| File name: | 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9 |
| Full analysis: | https://app.any.run/tasks/661c5450-7018-44fa-82d9-39203d3c294e |
| Verdict: | Malicious activity |
| Analysis date: | October 22, 2024, 20:43:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 5228C093AF0EB2597539AC2E1A71BD11 |
| SHA1: | C9518010EC7E71ED2C2D41F44F4D70F00F19BB9F |
| SHA256: | 633914338EEB5FE0181C69710C9278D01C31ADA90EEA53D5B2B14E9BAD19FBA9 |
| SSDEEP: | 98304:XCIiidV585p5pJwGr36iv/AgKtx6OHfrKzYHuX8QQ8CC/342mgUjelgE3b9OIMYT:/uHdeegZk1cN4Bpnm9ArsgY |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe (PID: 5952)
Checks Windows Trust Settings
- 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe (PID: 5952)
Reads the BIOS version
- 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe (PID: 5952)
INFO
Checks supported languages
- 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe (PID: 5952)
Reads the computer name
- 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe (PID: 5952)
Reads the software policy settings
- 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe (PID: 5952)
Reads the machine GUID from the registry
- 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe (PID: 5952)
Checks proxy server information
- 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe (PID: 5952)
Themida protector has been detected
- 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe (PID: 5952)
UPX packer has been detected
- 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe (PID: 5952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:10:21 14:50:06+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 5050368 |
| InitializedDataSize: | 12328960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x15c3058 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.0.0 |
| ProductVersionNumber: | 1.3.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 1.3.0.0 |
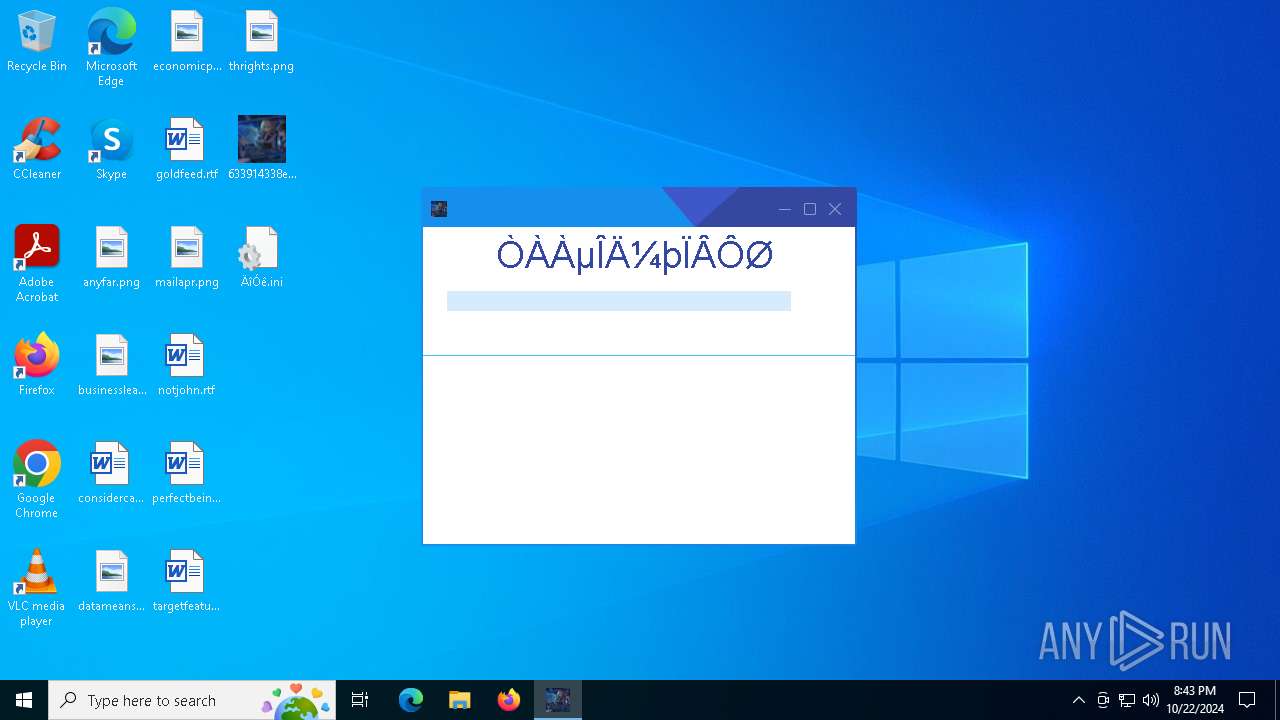
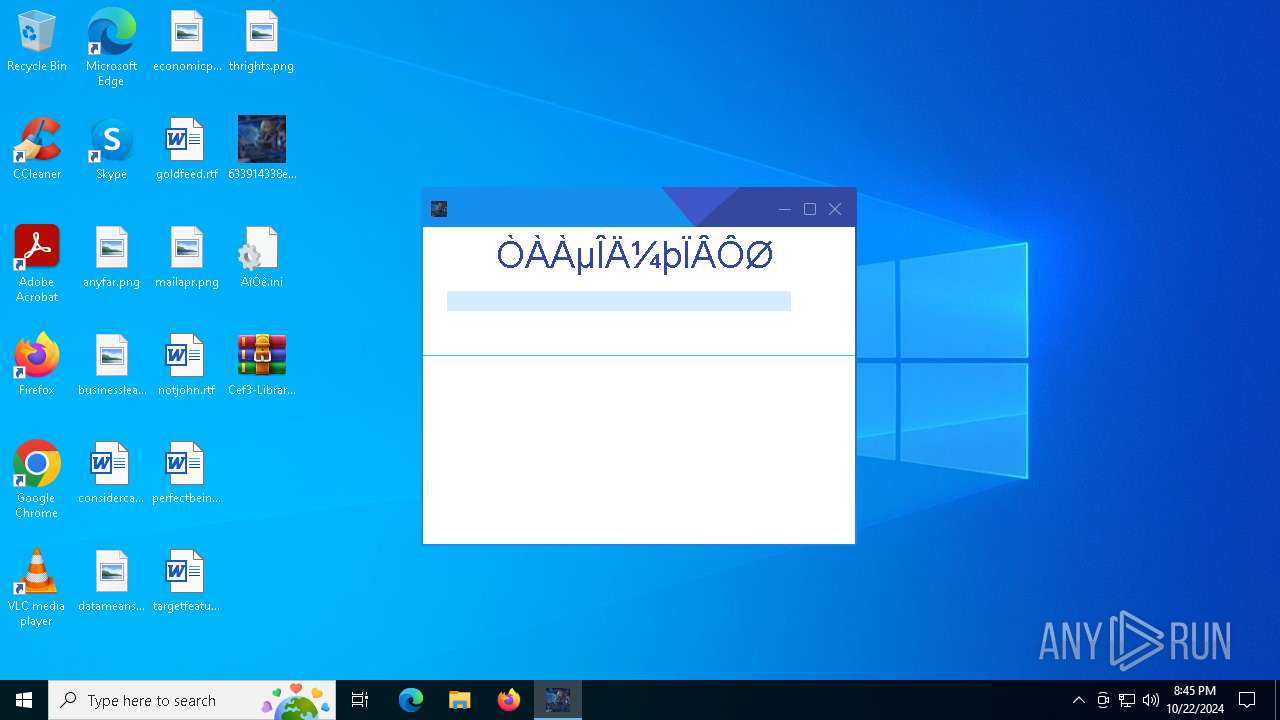
| FileDescription: | 念雨登录器 |
| ProductName: | 念雨登录器2.5 |
| ProductVersion: | 1.3.0.0 |
| LegalCopyright: | 作者版权所有 请尊重并使用正版 |
| Comments: | 念雨登录器 |
Total processes
122
Monitored processes
1
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5952 | "C:\Users\admin\Desktop\633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe" | C:\Users\admin\Desktop\633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: 念雨登录器 Version: 1.3.0.0 Modules
| |||||||||||||||
Total events
3 523
Read events
3 517
Write events
6
Delete events
0
Modification events
| (PID) Process: | (5952) 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Multimedia\DrawDib |
| Operation: | write | Name: | 1280x720x32(BGR 0) |
Value: 31,31,31,31 | |||
| (PID) Process: | (5952) 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings |
| Operation: | write | Name: | JITDebug |
Value: 0 | |||
| (PID) Process: | (5952) 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: D2CE080000000000 | |||
| (PID) Process: | (5952) 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5952) 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5952) 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
3
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5952 | 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\c1e48a7a6eb5019a88cdd414b0b7e246[1].txt | binary | |
MD5:E7DAF1108902389CA2AD5F4C311111CF | SHA256:D692E6EEC9CABDA20B4D43FA3D63C3105D36D0CF85158E8CB2C35038EDDA38D4 | |||
| 5952 | 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\fn[1].htm | html | |
MD5:455CBEE2B4766F650EF6886A43024D00 | SHA256:86AFF0E287C6FC202C12C78F8AEE3B95C8D02640A32F6594333ED3A5704D7993 | |||
| 5952 | 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\iU5He27gt6de[1].htm | html | |
MD5:890768494757FF9D10A22920BA997584 | SHA256:2D06E5EE8BF87215F9A310C4E9A54842C5B03B6C92445D22C05D0624836B4D93 | |||
| 5952 | 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | C:\Users\admin\Desktop\ÄîÓê.ini | text | |
MD5:19A591B5ABFECA8D3600AB6B7E9435B0 | SHA256:8D91B3E01BAC5720FEA089363E1C5B9FEDD89D9DDE5CEB8470681E0494863B39 | |||
| 5952 | 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\ajaxm[1].php | binary | |
MD5:B304A9C1156AE1FCD6D0554A4DA13526 | SHA256:8A0D81F6F5B757C3D988214069C9C4BCB1E3AE1658884934143CB0F3867F5E3A | |||
| 5952 | 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\6dea143f6cd01f01a08a8474967ece65[1].txt | binary | |
MD5:34CCF29FA429B1CFE424182F89C45B19 | SHA256:D36A0E0F2FCD93D21743EC0B179F466AEB353140ED277F26E167A79B30F9A4F2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
35
DNS requests
12
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5952 | 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | HEAD | 200 | 103.235.46.96:80 | http://www.baidu.com/ | unknown | — | — | whitelisted |
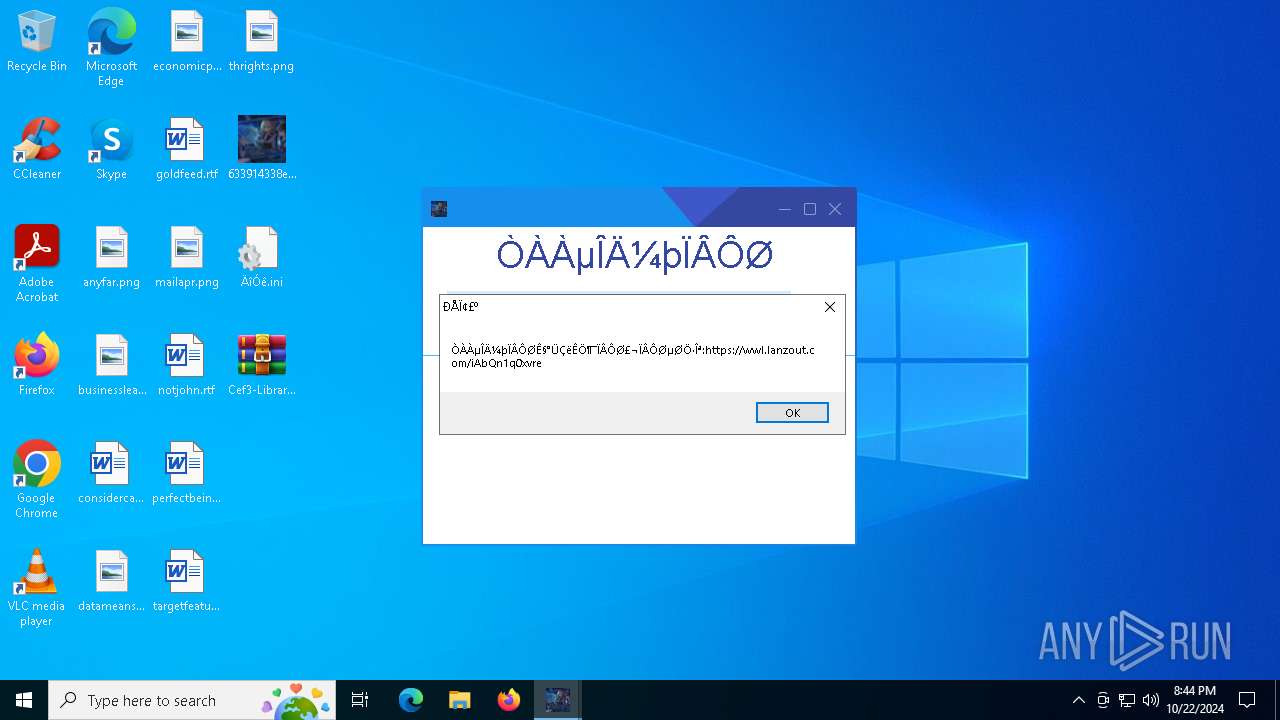
— | — | GET | 200 | 60.165.116.42:443 | https://nianyu.lanzoul.com/iU5He27gt6de | unknown | — | — | unknown |
— | — | GET | — | 1.56.98.203:443 | https://c1031.lanosso.com/5802f60a876ff96f4c25c1715cea07d1/67180e7d/2024/08/15/8ed51b645a5325ce23b738f56106c75b.zip?fileName=Cef3-Library.zip | unknown | — | — | unknown |
5952 | 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | GET | 302 | 47.98.88.99:80 | http://develope-oss.lanzouc.com/file/?VzECPF5vAjMACVRsU2ZQPFNsADhUSAViVzYEMV0sVxoBaFtuCSZVYAktV3gHfVYtVWYFcAV8UzdWOFQ+Bz5bBVc+AjFePgJnAG9UN1MxUGdTPgAyVD4FM1d2BGRdcldrAThbPwlnVTAJZlc4B2FWZVUpBXAFKlNsVmNUYgdpW25XeAJlXjsCeQBnVDdTKFBpU2wAYVQ+BTZXMgQ0XTVXYwFgWzkJZ1UzCWpXYgc2VmVVPAViBW1TYlZpVDQHbltsV2YCZV41AjUAYVQ3U2VQf1NzAGxUewUhVyUEcV1kVyQBaFtoCWlVMAlrVzMHYFZlVTcFNgV8UyVWOFQ/Bz5bPFdqAmReNAJkAG9UNFM0UGFTMQA3VDsFKVd+BCRdZ1c6AXZbMQllVTYJbVc4B2VWZVU2BTgFa1NoVndUJwcrWy1XagJkXjQCZABlVDRTMFBmUz8ANlQ5BSFXJQRrXXFXawE3WzUJelU2CWZXLwdiVmRVIQUyBW9TYFZ/VHQHP1s1VyACO15cAjUAPVQ/UzY= | unknown | — | — | unknown |
— | — | GET | 200 | 163.181.92.234:443 | https://note.youdao.com/yws/api/note/6dea143f6cd01f01a08a8474967ece65?sev=j1&editorType=1&editorVersion=new-json-editor | unknown | binary | 56.9 Kb | whitelisted |
3524 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 61.54.86.137:443 | https://nianyu.lanzoul.com/ajaxm.php | unknown | binary | 603 b | unknown |
— | — | GET | 200 | 116.153.39.128:443 | https://nianyu.lanzoul.com/fn?AmRWPApmD2IGZVMzBmRUYlc6AjICaVB0BXZaYVU4VGIAMls1DWYGYQVjBmRRNAYzBnpVJ1ZsAGBWIlI9UGtTPAJpVmQKLg9mBiZTVQYnVAQ_c | unknown | html | 1.81 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3524 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.186:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3524 | RUXIMICS.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
note.youdao.com |
| whitelisted |
nianyu.lanzoul.com |
| unknown |
www.baidu.com |
| whitelisted |
develope-oss.lanzouc.com |
| unknown |
c1031.lanosso.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Misc activity | ET POLICY Pastebin-style service note .youdao .com in DNS query |
2172 | svchost.exe | Misc activity | ET POLICY Pastebin-style service note .youdao .com in DNS query |
5952 | 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | Misc activity | ET POLICY Pastebin-style service (note .youdao .com) in TLS SNI |
5952 | 633914338eeb5fe0181c69710c9278d01c31ada90eea53d5b2b14e9bad19fba9.exe | Misc activity | ET POLICY Pastebin-style service (note .youdao .com) in TLS SNI |
— | — | Potential Corporate Privacy Violation | ET POLICY Unsupported/Fake Windows NT Version 5.0 |
1 ETPRO signatures available at the full report