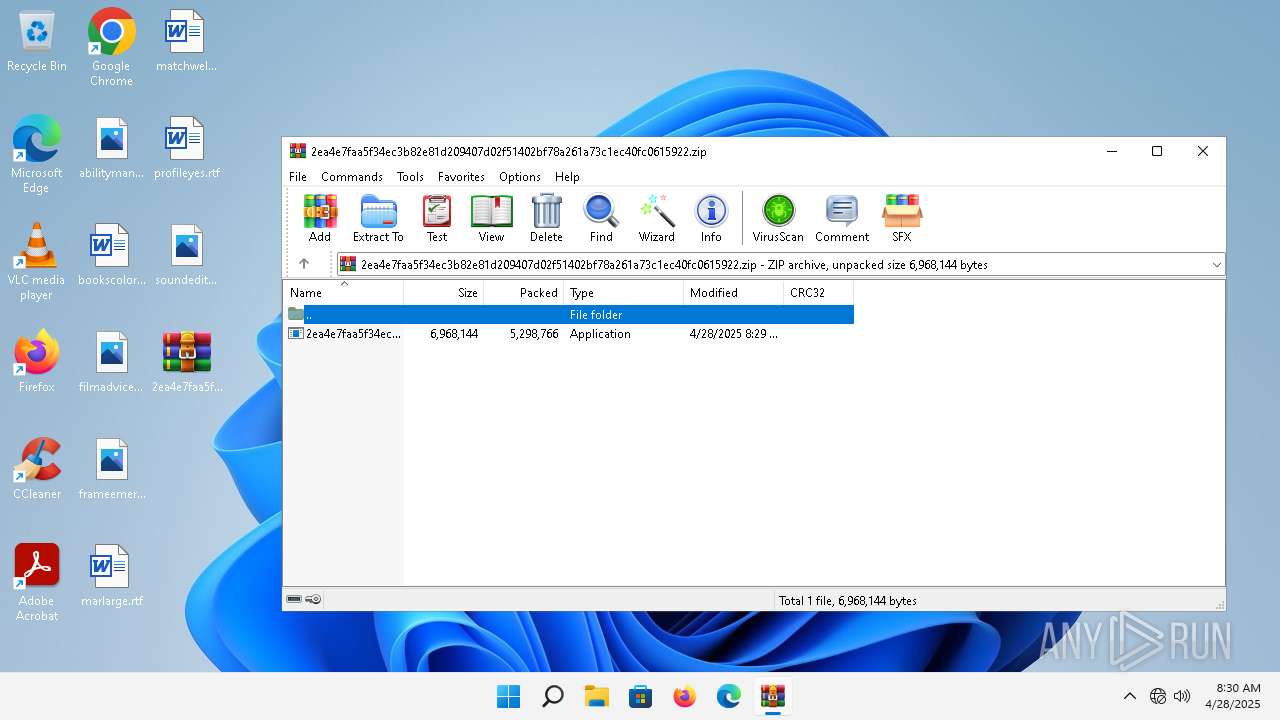
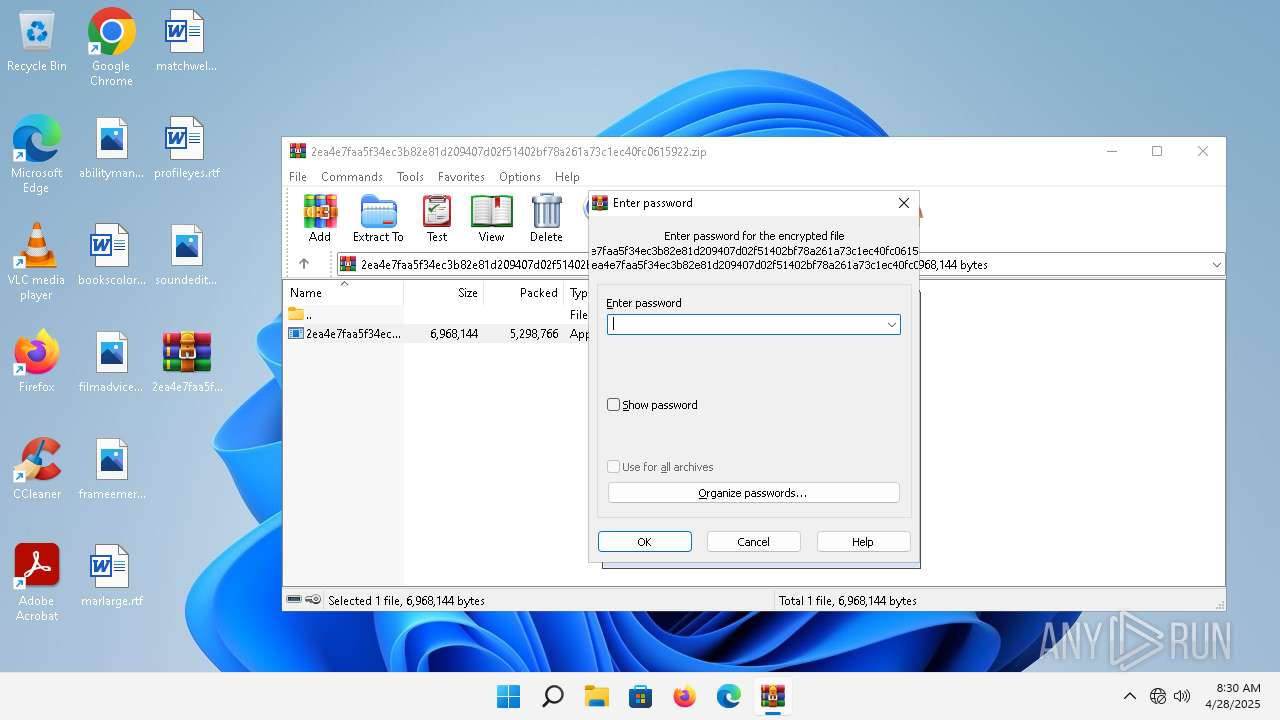
| File name: | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.zip |
| Full analysis: | https://app.any.run/tasks/44075fa4-23d0-4f30-b1b2-71023d1091b8 |
| Verdict: | Malicious activity |
| Analysis date: | April 28, 2025, 08:30:04 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
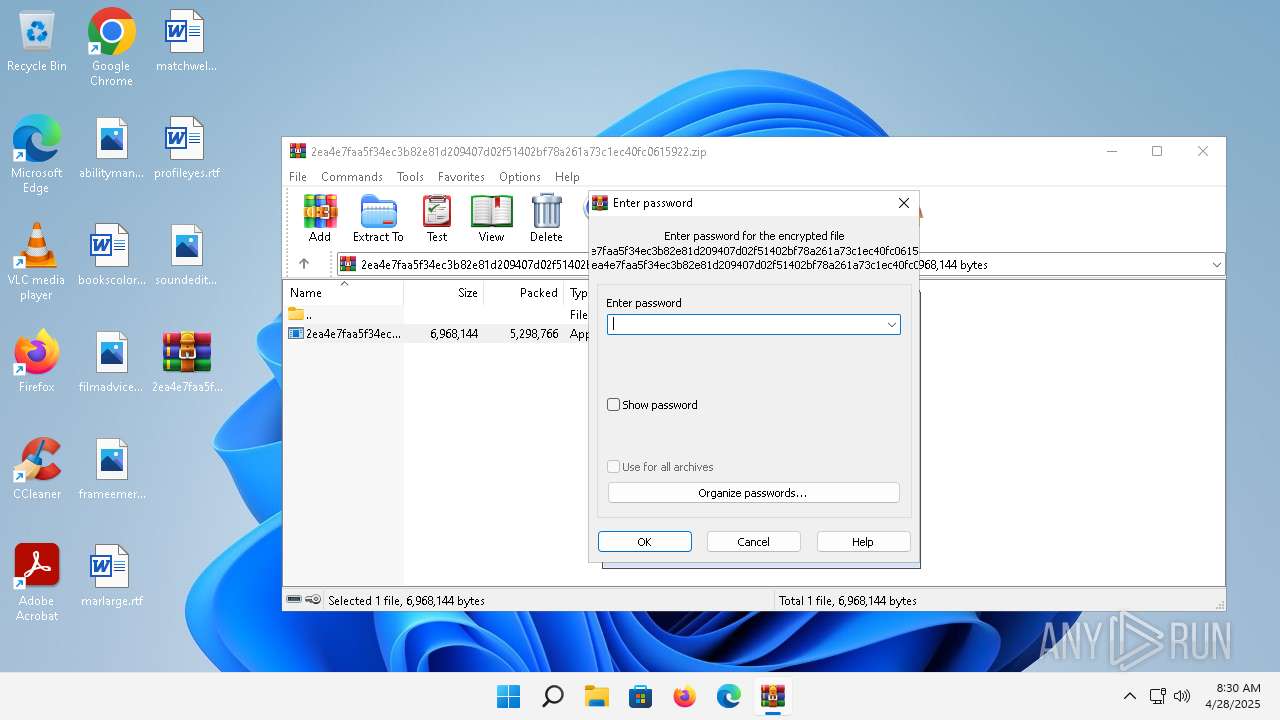
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 73959A288B8D23AB2EDF24629838B9D7 |
| SHA1: | A27AD07AEBE3711D627A221384D640B3BE2B1266 |
| SHA256: | 638FE6BDF2D1248420F248A93EB67F00B8184F253DECB79FC89E90A58B37250E |
| SSDEEP: | 98304:B48ao2XMQuHvWZwOG2R6oGK/pN3fBRBBIJYHslDnfQ9u669jYmiGmGIzxAn8O36P:I83R6bdhN |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2552)
SUSPICIOUS
Reads the Internet Settings
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 2200)
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 1072)
- Notepad.exe (PID: 3040)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2552)
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 2200)
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 1072)
- Notepad.exe (PID: 3040)
Reads settings of System Certificates
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 2200)
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 1072)
Adds/modifies Windows certificates
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 2200)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2552)
Reads the software policy settings
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 2200)
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 1072)
Reads the machine GUID from the registry
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 2200)
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 1072)
Reads the computer name
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 2200)
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 1072)
- Notepad.exe (PID: 3040)
Create files in a temporary directory
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 2200)
Checks supported languages
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 2200)
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 1072)
- Notepad.exe (PID: 3040)
Checks proxy server information
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 2200)
Creates files or folders in the user directory
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 2200)
Manual execution by a user
- 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe (PID: 1072)
- Notepad.exe (PID: 3040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:04:28 08:29:52 |
| ZipCRC: | 0xcbaaf1d7 |
| ZipCompressedSize: | 5298766 |
| ZipUncompressedSize: | 6968144 |
| ZipFileName: | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe |
Total processes
111
Monitored processes
7
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1072 | "C:\Users\admin\Desktop\2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe" | C:\Users\admin\Desktop\2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | explorer.exe | ||||||||||||
User: admin Company: Kakao Games Corp. Integrity Level: HIGH Description: GBOdin Launcher Exit code: 0 Version: 1.2.0.0 Modules
| |||||||||||||||
| 1996 | "C:\Windows\system32\DllHost.exe" /Processid:{B41DB860-64E4-11D2-9906-E49FADC173CA} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2552.32446\2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2552.32446\2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | WinRAR.exe | ||||||||||||
User: admin Company: Kakao Games Corp. Integrity Level: HIGH Description: GBOdin Launcher Exit code: 0 Version: 1.2.0.0 Modules
| |||||||||||||||
| 2552 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2756 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb2552.32446\2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb2552.32446\2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Kakao Games Corp. Integrity Level: MEDIUM Description: GBOdin Launcher Exit code: 3221226540 Version: 1.2.0.0 Modules
| |||||||||||||||
| 2856 | C:\Windows\System32\rundll32.exe C:\Windows\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3040 | "C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe" "C:\Users\admin\Desktop\logs\2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922_250428_083050123_1072.log" | C:\Program Files\WindowsApps\Microsoft.WindowsNotepad_11.2205.11.0_x64__8wekyb3d8bbwe\Notepad\Notepad.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
13 205
Read events
13 155
Write events
48
Delete events
2
Modification events
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.zip | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2552) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
2
Suspicious files
6
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2200 | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8EC9B1D0ABBD7F98B401D425828828CE_CC2FDB5BF7AAA054F18D8207D17FCE4B | binary | |
MD5:39E8B50B43316A1D7E5272D95EE95BE0 | SHA256:E85B5BF35AB0F1AA7FDD3A51BF55F573CF63DA673AB3A5FB002DA18EF8AAED2D | |||
| 2200 | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:ADD68522AF9BBA0D19B8F23255DE90B4 | SHA256:8AD40DF49994AFECB41BF0CEB7C347B06B486C26078471C83A2DAF62FDB9B131 | |||
| 2200 | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:5822DA116C7BB37E659E170DF4666E60 | SHA256:09CB3914026CFB72D695B53725718B0EB74D367DED37D31A24DAC231E8C442AB | |||
| 2552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2552.32446\2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | executable | |
MD5:663FFEC826FD9EE696EEB0296718FC95 | SHA256:2EA4E7FAA5F34EC3B82E81D209407D02F51402BF78A261A73C1EC40FC0615922 | |||
| 2200 | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8EC9B1D0ABBD7F98B401D425828828CE_CC2FDB5BF7AAA054F18D8207D17FCE4B | binary | |
MD5:C33213D9BD683913F8BFFF0C2B589EA0 | SHA256:02EDB7C8D9C9649CAA3433D678716C32870039ED45A7A82DB398539C23DB1227 | |||
| 2200 | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:82CD71B6738DAB4B3765C7BFFE4C13C3 | SHA256:7FE955E3A0E4CD091CE1610D1F4B1D45AC58711155303674413FC0C51C8FDAA6 | |||
| 2200 | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:9857F8E44304BDA9FD1CA68223E9D3DA | SHA256:1890BA221DFAF6290EC5FA3DEE1B09C399A4697A8D85FD1C1E1227C39EE3B28F | |||
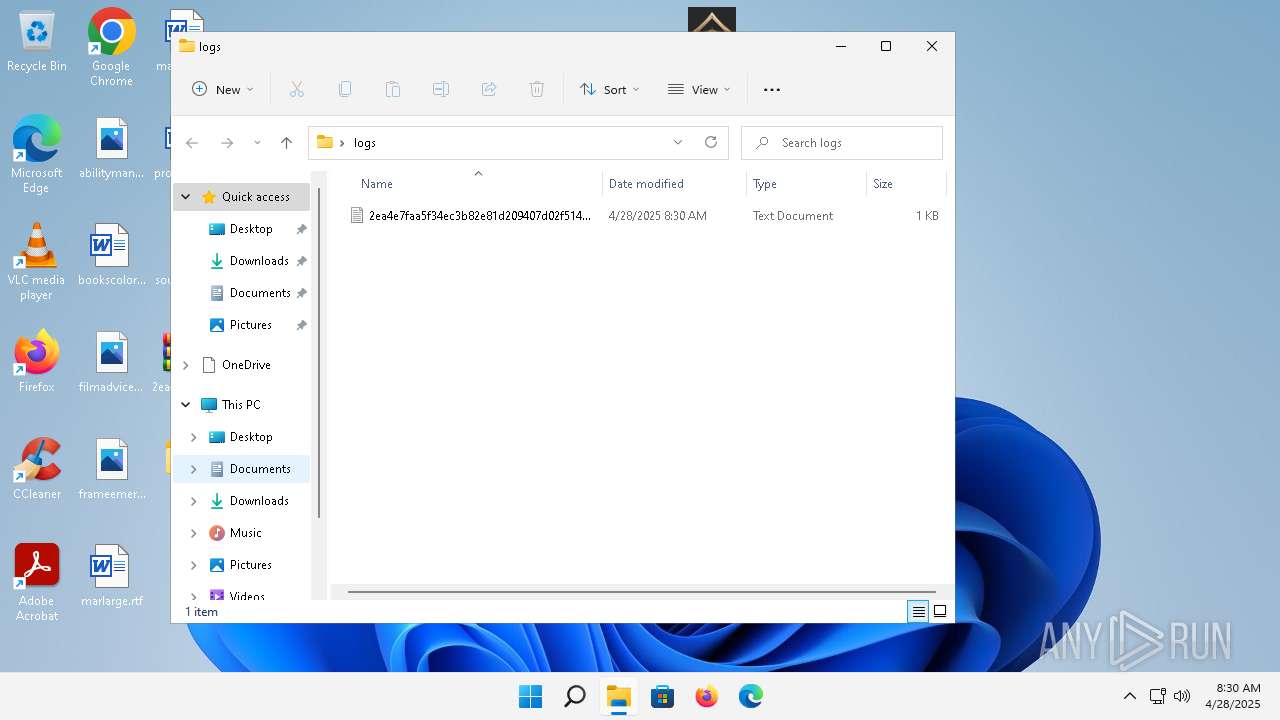
| 1072 | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | C:\Users\admin\Desktop\logs\2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922_250428_083050123_1072.log | text | |
MD5:3B3A9790525EC3800A52DF2BECEBC7E3 | SHA256:E2DC0A0494028CE9F11F63ACC85F67C515BB8E22A7DC5377112D6BF8A64C659C | |||
| 2552 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2552.35232\2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | executable | |
MD5:663FFEC826FD9EE696EEB0296718FC95 | SHA256:2EA4E7FAA5F34EC3B82E81D209407D02F51402BF78A261A73C1EC40FC0615922 | |||
| 2200 | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2552.32446\logs\2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922_250428_083020840_2200.log | text | |
MD5:9E376373E533D6ABECD8AA96E38C1DEB | SHA256:7FD98986269A7D4C3DB4929379FB6DC7F00C7B6F36DD8D62990CD9967BE981A8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
18
DNS requests
12
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3460 | smartscreen.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?99c8b7af08ef5c15 | unknown | — | — | whitelisted |
3460 | smartscreen.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3640 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2200 | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
2200 | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
2200 | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAQuG78QBdk%2FfJm%2BvbMLhcQ%3D | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?e8295883656f7dad | unknown | — | — | whitelisted |
1352 | svchost.exe | GET | 200 | 184.24.77.20:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?7ffa61214c1c53e3 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?15be5abb986864ed | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1352 | svchost.exe | 184.24.77.4:80 | — | Akamai International B.V. | DE | unknown |
3460 | smartscreen.exe | 48.209.162.134:443 | checkappexec.microsoft.com | — | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3460 | smartscreen.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
3460 | smartscreen.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
4556 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3640 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3640 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2200 | 2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2776 | svchost.exe | 20.42.73.27:443 | v10.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
v10.events.data.microsoft.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
dns.msftncsi.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1352 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
Process | Message |
|---|---|
2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | [2025-04-28 08:30:21.871][ERROR] ArgumentParser::Parse : Argument is null!!
|
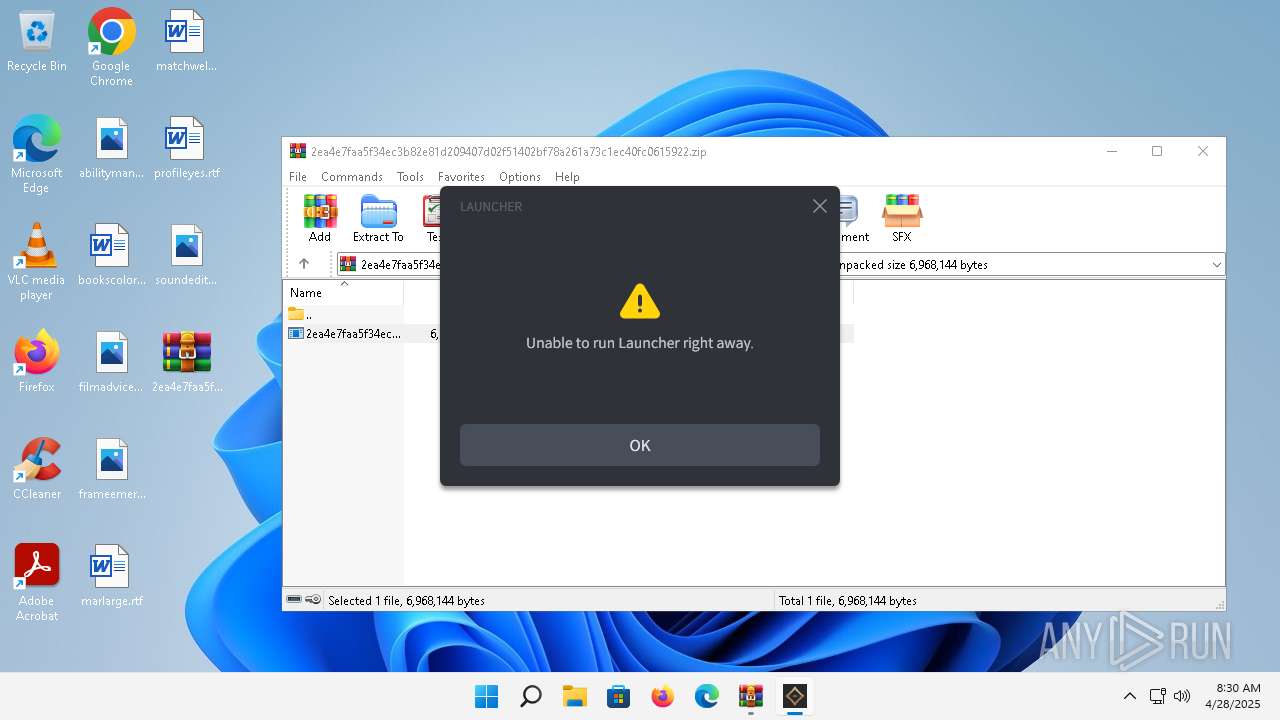
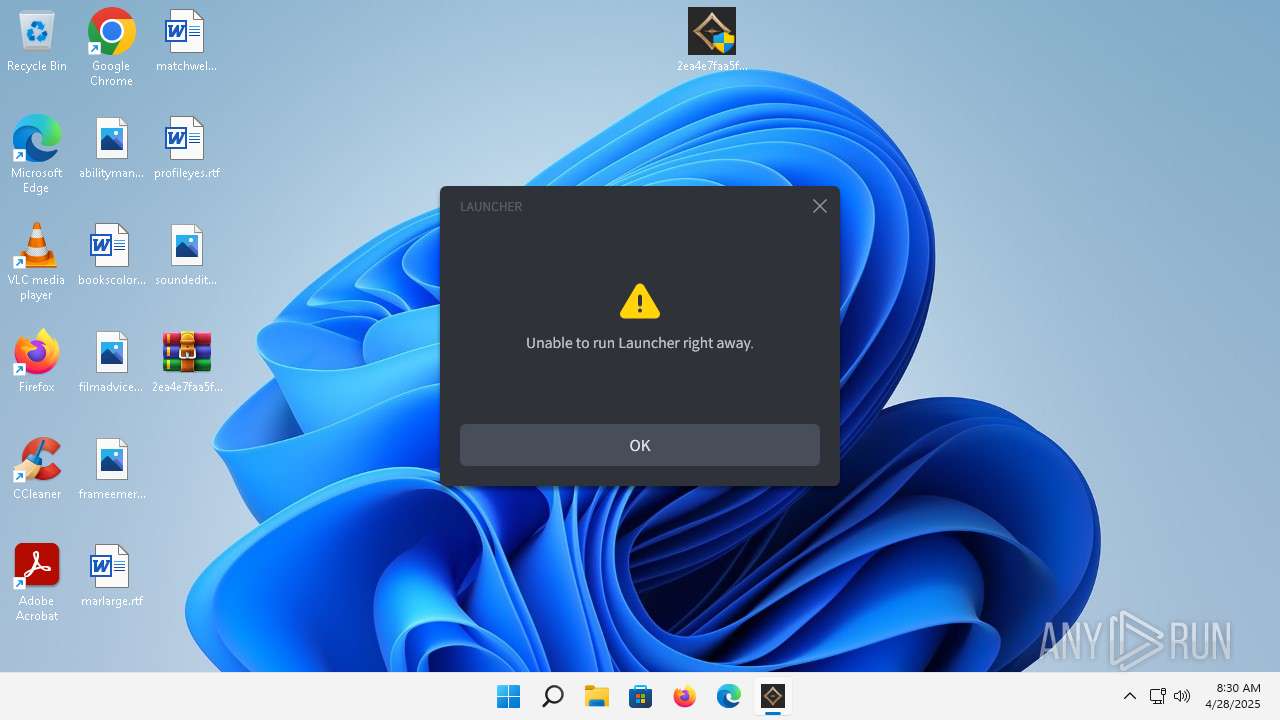
2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | [2025-04-28 08:30:21.887][ERROR] Unable to run Launcher right away.
|
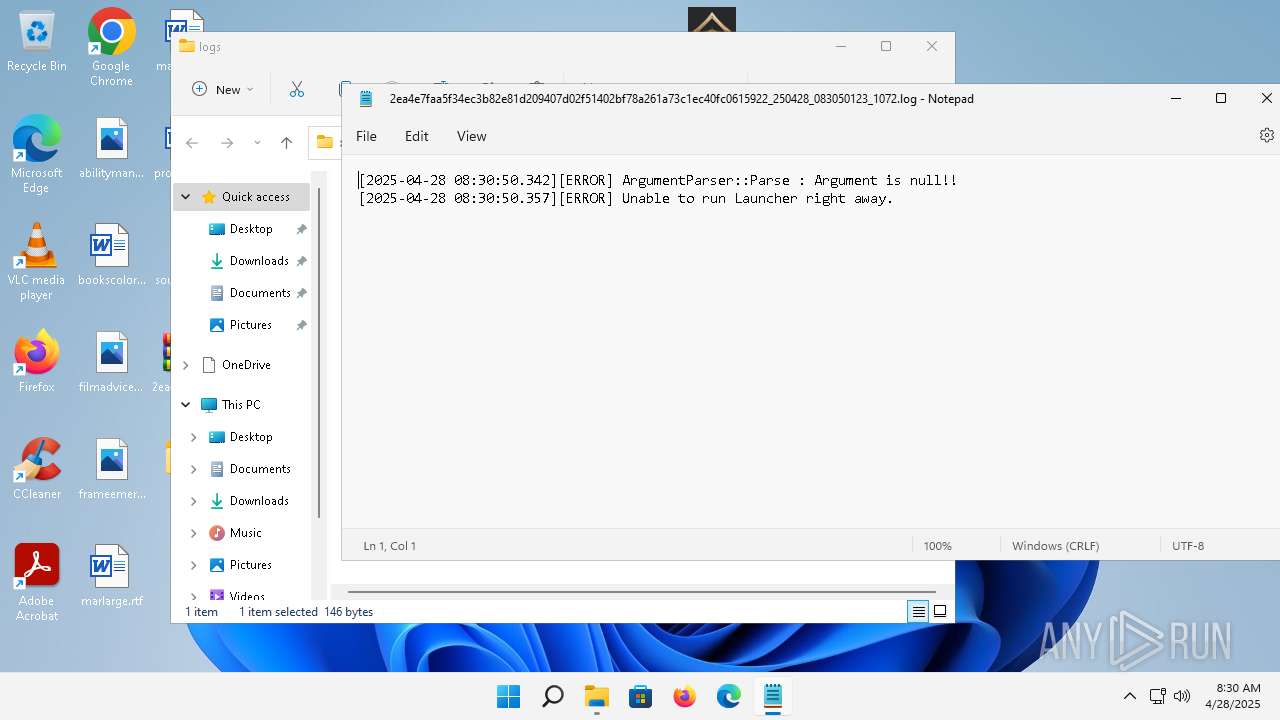
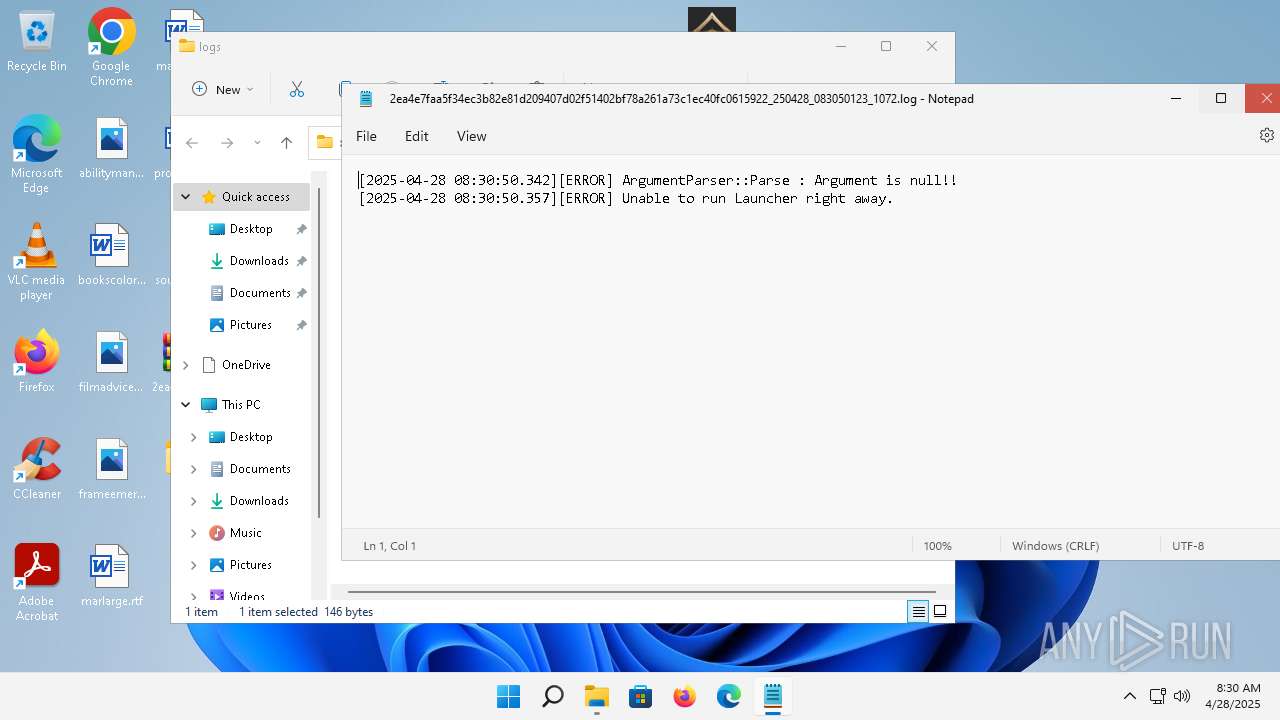
2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | [2025-04-28 08:30:50.342][ERROR] ArgumentParser::Parse : Argument is null!!
|
2ea4e7faa5f34ec3b82e81d209407d02f51402bf78a261a73c1ec40fc0615922.exe | [2025-04-28 08:30:50.357][ERROR] Unable to run Launcher right away.
|