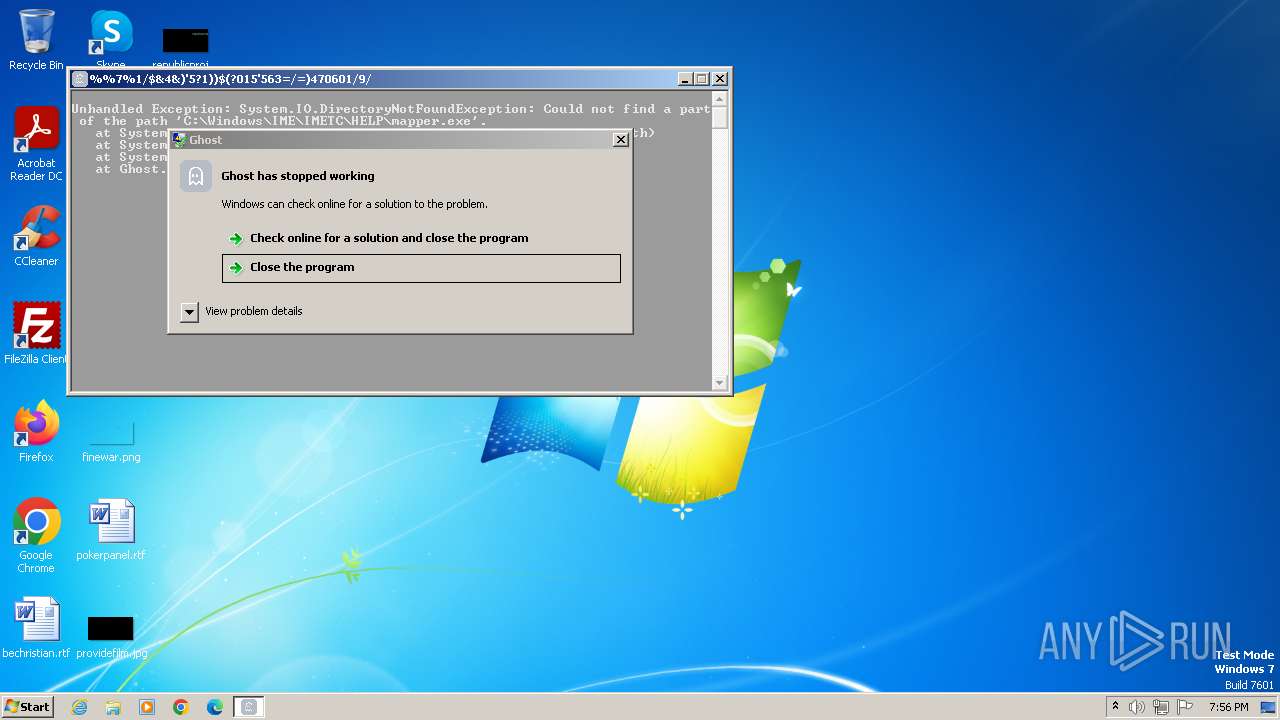
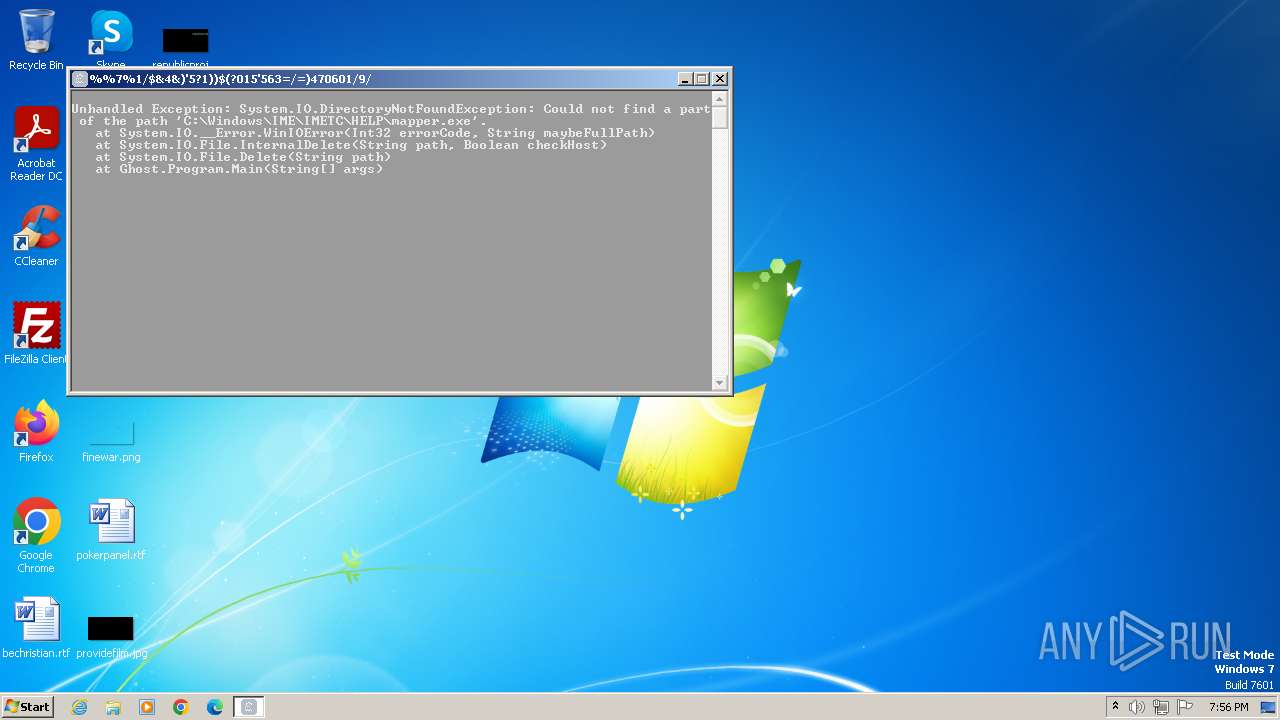
| File name: | Ghost.exe |
| Full analysis: | https://app.any.run/tasks/fe6b4f70-8c6d-456b-92fb-76ea4475d5ac |
| Verdict: | Malicious activity |
| Analysis date: | December 15, 2023, 19:55:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 89E686A70130B508B805ABCCF381CC4A |
| SHA1: | CC2D61D5680CD130A3E92E2B2D935B2B50F6B501 |
| SHA256: | 641F619327A221AC829A80C2100575C4C62B19B943028C2FA2304E4C5368AC64 |
| SSDEEP: | 768:86gtyTl6aQjsY2QDSi98bE9qOIrBG9/48ef6qTUtYcFA/Vc6K:8jysaQjsqmiqbQqOIrY9/7eCqTI8Vcl |
MALICIOUS
Actions looks like stealing of personal data
- CCleaner.exe (PID: 3936)
Drops the executable file immediately after the start
- CCleaner.exe (PID: 3936)
Steals credentials from Web Browsers
- CCleaner.exe (PID: 3936)
SUSPICIOUS
Reads settings of System Certificates
- Ghost.exe (PID: 2908)
- CCleaner.exe (PID: 3936)
Reads the Internet Settings
- Ghost.exe (PID: 2908)
- CCleaner.exe (PID: 1276)
- CCleaner.exe (PID: 3936)
Adds/modifies Windows certificates
- Ghost.exe (PID: 2908)
Application launched itself
- CCleaner.exe (PID: 1276)
Checks Windows Trust Settings
- CCleaner.exe (PID: 3936)
Reads Internet Explorer settings
- CCleaner.exe (PID: 3936)
Searches for installed software
- CCleaner.exe (PID: 3936)
Reads Microsoft Outlook installation path
- CCleaner.exe (PID: 3936)
Reads security settings of Internet Explorer
- CCleaner.exe (PID: 3936)
INFO
Reads Environment values
- Ghost.exe (PID: 2908)
- CCleaner.exe (PID: 1276)
- CCleaner.exe (PID: 3936)
Reads the computer name
- Ghost.exe (PID: 2908)
- wmpnscfg.exe (PID: 600)
- CCleaner.exe (PID: 1276)
- CCleaner.exe (PID: 3936)
Checks supported languages
- Ghost.exe (PID: 2908)
- wmpnscfg.exe (PID: 600)
- CCleaner.exe (PID: 1276)
- CCleaner.exe (PID: 3936)
Reads the machine GUID from the registry
- Ghost.exe (PID: 2908)
- CCleaner.exe (PID: 3936)
Manual execution by a user
- wmpnscfg.exe (PID: 600)
- CCleaner.exe (PID: 1276)
Reads CPU info
- CCleaner.exe (PID: 3936)
Reads product name
- CCleaner.exe (PID: 3936)
Creates files in the program directory
- CCleaner.exe (PID: 3936)
Creates files or folders in the user directory
- CCleaner.exe (PID: 3936)
Checks proxy server information
- CCleaner.exe (PID: 3936)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2048:10:25 11:12:47+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 33280 |
| InitializedDataSize: | 71168 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa002 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Ghost |
| FileVersion: | 1.0.0.0 |
| InternalName: | Ghost.exe |
| LegalCopyright: | Copyright © 2023 |
| LegalTrademarks: | - |
| OriginalFileName: | Ghost.exe |
| ProductName: | Ghost |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
51
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 600 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1276 | "C:\Program Files\CCleaner\CCleaner.exe" | C:\Program Files\CCleaner\CCleaner.exe | — | explorer.exe | |||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: MEDIUM Description: CCleaner Exit code: 0 Version: 6.14.0.10584 Modules
| |||||||||||||||
| 1996 | "C:\Users\admin\AppData\Local\Temp\Ghost.exe" | C:\Users\admin\AppData\Local\Temp\Ghost.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Ghost Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2908 | "C:\Users\admin\AppData\Local\Temp\Ghost.exe" | C:\Users\admin\AppData\Local\Temp\Ghost.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Ghost Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3936 | "C:\Program Files\CCleaner\CCleaner.exe" /uac | C:\Program Files\CCleaner\CCleaner.exe | CCleaner.exe | ||||||||||||
User: admin Company: Piriform Software Ltd Integrity Level: HIGH Description: CCleaner Exit code: 0 Version: 6.14.0.10584 Modules
| |||||||||||||||
Total events
17 969
Read events
17 789
Write events
130
Delete events
50
Modification events
| (PID) Process: | (2908) Ghost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2908) Ghost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\CABD2A79A1076A31F21D253635CB039D4329A5E8 |
| Operation: | write | Name: | Blob |
Value: 1900000001000000100000002FE1F70BB05D7C92335BC5E05B984DA662000000010000002000000096BCEC06264976F37460779ACF28C5A7CFE8A3C0AAE11A8FFCEE05C0BDDF08C60B000000010000001A0000004900530052004700200052006F006F007400200058003100000014000000010000001400000079B459E67BB6E5E40173800888C81A58F6E99B6E1D000000010000001000000073B6876195F5D18E048510422AEF04E309000000010000000C000000300A06082B06010505070301030000000100000014000000CABD2A79A1076A31F21D253635CB039D4329A5E80F00000001000000200000003F0411EDE9C4477057D57E57883B1F205B20CDC0F3263129B1EE0269A2678F6320000000010000006F0500003082056B30820353A0030201020211008210CFB0D240E3594463E0BB63828B00300D06092A864886F70D01010B0500304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F74205831301E170D3135303630343131303433385A170D3335303630343131303433385A304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F7420583130820222300D06092A864886F70D01010105000382020F003082020A0282020100ADE82473F41437F39B9E2B57281C87BEDCB7DF38908C6E3CE657A078F775C2A2FEF56A6EF6004F28DBDE68866C4493B6B163FD14126BBF1FD2EA319B217ED1333CBA48F5DD79DFB3B8FF12F1219A4BC18A8671694A66666C8F7E3C70BFAD292206F3E4C0E680AEE24B8FB7997E94039FD347977C99482353E838AE4F0A6F832ED149578C8074B6DA2FD0388D7B0370211B75F2303CFA8FAEDDDA63ABEB164FC28E114B7ECF0BE8FFB5772EF4B27B4AE04C12250C708D0329A0E15324EC13D9EE19BF10B34A8C3F89A36151DEAC870794F46371EC2EE26F5B9881E1895C34796C76EF3B906279E6DBA49A2F26C5D010E10EDED9108E16FBB7F7A8F7C7E50207988F360895E7E237960D36759EFB0E72B11D9BBC03F94905D881DD05B42AD641E9AC0176950A0FD8DFD5BD121F352F28176CD298C1A80964776E4737BACEAC595E689D7F72D689C50641293E593EDD26F524C911A75AA34C401F46A199B5A73A516E863B9E7D72A712057859ED3E5178150B038F8DD02F05B23E7B4A1C4B730512FCC6EAE050137C439374B3CA74E78E1F0108D030D45B7136B407BAC130305C48B7823B98A67D608AA2A32982CCBABD83041BA2830341A1D605F11BC2B6F0A87C863B46A8482A88DC769A76BF1F6AA53D198FEB38F364DEC82B0D0A28FFF7DBE21542D422D0275DE179FE18E77088AD4EE6D98B3AC6DD27516EFFBC64F533434F0203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041479B459E67BB6E5E40173800888C81A58F6E99B6E300D06092A864886F70D01010B05000382020100551F58A9BCB2A850D00CB1D81A6920272908AC61755C8A6EF882E5692FD5F6564BB9B8731059D321977EE74C71FBB2D260AD39A80BEA17215685F1500E59EBCEE059E9BAC915EF869D8F8480F6E4E99190DC179B621B45F06695D27C6FC2EA3BEF1FCFCBD6AE27F1A9B0C8AEFD7D7E9AFA2204EBFFD97FEA912B22B1170E8FF28A345B58D8FC01C954B9B826CC8A8833894C2D843C82DFEE965705BA2CBBF7C4B7C74E3B82BE31C822737392D1C280A43939103323824C3C9F86B255981DBE29868C229B9EE26B3B573A82704DDC09C789CB0A074D6CE85D8EC9EFCEABC7BBB52B4E45D64AD026CCE572CA086AA595E315A1F7A4EDC92C5FA5FBFFAC28022EBED77BBBE3717B9016D3075E46537C3707428CD3C4969CD599B52AE0951A8048AE4C3907CECC47A452952BBAB8FBADD233537DE51D4D6DD5A1B1C7426FE64027355CA328B7078DE78D3390E7239FFB509C796C46D5B415B3966E7E9B0C963AB8522D3FD65BE1FB08C284FE24A8A389DAAC6AE1182AB1A843615BD31FDC3B8D76F22DE88D75DF17336C3D53FB7BCB415FFFDCA2D06138E196B8AC5D8B37D775D533C09911AE9D41C1727584BE0241425F67244894D19B27BE073FB9B84F817451E17AB7ED9D23E2BEE0D52804133C31039EDD7A6C8FC60718C67FDE478E3F289E0406CFA5543477BDEC899BE91743DF5BDB5FFE8E1E57A2CD409D7E6222DADE1827 | |||
| (PID) Process: | (2908) Ghost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\CABD2A79A1076A31F21D253635CB039D4329A5E8 |
| Operation: | write | Name: | Blob |
Value: 0400000001000000100000000CD2F9E0DA1773E9ED864DA5E370E74E0F00000001000000200000003F0411EDE9C4477057D57E57883B1F205B20CDC0F3263129B1EE0269A2678F63030000000100000014000000CABD2A79A1076A31F21D253635CB039D4329A5E809000000010000000C000000300A06082B060105050703011D000000010000001000000073B6876195F5D18E048510422AEF04E314000000010000001400000079B459E67BB6E5E40173800888C81A58F6E99B6E0B000000010000001A0000004900530052004700200052006F006F007400200058003100000062000000010000002000000096BCEC06264976F37460779ACF28C5A7CFE8A3C0AAE11A8FFCEE05C0BDDF08C61900000001000000100000002FE1F70BB05D7C92335BC5E05B984DA620000000010000006F0500003082056B30820353A0030201020211008210CFB0D240E3594463E0BB63828B00300D06092A864886F70D01010B0500304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F74205831301E170D3135303630343131303433385A170D3335303630343131303433385A304F310B300906035504061302555331293027060355040A1320496E7465726E65742053656375726974792052657365617263682047726F7570311530130603550403130C4953524720526F6F7420583130820222300D06092A864886F70D01010105000382020F003082020A0282020100ADE82473F41437F39B9E2B57281C87BEDCB7DF38908C6E3CE657A078F775C2A2FEF56A6EF6004F28DBDE68866C4493B6B163FD14126BBF1FD2EA319B217ED1333CBA48F5DD79DFB3B8FF12F1219A4BC18A8671694A66666C8F7E3C70BFAD292206F3E4C0E680AEE24B8FB7997E94039FD347977C99482353E838AE4F0A6F832ED149578C8074B6DA2FD0388D7B0370211B75F2303CFA8FAEDDDA63ABEB164FC28E114B7ECF0BE8FFB5772EF4B27B4AE04C12250C708D0329A0E15324EC13D9EE19BF10B34A8C3F89A36151DEAC870794F46371EC2EE26F5B9881E1895C34796C76EF3B906279E6DBA49A2F26C5D010E10EDED9108E16FBB7F7A8F7C7E50207988F360895E7E237960D36759EFB0E72B11D9BBC03F94905D881DD05B42AD641E9AC0176950A0FD8DFD5BD121F352F28176CD298C1A80964776E4737BACEAC595E689D7F72D689C50641293E593EDD26F524C911A75AA34C401F46A199B5A73A516E863B9E7D72A712057859ED3E5178150B038F8DD02F05B23E7B4A1C4B730512FCC6EAE050137C439374B3CA74E78E1F0108D030D45B7136B407BAC130305C48B7823B98A67D608AA2A32982CCBABD83041BA2830341A1D605F11BC2B6F0A87C863B46A8482A88DC769A76BF1F6AA53D198FEB38F364DEC82B0D0A28FFF7DBE21542D422D0275DE179FE18E77088AD4EE6D98B3AC6DD27516EFFBC64F533434F0203010001A3423040300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF301D0603551D0E0416041479B459E67BB6E5E40173800888C81A58F6E99B6E300D06092A864886F70D01010B05000382020100551F58A9BCB2A850D00CB1D81A6920272908AC61755C8A6EF882E5692FD5F6564BB9B8731059D321977EE74C71FBB2D260AD39A80BEA17215685F1500E59EBCEE059E9BAC915EF869D8F8480F6E4E99190DC179B621B45F06695D27C6FC2EA3BEF1FCFCBD6AE27F1A9B0C8AEFD7D7E9AFA2204EBFFD97FEA912B22B1170E8FF28A345B58D8FC01C954B9B826CC8A8833894C2D843C82DFEE965705BA2CBBF7C4B7C74E3B82BE31C822737392D1C280A43939103323824C3C9F86B255981DBE29868C229B9EE26B3B573A82704DDC09C789CB0A074D6CE85D8EC9EFCEABC7BBB52B4E45D64AD026CCE572CA086AA595E315A1F7A4EDC92C5FA5FBFFAC28022EBED77BBBE3717B9016D3075E46537C3707428CD3C4969CD599B52AE0951A8048AE4C3907CECC47A452952BBAB8FBADD233537DE51D4D6DD5A1B1C7426FE64027355CA328B7078DE78D3390E7239FFB509C796C46D5B415B3966E7E9B0C963AB8522D3FD65BE1FB08C284FE24A8A389DAAC6AE1182AB1A843615BD31FDC3B8D76F22DE88D75DF17336C3D53FB7BCB415FFFDCA2D06138E196B8AC5D8B37D775D533C09911AE9D41C1727584BE0241425F67244894D19B27BE073FB9B84F817451E17AB7ED9D23E2BEE0D52804133C31039EDD7A6C8FC60718C67FDE478E3F289E0406CFA5543477BDEC899BE91743DF5BDB5FFE8E1E57A2CD409D7E6222DADE1827 | |||
| (PID) Process: | (1276) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1276) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1276) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1276) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3936) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | DAST |
Value: 07/06/2023 15:07:35 | |||
| (PID) Process: | (3936) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | T8062 |
Value: 1 | |||
| (PID) Process: | (3936) CCleaner.exe | Key: | HKEY_CURRENT_USER\Software\Piriform\CCleaner |
| Operation: | write | Name: | UpdateBackground |
Value: 0 | |||
Executable files
2
Suspicious files
25
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3936 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\HWBV2ADH3E6XY8NYQHME.temp | binary | |
MD5:ED3EB3ED7658E95312572C7B86324763 | SHA256:3B75DA9C34459406C0BCFEAFAA8DB3A152E61535EB10988C211ED782C69158A0 | |||
| 3936 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ed7a5cc3cca8d52a.customDestinations-ms | binary | |
MD5:ED3EB3ED7658E95312572C7B86324763 | SHA256:3B75DA9C34459406C0BCFEAFAA8DB3A152E61535EB10988C211ED782C69158A0 | |||
| 3936 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3936 | CCleaner.exe | C:\Program Files\CCleaner\gcapi_dll.dll | executable | |
MD5:F637D5D3C3A60FDDB5DD397556FE9B1D | SHA256:641B843CB6EE7538EC267212694C9EF0616B9AC9AB14A0ABD7CF020678D50B02 | |||
| 3936 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:72CFF64CB151783821F145F4CEBCCEB5 | SHA256:7DA264D43511334C645157E22B548DD518245C6750FB6A51B3DCEA08A19D3477 | |||
| 3936 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:9B9EC11FC5CBF962FBAC34E486F417A1 | SHA256:FD1BB8C704558BF9AB996E9CB1CD486E5373233D510A966F707CBEB05DEAA532 | |||
| 3936 | CCleaner.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\ed7a5cc3cca8d52a.customDestinations-ms~RF217f9f.TMP | binary | |
MD5:DA39F131D86385E1285BF5489BA6B6F9 | SHA256:38C92C3B93D15CCF2E5E59D01D223366D60FF508037EF997C0CDCC11CEC8BAD0 | |||
| 3936 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_45E3C223BCF135987E4038FB6B0DBA13 | binary | |
MD5:037AE8164352CA91E80AD33054D1906D | SHA256:07C018EB07002663D5248DAA8A65EAF587955E3DB45735E7E3AC9CB13D7D664E | |||
| 3936 | CCleaner.exe | C:\Program Files\CCleaner\gcapi_17026701933936.dll | executable | |
MD5:F637D5D3C3A60FDDB5DD397556FE9B1D | SHA256:641B843CB6EE7538EC267212694C9EF0616B9AC9AB14A0ABD7CF020678D50B02 | |||
| 3936 | CCleaner.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:0E69BA27F7378B985ABEBF42AF823480 | SHA256:25B3AC73DAED10516B68ED1C84D09AE4014306A68FBF4976DCFEC3A39E803398 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
25
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2908 | Ghost.exe | GET | — | 193.108.153.12:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?7457fdfdff5aa179 | unknown | — | — | unknown |
3936 | CCleaner.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?46869083e2ec8ec2 | unknown | compressed | 4.66 Kb | unknown |
3936 | CCleaner.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?dd353d0c0c5f7219 | unknown | compressed | 4.66 Kb | unknown |
3936 | CCleaner.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7bb8771517569d9f | unknown | compressed | 4.66 Kb | unknown |
3936 | CCleaner.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9f5a0b05808e23e5 | unknown | compressed | 4.66 Kb | unknown |
3936 | CCleaner.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3936 | CCleaner.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIAjrICMzZli2TN25s%3D | unknown | binary | 724 b | unknown |
3936 | CCleaner.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
3936 | CCleaner.exe | GET | 200 | 142.250.185.99:80 | http://ocsp.pki.goog/s/gts1d4/fKYaaVX9oaM/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEFR%2BOO9BG%2B3VCUfYZJRDCnY%3D | unknown | binary | 471 b | unknown |
3936 | CCleaner.exe | GET | 200 | 104.124.11.43:80 | http://ncc.avast.com/ncc.txt | unknown | text | 26 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2908 | Ghost.exe | 172.67.72.57:443 | keyauth.win | CLOUDFLARENET | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2908 | Ghost.exe | 193.108.153.12:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3936 | CCleaner.exe | 104.124.11.43:80 | ncc.avast.com | Akamai International B.V. | DE | unknown |
3936 | CCleaner.exe | 95.101.197.220:443 | www.ccleaner.com | Akamai International B.V. | NL | unknown |
3936 | CCleaner.exe | 34.160.176.28:443 | shepherd.ff.avast.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
keyauth.win |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ncc.avast.com |
| whitelisted |
analytics.ff.avast.com |
| whitelisted |
www.ccleaner.com |
| whitelisted |
ipm-provider.ff.avast.com |
| whitelisted |
shepherd.ff.avast.com |
| whitelisted |
ip-info.ff.avast.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
CCleaner.exe | [2023-12-15 19:56:32.777] [error ] [settings ] [ 3936: 3288] [6000C4: 356] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | Failed to open log file 'C:\Program Files\CCleaner' |
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | [2023-12-15 19:56:33.339] [error ] [settings ] [ 3936: 4044] [9434E9: 359] Failed to get program directory
Exception: Unable to determine program folder of product 'piriform-cc'!
Code: 0x000000c0 (192)
|
CCleaner.exe | [2023-12-15 19:56:33.355] [error ] [Burger ] [ 3936: 4044] [FDA25D: 244] [23.1.806.0] [BurgerReporter.cpp] [244] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner.exe | [2023-12-15 19:56:33.355] [error ] [Burger ] [ 3936: 4044] [FDA25D: 244] [23.1.806.0] [BurgerReporter.cpp] [244] asw::standalone_svc::BurgerReporter::BurgerSwitch: Could not read property BURGER_SETTINGS_PANCAKE_HOSTNAME (0x00000003)
|
CCleaner.exe | startCheckingLicense()
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | OnLanguage - en
|
CCleaner.exe | OnLanguage - en
|