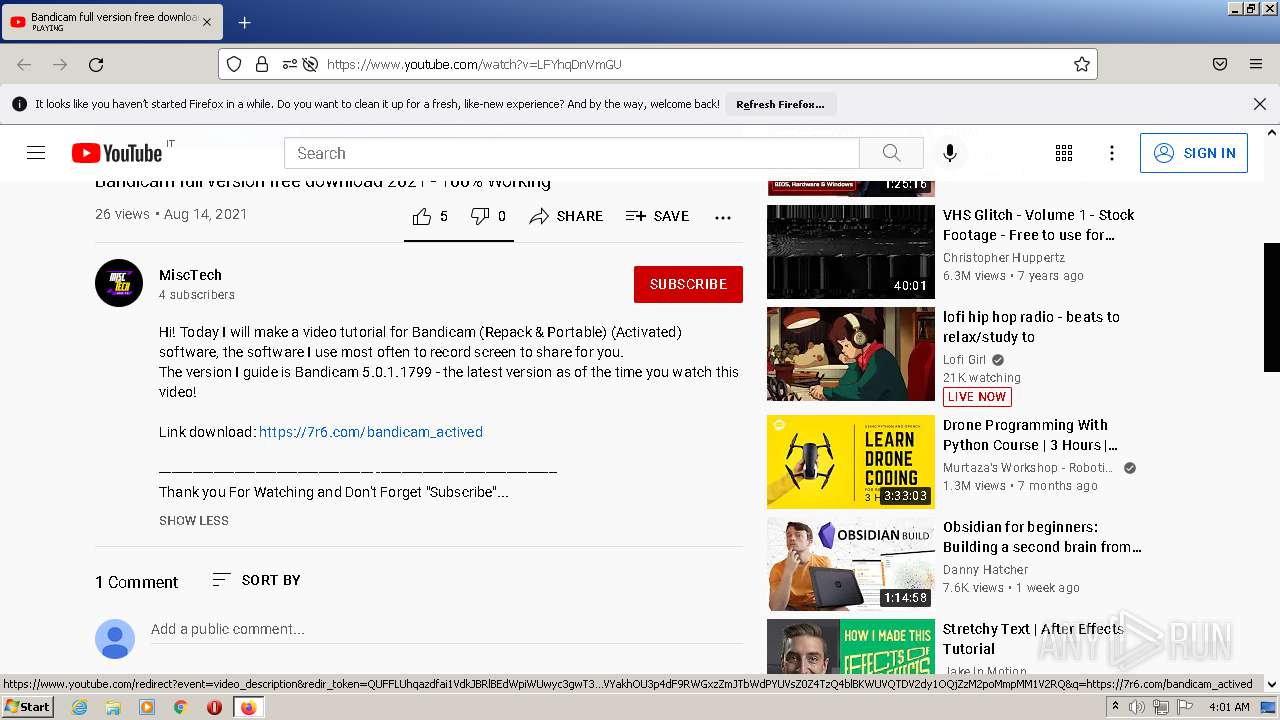
| URL: | https://www.youtube.com/watch?v=LFYhqDnVmGU |
| Full analysis: | https://app.any.run/tasks/1d1ffd2e-c885-42c3-bc8e-5f44635933f8 |
| Verdict: | Malicious activity |
| Analysis date: | August 23, 2021, 03:00:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | D508CC6557B94B5B73ACBE24D8EC0368 |
| SHA1: | 6991682EA436FD456752B84A9E377CE51C812EE9 |
| SHA256: | 6436A96D7147B7641D740FEAD349AC1DB0BA182A53CF77D1678F466AACCF6B03 |
| SSDEEP: | 3:N8DSLUxGTKSEIYskn:2OLUxGF5YH |
MALICIOUS
Loads the Task Scheduler COM API
- firefox.exe (PID: 908)
- bdcam.exe (PID: 4016)
Drops executable file immediately after starts
- Bandicam 5.0.1.1799.exe (PID: 2680)
- Bandicam 5.0.1.1799.tmp (PID: 2756)
Application was dropped or rewritten from another process
- Bandicam 5.0.1.1799.exe (PID: 380)
- Bandicam 5.0.1.1799.exe (PID: 2680)
- bdcam.exe (PID: 4016)
- bdcam.exe (PID: 3064)
Registers / Runs the DLL via REGSVR32.EXE
- Bandicam 5.0.1.1799.tmp (PID: 2756)
Loads dropped or rewritten executable
- bdcam.exe (PID: 3064)
- rundll32.exe (PID: 3092)
- bdcam.exe (PID: 4016)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3928)
- Bandicam 5.0.1.1799.exe (PID: 2680)
- Bandicam 5.0.1.1799.tmp (PID: 2756)
- cmd.exe (PID: 996)
- cmd.exe (PID: 1760)
- bdcam.exe (PID: 3064)
- cmd.exe (PID: 2600)
- bdcam.exe (PID: 4016)
- bcact.exe (PID: 2968)
Drops a file with too old compile date
- WinRAR.exe (PID: 3928)
- Bandicam 5.0.1.1799.exe (PID: 2680)
- Bandicam 5.0.1.1799.tmp (PID: 2756)
Reads the computer name
- WinRAR.exe (PID: 3928)
- Bandicam 5.0.1.1799.tmp (PID: 2756)
- bdcam.exe (PID: 3064)
- bdcam.exe (PID: 4016)
Reads Windows owner or organization settings
- Bandicam 5.0.1.1799.tmp (PID: 2756)
Reads the Windows organization settings
- Bandicam 5.0.1.1799.tmp (PID: 2756)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3928)
- Bandicam 5.0.1.1799.exe (PID: 2680)
- Bandicam 5.0.1.1799.tmp (PID: 2756)
- firefox.exe (PID: 908)
Drops a file that was compiled in debug mode
- Bandicam 5.0.1.1799.tmp (PID: 2756)
- firefox.exe (PID: 908)
Creates a directory in Program Files
- Bandicam 5.0.1.1799.tmp (PID: 2756)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 1636)
Starts CMD.EXE for commands execution
- Bandicam 5.0.1.1799.tmp (PID: 2756)
- cmd.exe (PID: 996)
Application launched itself
- cmd.exe (PID: 996)
Creates files in the Windows directory
- Bandicam 5.0.1.1799.tmp (PID: 2756)
Uses RUNDLL32.EXE to load library
- bdcam.exe (PID: 3064)
Changes default file association
- bdcam.exe (PID: 3064)
Uses NETSH.EXE for network configuration
- Bandicam 5.0.1.1799.tmp (PID: 2756)
Starts Internet Explorer
- Bandicam 5.0.1.1799.tmp (PID: 2756)
Reads Environment values
- netsh.exe (PID: 3260)
- netsh.exe (PID: 3072)
- netsh.exe (PID: 3780)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1868)
Drops a file with a compile date too recent
- firefox.exe (PID: 908)
INFO
Checks supported languages
- firefox.exe (PID: 3820)
- firefox.exe (PID: 908)
- firefox.exe (PID: 3700)
- firefox.exe (PID: 3840)
- firefox.exe (PID: 3408)
- firefox.exe (PID: 2432)
- firefox.exe (PID: 2628)
- firefox.exe (PID: 2484)
- firefox.exe (PID: 2904)
- firefox.exe (PID: 1120)
- regsvr32.exe (PID: 1636)
- rundll32.exe (PID: 3092)
- regedit.exe (PID: 1272)
- netsh.exe (PID: 3260)
- iexplore.exe (PID: 1760)
- netsh.exe (PID: 3780)
- netsh.exe (PID: 3072)
- iexplore.exe (PID: 1868)
- firefox.exe (PID: 2320)
Reads the computer name
- firefox.exe (PID: 908)
- firefox.exe (PID: 3700)
- firefox.exe (PID: 3840)
- firefox.exe (PID: 2628)
- firefox.exe (PID: 3408)
- firefox.exe (PID: 2432)
- firefox.exe (PID: 2484)
- firefox.exe (PID: 1120)
- firefox.exe (PID: 2904)
- iexplore.exe (PID: 1760)
- netsh.exe (PID: 3780)
- netsh.exe (PID: 3072)
- iexplore.exe (PID: 1868)
- netsh.exe (PID: 3260)
- firefox.exe (PID: 2320)
Reads CPU info
- firefox.exe (PID: 908)
Application launched itself
- firefox.exe (PID: 3820)
- firefox.exe (PID: 908)
- iexplore.exe (PID: 1760)
Creates files in the program directory
- firefox.exe (PID: 908)
- Bandicam 5.0.1.1799.tmp (PID: 2756)
Checks Windows Trust Settings
- firefox.exe (PID: 908)
- iexplore.exe (PID: 1868)
- iexplore.exe (PID: 1760)
Reads the date of Windows installation
- firefox.exe (PID: 908)
Manual execution by user
- WinRAR.exe (PID: 3928)
Loads dropped or rewritten executable
- Bandicam 5.0.1.1799.tmp (PID: 2756)
Application was dropped or rewritten from another process
- Bandicam 5.0.1.1799.tmp (PID: 2756)
- bcact.exe (PID: 2968)
Creates a software uninstall entry
- Bandicam 5.0.1.1799.tmp (PID: 2756)
Creates files in the user directory
- firefox.exe (PID: 908)
- iexplore.exe (PID: 1868)
- iexplore.exe (PID: 1760)
Changes internet zones settings
- iexplore.exe (PID: 1760)
Reads internet explorer settings
- iexplore.exe (PID: 1868)
Reads settings of System Certificates
- iexplore.exe (PID: 1868)
- iexplore.exe (PID: 1760)
- firefox.exe (PID: 908)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1868)
- iexplore.exe (PID: 1760)
Changes settings of System certificates
- iexplore.exe (PID: 1868)
- iexplore.exe (PID: 1760)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 1868)
Reads the hosts file
- bdcam.exe (PID: 4016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
79
Monitored processes
29
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 380 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3928.47327\Bandicam 5.0.1.1799 (Repack & Portable) (Activated)\Bandicam 5.0.1.1799.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3928.47327\Bandicam 5.0.1.1799 (Repack & Portable) (Activated)\Bandicam 5.0.1.1799.exe | — | WinRAR.exe | |||||||||||
User: admin Company: lrepacks.ru Integrity Level: MEDIUM Description: Bandicam Setup Exit code: 3221226540 Version: 5.0.1.1799.0 Modules
| |||||||||||||||
| 908 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://www.youtube.com/watch?v=LFYhqDnVmGU | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 91.0 Modules
| |||||||||||||||
| 996 | "C:\Windows\system32\cmd.exe" /C "C:\Users\admin\AppData\Local\Temp\is-3IPDB.tmp\bcact.bat" | C:\Windows\system32\cmd.exe | — | Bandicam 5.0.1.1799.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1120 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="908.11.659895420\1153386713" -parentBuildID 20210804193234 -prefsHandle 3740 -prefMapHandle 3736 -prefsLen 5920 -prefMapSize 246031 -appdir "C:\Program Files\Mozilla Firefox\browser" - 908 "\\.\pipe\gecko-crash-server-pipe.908" 3980 d4969b8 rdd | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 91.0 Modules
| |||||||||||||||
| 1272 | "C:\Windows\regedit.exe" /S "C:\Users\admin\AppData\Local\Temp\Rar$EXa3928.47327\Bandicam 5.0.1.1799 (Repack & Portable) (Activated)\settings.reg" | C:\Windows\regedit.exe | Bandicam 5.0.1.1799.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1636 | "C:\Windows\system32\regsvr32.exe" /s "C:\Program Files\Bandicam\BandiMPEG1\bdfilters.dll" | C:\Windows\system32\regsvr32.exe | — | Bandicam 5.0.1.1799.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1760 | C:\Windows\system32\cmd.exe /S /D /c" echo bandicam@bandisoft.com // lrepacks.ru" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1760 | "C:\Program Files\Internet Explorer\iexplore.exe" http://lrepacks.ru/ | C:\Program Files\Internet Explorer\iexplore.exe | Bandicam 5.0.1.1799.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1868 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1760 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2320 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="908.18.1746149222\176019369" -childID 7 -isForBrowser -prefsHandle 7908 -prefMapHandle 1552 -prefsLen 8735 -prefMapSize 246031 -jsInit 928 285716 -parentBuildID 20210804193234 -appdir "C:\Program Files\Mozilla Firefox\browser" - 908 "\\.\pipe\gecko-crash-server-pipe.908" 3372 1543ae28 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 91.0 Modules
| |||||||||||||||
Total events
58 347
Read events
56 674
Write events
1 660
Delete events
13
Modification events
| (PID) Process: | (3820) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: DA31BCE304000000 | |||
| (PID) Process: | (908) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 923DBCE304000000 | |||
| (PID) Process: | (908) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (908) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (908) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (908) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (908) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (908) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (908) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|ServicesSettingsServer |
Value: https://firefox.settings.services.mozilla.com/v1 | |||
| (PID) Process: | (908) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SecurityContentSignatureRootHash |
Value: 97:E8:BA:9C:F1:2F:B3:DE:53:CC:42:A4:E6:57:7E:D6:4D:F4:93:C2:47:B4:14:FE:A0:36:81:8D:38:23:56:0E | |||
Executable files
46
Suspicious files
326
Text files
330
Unknown types
602
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 908 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 908 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:— | SHA256:— | |||
| 908 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | text | |
MD5:— | SHA256:— | |||
| 908 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-child-current.bin | binary | |
MD5:— | SHA256:— | |||
| 908 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:— | SHA256:— | |||
| 908 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\QLDYZ5~1.DEF\cert9.db | sqlite | |
MD5:— | SHA256:— | |||
| 908 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\protections.sqlite-journal | binary | |
MD5:— | SHA256:— | |||
| 908 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-wal | binary | |
MD5:— | SHA256:— | |||
| 908 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\QLDYZ5~1.DEF\cert9.db-journal | binary | |
MD5:— | SHA256:— | |||
| 908 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4 | jsonlz4 | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
95
TCP/UDP connections
362
DNS requests
651
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
908 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
908 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1o1core | US | der | 472 b | whitelisted |
908 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
908 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
908 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
908 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
908 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
908 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
908 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
908 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
908 | firefox.exe | 74.125.111.137:443 | r4---sn-4g5edn6k.googlevideo.com | Google Inc. | US | whitelisted |
908 | firefox.exe | 142.250.186.161:443 | yt3.ggpht.com | Google Inc. | US | whitelisted |
908 | firefox.exe | 142.250.184.196:443 | www.google.com | Google Inc. | US | whitelisted |
908 | firefox.exe | 142.250.185.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
908 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | — | US | whitelisted |
908 | firefox.exe | 142.250.185.238:443 | www.youtube.com | Google Inc. | US | whitelisted |
908 | firefox.exe | 142.250.186.35:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
908 | firefox.exe | 143.204.98.76:443 | firefox.settings.services.mozilla.com | — | US | suspicious |
908 | firefox.exe | 143.204.98.36:443 | content-signature-2.cdn.mozilla.net | — | US | suspicious |
908 | firefox.exe | 142.250.185.86:443 | i.ytimg.com | Google Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
www.youtube.com |
| whitelisted |
youtube-ui.l.google.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
pki-goog.l.google.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
content-signature-2.cdn.mozilla.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request On Non-Standard High Port) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request On Non-Standard High Port) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request On Non-Standard High Port) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request On Non-Standard High Port) |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
908 | firefox.exe | Generic Protocol Command Decode | SURICATA STREAM Last ACK with wrong seq |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1 ETPRO signatures available at the full report
Process | Message |
|---|---|
regedit.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|