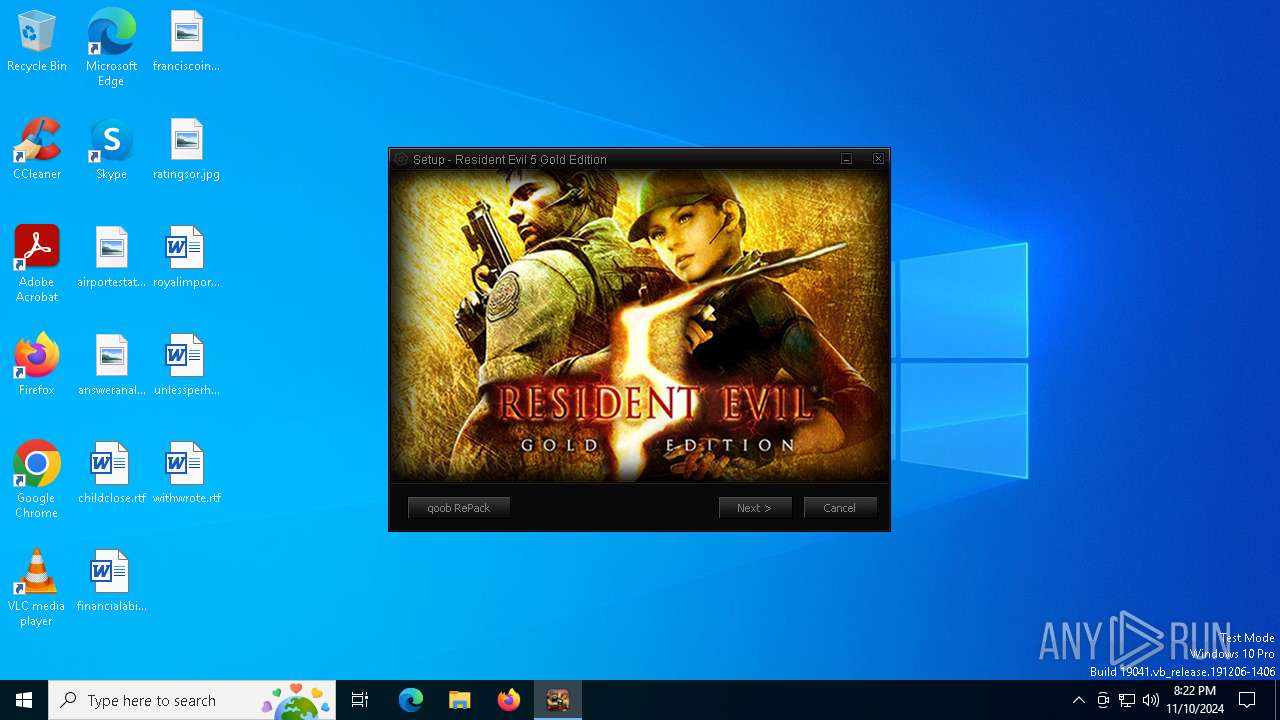
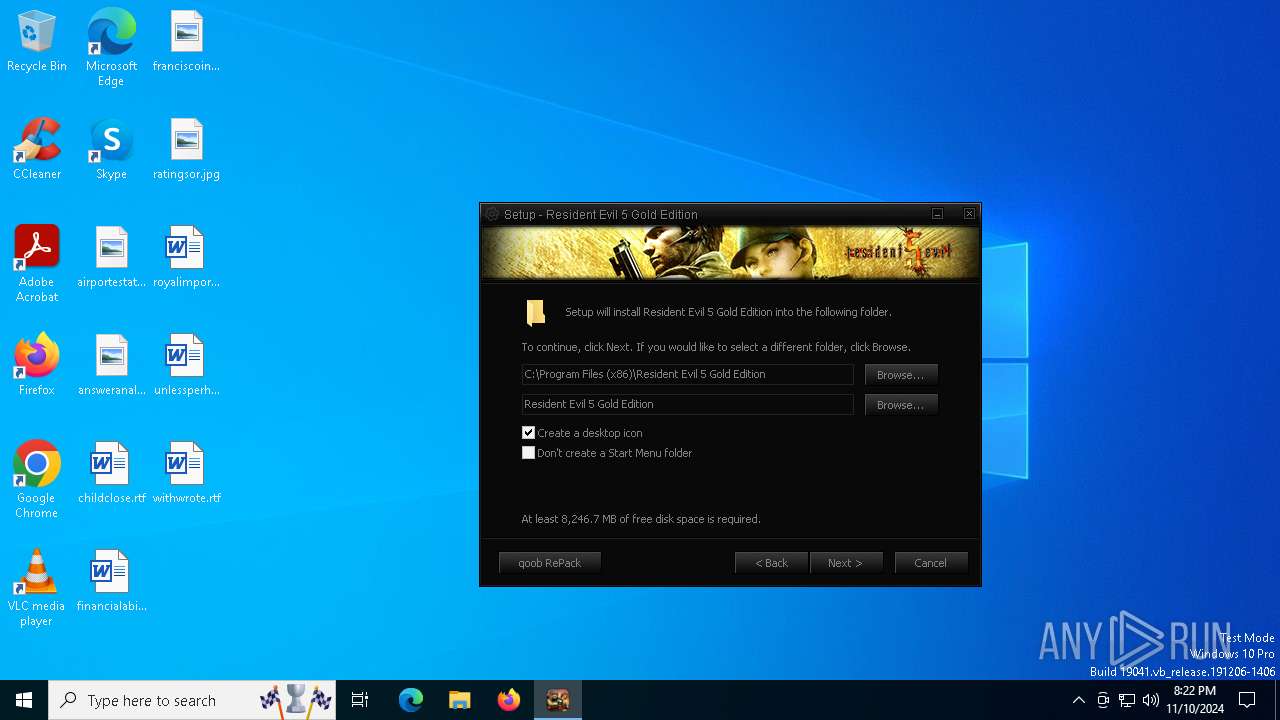
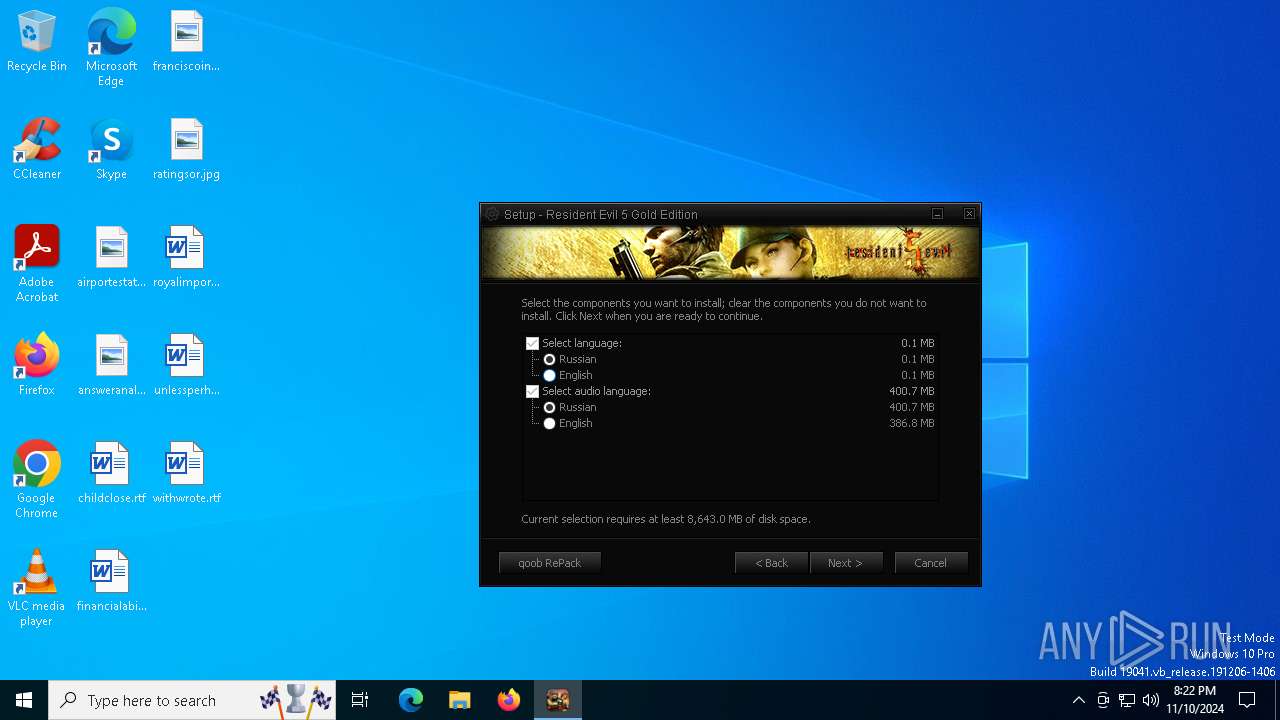
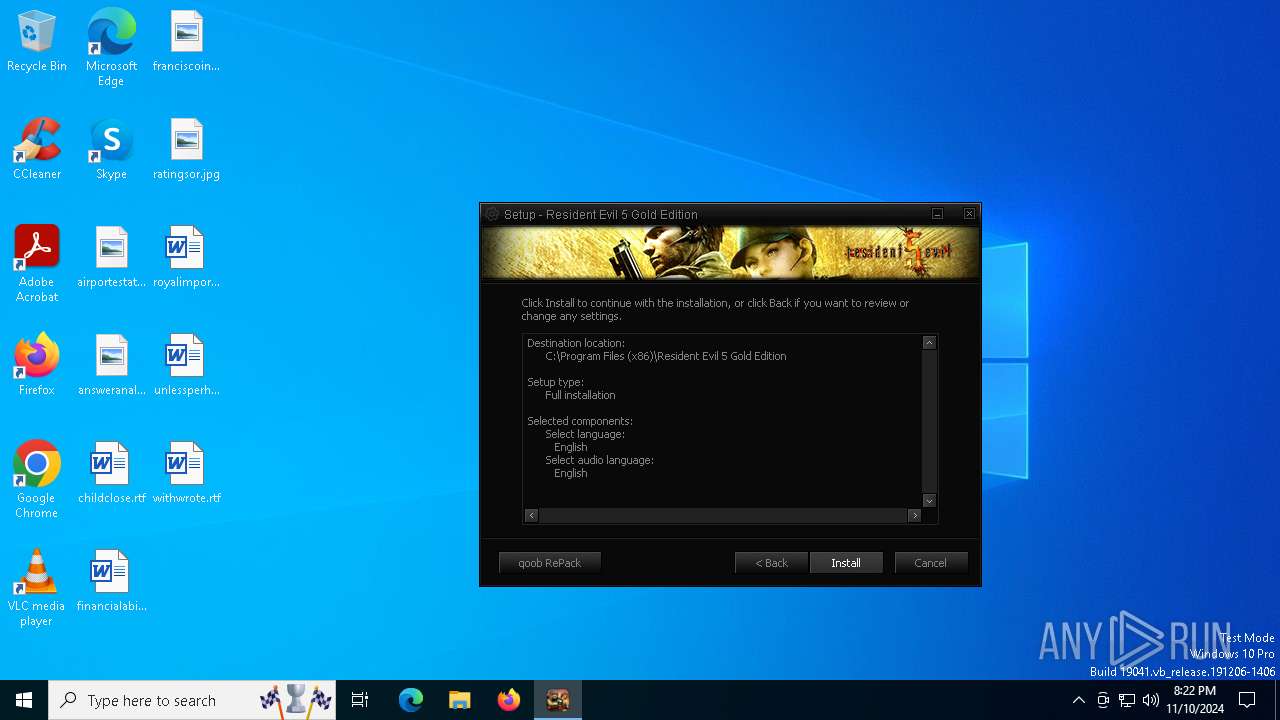
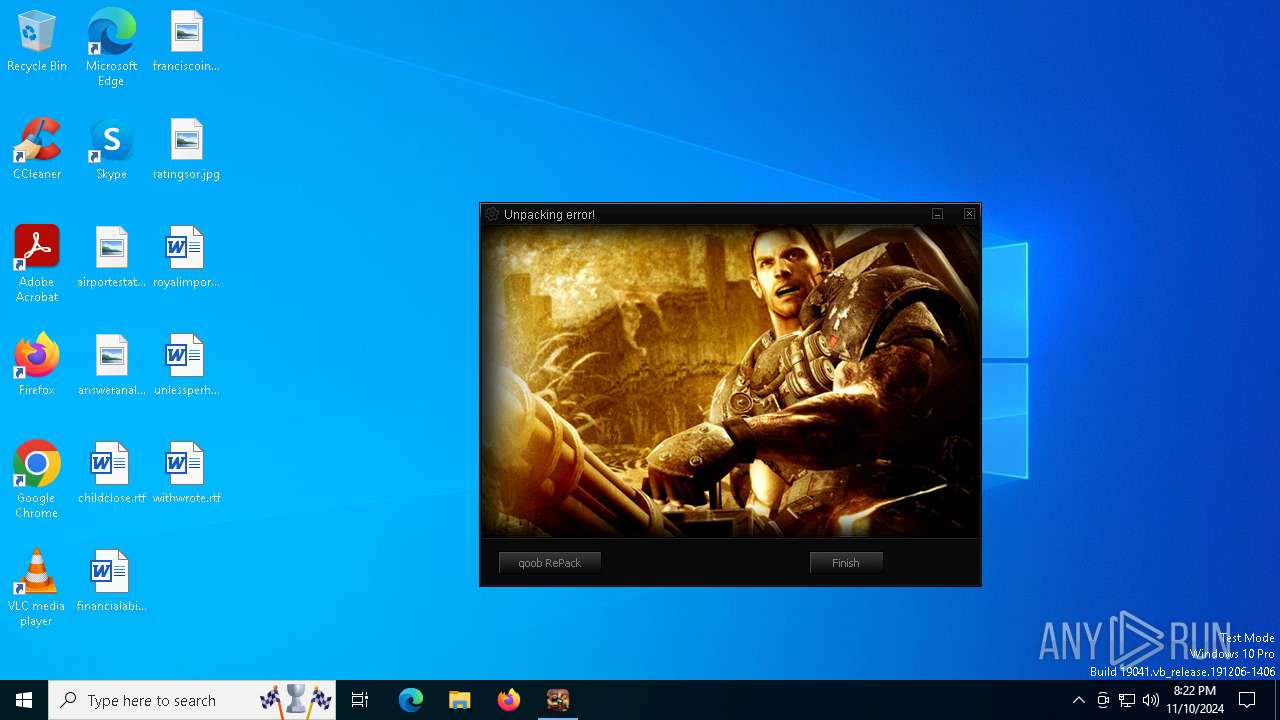
| File name: | Setup.exe |
| Full analysis: | https://app.any.run/tasks/982e7609-cf33-4f87-9d09-06ce0388e413 |
| Verdict: | Malicious activity |
| Analysis date: | November 10, 2024, 20:21:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 8DFF0B049FF0CF67936914A3D35F947B |
| SHA1: | B457972A2AB40DD6FF815ADCC95BDA094EEB66DE |
| SHA256: | 63786B955D3C62903C8388FABBD48E46B00C12A0F53A5FFFC62A4FDEC075484D |
| SSDEEP: | 98304:YdQy9jysXAZDeGNv2pB3aqBuxAOiegt1ibUgFMePt/jdInhnnNVlRV/8EnnGB5bm:QKNHOFKR8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- Setup.tmp (PID: 6316)
- Setup.exe (PID: 6468)
- unins000.exe (PID: 7000)
- _iu14D2N.tmp (PID: 6688)
Process drops legitimate windows executable
- Setup.tmp (PID: 6316)
- _iu14D2N.tmp (PID: 6688)
Reads the Windows owner or organization settings
- Setup.tmp (PID: 6316)
There is functionality for taking screenshot (YARA)
- Setup.tmp (PID: 6316)
Starts application with an unusual extension
- unins000.exe (PID: 7000)
Starts itself from another location
- unins000.exe (PID: 7000)
INFO
Create files in a temporary directory
- Setup.exe (PID: 6468)
- Setup.tmp (PID: 6316)
Checks supported languages
- Setup.exe (PID: 6468)
- Setup.tmp (PID: 6316)
Reads the computer name
- Setup.tmp (PID: 6316)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (81.5) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10.5) |
| .exe | | | Win32 Executable (generic) (3.3) |
| .exe | | | Win16/32 Executable Delphi generic (1.5) |
| .exe | | | Generic Win/DOS Executable (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 37888 |
| InitializedDataSize: | 95744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9c14 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | |
| FileDescription: | Setup |
| FileVersion: | 1.0 |
| LegalCopyright: | Setup |
| ProductName: | Setup |
| ProductVersion: | 1.0.0.129.U1 |
Total processes
140
Monitored processes
7
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6288 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup Exit code: 3221226540 Version: 1.0 Modules
| |||||||||||||||
| 6316 | "C:\Users\admin\AppData\Local\Temp\is-J3NQ9.tmp\Setup.tmp" /SL5="$4029A,1450874,134656,C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-J3NQ9.tmp\Setup.tmp | Setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 6380 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6468 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup Exit code: 0 Version: 1.0 Modules
| |||||||||||||||
| 6688 | "C:\Users\admin\AppData\Local\Temp\_iu14D2N.tmp" /SECONDPHASE="C:\Program Files (x86)\Resident Evil 5 Gold Edition\unins000.exe" /FIRSTPHASEWND=$50290 /VERYSILENT | C:\Users\admin\AppData\Local\Temp\_iu14D2N.tmp | unins000.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 7000 | "C:\Program Files (x86)\Resident Evil 5 Gold Edition\unins000.exe" /VERYSILENT | C:\Program Files (x86)\Resident Evil 5 Gold Edition\unins000.exe | Setup.tmp | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 7116 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
700
Read events
669
Write events
25
Delete events
6
Modification events
| (PID) Process: | (6316) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CAPCOM\RESIDENT EVIL 5 |
| Operation: | write | Name: | launch |
Value: 0 | |||
| (PID) Process: | (6316) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CAPCOM\RESIDENT EVIL 5 |
| Operation: | write | Name: | GUID |
Value: {AC08BBA0-96B9-431A-A7D0-D8598E493775} | |||
| (PID) Process: | (6316) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CAPCOM\RESIDENT EVIL 5 |
| Operation: | write | Name: | InstallDir |
Value: C:\Program Files (x86)\Resident Evil 5 Gold Edition\ | |||
| (PID) Process: | (6316) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\CAPCOM\RESIDENT EVIL 5 |
| Operation: | write | Name: | Language |
Value: 1033 | |||
| (PID) Process: | (6316) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Resident Evil 5 Gold Edition_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.5.1.ee2 (a) | |||
| (PID) Process: | (6316) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Resident Evil 5 Gold Edition_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files (x86)\Resident Evil 5 Gold Edition | |||
| (PID) Process: | (6316) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Resident Evil 5 Gold Edition_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\Resident Evil 5 Gold Edition\ | |||
| (PID) Process: | (6316) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Resident Evil 5 Gold Edition_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Resident Evil 5 Gold Edition | |||
| (PID) Process: | (6316) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Resident Evil 5 Gold Edition_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (6316) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Resident Evil 5 Gold Edition_is1 |
| Operation: | write | Name: | Inno Setup: Setup Type |
Value: full | |||
Executable files
18
Suspicious files
1
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
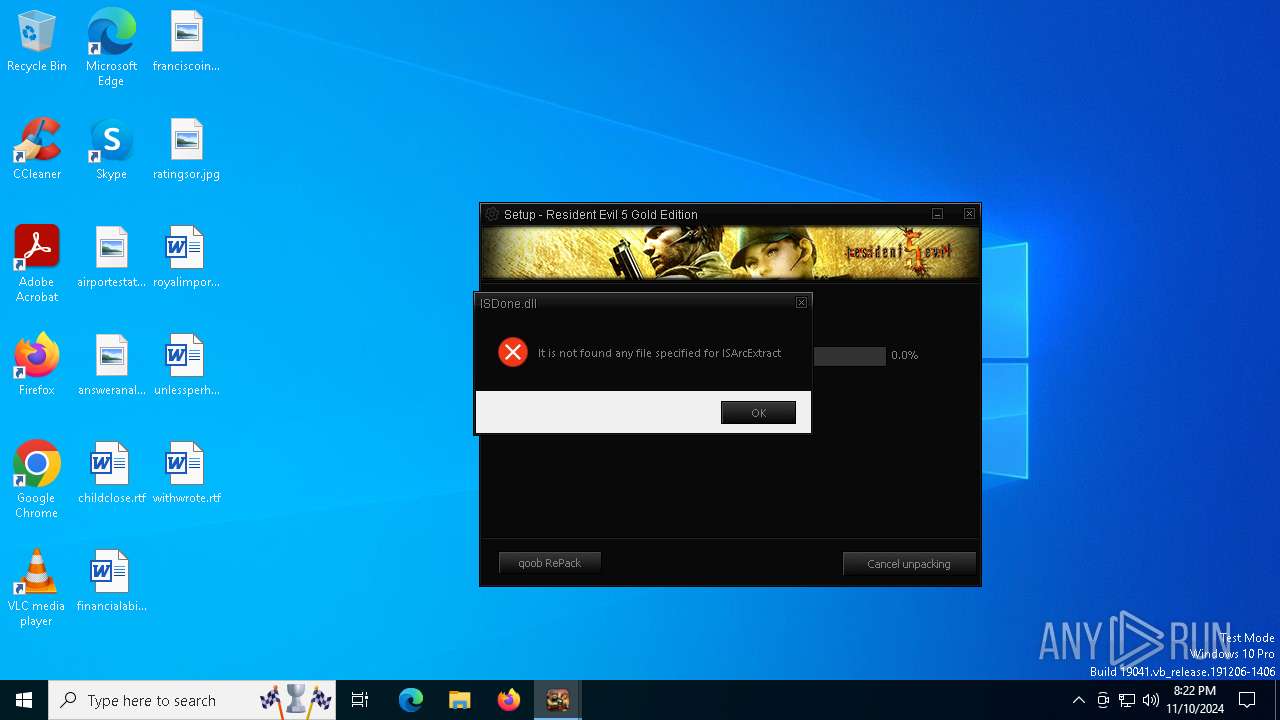
| 6316 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-UUO59.tmp\ISDone.dll | executable | |
MD5:4FEAFA8B5E8CDB349125C8AF0AC43974 | SHA256:BB8A0245DCC5C10A1C7181BAD509B65959855009A8105863EF14F2BB5B38AC71 | |||
| 6316 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-UUO59.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 6316 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-UUO59.tmp\front.bmp | image | |
MD5:CCA01C4F3BCA4C71684E9C691FF1FEAE | SHA256:9D6B5327C9F88C4A2FB08417F7A5410B74107B1898041523FB790ED234F8DB86 | |||
| 6316 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-UUO59.tmp\TRiNiUM.cjstyles | executable | |
MD5:C9F1AC6319EF3FD1F85840D72C971F7A | SHA256:6062BF6F7590DA39FFEEE6C1FDD65833843D56DF748BEA047671CFDF6F57DADA | |||
| 6316 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-UUO59.tmp\pZLib.exe | executable | |
MD5:8E52F6FB1BC36ACBF6052728FDA914BA | SHA256:D838C438108E312F2D0C32E069330063C09DDC558A3B6F9A9AD6393B9DFCDB40 | |||
| 6316 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-UUO59.tmp\English.ini | text | |
MD5:B031BEE9106D82782B43BDF5D4AD79B0 | SHA256:E1B6F4DC9BA12E110B33D370E8F06F176228059C42754BE5DA7B92AB939FF38E | |||
| 6316 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-UUO59.tmp\arc.ini | text | |
MD5:EC6C36FFD06868580068EAC1C21E96F3 | SHA256:252E1A95364CC08C1B3152DE330A419F8C4FBB724F0E137A221911DBCA0B7546 | |||
| 6316 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-UUO59.tmp\Facompress_MT.dll | executable | |
MD5:002508839634E56D43E4FD56E3DF2757 | SHA256:7EEB2C50920E30544E2F180B0C39488501372A8F8BD8393BCB095353E9114CDE | |||
| 6316 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-UUO59.tmp\CLS-srep.dll | executable | |
MD5:522D2FE95820798431E59BD982C373C2 | SHA256:AF4379F3D8E12938A2F4E6D8F7D8F135181C415FA6C443B27EB44C3BE173B2EF | |||
| 6316 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-UUO59.tmp\end.bmp | image | |
MD5:AD5AEFF96966D8AA96DE2F1D4615B9B6 | SHA256:09ED9528A966456DC10A9E3660CF73D11791252946494D960218E1E58A3373AD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
46
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.141:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5940 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1880 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5940 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6688 | _iu14D2N.tmp | GET | 200 | 172.67.212.119:80 | http://innosetup.pro/versions/1217.txt | unknown | — | — | unknown |
6724 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.141:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4360 | SearchApp.exe | 92.123.104.47:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1880 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |