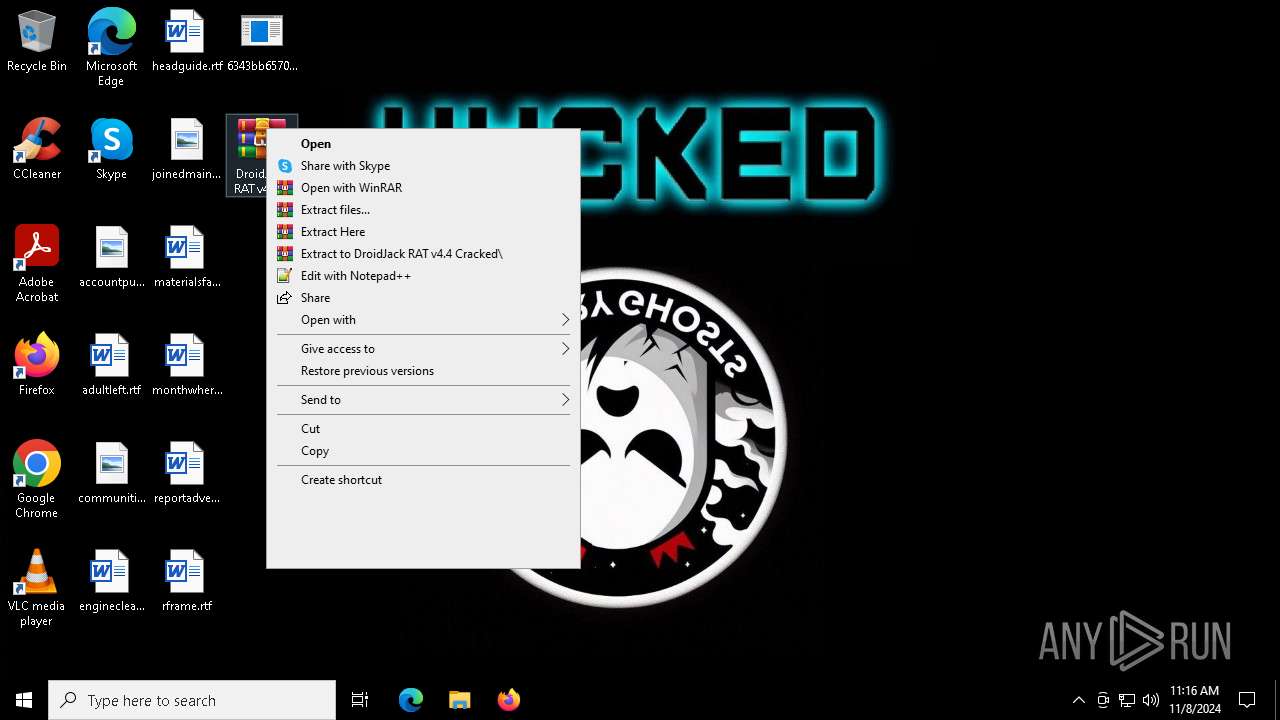
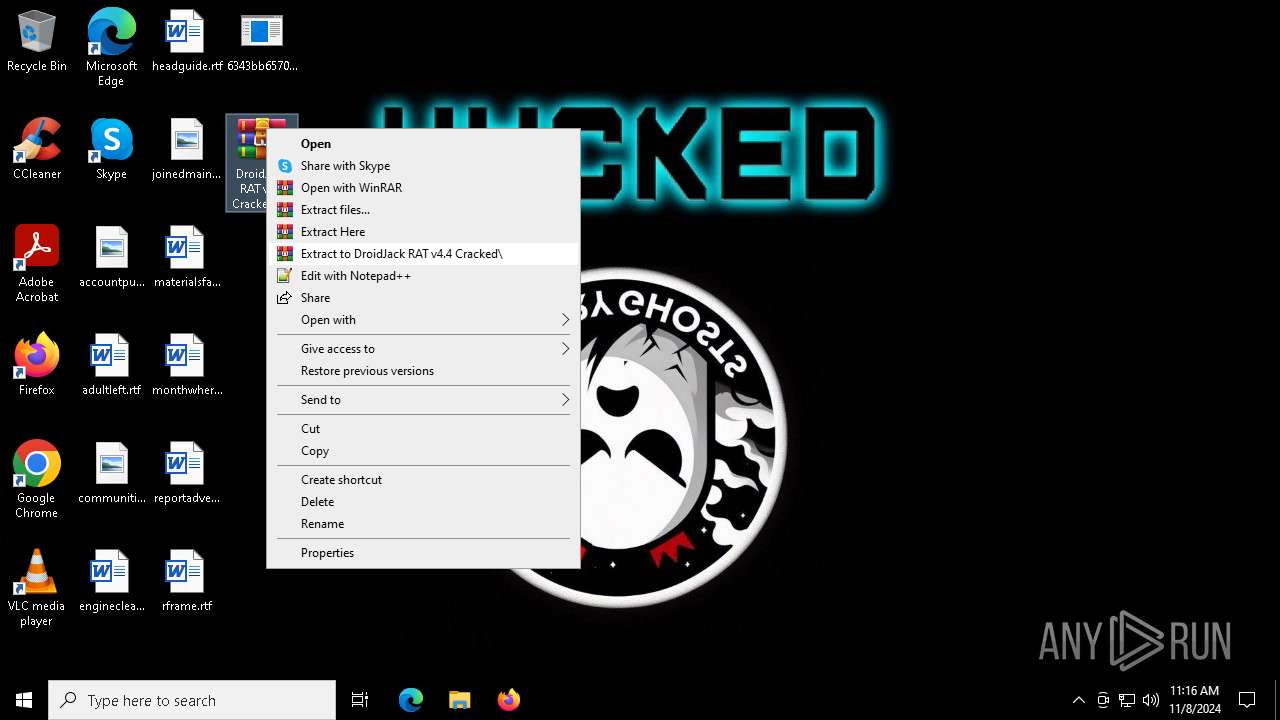
| File name: | 6343bb6570bdea7f0e829312cf5829defa9eb69238fefa6c272650e1e5219a86 |
| Full analysis: | https://app.any.run/tasks/594d2588-45d7-41dc-b160-a907765d9876 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2024, 11:16:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 4 sections |
| MD5: | F112EB122755CDD12D13759B1639AFEE |
| SHA1: | 334CB78CB70535C4BE7DDFAA01B38B853C3CDE44 |
| SHA256: | 6343BB6570BDEA7F0E829312CF5829DEFA9EB69238FEFA6C272650E1E5219A86 |
| SSDEEP: | 49152:AEijzDhqybJ5FhTE8Sz/mxwmku4kFV1bYwVLctMem:AjzhqeJk |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Creates files or folders in the user directory
- 6343bb6570bdea7f0e829312cf5829defa9eb69238fefa6c272650e1e5219a86.exe (PID: 6664)
Checks supported languages
- 6343bb6570bdea7f0e829312cf5829defa9eb69238fefa6c272650e1e5219a86.exe (PID: 6664)
Manual execution by a user
- Taskmgr.exe (PID: 6432)
- Taskmgr.exe (PID: 6936)
- WinRAR.exe (PID: 6344)
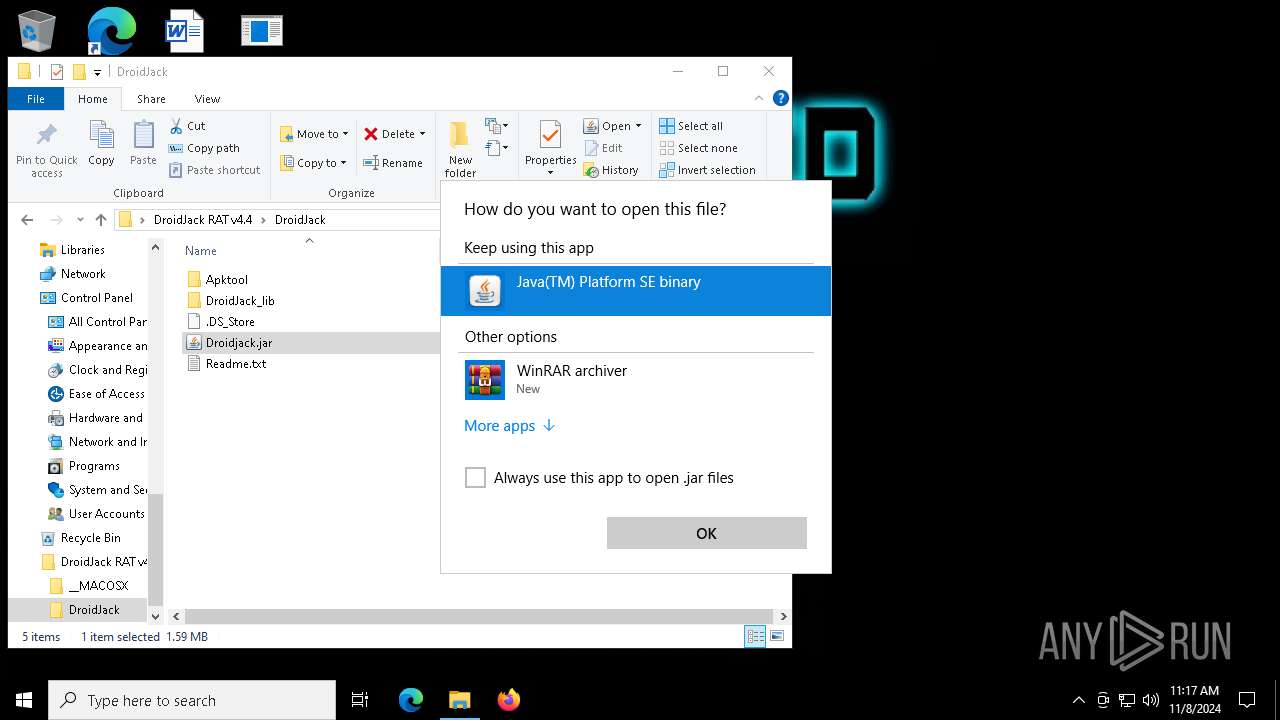
Application based on Java
- javaw.exe (PID: 1744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:06:26 14:57:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.39 |
| CodeSize: | 122880 |
| InitializedDataSize: | 7896576 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x12a7 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
139
Monitored processes
10
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1744 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\Desktop\DroidJack RAT v4.4\DroidJack\Droidjack.jar" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | OpenWith.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3156 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6344 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\DroidJack RAT v4.4 Cracked.rar" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6432 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6664 | "C:\Users\admin\Desktop\6343bb6570bdea7f0e829312cf5829defa9eb69238fefa6c272650e1e5219a86.exe" | C:\Users\admin\Desktop\6343bb6570bdea7f0e829312cf5829defa9eb69238fefa6c272650e1e5219a86.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6704 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 6343bb6570bdea7f0e829312cf5829defa9eb69238fefa6c272650e1e5219a86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6716 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6936 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7024 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 742
Read events
3 729
Write events
12
Delete events
1
Modification events
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6936) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6344) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6936) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AAE92EF77F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AAE92EF77F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AAE92EF77F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AAE92EF77F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AAE92EF77F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000ABE92EF77F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028ABE92EF77F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050ABE92EF77F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AAE92EF77F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070ABE92EF77F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088ABE92EF77F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8ABE92EF77F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8ABE92EF77F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0ABE92EF77F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010ACE92EF77F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AAE92EF77F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AAE92EF77F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AAE92EF77F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040ACE92EF77F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068ACE92EF77F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090ACE92EF77F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8ACE92EF77F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8ACE92EF77F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8ACE92EF77F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028ABE92EF77F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AAE92EF77F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020ADE92EF77F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040ADE92EF77F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068ADE92EF77F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AAE92EF77F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050ABE92EF77F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AAE92EF77F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070ABE92EF77F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088ABE92EF77F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8ABE92EF77F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8ABE92EF77F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AAE92EF77F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088ADE92EF77F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8ADE92EF77F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0ADE92EF77F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AEE92EF77F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AEE92EF77F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AEE92EF77F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AEE92EF77F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
| (PID) Process: | (4040) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.jar\OpenWithProgids |
| Operation: | write | Name: | jarfile |
Value: | |||
| (PID) Process: | (4040) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.jar\UserChoice |
| Operation: | write | Name: | ProgId |
Value: jarfile | |||
| (PID) Process: | (4040) OpenWith.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.jar\UserChoice |
| Operation: | write | Name: | Hash |
Value: H/u8ZNpoR30= | |||
Executable files
6
Suspicious files
31
Text files
571
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6664 | 6343bb6570bdea7f0e829312cf5829defa9eb69238fefa6c272650e1e5219a86.exe | C:\Users\admin\AppData\Local\VirtualStore\wallpaper.bmp | — | |
MD5:— | SHA256:— | |||
| 6344 | WinRAR.exe | C:\Users\admin\Desktop\DroidJack RAT v4.4\DroidJack\Apktool\apktool.jar | java | |
MD5:2C25FD4270D6AFF37C5165342991BCE6 | SHA256:C15CF1B87486D83DBC9E5CE64A03178A64EEEECF62CF08637193BA759F61419B | |||
| 6344 | WinRAR.exe | C:\Users\admin\Desktop\DroidJack RAT v4.4\DroidJack\Apktool\SandroRat\AndroidManifest.xml | xml | |
MD5:5219C1C088A2BFCF1DA2D9CA96E9F5C5 | SHA256:1313F5C0564116D5B47D64C717C9E4862AA8022401E3372232BC66D3862BE461 | |||
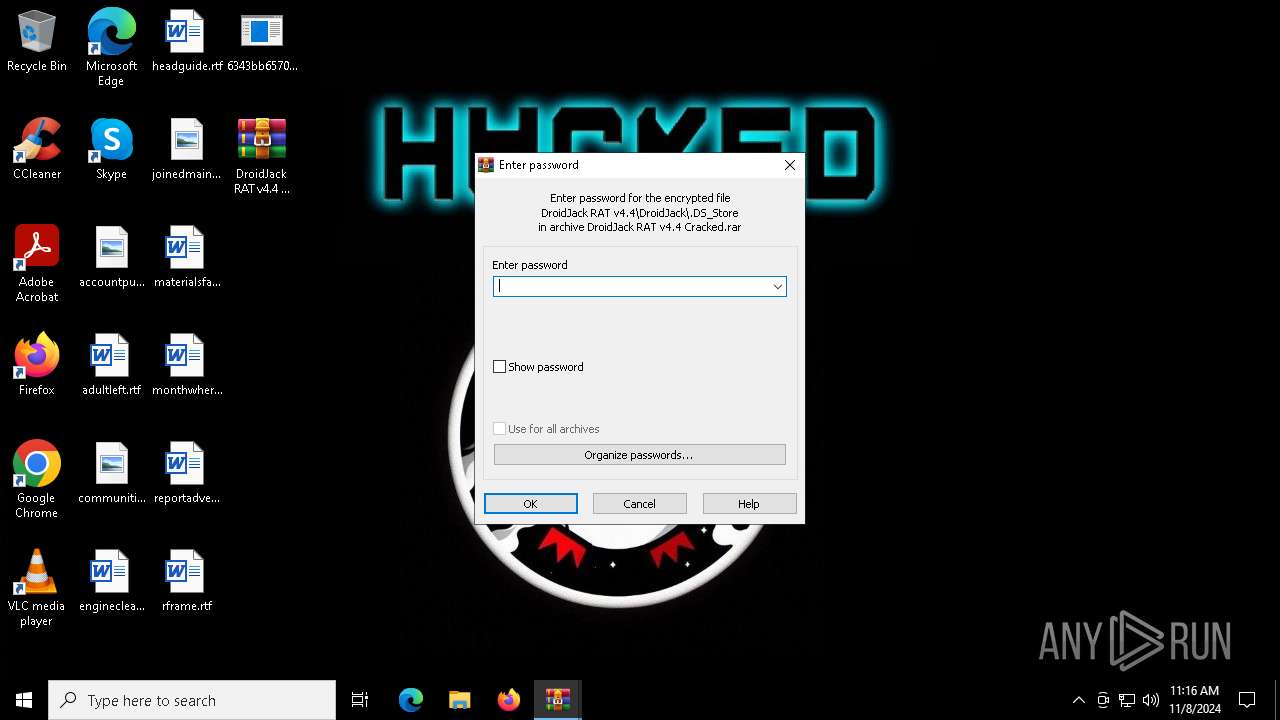
| 6344 | WinRAR.exe | C:\Users\admin\Desktop\DroidJack RAT v4.4\DroidJack\.DS_Store | binary | |
MD5:5EFC66C86F9EE056C23448A95D827D1C | SHA256:923211913F3C80FB88E966BE6301E7965C28785E911372ABA7CB4ADFFAC305A2 | |||
| 6344 | WinRAR.exe | C:\Users\admin\Desktop\DroidJack RAT v4.4\DroidJack\Apktool\aapts.zip | compressed | |
MD5:4D936C19E227412689D07A172CF7C073 | SHA256:9BA477194B6BEE993D26D1051A4E02143540F6B12CF93D498F380EA0E40E1A1A | |||
| 6344 | WinRAR.exe | C:\Users\admin\Desktop\DroidJack RAT v4.4\DroidJack\Apktool\SandroRat\build\apk\res\layout\videoview.xml | xml | |
MD5:ECC1BCC71850722C966C800D4807B89B | SHA256:B3490F616FF5504C4ABA6D27F9538F0389C7E5D4083A5517A544E00888C043E6 | |||
| 6344 | WinRAR.exe | C:\Users\admin\Desktop\DroidJack RAT v4.4\DroidJack\Apktool\SandroRat\build\apk\res\layout\activity_main.xml | binary | |
MD5:AB5FC43FE7544713C5E9848DC609F3C0 | SHA256:2A515E638ECFC7D51EC7096DCEAF4628DC9646386423311133618B74C0BC24D3 | |||
| 6344 | WinRAR.exe | C:\Users\admin\Desktop\DroidJack RAT v4.4\DroidJack\Apktool\SandroRat\build\apk\AndroidManifest.xml | binary | |
MD5:B11EEDBE053EC4CB2AB4C3561F5862BE | SHA256:AABB5C8DA1622B25DBAA4AABC31064CB67004E330E1825A94C7B930BEFE9A323 | |||
| 6344 | WinRAR.exe | C:\Users\admin\Desktop\DroidJack RAT v4.4\DroidJack\Apktool\SandroRat\build\apk\res\drawable-mdpi-v4\ic_launcher.png | image | |
MD5:ACEFC1F320111A8D71BCDB8B4AA0656C | SHA256:05346D62D4096537906928AF523EF9D5997663707A1D48E08F20992584E1424D | |||
| 6344 | WinRAR.exe | C:\Users\admin\Desktop\DroidJack RAT v4.4\DroidJack\Apktool\SandroRat\build\apk\resources.arsc | binary | |
MD5:06B046A2CF17A1C3DB22C75928520039 | SHA256:E267C694C92B56E43E28A0384A1E1B4749036DD7E817E2612138260DFAF2899A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
47
DNS requests
21
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6088 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
540 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
540 | SIHClient.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.218.209.163:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7116 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1744 | javaw.exe | GET | — | 172.232.25.148:80 | http://www.droidjack.net/Terms.html | unknown | — | — | malicious |
1744 | javaw.exe | GET | — | 172.232.25.148:80 | http://www.droidjack.net/Terms.html | unknown | — | — | malicious |
6944 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
3524 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6944 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 23.218.209.163:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
1744 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |