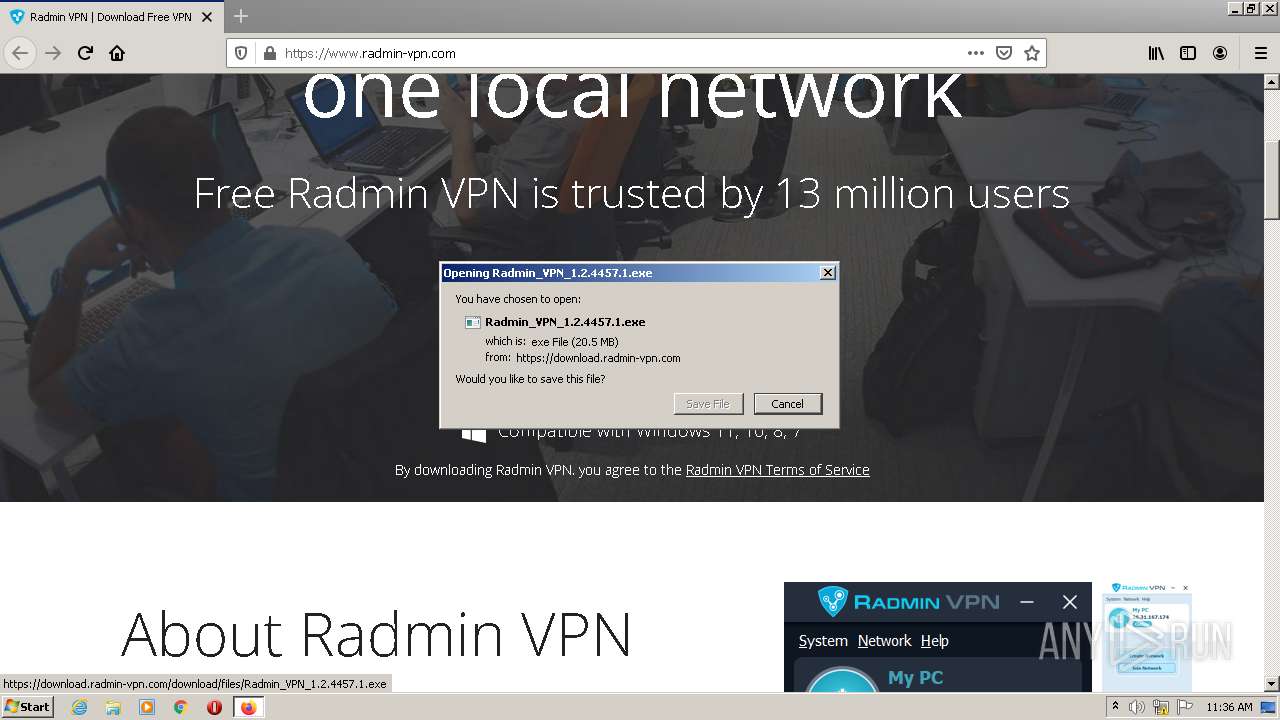
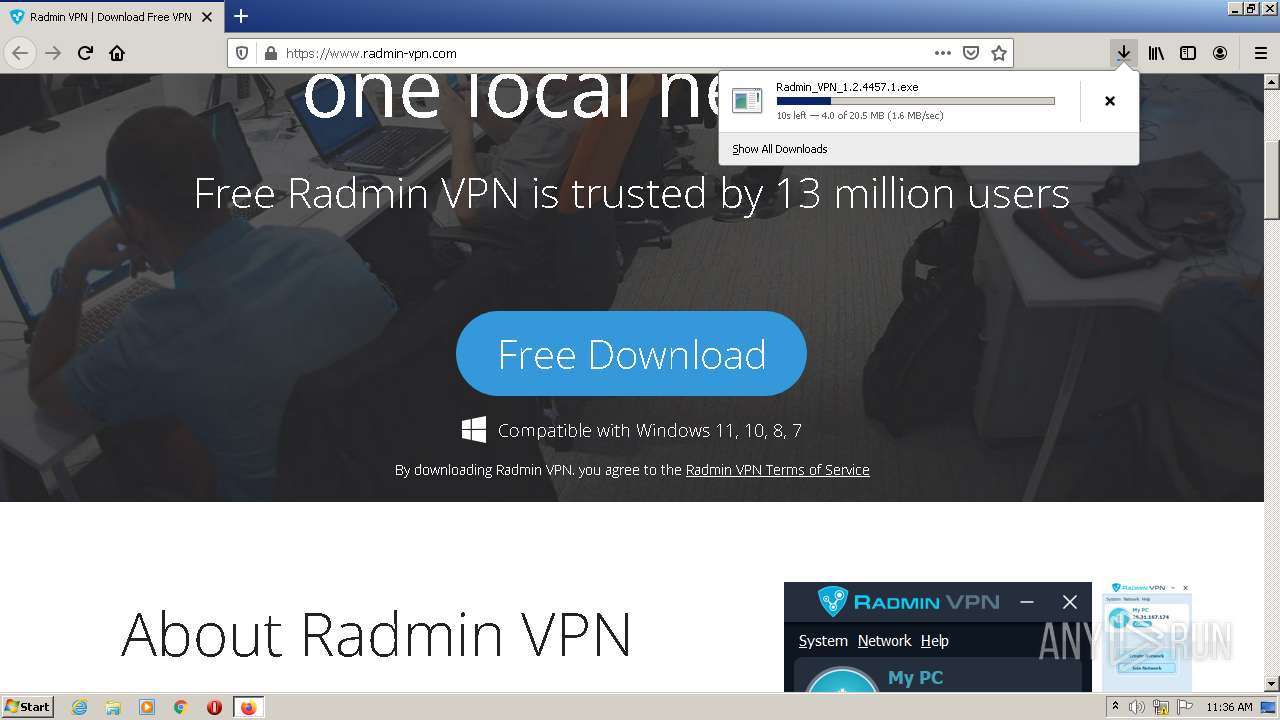
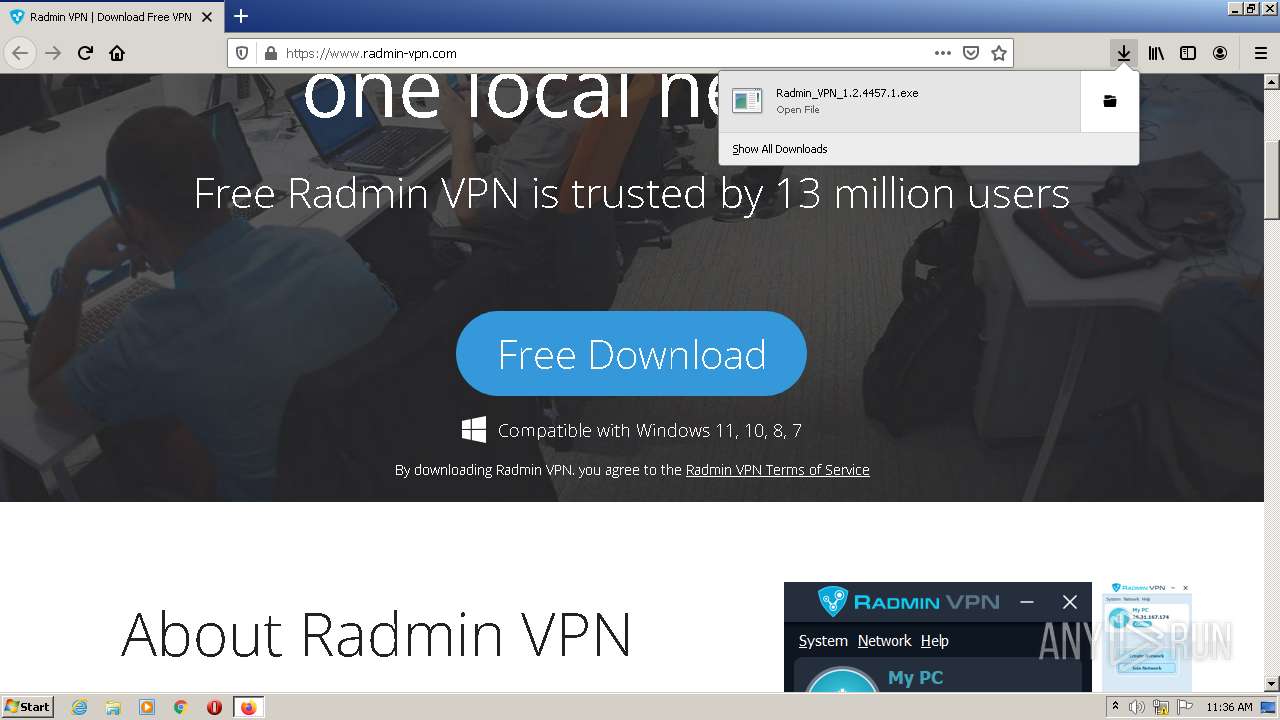
| URL: | https://www.radmin-vpn.com/ |
| Full analysis: | https://app.any.run/tasks/c7d9c971-d95b-4b91-bd3d-01566fbc19df |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 10:36:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 44E57FB422BB4F974863C49AB77EC5EF |
| SHA1: | 7F77A55F800263C5AD694A81A6D7B070141A742F |
| SHA256: | 643949A5B28A0DE47985C225C923FF4C3B62A6B7B62169B32799B9124C8DABE0 |
| SSDEEP: | 3:N8DSLU+TZSK:2OLUIZ5 |
MALICIOUS
Application was dropped or rewritten from another process
- Radmin_VPN_1.2.4457.1.exe (PID: 1588)
- Radmin_VPN_1.2.4457.1.exe (PID: 3496)
- RvControlSvc.exe (PID: 3396)
- RvRvpnGui.exe (PID: 2284)
Drops executable file immediately after starts
- firefox.exe (PID: 3216)
- Radmin_VPN_1.2.4457.1.exe (PID: 1588)
- Radmin_VPN_1.2.4457.1.exe (PID: 3496)
- Radmin_VPN_1.2.4457.1.tmp (PID: 3972)
- MSI4545.tmp (PID: 2512)
- msiexec.exe (PID: 2376)
- DrvInst.exe (PID: 3872)
- DrvInst.exe (PID: 2712)
Changes settings of System certificates
- msiexec.exe (PID: 2376)
Changes the autorun value in the registry
- DrvInst.exe (PID: 2712)
- RvControlSvc.exe (PID: 3396)
Loads dropped or rewritten executable
- RvControlSvc.exe (PID: 3396)
- RvRvpnGui.exe (PID: 2284)
SUSPICIOUS
Executable content was dropped or overwritten
- firefox.exe (PID: 3216)
- Radmin_VPN_1.2.4457.1.exe (PID: 1588)
- Radmin_VPN_1.2.4457.1.exe (PID: 3496)
- Radmin_VPN_1.2.4457.1.tmp (PID: 3972)
- MSI4545.tmp (PID: 2512)
- msiexec.exe (PID: 2376)
- DrvInst.exe (PID: 3872)
- DrvInst.exe (PID: 2712)
Checks supported languages
- Radmin_VPN_1.2.4457.1.exe (PID: 1588)
- Radmin_VPN_1.2.4457.1.tmp (PID: 2300)
- Radmin_VPN_1.2.4457.1.exe (PID: 3496)
- Radmin_VPN_1.2.4457.1.tmp (PID: 3972)
- msiexec.exe (PID: 2376)
- MsiExec.exe (PID: 3332)
- MSI4545.tmp (PID: 2512)
- DrvInst.exe (PID: 3872)
- DrvInst.exe (PID: 2712)
- MsiExec.exe (PID: 2724)
- RvControlSvc.exe (PID: 3396)
- RvRvpnGui.exe (PID: 2284)
Drops a file with a compile date too recent
- firefox.exe (PID: 3216)
- Radmin_VPN_1.2.4457.1.exe (PID: 1588)
- Radmin_VPN_1.2.4457.1.exe (PID: 3496)
- Radmin_VPN_1.2.4457.1.tmp (PID: 3972)
- MSI4545.tmp (PID: 2512)
- msiexec.exe (PID: 2376)
- DrvInst.exe (PID: 3872)
- DrvInst.exe (PID: 2712)
Reads the computer name
- Radmin_VPN_1.2.4457.1.tmp (PID: 2300)
- Radmin_VPN_1.2.4457.1.tmp (PID: 3972)
- msiexec.exe (PID: 2376)
- MsiExec.exe (PID: 3332)
- MSI4545.tmp (PID: 2512)
- DrvInst.exe (PID: 3872)
- DrvInst.exe (PID: 2712)
- MsiExec.exe (PID: 2724)
- RvRvpnGui.exe (PID: 2284)
- RvControlSvc.exe (PID: 3396)
Reads Windows owner or organization settings
- Radmin_VPN_1.2.4457.1.tmp (PID: 3972)
- msiexec.exe (PID: 2376)
Reads the Windows organization settings
- Radmin_VPN_1.2.4457.1.tmp (PID: 3972)
- msiexec.exe (PID: 2376)
Adds / modifies Windows certificates
- msiexec.exe (PID: 2376)
Creates a directory in Program Files
- msiexec.exe (PID: 2376)
Changes the autorun value in the registry
- msiexec.exe (PID: 2376)
Executed via COM
- DrvInst.exe (PID: 3872)
- DrvInst.exe (PID: 2712)
Removes files from Windows directory
- DrvInst.exe (PID: 3872)
- DrvInst.exe (PID: 2712)
Creates files in the Windows directory
- DrvInst.exe (PID: 3872)
- DrvInst.exe (PID: 2712)
Creates files in the driver directory
- DrvInst.exe (PID: 2712)
- DrvInst.exe (PID: 3872)
Reads Environment values
- DrvInst.exe (PID: 2712)
- netsh.exe (PID: 3512)
- netsh.exe (PID: 880)
- netsh.exe (PID: 2608)
- netsh.exe (PID: 1852)
- netsh.exe (PID: 1220)
- netsh.exe (PID: 3048)
- netsh.exe (PID: 2704)
- netsh.exe (PID: 2620)
- netsh.exe (PID: 2752)
- netsh.exe (PID: 1740)
Creates or modifies windows services
- DrvInst.exe (PID: 2712)
Uses NETSH.EXE for network configuration
- MsiExec.exe (PID: 2724)
- RvControlSvc.exe (PID: 3396)
Executed as Windows Service
- RvControlSvc.exe (PID: 3396)
Creates files in the program directory
- RvControlSvc.exe (PID: 3396)
INFO
Checks supported languages
- firefox.exe (PID: 1636)
- firefox.exe (PID: 2796)
- firefox.exe (PID: 3568)
- firefox.exe (PID: 2424)
- firefox.exe (PID: 964)
- firefox.exe (PID: 1276)
- firefox.exe (PID: 2120)
- firefox.exe (PID: 3216)
- netsh.exe (PID: 880)
- netsh.exe (PID: 3512)
- netsh.exe (PID: 2608)
- netsh.exe (PID: 2620)
- netsh.exe (PID: 1220)
- netsh.exe (PID: 3048)
- netsh.exe (PID: 2704)
- netsh.exe (PID: 1852)
- netsh.exe (PID: 2752)
- netsh.exe (PID: 1740)
Reads the computer name
- firefox.exe (PID: 3216)
- firefox.exe (PID: 1276)
- firefox.exe (PID: 3568)
- firefox.exe (PID: 2120)
- firefox.exe (PID: 964)
- firefox.exe (PID: 2796)
- firefox.exe (PID: 2424)
- netsh.exe (PID: 3512)
- netsh.exe (PID: 880)
- netsh.exe (PID: 2608)
- netsh.exe (PID: 1220)
- netsh.exe (PID: 1852)
- netsh.exe (PID: 3048)
- netsh.exe (PID: 2704)
- netsh.exe (PID: 2620)
- netsh.exe (PID: 2752)
- netsh.exe (PID: 1740)
Application launched itself
- firefox.exe (PID: 1636)
- firefox.exe (PID: 3216)
- msiexec.exe (PID: 2376)
Reads CPU info
- firefox.exe (PID: 3216)
Creates files in the program directory
- firefox.exe (PID: 3216)
- msiexec.exe (PID: 2376)
Dropped object may contain Bitcoin addresses
- firefox.exe (PID: 3216)
- msiexec.exe (PID: 2376)
Reads settings of System Certificates
- firefox.exe (PID: 3216)
- msiexec.exe (PID: 2376)
- MSI4545.tmp (PID: 2512)
- DrvInst.exe (PID: 3872)
- DrvInst.exe (PID: 2712)
Checks Windows Trust Settings
- firefox.exe (PID: 3216)
- msiexec.exe (PID: 2376)
- MSI4545.tmp (PID: 2512)
- DrvInst.exe (PID: 3872)
- DrvInst.exe (PID: 2712)
Application was dropped or rewritten from another process
- Radmin_VPN_1.2.4457.1.tmp (PID: 2300)
- Radmin_VPN_1.2.4457.1.tmp (PID: 3972)
- MSI4545.tmp (PID: 2512)
Creates files in the user directory
- firefox.exe (PID: 3216)
Loads dropped or rewritten executable
- Radmin_VPN_1.2.4457.1.tmp (PID: 3972)
Starts application with an unusual extension
- msiexec.exe (PID: 2376)
Creates a software uninstall entry
- msiexec.exe (PID: 2376)
Manual execution by user
- RvRvpnGui.exe (PID: 2284)
Reads the date of Windows installation
- firefox.exe (PID: 3216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
80
Monitored processes
30
Malicious processes
10
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 880 | netsh advfirewall firewall add rule name="Radmin VPN icmpv4" action=allow enable=yes dir=in profile=any remoteip=26.0.0.0/8 protocol=icmpv4 | C:\Windows\system32\netsh.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 964 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3216.34.1404928775\322574355" -childID 5 -isForBrowser -prefsHandle 4052 -prefMapHandle 4048 -prefsLen 7470 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3216 "\\.\pipe\gecko-crash-server-pipe.3216" 4064 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1220 | C:\Windows\system32\netsh.exe interface set interface "Radmin VPN" ENABLE | C:\Windows\system32\netsh.exe | — | RvControlSvc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1276 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3216.0.1238467525\1538231569" -parentBuildID 20201112153044 -prefsHandle 1104 -prefMapHandle 876 -prefsLen 1 -prefMapSize 238726 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3216 "\\.\pipe\gecko-crash-server-pipe.3216" 1200 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
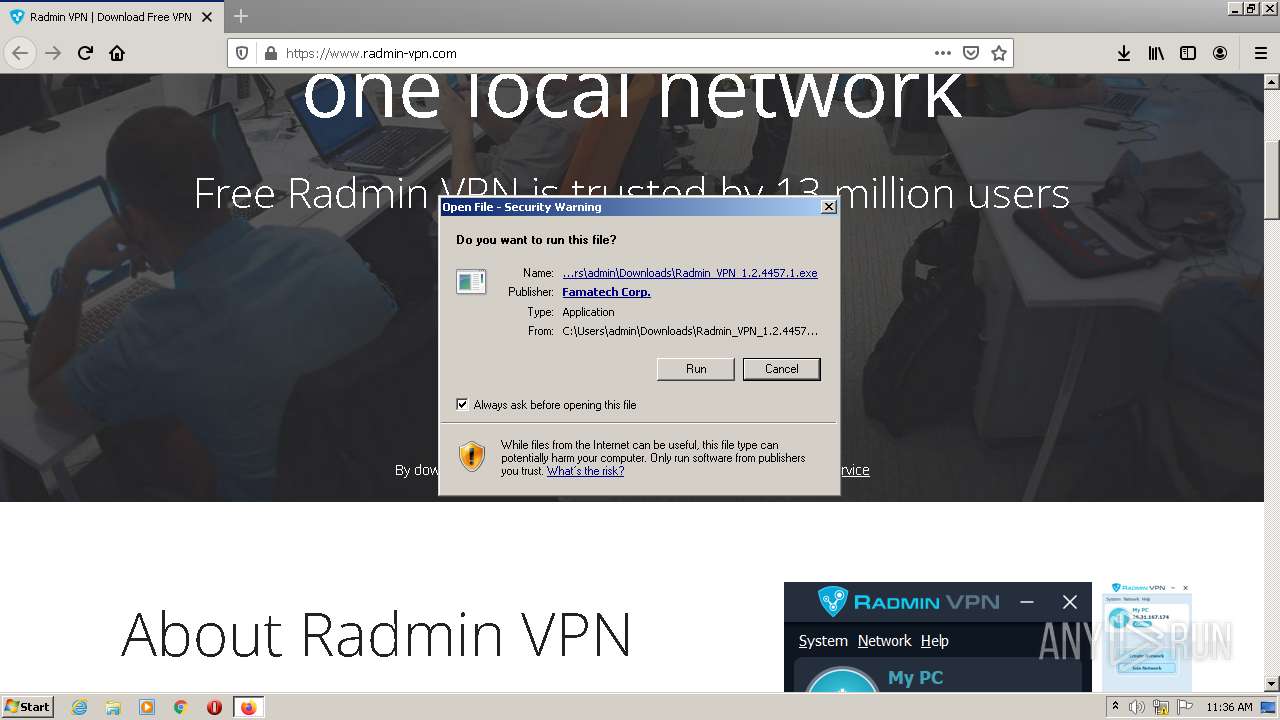
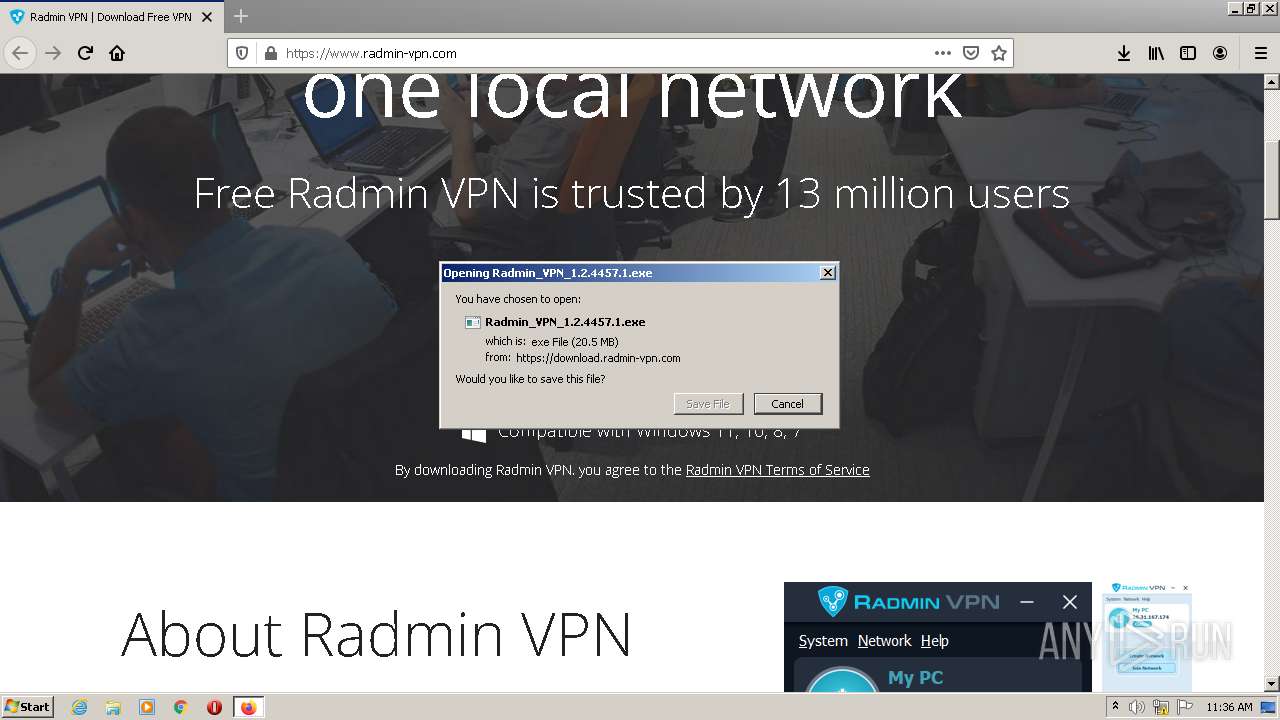
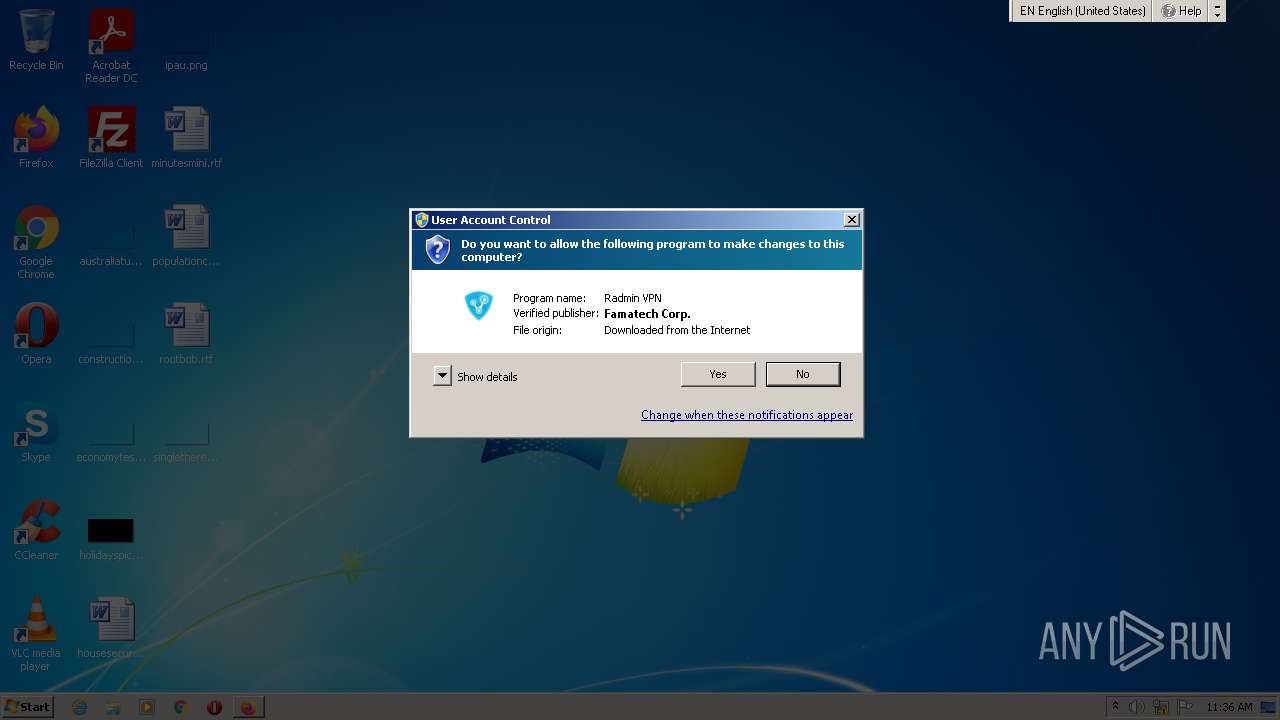
| 1588 | "C:\Users\admin\Downloads\Radmin_VPN_1.2.4457.1.exe" | C:\Users\admin\Downloads\Radmin_VPN_1.2.4457.1.exe | firefox.exe | ||||||||||||
User: admin Company: Famatech Corp. Integrity Level: MEDIUM Description: Radmin VPN Setup Exit code: 0 Version: 1.2.4457.1 Modules
| |||||||||||||||
| 1636 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://www.radmin-vpn.com/" | C:\Program Files\Mozilla Firefox\firefox.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 1740 | C:\Windows\system32\netsh.exe interface ipv6 add address interface="Radmin VPN" address=fdfd::1ab5:5027 | C:\Windows\system32\netsh.exe | — | RvControlSvc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1852 | C:\Windows\system32\netsh.exe interface ip delete route prefix=0.0.0.0/0 interface="Radmin VPN" nexthop=26.0.0.1 | C:\Windows\system32\netsh.exe | — | RvControlSvc.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3216.21.765057132\1818027163" -childID 4 -isForBrowser -prefsHandle 3796 -prefMapHandle 3804 -prefsLen 7470 -prefMapSize 238726 -parentBuildID 20201112153044 -appdir "C:\Program Files\Mozilla Firefox\browser" - 3216 "\\.\pipe\gecko-crash-server-pipe.3216" 3772 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 83.0 Modules
| |||||||||||||||
| 2284 | "C:\Program Files\Radmin VPN\RvRvpnGui.exe" /show | C:\Program Files\Radmin VPN\RvRvpnGui.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Famatech Corp. Integrity Level: MEDIUM Description: Radmin VPN Exit code: 0 Version: 1.2.4457.1 Modules
| |||||||||||||||
Total events
36 452
Read events
35 255
Write events
1 100
Delete events
97
Modification events
| (PID) Process: | (1636) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 9E1569ED8C000000 | |||
| (PID) Process: | (3216) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 9E1F69ED8C000000 | |||
| (PID) Process: | (3216) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (3216) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3216) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (3216) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (3216) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|ServicesSettingsServer |
Value: https://firefox.settings.services.mozilla.com/v1 | |||
| (PID) Process: | (3216) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SecurityContentSignatureRootHash |
Value: 97:E8:BA:9C:F1:2F:B3:DE:53:CC:42:A4:E6:57:7E:D6:4D:F4:93:C2:47:B4:14:FE:A0:36:81:8D:38:23:56:0E | |||
| (PID) Process: | (3216) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3216) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
120
Suspicious files
128
Text files
40
Unknown types
79
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3216 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3216 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 3216 | firefox.exe | C:\Users\admin\AppData\Local\Temp\mz_etilqs_GwvuhbT8ZFgrzpU | binary | |
MD5:— | SHA256:— | |||
| 3216 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-wal | binary | |
MD5:— | SHA256:— | |||
| 3216 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\places.sqlite-wal | sqlite-wal | |
MD5:— | SHA256:— | |||
| 3216 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\favicons.sqlite-wal | sqlite-wal | |
MD5:— | SHA256:— | |||
| 3216 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3216 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3216 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:994A33896BB41A278A315D0D796422B6 | SHA256:54EC50A20FFF8CC016710E49437CF6A11D3FE5EE7B28C185E4A9AAFEE2908B63 | |||
| 3216 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:299A2B747C11E4BDA194E563FEA4A699 | SHA256:94EE461F62E8B4A0A65471A41E10C8C56722B73C0A019D76ACA7F5BAF109813E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
40
DNS requests
110
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3216 | firefox.exe | POST | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
3216 | firefox.exe | POST | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
3216 | firefox.exe | POST | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
3216 | firefox.exe | POST | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
3216 | firefox.exe | POST | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
3216 | firefox.exe | POST | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
3216 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3216 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3216 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3216 | firefox.exe | POST | 200 | 142.250.185.227:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3216 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | — | US | whitelisted |
3216 | firefox.exe | 188.40.30.100:443 | www.radmin-vpn.com | Hetzner Online GmbH | DE | suspicious |
3216 | firefox.exe | 143.204.89.95:443 | firefox.settings.services.mozilla.com | — | US | suspicious |
3216 | firefox.exe | 142.250.185.104:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
3216 | firefox.exe | 142.250.185.227:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3216 | firefox.exe | 172.217.23.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3216 | firefox.exe | 142.250.179.138:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3216 | firefox.exe | 142.250.185.202:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
3216 | firefox.exe | 172.217.16.142:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
3216 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
www.radmin-vpn.com |
| suspicious |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
radmin-vpn.com |
| suspicious |
firefox.settings.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
location.services.mozilla.com |
| whitelisted |
locprod2-elb-us-west-2.prod.mozaws.net |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3216 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3216 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3216 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3216 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3216 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3216 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3216 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3216 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3216 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3216 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |