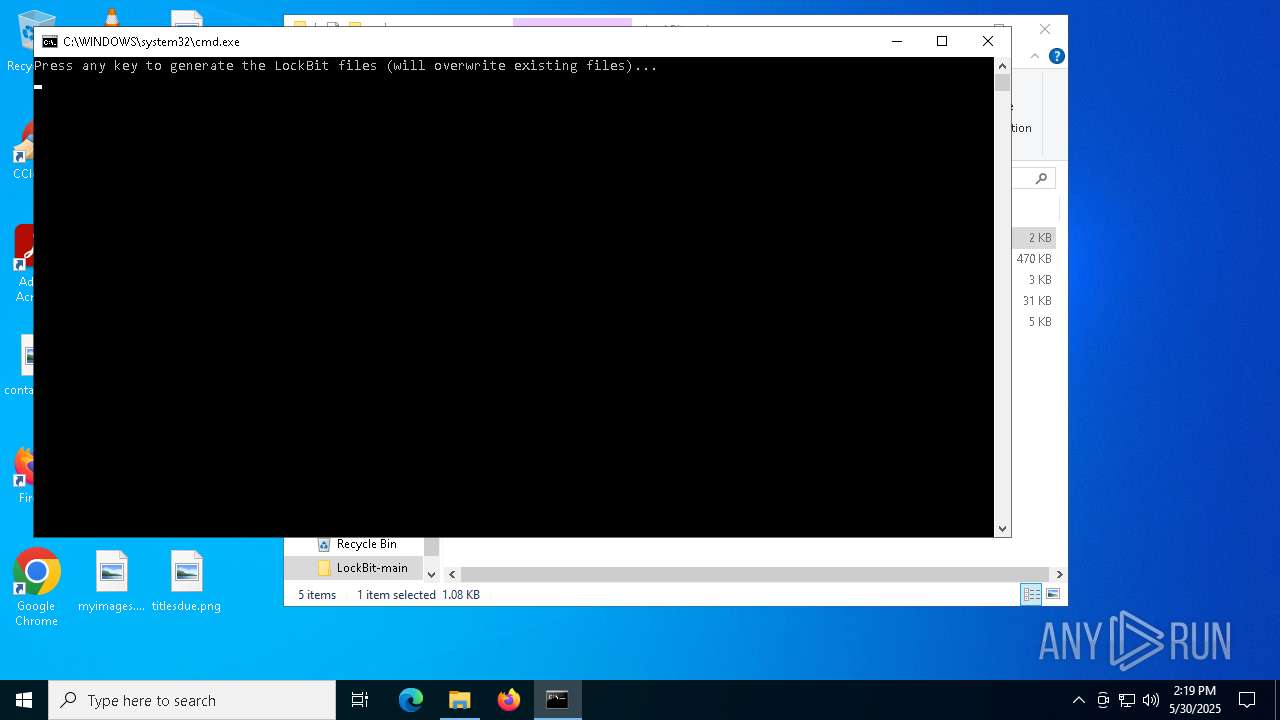
Starts CMD.EXE for commands execution
- 5C3F.tmp (PID: 2404)
Hides command output
- cmd.exe (PID: 7676)
INFO
Checks supported languages
- keygen.exe (PID: 2320)
- builder.exe (PID: 2064)
- builder.exe (PID: 5232)
- builder.exe (PID: 1568)
- keygen.exe (PID: 8096)
- builder.exe (PID: 7928)
- builder.exe (PID: 7608)
- builder.exe (PID: 7584)
- builder.exe (PID: 7408)
- builder.exe (PID: 720)
- LB3_pass.exe (PID: 1116)
- LB3.exe (PID: 8116)
- LB3.exe (PID: 7564)
- builder.exe (PID: 7804)
- ShellExperienceHost.exe (PID: 7652)
Reads the computer name
- builder.exe (PID: 2064)
- builder.exe (PID: 5232)
- builder.exe (PID: 1568)
- LB3.exe (PID: 8116)
- ShellExperienceHost.exe (PID: 7652)
- LB3.exe (PID: 7564)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7264)
Manual execution by a user
- cmd.exe (PID: 7268)
- WinRAR.exe (PID: 7264)
- cmd.exe (PID: 7456)
- LB3_pass.exe (PID: 1116)
- LB3.exe (PID: 8116)
- notepad.exe (PID: 8000)
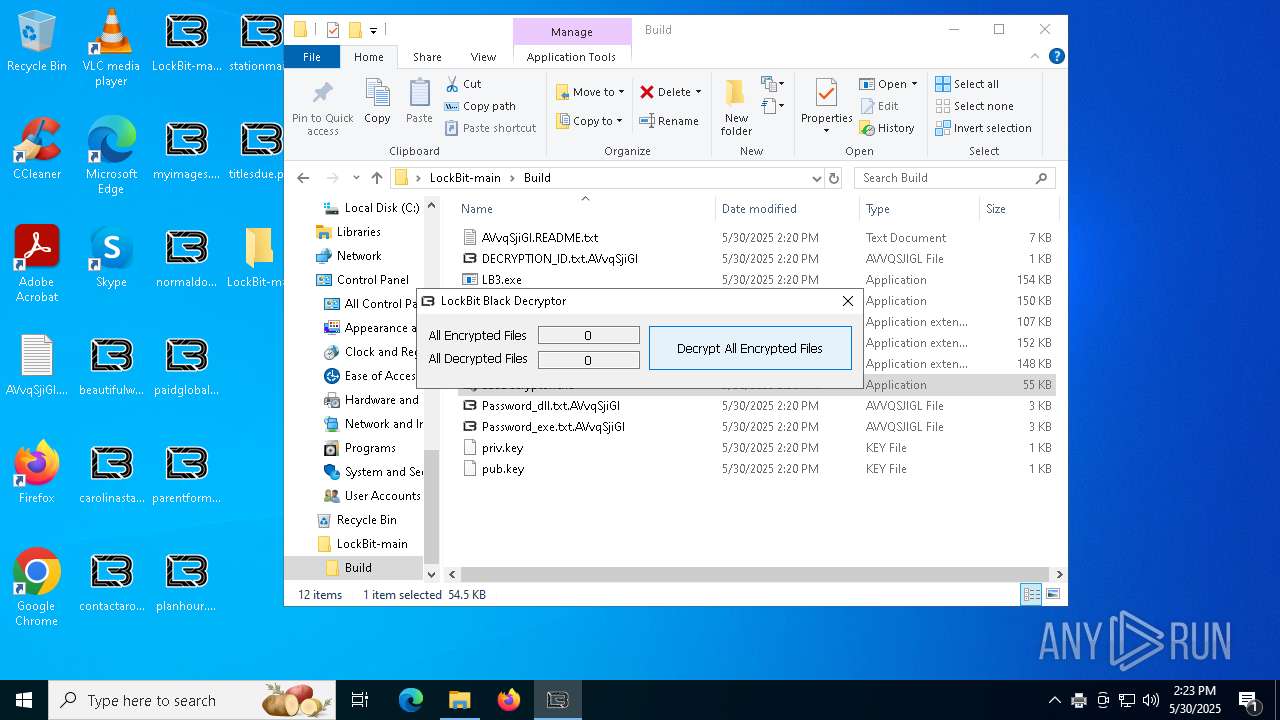
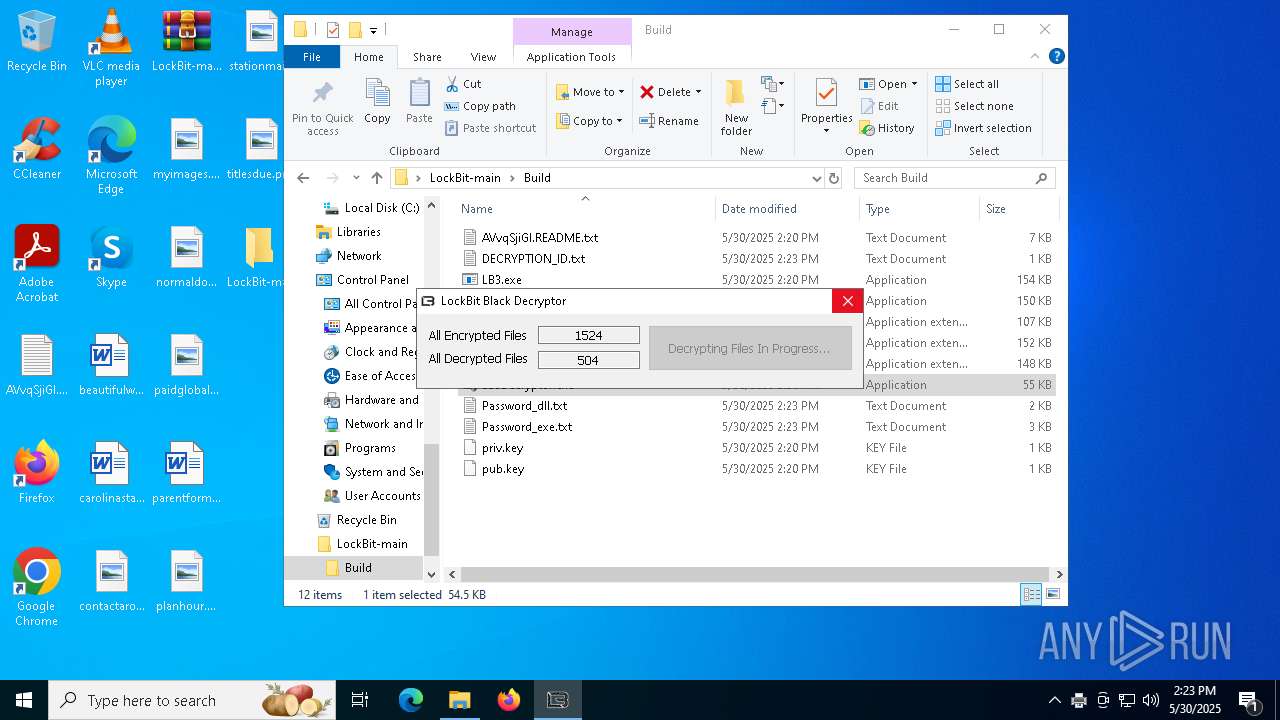
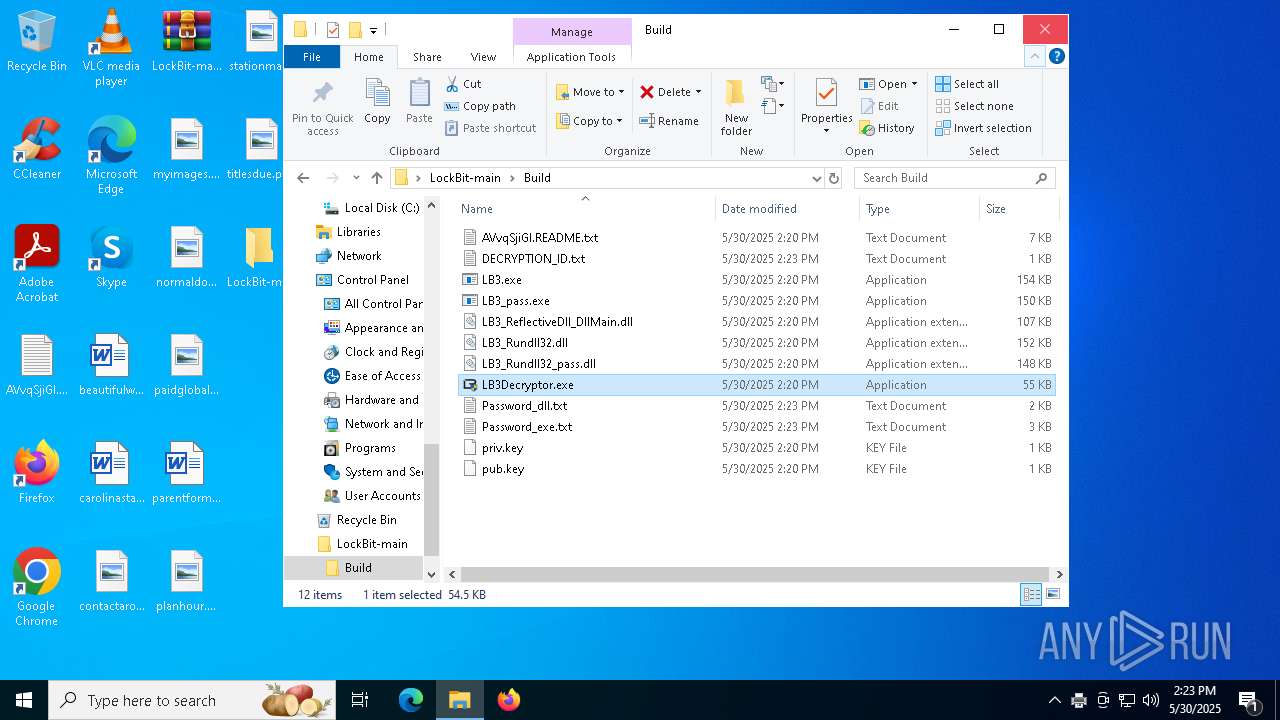
- LB3Decryptor.exe (PID: 7908)
- LB3Decryptor.exe (PID: 472)
Reads the software policy settings
- slui.exe (PID: 3884)
Creates files or folders in the user directory
- WerFault.exe (PID: 7732)
- LB3.exe (PID: 7564)
Reads the machine GUID from the registry
- LB3.exe (PID: 8116)
Creates files in the program directory
- LB3.exe (PID: 7564)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 8088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jpg | | | JFIF JPEG bitmap (50) |
|---|---|---|
| .jpg | | | JPEG bitmap (37.4) |
| .mp3 | | | MP3 audio (12.4) |
EXIF
JFIF
| JFIFVersion: | 1.01 |
|---|---|
| ResolutionUnit: | inches |
| XResolution: | 120 |
| YResolution: | 120 |
Composite
| ImageSize: | 640x480 |
|---|---|
| Megapixels: | 0.307 |
Total processes
174
Monitored processes
37
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
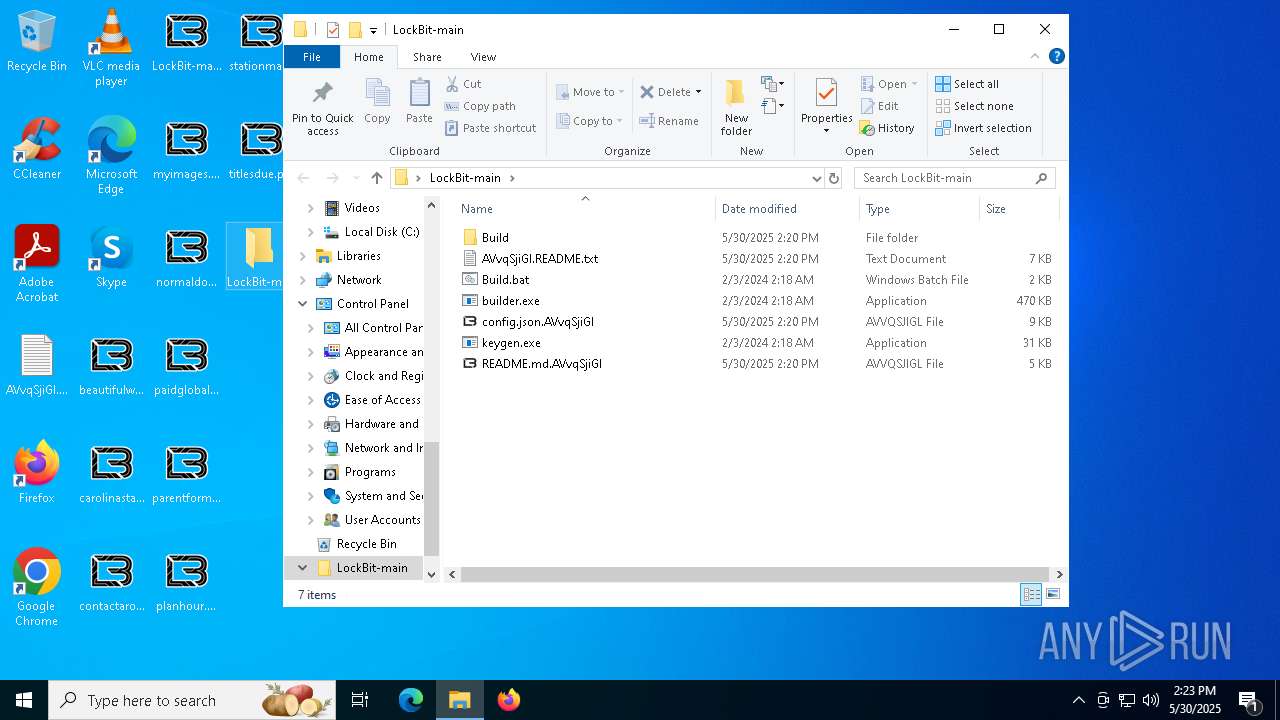
| 472 | "C:\Users\admin\Desktop\LockBit-main\Build\LB3Decryptor.exe" | C:\Users\admin\Desktop\LockBit-main\Build\LB3Decryptor.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
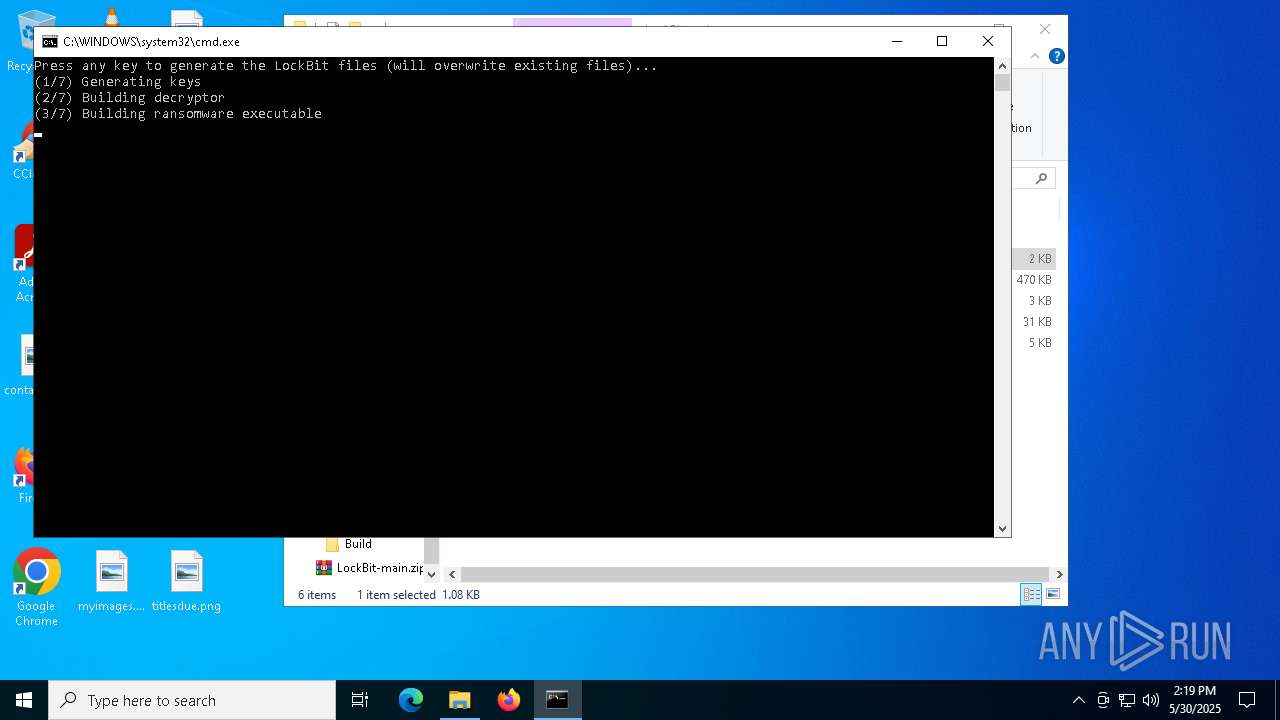
| 720 | builder -type enc -ref -pubkey Build\pub.key -config config.json -ofile Build\LB3_ReflectiveDll_DllMain.dll | C:\Users\admin\Desktop\LockBit-main\builder.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1116 | "C:\Users\admin\Desktop\LockBit-main\Build\LB3_pass.exe" | C:\Users\admin\Desktop\LockBit-main\Build\LB3_pass.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 1568 | builder -type enc -exe -pass -pubkey Build\pub.key -config config.json -ofile Build\LB3_pass.exe | C:\Users\admin\Desktop\LockBit-main\builder.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1748 | C:\WINDOWS\splwow64.exe 12288 | C:\Windows\splwow64.exe | — | LB3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2064 | builder -type enc -exe -pubkey Build\pub.key -config config.json -ofile Build\LB3.exe | C:\Users\admin\Desktop\LockBit-main\builder.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2320 | keygen -path Build -pubkey pub.key -privkey priv.key | C:\Users\admin\Desktop\LockBit-main\keygen.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2404 | "C:\ProgramData\5C3F.tmp" | C:\ProgramData\5C3F.tmp | LB3.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2596 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\AppData\Local\Temp\5-27-2025_1-09_35323.jpg | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3676 | C:\WINDOWS\system32\printfilterpipelinesvc.exe -Embedding | C:\Windows\System32\printfilterpipelinesvc.exe | — | svchost.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Print Filter Pipeline Host Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 791
Read events
13 233
Write events
2 548
Delete events
10
Modification events
| (PID) Process: | (2596) rundll32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Photo Viewer\Viewer |
| Operation: | write | Name: | MainWndPos |
Value: 6000000033000000A00400007502000000000000 | |||
| (PID) Process: | (7264) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7264) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7264) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7264) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (8088) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (7652) ShellExperienceHost.exe | Key: | \REGISTRY\A\{eb5b25cb-d683-8921-36ff-f17d1be23cfd}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D0000001EF211F96DD1DB01 | |||
| (PID) Process: | (5112) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (5112) SearchApp.exe | Key: | \REGISTRY\A\{23e390d0-6b9c-a392-7bb5-da9029bd0dbe}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_USEREMAIL |
Value: 0000B9253D2F6ED1DB01 | |||
| (PID) Process: | (5112) SearchApp.exe | Key: | \REGISTRY\A\{23e390d0-6b9c-a392-7bb5-da9029bd0dbe}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPETEXT |
Value: 0000B9253D2F6ED1DB01 | |||
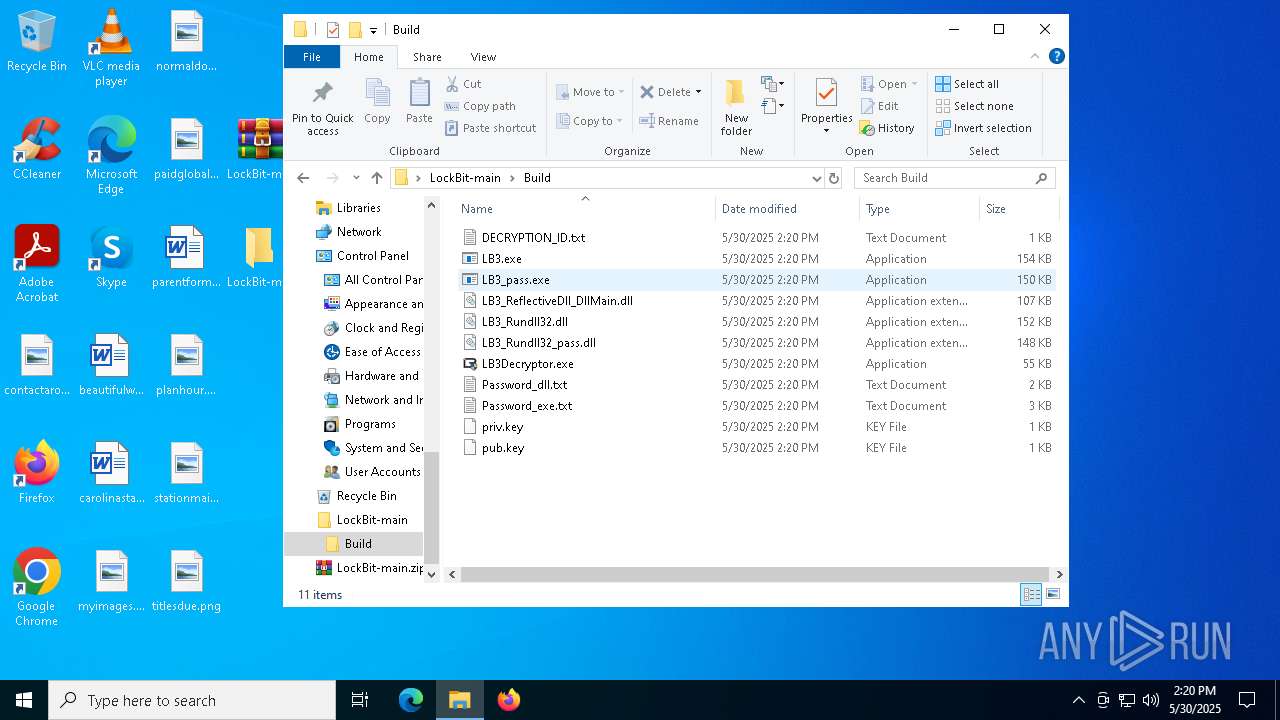
Executable files
10
Suspicious files
2 502
Text files
2 384
Unknown types
236
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7264 | WinRAR.exe | C:\Users\admin\Desktop\LockBit-main\builder.exe | executable | |
MD5:C2BC344F6DDE0573EA9ACDFB6698BF4C | SHA256:A736269F5F3A9F2E11DD776E352E1801BC28BB699E47876784B8EF761E0062DB | |||
| 7264 | WinRAR.exe | C:\Users\admin\Desktop\LockBit-main\keygen.exe | executable | |
MD5:71C3B2F765B04D0B7EA0328F6CE0C4E2 | SHA256:EA6D4DEDD8C85E4A6BB60408A0DC1D56DEF1F4AD4F069C730DC5431B1C23DA37 | |||
| 7264 | WinRAR.exe | C:\Users\admin\Desktop\LockBit-main\Build.bat | text | |
MD5:B8F24EFD1D30AAC9D360DB90C8717AEE | SHA256:95DF1D82137315708931F1FC3411E891CD42D1CAB413D4380B479788729248ED | |||
| 7732 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_LB3_pass.exe_2b4a443d98d2ecb187ae8a96695a6579a8b0907a_d9cc3852_e0b74572-d523-4f59-9fed-faf06a7f9295\Report.wer | — | |
MD5:— | SHA256:— | |||
| 8096 | keygen.exe | C:\Users\admin\Desktop\LockBit-main\Build\priv.key | text | |
MD5:9F586638E28533DE38AC914871C90780 | SHA256:92A986A5E8A89E9253452CDC0AA3AAEA5493E1615B3784E158EC2BF48762AC28 | |||
| 7608 | builder.exe | C:\Users\admin\Desktop\LockBit-main\Build\LB3_pass.exe | executable | |
MD5:D051F0D9068B9ACFEE1644E4ABD5D164 | SHA256:AEBD97AD80E7540BD9D1F9DE0700EED1355E1948F510B3A44A5CDEE3B1F14DC5 | |||
| 7928 | builder.exe | C:\Users\admin\Desktop\LockBit-main\Build\LB3Decryptor.exe | executable | |
MD5:E3265AD092FF6C6ADBDCC7404FC2F0D7 | SHA256:6AB34E9DAE405BC6753E2000F4110F53D24F0BDE9A9E45FDD5F8BD347B098126 | |||
| 8096 | keygen.exe | C:\Users\admin\Desktop\LockBit-main\Build\DECRYPTION_ID.txt | text | |
MD5:CA3833E86675807C9536BC69FB762857 | SHA256:AE1450A92728E653CE5B74B59A5BB8AE04108E839FEA3CF1A3788581A7F781A3 | |||
| 7608 | builder.exe | C:\Users\admin\Desktop\LockBit-main\Build\Password_exe.txt | text | |
MD5:56A52A127EA63AB6B54CB4BBF17F064D | SHA256:5C65F715A7B408FE4EDC960A7AFAA551A3FA06D11523237E791194C763A81EA6 | |||
| 7584 | builder.exe | C:\Users\admin\Desktop\LockBit-main\Build\LB3.exe | executable | |
MD5:8A596C84DA944DDC9BFBA1DF3AF44E87 | SHA256:2C64E1CF7F93BFA9B1351CF9E7EAF28F75C73B3B5019115561C2947D3466B247 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
29
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
960 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
960 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5112 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7920 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
960 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
960 | SIHClient.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
960 | SIHClient.exe | 13.85.23.206:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |