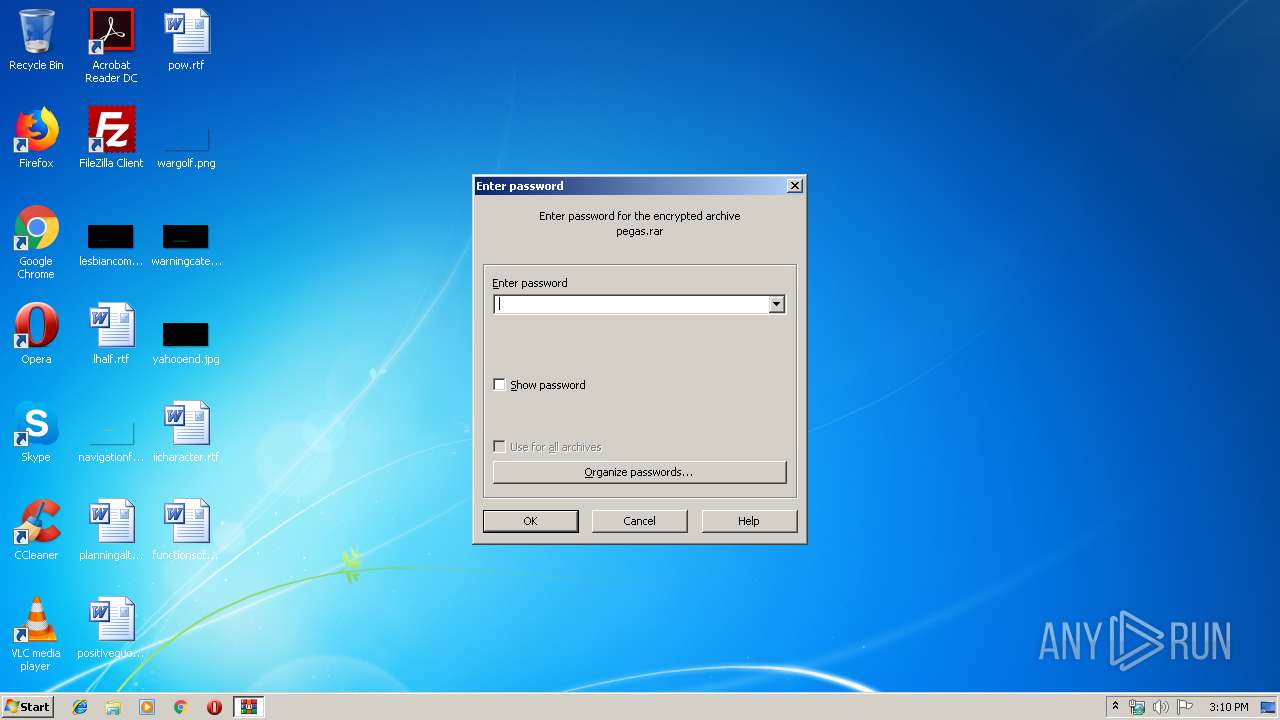
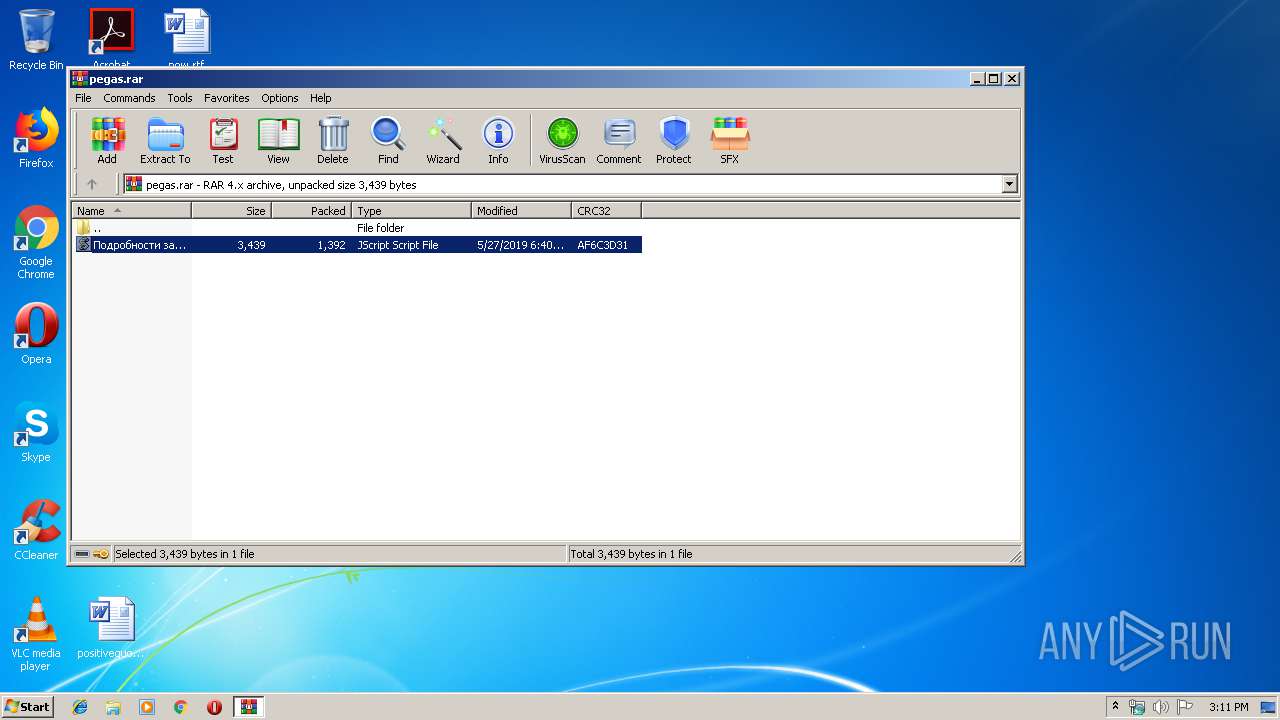
| File name: | pegas.rar |
| Full analysis: | https://app.any.run/tasks/0d83d93b-5418-4011-9c05-fff0f8391e2d |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2019, 14:10:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, flags: EncryptedBlockHeader |
| MD5: | 38D51A0508F92CCFC06428A738E64925 |
| SHA1: | 396D128FD59C1EB371A7FE8CEF6D0B208F1A0ECB |
| SHA256: | 63D18BCEC4775C2AB66E64C71A205933404AC86AD0951503816CA41FD8B18CC6 |
| SSDEEP: | 48:qI+95fRngyQQ82OtbLyVlruTjCar0O8L3l3b6AIlO3:G5fRgeMbooOx3oO3 |
MALICIOUS
Changes settings of System certificates
- WScript.exe (PID: 2856)
- WScript.exe (PID: 3832)
- WScript.exe (PID: 3388)
SUSPICIOUS
Executes scripts
- WinRAR.exe (PID: 2828)
Adds / modifies Windows certificates
- WScript.exe (PID: 3832)
- WScript.exe (PID: 3388)
- WScript.exe (PID: 2856)
INFO
Reads settings of System Certificates
- WScript.exe (PID: 3832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
Total processes
36
Monitored processes
4
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2828 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\pegas.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
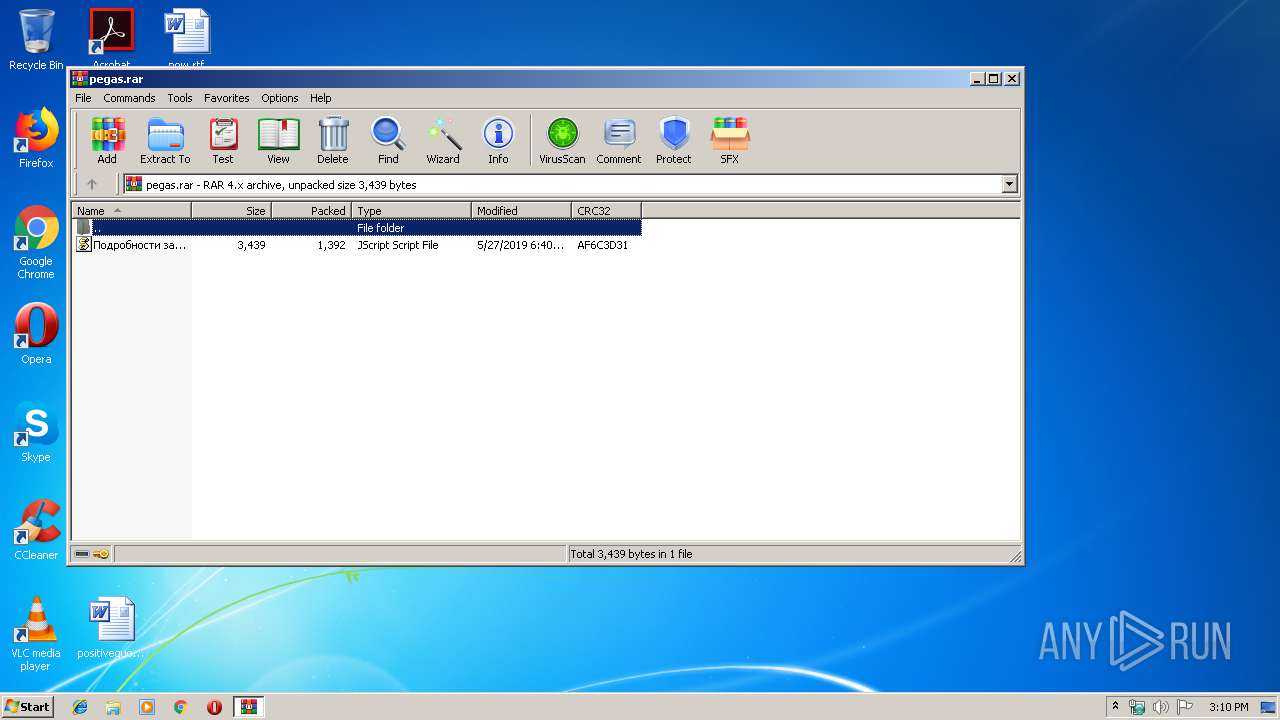
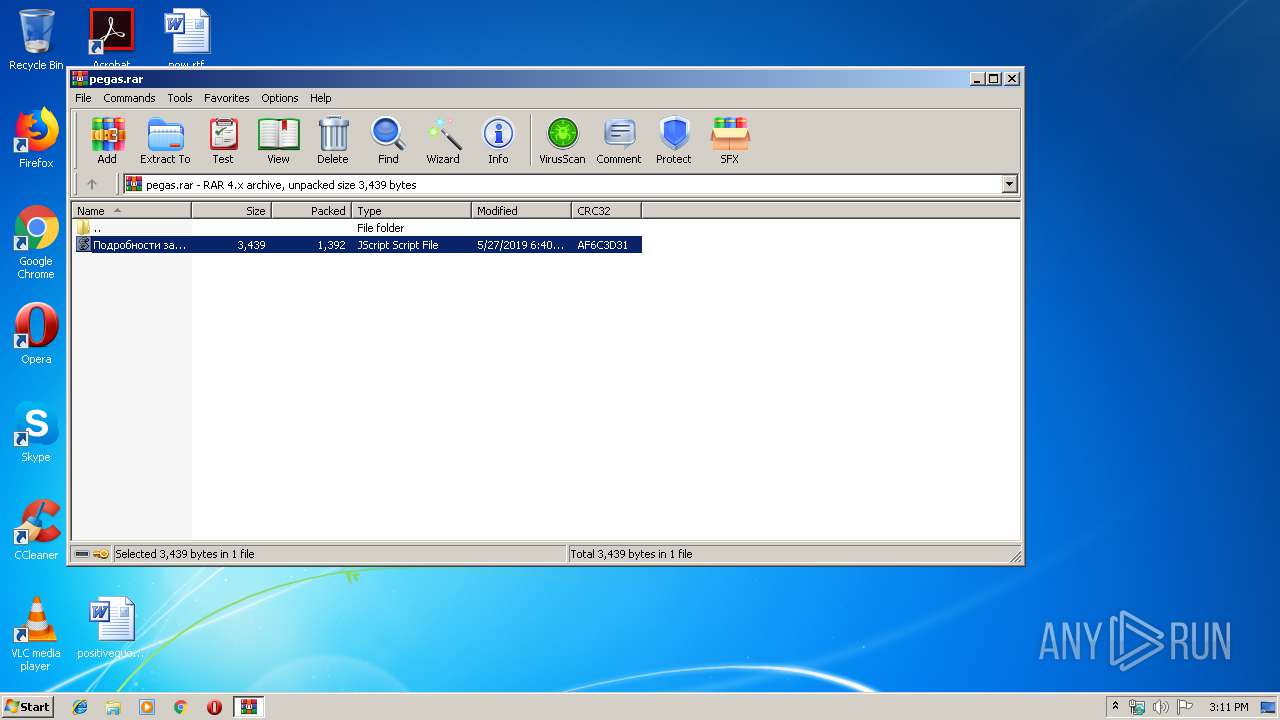
| 2856 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIb2828.45953\Подробности заказа ООО Авиакомпания Икар.js" | C:\Windows\System32\WScript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3388 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIb2828.46842\Подробности заказа ООО Авиакомпания Икар.js" | C:\Windows\System32\WScript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3832 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIb2828.47124\Подробности заказа ООО Авиакомпания Икар.js" | C:\Windows\System32\WScript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
667
Read events
564
Write events
94
Delete events
9
Modification events
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\pegas.rar | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2828) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\wshext.dll,-4804 |
Value: JScript Script File | |||
Executable files
0
Suspicious files
1
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2828.47124\Подробности заказа ООО Авиакомпания Икар.js | text | |
MD5:— | SHA256:— | |||
| 2828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2828.45953\Подробности заказа ООО Авиакомпания Икар.js | text | |
MD5:— | SHA256:— | |||
| 2828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2828.46842\Подробности заказа ООО Авиакомпания Икар.js | text | |
MD5:— | SHA256:— | |||
| 2856 | WScript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A2ECA083537A02B6158458FF1752C63F | binary | |
MD5:— | SHA256:— | |||
| 2856 | WScript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A2ECA083537A02B6158458FF1752C63F | der | |
MD5:B15409274F54AD8F023D3B85A5ECEC5D | SHA256:25847D668EB4F04FDD40B12B6B0740C567DA7D024308EB6C2C96FE41D9DE218D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
7
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2856 | WScript.exe | GET | 200 | 23.77.208.94:80 | http://cert.int-x3.letsencrypt.org/ | NL | der | 1.15 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2856 | WScript.exe | 23.77.208.94:80 | cert.int-x3.letsencrypt.org | Akamai International B.V. | NL | whitelisted |
2856 | WScript.exe | 85.93.145.251:443 | mat.tradetoolsfx.com | JSC Internet-Cosmos | RU | unknown |
3388 | WScript.exe | 85.93.145.251:443 | mat.tradetoolsfx.com | JSC Internet-Cosmos | RU | unknown |
3832 | WScript.exe | 85.93.145.251:443 | mat.tradetoolsfx.com | JSC Internet-Cosmos | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mat.tradetoolsfx.com |
| unknown |
cert.int-x3.letsencrypt.org |
| whitelisted |
cryptobinary-options.tradetoolsfx.com |
| unknown |