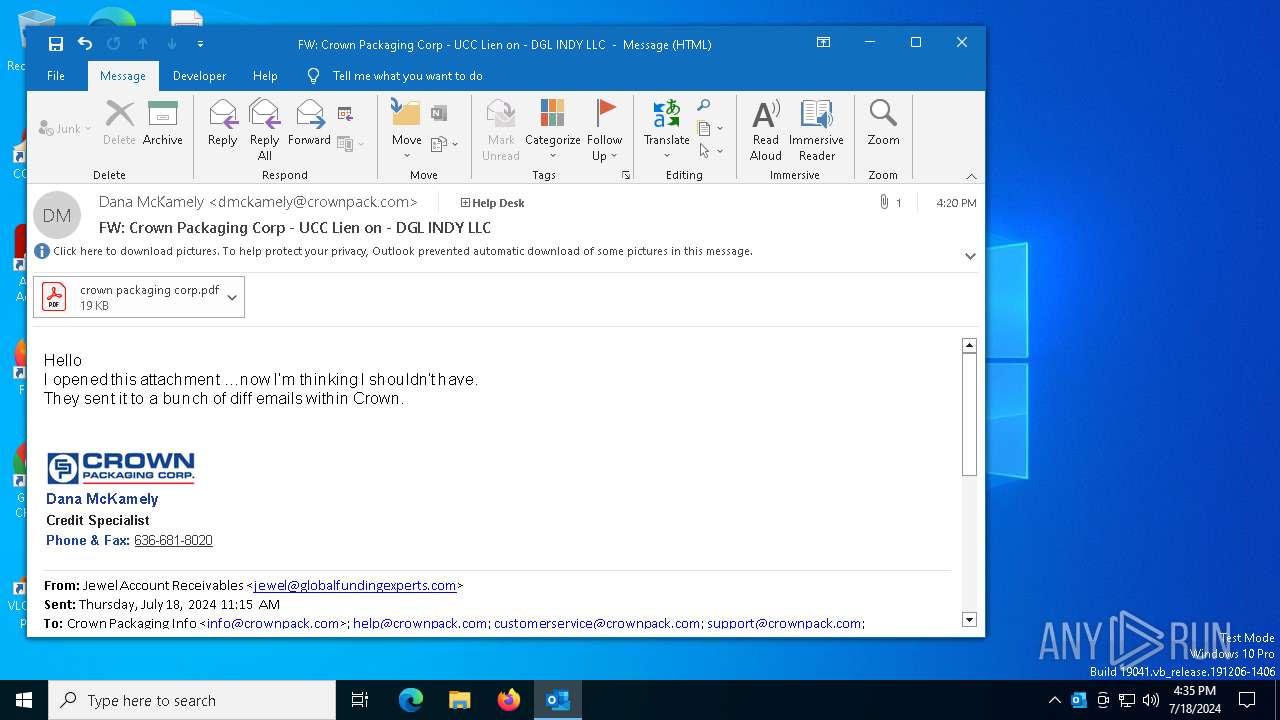
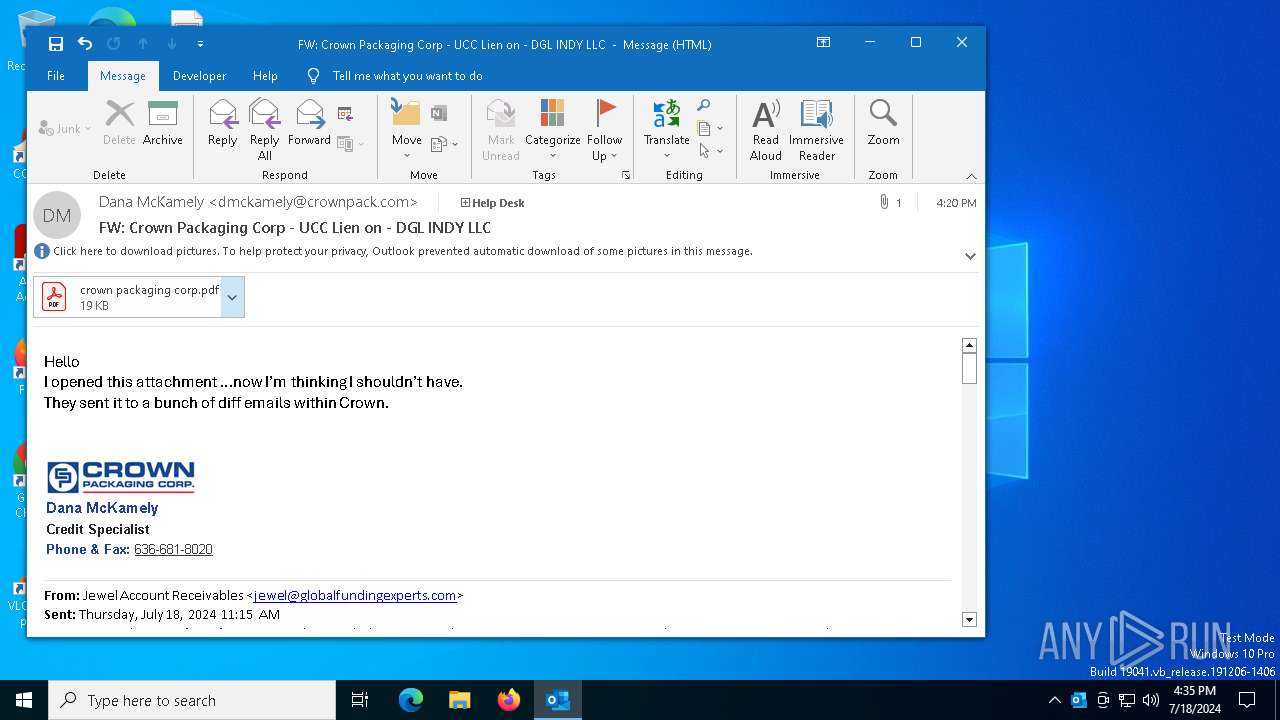
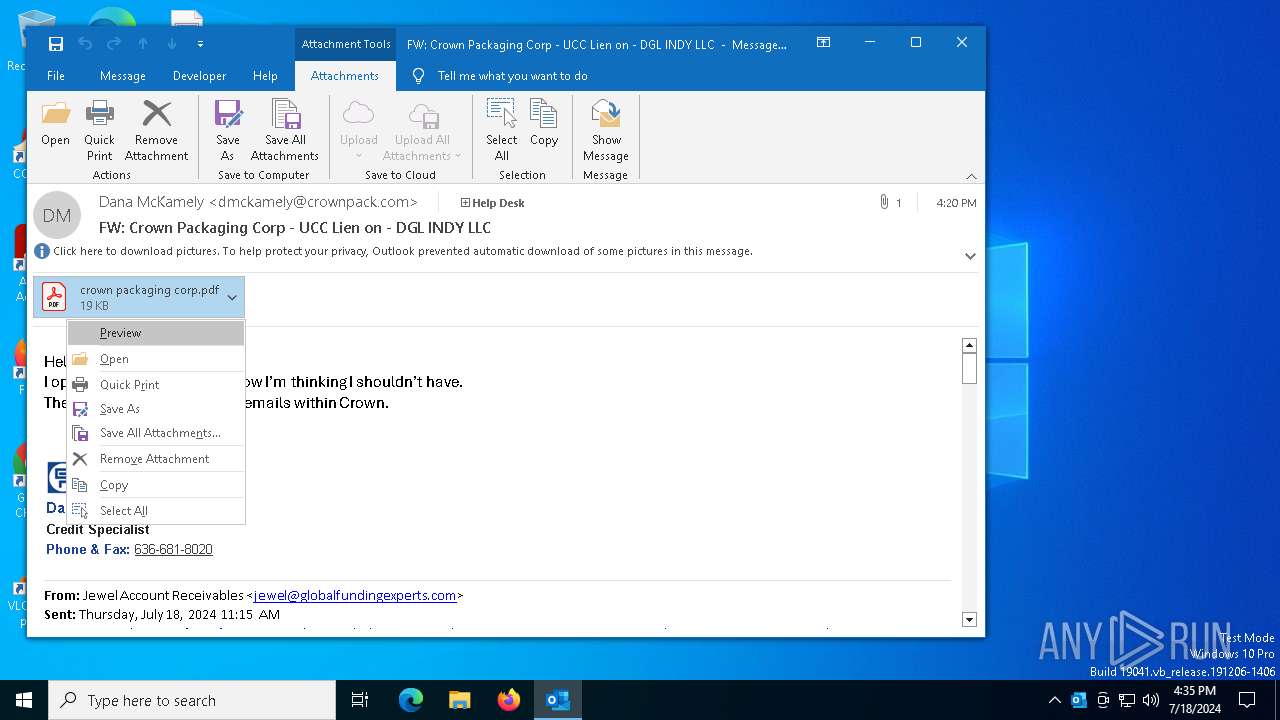
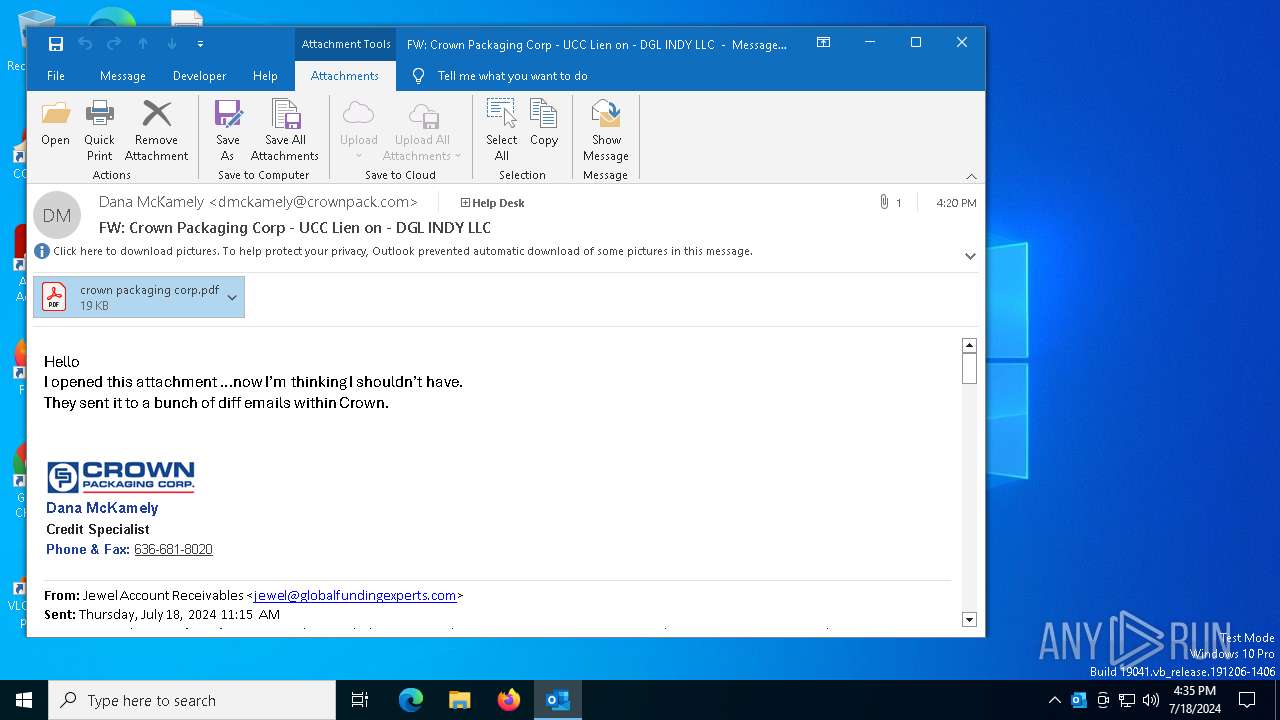
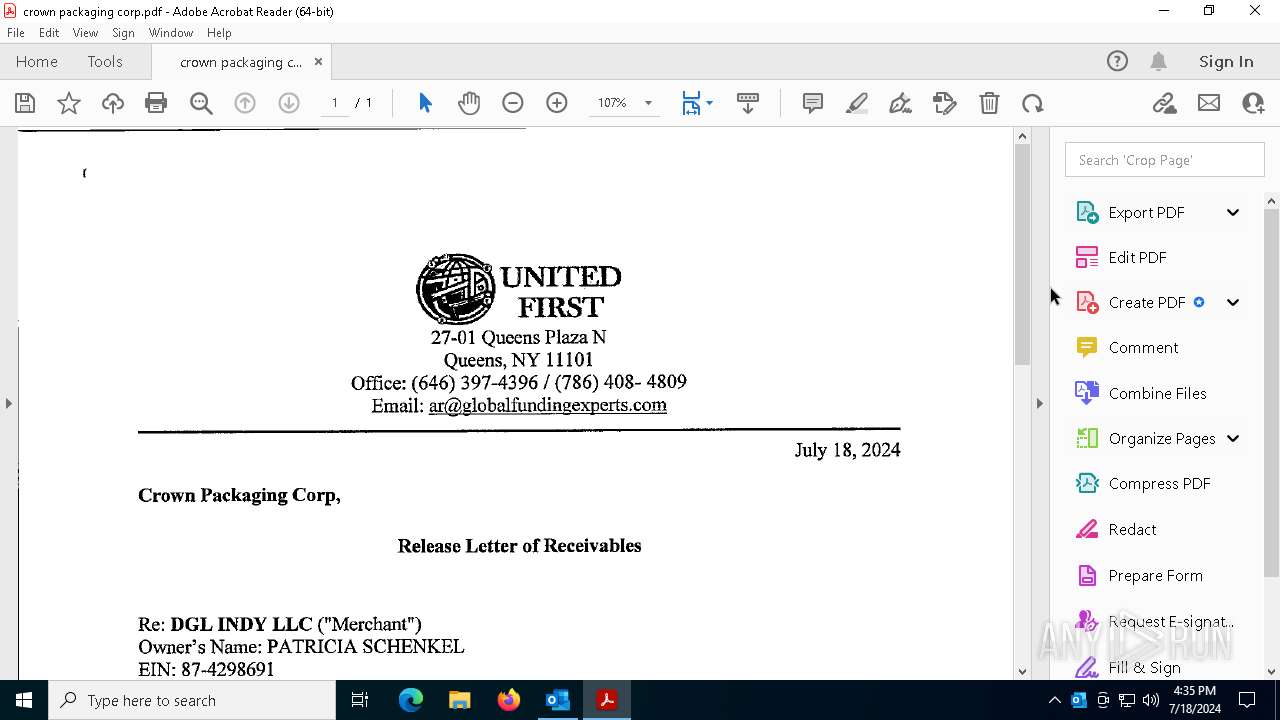
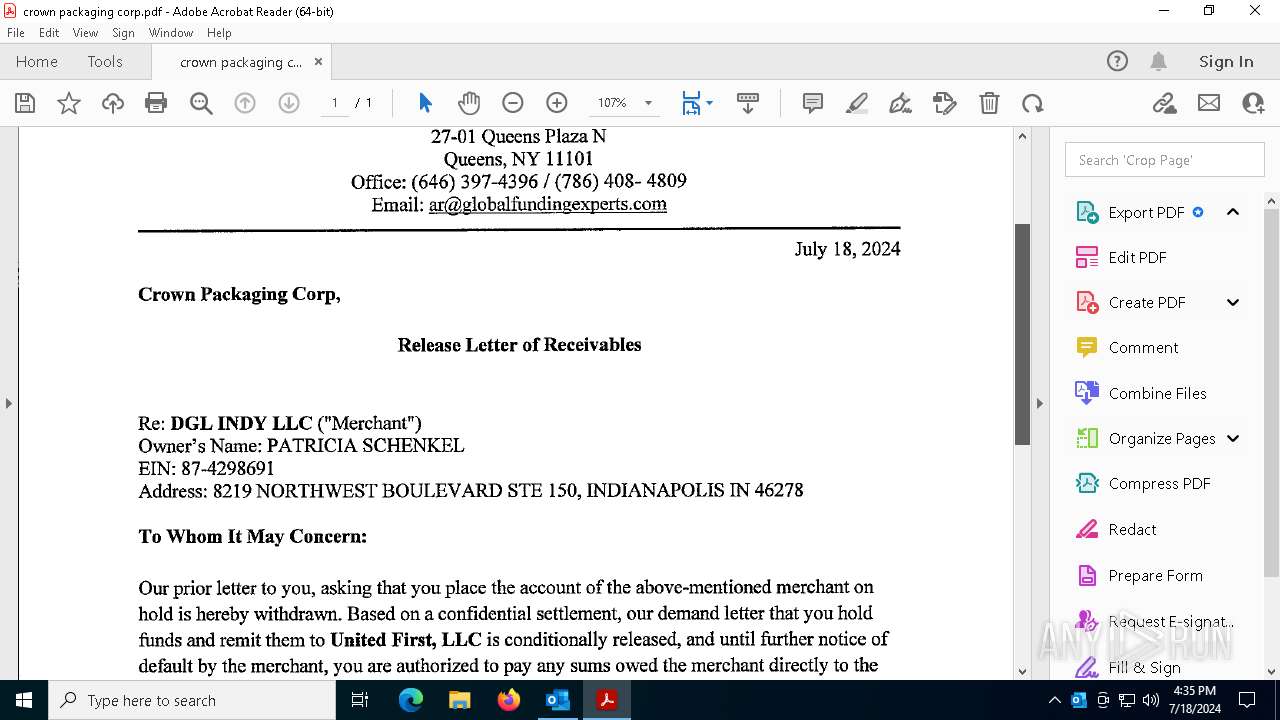
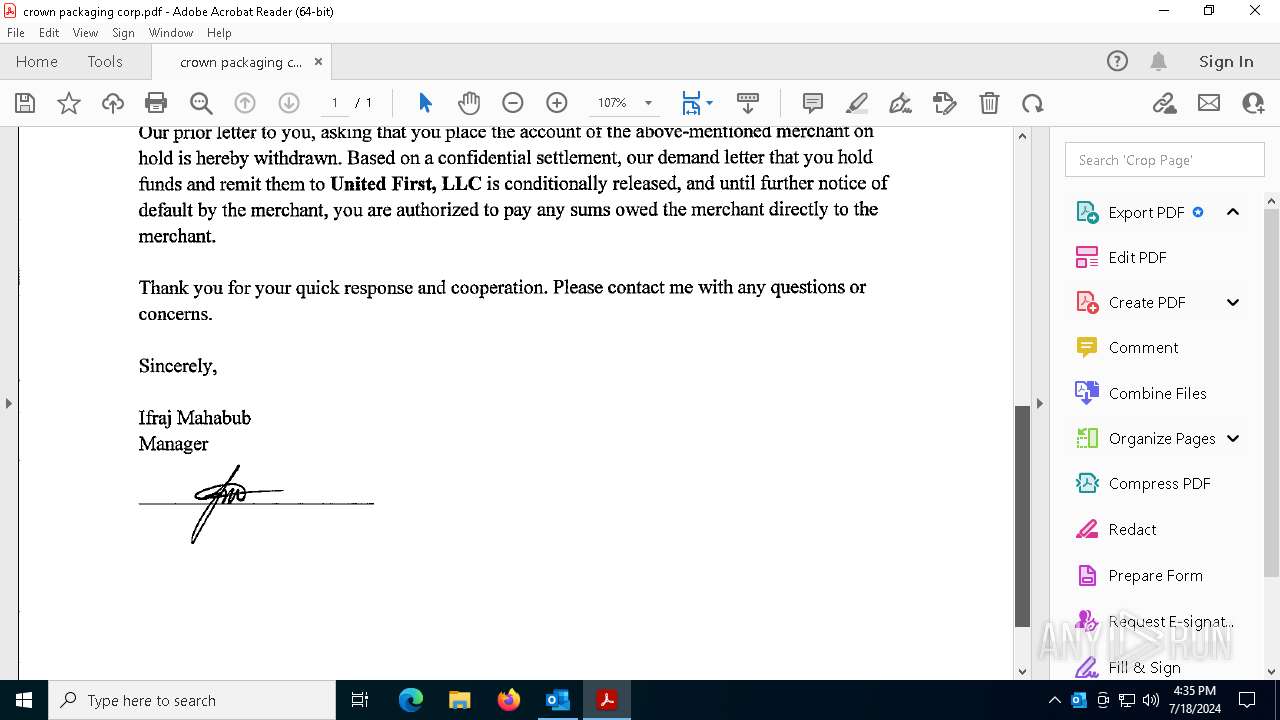
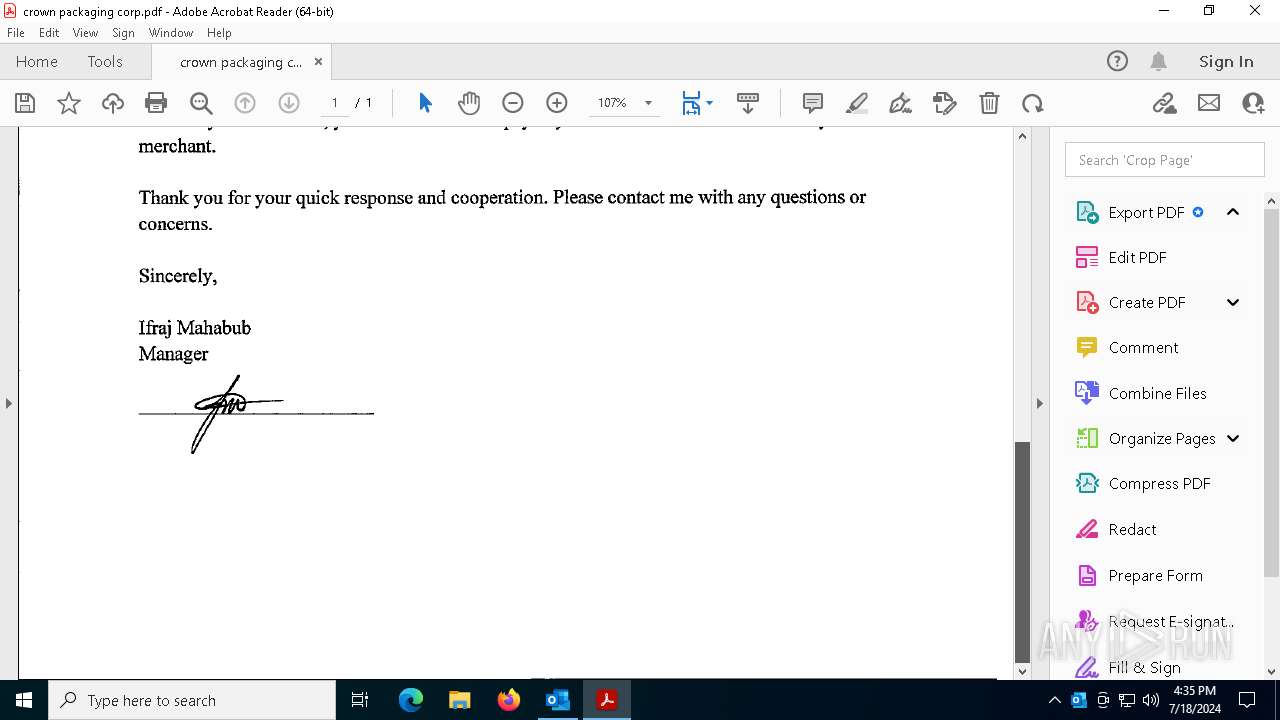
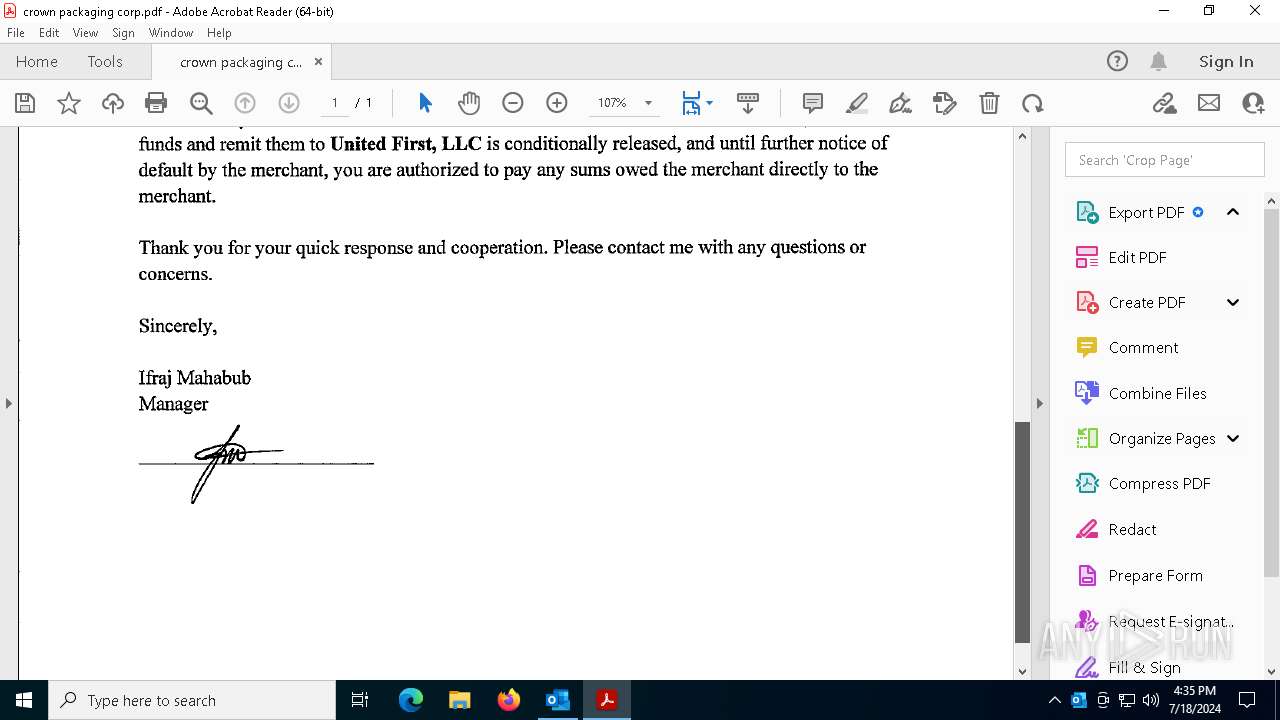
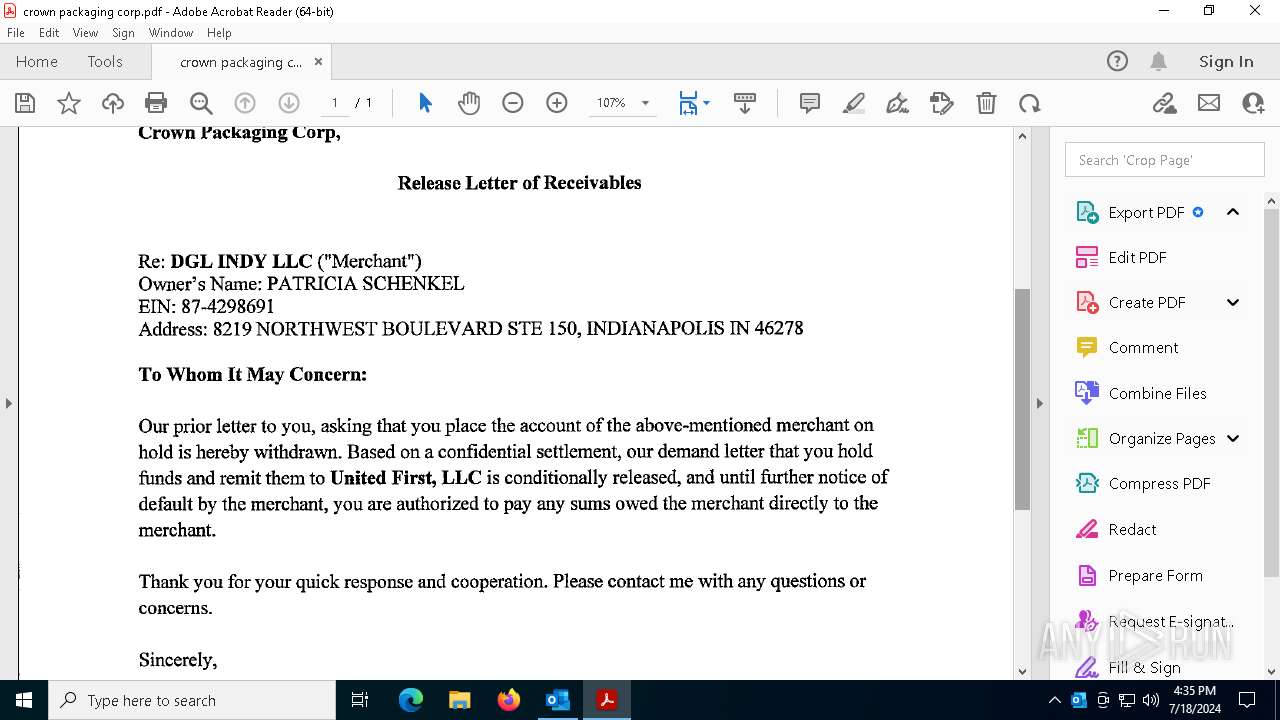
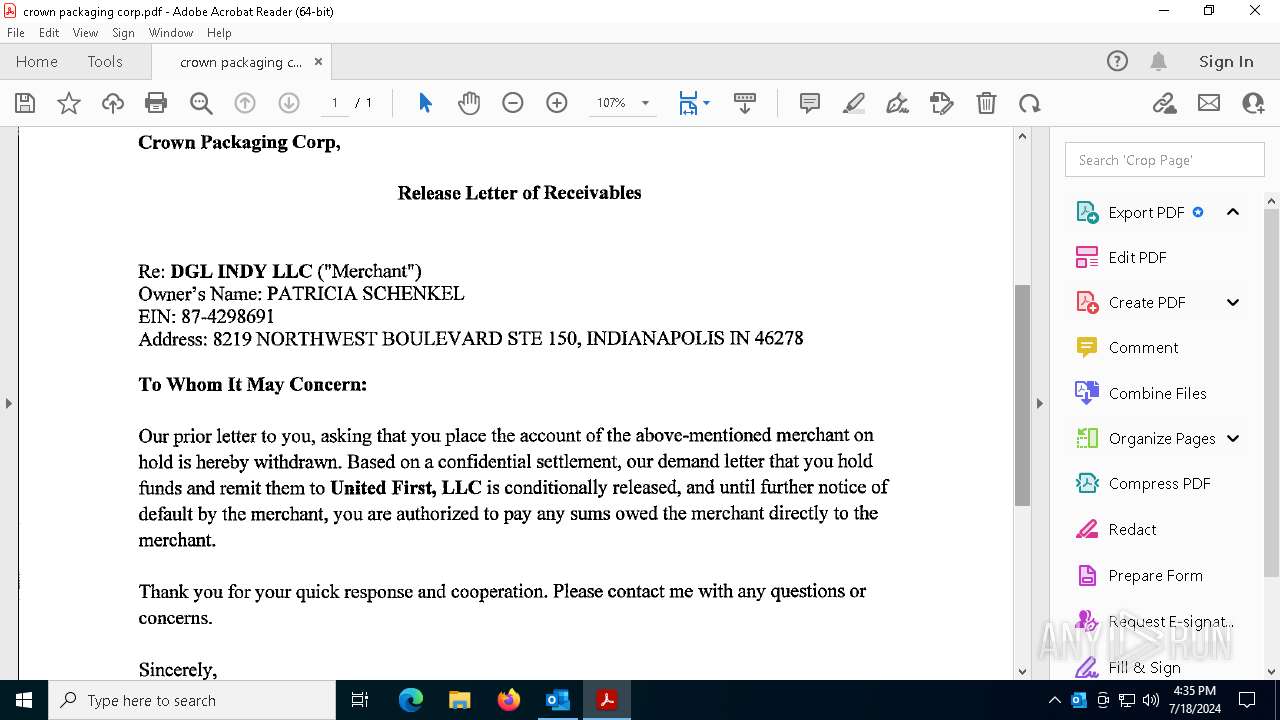
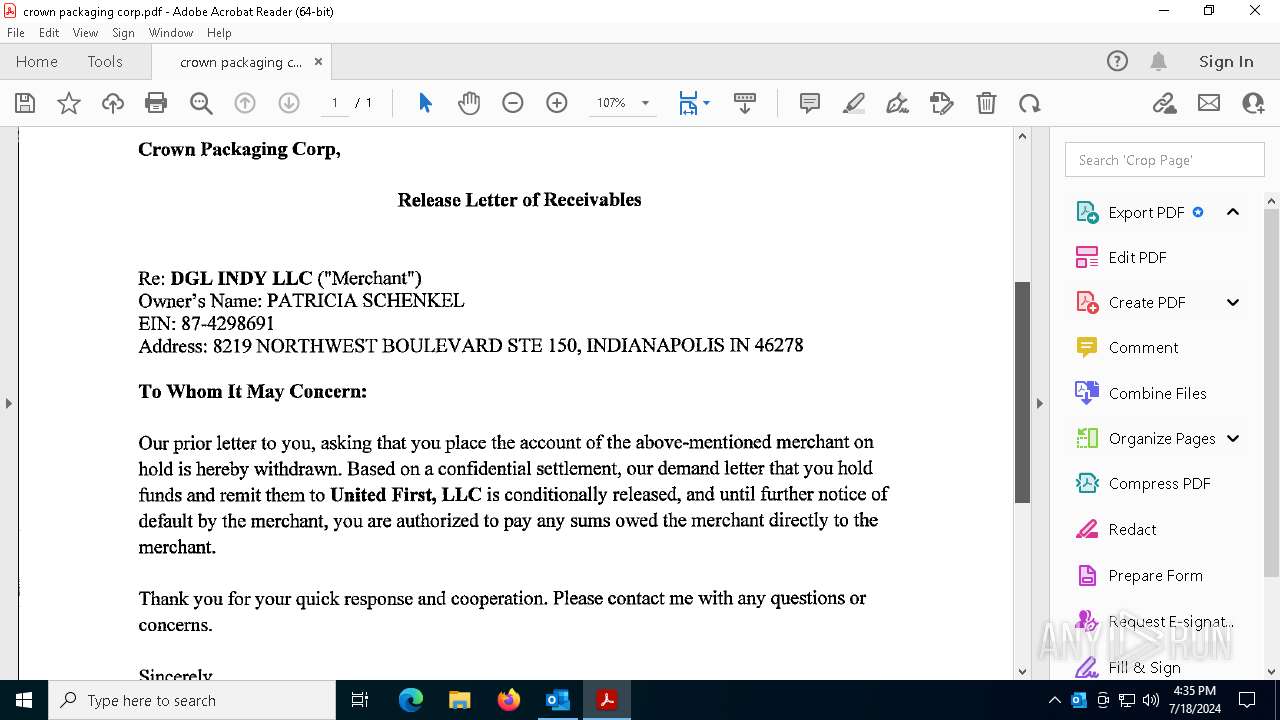
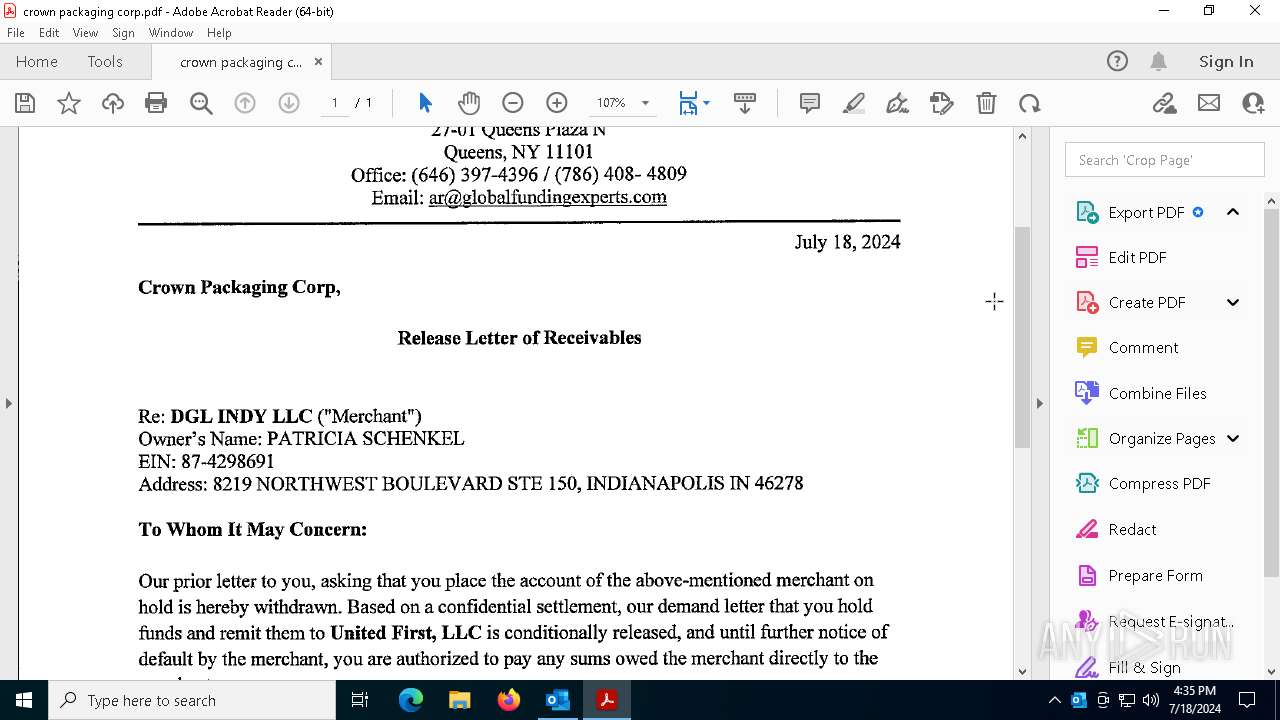
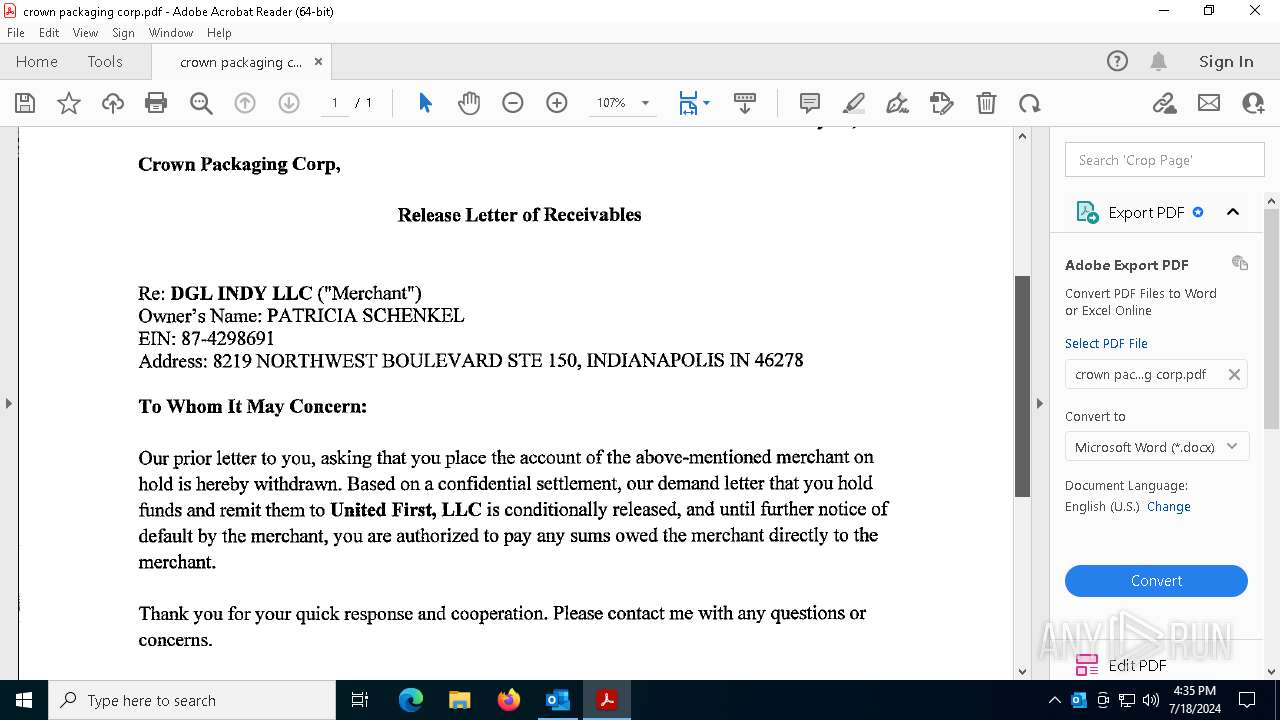
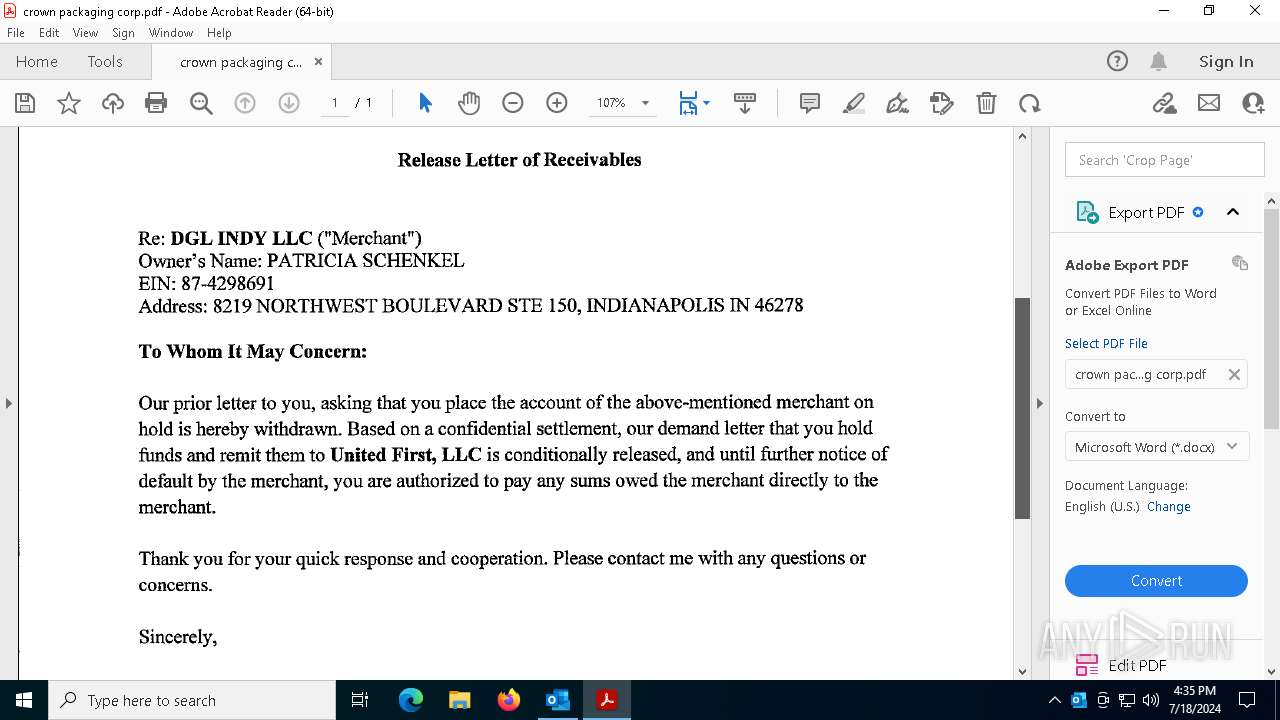
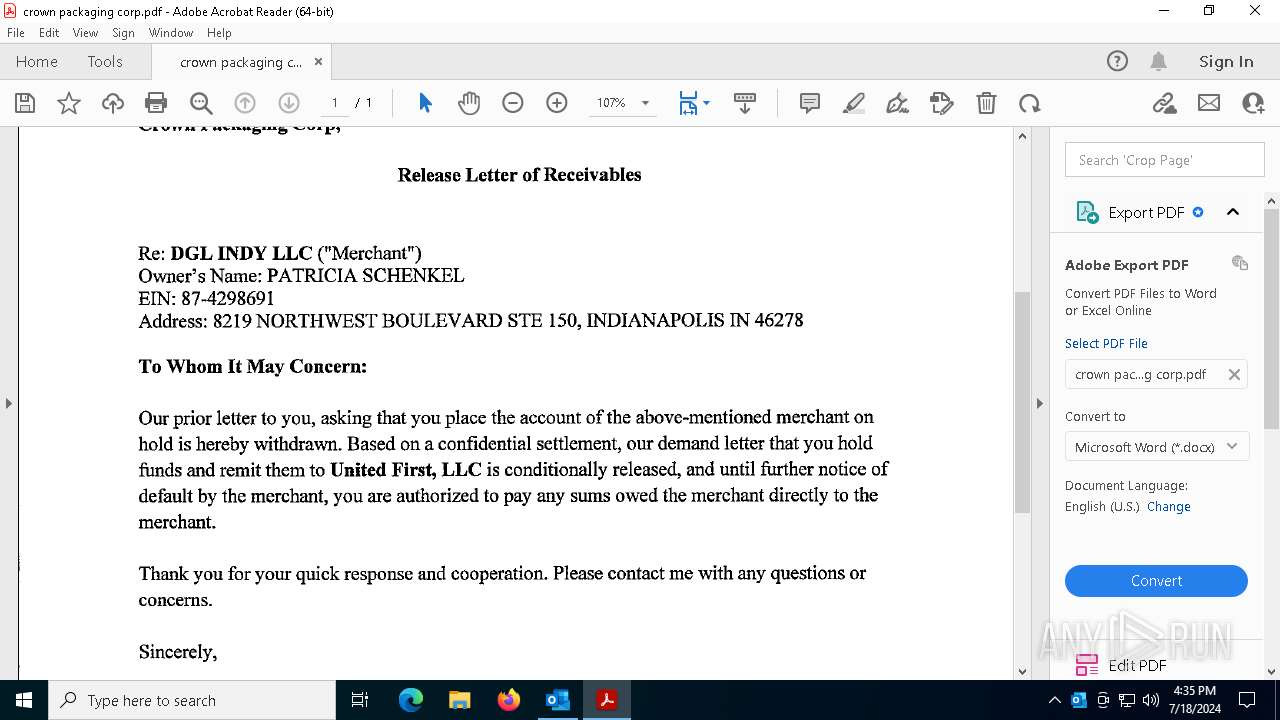
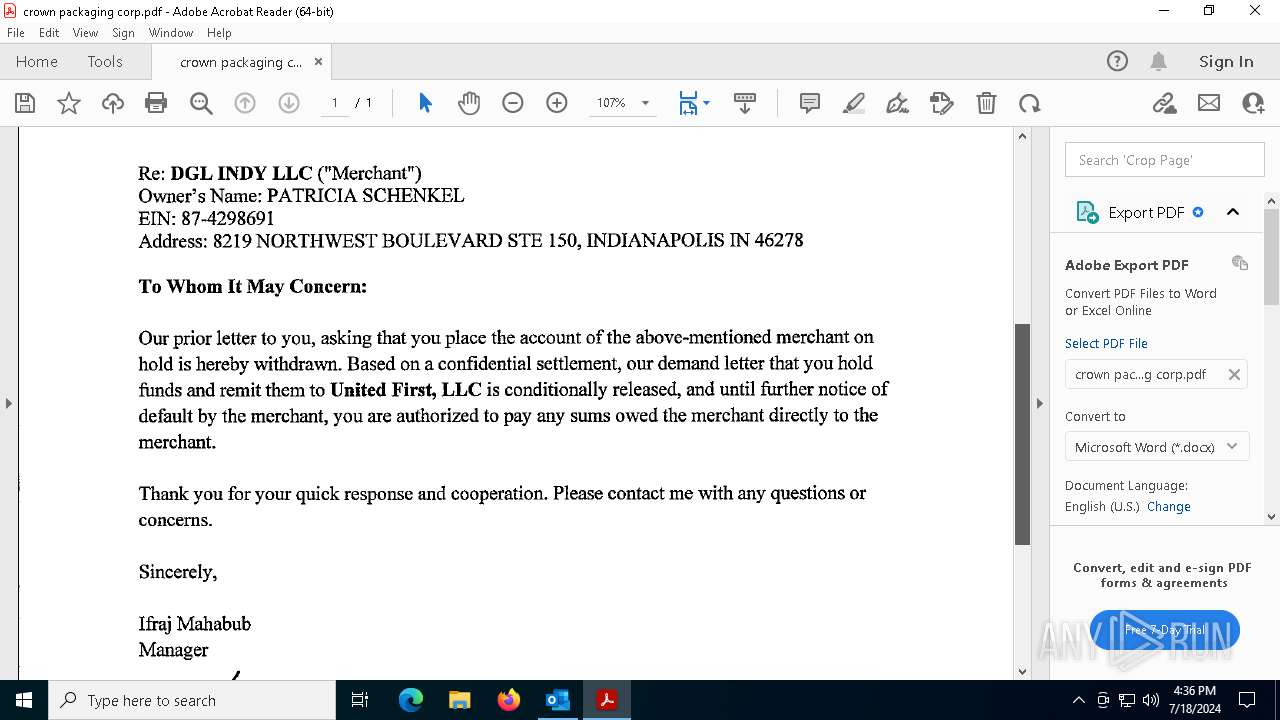
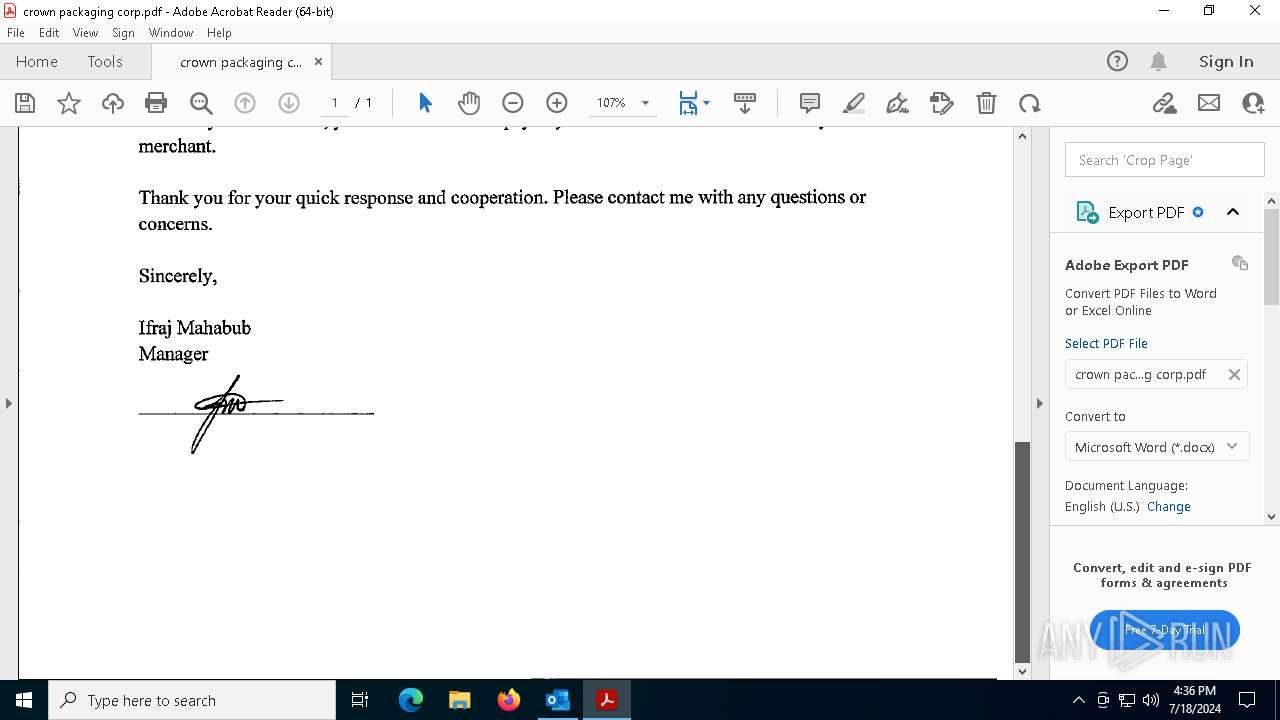
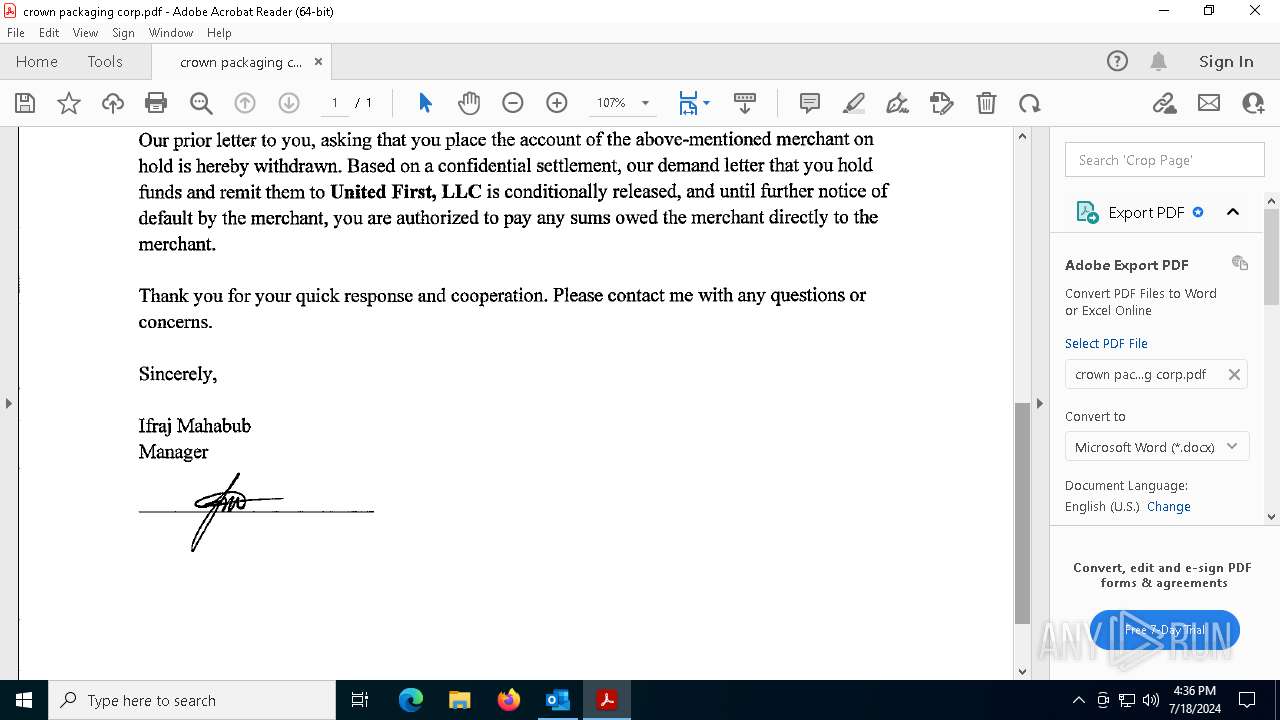
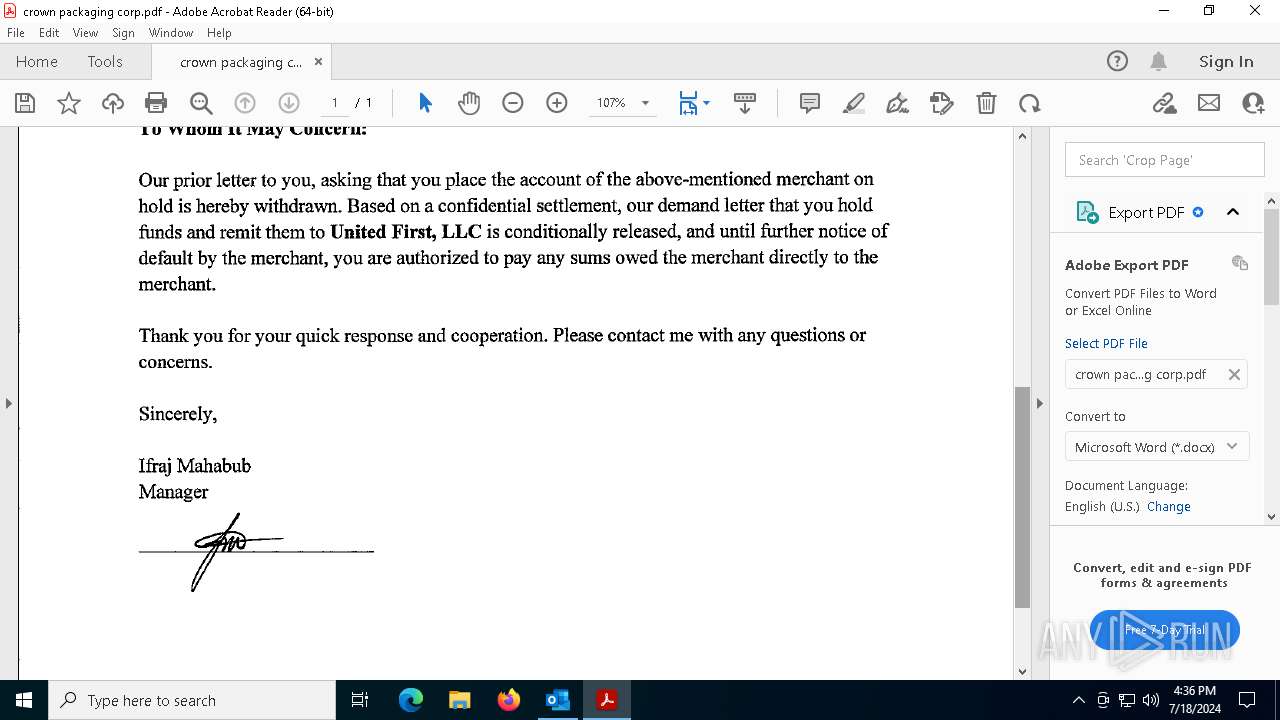
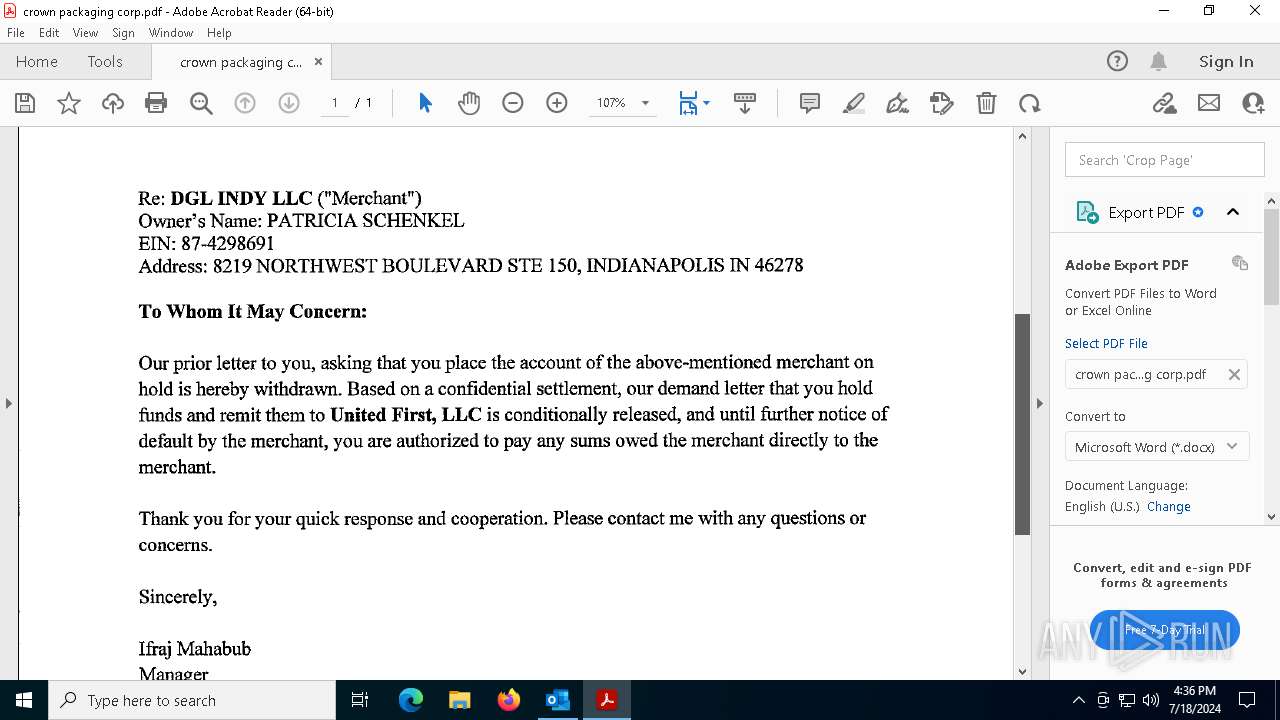
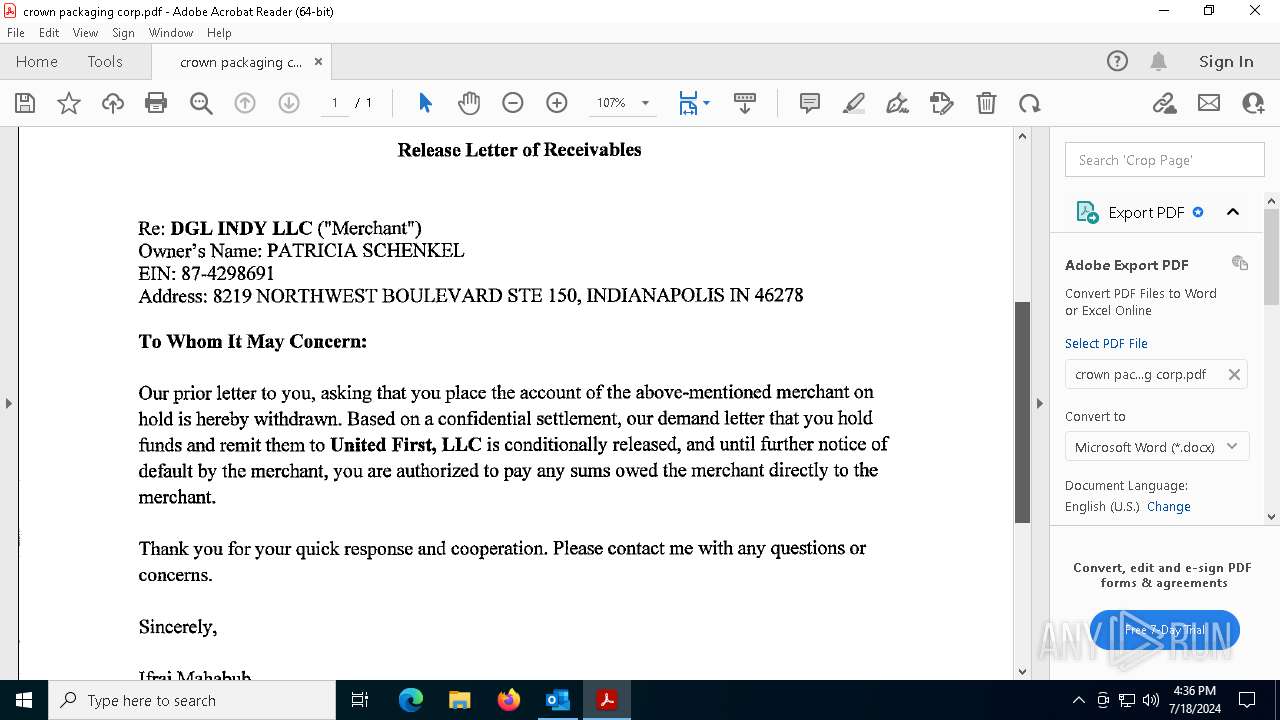
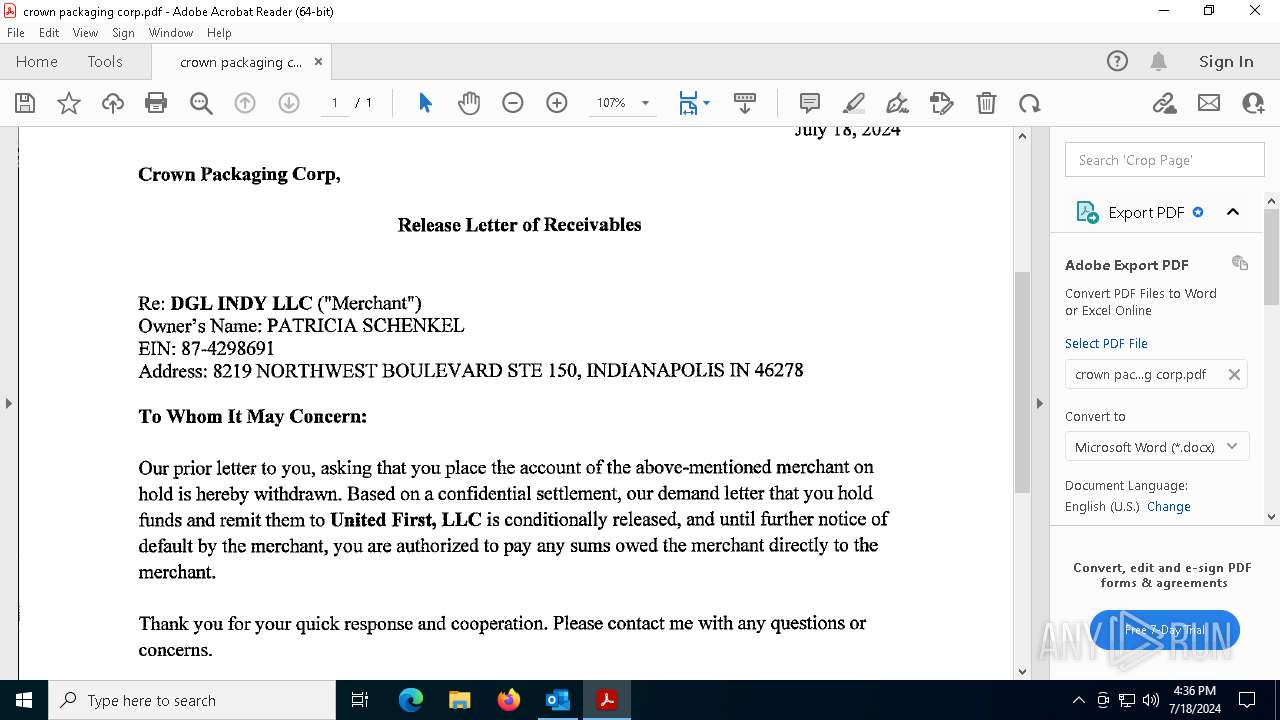
| File name: | FW_ Crown Packaging Corp - UCC Lien on - DGL INDY LLC.msg |
| Full analysis: | https://app.any.run/tasks/12075cf0-38a1-4213-b314-1d9615effe7b |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2024, 16:34:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 5BC6A8C1D2764AEE04371E002FA97B00 |
| SHA1: | C3FEDF0CDE2EFFF7B4BA311BBDDB7C24B1FA4AD7 |
| SHA256: | 63DCB30CB0DCC7A4697FADC0E195B10632913C0B6B54FACF46BFE248AD457C56 |
| SSDEEP: | 3072:l9LHHEYdQLMnJCMMqMMz1fY1K7N/Vlln:fLHH1OMnJCMMqMMxY87N/V |
MALICIOUS
The DLL Hijacking
- OfficeClickToRun.exe (PID: 6404)
Creates a writable file in the system directory
- OfficeClickToRun.exe (PID: 6404)
Scans artifacts that could help determine the target
- OfficeClickToRun.exe (PID: 6404)
SUSPICIOUS
Executes as Windows Service
- OfficeClickToRun.exe (PID: 6404)
Checks Windows Trust Settings
- OfficeClickToRun.exe (PID: 6404)
INFO
Reads the computer name
- OfficeClickToRun.exe (PID: 6404)
Reads Microsoft Office registry keys
- OfficeClickToRun.exe (PID: 6404)
- Acrobat.exe (PID: 6940)
Process checks computer location settings
- OfficeClickToRun.exe (PID: 6404)
Reads the machine GUID from the registry
- OfficeClickToRun.exe (PID: 6404)
Reads CPU info
- OfficeClickToRun.exe (PID: 6404)
Reads the software policy settings
- OfficeClickToRun.exe (PID: 6404)
Reads Environment values
- OfficeClickToRun.exe (PID: 6404)
Checks proxy server information
- OfficeClickToRun.exe (PID: 6404)
Application launched itself
- Acrobat.exe (PID: 6240)
- AcroCEF.exe (PID: 7916)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 3924)
Checks supported languages
- acrobat_sl.exe (PID: 8028)
- OfficeClickToRun.exe (PID: 6404)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 4428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (41) |
|---|---|---|
| .oft | | | Outlook Form Template (23.9) |
| .doc | | | Microsoft Word document (old ver.) (10.9) |
Total processes
148
Monitored processes
23
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --first-renderer-process --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2292 --field-trial-handle=1572,i,10319501994827606734,16326576034474140609,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 764 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2108 --field-trial-handle=1572,i,10319501994827606734,16326576034474140609,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | AcroCEF.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 908 | C:\Windows\System32\CompPkgSrv.exe -Embedding | C:\Windows\System32\CompPkgSrv.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Component Package Support Server Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1032 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "4C456E7A-BE77-42F9-A590-53578654AC0A" "EF3C1FE6-27C8-4B2B-AFBF-82F205080708" "3924" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 1292 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=utility --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2020 --field-trial-handle=1572,i,10319501994827606734,16326576034474140609,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:8 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 3040 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2304 --field-trial-handle=1572,i,10319501994827606734,16326576034474140609,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 3924 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /f "C:\Users\admin\Downloads\FW_ Crown Packaging Corp - UCC Lien on - DGL INDY LLC.msg" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 4428 | "C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Acrobat /VERSION:23.0 /MODE:3 | C:\Program Files (x86)\Common Files\Adobe\ARM\1.0\AdobeARM.exe | Acrobat.exe | ||||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Version: 1.824.460.1042 Modules
| |||||||||||||||
| 4948 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=2008 --field-trial-handle=1572,i,10319501994827606734,16326576034474140609,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Exit code: 0 Version: 23.1.20093.0 Modules
| |||||||||||||||
| 5352 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=renderer --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --touch-events=enabled --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --mojo-platform-channel-handle=2588 --field-trial-handle=1572,i,10319501994827606734,16326576034474140609,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:1 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
Total events
47 913
Read events
46 417
Write events
1 347
Delete events
149
Modification events
| (PID) Process: | (6404) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6404) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 1 | |||
| (PID) Process: | (6404) OfficeClickToRun.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\Windows Error Reporting\RuntimeExceptionHelperModules |
| Operation: | write | Name: | C:\Program Files\Common Files\Microsoft Shared\ClickToRun\c2r64werhandler.dll |
Value: 0 | |||
| (PID) Process: | (6404) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Office\16.0\Common |
| Operation: | write | Name: | SessionId |
Value: D10BD1EED722F749AD4CBB30356436F4 | |||
| (PID) Process: | (6404) OfficeClickToRun.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Office\ClickToRun |
| Operation: | write | Name: | MachineMetadataSentTime |
Value: 13365794112407 | |||
| (PID) Process: | (6404) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6404) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6404) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6404) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6404) OfficeClickToRun.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Office\16.0\Common\Internet\WebServiceCache\AllUsers\officeclient.microsoft.com\config16--syslcid=1033&build=16.0.16026&crev=3\0 |
| Operation: | write | Name: | FilePath |
Value: officeclient.microsoft.com\F5459BB5-D948-42B0-BD3F-EBEAC82C2A3A | |||
Executable files
1
Suspicious files
110
Text files
25
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3924 | OUTLOOK.EXE | C:\USERS\ADMIN\DOCUMENTS\OUTLOOK FILES\OUTLOOK1.PST | — | |
MD5:— | SHA256:— | |||
| 3924 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\4B05AA78-9311-4EE8-B2F9-0367EA8055E6 | xml | |
MD5:86C19A3BE08DC63F6AFF596D17F92CE9 | SHA256:180D6207B9EBF21875DCE81CEF4AF5FD2D400BDDD9D5D8C855B01EEE37984046 | |||
| 3924 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:293548FDBB6A8B275CA5B444D8A4436A | SHA256:E5EA072225D4B52314DE16090E712E9D03D7407F0550439D7697AECE6125B184 | |||
| 3924 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\5315DDA4.dat | image | |
MD5:74B942FA1BE3868E63923EA505E362BF | SHA256:C8576D4225231224A25B3A46365DA5644828E4D276DC51FC94CBB7DC59D6338D | |||
| 3924 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\5475cb191e478c39370a215b2da98a37e9dc813d.tbres | binary | |
MD5:C5D723557AC354772A30798F7E10248C | SHA256:41D82325EB93260BC3C1C8E30555F44364554A831D3C8DF277EACC67C41B9D3F | |||
| 3924 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:83EEEA16DBC2BB8939B3586CBAB211A9 | SHA256:1850397AC5B35D4DA96FF6B4BA6E6BD41A73693C085F5B456F57CED23A25B848 | |||
| 3924 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\msoEDD9.tmp | image | |
MD5:ED3C1C40B68BA4F40DB15529D5443DEC | SHA256:039FE79B74E6D3D561E32D4AF570E6CA70DB6BB3718395BE2BF278B9E601279A | |||
| 3924 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FORMS\FRMDATA64.DAT | binary | |
MD5:6D4DE3C5917BAA7B9B0C272974B2FD4E | SHA256:EA295E017CCCD7A740EE9B7BFED3CC7C0FBBE82C991C26C051F8B3F549AB2F14 | |||
| 3924 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.MSO\ED0FA752.dat | image | |
MD5:D89746888DA2D9510B64A9F031EAECD5 | SHA256:EF1955AE757C8B966C83248350331BD3A30F658CED11F387F8EBF05AB3368629 | |||
| 3924 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
41
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4428 | AdobeARM.exe | GET | 404 | 2.16.164.123:80 | http://acroipm2.adobe.com/assets/Owner/arm/2024/7/OwnerAPI/Rdr.txt | unknown | — | — | whitelisted |
4428 | AdobeARM.exe | GET | 404 | 2.16.164.123:80 | http://acroipm2.adobe.com/assets/Owner/arm/2024/7/UC/Other.txt | unknown | — | — | whitelisted |
4428 | AdobeARM.exe | GET | 404 | 2.16.164.123:80 | http://acroipm2.adobe.com/assets/Owner/arm/29/adnme/NoValidReasonForAdnme.txt | unknown | — | — | whitelisted |
4428 | AdobeARM.exe | GET | 304 | 2.16.164.123:80 | http://acroipm2.adobe.com/assets/Owner/arm/ProcessMAU.txt | unknown | — | — | whitelisted |
4428 | AdobeARM.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
4428 | AdobeARM.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
4428 | AdobeARM.exe | GET | 304 | 2.16.164.123:80 | http://acroipm2.adobe.com/assets/Owner/arm/ReportOwner.txt | unknown | — | — | whitelisted |
3924 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
6240 | Acrobat.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
4428 | AdobeARM.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEA0aNA9419AA4In9uq1lIt8%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4716 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7856 | svchost.exe | 4.209.33.156:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
5460 | backgroundTaskHost.exe | 20.31.169.57:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5460 | backgroundTaskHost.exe | 20.199.58.43:443 | fd.api.iris.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
2760 | svchost.exe | 40.115.3.253:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1016 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4716 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
google.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |