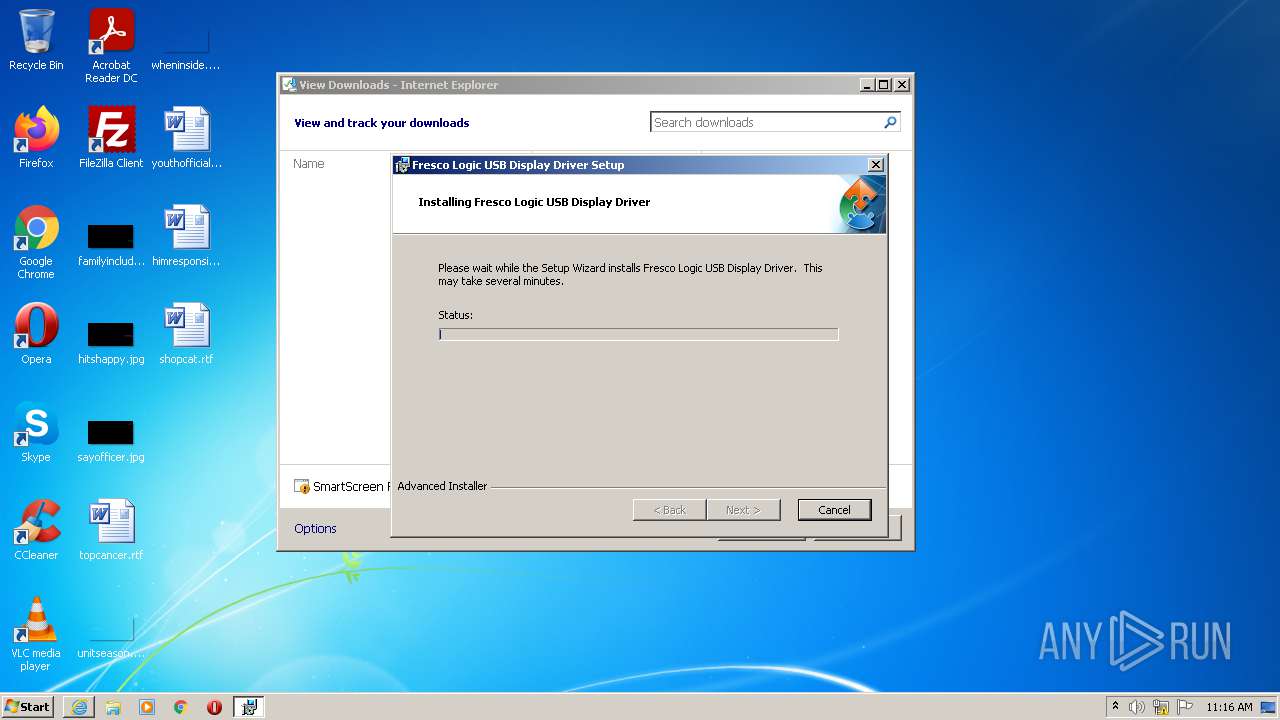
| URL: | http://updates.frescologic.com/FL2000/FL2000-2.1.34054.0.exe |
| Full analysis: | https://app.any.run/tasks/858efbd5-dddb-48d1-8075-4d4a68d3e077 |
| Verdict: | Malicious activity |
| Analysis date: | August 03, 2021, 10:15:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 934A0B124B1DED19DB42F003BDF34134 |
| SHA1: | 90EAF88E56A0A17B735C563C5A324B2373003B0C |
| SHA256: | 63A7016F52AA98E80C6D15FFEE63D6B5CA53CAB0A0A71DF5AE932E95CEDDC0F4 |
| SSDEEP: | 3:N1KLQRAMDXxJZM6lGcPgVJ:CUdLxY0YVJ |
MALICIOUS
Application was dropped or rewritten from another process
- FL2000-2.1.34054.0.exe (PID: 3136)
- FL2000-2.1.34054.0.exe (PID: 3924)
- devcon.exe (PID: 2228)
- devcon.exe (PID: 4024)
- flvga_tray.exe (PID: 2564)
- devcon.exe (PID: 2624)
Drops executable file immediately after starts
- DrvInst.exe (PID: 2396)
- DrvInst.exe (PID: 3472)
- DrvInst.exe (PID: 876)
- xcopy.exe (PID: 2576)
- MsiExec.exe (PID: 2392)
Changes the autorun value in the registry
- msiexec.exe (PID: 3320)
Executes PowerShell scripts
- cmd.exe (PID: 3668)
- cmd.exe (PID: 2716)
Loads the Task Scheduler DLL interface
- FL2000-2.1.34054.0.exe (PID: 3924)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1568)
Drops a file that was compiled in debug mode
- iexplore.exe (PID: 1568)
- iexplore.exe (PID: 3372)
- msiexec.exe (PID: 3096)
- msiexec.exe (PID: 3320)
- DrvInst.exe (PID: 2396)
- MsiExec.exe (PID: 2392)
- DrvInst.exe (PID: 3472)
- DrvInst.exe (PID: 876)
- xcopy.exe (PID: 2576)
Reads the computer name
- FL2000-2.1.34054.0.exe (PID: 3924)
- DrvInst.exe (PID: 3472)
- DrvInst.exe (PID: 876)
- powershell.exe (PID: 3912)
- powershell.exe (PID: 2604)
- devcon.exe (PID: 2228)
- DrvInst.exe (PID: 3612)
- devcon.exe (PID: 4024)
- flvga_tray.exe (PID: 2564)
- DrvInst.exe (PID: 2396)
- devcon.exe (PID: 2624)
Executable content was dropped or overwritten
- iexplore.exe (PID: 1568)
- iexplore.exe (PID: 3372)
- FL2000-2.1.34054.0.exe (PID: 3924)
- msiexec.exe (PID: 3096)
- msiexec.exe (PID: 3320)
- DrvInst.exe (PID: 2396)
- MsiExec.exe (PID: 2392)
- DrvInst.exe (PID: 3472)
- DrvInst.exe (PID: 876)
- xcopy.exe (PID: 2576)
Checks supported languages
- FL2000-2.1.34054.0.exe (PID: 3924)
- DrvInst.exe (PID: 2396)
- DrvInst.exe (PID: 3472)
- DrvInst.exe (PID: 876)
- cmd.exe (PID: 2052)
- powershell.exe (PID: 3912)
- cmd.exe (PID: 3668)
- powershell.exe (PID: 2604)
- cmd.exe (PID: 2716)
- devcon.exe (PID: 2228)
- devcon.exe (PID: 4024)
- DrvInst.exe (PID: 3612)
- devcon.exe (PID: 2624)
- flvga_tray.exe (PID: 2564)
Creates files in the user directory
- FL2000-2.1.34054.0.exe (PID: 3924)
- powershell.exe (PID: 3912)
- powershell.exe (PID: 2604)
Reads Environment values
- FL2000-2.1.34054.0.exe (PID: 3924)
- vssvc.exe (PID: 2472)
Executed as Windows Service
- msiexec.exe (PID: 3320)
- vssvc.exe (PID: 2472)
Reads Windows owner or organization settings
- msiexec.exe (PID: 3096)
- msiexec.exe (PID: 3320)
Application launched itself
- msiexec.exe (PID: 3320)
- cmd.exe (PID: 2052)
Reads the Windows organization settings
- msiexec.exe (PID: 3096)
- msiexec.exe (PID: 3320)
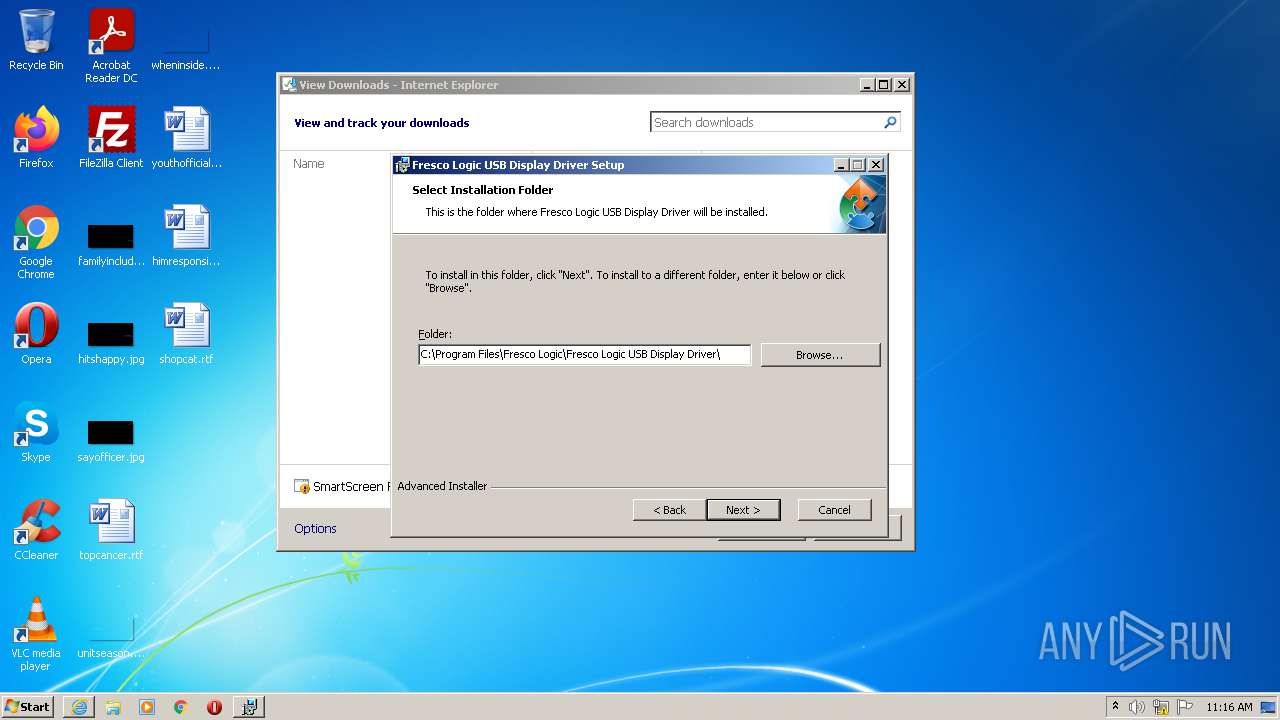
Creates a directory in Program Files
- msiexec.exe (PID: 3320)
Drops a file with too old compile date
- msiexec.exe (PID: 3320)
- MsiExec.exe (PID: 2392)
Creates files in the program directory
- msiexec.exe (PID: 3320)
Removes files from Windows directory
- DrvInst.exe (PID: 2396)
- DrvInst.exe (PID: 3472)
- DrvInst.exe (PID: 876)
- DrvInst.exe (PID: 3612)
Searches for installed software
- msiexec.exe (PID: 3320)
Creates files in the driver directory
- DrvInst.exe (PID: 2396)
- DrvInst.exe (PID: 3472)
- DrvInst.exe (PID: 876)
- DrvInst.exe (PID: 3612)
Creates a software uninstall entry
- MsiExec.exe (PID: 2392)
- msiexec.exe (PID: 3320)
Executed via COM
- DrvInst.exe (PID: 3472)
- DrvInst.exe (PID: 876)
- DrvInst.exe (PID: 3612)
- DrvInst.exe (PID: 2396)
Creates files in the Windows directory
- DrvInst.exe (PID: 3472)
- DrvInst.exe (PID: 876)
- xcopy.exe (PID: 2576)
- DrvInst.exe (PID: 3612)
- DrvInst.exe (PID: 2396)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 3320)
- cmd.exe (PID: 2052)
Starts SC.EXE for service management
- cmd.exe (PID: 2052)
Reads the date of Windows installation
- powershell.exe (PID: 3912)
- powershell.exe (PID: 2604)
INFO
Checks supported languages
- iexplore.exe (PID: 3372)
- iexplore.exe (PID: 1568)
- msiexec.exe (PID: 3096)
- msiexec.exe (PID: 3320)
- MsiExec.exe (PID: 120)
- MsiExec.exe (PID: 2164)
- vssvc.exe (PID: 2472)
- MsiExec.exe (PID: 2392)
- xcopy.exe (PID: 2576)
- sc.exe (PID: 2672)
- sc.exe (PID: 2776)
- taskmgr.exe (PID: 2512)
- timeout.exe (PID: 2168)
Changes internet zones settings
- iexplore.exe (PID: 3372)
Reads the computer name
- iexplore.exe (PID: 3372)
- iexplore.exe (PID: 1568)
- msiexec.exe (PID: 3096)
- msiexec.exe (PID: 3320)
- MsiExec.exe (PID: 120)
- vssvc.exe (PID: 2472)
- MsiExec.exe (PID: 2164)
- MsiExec.exe (PID: 2392)
- sc.exe (PID: 2776)
- sc.exe (PID: 2672)
- taskmgr.exe (PID: 2512)
Reads the date of Windows installation
- iexplore.exe (PID: 3372)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3372)
Checks Windows Trust Settings
- iexplore.exe (PID: 3372)
- msiexec.exe (PID: 3096)
- msiexec.exe (PID: 3320)
- DrvInst.exe (PID: 2396)
- DrvInst.exe (PID: 3472)
- DrvInst.exe (PID: 876)
- DrvInst.exe (PID: 3612)
- devcon.exe (PID: 4024)
Application launched itself
- iexplore.exe (PID: 3372)
Reads settings of System Certificates
- iexplore.exe (PID: 3372)
- msiexec.exe (PID: 3096)
- msiexec.exe (PID: 3320)
- DrvInst.exe (PID: 2396)
- DrvInst.exe (PID: 3472)
- DrvInst.exe (PID: 876)
- devcon.exe (PID: 4024)
- DrvInst.exe (PID: 3612)
Manual execution by user
- taskmgr.exe (PID: 2512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
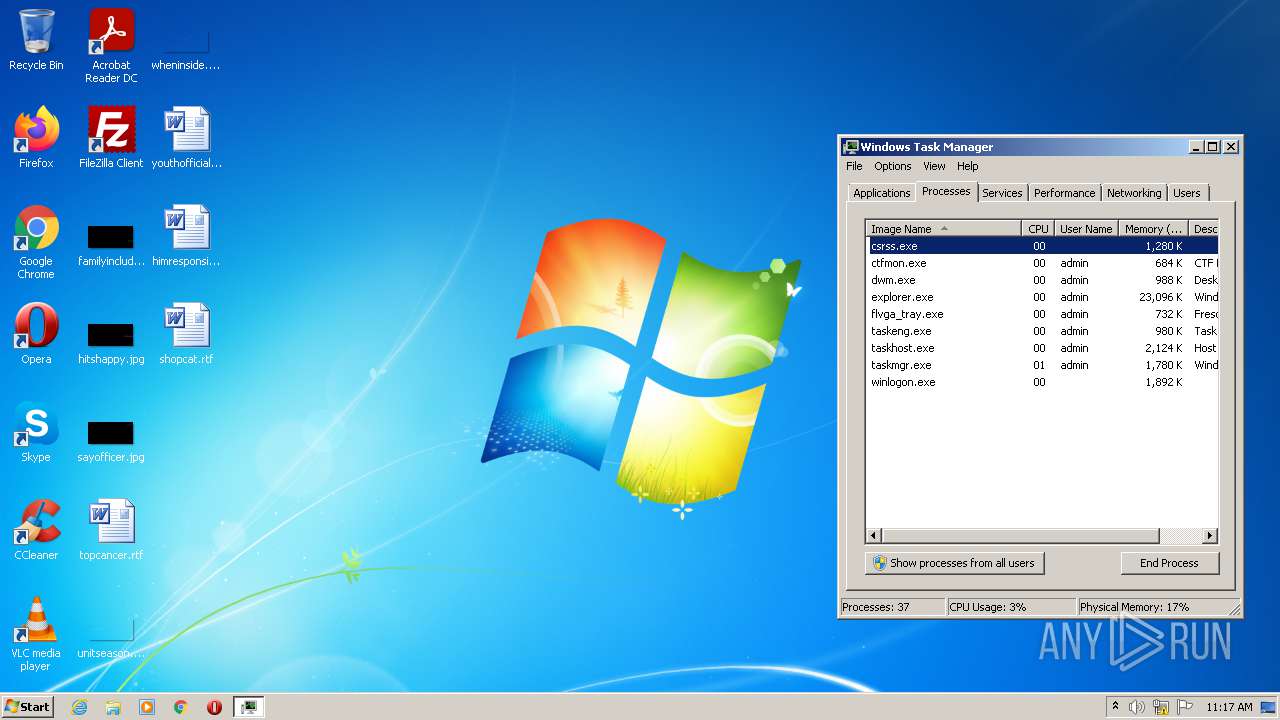
Total processes
69
Monitored processes
28
Malicious processes
11
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | C:\Windows\system32\MsiExec.exe -Embedding D086B127272424D78927F817A7290553 C | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
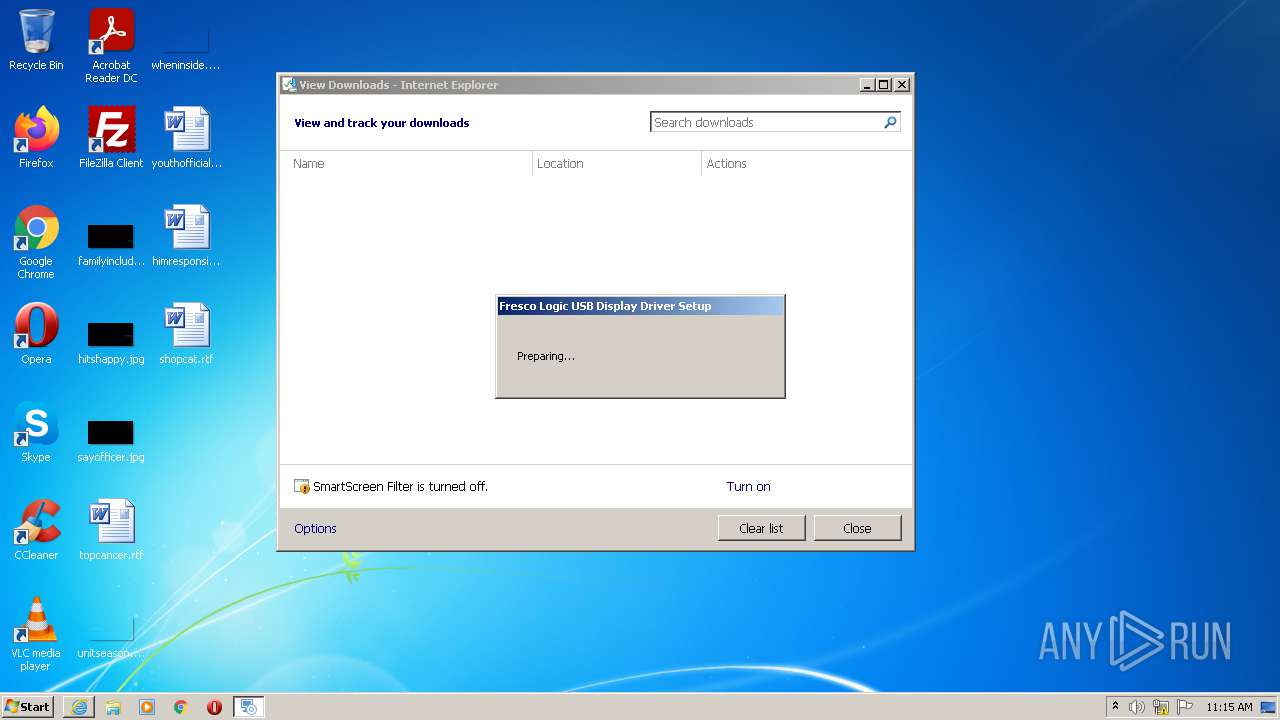
| 876 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{0e46b115-1c46-17df-03dc-357fa9164674}\fresco_iddcx.inf" "0" "61394d9b3" "000005D0" "WinSta0\Default" "00000574" "208" "C:\Program Files\Fresco Logic\Fresco Logic USB Display Driver\fresco_iddcx" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1568 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3372 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2052 | C:\Windows\system32\cmd.exe /c ""C:\Program Files\Fresco Logic\Fresco Logic USB Display Driver\post_install.cmd"" | C:\Windows\system32\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2164 | C:\Windows\system32\MsiExec.exe -Embedding E12EBBC05E0FE84E8C9FE95FC95CFC18 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2168 | timeout /t 1 /nobreak | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2228 | .\devcon\x86\devcon.exe disable =Display | C:\Program Files\Fresco Logic\Fresco Logic USB Display Driver\devcon\x86\devcon.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Setup API Exit code: 1 Version: 10.0.14393.0 (rs1_release.160715-1616) Modules
| |||||||||||||||
| 2392 | C:\Windows\system32\MsiExec.exe -Embedding A17DA7B259C252B6CFCE767100A86E74 E Global\MSI0000 | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2396 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{30b8af2a-e698-7708-020a-bb412aafb830}\FL2000.inf" "0" "6c2ff297b" "000005CC" "WinSta0\Default" "00000544" "208" "C:\Program Files\Fresco Logic\Fresco Logic USB Display Driver\FL2000" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2472 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft� Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
33 776
Read events
33 103
Write events
644
Delete events
29
Modification events
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30902352 | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30902352 | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3372) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
63
Suspicious files
44
Text files
14
Unknown types
33
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
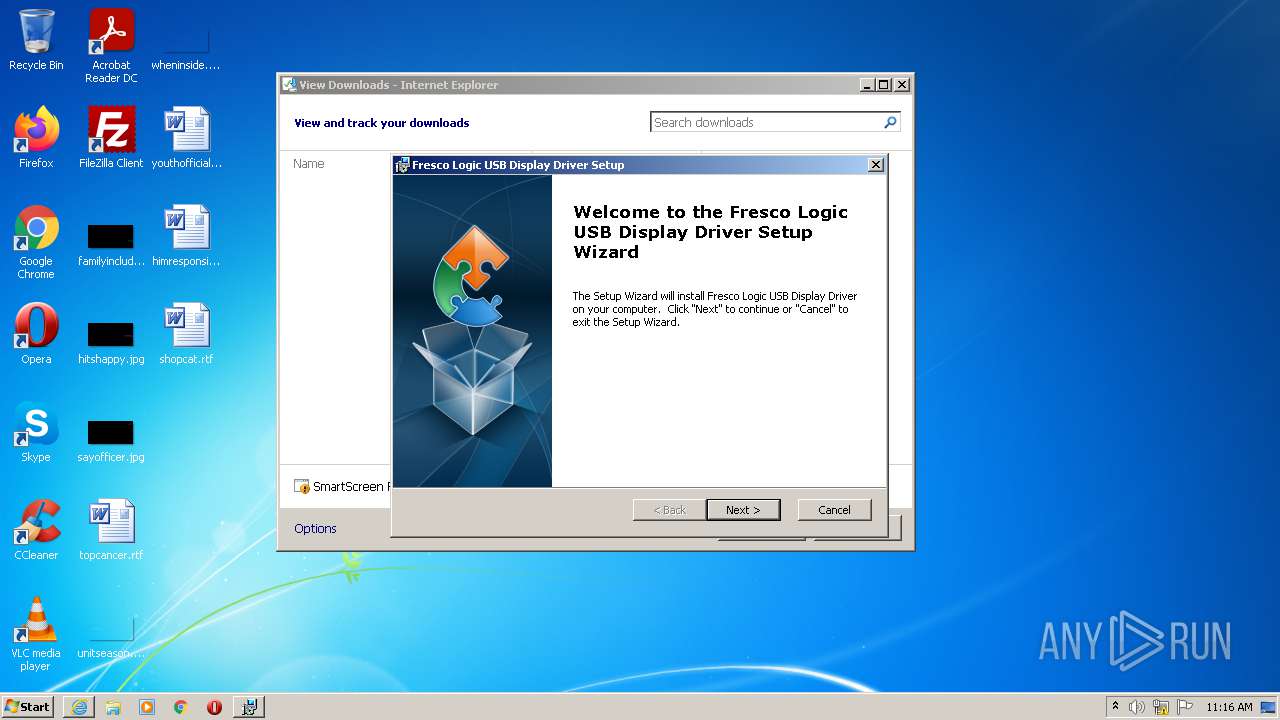
| 3924 | FL2000-2.1.34054.0.exe | C:\Users\admin\AppData\Roaming\Fresco Logic\Fresco Logic USB Display Driver 2.1.34054.0\install\holder0.aiph | — | |
MD5:— | SHA256:— | |||
| 1568 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\FL2000-2.1.34054.0[1].exe | executable | |
MD5:— | SHA256:— | |||
| 3372 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{C4A992D8-F443-11EB-A15C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 3320 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3372 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF6B4FF791FE20C0A8.TMP | gmc | |
MD5:— | SHA256:— | |||
| 3924 | FL2000-2.1.34054.0.exe | C:\Users\admin\AppData\Local\Temp\tinE752.tmp | html | |
MD5:— | SHA256:— | |||
| 3924 | FL2000-2.1.34054.0.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\EBEOVIAY.txt | text | |
MD5:— | SHA256:— | |||
| 3924 | FL2000-2.1.34054.0.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\60Y648D5.txt | text | |
MD5:— | SHA256:— | |||
| 3924 | FL2000-2.1.34054.0.exe | C:\Users\admin\AppData\Local\Temp\tinE752.tmp.part | html | |
MD5:— | SHA256:— | |||
| 1568 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\78RFYB7Z\FL2000-2.1.34054.0.exe.m2j3e0q.partial | executable | |
MD5:18B0139CA76E7447BC64F9A812F4A9F2 | SHA256:5E0590D6DCCC198B427C7C51CA5CC50448C2D4AAAE275322B1378D78058750E7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
16
DNS requests
9
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3924 | FL2000-2.1.34054.0.exe | GET | 200 | 172.217.18.100:80 | http://www.google.com/ | US | html | 13.6 Kb | malicious |
3372 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
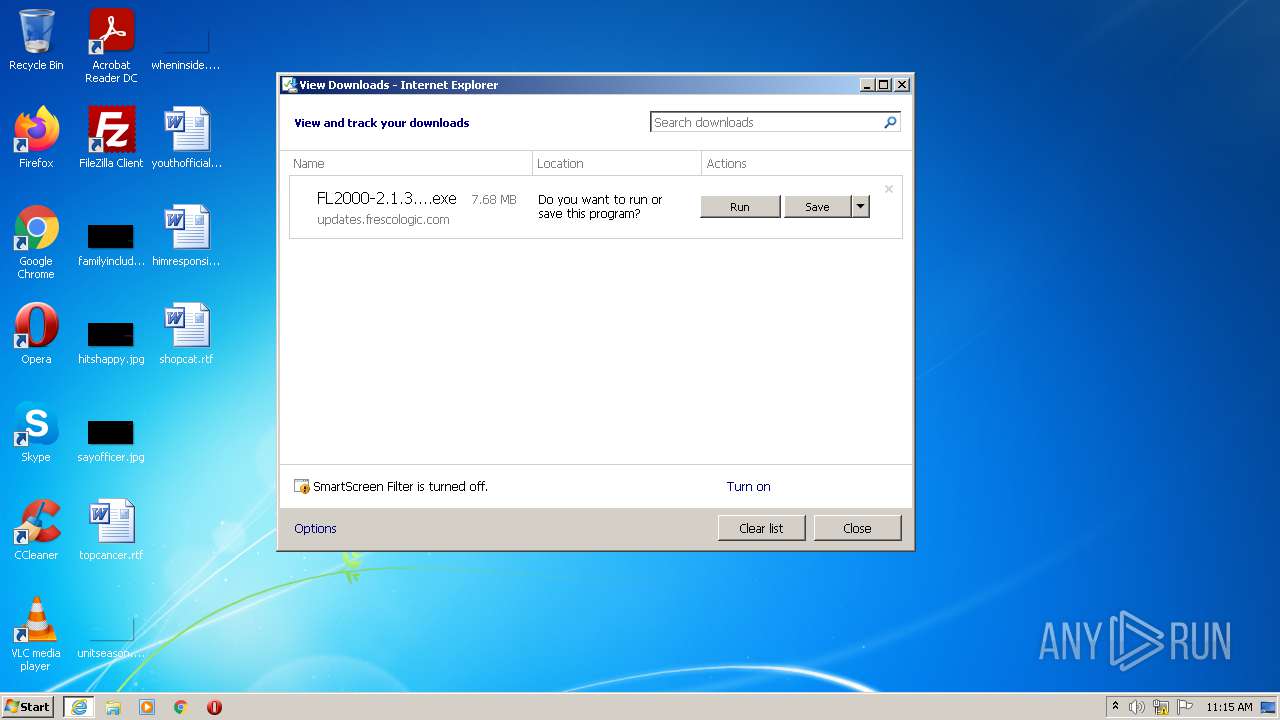
1568 | iexplore.exe | GET | 200 | 52.218.221.155:80 | http://updates.frescologic.com/FL2000/FL2000-2.1.34054.0.exe | US | executable | 7.69 Mb | shared |
3372 | iexplore.exe | GET | 200 | 2.16.186.89:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?cf4b7aa6a1e0fa15 | unknown | compressed | 4.70 Kb | whitelisted |
3372 | iexplore.exe | GET | 200 | 2.16.186.89:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2d9a1cfa2a755b44 | unknown | compressed | 4.70 Kb | whitelisted |
3372 | iexplore.exe | GET | 200 | 2.16.186.89:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c8d4d2aacb6de78d | unknown | compressed | 4.70 Kb | whitelisted |
3924 | FL2000-2.1.34054.0.exe | GET | 200 | 52.92.164.233:80 | http://updates.frescologic.com/FL2000/FL2000_Updates.txt | US | text | 1.79 Kb | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3372 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3372 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1568 | iexplore.exe | 52.218.221.155:80 | updates.frescologic.com | Amazon.com, Inc. | US | suspicious |
3372 | iexplore.exe | 2.16.186.89:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
— | — | 20.73.194.208:443 | — | — | US | whitelisted |
1360 | svchost.exe | 20.73.194.208:443 | — | — | US | whitelisted |
3924 | FL2000-2.1.34054.0.exe | 52.92.164.233:80 | updates.frescologic.com | — | US | malicious |
3924 | FL2000-2.1.34054.0.exe | 172.217.18.100:80 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
updates.frescologic.com |
| shared |
www.google.com |
| malicious |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1568 | iexplore.exe | Potentially Bad Traffic | ET POLICY Executable served from Amazon S3 |
1568 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2 ETPRO signatures available at the full report