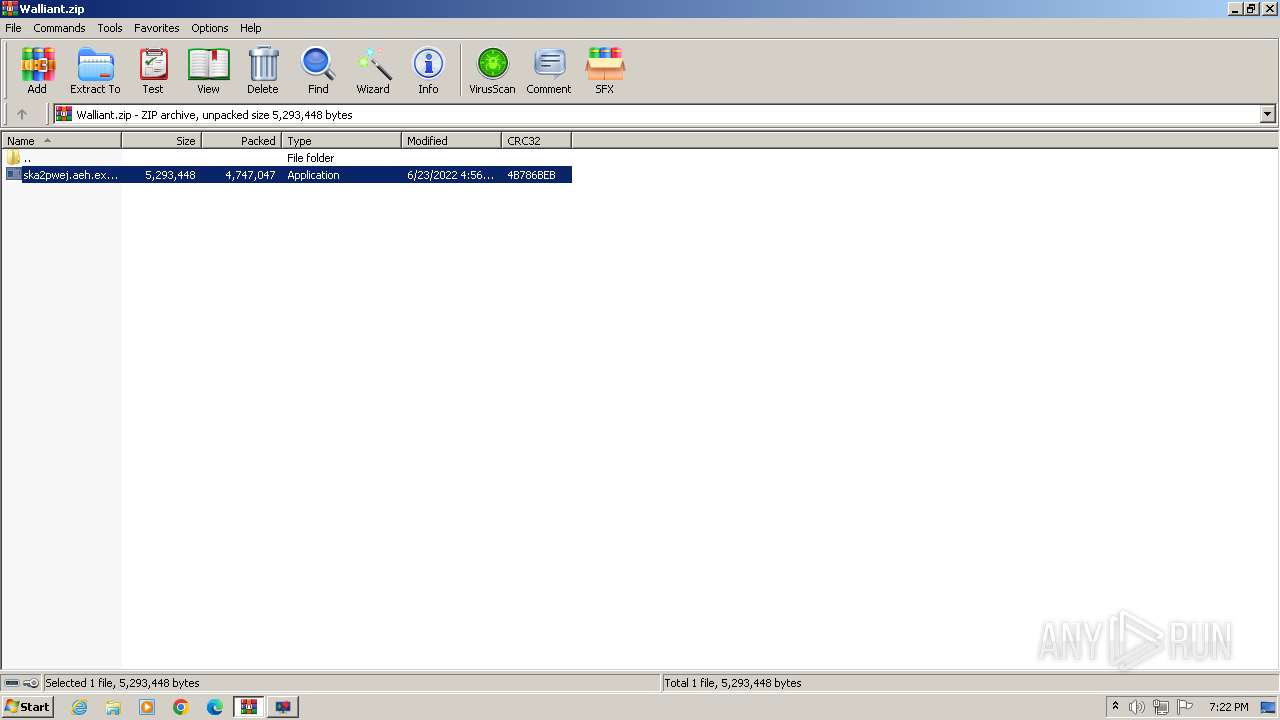
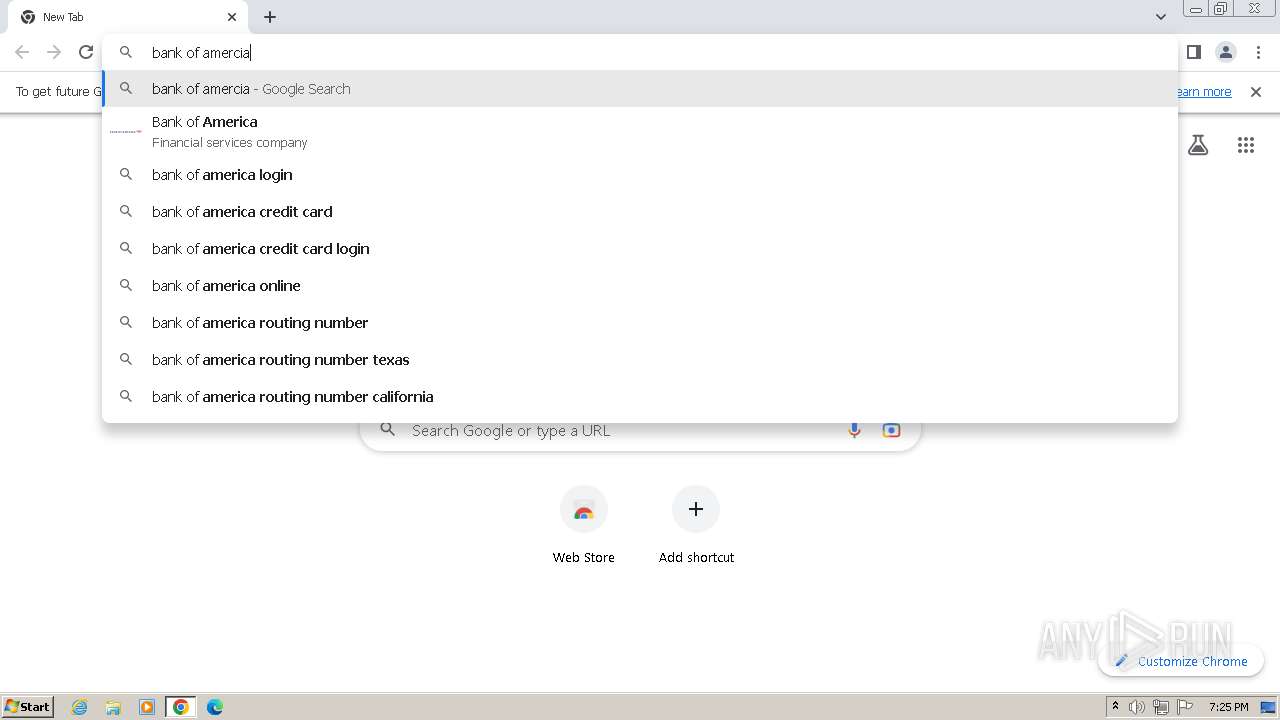
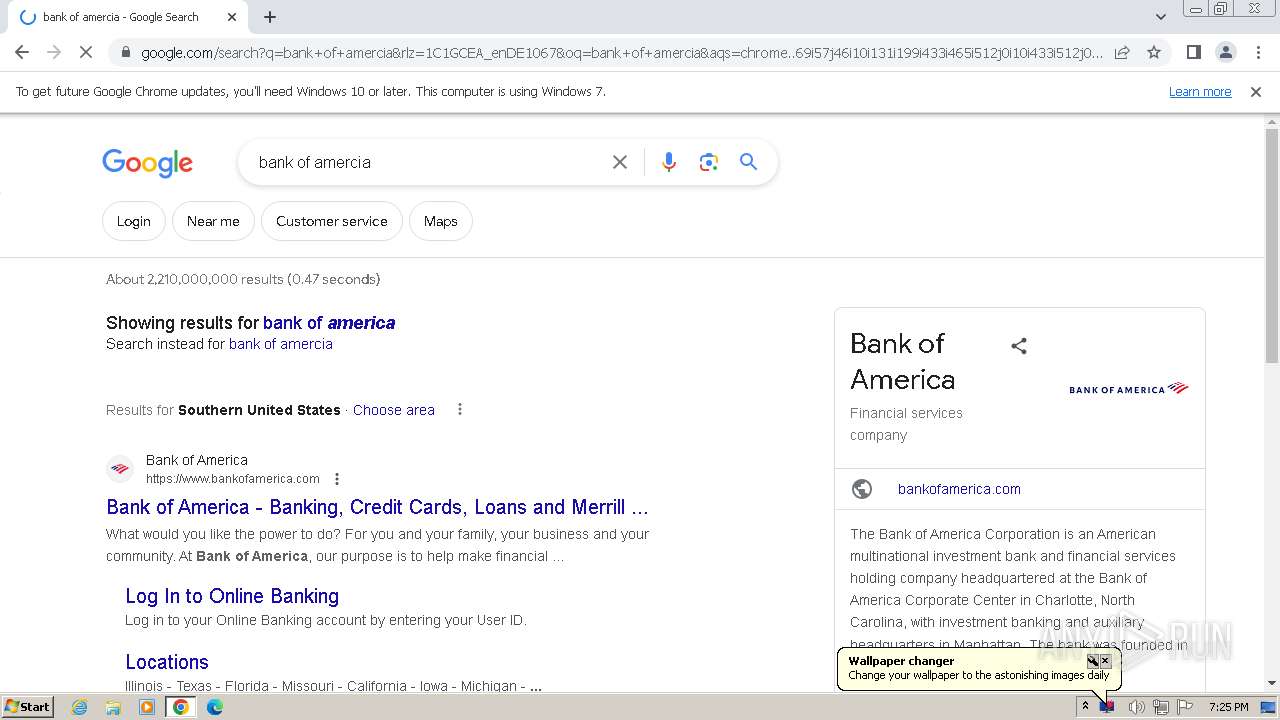
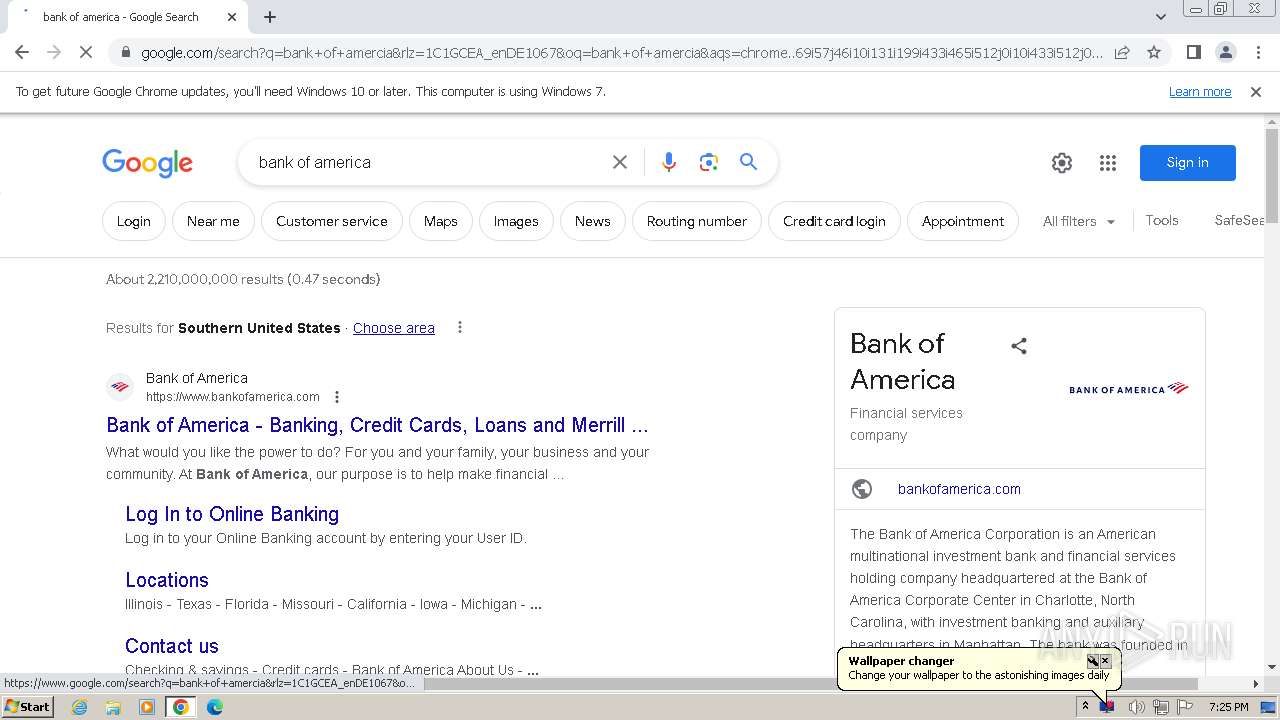
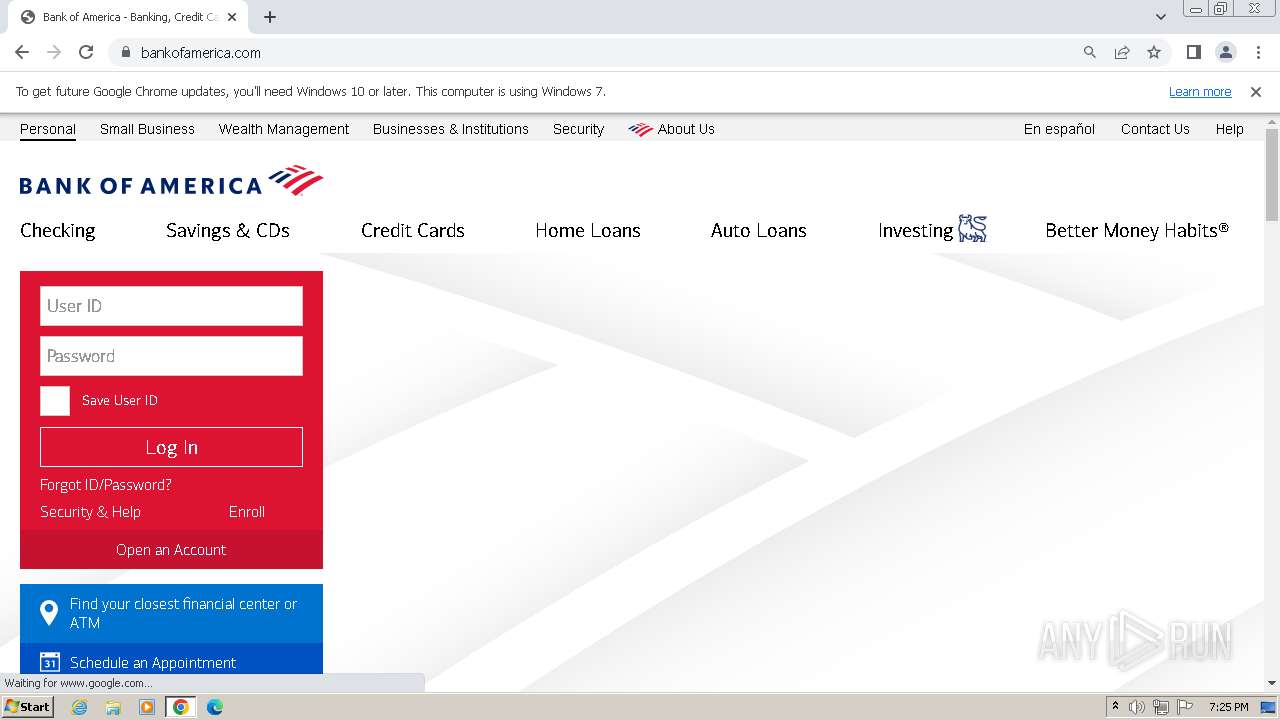
| File name: | Walliant.zip |
| Full analysis: | https://app.any.run/tasks/e240b602-f8ec-4283-945e-8549946a45e8 |
| Verdict: | Malicious activity |
| Analysis date: | October 23, 2023, 18:21:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 33968A33F7E098D31920C07E56C66DE2 |
| SHA1: | 9C684A0DADAE9F940DD40D8D037FAA6ADDF22DDB |
| SHA256: | 6364269DBDC73D638756C2078ECB1A39296DDD12B384D05121045F95D357D504 |
| SSDEEP: | 98304:QXEXw3QBAg+V40y49wQ2pFQ0xxYtroaNrZaYzu9:kEA3AAg+Vt9V81xxYtfNLO |
MALICIOUS
Drops the executable file immediately after the start
- ska2pwej.aeh.exe (PID: 1848)
- ska2pwej.aeh.tmp (PID: 2824)
- xkzpbcqh.exe (PID: 3852)
- walliant.exe (PID: 3808)
- xkzpbcqh.tmp (PID: 976)
Application was dropped or rewritten from another process
- walliant.exe (PID: 3808)
- xkzpbcqh.exe (PID: 3852)
- Walliant.exe (PID: 3812)
Loads dropped or rewritten executable
- walliant.exe (PID: 3808)
- Walliant.exe (PID: 3812)
Changes the autorun value in the registry
- Walliant.exe (PID: 3812)
SUSPICIOUS
Reads the Windows owner or organization settings
- ska2pwej.aeh.tmp (PID: 2824)
- xkzpbcqh.tmp (PID: 976)
Reads settings of System Certificates
- ska2pwej.aeh.tmp (PID: 2824)
- walliant.exe (PID: 3808)
- Walliant.exe (PID: 3812)
- xkzpbcqh.tmp (PID: 976)
Process drops legitimate windows executable
- ska2pwej.aeh.tmp (PID: 2824)
- xkzpbcqh.tmp (PID: 976)
Checks Windows Trust Settings
- walliant.exe (PID: 3808)
- Walliant.exe (PID: 3812)
Reads security settings of Internet Explorer
- walliant.exe (PID: 3808)
- Walliant.exe (PID: 3812)
Reads the Internet Settings
- walliant.exe (PID: 3808)
- Walliant.exe (PID: 3812)
Reads Internet Explorer settings
- walliant.exe (PID: 3808)
- Walliant.exe (PID: 3812)
Reads Microsoft Outlook installation path
- walliant.exe (PID: 3808)
- Walliant.exe (PID: 3812)
Searches for installed software
- xkzpbcqh.tmp (PID: 976)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 556)
Checks supported languages
- ska2pwej.aeh.exe (PID: 1848)
- ska2pwej.aeh.tmp (PID: 2824)
- walliant.exe (PID: 3808)
- xkzpbcqh.exe (PID: 3852)
- xkzpbcqh.tmp (PID: 976)
- Walliant.exe (PID: 3812)
Reads the computer name
- ska2pwej.aeh.tmp (PID: 2824)
- walliant.exe (PID: 3808)
- xkzpbcqh.tmp (PID: 976)
- Walliant.exe (PID: 3812)
Reads the machine GUID from the registry
- ska2pwej.aeh.tmp (PID: 2824)
- walliant.exe (PID: 3808)
- Walliant.exe (PID: 3812)
- xkzpbcqh.tmp (PID: 976)
Create files in a temporary directory
- ska2pwej.aeh.exe (PID: 1848)
- walliant.exe (PID: 3808)
- xkzpbcqh.exe (PID: 3852)
- xkzpbcqh.tmp (PID: 976)
Application was dropped or rewritten from another process
- ska2pwej.aeh.tmp (PID: 2824)
Creates files or folders in the user directory
- ska2pwej.aeh.tmp (PID: 2824)
- walliant.exe (PID: 3808)
- xkzpbcqh.tmp (PID: 976)
Reads product name
- walliant.exe (PID: 3808)
- Walliant.exe (PID: 3812)
Reads Environment values
- walliant.exe (PID: 3808)
- Walliant.exe (PID: 3812)
Checks proxy server information
- walliant.exe (PID: 3808)
- Walliant.exe (PID: 3812)
Reads the time zone
- Walliant.exe (PID: 3812)
Application launched itself
- chrome.exe (PID: 1692)
- msedge.exe (PID: 3748)
- chrome.exe (PID: 3340)
The process uses the downloaded file
- chrome.exe (PID: 1144)
- chrome.exe (PID: 2880)
- chrome.exe (PID: 1032)
Manual execution by a user
- chrome.exe (PID: 1692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | ska2pwej.aeh.exe |
|---|---|
| ZipUncompressedSize: | 5293448 |
| ZipCompressedSize: | 4747047 |
| ZipCRC: | 0x4b786beb |
| ZipModifyDate: | 2022:06:23 18:56:34 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0001 |
| ZipRequiredVersion: | 20 |
Total processes
86
Monitored processes
49
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4340 --field-trial-handle=1164,i,8662241861587882323,18235674275203781155,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 556 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Walliant.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 976 | "C:\Users\admin\AppData\Local\Temp\is-G9IQ0.tmp\xkzpbcqh.tmp" /SL5="$13012C,5010045,830976,C:\Users\admin\AppData\Local\Temp\xkzpbcqh.exe" /VERYSILENT /SUPPRESSMSGBOXES /NOCANCEL /NORESTART | C:\Users\admin\AppData\Local\Temp\is-G9IQ0.tmp\xkzpbcqh.tmp | xkzpbcqh.exe | ||||||||||||
User: admin Company: Walliant Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1032 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4032 --field-trial-handle=1164,i,8662241861587882323,18235674275203781155,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1144 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2288 --field-trial-handle=1164,i,8662241861587882323,18235674275203781155,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1396 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1504 --field-trial-handle=1164,i,8662241861587882323,18235674275203781155,131072 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1692 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1764 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --no-sandbox --disable-breakpad --headless=new --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\Temp\chrome-runner2670878196" --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=984 --field-trial-handle=1148,i,100442801975069013,2121862925999964396,131072 --enable-features=NetworkService,NetworkServiceInProcess --disable-features=AutofillServerCommunication,InterestFeedContentSuggestions,MediaRouter,PaintHolding,Translate /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
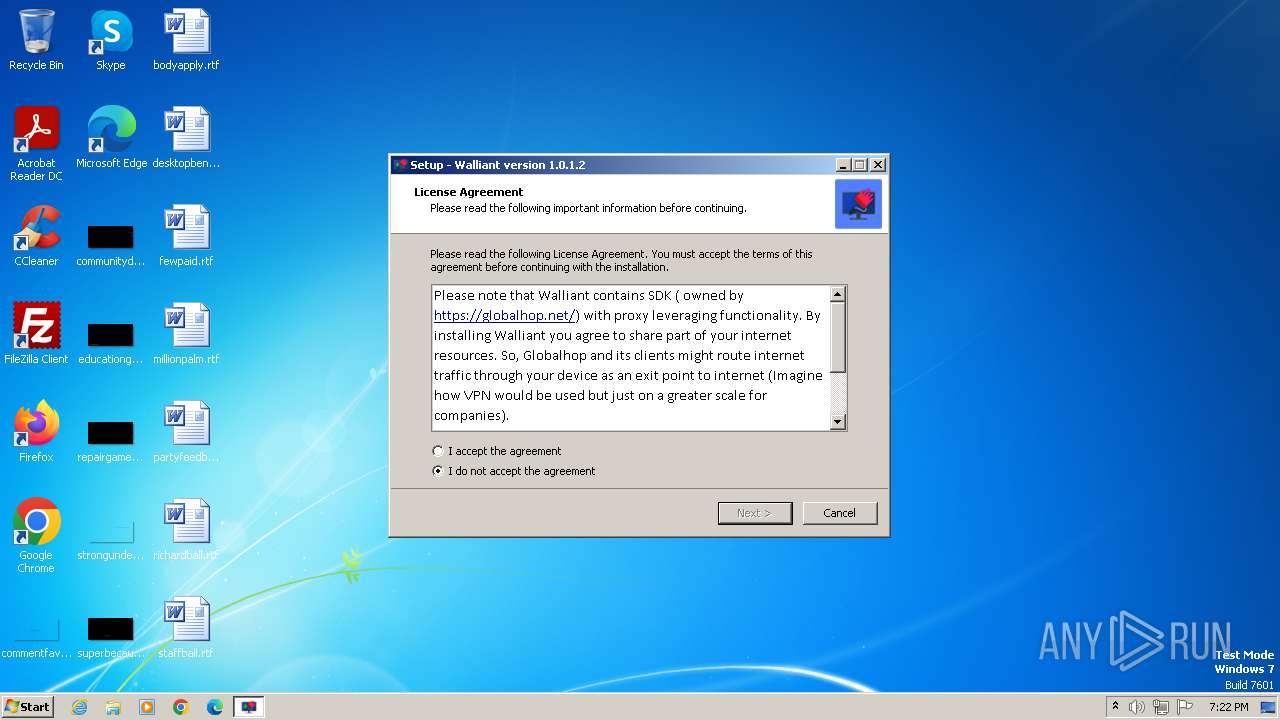
| 1848 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb556.30264\ska2pwej.aeh.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb556.30264\ska2pwej.aeh.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Walliant Integrity Level: MEDIUM Description: Walliant Setup Exit code: 0 Version: 1.0.1.2 Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-sandbox --ignore-certificate-errors --mute-audio --ignore-certificate-errors --noerrdialogs --user-data-dir="C:\Users\admin\AppData\Local\Temp\chrome-runner2812944890" --mojo-platform-channel-handle=1380 --field-trial-handle=1308,i,947365802224771944,17028331048590010273,131072 --enable-features=NetworkService,NetworkServiceInProcess --disable-features=AutofillServerCommunication,InterestFeedContentSuggestions,MediaRouter,PaintHolding,Translate /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
26 855
Read events
26 602
Write events
237
Delete events
16
Modification events
| (PID) Process: | (556) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (556) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
40
Suspicious files
504
Text files
96
Unknown types
57
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2824 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\is-VEDBU.tmp | executable | |
MD5:60D3737A1F84758238483D865A3056DC | SHA256:3436C29DEC2C7F633F4766ACAF334F6C395D70EA6180C0EA7C1610591D5D89B9 | |||
| 2824 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\is-C41PA.tmp | executable | |
MD5:35CBDBE6987B9951D3467DDA2F318F3C | SHA256:E4915F18FD6713EE84F27A06ED1F6F555CDBEBE1522792CF4B4961664550CF83 | |||
| 2824 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\walliant.exe | executable | |
MD5:60D3737A1F84758238483D865A3056DC | SHA256:3436C29DEC2C7F633F4766ACAF334F6C395D70EA6180C0EA7C1610591D5D89B9 | |||
| 2824 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\unins000.exe | executable | |
MD5:62E5DBC52010C304C82ADA0AC564EFF9 | SHA256:BD54AD7A25594DC823572D9B23A3490FF6B8B1742A75E368D110421AB08909B2 | |||
| 2824 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\Countly.dll | executable | |
MD5:BF6A0F5D2D5F54CEB5B899A2172A335B | SHA256:32EF07A1A2954A40436D625814D0CE0E04F4A45E711BEEBC7E159D4C1B2556B6 | |||
| 2824 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\AsyncBridge.Net35.dll | executable | |
MD5:35CBDBE6987B9951D3467DDA2F318F3C | SHA256:E4915F18FD6713EE84F27A06ED1F6F555CDBEBE1522792CF4B4961664550CF83 | |||
| 2824 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\is-0LVRI.tmp | executable | |
MD5:BF6A0F5D2D5F54CEB5B899A2172A335B | SHA256:32EF07A1A2954A40436D625814D0CE0E04F4A45E711BEEBC7E159D4C1B2556B6 | |||
| 2824 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\is-VP3GT.tmp | executable | |
MD5:62E5DBC52010C304C82ADA0AC564EFF9 | SHA256:BD54AD7A25594DC823572D9B23A3490FF6B8B1742A75E368D110421AB08909B2 | |||
| 556 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb556.30264\ska2pwej.aeh.exe | executable | |
MD5:929335D847F8265C0A8648DD6D593605 | SHA256:6613ACB18CB8BF501FBA619F04F8298E5E633CB220C450212BBC9DD2BEF9538D | |||
| 2824 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\SharpRaven.dll | executable | |
MD5:C1A31AB7394444FD8AA2E8FE3C7C5094 | SHA256:64B7231EDA298844697D38DD3539BD97FE995D88AE0C5E0C09D63A908F7336C4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
128
DNS requests
215
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
864 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AJqZYiqGvCtix64S2N84g-M_2020.11.2.164946/EWvH2e-LS80S29cxzuTfRA | unknown | — | — | unknown |
864 | svchost.exe | HEAD | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | unknown |
3808 | walliant.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?78f1aa4193cd9e35 | unknown | compressed | 61.6 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AJqZYiqGvCtix64S2N84g-M_2020.11.2.164946/EWvH2e-LS80S29cxzuTfRA | unknown | binary | 11.1 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AJqZYiqGvCtix64S2N84g-M_2020.11.2.164946/EWvH2e-LS80S29cxzuTfRA | unknown | binary | 8.07 Kb | unknown |
3808 | walliant.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?6aca543146ff7887 | unknown | compressed | 61.6 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AJqZYiqGvCtix64S2N84g-M_2020.11.2.164946/EWvH2e-LS80S29cxzuTfRA | unknown | binary | 18.9 Kb | unknown |
2300 | chrome.exe | GET | 200 | 2.19.198.26:80 | http://aia.entrust.net/l1m-chain256.cer | unknown | binary | 1.30 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AJqZYiqGvCtix64S2N84g-M_2020.11.2.164946/EWvH2e-LS80S29cxzuTfRA | unknown | binary | 7.63 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AJqZYiqGvCtix64S2N84g-M_2020.11.2.164946/EWvH2e-LS80S29cxzuTfRA | unknown | binary | 16.0 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2824 | ska2pwej.aeh.tmp | 104.21.57.77:443 | stats.walliant.com | CLOUDFLARENET | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3808 | walliant.exe | 188.114.97.3:443 | cheverel.net | CLOUDFLARENET | NL | unknown |
3808 | walliant.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3808 | walliant.exe | 104.21.57.77:443 | stats.walliant.com | CLOUDFLARENET | — | unknown |
3808 | walliant.exe | 104.16.123.96:443 | www.cloudflare.com | CLOUDFLARENET | — | unknown |
3808 | walliant.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3808 | walliant.exe | 2.21.20.218:443 | img-prod-cms-rt-microsoft-com.akamaized.net | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
stats.walliant.com |
| unknown |
cheverel.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
www.cloudflare.com |
| whitelisted |
arc.msn.com |
| whitelisted |
img-prod-cms-rt-microsoft-com.akamaized.net |
| whitelisted |
update.walliant.com |
| unknown |
track.walliant.com |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2300 | chrome.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2300 | chrome.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2300 | chrome.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2300 | chrome.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2300 | chrome.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2300 | chrome.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2300 | chrome.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2300 | chrome.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2300 | chrome.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
2300 | chrome.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chrome-runner2670878196 directory exists )
|
chrome.exe | Too long restart command line passed |
chrome.exe | |
msedge.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\chrome-runner2812944890 directory exists )
|
msedge.exe | Too long restart command line passed |
msedge.exe | |
msedge.exe | Error - |