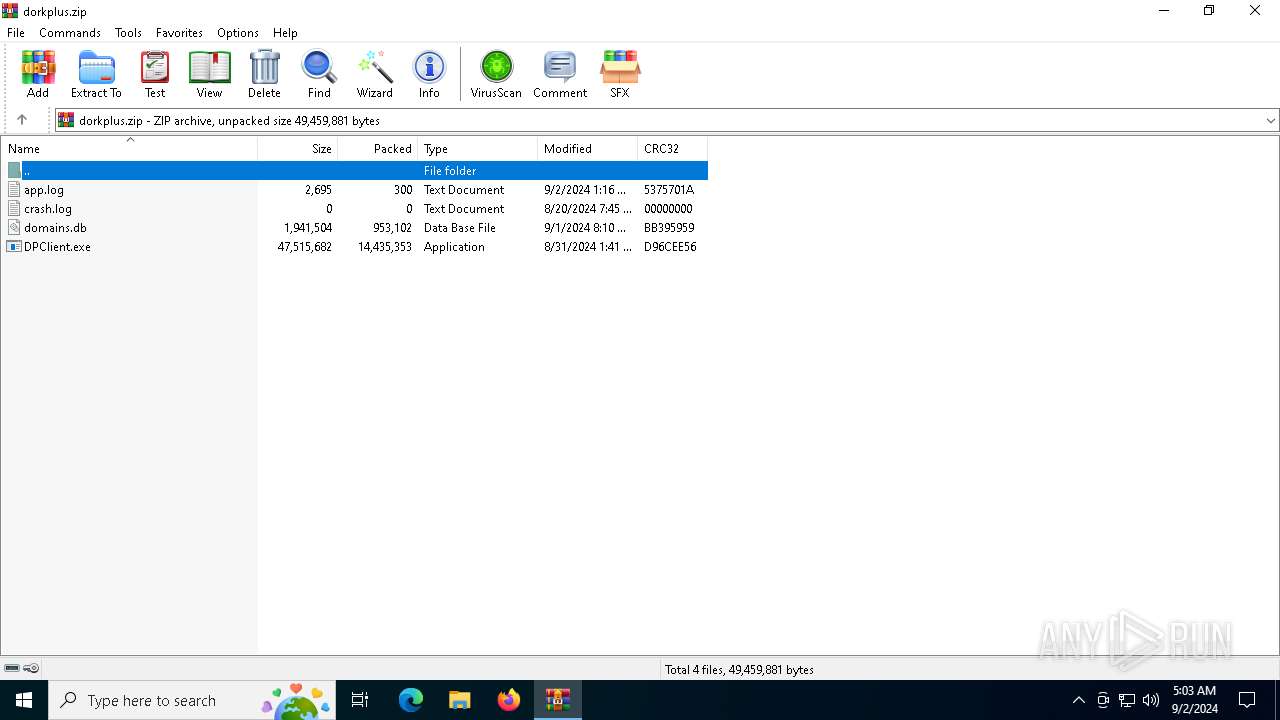
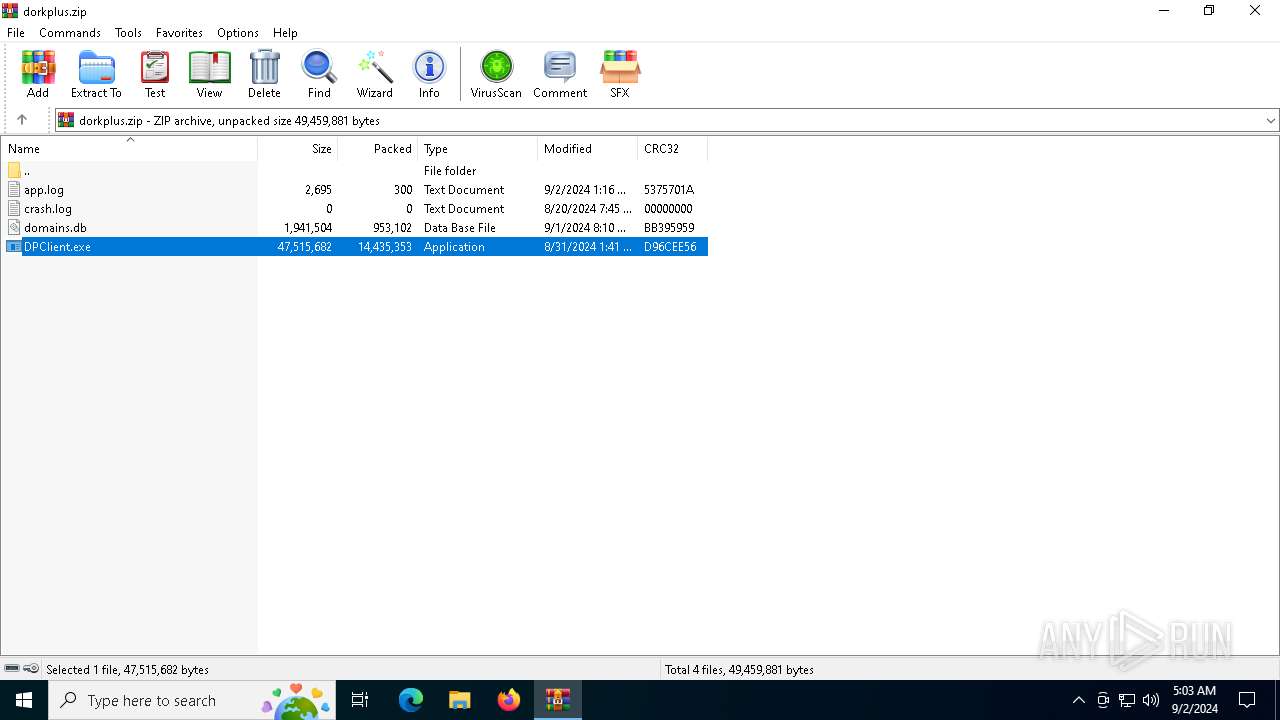
| File name: | dorkplus.zip |
| Full analysis: | https://app.any.run/tasks/dad81ca6-017c-43a9-ac51-ea9286b521bf |
| Verdict: | Malicious activity |
| Analysis date: | September 02, 2024, 05:03:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F27772112E6624BA667C7966AC9B7C17 |
| SHA1: | F38E6EB1A2761B45D197CE54BD4EE1F46ECEFE4C |
| SHA256: | 641F48B7F9B23D49C3AE86E047858CA127632B43E4FA9D0264BAB837AB43777C |
| SSDEEP: | 98304:27LoFP4ve9c93Je1UKQztKIGSwykCtFnaJyS3P2yvJLN/c5doHcJ2V1bcGWWaE1c:PH7N1ZAVnK+6FVkvTZwALdRto6P |
MALICIOUS
Changes the autorun value in the registry
- MicrosoftEdgeUpdate.exe (PID: 7080)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 508)
- MicrosoftEdgeUpdate.exe (PID: 7080)
Executable content was dropped or overwritten
- DPClient.exe (PID: 7028)
- MicrosoftEdgeWebview2Setup.exe (PID: 6984)
- MicrosoftEdgeUpdate.exe (PID: 7080)
Drops the executable file immediately after the start
- DPClient.exe (PID: 7028)
- MicrosoftEdgeWebview2Setup.exe (PID: 6984)
- MicrosoftEdgeUpdate.exe (PID: 7080)
Process drops legitimate windows executable
- DPClient.exe (PID: 7028)
- MicrosoftEdgeWebview2Setup.exe (PID: 6984)
- MicrosoftEdgeUpdate.exe (PID: 7080)
Starts a Microsoft application from unusual location
- MicrosoftEdgeWebview2Setup.exe (PID: 6984)
- MicrosoftEdgeUpdate.exe (PID: 7080)
Starts itself from another location
- MicrosoftEdgeUpdate.exe (PID: 7080)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdate.exe (PID: 4004)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2468)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 3028)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 368)
Reads the date of Windows installation
- MicrosoftEdgeUpdate.exe (PID: 7080)
Potential Corporate Privacy Violation
- svchost.exe (PID: 5284)
Found regular expressions for crypto-addresses (YARA)
- DPClient.exe (PID: 7028)
There is functionality for capture public ip (YARA)
- DPClient.exe (PID: 7028)
INFO
Reads the computer name
- DPClient.exe (PID: 7028)
- MicrosoftEdgeUpdate.exe (PID: 7080)
- MicrosoftEdgeUpdate.exe (PID: 4004)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2468)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 3028)
- MicrosoftEdgeUpdate.exe (PID: 6008)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 368)
- MicrosoftEdgeUpdate.exe (PID: 2384)
- MicrosoftEdgeUpdate.exe (PID: 3972)
Checks supported languages
- DPClient.exe (PID: 7028)
- MicrosoftEdgeWebview2Setup.exe (PID: 6984)
- MicrosoftEdgeUpdate.exe (PID: 7080)
- MicrosoftEdgeUpdate.exe (PID: 4004)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 2468)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 3028)
- MicrosoftEdgeUpdate.exe (PID: 3972)
- MicrosoftEdgeUpdate.exe (PID: 6008)
- MicrosoftEdgeUpdateComRegisterShell64.exe (PID: 368)
- MicrosoftEdgeUpdate.exe (PID: 2384)
The process uses the downloaded file
- WinRAR.exe (PID: 508)
Reads the machine GUID from the registry
- DPClient.exe (PID: 7028)
Reads Environment values
- DPClient.exe (PID: 7028)
- MicrosoftEdgeUpdate.exe (PID: 2384)
Create files in a temporary directory
- DPClient.exe (PID: 7028)
- MicrosoftEdgeWebview2Setup.exe (PID: 6984)
- MicrosoftEdgeUpdate.exe (PID: 7080)
- svchost.exe (PID: 5284)
Reads the software policy settings
- DPClient.exe (PID: 7028)
- MicrosoftEdgeUpdate.exe (PID: 2384)
- MicrosoftEdgeUpdate.exe (PID: 6008)
Creates files or folders in the user directory
- MicrosoftEdgeUpdate.exe (PID: 7080)
Checks proxy server information
- MicrosoftEdgeUpdate.exe (PID: 2384)
- MicrosoftEdgeUpdate.exe (PID: 6008)
Process checks computer location settings
- MicrosoftEdgeUpdate.exe (PID: 7080)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:09:02 04:16:10 |
| ZipCRC: | 0x5375701a |
| ZipCompressedSize: | 300 |
| ZipUncompressedSize: | 2695 |
| ZipFileName: | app.log |
Total processes
134
Monitored processes
13
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 368 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.15\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.15\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.15 Modules
| |||||||||||||||
| 508 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\dorkplus.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2384 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /ping PD94bWwgdmVyc2lvbj0iMS4wIiBlbmNvZGluZz0iVVRGLTgiPz48cmVxdWVzdCBwcm90b2NvbD0iMy4wIiB1cGRhdGVyPSJPbWFoYSIgdXBkYXRlcnZlcnNpb249IjEuMy4xOTUuMTUiIHNoZWxsX3ZlcnNpb249IjEuMy4xOTUuMTUiIGlzbWFjaGluZT0iMCIgc2Vzc2lvbmlkPSJ7NTAyOUQ3MzctMzRDNC00RDk2LUFEMzgtNUVBN0I4OTk5ODlDfSIgdXNlcmlkPSJ7OUEzODdDNEYtNDY1My00MkM5LUJGQTctOTMwMDk4MDFGMUQ5fSIgaW5zdGFsbHNvdXJjZT0idGFnZ2VkbWkiIHJlcXVlc3RpZD0iezE2NDNGRUNDLTI2NTMtNEQzMy1BQUM2LTY4REU5NEU0QjA1MH0iIGRlZHVwPSJjciIgZG9tYWluam9pbmVkPSIwIj48aHcgbG9naWNhbF9jcHVzPSI0IiBwaHlzbWVtb3J5PSI0IiBkaXNrX3R5cGU9IjIiIHNzZT0iMSIgc3NlMj0iMSIgc3NlMz0iMSIgc3NzZTM9IjEiIHNzZTQxPSIxIiBzc2U0Mj0iMSIgYXZ4PSIxIi8-PG9zIHBsYXRmb3JtPSJ3aW4iIHZlcnNpb249IjEwLjAuMTkwNDUuNDA0NiIgc3A9IiIgYXJjaD0ieDY0IiBwcm9kdWN0X3R5cGU9IjQ4IiBpc193aXA9IjAiIGlzX2luX2xvY2tkb3duX21vZGU9IjAiLz48b2VtIHByb2R1Y3RfbWFudWZhY3R1cmVyPSJERUxMIiBwcm9kdWN0X25hbWU9IkRFTEwiLz48ZXhwIGV0YWc9IiIvPjxhcHAgYXBwaWQ9IntGM0M0RkUwMC1FRkQ1LTQwM0ItOTU2OS0zOThBMjBGMUJBNEF9IiB2ZXJzaW9uPSIiIG5leHR2ZXJzaW9uPSIxLjMuMTk1LjE1IiBsYW5nPSIiIGJyYW5kPSIiIGNsaWVudD0iIj48ZXZlbnQgZXZlbnR0eXBlPSIyIiBldmVudHJlc3VsdD0iMSIgZXJyb3Jjb2RlPSIwIiBleHRyYWNvZGUxPSIwIiBzeXN0ZW1fdXB0aW1lX3RpY2tzPSIxMjM3Njc0MDc5NSIgaW5zdGFsbF90aW1lX21zPSI3MDQiLz48L2FwcD48L3JlcXVlc3Q- | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | MicrosoftEdgeUpdate.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.15 Modules
| |||||||||||||||
| 2468 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.15\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.15\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.15 Modules
| |||||||||||||||
| 3028 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.15\MicrosoftEdgeUpdateComRegisterShell64.exe" /user | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\1.3.195.15\MicrosoftEdgeUpdateComRegisterShell64.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update COM Registration Helper Exit code: 0 Version: 1.3.195.15 Modules
| |||||||||||||||
| 3972 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /handoff "appguid={F3017226-FE2A-4295-8BDF-00C3A9A7E4C5}&appname=Microsoft%20Edge%20Webview2%20Runtime&needsadmin=false" /installsource taggedmi /sessionid "{5029D737-34C4-4D96-AD38-5EA7B899989C}" | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.195.15 Modules
| |||||||||||||||
| 4004 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" /regserver | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | — | MicrosoftEdgeUpdate.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Exit code: 0 Version: 1.3.195.15 Modules
| |||||||||||||||
| 5284 | C:\WINDOWS\System32\svchost.exe -k netsvcs -p -s BITS | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5980 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | DPClient.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6008 | "C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe" -Embedding | C:\Users\admin\AppData\Local\Microsoft\EdgeUpdate\MicrosoftEdgeUpdate.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Update Version: 1.3.195.15 Modules
| |||||||||||||||
Total events
16 767
Read events
15 613
Write events
1 120
Delete events
34
Modification events
| (PID) Process: | (508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\dorkplus.zip | |||
| (PID) Process: | (508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (508) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
202
Suspicious files
1
Text files
4
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa508.22102\DPClient.exe | — | |
MD5:— | SHA256:— | |||
| 508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa508.22102\domains.db | sqlite | |
MD5:7C44F232A2F8F49225DAFB0B51E0D276 | SHA256:9FACE0239ECE675E1EC2785C2837C80D0C8D8A93879D0FE5374D29595F55E27F | |||
| 508 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa508.22102\app.log | text | |
MD5:4BC4CE162B46A500CB58F9F4541EA7D2 | SHA256:FA1109185D4267E8FBD10B6B958D1959DDA923B84CB9D04EF5B77D0163CEFD80 | |||
| 6984 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDB16.tmp\psuser_arm64.dll | executable | |
MD5:8794441685051F17888531456541FA32 | SHA256:A5E702A398C0890447E01047CD0360CAEAA6A3B8A92E0755B807858BEE4B9C0A | |||
| 6984 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDB16.tmp\MicrosoftEdgeUpdateComRegisterShell64.exe | executable | |
MD5:205590D4FB4B1914D2853AB7A9839CCF | SHA256:5F82471D58B6E700248D9602CE4A0A5CDA4D2E2863EF1EB9FEE4EFFCC07F3767 | |||
| 7028 | DPClient.exe | C:\Users\admin\AppData\Local\Temp\MicrosoftEdgeWebview2Setup.exe | executable | |
MD5:45E5CA74B9AE3C3FC6F6A63C609783B6 | SHA256:B4AFD37B9087DF7E041AE749FD0FA342926D9CCE533BDE9CDC4283132C3820A9 | |||
| 6984 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDB16.tmp\msedgeupdate.dll | executable | |
MD5:5D89123F9B96098D8FAD74108BDD5F7E | SHA256:03C3C918886E58F096AA8E919B1E9F8DCD5A9F2A4765971049BF8DA305476F44 | |||
| 6984 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDB16.tmp\psmachine.dll | executable | |
MD5:F1101C00EAAC144AA67F4A9334BB6F23 | SHA256:40D41C46A3E927E98BEEAD383624EFBE2FAF2CCBD0FA8F08C012DFD5FE36913A | |||
| 6984 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDB16.tmp\MicrosoftEdgeUpdateOnDemand.exe | executable | |
MD5:D0373E02A529653013865E392C417471 | SHA256:D4CB47B4444BE38BB6DCADC8BC9CACC029CB73A66BC7AF152C1C4CA022446AA4 | |||
| 6984 | MicrosoftEdgeWebview2Setup.exe | C:\Users\admin\AppData\Local\Temp\EUDB16.tmp\psuser.dll | executable | |
MD5:C31C15567530C4B121EBEC83973C6F7D | SHA256:17762EFA738632BCD376456F9E0C2331CFFD875208F9AD8D428BFD09785EB240 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
27
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5816 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5284 | svchost.exe | HEAD | 200 | 23.48.23.7:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e21df09-d909-4575-8e24-d945909e58df?P1=1725858223&P2=404&P3=2&P4=BWozuhQ7wwKaKGP1TOU%2bbcghTcPeA0ygV5N7gQgx0KtunoJLHGqLp14EYiIViR4UFOnpukarevjCqhBmtSCtuQ%3d%3d | unknown | — | — | whitelisted |
5284 | svchost.exe | GET | — | 23.48.23.7:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e21df09-d909-4575-8e24-d945909e58df?P1=1725858223&P2=404&P3=2&P4=BWozuhQ7wwKaKGP1TOU%2bbcghTcPeA0ygV5N7gQgx0KtunoJLHGqLp14EYiIViR4UFOnpukarevjCqhBmtSCtuQ%3d%3d | unknown | — | — | whitelisted |
6704 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6704 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2248 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4132 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5816 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5816 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
7028 | DPClient.exe | 172.67.190.41:443 | api.dorkplus.com | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.dorkplus.com |
| unknown |
go.microsoft.com |
| whitelisted |
msedge.sf.dl.delivery.mp.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
msedge.api.cdp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5284 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |