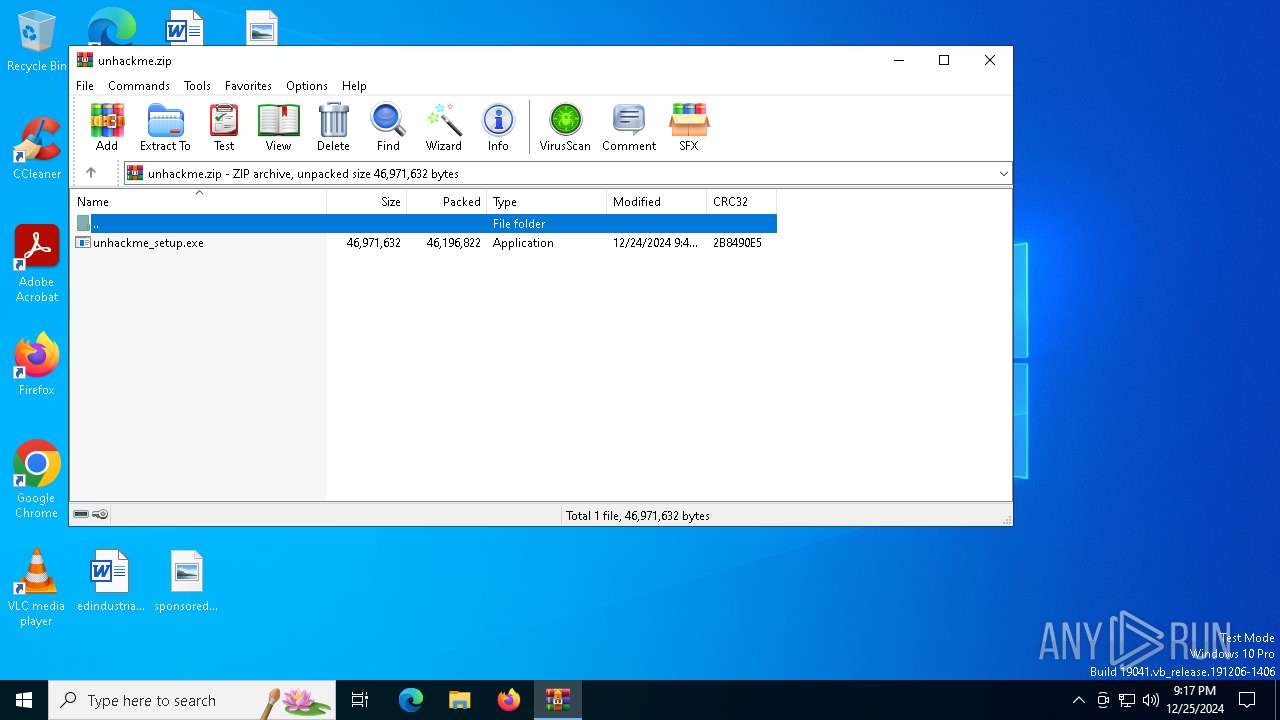
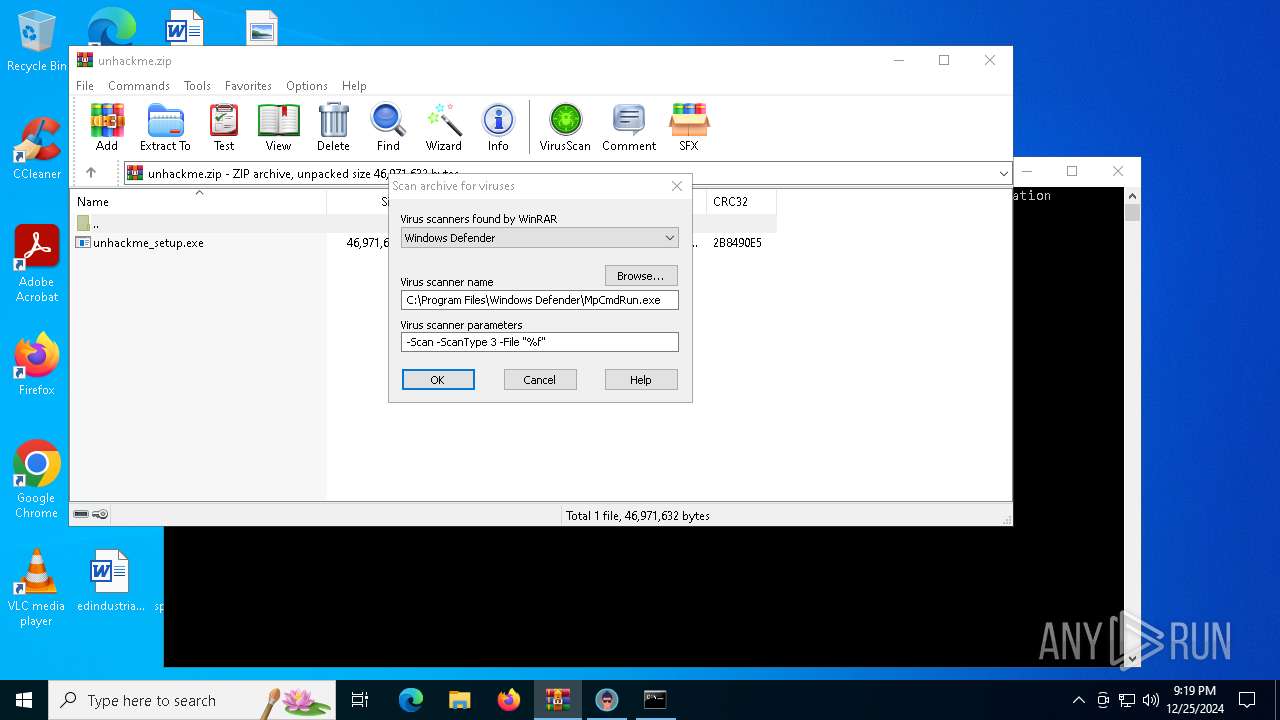
| File name: | unhackme.zip |
| Full analysis: | https://app.any.run/tasks/99f54db2-c3b9-409d-a64a-df433b4443e0 |
| Verdict: | Malicious activity |
| Analysis date: | December 25, 2024, 21:17:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 8FCF0B5D78C422BC2AEEEF5A565D5D5E |
| SHA1: | 983EF7306967D14907577706A75F34023CDEE2C9 |
| SHA256: | 63A6454805E4A7458A46B122983D61397738C10E3F025CE9E10D9450565BBD43 |
| SSDEEP: | 393216:3XGDNHaZRuZhMD7KAZPIXTWj+Yz9TIa1+YBZLbb59fUWIHfvmBtvImZ1ec1v+T:3WgRAhYd5f1rZ3XoWrZUDT |
MALICIOUS
Generic archive extractor
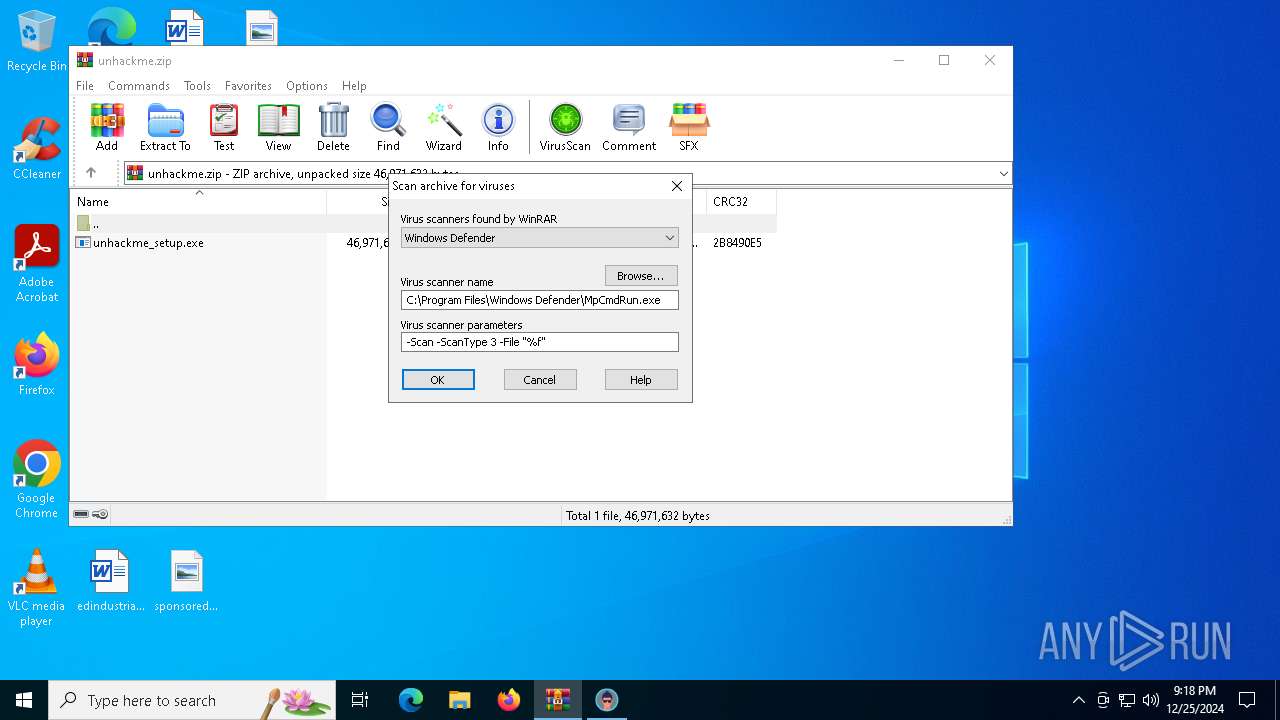
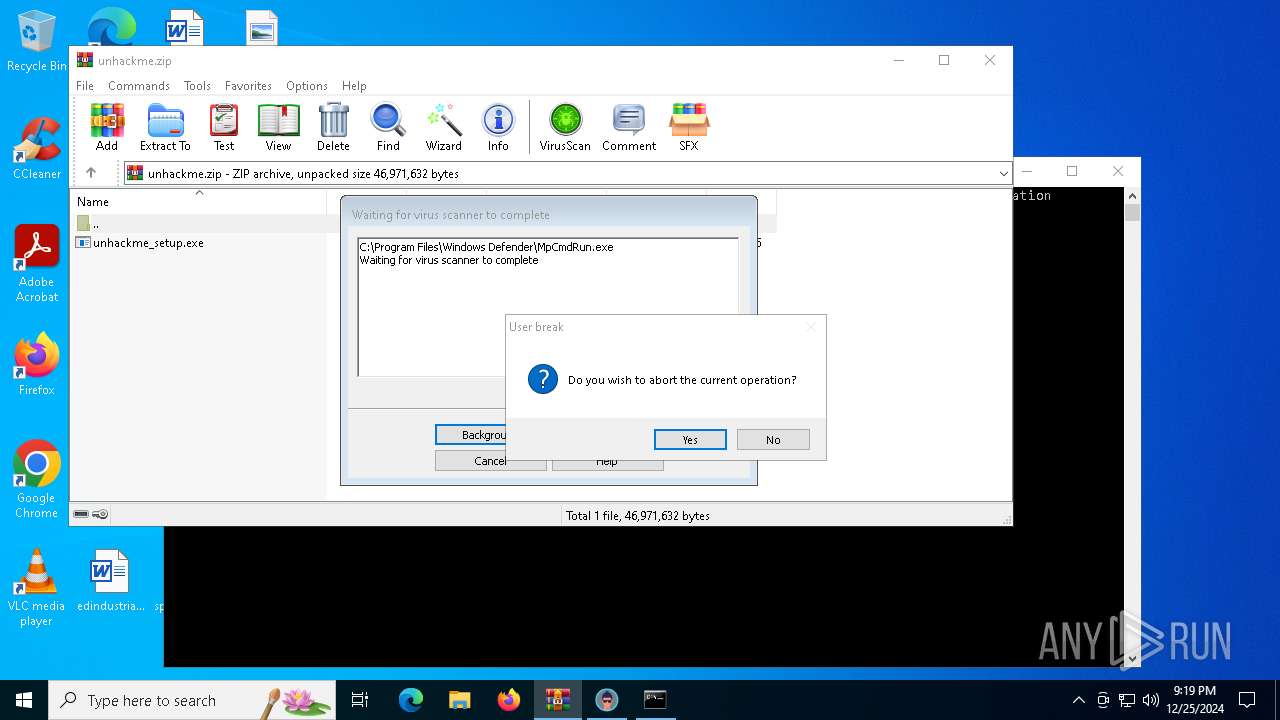
- WinRAR.exe (PID: 5564)
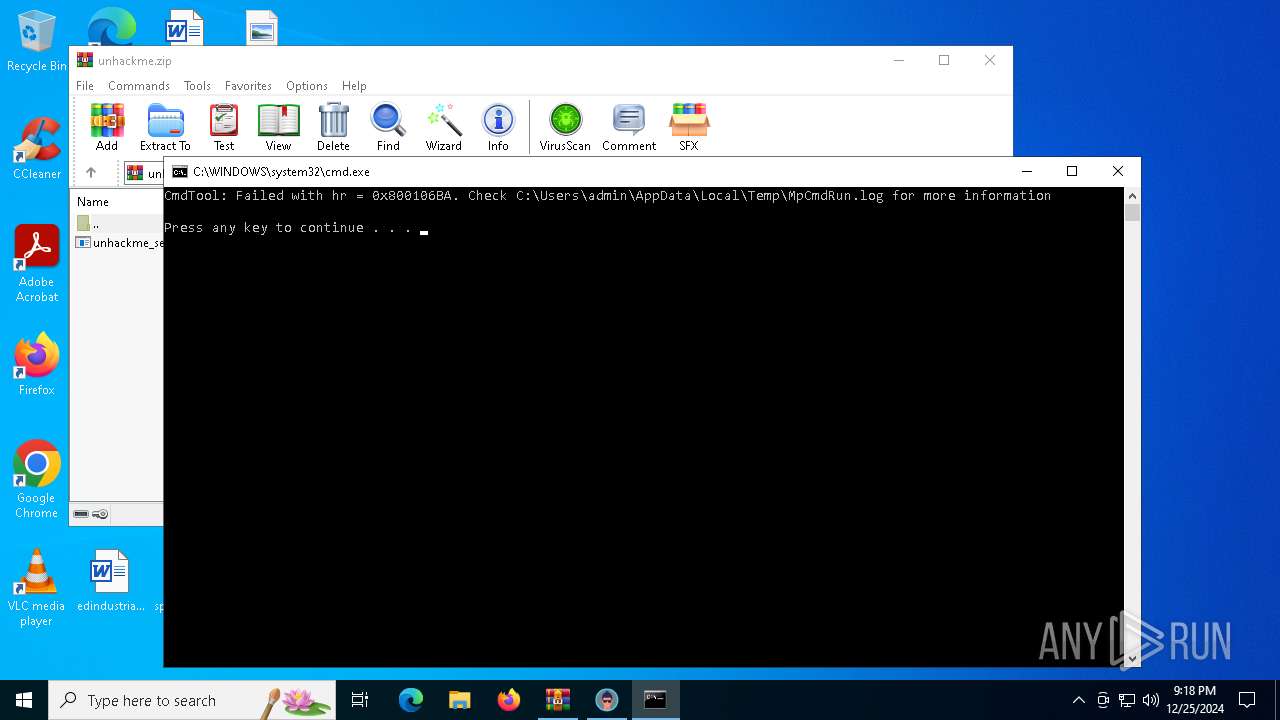
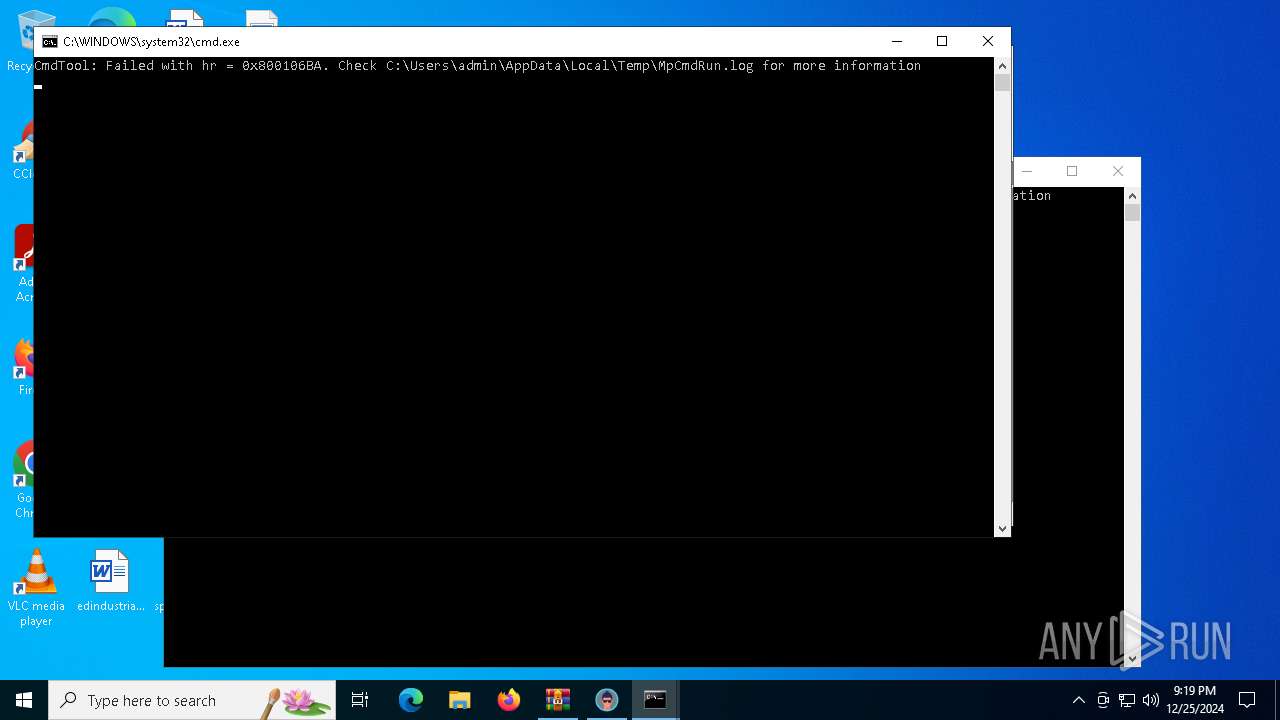
Antivirus name has been found in the command line (generic signature)
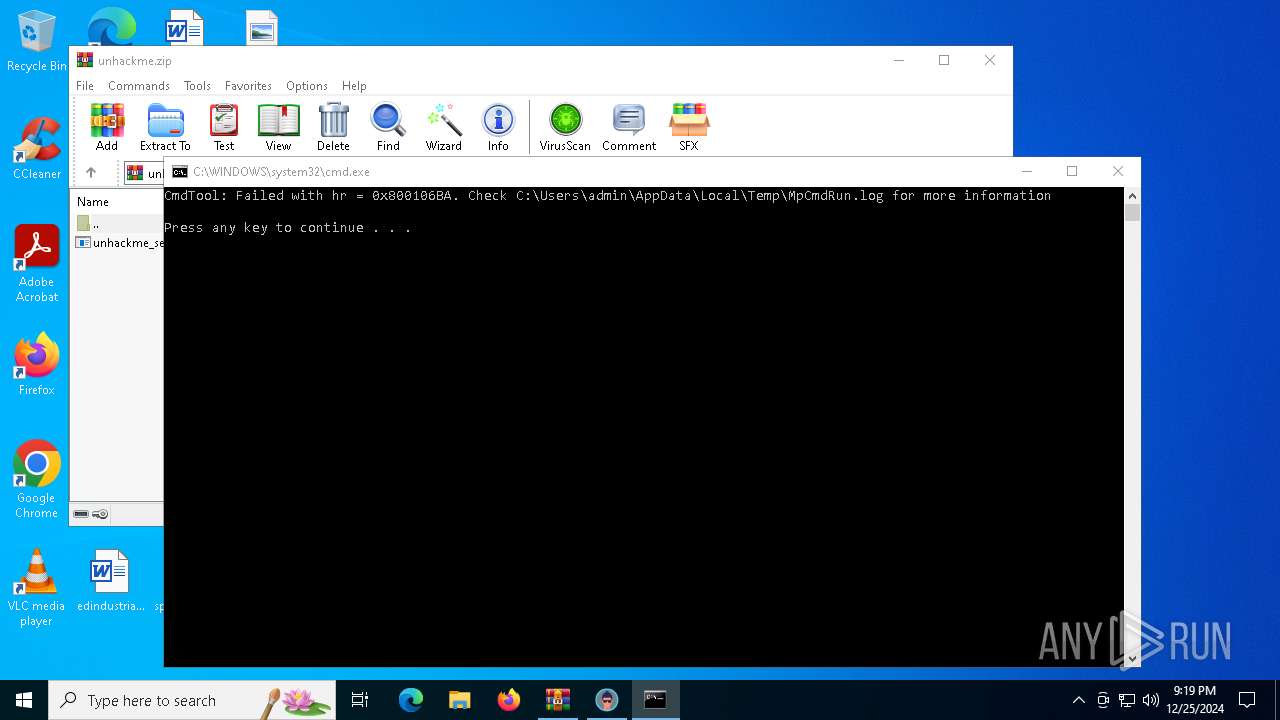
- MpCmdRun.exe (PID: 6012)
- MpCmdRun.exe (PID: 5988)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5564)
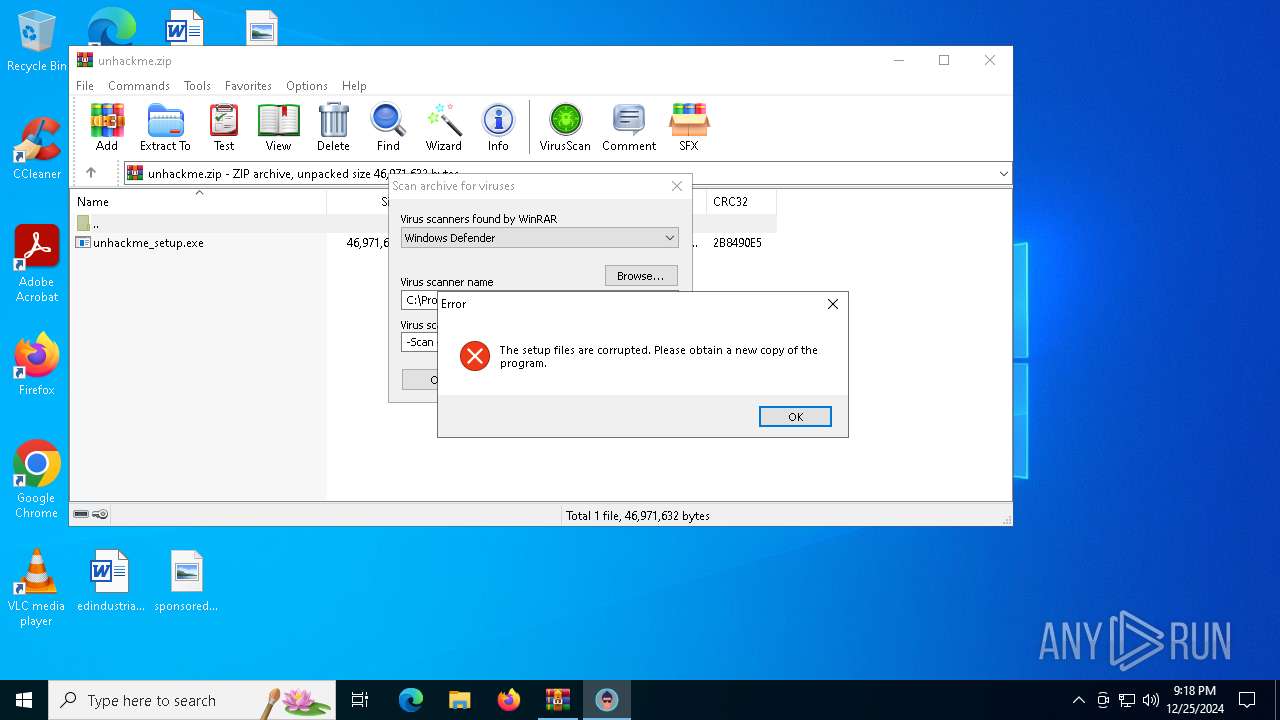
Executing commands from a ".bat" file
- WinRAR.exe (PID: 5564)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 5564)
INFO
Manual execution by a user
- unhackme_setup.exe (PID: 3524)
Checks supported languages
- unhackme_setup.exe (PID: 3524)
- MpCmdRun.exe (PID: 6012)
- MpCmdRun.exe (PID: 5988)
Reads the computer name
- unhackme_setup.exe (PID: 3524)
- MpCmdRun.exe (PID: 6012)
- MpCmdRun.exe (PID: 5988)
The process uses the downloaded file
- WinRAR.exe (PID: 5564)
Create files in a temporary directory
- MpCmdRun.exe (PID: 6012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:12:24 12:44:12 |
| ZipCRC: | 0x2b8490e5 |
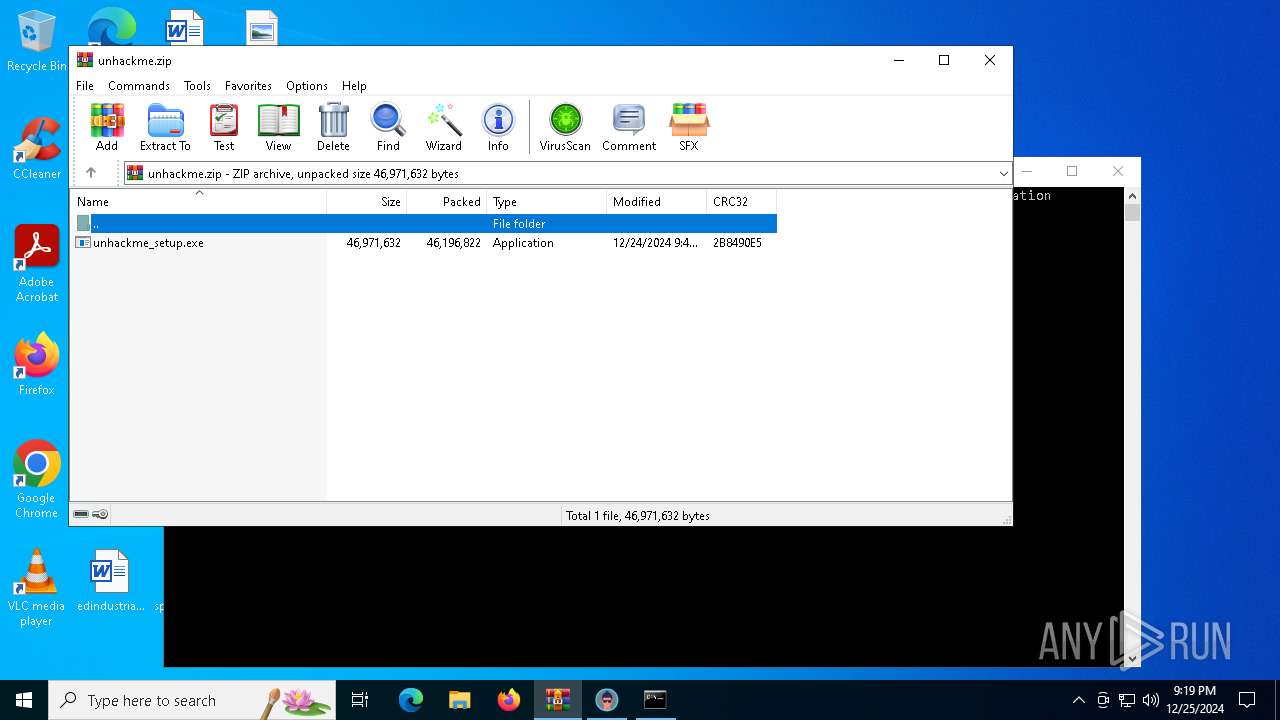
| ZipCompressedSize: | 46196822 |
| ZipUncompressedSize: | 46971632 |
| ZipFileName: | unhackme_setup.exe |
Total processes
116
Monitored processes
8
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 624 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3524 | "C:\Users\admin\Desktop\unhackme_setup.exe" | C:\Users\admin\Desktop\unhackme_setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Greatis Software Integrity Level: MEDIUM Description: UnHackMe Setup Version: 16.80.2024.1224 Modules
| |||||||||||||||
| 3988 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR5564.31462\Rar$Scan30325.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5564 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\unhackme.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5740 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR5564.38809\Rar$Scan103676.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5988 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR5564.38809" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6012 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR5564.31462" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 763
Read events
1 753
Write events
10
Delete events
0
Modification events
| (PID) Process: | (5564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\unhackme.zip | |||
| (PID) Process: | (5564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
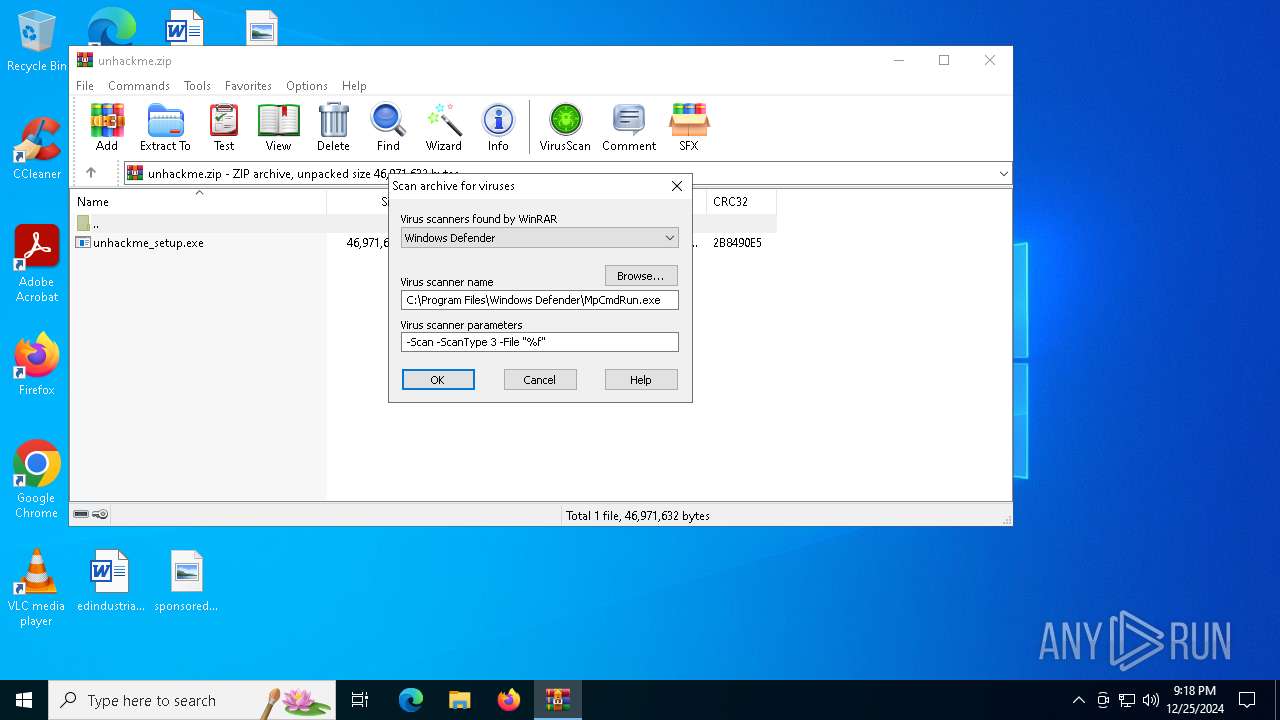
| (PID) Process: | (5564) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
0
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5564.31462\unhackme.zip\unhackme_setup.exe | — | |
MD5:— | SHA256:— | |||
| 5564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5564.38809\unhackme.zip\unhackme_setup.exe | — | |
MD5:— | SHA256:— | |||
| 5564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5564.38809\Rar$Scan103676.bat | text | |
MD5:DE4E0B7E2BC90BEE6F045BBF4DDD5317 | SHA256:5355D73B0DC37965FAFC388B2A722EB8BCCE672BF8E8E9F62CFE64925FA1C42E | |||
| 6012 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:74E861A188771FBE94F7CA1E2FAA133F | SHA256:9941E23FDD22508E48D39FBAC41AD9A6031A988CA8DB80100209605BEDDEF452 | |||
| 5564 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR5564.31462\Rar$Scan30325.bat | text | |
MD5:FC3646302AB26917BDDB9BCDFFC92E2E | SHA256:4177EFBB8D0DF2CF1F9B968493427DA890EF2C36BDAC7150D469B1E75B360411 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
21
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 2.21.110.139:443 | — | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |