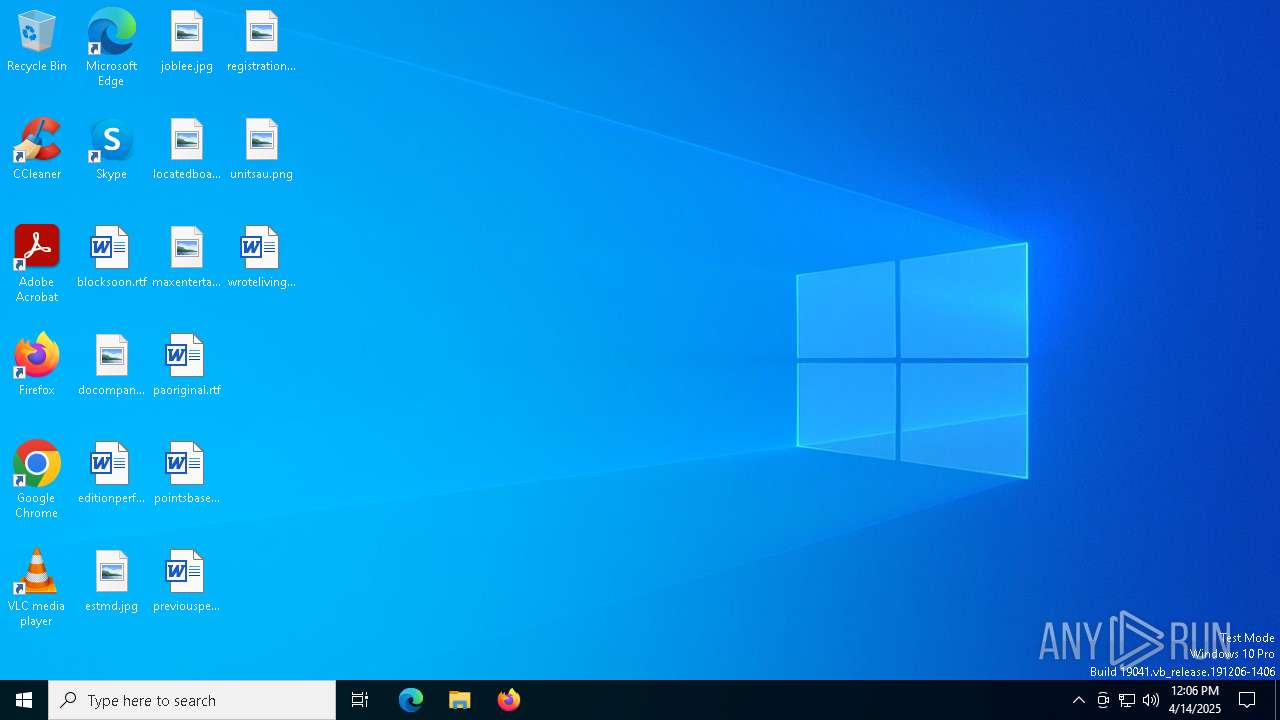
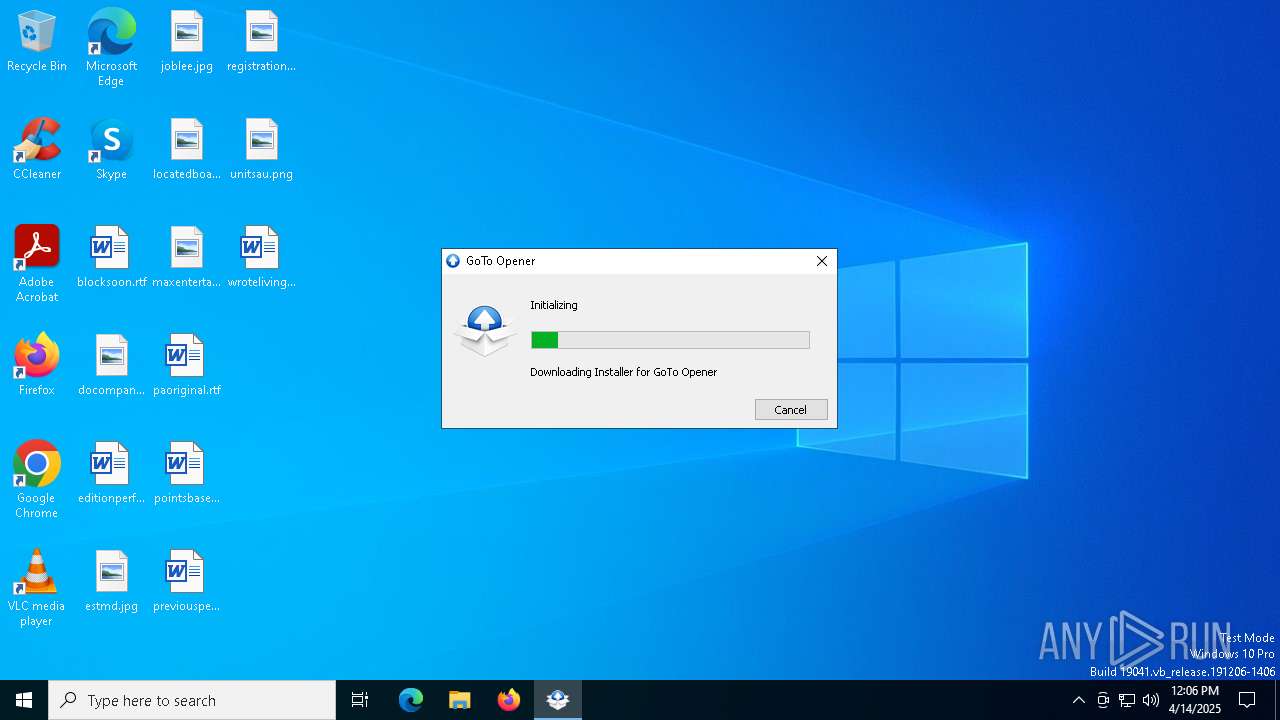
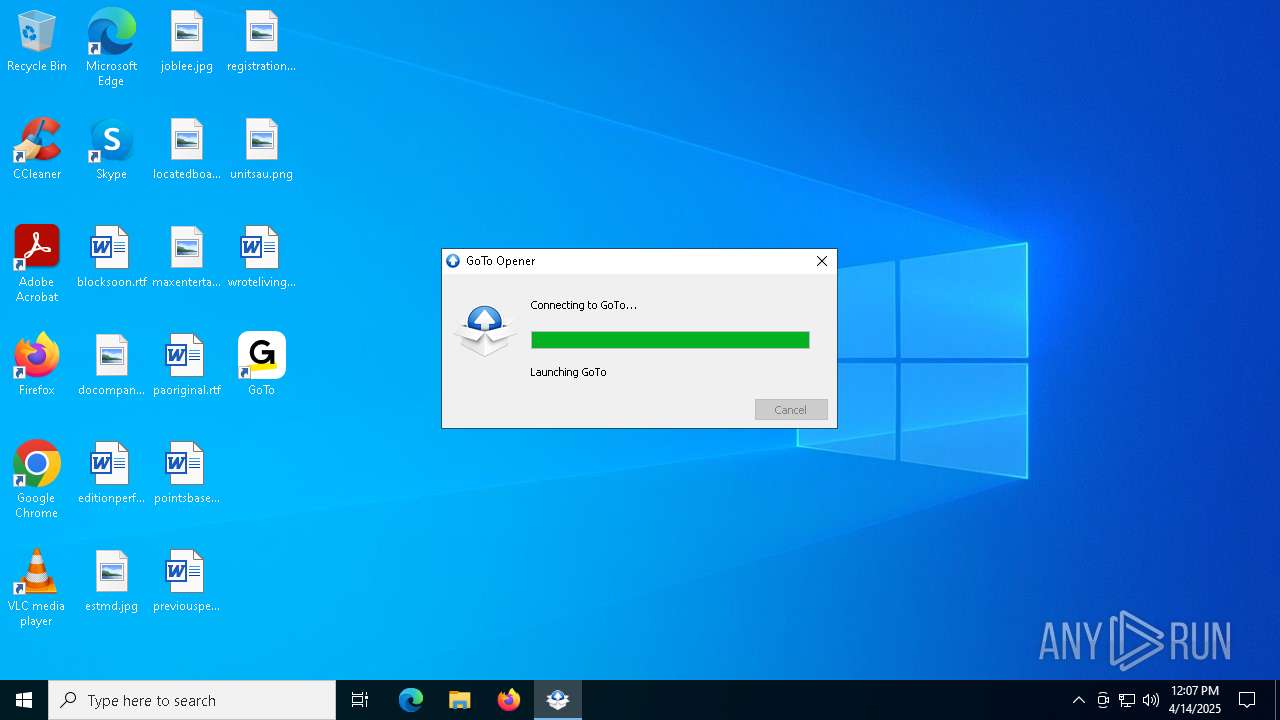
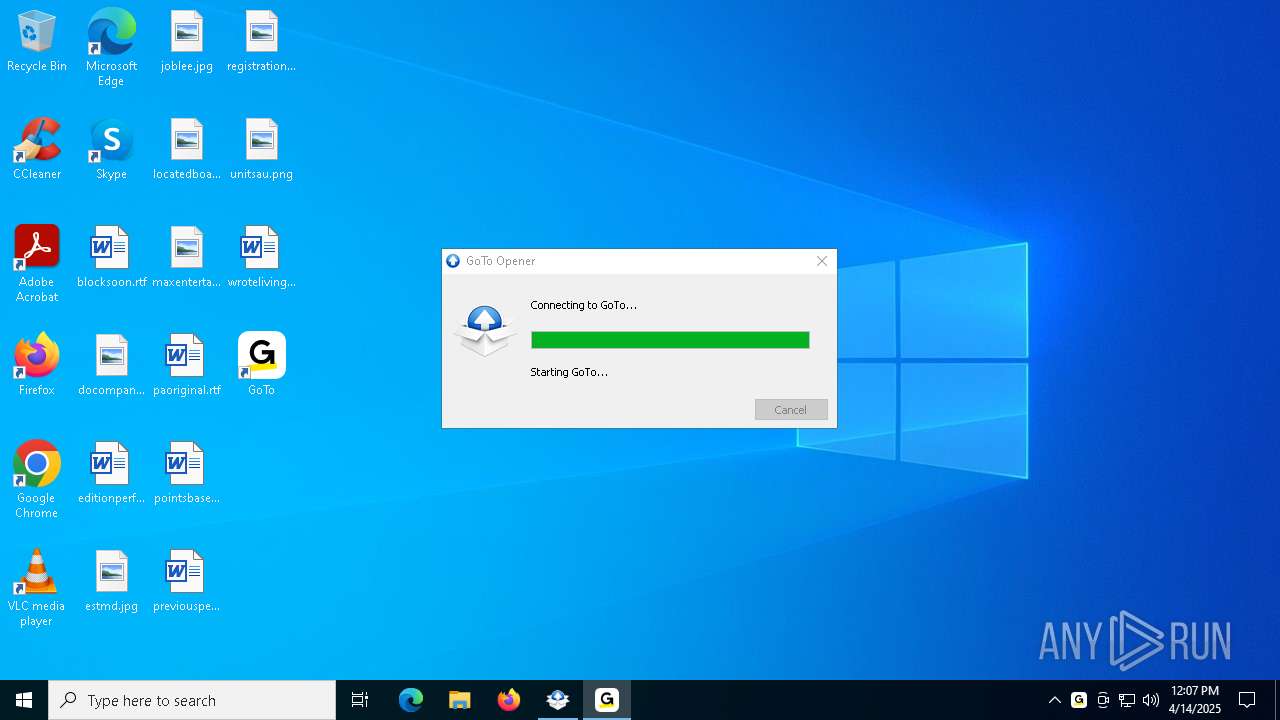
| File name: | GoToMeeting Opener.exe |
| Full analysis: | https://app.any.run/tasks/329c4680-d012-4233-8425-c1f4167d8f04 |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2025, 12:06:05 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | 276DF38F40788AB7DBA2BD96FF7D47D3 |
| SHA1: | C9FC1B9095F81DCAB019CF75371E42C531B65CE5 |
| SHA256: | 63ABAB66C5860CB8400FCB15249B9A24F0B59F61C19A151C17CDE00B441A1847 |
| SSDEEP: | 12288:qDr4xkGkHncbsvljTu8ebbFFomBmxgxK79rhBaMBV7h4BV9y1d8hSr:qDrSkGUncgvljTu8OFomBzKKy1d7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- GoToMeeting Opener.exe (PID: 2980)
Executable content was dropped or overwritten
- GoToMeeting Opener.exe (PID: 2980)
- GoToSetup.exe (PID: 5072)
There is functionality for taking screenshot (YARA)
- GoToMeeting Opener.exe (PID: 2980)
- GoToSetup.exe (PID: 5072)
Drops 7-zip archiver for unpacking
- GoToSetup.exe (PID: 5072)
Process drops legitimate windows executable
- GoToSetup.exe (PID: 5072)
The process drops C-runtime libraries
- GoToSetup.exe (PID: 5072)
Creates a software uninstall entry
- GoToSetup.exe (PID: 5072)
The process creates files with name similar to system file names
- GoToSetup.exe (PID: 5072)
Application launched itself
- GoTo.exe (PID: 5204)
Starts CMD.EXE for commands execution
- GoToMeeting Opener.exe (PID: 2980)
Executing commands from a ".bat" file
- GoToMeeting Opener.exe (PID: 2980)
INFO
Create files in a temporary directory
- GoToMeeting Opener.exe (PID: 2980)
- GoToSetup.exe (PID: 5072)
- GoTo.exe (PID: 5204)
Reads the computer name
- GoToMeeting Opener.exe (PID: 2980)
- GoTo.exe (PID: 5204)
- GoTo.exe (PID: 4880)
- GoTo.exe (PID: 2420)
The sample compiled with english language support
- GoToMeeting Opener.exe (PID: 2980)
- GoToSetup.exe (PID: 5072)
Checks proxy server information
- GoToMeeting Opener.exe (PID: 2980)
- GoTo.exe (PID: 5204)
Checks supported languages
- GoToMeeting Opener.exe (PID: 2980)
- GoTo.exe (PID: 5204)
- GoTo.exe (PID: 2616)
- GoTo.exe (PID: 4880)
- GoTo.exe (PID: 5304)
- GoTo.exe (PID: 2420)
Process checks whether UAC notifications are on
- GoToMeeting Opener.exe (PID: 2980)
GOTOASSIST has been detected
- GoToMeeting Opener.exe (PID: 2980)
- GoToSetup.exe (PID: 5072)
- GoTo.exe (PID: 4880)
- GoTo.exe (PID: 5204)
- GoTo.exe (PID: 2616)
- GoTo.exe (PID: 5304)
- GoTo.exe (PID: 2420)
Creates files or folders in the user directory
- GoToMeeting Opener.exe (PID: 2980)
- GoTo.exe (PID: 5204)
- GoToSetup.exe (PID: 5072)
- GoTo.exe (PID: 5304)
Reads the machine GUID from the registry
- GoToMeeting Opener.exe (PID: 2980)
- GoTo.exe (PID: 5204)
Reads the software policy settings
- GoToMeeting Opener.exe (PID: 2980)
- GoTo.exe (PID: 5204)
UPX packer has been detected
- GoToMeeting Opener.exe (PID: 2980)
Reads product name
- GoTo.exe (PID: 5204)
Reads Environment values
- GoTo.exe (PID: 5204)
Reads CPU info
- GoTo.exe (PID: 5204)
Reads the time zone
- GoTo.exe (PID: 5204)
Process checks computer location settings
- GoTo.exe (PID: 5204)
- GoTo.exe (PID: 2420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (30.7) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (30.1) |
| .exe | | | Win32 EXE Yoda's Crypter (29.5) |
| .exe | | | Win32 Executable (generic) (5) |
| .exe | | | Generic Win/DOS Executable (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:23 13:44:36+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 299008 |
| InitializedDataSize: | 73728 |
| UninitializedDataSize: | 839680 |
| EntryPoint: | 0x116040 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.568 |
| ProductVersionNumber: | 1.0.0.568 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | LogMeIn, Inc. |
| LegalCopyright: | Copyright © 2012-2024 LogMeIn, Inc. |
| ProductName: | GoTo Opener |
| FileDescription: | GoTo Opener |
| InternalName: | GoToOpener |
| OriginalFileName: | GoToOpener.exe |
| FileVersion: | 1.0.0.568 |
| ProductVersion: | 1.0.0.568 |
Total processes
141
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1272 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1300 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 1764 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\D5CB1B48-C052-4411-8378-BF63047AFB3C.bat" "C:\Users\admin\AppData\Local\Temp\GoToMeeting Opener.exe"" | C:\Windows\SysWOW64\cmd.exe | — | GoToMeeting Opener.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\AppData\Local\Programs\goto\GoTo.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\GoTo" --secure-schemes=sentry-ipc --bypasscsp-schemes=sentry-ipc --cors-schemes=sentry-ipc --fetch-schemes=sentry-ipc --app-user-model-id=GoTo --app-path="C:\Users\admin\AppData\Local\Programs\goto\resources\app.asar" --enable-sandbox --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --field-trial-handle=3056,i,16542837400297067535,16461797468144540207,262144 --enable-features=AudioWorkletThreadRealtimePriority --disable-features=ScreenCaptureKitStreamPickerVentura,SpareRendererForSitePerProcess,WebRtcHideLocalIpsWithMdns,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=2912 --env=production /prefetch:1 | C:\Users\admin\AppData\Local\Programs\goto\GoTo.exe | — | GoTo.exe | |||||||||||
User: admin Company: GoTo Group, Inc. Integrity Level: LOW Description: GoTo Version: 4.14.0.1 Modules
| |||||||||||||||
| 2616 | C:\Users\admin\AppData\Local\Programs\goto\GoTo.exe --type=crashpad-handler --user-data-dir=C:\Users\admin\AppData\Roaming\GoTo /prefetch:4 --no-rate-limit --monitor-self-annotation=ptype=crashpad-handler --database=C:\Users\admin\AppData\Roaming\GoTo\Crashpad --url=https://f.a.k/e --annotation=_productName=GoTo --annotation=_version=4.14.0 --annotation=plat=Win64 --annotation=prod=Electron --annotation=ver=33.2.0-3 --initial-client-data=0x5d4,0x5d8,0x5dc,0x5c8,0x5e0,0x7ff6194cb60c,0x7ff6194cb618,0x7ff6194cb628 | C:\Users\admin\AppData\Local\Programs\goto\GoTo.exe | — | GoTo.exe | |||||||||||
User: admin Company: GoTo Group, Inc. Integrity Level: MEDIUM Description: GoTo Version: 4.14.0.1 Modules
| |||||||||||||||
| 2980 | "C:\Users\admin\AppData\Local\Temp\GoToMeeting Opener.exe" | C:\Users\admin\AppData\Local\Temp\GoToMeeting Opener.exe | explorer.exe | ||||||||||||
User: admin Company: LogMeIn, Inc. Integrity Level: MEDIUM Description: GoTo Opener Exit code: 0 Version: 1.0.0.568 Modules
| |||||||||||||||
| 4880 | "C:\Users\admin\AppData\Local\Programs\goto\GoTo.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\GoTo" --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=2172,i,16542837400297067535,16461797468144540207,262144 --enable-features=AudioWorkletThreadRealtimePriority --disable-features=ScreenCaptureKitStreamPickerVentura,SpareRendererForSitePerProcess,WebRtcHideLocalIpsWithMdns,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=2156 /prefetch:2 | C:\Users\admin\AppData\Local\Programs\goto\GoTo.exe | — | GoTo.exe | |||||||||||
User: admin Company: GoTo Group, Inc. Integrity Level: LOW Description: GoTo Version: 4.14.0.1 Modules
| |||||||||||||||
| 5072 | "C:\Users\admin\AppData\Local\Temp\35A32094-E3D5-45EC-89B7-A204457D5CD0\GoToSetup.exe" /S | C:\Users\admin\AppData\Local\Temp\35A32094-E3D5-45EC-89B7-A204457D5CD0\GoToSetup.exe | GoToMeeting Opener.exe | ||||||||||||
User: admin Company: GoTo Group, Inc. Integrity Level: MEDIUM Description: GoTo desktop app Exit code: 0 Version: 4.14.0.1 Modules
| |||||||||||||||
Total events
49 958
Read events
49 915
Write events
25
Delete events
18
Modification events
| (PID) Process: | (2980) GoToMeeting Opener.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\LogMeInInc\GoTo Opener |
| Operation: | write | Name: | UUID |
Value: {F7179F54-D7A7-4675-8183-720520D6B7C6} | |||
| (PID) Process: | (2980) GoToMeeting Opener.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2980) GoToMeeting Opener.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2980) GoToMeeting Opener.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5072) GoToSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\LogMeInInc\GoTo\ElectronInstallDetails |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\Programs\goto | |||
| (PID) Process: | (5072) GoToSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\LogMeInInc\GoTo\ElectronInstallDetails |
| Operation: | write | Name: | KeepShortcuts |
Value: true | |||
| (PID) Process: | (5072) GoToSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\LogMeInInc\GoTo\ElectronInstallDetails |
| Operation: | write | Name: | ShortcutName |
Value: GoTo | |||
| (PID) Process: | (5072) GoToSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\b5746384-3503-4fbf-824a-0a42d1bd0639 |
| Operation: | write | Name: | DisplayName |
Value: GoTo 4.14.0 | |||
| (PID) Process: | (5072) GoToSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\b5746384-3503-4fbf-824a-0a42d1bd0639 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Users\admin\AppData\Local\Programs\goto\Uninstall GoTo.exe" /currentuser | |||
| (PID) Process: | (5072) GoToSetup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\b5746384-3503-4fbf-824a-0a42d1bd0639 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Users\admin\AppData\Local\Programs\goto\Uninstall GoTo.exe" /currentuser /S | |||
Executable files
63
Suspicious files
720
Text files
98
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5072 | GoToSetup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\goto-4.14.0-x64.nsis[1].7z | — | |
MD5:— | SHA256:— | |||
| 5072 | GoToSetup.exe | C:\Users\admin\AppData\Local\Temp\nshBCDA.tmp\package.7z | — | |
MD5:— | SHA256:— | |||
| 5072 | GoToSetup.exe | C:\Users\admin\AppData\Local\Temp\nshBCDA.tmp\7z-out\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 5072 | GoToSetup.exe | C:\Users\admin\AppData\Local\Temp\nshBCDA.tmp\7z-out\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 2980 | GoToMeeting Opener.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:8325C7907AD1340FBB951DFA5AB41304 | SHA256:62D528B4387F816D56EF14159836095ED933036762E2B338B50CE2FFDC73267C | |||
| 2980 | GoToMeeting Opener.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\59D76868C250B3240414CE3EFBB12518_92613D624E32A075FF5B57BD469359EB | binary | |
MD5:76FD587BC76A82842BAAB0AC7AB6FBD7 | SHA256:AE8BD072D8B5DF24AD06E6B8B6F7FB7CC2F28DDC15ED94623804C7D5939660D0 | |||
| 2980 | GoToMeeting Opener.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_056B48C93C4964C2E64C0A8958238656 | binary | |
MD5:7D6496483CF9777E5DAF416E9C590682 | SHA256:46DD8CC56121CAA7572A32F0091B91170D52AC5EB09119698B5BBECEE43A986C | |||
| 2980 | GoToMeeting Opener.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_49536AB5156BDD74EFF881D01C36A419 | binary | |
MD5:C6BA353A011833581502174BAABB1FC1 | SHA256:F65D8870B04858D40C656E38092EABE431CF06281AAAA6B346E6633A8A3D754D | |||
| 5072 | GoToSetup.exe | C:\Users\admin\AppData\Local\Temp\nshBCDA.tmp\7z-out\electron.d.ts | text | |
MD5:208B98EC77CF3648DBF19FD48D8850EC | SHA256:E52724E976508DE72A04E2162F964AF6011C2A88E1233E010C8C39773576F3F3 | |||
| 2980 | GoToMeeting Opener.exe | C:\Users\admin\AppData\Local\Temp\C3E9F120-8EC5-4C44-9273-DA8B0226B00B\GoTo Opener.exe | executable | |
MD5:D28494052AC3206DDB3E6A1D0AE4C186 | SHA256:1946F1AF5A374CC1F1935DEFF5EB9AB611921A4F64FCEEAA1430E929E1015EB4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
46
DNS requests
51
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAjegkJ27mLaGBP72%2FEoqPs%3D | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5204 | GoTo.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnxLiz3Fu1WB6n1%2FE6xWn1b0jXiQQUdIWAwGbH3zfez70pN6oDHb7tzRcCEAOz8rqxAGy%2FDjpS8efkRh8%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2980 | GoToMeeting Opener.exe | GET | 200 | 18.66.145.213:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkpLy9ROx7U76vGUhC06D6E%3D | unknown | — | — | whitelisted |
2980 | GoToMeeting Opener.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnxLiz3Fu1WB6n1%2FE6xWn1b0jXiQQUdIWAwGbH3zfez70pN6oDHb7tzRcCEAn8rBVjddlhALZWk5%2B5xig%3D | unknown | — | — | whitelisted |
2980 | GoToMeeting Opener.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | whitelisted |
2980 | GoToMeeting Opener.exe | GET | 200 | 18.66.145.213:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2980 | GoToMeeting Opener.exe | 150.136.248.95:443 | launchstatus.getgo.com | ORACLE-BMC-31898 | US | whitelisted |
2980 | GoToMeeting Opener.exe | 18.245.86.29:443 | meet.servers.getgo.com | — | US | whitelisted |
2980 | GoToMeeting Opener.exe | 18.66.145.213:80 | ocsp.rootca1.amazontrust.com | AMAZON-02 | US | whitelisted |
2980 | GoToMeeting Opener.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2980 | GoToMeeting Opener.exe | 3.161.82.75:443 | goto-desktop.getgo.com | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
launchstatus.getgo.com |
| whitelisted |
meet.servers.getgo.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
goto-desktop.getgo.com |
| whitelisted |
goto-desktop.goto.com |
| malicious |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5304 | GoTo.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
5304 | GoTo.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
5304 | GoTo.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
5304 | GoTo.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
5304 | GoTo.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
5304 | GoTo.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
5304 | GoTo.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
5304 | GoTo.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
5304 | GoTo.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |