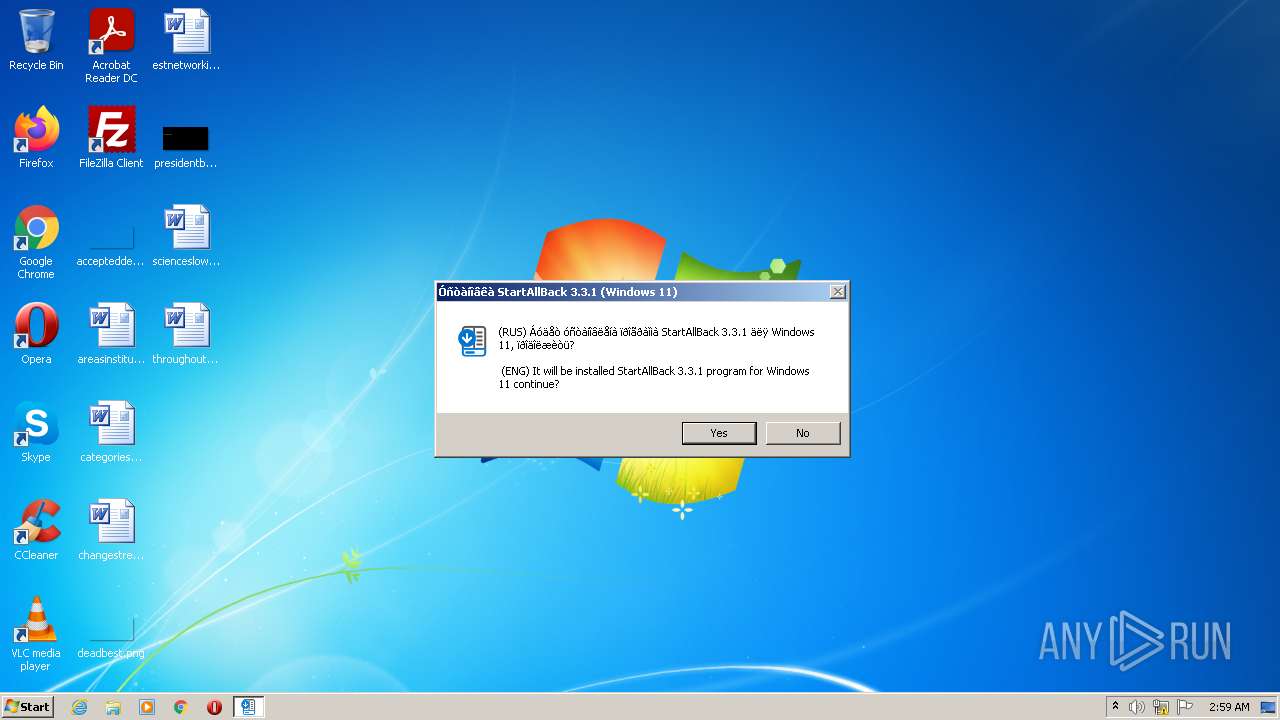
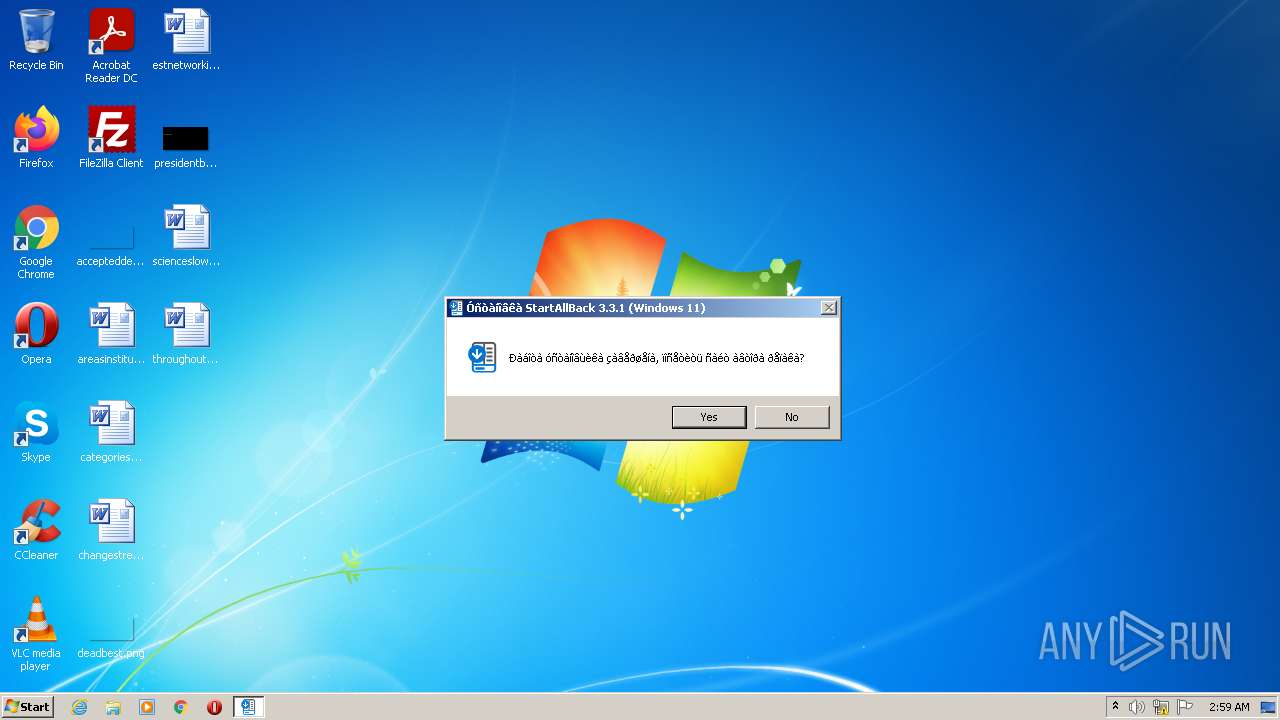
| File name: | StartAllBack-3.3.1.exe |
| Full analysis: | https://app.any.run/tasks/a925028d-d8ee-4f69-834c-cb61c43e26a0 |
| Verdict: | Malicious activity |
| Analysis date: | March 16, 2022, 02:59:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 3CE5BAB91FA4C276E925379D0298BDA0 |
| SHA1: | BDF393A760612B914CC7024E66AD93FE5EAAEE3C |
| SHA256: | 639AB4DCF9E6EF3E89D50536FA8FE74144201DA3803030582D261DCB5C64B285 |
| SSDEEP: | 24576:6diL11N0kTXFqOa3bQl/w/yacPIRB+9Wwy9aX0y5rdKNIl8/HJW5aF5pFhFC:6cN1Gr3/yLIP+9zy9E5t8xW5oFO |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks supported languages
- StartAllBack-3.3.1.exe (PID: 2020)
Drops a file with a compile date too recent
- StartAllBack-3.3.1.exe (PID: 2020)
Reads the computer name
- StartAllBack-3.3.1.exe (PID: 2020)
Executable content was dropped or overwritten
- StartAllBack-3.3.1.exe (PID: 2020)
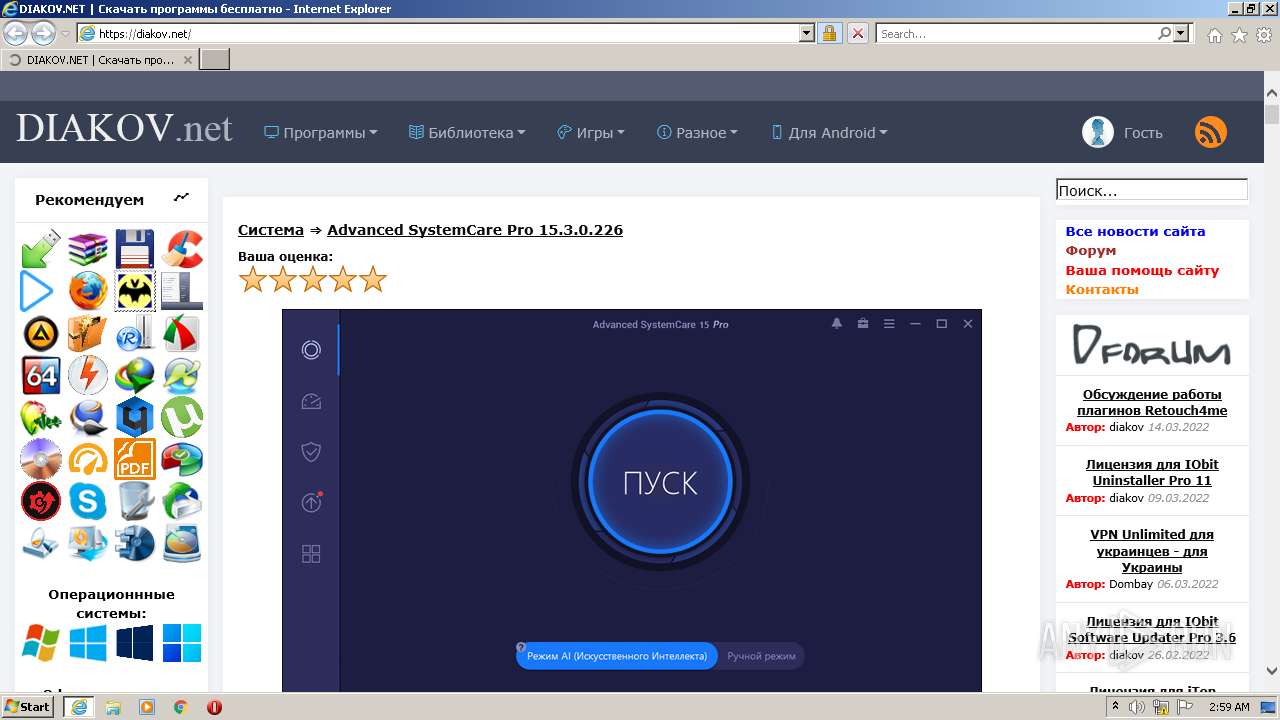
Starts Internet Explorer
- StartAllBack-3.3.1.exe (PID: 2020)
Drops a file with too old compile date
- StartAllBack-3.3.1.exe (PID: 2020)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2812)
Drops a file that was compiled in debug mode
- StartAllBack-3.3.1.exe (PID: 2020)
INFO
Reads the computer name
- iexplore.exe (PID: 3932)
- iexplore.exe (PID: 2812)
- explorer.exe (PID: 1792)
Checks supported languages
- iexplore.exe (PID: 3932)
- iexplore.exe (PID: 2812)
- explorer.exe (PID: 1792)
Reads settings of System Certificates
- iexplore.exe (PID: 2812)
- iexplore.exe (PID: 3932)
Dropped object may contain Bitcoin addresses
- StartAllBack-3.3.1.exe (PID: 2020)
Changes internet zones settings
- iexplore.exe (PID: 3932)
Application launched itself
- iexplore.exe (PID: 3932)
Checks Windows Trust Settings
- iexplore.exe (PID: 2812)
- iexplore.exe (PID: 3932)
Reads internet explorer settings
- iexplore.exe (PID: 2812)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2812)
Changes settings of System certificates
- iexplore.exe (PID: 2812)
Creates files in the user directory
- iexplore.exe (PID: 2812)
Reads CPU info
- iexplore.exe (PID: 2812)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | NSIS - Nullsoft Scriptable Install System (94.8) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (3.4) |
| .dll | | | Win32 Dynamic Link Library (generic) (0.7) |
| .exe | | | Win32 Executable (generic) (0.5) |
| .exe | | | Generic Win/DOS Executable (0.2) |
EXIF
EXE
| FileDescription: | StartAllBack 3.3.1 (Windows 11) |
|---|---|
| CompanyName: | diakov.net |
| CharacterSet: | Windows, Cyrillic |
| LanguageCode: | Russian |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x0000 |
| ProductVersionNumber: | 3.3.1.4290 |
| FileVersionNumber: | 3.3.1.4290 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | 6 |
| OSVersion: | 4 |
| EntryPoint: | 0x323c |
| UninitializedDataSize: | 1024 |
| InitializedDataSize: | 119808 |
| CodeSize: | 23552 |
| LinkerVersion: | 6 |
| PEType: | PE32 |
| TimeStamp: | 2009:12:05 23:50:46+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 05-Dec-2009 22:50:46 |
| Detected languages: |
|
| CompanyName: | diakov.net |
| FileDescription: | StartAllBack 3.3.1 (Windows 11) |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 05-Dec-2009 22:50:46 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00005A5A | 0x00005C00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.4177 |
.rdata | 0x00007000 | 0x00001190 | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.18163 |
.data | 0x00009000 | 0x0001AF98 | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.70903 |
.ndata | 0x00024000 | 0x0000B000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x0002F000 | 0x0000A218 | 0x0000A400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.85851 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.10394 | 533 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.1461 | 9640 | UNKNOWN | English - United States | RT_ICON |
3 | 7.71875 | 6057 | UNKNOWN | English - United States | RT_ICON |
4 | 4.02386 | 4264 | UNKNOWN | English - United States | RT_ICON |
5 | 4.13054 | 1128 | UNKNOWN | English - United States | RT_ICON |
6 | 0 | 744 | UNKNOWN | English - United States | RT_ICON |
7 | 0 | 296 | UNKNOWN | English - United States | RT_ICON |
103 | 2.8819 | 104 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.51583 | 256 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.87057 | 284 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
ole32.dll |
Total processes
43
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1792 | C:\Windows\explorer.exe | C:\Windows\explorer.exe | — | StartAllBack-3.3.1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2020 | "C:\Users\admin\AppData\Local\Temp\StartAllBack-3.3.1.exe" | C:\Users\admin\AppData\Local\Temp\StartAllBack-3.3.1.exe | Explorer.EXE | ||||||||||||
User: admin Company: diakov.net Integrity Level: HIGH Description: StartAllBack 3.3.1 (Windows 11) Exit code: 0 Modules
| |||||||||||||||
| 2812 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3932 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3472 | "C:\Users\admin\AppData\Local\Temp\StartAllBack-3.3.1.exe" | C:\Users\admin\AppData\Local\Temp\StartAllBack-3.3.1.exe | — | Explorer.EXE | |||||||||||
User: admin Company: diakov.net Integrity Level: MEDIUM Description: StartAllBack 3.3.1 (Windows 11) Exit code: 3221226540 Modules
| |||||||||||||||
| 3932 | "C:\Program Files\Internet Explorer\iexplore.exe" https://diakov.net/ | C:\Program Files\Internet Explorer\iexplore.exe | StartAllBack-3.3.1.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
42 126
Read events
41 863
Write events
263
Delete events
0
Modification events
| (PID) Process: | (2020) StartAllBack-3.3.1.exe | Key: | HKEY_CURRENT_USER\Software\StartAll |
| Operation: | write | Name: | AutoUpdates |
Value: 0 | |||
| (PID) Process: | (2020) StartAllBack-3.3.1.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-500\Software\StartAll |
| Operation: | write | Name: | AutoUpdates |
Value: 0 | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30947553 | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30947553 | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3932) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
6
Suspicious files
36
Text files
111
Unknown types
38
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2020 | StartAllBack-3.3.1.exe | C:\Users\admin\AppData\Local\Temp\nsb5254.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | — | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab9356.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar9345.tmp | — | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | — | |
MD5:— | SHA256:— | |||
| 2020 | StartAllBack-3.3.1.exe | C:\Users\admin\AppData\Local\Temp\Start\StartAllBackCfg.exe | executable | |
MD5:— | SHA256:— | |||
| 2020 | StartAllBack-3.3.1.exe | C:\Users\admin\AppData\Local\Temp\Start\StartAllBackLoaderX64.dll | executable | |
MD5:— | SHA256:— | |||
| 2020 | StartAllBack-3.3.1.exe | C:\Users\admin\AppData\Local\Temp\Start\UpdateCheck.exe | text | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar9357.tmp | cat | |
MD5:— | SHA256:— | |||
| 2812 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
82
TCP/UDP connections
159
DNS requests
73
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2812 | iexplore.exe | GET | — | 5.45.205.244:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEGZO%2BD8ePKMpE43xiMelpT4%3D | RU | — | — | whitelisted |
2812 | iexplore.exe | GET | 200 | 92.123.195.57:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?ed7a6295d6b0e360 | unknown | compressed | 59.5 Kb | whitelisted |
2812 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
2812 | iexplore.exe | GET | 200 | 92.123.224.113:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgNOuMLysuHv%2BnazIQy6nTlrbw%3D%3D | unknown | der | 503 b | shared |
2812 | iexplore.exe | GET | 200 | 5.45.205.244:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEGZO%2BD8ePKMpE43xiMelpT4%3D | RU | der | 1.48 Kb | whitelisted |
2812 | iexplore.exe | GET | 200 | 18.66.242.58:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
2812 | iexplore.exe | GET | 200 | 104.18.31.182:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | US | der | 471 b | whitelisted |
2812 | iexplore.exe | GET | 200 | 92.123.224.113:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgRHZVyh9nlP4S60s5TNh%2FVCAA%3D%3D | unknown | der | 503 b | shared |
2812 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDWxNMTh5qYFwoAAAABN4d2 | US | der | 472 b | whitelisted |
2812 | iexplore.exe | GET | 200 | 18.66.242.94:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2812 | iexplore.exe | 77.83.173.15:443 | diakov.net | — | — | unknown |
2812 | iexplore.exe | 92.123.224.113:80 | r3.o.lencr.org | Akamai International B.V. | — | suspicious |
2812 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2812 | iexplore.exe | 104.89.32.83:80 | x1.c.lencr.org | Akamai Technologies, Inc. | NL | suspicious |
2812 | iexplore.exe | 5.255.255.50:443 | yandex.ru | YANDEX LLC | RU | whitelisted |
2812 | iexplore.exe | 142.251.39.98:443 | pagead2.googlesyndication.com | Google Inc. | US | unknown |
2812 | iexplore.exe | 18.64.103.90:443 | app.appsflyer.com | Massachusetts Institute of Technology | US | unknown |
2812 | iexplore.exe | 142.250.181.227:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2812 | iexplore.exe | 18.66.242.94:80 | o.ss2.us | Massachusetts Institute of Technology | US | unknown |
2812 | iexplore.exe | 18.66.242.58:80 | ocsp.rootg2.amazontrust.com | Massachusetts Institute of Technology | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
diakov.net |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
yandex.ru |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
app.appsflyer.com |
| suspicious |
w.uptolike.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
o.ss2.us |
| whitelisted |