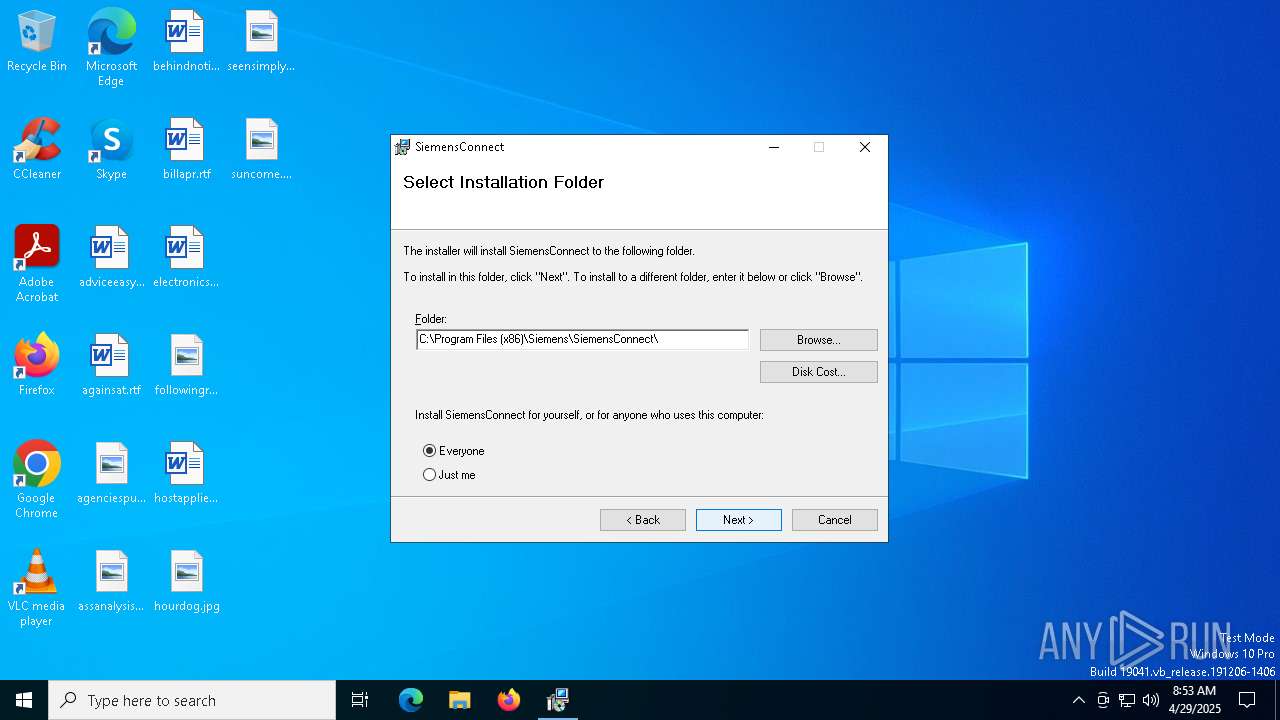
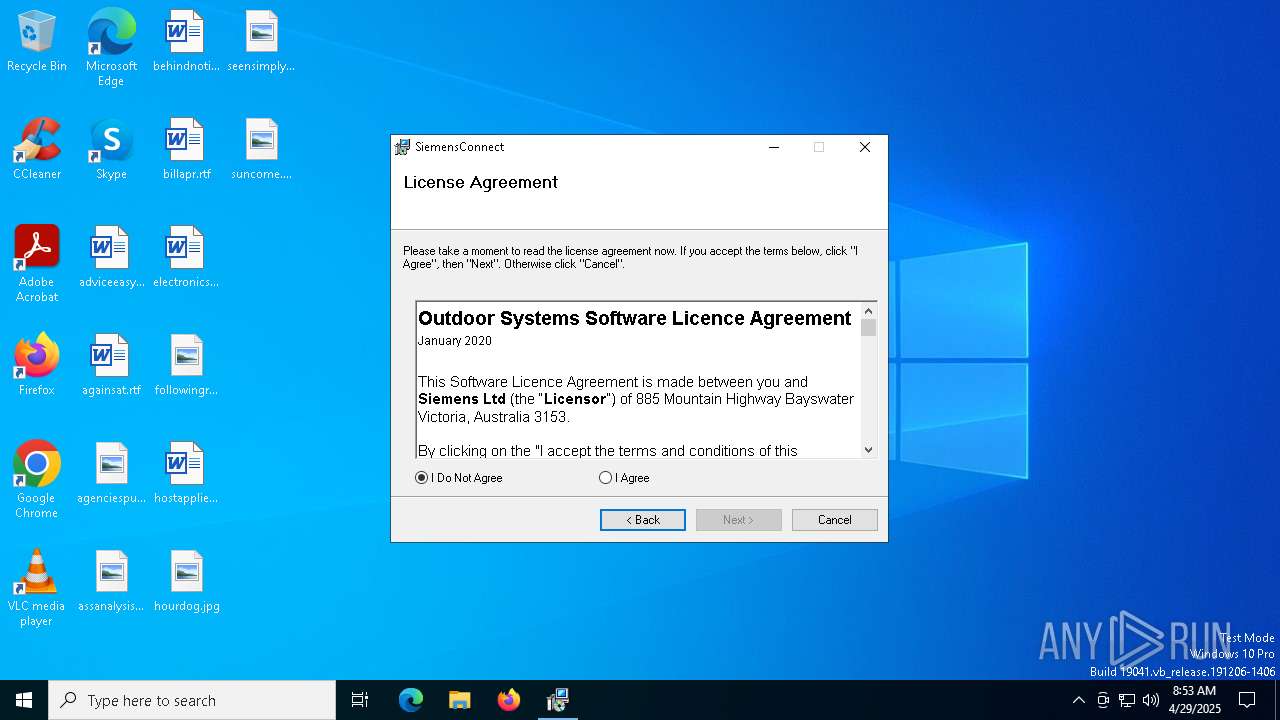
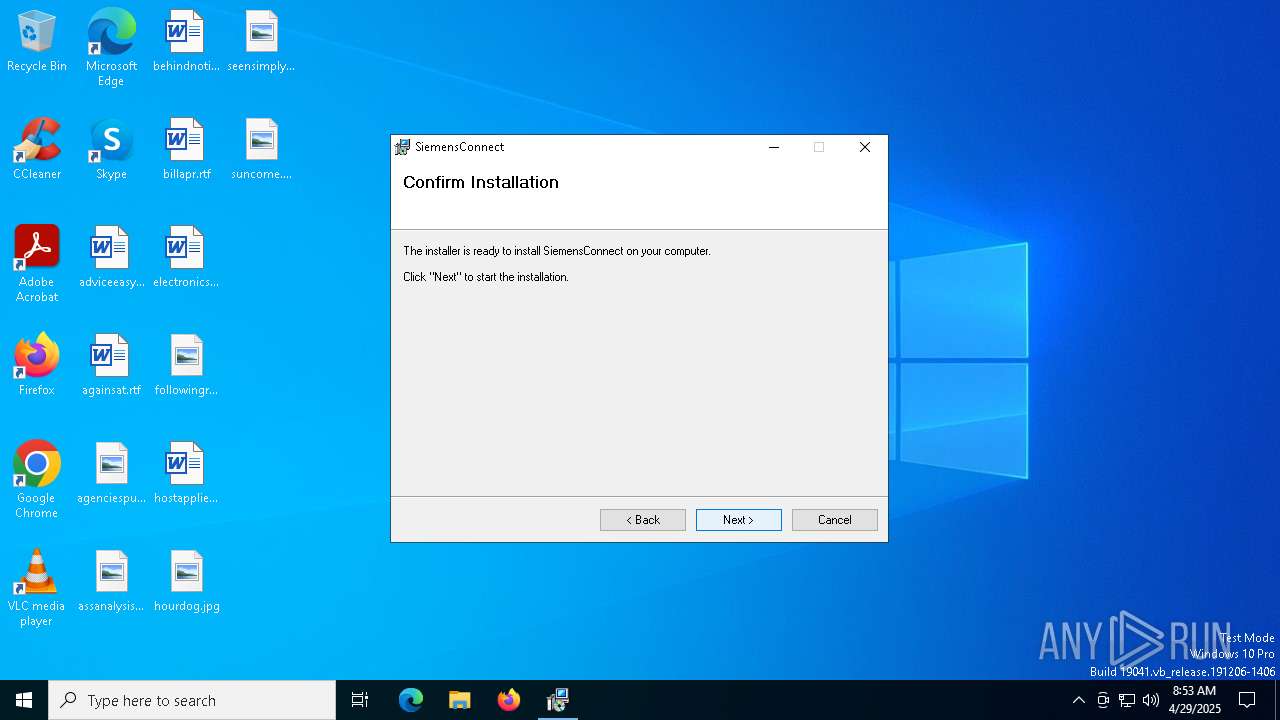
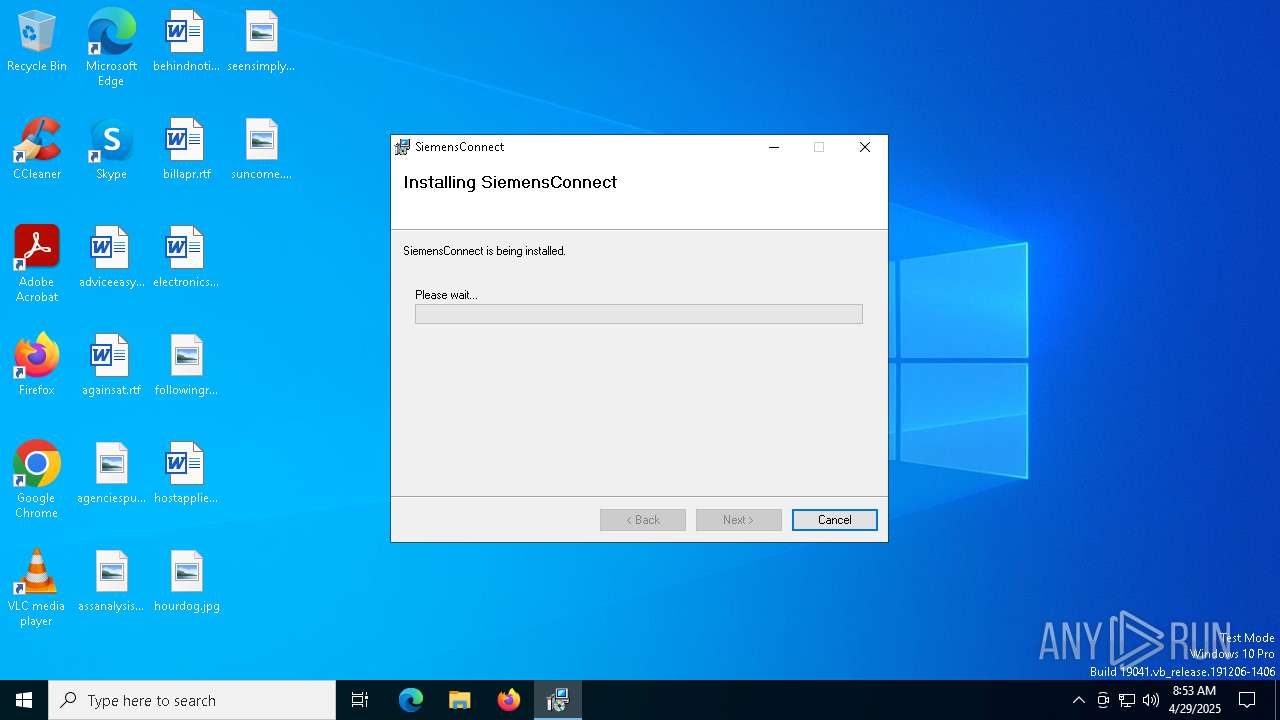
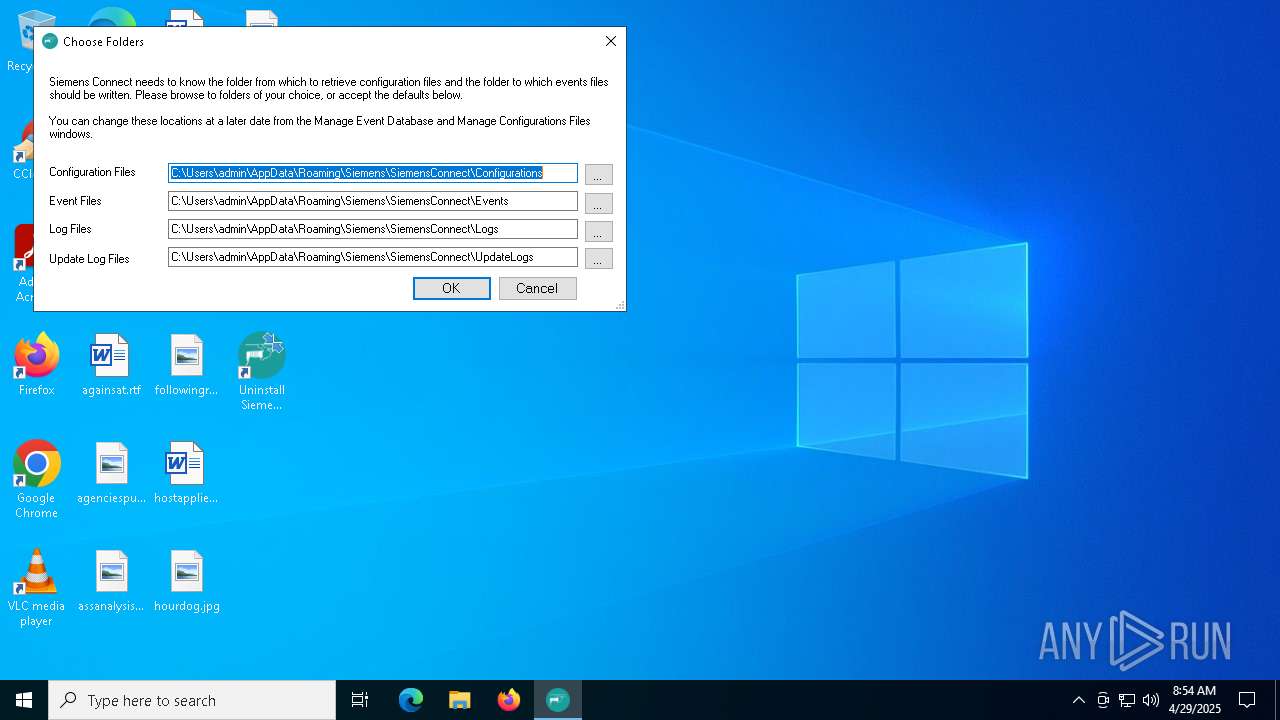
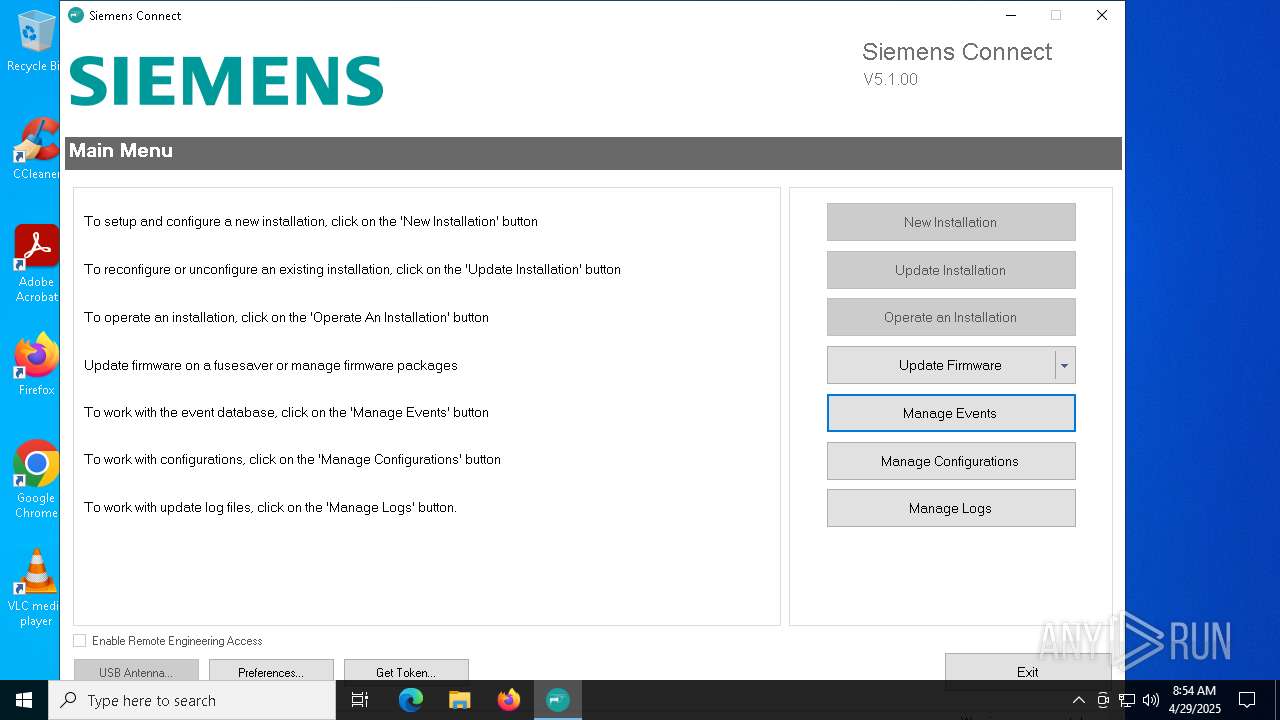
| File name: | SiemensConnectSetup(5.1.00).exe |
| Full analysis: | https://app.any.run/tasks/1fb411c7-3751-4be9-b7f5-140c72fea2a8 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 08:53:38 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | AD16E33FC73D8F0A742E9DA028236131 |
| SHA1: | B36F0271C3F7F1A01B2374365A930ED9C8056B46 |
| SHA256: | 63A2460C887C005B160FEA34990D1942DD63BA3B0454EA0B6DCAF1DD58649DFD |
| SSDEEP: | 98304:jn2deP4BXmJOSun2kEyaf70kUD2deBHoMLl3vvILlRg5SFsO99I90S25okD7/gfA:mP3GOqPwdQ8hnsO5Q/m9tn0ciTjo |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- SiemensConnectSetup(5.1.00).exe (PID: 2320)
- msiexec.exe (PID: 1196)
Starts a Microsoft application from unusual location
- SiemensConnectSetup(5.1.00).exe (PID: 2320)
Executable content was dropped or overwritten
- SiemensConnectSetup(5.1.00).exe (PID: 2320)
Reads security settings of Internet Explorer
- setup.exe (PID: 5116)
Executes as Windows Service
- VSSVC.exe (PID: 4608)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 1196)
INFO
The sample compiled with german language support
- SiemensConnectSetup(5.1.00).exe (PID: 2320)
Checks supported languages
- SiemensConnectSetup(5.1.00).exe (PID: 2320)
- setup.exe (PID: 5116)
- msiexec.exe (PID: 1196)
- msiexec.exe (PID: 6872)
Create files in a temporary directory
- SiemensConnectSetup(5.1.00).exe (PID: 2320)
- setup.exe (PID: 5116)
- msiexec.exe (PID: 6872)
The sample compiled with english language support
- SiemensConnectSetup(5.1.00).exe (PID: 2320)
- msiexec.exe (PID: 4756)
- msiexec.exe (PID: 1196)
Reads the computer name
- setup.exe (PID: 5116)
- msiexec.exe (PID: 1196)
- msiexec.exe (PID: 6872)
Process checks computer location settings
- setup.exe (PID: 5116)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4756)
- msiexec.exe (PID: 1196)
Manages system restore points
- SrTasks.exe (PID: 208)
Manual execution by a user
- SiemensConnect.exe (PID: 684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2000:11:24 11:50:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.2 |
| CodeSize: | 25600 |
| InitializedDataSize: | 15394304 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6a00 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.19041.3570 |
| ProductVersionNumber: | 11.0.19041.3570 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | German |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Win32 Cabinet Self-Extractor |
| FileVersion: | 11.00.19041.3570 (WinBuild.160101.0800) |
| InternalName: | Wextract |
| LegalCopyright: | © Microsoft Corporation. Alle Rechte vorbehalten. |
| OriginalFileName: | WEXTRACT.EXE .MUI |
| ProductName: | Internet Explorer |
| ProductVersion: | 11.00.19041.3570 |
Total processes
146
Monitored processes
13
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
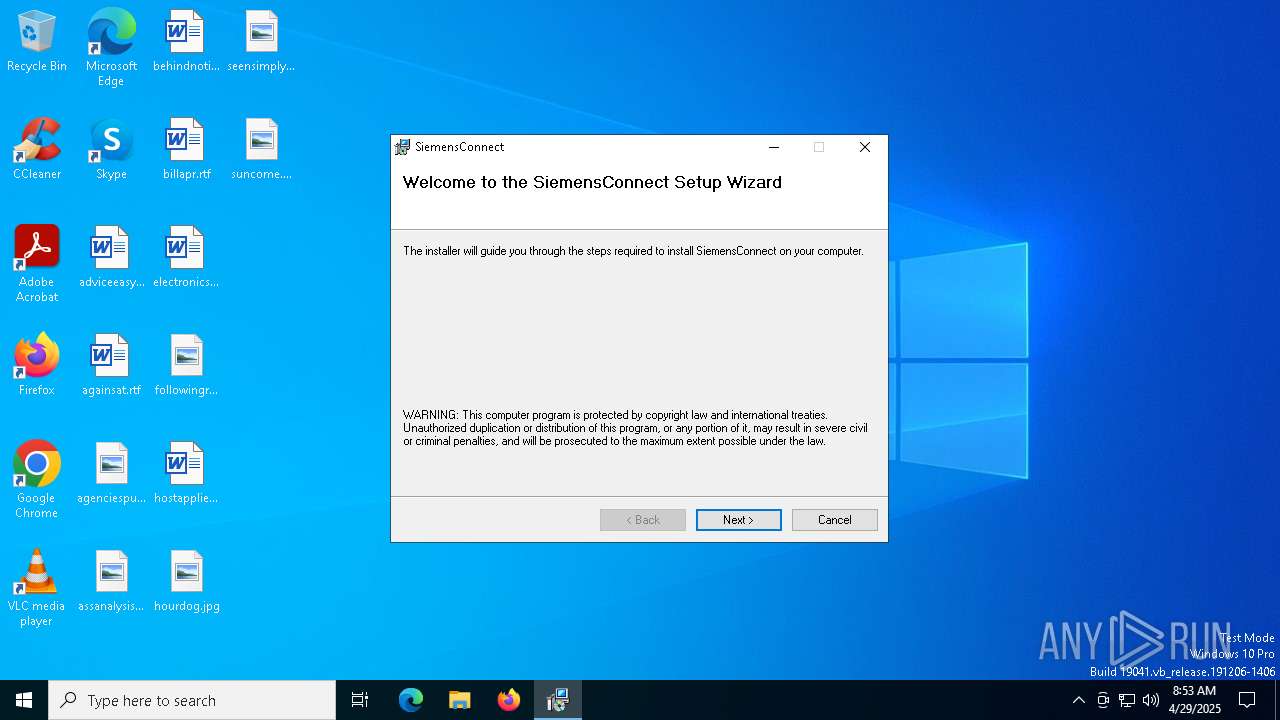
| 684 | "C:\Program Files (x86)\Siemens\SiemensConnect\SiemensConnect.exe" | C:\Program Files (x86)\Siemens\SiemensConnect\SiemensConnect.exe | — | explorer.exe | |||||||||||
User: admin Company: Siemens Integrity Level: MEDIUM Description: Siemens Connect Version: 5.1.00.0 Modules
| |||||||||||||||
| 976 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | "C:\Users\admin\AppData\Local\Temp\SiemensConnectSetup(5.1.00).exe" | C:\Users\admin\AppData\Local\Temp\SiemensConnectSetup(5.1.00).exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4608 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4756 | "C:\Windows\SysWOW64\msiexec.exe" -I "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\SiemensConnectSetup.msi" | C:\Windows\SysWOW64\msiexec.exe | setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5116 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\setup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\setup.exe | — | SiemensConnectSetup(5.1.00).exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup Exit code: 0 Version: 17.0.33927.210 built by: D17.7 Modules
| |||||||||||||||
Total events
4 940
Read events
4 542
Write events
381
Delete events
17
Modification events
| (PID) Process: | (1196) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000092A31E40E4B8DB01AC040000D8020000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1196) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000092A31E40E4B8DB01AC040000D8020000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1196) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000021626140E4B8DB01AC040000D8020000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1196) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000005FC56340E4B8DB01AC040000D8020000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1196) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000021626140E4B8DB01AC040000D8020000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1196) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000978D6840E4B8DB01AC040000D8020000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1196) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (4608) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000002651E940E4B8DB010012000068040000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4608) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000002651E940E4B8DB0100120000AC150000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4608) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000002651E940E4B8DB0100120000C8150000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
67
Suspicious files
23
Text files
18
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2320 | SiemensConnectSetup(5.1.00).exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\SiemensConnectSetup.msi | — | |
MD5:— | SHA256:— | |||
| 1196 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1196 | msiexec.exe | C:\Windows\Installer\112d47.msi | — | |
MD5:— | SHA256:— | |||
| 2320 | SiemensConnectSetup(5.1.00).exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\setup.exe | executable | |
MD5:5A554D061FCD6301E81C3638F771EE17 | SHA256:33AB25297489EA3C06AF2E2CC00C5B01475D2CC1DEE6A6F07B06C817306D9F0A | |||
| 6872 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFGC507.tmp | xml | |
MD5:2BE48F533744EFA173A2EDE37EA8031E | SHA256:02375FA63B79648ED6BB419C08F78BA9032EE22BA7170250E24427F47FDDFA4E | |||
| 1196 | msiexec.exe | C:\Program Files (x86)\Siemens\SiemensConnect\C1.Win.4.dll | executable | |
MD5:B028287A26215FF2F286EDE9AB9498E1 | SHA256:6611820E88EA582843FB7ED50CC7176EA194C03D2979A35E7D5797C4E56EF3DB | |||
| 4756 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIC518.tmp | executable | |
MD5:684F2D21637CB5835172EDAD55B6A8D9 | SHA256:DA1FE86141C446921021BB26B6FE2BD2D1BB51E3E614F46F8103FFAD8042F2C0 | |||
| 4756 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIC4B9.tmp | executable | |
MD5:684F2D21637CB5835172EDAD55B6A8D9 | SHA256:DA1FE86141C446921021BB26B6FE2BD2D1BB51E3E614F46F8103FFAD8042F2C0 | |||
| 1196 | msiexec.exe | C:\Windows\Temp\~DF43F2BA0DDE9E9246.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 1196 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:6F308EACDBA1D92E8244948949192C0E | SHA256:613CA799A89103EEB4FCB026DF032D019E19C40E2C2908281C148E1B00B41C54 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
28
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
736 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
736 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.63.118.230:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |