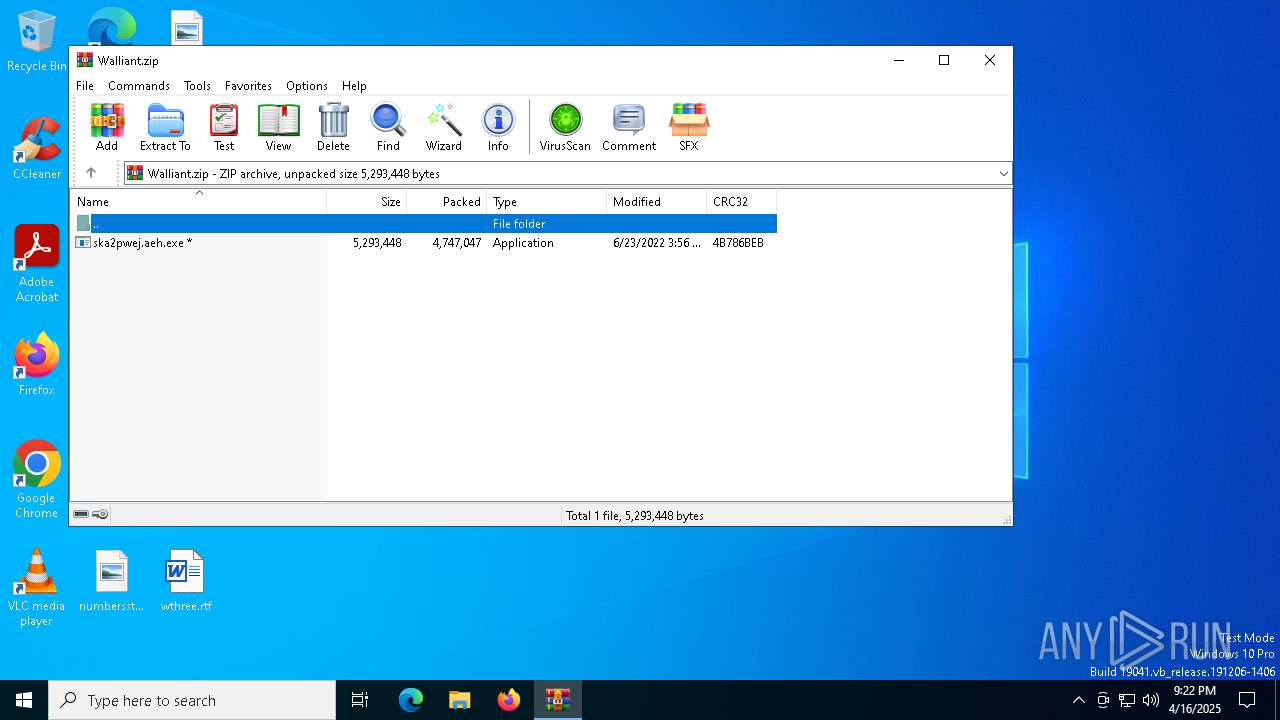
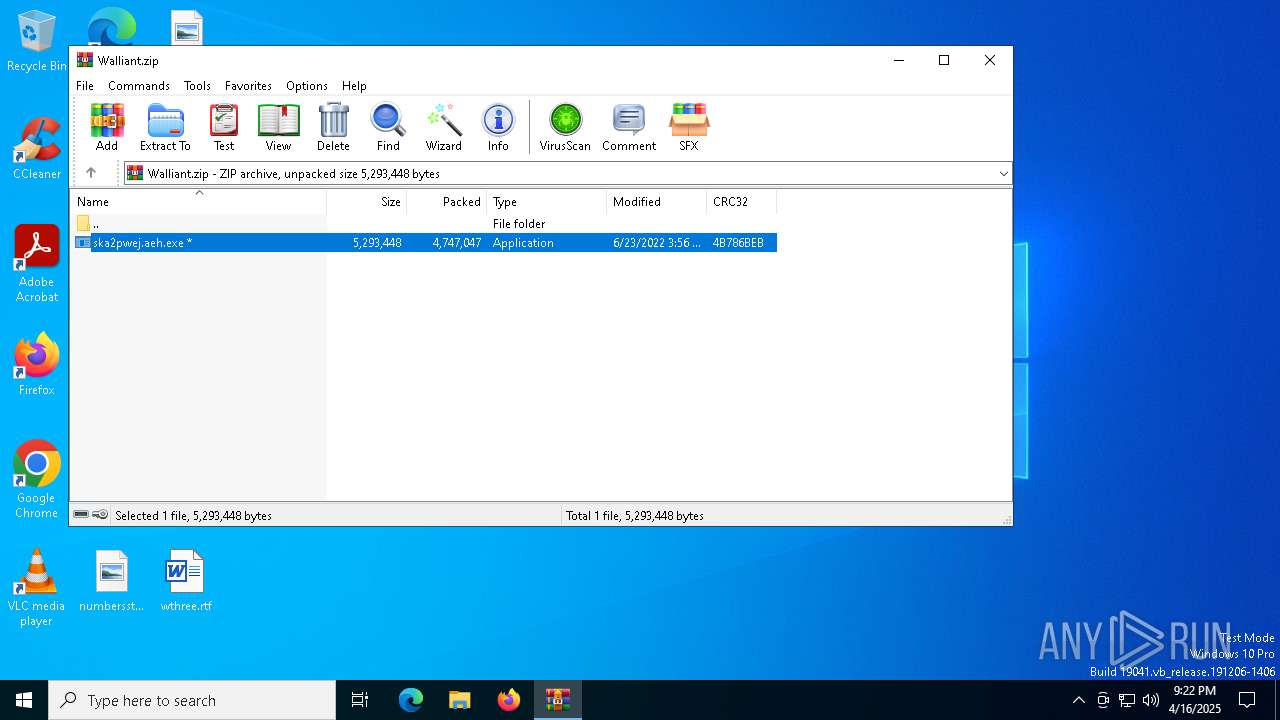
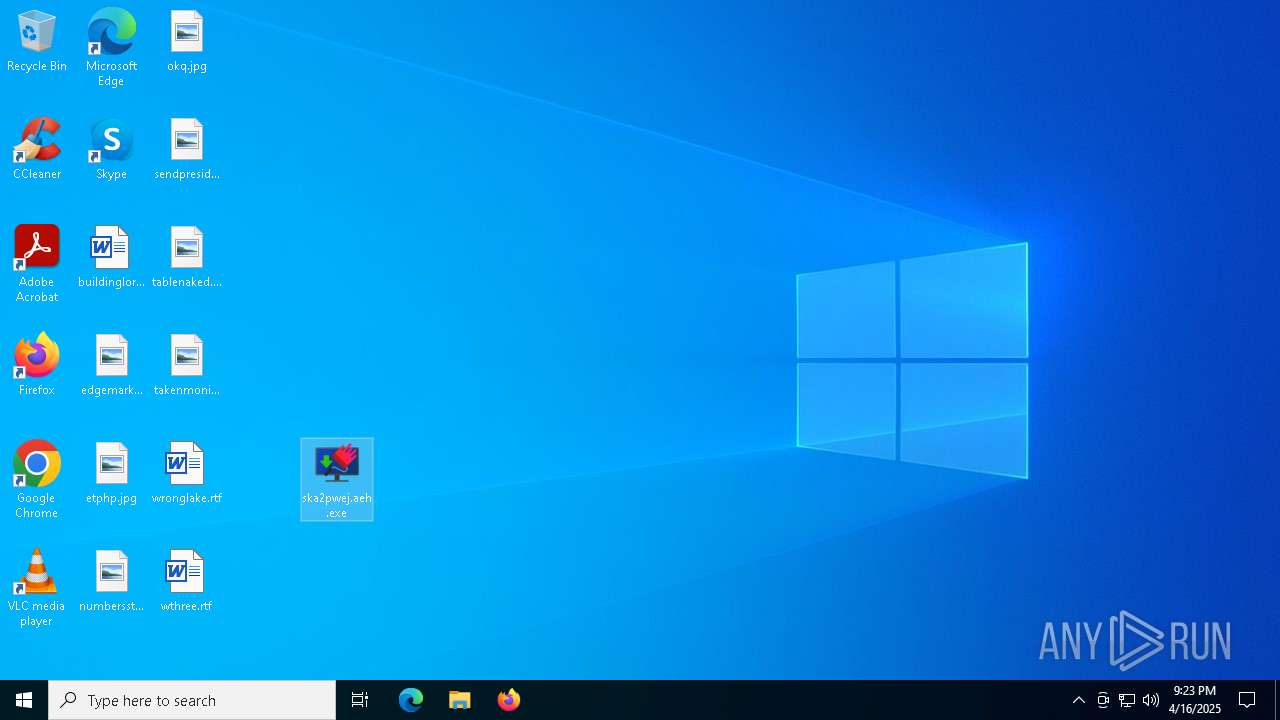
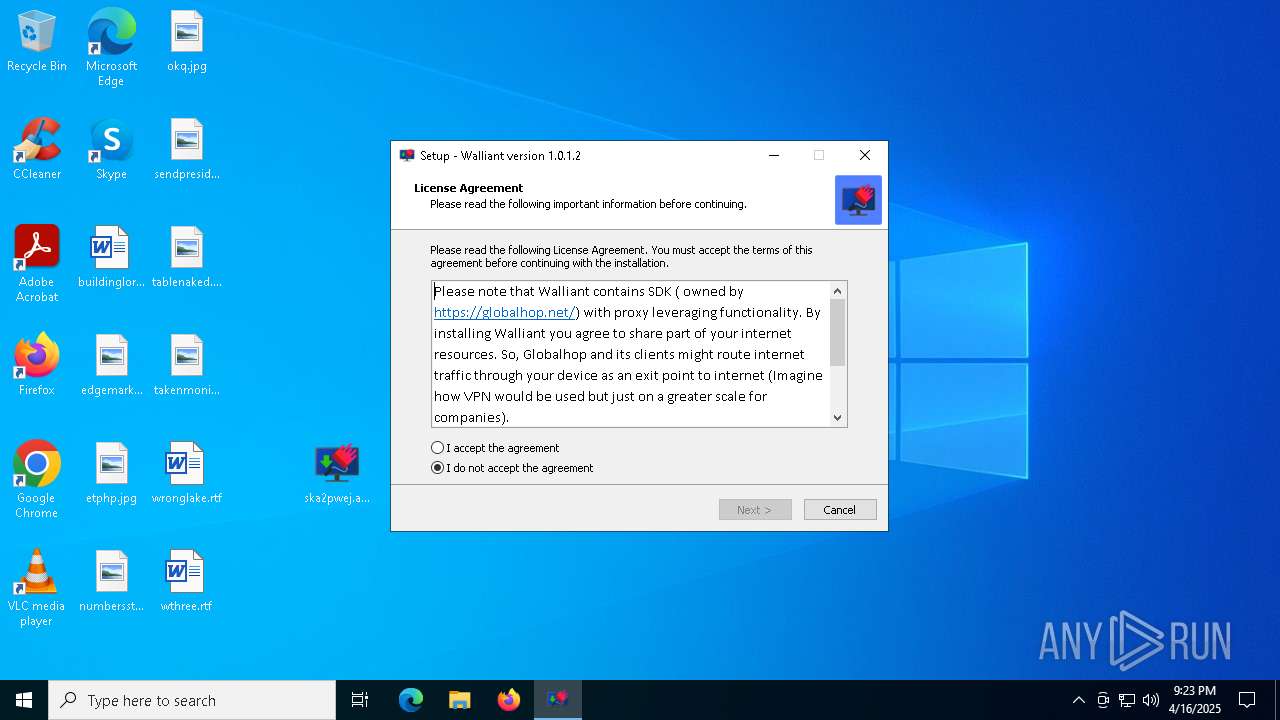
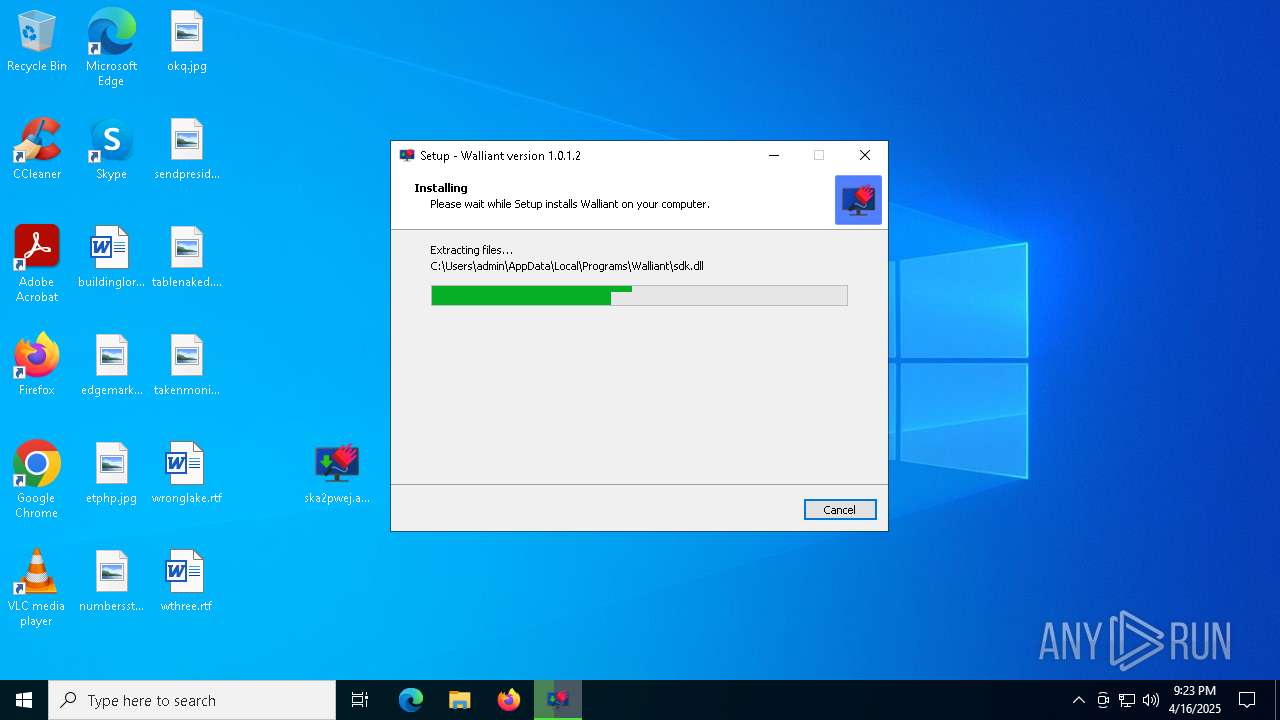
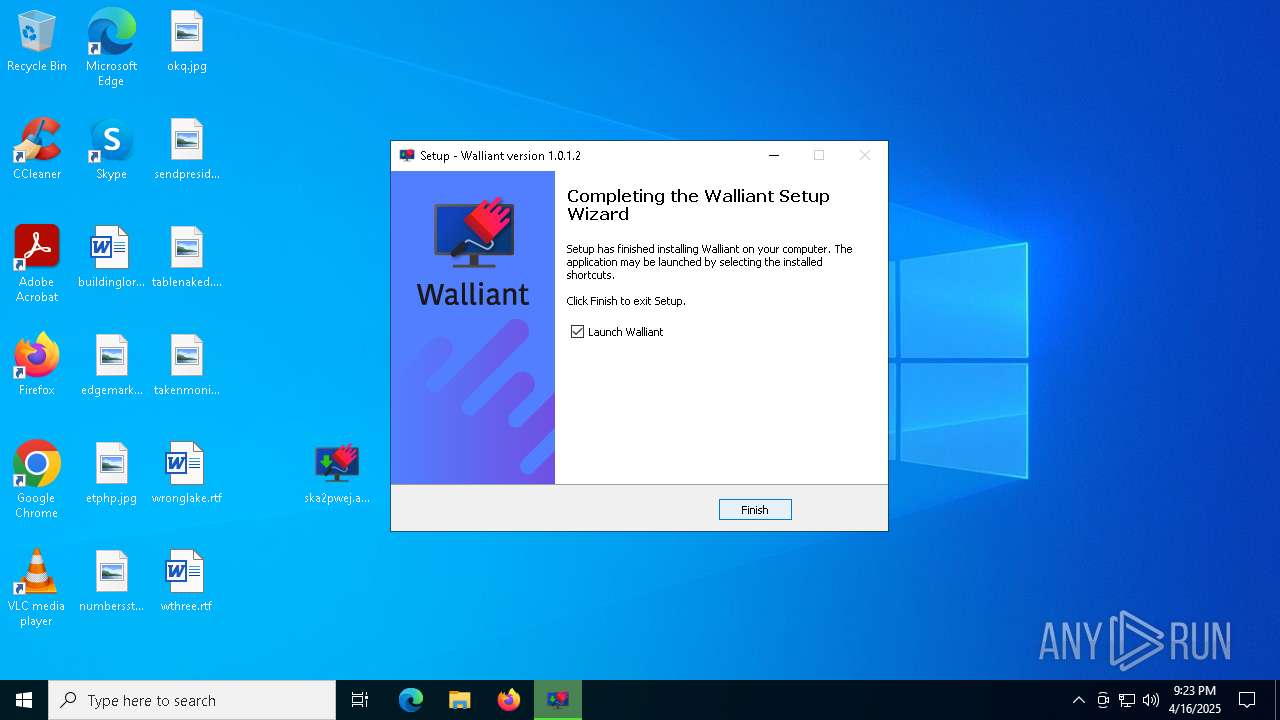
| File name: | Walliant.zip |
| Full analysis: | https://app.any.run/tasks/1a9a8dc7-03da-43d0-a619-980a7a4b545b |
| Verdict: | Malicious activity |
| Analysis date: | April 16, 2025, 21:22:15 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 33968A33F7E098D31920C07E56C66DE2 |
| SHA1: | 9C684A0DADAE9F940DD40D8D037FAA6ADDF22DDB |
| SHA256: | 6364269DBDC73D638756C2078ECB1A39296DDD12B384D05121045F95D357D504 |
| SSDEEP: | 98304:QXEXw3QBAg+V40y49wQ2pFQ0xxYtroaNrZaYzu9:kEA3AAg+Vt9V81xxYtfNLO |
MALICIOUS
Changes the autorun value in the registry
- ska2pwej.aeh.tmp (PID: 8104)
SUSPICIOUS
Reads the Windows owner or organization settings
- ska2pwej.aeh.tmp (PID: 8104)
Executable content was dropped or overwritten
- ska2pwej.aeh.exe (PID: 8084)
- ska2pwej.aeh.tmp (PID: 8104)
Process drops legitimate windows executable
- ska2pwej.aeh.tmp (PID: 8104)
Reads security settings of Internet Explorer
- walliant.exe (PID: 7400)
- walliant.exe (PID: 2552)
Reads Internet Explorer settings
- walliant.exe (PID: 7400)
Reads Microsoft Outlook installation path
- walliant.exe (PID: 7400)
INFO
Manual execution by a user
- ska2pwej.aeh.exe (PID: 8084)
- walliant.exe (PID: 2552)
- mspaint.exe (PID: 7348)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1300)
Reads the computer name
- ska2pwej.aeh.tmp (PID: 8104)
- walliant.exe (PID: 2552)
- walliant.exe (PID: 7400)
Checks supported languages
- ska2pwej.aeh.tmp (PID: 8104)
- ska2pwej.aeh.exe (PID: 8084)
- walliant.exe (PID: 7400)
- walliant.exe (PID: 2552)
Create files in a temporary directory
- ska2pwej.aeh.tmp (PID: 8104)
- ska2pwej.aeh.exe (PID: 8084)
Reads the machine GUID from the registry
- ska2pwej.aeh.tmp (PID: 8104)
- walliant.exe (PID: 2552)
- walliant.exe (PID: 7400)
Reads the software policy settings
- ska2pwej.aeh.tmp (PID: 8104)
- walliant.exe (PID: 7400)
- slui.exe (PID: 7444)
- slui.exe (PID: 5164)
- walliant.exe (PID: 2552)
Creates files or folders in the user directory
- ska2pwej.aeh.tmp (PID: 8104)
- walliant.exe (PID: 7400)
Creates a software uninstall entry
- ska2pwej.aeh.tmp (PID: 8104)
Detects InnoSetup installer (YARA)
- ska2pwej.aeh.exe (PID: 8084)
- ska2pwej.aeh.tmp (PID: 8104)
Compiled with Borland Delphi (YARA)
- ska2pwej.aeh.exe (PID: 8084)
- ska2pwej.aeh.tmp (PID: 8104)
Checks proxy server information
- walliant.exe (PID: 7400)
- slui.exe (PID: 5164)
Application based on Golang
- walliant.exe (PID: 7400)
Detects GO elliptic curve encryption (YARA)
- walliant.exe (PID: 7400)
Disables trace logs
- walliant.exe (PID: 7400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:06:23 18:56:34 |
| ZipCRC: | 0x4b786beb |
| ZipCompressedSize: | 4747047 |
| ZipUncompressedSize: | 5293448 |
| ZipFileName: | ska2pwej.aeh.exe |
Total processes
148
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1300 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Walliant.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2552 | "C:\Users\admin\AppData\Local\Programs\Walliant\walliant.exe" | C:\Users\admin\AppData\Local\Programs\Walliant\walliant.exe | — | explorer.exe | |||||||||||
User: admin Company: Walliant Integrity Level: MEDIUM Description: Walliant Exit code: 0 Version: 1.0.1.2 Modules
| |||||||||||||||
| 5164 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7348 | "C:\WINDOWS\system32\mspaint.exe" "C:\Users\admin\Desktop\takenmonitor.jpg" | C:\Windows\System32\mspaint.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Paint Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7400 | "C:\Users\admin\AppData\Local\Programs\Walliant\walliant.exe" | C:\Users\admin\AppData\Local\Programs\Walliant\walliant.exe | ska2pwej.aeh.tmp | ||||||||||||
User: admin Company: Walliant Integrity Level: MEDIUM Description: Walliant Version: 1.0.1.2 Modules
| |||||||||||||||
| 7412 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7444 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8084 | "C:\Users\admin\Desktop\ska2pwej.aeh.exe" | C:\Users\admin\Desktop\ska2pwej.aeh.exe | explorer.exe | ||||||||||||
User: admin Company: Walliant Integrity Level: MEDIUM Description: Walliant Setup Exit code: 0 Version: 1.0.1.2 Modules
| |||||||||||||||
| 8104 | "C:\Users\admin\AppData\Local\Temp\is-3UQFF.tmp\ska2pwej.aeh.tmp" /SL5="$C0276,4511977,830464,C:\Users\admin\Desktop\ska2pwej.aeh.exe" | C:\Users\admin\AppData\Local\Temp\is-3UQFF.tmp\ska2pwej.aeh.tmp | ska2pwej.aeh.exe | ||||||||||||
User: admin Company: Walliant Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
12 678
Read events
12 590
Write events
86
Delete events
2
Modification events
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Walliant.zip | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1300) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
Executable files
19
Suspicious files
15
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1300 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1300.37049\ska2pwej.aeh.exe | executable | |
MD5:929335D847F8265C0A8648DD6D593605 | SHA256:6613ACB18CB8BF501FBA619F04F8298E5E633CB220C450212BBC9DD2BEF9538D | |||
| 8104 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Temp\is-3BSPV.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 8104 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\unins000.exe | executable | |
MD5:62E5DBC52010C304C82ADA0AC564EFF9 | SHA256:BD54AD7A25594DC823572D9B23A3490FF6B8B1742A75E368D110421AB08909B2 | |||
| 8104 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\AsyncBridge.Net35.dll | executable | |
MD5:35CBDBE6987B9951D3467DDA2F318F3C | SHA256:E4915F18FD6713EE84F27A06ED1F6F555CDBEBE1522792CF4B4961664550CF83 | |||
| 8104 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\is-V8GHJ.tmp | executable | |
MD5:35CBDBE6987B9951D3467DDA2F318F3C | SHA256:E4915F18FD6713EE84F27A06ED1F6F555CDBEBE1522792CF4B4961664550CF83 | |||
| 8104 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\is-FOEMS.tmp | executable | |
MD5:60D3737A1F84758238483D865A3056DC | SHA256:3436C29DEC2C7F633F4766ACAF334F6C395D70EA6180C0EA7C1610591D5D89B9 | |||
| 8104 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\is-M26LJ.tmp | executable | |
MD5:62E5DBC52010C304C82ADA0AC564EFF9 | SHA256:BD54AD7A25594DC823572D9B23A3490FF6B8B1742A75E368D110421AB08909B2 | |||
| 8084 | ska2pwej.aeh.exe | C:\Users\admin\AppData\Local\Temp\is-3UQFF.tmp\ska2pwej.aeh.tmp | executable | |
MD5:62E5DBC52010C304C82ADA0AC564EFF9 | SHA256:BD54AD7A25594DC823572D9B23A3490FF6B8B1742A75E368D110421AB08909B2 | |||
| 8104 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\walliant.exe | executable | |
MD5:60D3737A1F84758238483D865A3056DC | SHA256:3436C29DEC2C7F633F4766ACAF334F6C395D70EA6180C0EA7C1610591D5D89B9 | |||
| 8104 | ska2pwej.aeh.tmp | C:\Users\admin\AppData\Local\Programs\Walliant\Countly.dll | executable | |
MD5:BF6A0F5D2D5F54CEB5B899A2172A335B | SHA256:32EF07A1A2954A40436D625814D0CE0E04F4A45E711BEEBC7E159D4C1B2556B6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
55
DNS requests
40
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7400 | walliant.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAewQY2lHhSMMxu83rcTgyM%3D | unknown | — | — | whitelisted |
7912 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7400 | walliant.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTDZGCsCkDHH%2BXwJVKt4ohdOTWBUQQUy1yTroib%2FkNvVlBSAm14%2FKzhsVoCEApxobDClvXHkGVHCjwgU34%3D | unknown | — | — | whitelisted |
7400 | walliant.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/CodeSigPCA.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7400 | walliant.exe | HEAD | 200 | 137.184.201.80:80 | http://center01.deltaork.com/ | unknown | — | — | unknown |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.32.238.112:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7912 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7400 | walliant.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAQJGBtf1btmdVNDtW%2BVUAg%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6708 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.32.238.112:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
stats.walliant.com |
| unknown |