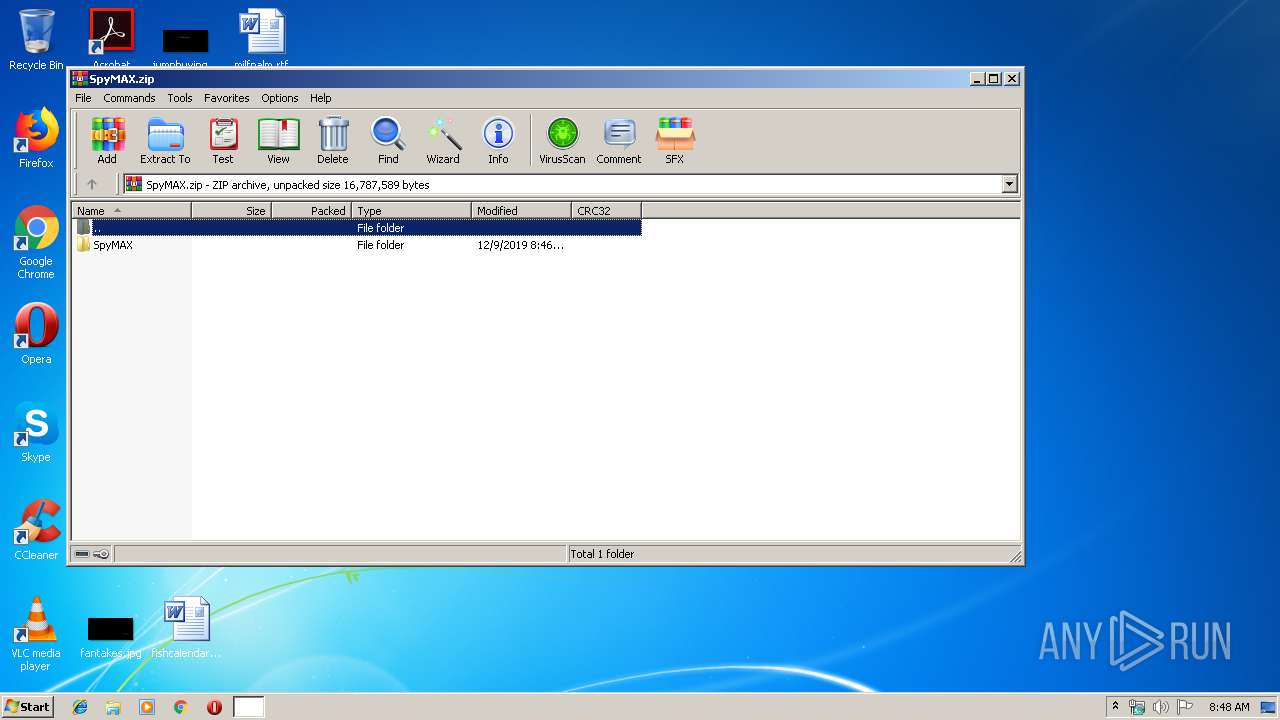
| File name: | SpyMAX.zip |
| Full analysis: | https://app.any.run/tasks/e5fe21ad-db8a-498c-9f4f-a513cfd3f396 |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2019, 08:48:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 5C684A879E0B7C553B84E25CC0B65BED |
| SHA1: | AA80C9A255FF062516B70A737978AE256989BF7C |
| SHA256: | 6395CC6263092793349803CD8930BEEA33C7C58394905522E3E57E307CC31BC9 |
| SSDEEP: | 196608:mEZshrLdo678cuWE5+XedequR+0x1oOO3NgU+GRtV:LcrLdq2wgiOGrZRtV |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3476)
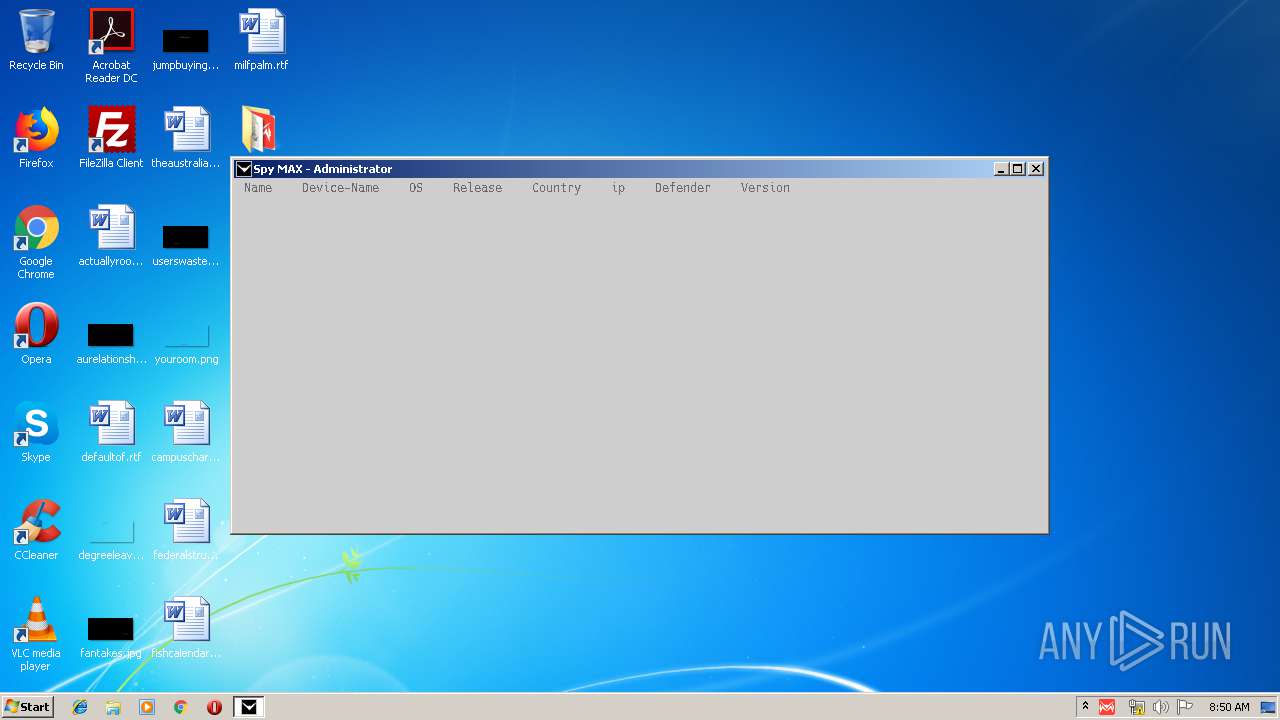
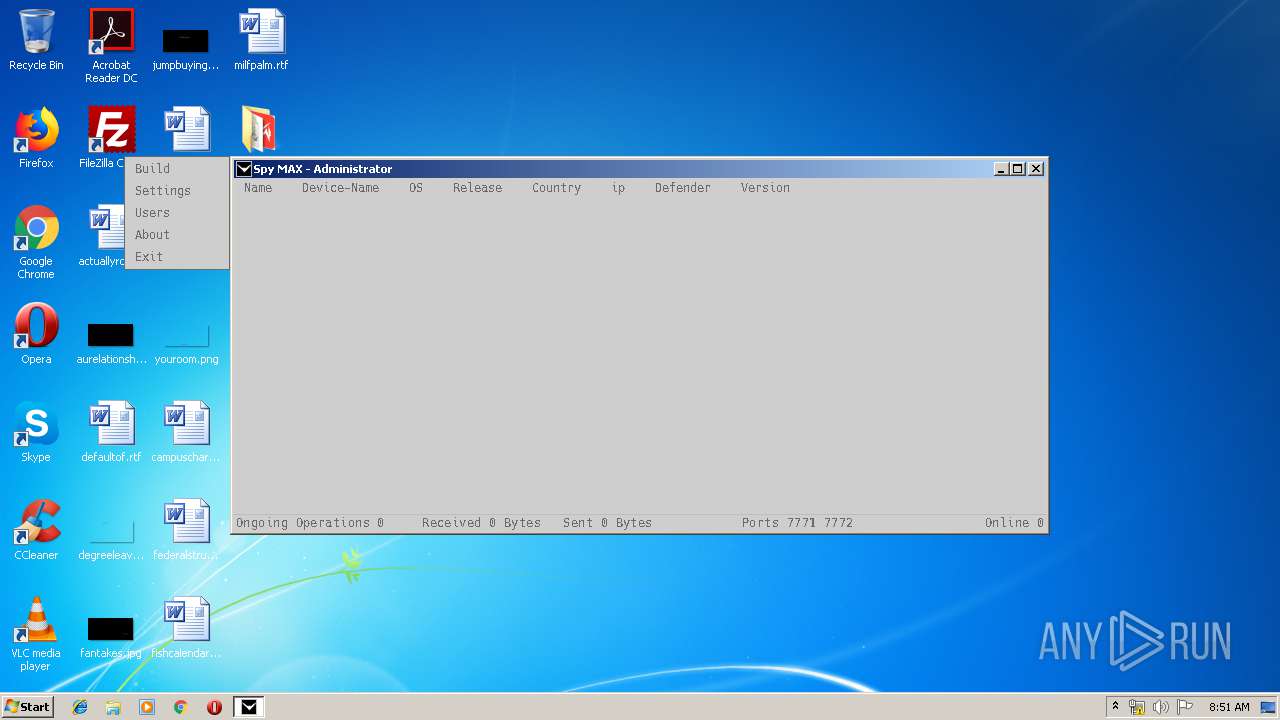
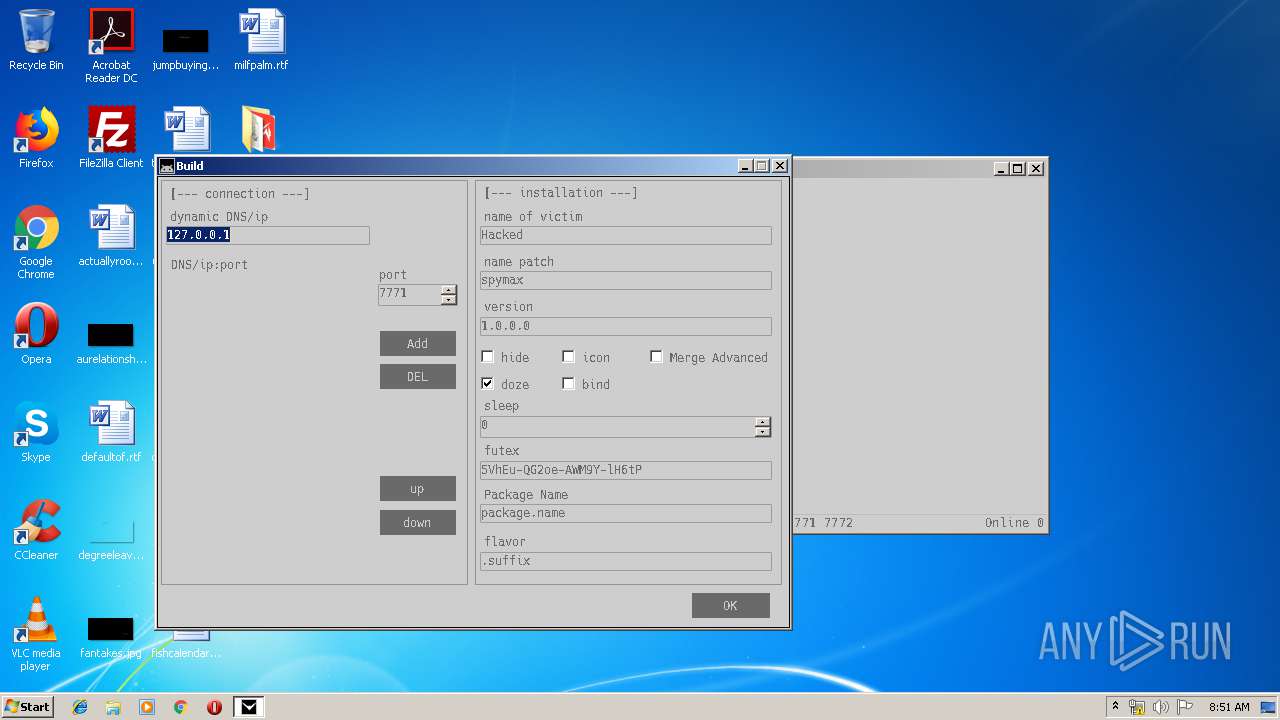
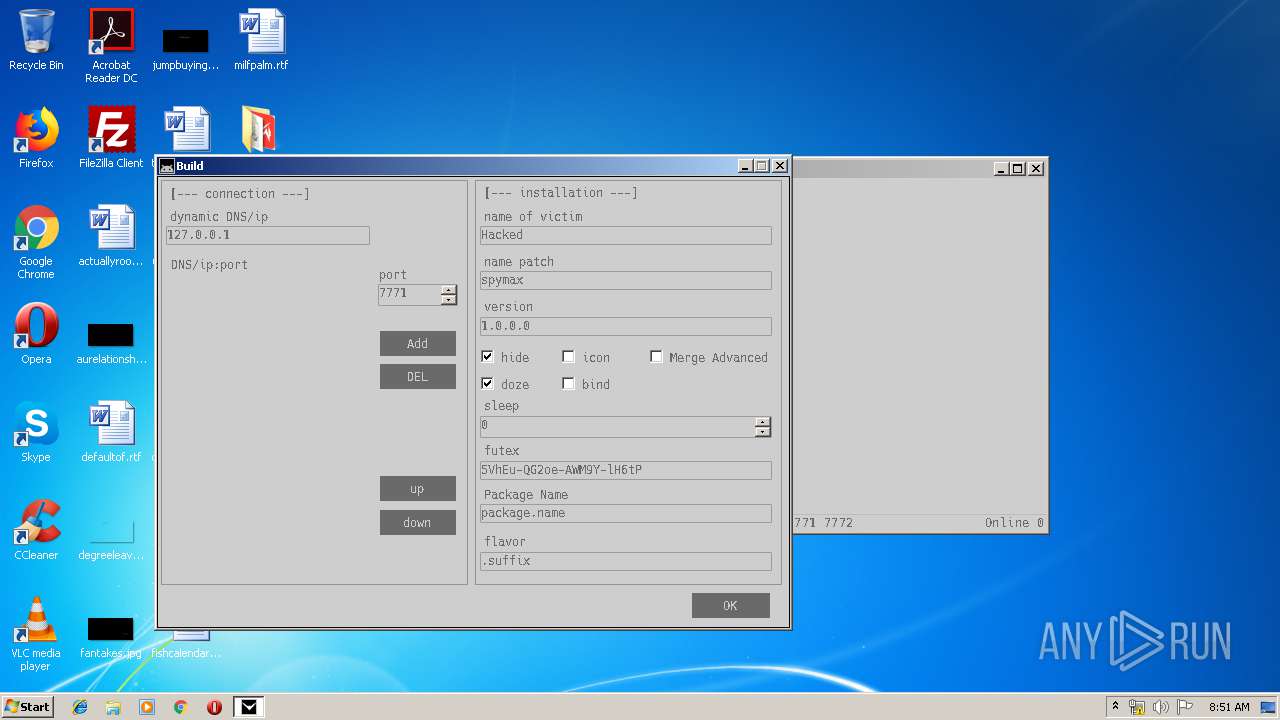
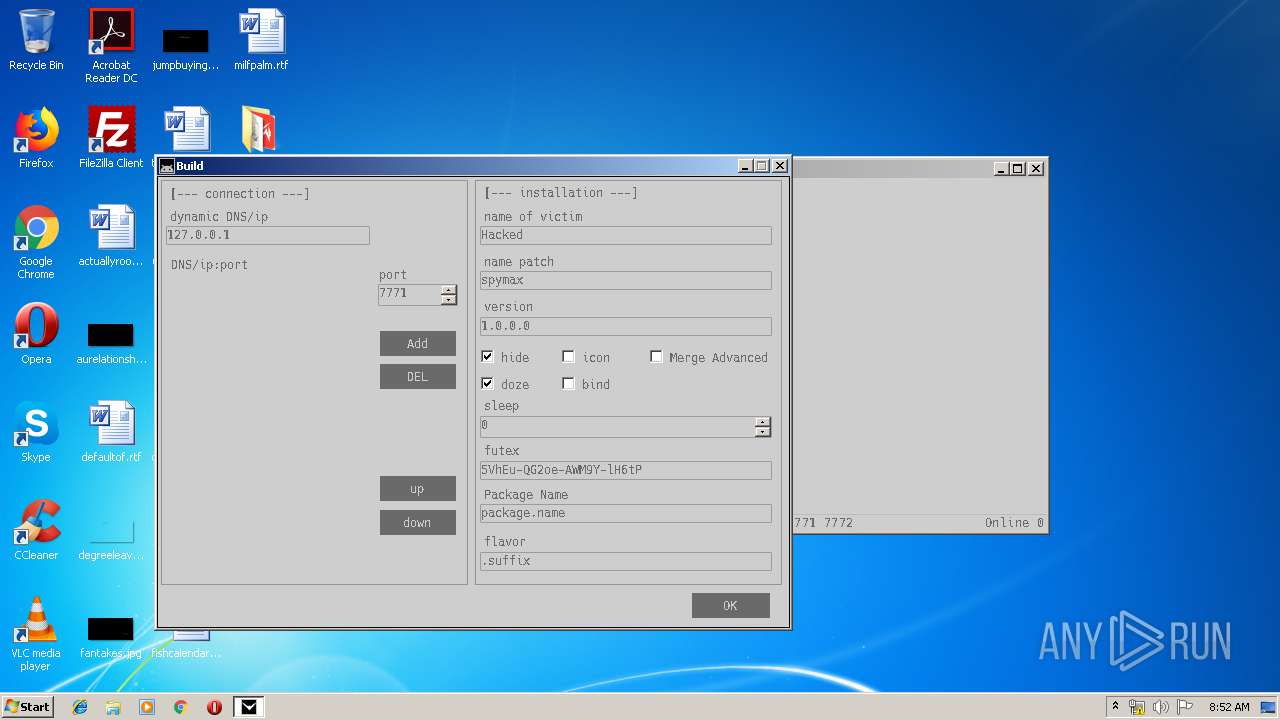
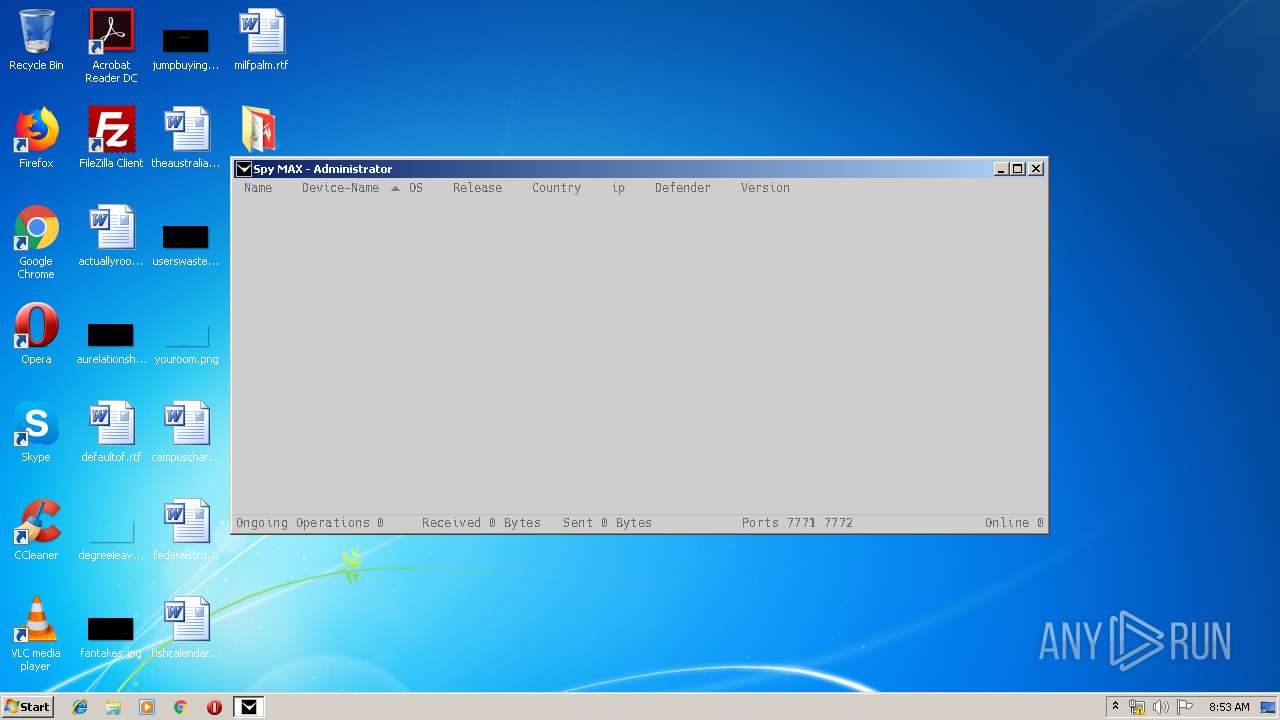
- Spy MAX.exe (PID: 2932)
Application was dropped or rewritten from another process
- Spy MAX.exe (PID: 2932)
- Spy MAX.exe (PID: 1556)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1784)
Application launched itself
- Spy MAX.exe (PID: 1556)
INFO
Manual execution by user
- Spy MAX.exe (PID: 1556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:12:09 16:46:28 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | SpyMAX/ |
Total processes
45
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1556 | "C:\Users\admin\Desktop\SpyMAX\Spy MAX.exe" | C:\Users\admin\Desktop\SpyMAX\Spy MAX.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Spy MAX - RAT Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 1784 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SpyMAX.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2932 | "C:\Users\admin\Desktop\SpyMAX\Spy MAX.exe" | C:\Users\admin\Desktop\SpyMAX\Spy MAX.exe | Spy MAX.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Spy MAX - RAT Exit code: 0 Version: 2.0.0.0 Modules
| |||||||||||||||
| 3476 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 436
Read events
1 370
Write events
65
Delete events
1
Modification events
| (PID) Process: | (1784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1784) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SpyMAX.zip | |||
| (PID) Process: | (1784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
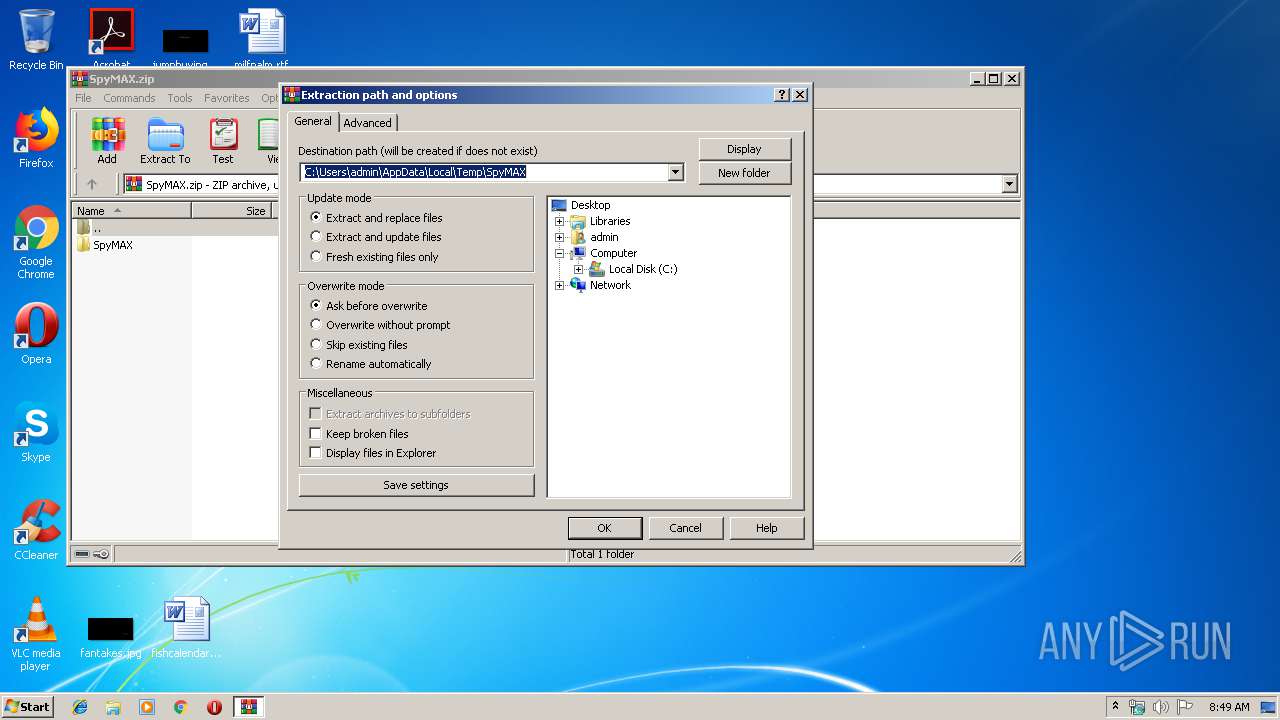
| (PID) Process: | (1784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (1784) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
4
Suspicious files
12
Text files
442
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1784 | WinRAR.exe | C:\Users\admin\Desktop\SpyMAX\PATCH-SDK26.apk | compressed | |
MD5:AC7E3B5BCD591FE15BF2C5AA43F389A8 | SHA256:CDE47BED5EC83E29F6455EC35228C3F56D488393668F5B720B79FCD6CB3BC098 | |||
| 1784 | WinRAR.exe | C:\Users\admin\Desktop\SpyMAX\res\Audio\4.wav | wav | |
MD5:87F33DC8407B25DEAF98AC120E1883D6 | SHA256:A3B05031FC5D69766F5C59923495A1158D0624D4D168070BC74B7F315405B127 | |||
| 1784 | WinRAR.exe | C:\Users\admin\Desktop\SpyMAX\res\Audio\1.wav | wav | |
MD5:194A5EC11D85E9364AA10762AE5ECA6C | SHA256:C340131B0790A6E9F3A12DBE8FC7AF2C6747824DB5D96F303826D8ADF0F58512 | |||
| 1784 | WinRAR.exe | C:\Users\admin\Desktop\SpyMAX\res\Audio\3.wav | wav | |
MD5:269E4F85692280ED9C59CB1C40517007 | SHA256:258C0A0B95163A9379E6BD7E95CEA5F47B96CE2816692016DAB5DAFA73AA1FE9 | |||
| 1784 | WinRAR.exe | C:\Users\admin\Desktop\SpyMAX\res\Audio\5.wav | wav | |
MD5:33794366BB58C3AF5E464B0A974CC182 | SHA256:19DFFF92A123AC883F38BF617D530C6CD222ABF5540E3F215C9A44F6FCBA0D60 | |||
| 1784 | WinRAR.exe | C:\Users\admin\Desktop\SpyMAX\res\Audio\2.wav | wav | |
MD5:9B15A3D6EA1205C555F91893859BDB7A | SHA256:40504BE5DA4002ABAD4B6B6B54DE0B966A3B9A5F4F24793B3AC9FC90E6CBE2CC | |||
| 1784 | WinRAR.exe | C:\Users\admin\Desktop\SpyMAX\PATCH-SDK28.apk | compressed | |
MD5:AC7E3B5BCD591FE15BF2C5AA43F389A8 | SHA256:CDE47BED5EC83E29F6455EC35228C3F56D488393668F5B720B79FCD6CB3BC098 | |||
| 1784 | WinRAR.exe | C:\Users\admin\Desktop\SpyMAX\res\Config\supported_video.inf | text | |
MD5:804CA35D9EF6A6A0A8A4879775F84652 | SHA256:3E14DBADD17619003B69DA69B70A94872F6144A28C55C4B5ED5AE61C62E9F3BB | |||
| 1784 | WinRAR.exe | C:\Users\admin\Desktop\SpyMAX\res\Audio\notification.wav | wav | |
MD5:A812F51D703FF92C95DD481FE270782F | SHA256:4AC90B06262E1D8DD6FC3F25E09ACD47619D159A46C763DC8298616910C0FE3A | |||
| 1784 | WinRAR.exe | C:\Users\admin\Desktop\SpyMAX\res\Config\supported_images.inf | text | |
MD5:C3F94480B3A61660454A61E7CD66A9D4 | SHA256:FB3B5F0884BECC997A4158100AFFCD232A45BEE9009C63AF17DE908FA1857344 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report